Abstract
Rapid advances in technology and shifting tastes among motorists have reworked the contemporary automobile production sector. Driving is now much safer and more convenient than ever before thanks to a plethora of new technology and apps. Millions of people are hurt every year despite the fact that automobiles are networked and have several sensors and radars for collision avoidance. Each year, many of them are injured in car accidents and need emergency care, and sadly, the fatality rate is growing. Vehicle and pedestrian collisions are still a serious problem, making it imperative to advance methods that prevent them. This paper refines our previous efficient VANET-based pedestrian safety system based on two-way communication between smart cars and the cell phones of vulnerable road users. We implemented the scheme using C and NS3 to simulate different traffic scenarios. Our objective is to measure the additional overhead to protect vulnerable road users. We prove that our proposed scheme adds just a little amount of additional overhead and successfully satisfies the stringent criteria of safety applications.
1. Introduction
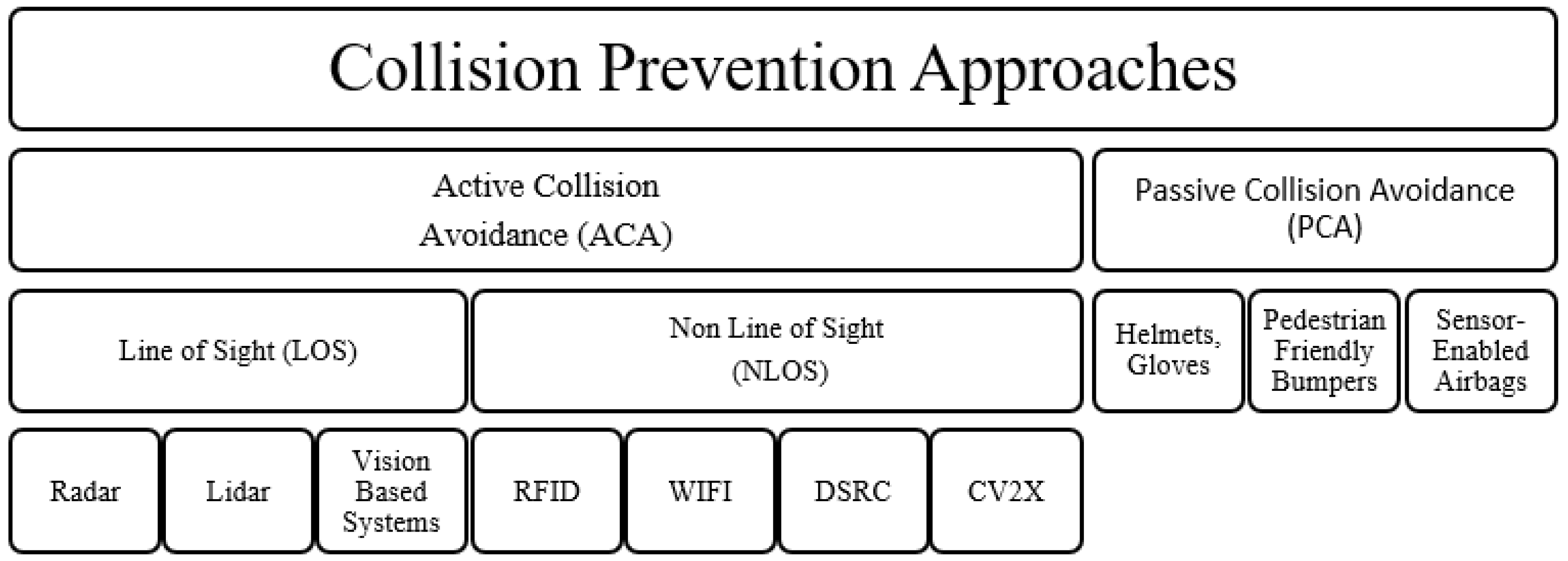
Vehicle-to-everything communication might reduce crash rates, pollution, and poor road management [1]. Speed-related crashes account for four times as many homicide fatalities annually in certain countries [2]. Road accidents are mostly caused by human negligence while bolstering preventative efforts can lessen their impact [3]. According to [4], the mortality per capita rate in the USA increased by 6% between 2019 and 2020. Vulnerable road users (VRUs), defined in [5] as walkers, cyclists, and motor wheels with high accident involvement risk, are now a component of collision avoidance research. This is a positive shift since vulnerable road users (VRUs) accounted for over 50% of the 1.35 million fatalities on the roads in 2018 [6]. Collision damage is decreased via research on passive collision avoidance (PCA). Contrarily, autonomous collision avoidance (ACA) helps avoid crashes [7]. Bike lanes [8,9], bumpers [10] that are friendly to pedestrians, LED-equipped gloves [11] and helmets [12], and sensor-enabled airbag systems [13] are a few PCA techniques. Since these safeguards have not been been tested, it is unclear how effective they will be [14]. The two main groups of autonomous collision avoidance techniques are those that presume visibility or a line of sight (LOS), such as radar, lidar, and vision-based systems [7], and those designed for non-line of sight (NLOS) circumstances, which are the subject of this study. Vehicle-to-vulnerable road user (V2X) communication via RFID, DSRC, WIFI, or cellular V2X are examples of NLOS ACA techniques. The strategies for avoiding collisions are listed in Figure 1.
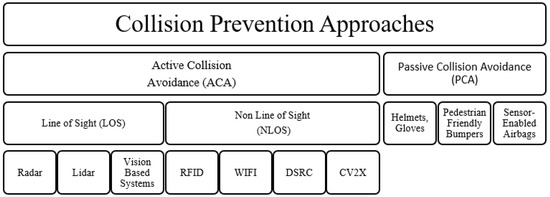
Figure 1.
Collision prevention approach classification.
Weather and lighting have little impact on NLOS techniques [15]. They depend on OBU-VRU communication [16]. This is crucial since the majority of fatal traffic accidents are caused by poor visibility and slow response times [17]. Connectivity is made possible by these policies [18]. This makes use of these users’ critical perception and information-sharing abilities with other road users [19]. In NLOS, several system design variables might categorize VRU safety systems, which are sometimes referred to as vehicle-to-pedestrian (V2P) systems. The role of the VRU device in the system is one significant distinction. Applications for awareness allow the driver total control and limit the VRU device to a “Hello” signal to announce its presence. The VRU device may carry out algorithmic computations and trajectory predictions in challenging collision avoidance applications [20]. Due to the startlingly high incidence of deadly VRU road accidents, research into V2P system design has expanded. These attempts make use of unique parameters with unique features and limitations, and there is still more work to be carried out in order to address problems with V2P system design.
The contributions of this paper are as follows.
- We build up on our previous V2P lightweight scheme [21] by enhancing an efficient VANET-based pedestrian protection scheme based on vehicle-to-pedestrian (V2P) communication between smart vehicles and vulnerable road users’ smartphones. Consequently, our scheme contributes to a decrease in road collisions and casualties that are likely to occur, and roads are anticipated to become safer as a result.
- We show the efficiency of our scheme through simulations and implementations to meet the real-time constraints of V2P communications in different traffic scenarios. We measured critical network parameters in terms of average throughput, processing delay, and network load.
- We compare the different technologies used in V2P system design in terms of range, latency, and ease of deployment in our related work and study the factors that influence V2P system design specifications, like VRU types, VRU roles, VRU devices, communication technologies, notified parties, and purpose.
The remainder of this paper is organized as follows. Section 2 presents our efficient VANET-based pedestrian protection scheme in detail. In Section 3, we explain our NS3 simulation, metrics, and the results for the proposed scheme. Section 4 offers background information on V2P system design, including categorizations by different design parameters, a comparison of different technologies used, and an overview of previous endeavors. In Section 5, we discuss the limitations of our work. Finally, Section 6 concludes our paper with a general discussion of results, and it presents future directions in the domain of V2P schemes.
