A Subjective Logical Framework-Based Trust Model for Wormhole Attack Detection and Mitigation in Low-Power and Lossy (RPL) IoT-Networks
Abstract
:1. Introduction
- A secure version of RPL-based IoT and WSN devices to detect and mitigate wormhole attacks.
- A controller-based hierarchical model to calculate the trust metrics for each node separately utilizing the subjective logic framework.
- A system that enhances the QoS-based parameters, keeping in view the resource-constrained nature of the RPL-based IoT and WSN device.
1.1. RPL
1.2. RPL Security
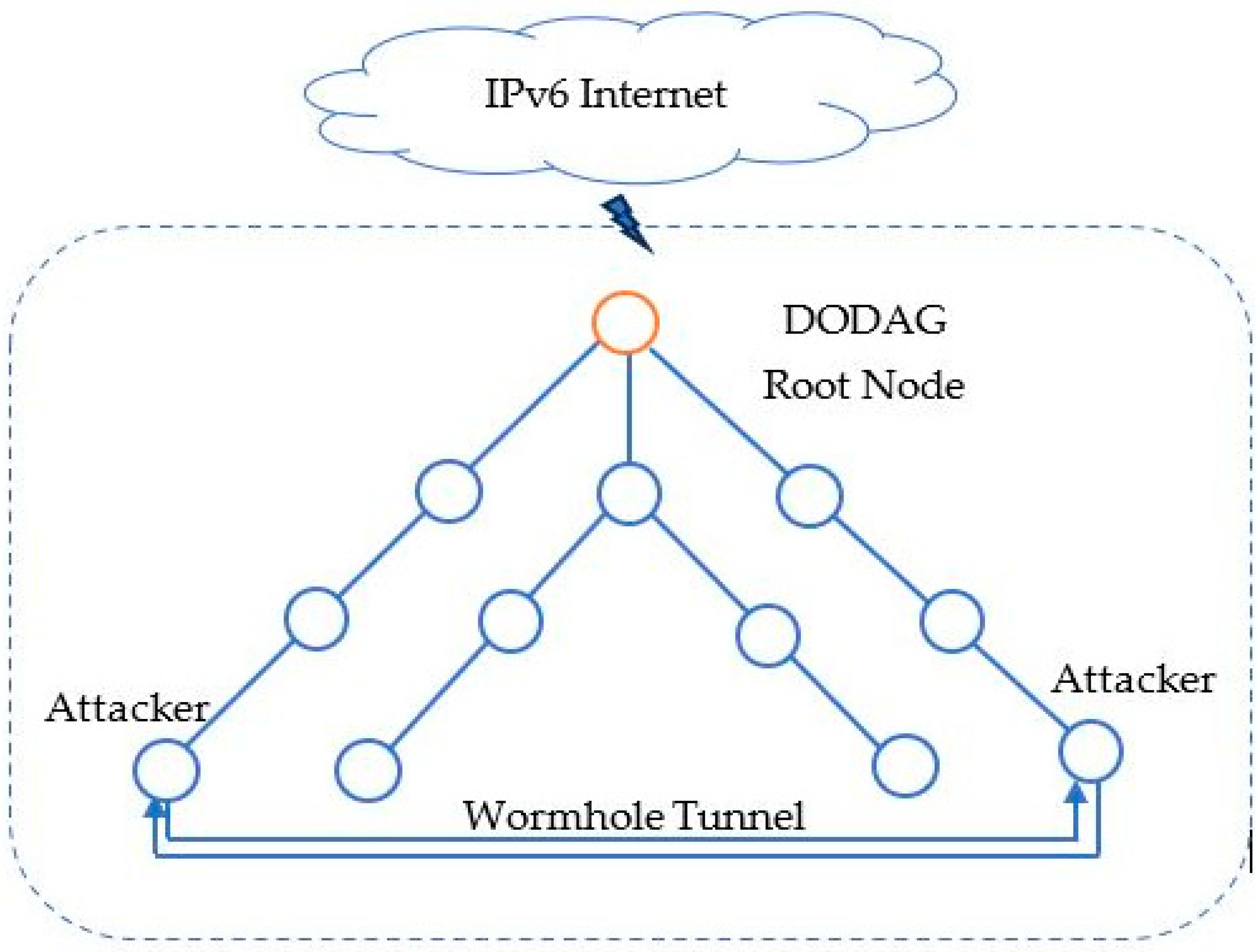
1.3. Wormhole Attack
1.4. SLF Trust Model
2. Related Work
3. Proposed Methodology (SLF-RPL)
3.1. Device Layer
3.2. Sink Layer
3.3. Controller Layer
3.4. Trust Model
3.5. Trust Calculation
3.6. Trust Aggregation
3.7. Discounting Method
3.8. Trust Model Evaluation
3.9. Selecting Nodes for Routing
3.10. Isolating the Attacker Node
4. Experiments and Results
4.1. Simulation Setup
4.2. Experimentation
4.3. Results Analysis
4.3.1. Wormhole Implementation
4.3.2. Attack Detection Rate
4.3.3. Packet Loss Ratio
4.3.4. Energy Consumption
4.3.5. Average Residual Energy
4.3.6. Attack Detection Time
4.4. Discussion of Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Alam, T. A reliable communication framework and its use in internet of things (IoT). CSEIT1835111|Receiv. 2018, 10, 450–456. [Google Scholar]
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. IETF 2012, rfc 6550. [Google Scholar]
- Lamaazi, H.; Benamar, N.; Jara, A.J. RPL-based networks in static and mobile environment: A performance assessment analysis. J. King Saud Univ.-Comput. Inf. Sci. 2018, 30, 320–333. [Google Scholar] [CrossRef]
- Arya, N.; Singh, U.; Singh, S. Detecting and avoiding of wormhole attack and collaborative blackhole attack on MANET using trusted AODV routing algorithm. In Proceedings of the 2015 International Conference on Computer, Communication and Control (IC4), Indore, India, 10–12 September 2015. [Google Scholar]
- Adat, V.; Gupta, B.B. Security in Internet of Things: Issues, challenges, taxonomy, and architecture. Telecommun. Syst. 2018, 67, 423–441. [Google Scholar] [CrossRef]
- Anthea, M.; Badonnel, R.; Chrisment, I. A Taxonomy of Attacks in RPL-based Internet of Things. Int. J. Netw. Secur. 2016, 18, 459–473. [Google Scholar]
- Iova, O.; Picco, P.; Istomin, T.; Kiraly, C. Rpl: The routing standard for the internet of things… or is it? IEEE Commun. Mag. 2016, 54, 16–22. [Google Scholar] [CrossRef]
- Pallavi, K.; Jaballah, W.B.; Conti, M.; Lal, C. LiDL: Localization with early detection of sybil and wormhole attacks in IoT networks. Comput. Secur. 2020, 94, 101849. [Google Scholar]
