Fuzzy Keyword Searchable Encryption Scheme Based on Blockchain
Abstract
:1. Introduction
2. Related Work
- (1)
- Fuzzy keyword search. In this paper, fuzzy keyword sets are constructed by editing distance, and security indexes are constructed for each fuzzy keyword set. The cloud server can return search results by searching for matches between trap doors and security indexes. When a keyword inconsistency problem occurs, our scheme will deduce some valid keywords from the input keyword as much as possible, and return the closest matching document.
- (2)
- Fair payment. In order to ensure the correctness of the results obtained by the data user, the data user generates an authentication tag for each fuzzy keyword set to verify the search results. At the same time, the smart contract is deployed to perform the validation operation and return the correct results to the user. In addition, smart contracts can automatically detect malicious behaviors of users or cloud servers and punish them accordingly to ensure the honest behavior of all participants so as to achieve fair payment.
- (3)
- Dynamic update. To improve system availability, our scheme supports the addition, modification, and deletion of cloud data. In addition, through security analysis and performance comparison analysis, it is proven that the scheme is secure and effective and can meet the requirements of ciphertext search applications in the cloud environment.
3. Preliminaries
3.1. Symmetric Searchable Encryption
3.2. Pseudorandom Function and Message Authentication Function
3.3. Edit Distance
- (1)
- word → ward (o → a)
- (2)
- ward → war (delete d)
- (3)
- war → wear (insert e)
3.4. Inverted Index
3.5. Security Index
4. Problem Formulation
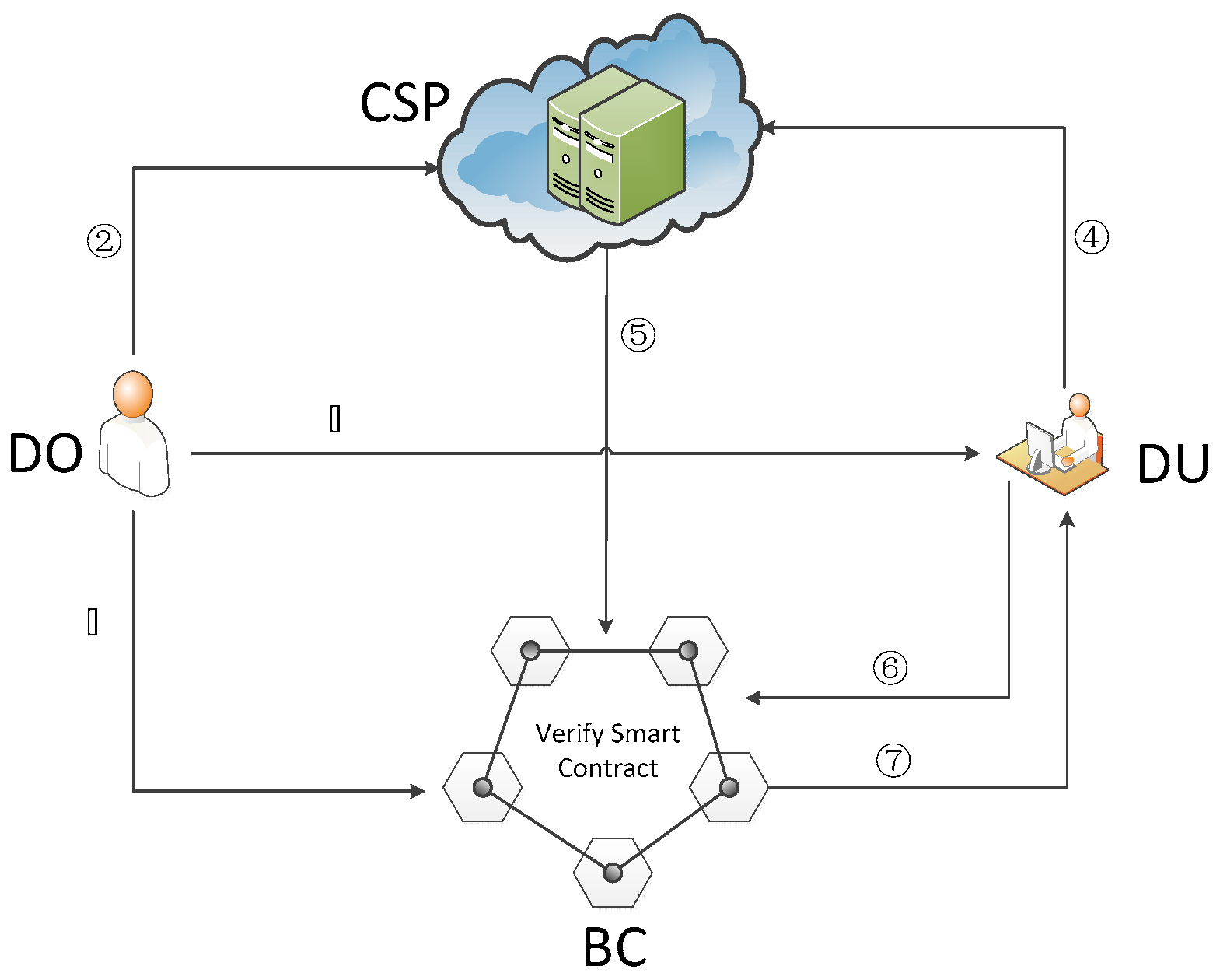
4.1. System Model
4.2. Algorithm Definition
- (1)
- : The algorithm is executed by the DO, which inputs security parameter and outputs the key set .