2. Proposed Vulnerable Road Users Protection Scheme
In this section, we propose our VANET-based pedestrian protection scheme followed by the NS3 simulation. Our simulation assesses various network parameters such as throughput, processing delay, and network load.
Scheme Overview and Network Model
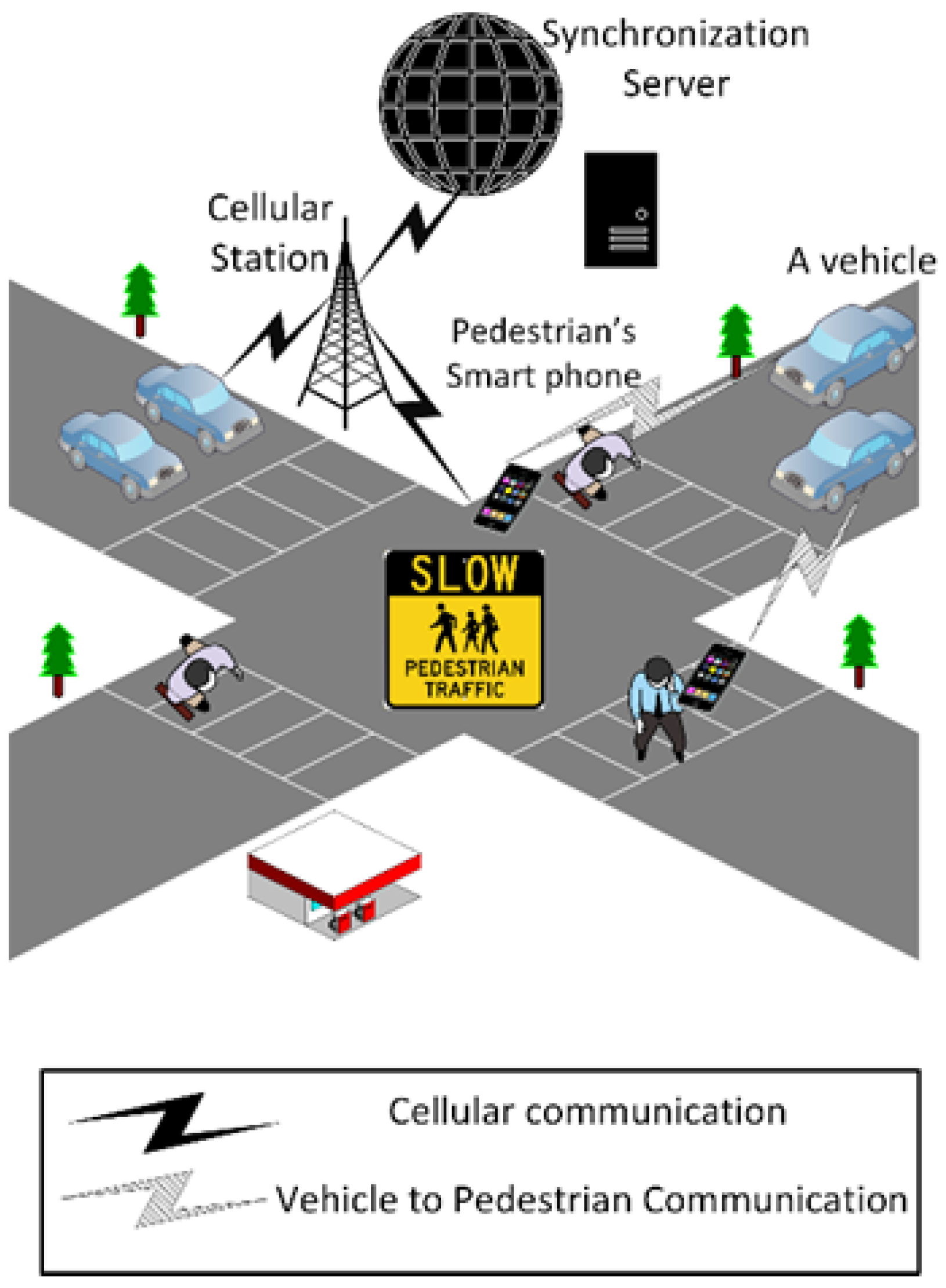
Our scheme consists of two phases, where vehicles first estimate the degree of threat by measuring the signal strength of nearby VRU smartphones as depicted in Figure 2. A lightweight collision detection algorithm (CDA) is then executed to confirm or refute a collision.
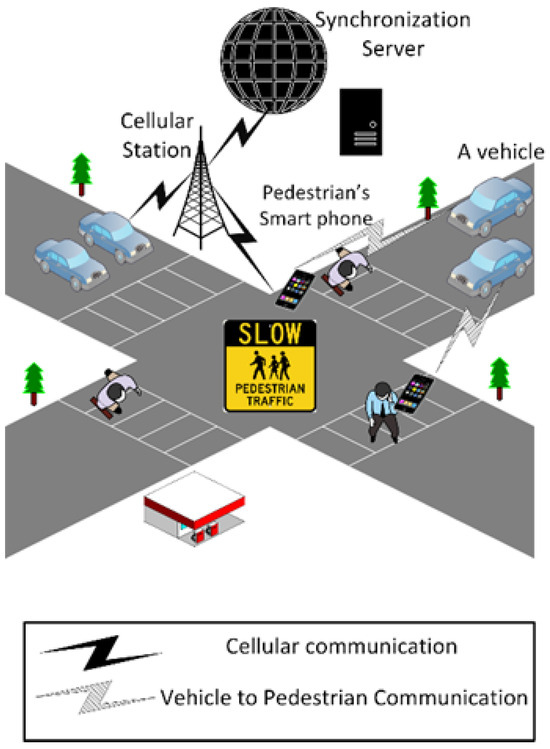
Figure 2.
Network model.
Our V2P network model consists of vehicles, VRU smartphones, and a synchronization server. The designated app on the VRU smartphone is responsible for creating WIFI hotspots to connect with nearby vehicles as well as running the CDA. The server is an additional asset that could or could not exist. Depending on the situation, it is advantageous in terms of its large storage and computation capabilities, but our system could run without it. Finally, vehicles move with different trajectories and speeds and are equipped with OBUs that communicate via cellular or DSRC communications.
In the first phase of our scheme, a VRU smartphone creates a WIFI hotspot, and nearby vehicles search for available hotspots and attempt to connect to them using their OBUs. Once a pedestrian-vehicle connection is established, the signal strength is measured to estimate the distance between the two parties. If the signal strength exceeds a certain threshold, suggesting that the distance between them is dangerously small, a lightweight CDA is executed to determine whether or not there is a real threat of collision. The vehicle and the pedestrian could connect directly via WIFI/DSRC or communicate via cellular network through the synchronization server, which increases system latency.