- Ahmed, R.; Matrawy, A.; Lung, C.-H. Routing attacks and mitigation methods for RPL-based Internet of Things. IEEE Commun. Surv. Tutor. 2018, 21, 1582–1606. [Google Scholar]
- Mariam, M.S.; Murugesan, R.K.; Jhanjhi, N.Z.; Jung, L.T. SMTrust: Proposing trust-based secure routing protocol for RPL attacks for IoT applications. In Proceedings of the 2020 International Conference on Computational Intelligence (ICCI), Bandar Seri Iskandar, Malaysia, 8–9 October 2020; IEEE: Piscateville, NJ, USA, 2020; pp. 305–310. [Google Scholar]
- Minalini, G.; Dutta, M. Intrusion detection of wormhole attack in IoT: A review. In Proceedings of the 2018 International Conference on Circuits and Systems in Digital Enterprise Technology (ICCSDET), Kottayam, India, 21–22 December 2018; IEEE: Piscateville, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Parvathy, K. Wormhole Attacks in Wireless Sensor Networks (WSN) & Internet of Things (IoT): A Review. Int. J. Recent Technol. Eng.IJRTE 2021, 10, 199–203. [Google Scholar]
- Pericle, P.; Vallati, C.; Varano, D.; Anastasi, G.; Dini, G. Implementation of a wormhole attack against a rpl network: Challenges and effects. In Proceedings of the 2018 14th Annual Conference on Wireless On-demand Network Systems and Services (WONS), Isola, France, 6–8 February 2018; IEEE: Piscateville, NJ, USA, 2018; pp. 95–102. [Google Scholar]
- Al Muhtadi, J.; Alamri, R.A.; Khan, F.A.; Saleem, K. Subjective logic-based trust model for fog computing. Comput. Commun. 2021, 178, 221–233. [Google Scholar] [CrossRef]
- Mohammad, P.; Seifi, Y.; Nasiri, M.; Bag-Mohammadi, M. PCC-RPL: An efficient trust-based security extension for RPL. Inf. Secur. J. A Glob. Perspect. 2022, 31, 168–178. [Google Scholar]
- Jhanjhi, N.Z.; Brohi, S.N.; Malik, N.A.; Humayun, M. Proposing a hybrid rpl protocol for rank and wormhole attack mitigation using machine learning. In Proceedings of the 2020 2nd International Conference on Computer and Information Sciences (ICCIS), Sakaka, Saudi Arabia, 13–15 October 2020; IEEE: Piscateville, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Fakher, S.; Shokair, M.; Moawad, M.; Sharshar, K. The Main Effective Parameters on WSN Performance. 2015. Available online: https://www.semanticscholar.org/paper/The-main-effective-parameters-on-wireless-sensor-Fakher-Shokair/6f6ae51109f8e415170e6d1943f98f630b938d3b (accessed on 1 July 2023).