- (2)
- : The algorithm is executed by the DO, which inputs key set and the plaintext set and then outputs the security index and the encrypted document set .
- (3)
- : The algorithm is executed by the DU, which inputs security parameter and query keyword and then outputs the search trap door .
- (4)
- : The algorithm is executed by the CSP. The CSP inputs trap door , security index , and encrypted document set and then outputs encrypted document result and verification tag pair .
- (5)
- : The algorithm is executed by a smart contract. The smart contract inputs security parameter , the encrypted document set , search trap door , and verification tag pair and then outputs receive or reject.
- (6)
- : The algorithm is executed by the DU, which inputs key and encrypted document set and then outputs plaintext set .
- (7)
- : The algorithm is executed by the DO. The DO inputs key set , adds the new document , modifies or deletes the document , and then outputs the new encrypted document set , security index , and verification tag .
4.3. Specific Construction
- (1)
- : The data owner inputs the security parameters and outputs the key set , where is the key for encrypting and decrypting documents; , is the key of MAC, is the key of PRP-π, and is the key of PRF-f.
- (2)
- : In order to improve the search efficiency of the system, we extend the inverted index and construct a linked list with three nodes as the index. The structure of the index is shown in Figure 2.
- (3)
- : When data users want to search for files that contain the keyword , they first calculate trap and send it to the cloud server.
- (4)
- : When the cloud server receives the trapdoor, it looks for all in . If the exists in the index , make . Then, find the corresponding index file and corresponding proof and calculate to decrypt the security index , which is used to obtain the inverted index . If , the cloud server adds to ; otherwise, do not add it. Finally, the cloud service submits , , together with the margin to the blockchain to complete the verification.
- (5)
- : Users invoke smart contracts by submitting service fees and a search trapdoor to the blockchain. The blockchain extracts from . If is in , the jth bit in is 1; otherwise, it is 0. Then, the blockchain computes , where . Then, check if is equal to . If so, the blockchain sends the result to the data user and submits the deposit and service fee to the cloud server; otherwise, it rejects the result. In addition, the deposit of the cloud server is deducted as a penalty, and the service fee is returned to the user.
- (6)
- : The data user decrypts by computing .
- (7)
- : DO can add document , delete document or dynamically modify document , output the updated encrypted document , security index , and verification tag , and upload them to the cloud again.
5. Scheme Analysis
5.1. Security Analysis
- (1)
- Adversary A selects an arbitrary set of document sets and keyword sets and sends them to the challenger.
- (2)
- The challenger uses the key generation algorithm to obtain the key set K and, on this basis, uses the encryption algorithm and index generation algorithm to obtain and then sends to adversary A.
- (3)
- Adversary A selects a keyword and sends it to the challenger.
- (4)
- Challenger sends trapdoor to adversary A.
- (5)
- Adversary A outputs .
- (1)
- Adversary A chooses the same set as in the real games and sends it to the simulator Sim.
- (2)
- Simulator Sim calculates and sends it to adversary A.
- (3)
- Adversary A selects a keyword and sends it to simulator Sim.
- (4)
- Simulator Sim calculates the trapdoor and sends it to adversary A.
- (5)
- Adversary A outputs .
5.2. Fairness Analysis
5.3. Performance Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Song, D.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the 2000 IEEE Security and Privacy Symposium, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
- Goh, E.-J. Secure Indexes. Cryptology ePrint Archive. 2003. Available online: http://eprint.iacr.org/2003/216 (accessed on 19 September 2022).