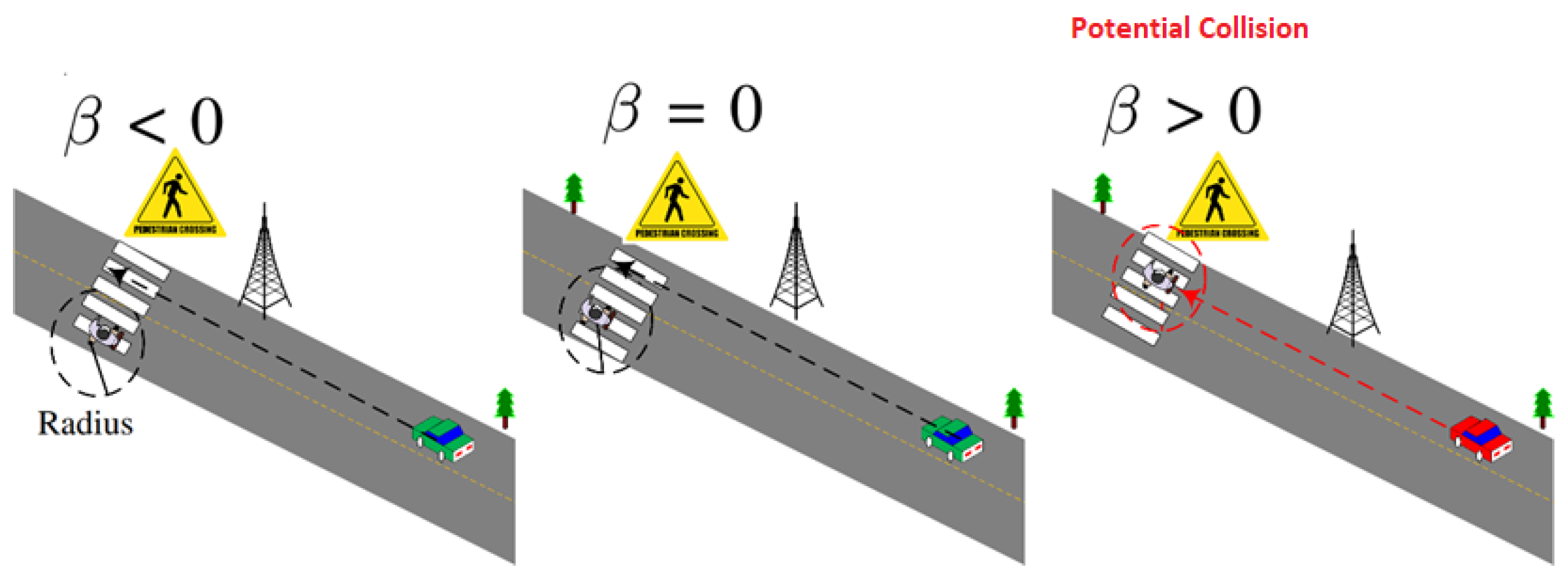
The second phase of our system is executed in instances where signal strength exceeds a certain threshold and involves the implementation of a CDA to detect potential collisions. The smartphone app at the VRU end requires the two most recent GPS locations of the incoming vehicle and uses them to construct a line representing its path. The VRU is located at the center of a circle of configurable radius; then, a circle-line intersection is calculated using analytic geometry, as shown in the efficient detection Algorithm 1.
The potential scenarios of collision detection after executing the detection algorithm are shown in Figure 3.
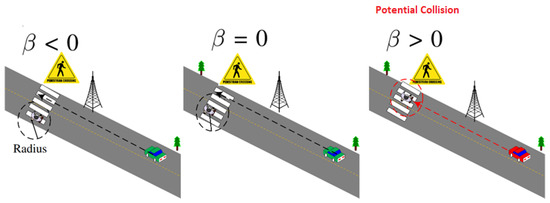
Figure 3.
Three different scenarios of pedestrian vehicle collision detection.
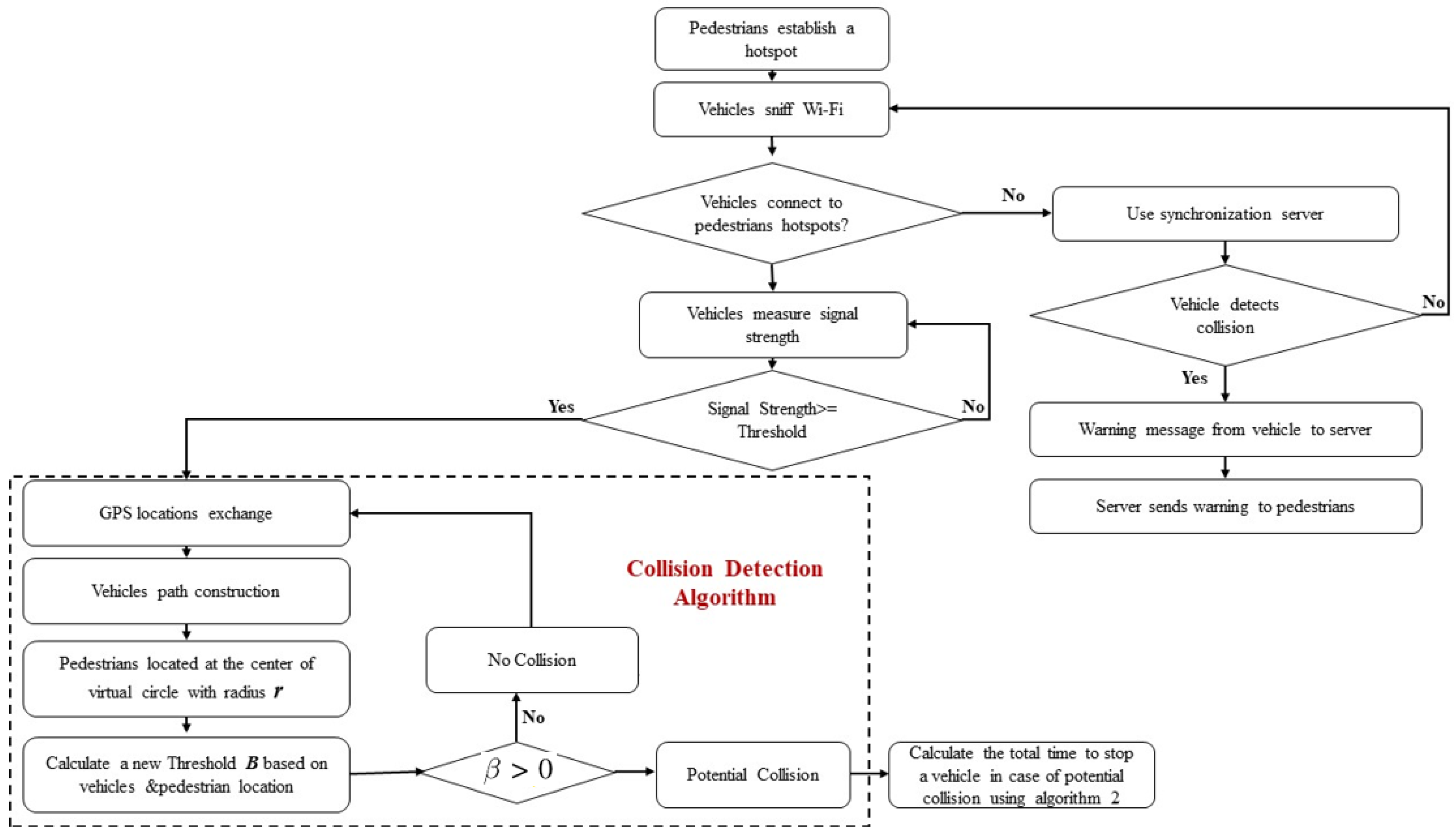
Our scheme is summarized in the flowchart depicted in Figure 4.
| Algorithm 1 Efficient Collision Detection Algorithm (CDA) |
|
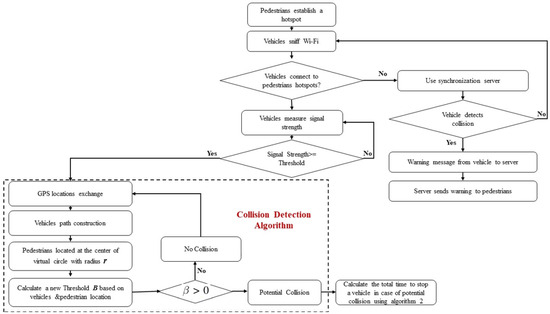
Figure 4.