- Bhawsar, A.; Pandey, Y.; Singh, U. Detection and prevention of wormhole attack using the trust-based routing system. In Proceedings of the 2020 International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 2–4 July 2020; IEEE: Piscateville, NJ, USA, 2020; pp. 809–814. [Google Scholar]
- Violettas, G.; Simoglou, G.; Petridou, S.; Mamatas, L. A Softwarized Intrusion Detection System for the RPL-based Internet of Things networks. Future Gener. Comput. Syst. 2021, 125, 698–714. [Google Scholar] [CrossRef]
- NAkhuseyinoglu, N.B.; Karimi, M.; Abdelhakim, M.; Krishnamurthy, P. On automated trust computation in iot with multiple attributes and subjective logic. In Proceedings of the 2020 IEEE 45th Conference on Local Computer Networks (LCN), Sydney, Australia, 16–19 November 2020; IEEE: Piscateville, NJ, USA, 2020; pp. 267–278. [Google Scholar]
- Wang, M.; Zhu, T.; Zhang, T.; Zhang, J.; Yu, S.; Zhou, W. Security and privacy in 6G networks: New areas and new challenges. Digit. Commun. Netw. 2020, 6, 281–291. [Google Scholar] [CrossRef]
- Murugesan, S.M. A Study on Leveraging Blockchain Technology for IoT Security Enhancement. In Proceedings of the 2018 Fourth International Conference on Advances in Computing, Communication & Automation (ICACCA), Subang Jaya, Malaysia., 26–28 October 2018. [Google Scholar]
- Airehrour, D.; Gutierrez, J.A.; Ray, S.K. SecTrust-RPL: A secure trust-aware RPL routing protocol for Internet of Things. Future Gener. Comput. Syst. 2019, 93, 860–876. [Google Scholar] [CrossRef]
- Muzammal, S.M.; Murugesan, R.K.; Jhanjhi, N.Z.; Humayun, M.; Ibrahim, A.O.; Abdelmaboud, A. A trust-based model for secure routing against RPL attacks in internet of things. Sensors 2022, 22, 7052. [Google Scholar] [CrossRef] [PubMed]
- Bhosale, S.A.; Sonavane, S.S. Wormhole attack detection system for IoT network: A hybrid approach. Wirel. Pers. Commun. 2022, 124, 1081–1108. [Google Scholar] [CrossRef]
- Haque, K.F.; Abdelgawad, A.; Yanambaka, V.P.; Yelamarthi, K. An Energy-Efficient and Reliable RPL for IoT. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; IEEE: Piscateville, NJ, USA, 2020; pp. 1–2. [Google Scholar]
- Ioulianou, P.; Vassilakis, V.; Shahandashti, S. A Trust-Based Intrusion Detection System for RPL Networks: Detecting a Combination of Rank and Blackhole Attacks. J. Cybersecur. Priv. 2022, 2, 124–153. [Google Scholar] [CrossRef]
- ul Hassan, T.; Asim, M.; Baker, T.; Hassan, J.; Tariq, N. CTrust-RPL: A control layer-based trust mechanism for supporting secure routing in routing protocol for low power and lossy networks-based Internet of Things applications. Trans. Emerg. Telecommun. Technol. 2021, 32, e4224. [Google Scholar] [CrossRef]
