- Curtmola, R.; Garay, J.; Kamara, S.; Ostrovsky, R. Searchable symmetric encryption: Improved definitions and efficient constructions. J. Comput. Secur. 2011, 19, 895–934. [Google Scholar] [CrossRef] [Green Version]
- Guo, C.; Zhuang, R.; Chang, C.-C.; Yuan, Q. Dynamic multi-keyword ranked search based on Bloom filter over encrypted cloud data. IEEE Access 2019, 7, 35826–35837. [Google Scholar] [CrossRef]
- Chai, Q.; Gong, G. Verifiable symmetric searchable encryption for semi-honest-but-curious cloud servers. In Proceedings of the IEEE International Conference on Communications(ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 917–922. [Google Scholar]
- Jiang, X.; Yu, J.; Yan, J.; Hao, R. Enabling efficient and verifiable multikeyword ranked search over encrypted cloud data. Inf. Sci. Int. J. 2017, 403–404, 22–41. [Google Scholar]
- Zhang, J.; Wu, M.; Wang, J.; Liu, P.; Jiang, Z.; Peng, C. Secure and verifiable multi-keyword searchable encryption scheme in cloud. J. Commun. 2021, 42, 139–149. [Google Scholar]
- Cai, C.; Weng, J.; Yuan, X.; Wang, C. Enabling reliable key-word search in encrypted decentralized storage with fairness. IEEE Trans. Depend. Sec. Comput. 2018, 18, 131–144. [Google Scholar] [CrossRef]
- Li, H.; Zhang, F.; He, J.; Tian, H. A searchable symmetric encryption scheme using BlockChain. arXiv 2017, arXiv:1711.01030. [Google Scholar]
- Hu, S.; Cai, C.; Wang, Q.; Wang, C.; Luo, X.; Ren, K. Searching an encrypted cloud meets blockchain: A decentralized, reliable and fair realization. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 792–800. [Google Scholar]
- Zhang, Y.; Deng, R.H.; Shu, J.; Yang, K.; Zheng, D. TKSE: Trust-worthy keyword search over encrypted data with two-side verifiability via blockchain. IEEE Access 2018, 6, 31077–31087. [Google Scholar] [CrossRef]
- Chen, L.; Lee, W.-K.; Chang, C.-C.; Choo, K.-K.-R.; Zhang, N. Blockchain based searchable encryption for electronic health record sharing. Future Gener. Comput. Syst. 2019, 95, 420–429. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, D.; Zhang, Y. Blockchain-based personal health records sharing scheme with data integrity verifiable. IEEE Access 2019, 7, 102887–102901. [Google Scholar] [CrossRef]
- Li, H.; Wang, T.; Qiao, Z.; Yang, B.; Gong, Y.; Wang, J.; Qiu, G. Blockchain-based searchable encryption with efficient result verification and fair payment. J. Inf. Secur. Appl. 2021, 58, 102791. [Google Scholar] [CrossRef]
- Li, J.; Wang, Q.; Wang, C.; Cao, N.; Ren, K.; Lou, W. Fuzzy key-word search over encrypted data in cloud computing. In Proceedings of the IEEEINFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–5. [Google Scholar]
- Wang, C.; Ren, K.; Yu, S.; Mahendra Raje Urs, K. Achieving usableand privacy-assured similarity search over outsourced cloud data. In Proceedings of the IEEEINFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 451–459. [Google Scholar]
- Ge, X.; Yu, J.; Hu, C.; Zhang, H.; Hao, R. Enabling efficient verifiable fuzzy keyword search over encrypted data in cloud computing. IEEE Access 2018, 6, 45725–45739. [Google Scholar] [CrossRef]
- Jiang, J.; Cai, L.; Wei, P.; Li, L. Aretrieval scheme supporting verifiable ciphertext fuzzy keyword. Comput. Eng. Appl. 2020, 56, 74–80. [Google Scholar]
- Yan, X.; Yuan, X.; Ye, Q.; Tang, Y. Blockchain-Based Searchable Encryption Scheme With Fair Payment. IEEE Access 2020, 8, 109687–109706. [Google Scholar] [CrossRef]
- Curtmola, R.; Garay, J.; Kamara, S.; Ostrovsky, R. Searchable symmetric encryption: Improved definitions and efficient constructions. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 79–88. [Google Scholar]

| F1 | F2 | F3 | ··· | FN | |
|---|---|---|---|---|---|
| w1 | 1 | 1 | 0 | ··· | 0 |
| w2 | 0 | 1 | 1 | ··· | 0 |
| w3 | 1 | 0 | 0 | ··· | 1 |
| ⋮ | ⋮ | ⋮ | ⋮ | ⋮ | |
| wn | 0 | 0 | 1 | ··· | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, Y.; Lu, J.; Feng, T. Fuzzy Keyword Searchable Encryption Scheme Based on Blockchain. Information 2022, 13, 517. https://doi.org/10.3390/info13110517
Jiang Y, Lu J, Feng T. Fuzzy Keyword Searchable Encryption Scheme Based on Blockchain. Information. 2022; 13(11):517. https://doi.org/10.3390/info13110517
Chicago/Turabian StyleJiang, Yongbo, Juncheng Lu, and Tao Feng. 2022. "Fuzzy Keyword Searchable Encryption Scheme Based on Blockchain" Information 13, no. 11: 517. https://doi.org/10.3390/info13110517
APA StyleJiang, Y., Lu, J., & Feng, T. (2022). Fuzzy Keyword Searchable Encryption Scheme Based on Blockchain. Information, 13(11), 517. https://doi.org/10.3390/info13110517