Our proposed collision detection methodology flowchart.
3. Simulation
In this section, we present the experimental setup, simulation parameters, and simulation results. We also discuss the simulation results and their implications.
3.1. Simulation Setup
We simulated the proposed scheme using NS-3 simulator [22] to assess the network’s performance. OpenStreetMap (OSM) was used to generate the topography, which resembles a square of size 600 × 600 m. The vehicular movement traces are generated randomly using SUMO [23]. We used IEEE 802.11p as the underlying protocol that provides communication among vehicles. We considered three different traffic scenarios: light traffic, average traffic, and heavy traffic. The vehicle’s arrival rate varies according to the desired number of vehicles in different scenarios. Vehicles are randomly inserted into the simulation at a uniform rate, which can be modeled as a binomial distribution of inserted vehicles for each edge. In large networks, this approximates a Poisson distribution, which adequately reflects the vehicle’s arrival in real-world scenarios. The pedestrians follow a random mobility model with an average speed of one meter per second. The pedestrians’ mobility is equivalent to people running and those who are scattered along the map. The simulation parameters are shown in detail in Table 1.

Table 1.
Simulation parameters.
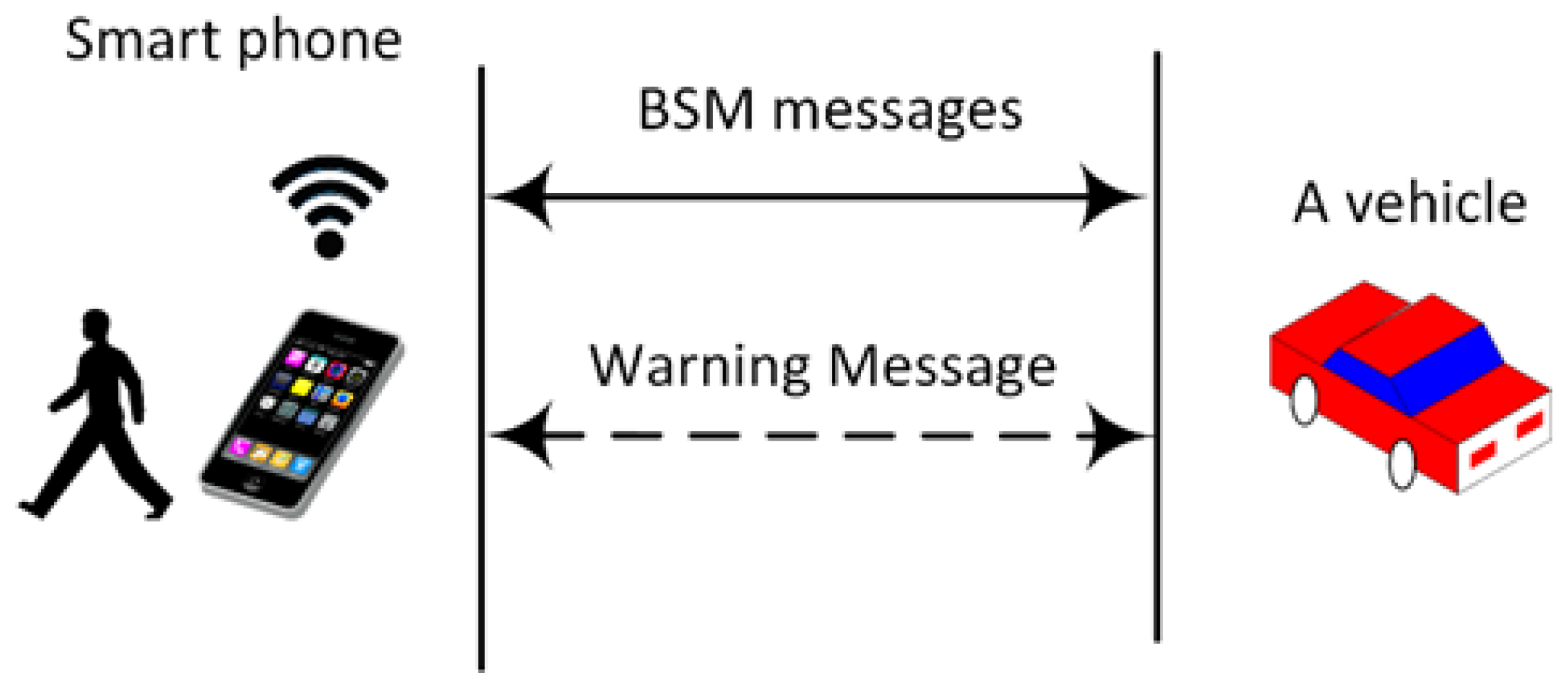
The simulation focuses on comparing the network overhead of our proposed scheme with a baseline vehicle-to-vehicle scheme. Specifically, we implemented two scenarios. The first scenario “Without Pedestrian Protection” comprises pure vehicle-to-vehicle communication, where vehicles exchange BSM messages without any pedestrian involvement in such communication. In the second scenario “With Pedestrian Protection”, we implemented vehicle-to-vehicle aside from vehicle-to-pedestrian, where pedestrians communicate with vehicles and run our scheme to detect a potential collision. When a node detects a potential collision with another node, it sends a warning message to this node, as shown in Figure 5. We used C++ on top of NS-3 to implement both schemes. Our study included three traffic scenarios:
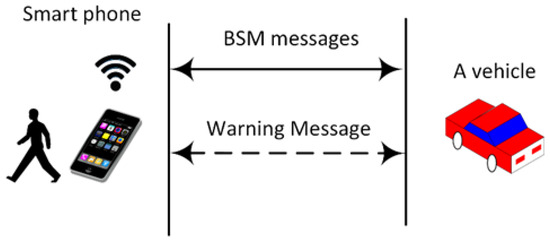
Figure 5.
Exchanged messages in our simulation.
- Low traffic scenario: 50 vehicles/10 pedestrians;
- Average traffic scenario: 100 vehicles/30 pedestrians;
- High traffic scenario: 145 vehicles/60 pedestrians.
3.2. Simulation Metrics
We considered the following performance metrics to assess the network performance in both schemes:
- Average throughput: The average amount of data in Kbps received by vehicles/pedestrians per second. This is an important metric for measuring the required bandwidth and assessing the feasibility of the proposed scheme.
- Processing delay: This is the average time it takes to run our proposed scheme and send a reply back to the sender. For example, when a vehicle receives a BSM message from a pedestrian, it runs our scheme and sends a warning message if it detects a collision. The processing delay is the time between the reception of the BSM message and the transmission of the warning message.
- Network load: This is the total number of packets sent by vehicles and pedestrians within the simulation time.
3.3. Simulation Results
In this section, we present the simulation results for our proposed V2P system using the three evaluation network parameters: Average throughput, processing delay, and network load.