| Citation | Year | Domain | Protocol | Summary of Related Work |
|---|---|---|---|---|
| SLF-RPL | WSN; IoT | RPL | Presents a Subjective Logical Framework (SLF)-based Trust Model for Wormhole Attack Detection and Mitigation in WSN–IoT Applications. | |
| [15] | 2021 | IoT | RPL | This study proposes the PCC-RPL (Parental Change Control RPL) methodology that controls the parent change mechanism of the IoT devices using the trust concept. The calculation in the model is performed at the node level of the topology. |
| [16] | 2021 | WSN/IoT | RPL | This study proposes a model for RPL security and addresses its vulnerabilities to both WSN-inherited and RPL-specific attacks. Study have used the machine-learning techniques to develop a secure and improved RPL version for the RPL security. The data classification is done in support vector machine for the analysis. |
| [18] | 2020 | WSN | AODV | This study proposes a model that uses the AODV protocol in its implementation and calculates the trust values of the nodes to detect and prevent a wormhole attack. |
| [21] | 2020 | WSN | LEACH | This paper proposes a method to mitigate the Sybil attack in the LEACH protocol-based WSN network. The study uses a three-tier detection designed for the attack in a severe environment. |
| [23] | 2017 | IoT | RPL | The Secure Trust (SecTrust) trust system is embedded into the RPL routing protocol to protect against Rank and Sybil attacks. The SunTrust-RPL uses a trust-based mechanism to detect and isolate attacks while optimizing network performance. |
| [25] | 2021 | IoT | NA | This study proposes a trust-based framework which computes the trust at the node level of the IoT devices. |
| [26] | 2020 | IoT | RPL | This study proposes the energy-based evaluation of the IoT devices. The evaluation is performed based on the reliability and energy efficiency of the devices. |
| Belief (b) | Disbelief (d) | Uncertainty (u) | Rating |
|---|---|---|---|
| If b > 0.5 | If d < 0.5 | If u < 0.5 | Node is Trusted |
| If b < 0.5 | If d > 0.5 | If u < 0.5 | Node is not Trusted |
| If b < 0.5 | If d < 0.5 | If u > 0.5 | Node is not Verified |
| If b ≤ 0.5 | If d ≤ 0.5 | If u ≤ 0.5 | Node is not Verified Yet |
| Simulation Parameters | Value |
|---|---|
| Simulation Tool | Contiki/Cooja 3.2 |
| Routing Protocol | RPL |
| Coverage Area | 100 m × 100 m |
| Simulation Time | 30, 60 and 90 min |
| Simulation Scenarios | 03 |
| # of Nodes in Topology | 30, 60, 90 |
| Attacker Nodes with Ratio | 3, 6, and 9 |
| Legitimate vs. Malicious Nodes Ratio | 1:10 |
| RX Ratio | 40% to 100% |
| TX Ratio | 100% |
| TX Range 50 m | 60 m |