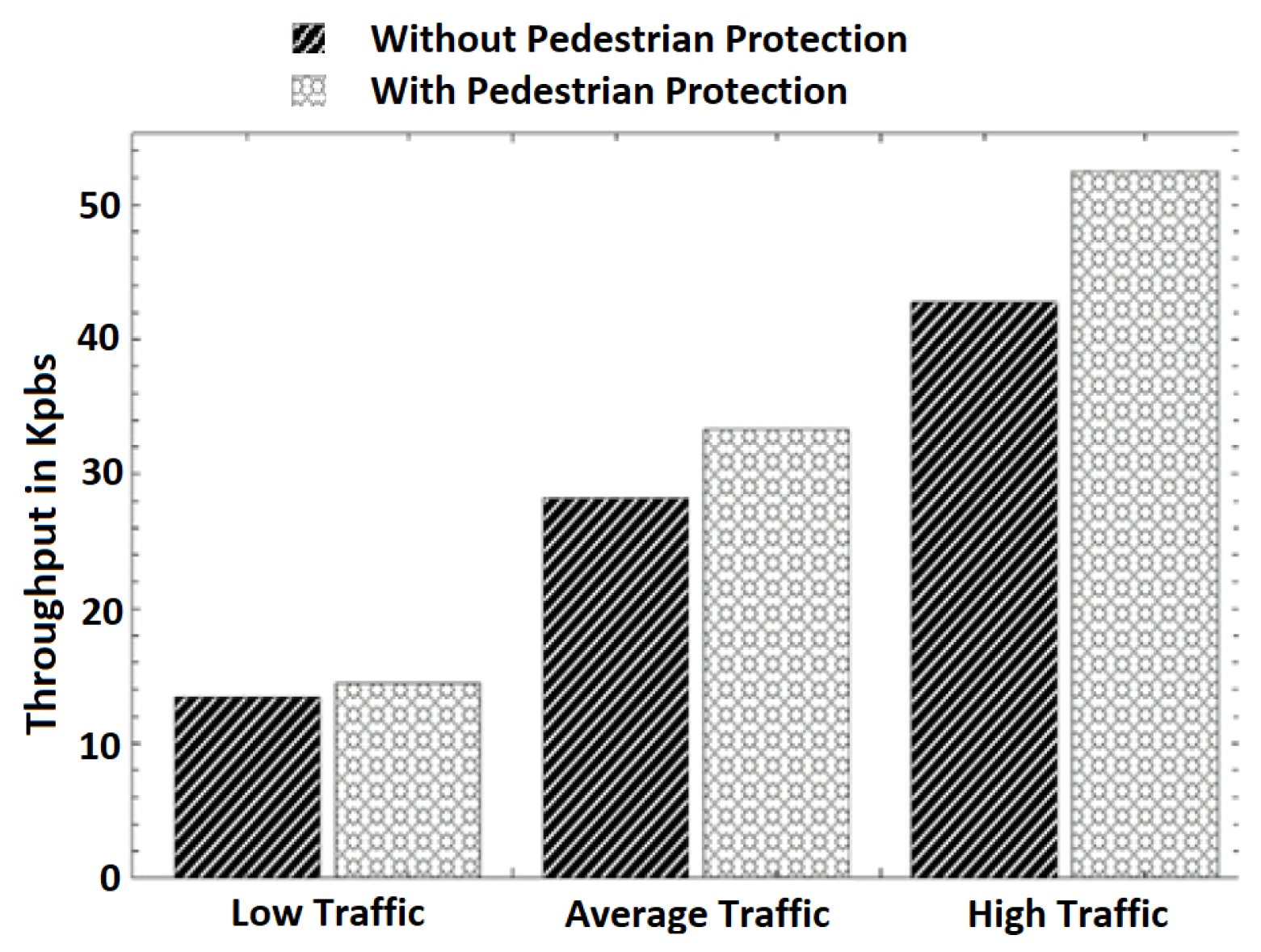
- Average throughput: The average throughput at different traffic scenarios is presented in Figure 6 It can be observed that the throughput increases with an increase in the number of vehicles and pedestrians in both schemes. In different traffic scenarios, the throughput’s increase is expected because the number of transmissions increases as the number of vehicles and pedestrians grows. We observed that our scheme introduces slightly more throughput in all traffic scenarios than the pure V2V scheme. This is because pedestrians’ engagement in communication with vehicles introduces more transmission and the reception of data. However, the increase in the throughput introduced by our scheme is minimal. For example, it can be observed that the throughputs of the pure V2V scheme and the scheme with pedestrian protection in the average traffic scenario are 28.21 and 33.28 Kbps, respectively. This is a 15% throughput increase introduced by our scheme for pedestrian safety. In addition, the throughput increase is only 8% in the low-traffic scenario.
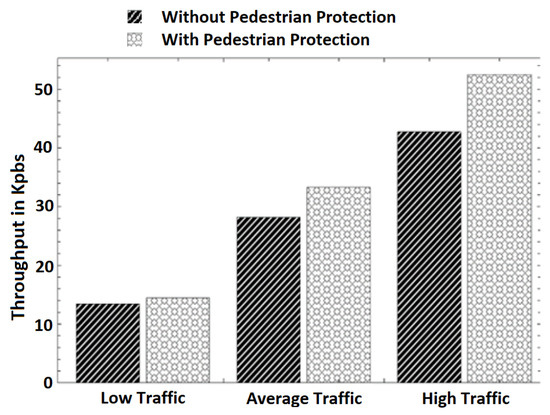 Figure 6. Average throughput in different traffic scenarios.
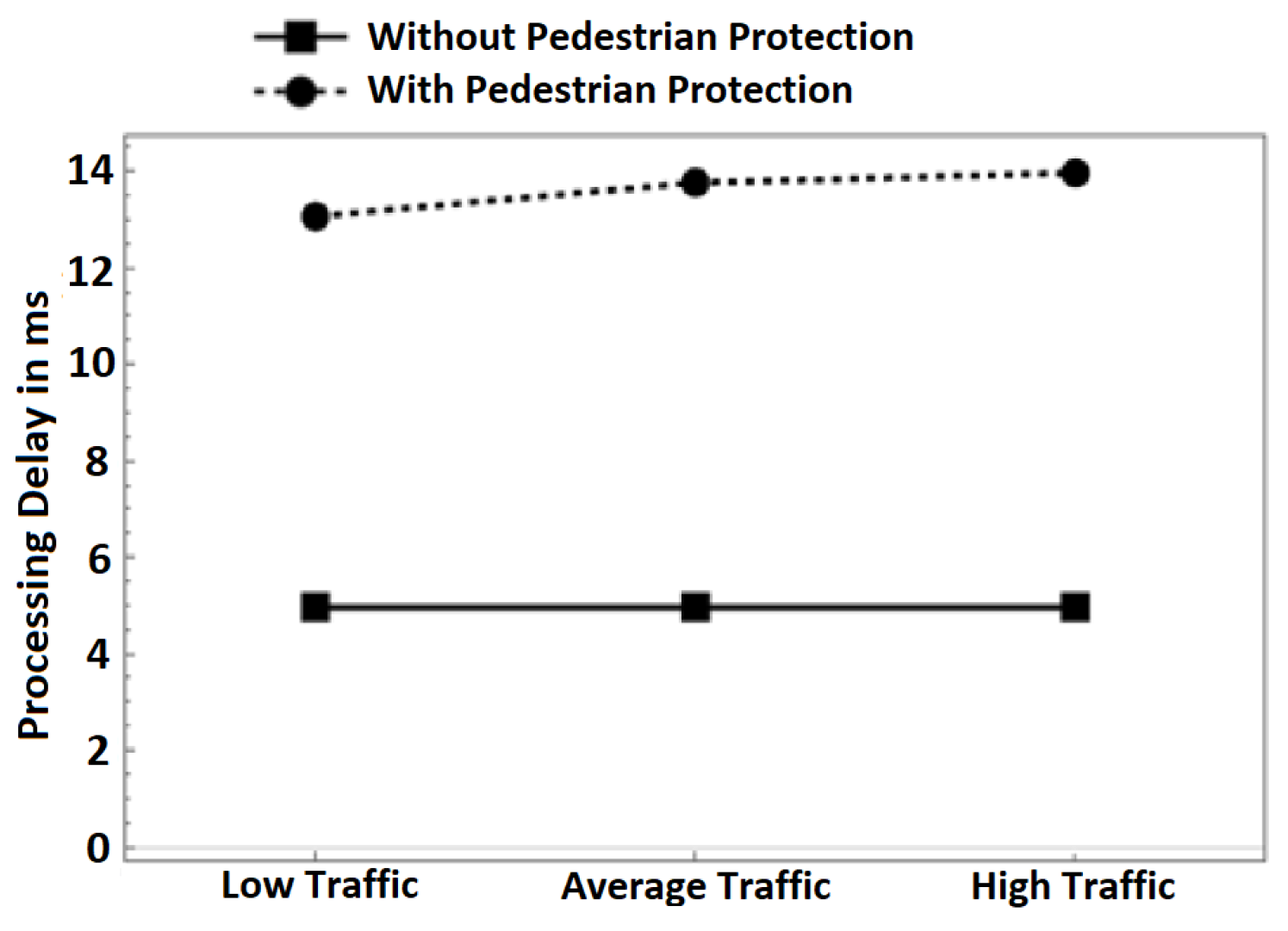
Figure 6. Average throughput in different traffic scenarios. - Processing delay: Figure 7 depicts the average processing delay. We differentiate between the delay in both schemes: with pedestrian protection and without pedestrian protection. In the pedestrian protection scheme, we run our scheme after the verification process of BSM messages. In the other scheme, we only run the verification process of BSM messages. We set the verification time of BSM messages to be 4.97 ms according to [24,25]. As observed in the following Figure 7, the delay introduced by both schemes is almost constant in all traffic scenarios, even with increasing the number of nodes in the high-traffic scenario. We observe that in our scheme, the processing delay times are 13.07, 13.77, and 13.97 ms in all traffic scenarios. Without pedestrian protection, the delay times are 4.97 ms for the same traffic scenarios. The introduced delay by our scheme is only 8 ms, which is a minimal cost and proves that our scheme is lightweight and fits well in VANET safety applications. More importantly, the delay is far below 100 ms even in dense traffic scenarios, which meets the minimum latency requirements of VANET safety applications according to [26,27].
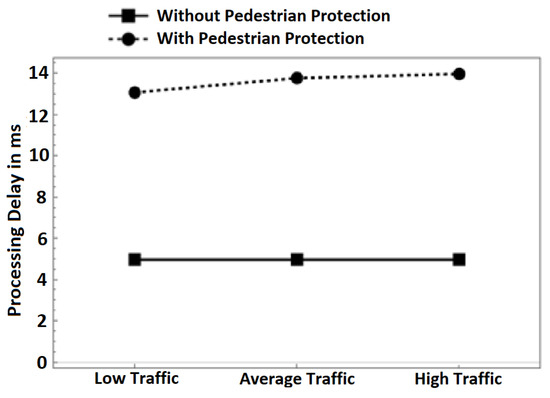 Figure 7. Processing delay in different traffic scenarios.
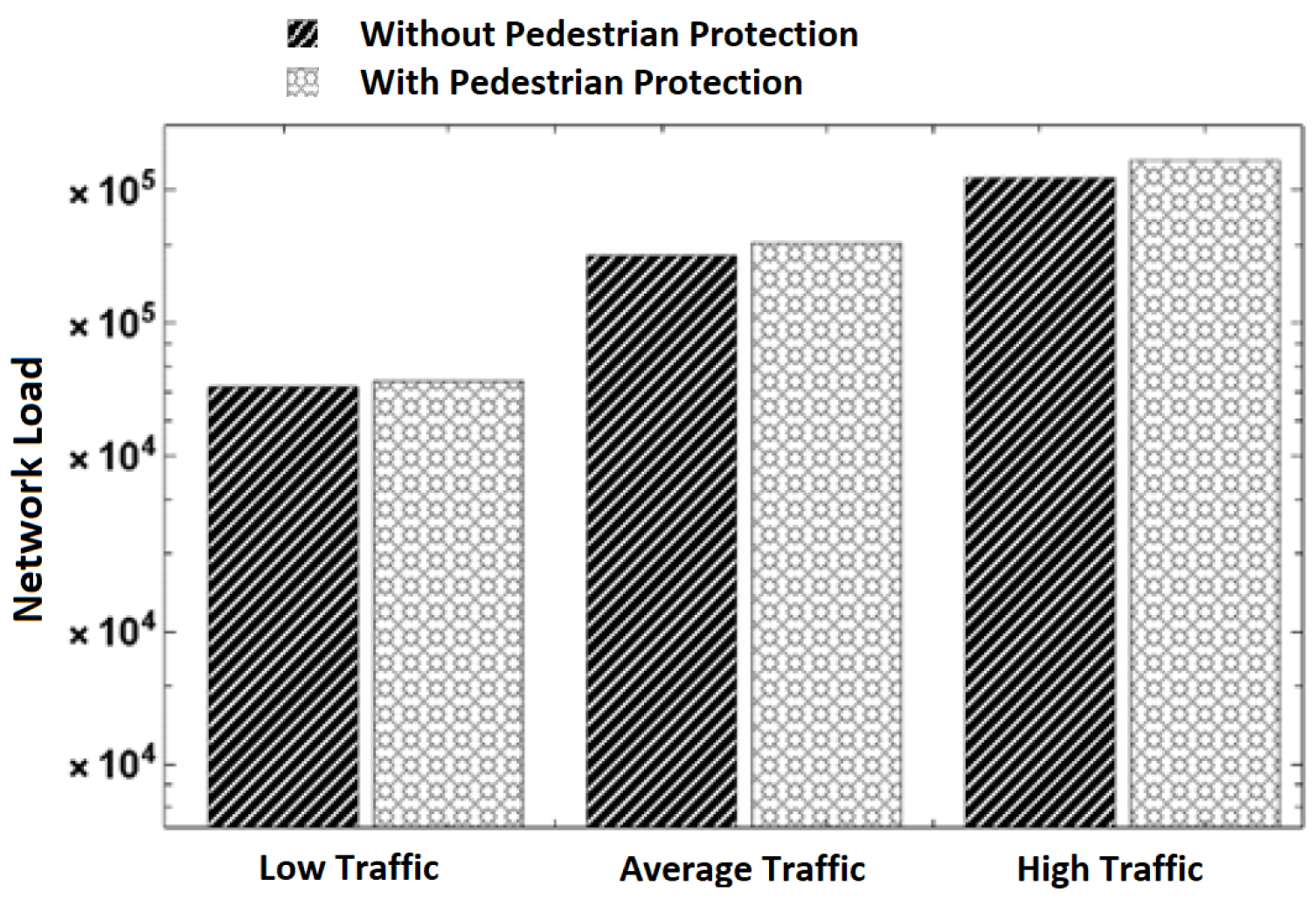
Figure 7. Processing delay in different traffic scenarios. - Network load: The number of packets transmitted throughout the simulation time at different traffic scenarios is shown in Figure 8. It can be observed that the number of packets increases with an increase in the number of vehicles and pedestrians involved in communication. This is normal behavior because of the increase in packet transmission. When comparing the pure V2V scheme with our scheme, we can observe that our scheme has more packets transmitted. We attribute the increase in transmitted packets to the pedestrians’ communication with vehicles. The increase in network load due to the use of our scheme is negligible. For example, our scheme transmits 73,967 packets while the pure V2V scheme transmits 71,712 packets in the low-traffic scenario. This is an increase in the transmission of 2255 packets only (3%), which is a small bandwidth cost for protecting pedestrians.