| Inference Range Initial Node Energy | 65 m 0.1 J |
| Experiments | Deployed Nodes | Attacker Nodes | Controller Nodes | Border Router | Runtime in Minutes |
|---|---|---|---|---|---|
| Ex 1 | 30 | 3 | 1 | 1 | 30 |
| Ex 2 | 60 | 6 | 1 | 2 | 60 |
| Ex 3 | 90 | 9 | 1 | 3 | 90 |
| Key Evaluation Parameters | Simulation Scenario: 30 Nodes | Simulation Scenario: 60 Nodes | Simulation Scenario: 90 Nodes | |||
|---|---|---|---|---|---|---|
| PCC-RPL | SLF-RPL | PCC-RPL | SLF-RPL | PCC-RPL | SLF-RPL | |
| Packet Loss Ratio (%) | 0.41 | 0.39 | 0.46 | 0.43 | 0.49 | 0.46 |
| Energy Consumption (J) | 0.0963 | 0.0728 | 0.0801 | 0.065 | 0.0673 | 0.0504 |
| Attack Detection Rate (Time in Mints) | 12 | 14 | 14 | 17 | 20 | 22 |
| Key Evaluation Parameters | 10 Min | 20 Min | 30 Min | 40 Min | 50 Min | 60 Min | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| PCC-RPL | SLF-RPL | PCC-RPL | SLF-RPL | PCC-RPL | SLF-RPL | PCC-RPL | SLF-RPL | PCC-RPL | SLF-RPL | PCC-RPL | SLF-RPL | |
| Attack Detection Rate (%) | 0.45 | 0.56 | 0.54 | 0.66 | 0.65 | 0.78 | 0.74 | 0.84 | 0.81 | 0.89 | 0.92 | 0.99 |
| Average Residual Energy (J) | 0.73 | 0.77 | 0.62 | 0.65 | 0.48 | 0.52 | 0.42 | 0.45 | 0.35 | 0.40 | 0.31 | 0.35 |
| Packet Loss Ratio (%) | 0.51 | 0.47 | 0.49 | 0.44 | 0.46 | 0.39 | 0.39 | 0.33 | 0.28 | 0.23 | 0.15 | 0.1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Javed, S.; Sajid, A.; Kiren, T.; Khan, I.U.; Dewi, C.; Cauteruccio, F.; Christanto, H.J. A Subjective Logical Framework-Based Trust Model for Wormhole Attack Detection and Mitigation in Low-Power and Lossy (RPL) IoT-Networks. Information 2023, 14, 478. https://doi.org/10.3390/info14090478
Javed S, Sajid A, Kiren T, Khan IU, Dewi C, Cauteruccio F, Christanto HJ. A Subjective Logical Framework-Based Trust Model for Wormhole Attack Detection and Mitigation in Low-Power and Lossy (RPL) IoT-Networks. Information. 2023; 14(9):478. https://doi.org/10.3390/info14090478
Chicago/Turabian StyleJaved, Sarmad, Ahthasham Sajid, Tayybah Kiren, Inam Ullah Khan, Christine Dewi, Francesco Cauteruccio, and Henoch Juli Christanto. 2023. "A Subjective Logical Framework-Based Trust Model for Wormhole Attack Detection and Mitigation in Low-Power and Lossy (RPL) IoT-Networks" Information 14, no. 9: 478. https://doi.org/10.3390/info14090478
APA StyleJaved, S., Sajid, A., Kiren, T., Khan, I. U., Dewi, C., Cauteruccio, F., & Christanto, H. J. (2023). A Subjective Logical Framework-Based Trust Model for Wormhole Attack Detection and Mitigation in Low-Power and Lossy (RPL) IoT-Networks. Information, 14(9), 478. https://doi.org/10.3390/info14090478