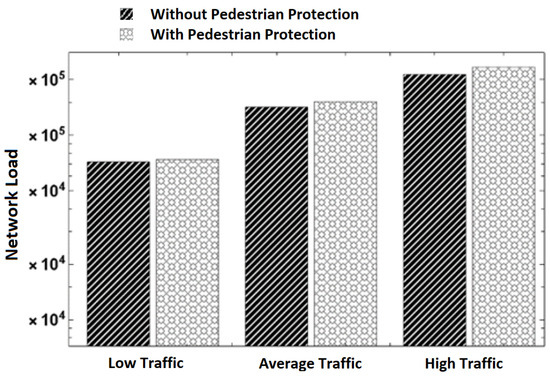 Figure 8. Network load in different traffic scenarios.
Figure 8. Network load in different traffic scenarios.
4. Related Work
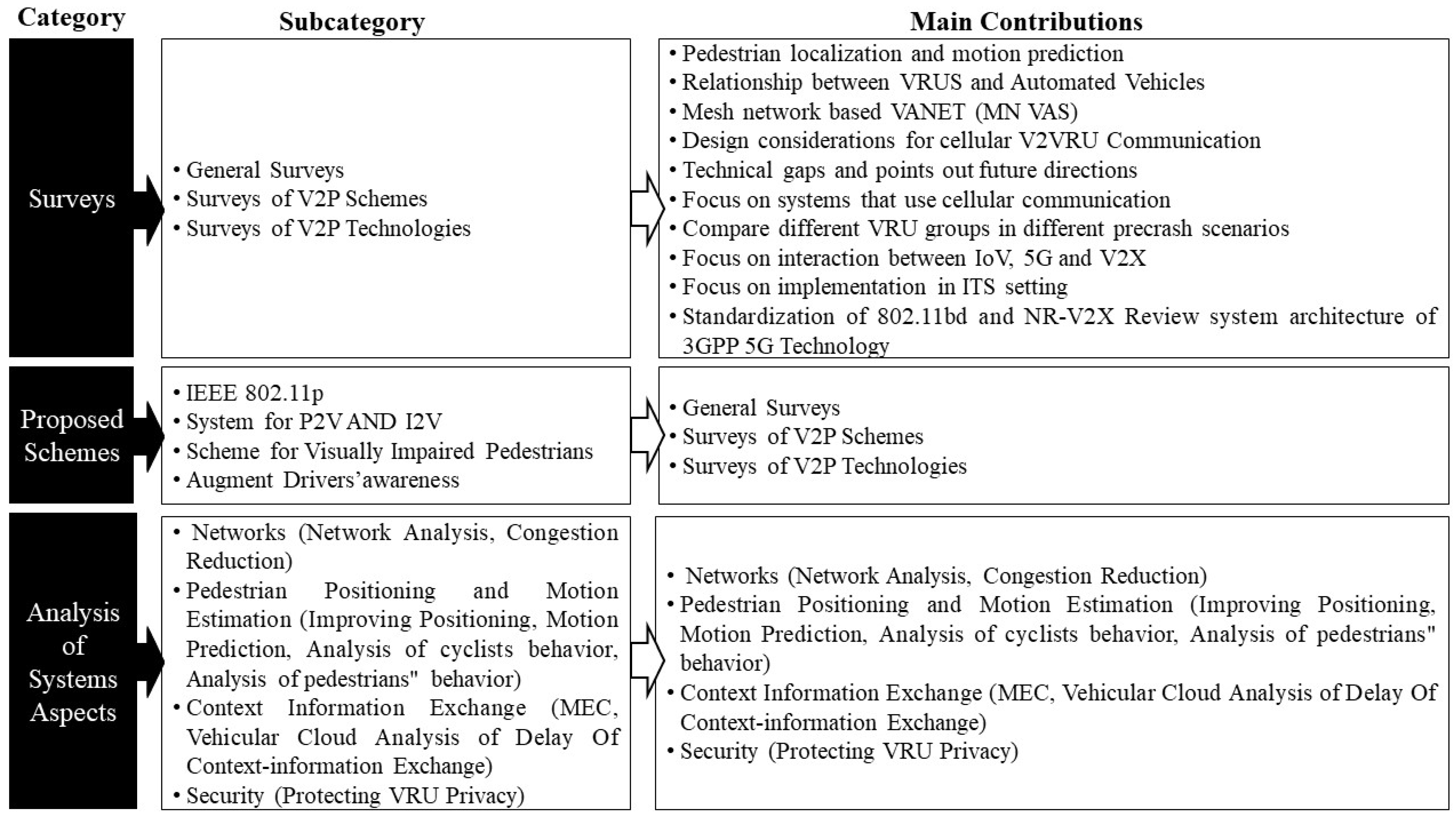
Network congestion, context information sharing, pedestrian placement, and energy efficiency are just some of the issues that might arise while designing a V2P system. This section will detail recent initiatives, which have included both theoretical inquiries and actual answers to these issues. Four methods were presented in [28] to eliminate superfluous warnings to VRUs, helping alleviate network congestion. To facilitate V2P communication in emergency situations, the authors of [29] suggested a dedicated channel paradigm. To further anticipate deployment issues, Ref. [30] provided a technique to estimate CITS performance in dynamic vehicular networks. The success of the algorithms powering the CITS application may be determined using this technique by analyzing actual or predicted traffic volumes. Finally, in [31], the authors tried to put a number on VRU awareness by analyzing the relationship between the sampling frequency of VRU warnings and the tradeoff between VRU safety and network congestion. A novel measure, VRU awareness probability (VAP), was created to quantify the likelihood of detection by neighboring cars based on the flow of signals between operational VRUs. The authors of [32] employed automobiles as anchors in addition to satellites to solve the issue of pedestrian placement, thereby overcoming GPS-related inconsistencies. By monitoring the evolution of CSI over time, they were also able to devise a technique for estimating the propagation angle of a signal. Their solution only needs one antenna on the VRU device (instead of the standard eight) and is more precise. The Kalman filter was used to mitigate GPS errors by the authors of [33]. To examine bikers’ behavior without placing real-life participants in danger, researchers in [16] simulated a VANET using data collected from a virtual riding environment. Both Refs. [34,35] used machine learning to analyze pedestrian activity. In the former, decision tree classifiers were used to differentiate between friendly and hostile pedestrians while connected to a server, whereas four conventional classifying vectors were used when no server was available. The former addressed movement prediction as a classification task, whereas the latter used two distinct classification paradigms: the linear kernel support vector machine and the XG Boost classifier. While the sharing of contextual information is crucial for V2P systems, delays in carrying this out may have a major impact on the effectiveness of collision detection algorithms (CDAs), as shown in [36]. The scientists looked into the link between the two and created a curb detection module to boost the precision of collision detection just as the pedestrian steps off the curb. In [37,38,39], multi-access edge computing (MEC) was employed to increase efficiency by computational offloading to cloud servers, weighing the tradeoff between latency and energy usage in context information transmission. These efforts make it possible to utilize a mobile device as an OBU without draining its power supply too quickly.
Finally, although VRU privacy and data security are essential issues, they are beyond the scope of this article. We do, however, briefly describe one attempt from [40], in which the authors use machine learning classifiers to provide a framework for the safe processing of massive amounts of data. Figure 9 summarizes the research directions and trends for V2P design.
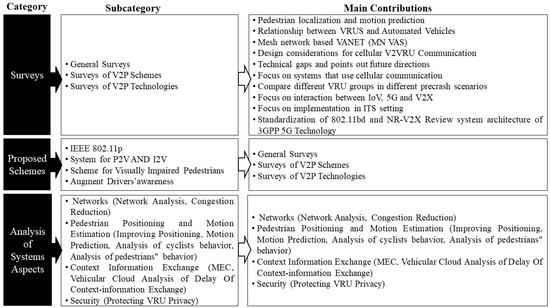
Figure 9.
Research directions and trends for V2P design.
Context information exchange, precise pedestrian positioning, network congestion, and energy efficiency are challenges in designing V2P systems [41]. In Table 2, we describe the different challenges in V2P design.

Table 2.
Challenges to V2P system design.
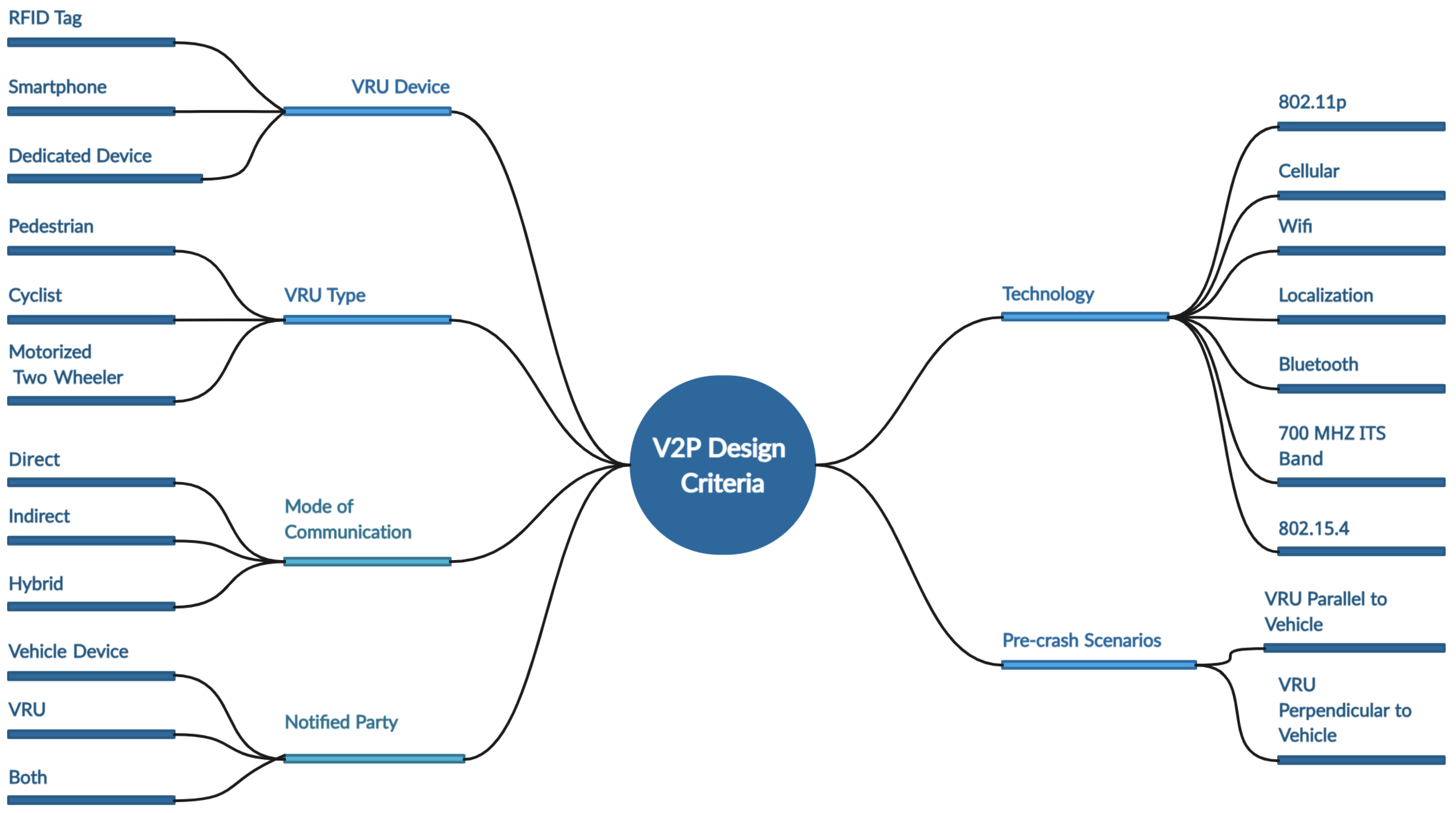
V2P systems can be classified according to several design criteria, contrasting the technologies utilized in V2P systems and design. ACA NLOS techniques, referred to as V2P systems, may be categorized in a variety of ways based on the parameters used. The different design parameters and associated classifications are illustrated in Figure 10.
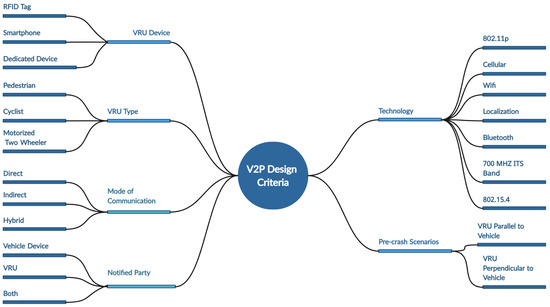
Figure 10.
Classification of V2P system design approaches.
These categorizations affect V2P system design. The VRU movement patterns and reaction times differ from autos, pedestrians, cyclists, and powered two-wheelers [42]. Children walk haphazardly, whereas older and handicapped people move slowly [43]. Variations affect the VRU’s role and device selection. Kids prefer tag-based unilateral communication since they cannot be VRUs. Various efforts have been made to develop V2P communication, with the goal of overcoming possible problems by adjusting the interaction of various aspects. Figure 11 classifies and provides an overview of the various V2P design initiatives based on the three design criteria: VRU type, the technology employed, and the VRU device.
Figure 11.
Design parameters in current V2P systems.
Visualization is a key aspect of V2P systems, helping convey information in an intuitive and effective manner. Visualization points are used to support safety in V2P systems and include pedestrian presence visualization, where icons are used on the vehicle’s display to indicate the presence of pedestrians in the vicinity. Crosswalk status indicators employ dynamic visual cues to indicate the status of a crosswalk (e.g., flashing lights, changing colors) to notify drivers of pedestrians who are actively crossing. Distance and speed visualization displays real-time information about the distance and speed of pedestrians relative to the vehicle to assist drivers in making informed decisions. Intersection safety visualization uses augmented reality or head-up displays to highlight potential collision points at intersections and provide guidance on safe navigation. Smart crosswalks integrate embedded LED lights that dynamically change based on the presence of pedestrians, creating a visual warning for drivers. Effective visualization in V2P systems can significantly contribute to safer road interactions by enhancing situational awareness for both drivers and pedestrians. It is essential to design these visualizations with clarity and simplicity to ensure the quick and accurate interpretation of information.
In [44], the authors discuss the communication between automated vehicles (AVs) and human road users through external human–machine interfaces (eHMIs), like the displays on the AV’s surface. The study examines the size requirements for displayed text or symbols to ensure legibility, considering factors such as road traffic dynamics and human reaction time. The results suggest that, for the maximum detection range among human road users, AVs should display symbols rather than text, and color-coded symbols can enhance message comprehension without affecting detection range. In [45], The paper explores the challenges of ensuring pedestrian safety, especially at crosswalks, in unique environments where traditional traffic infrastructure is absent, such as “naked streets.” The research introduces an innovative smart pole interaction unit (SPIU) with an external human-machine interface (eHMI) in autonomous vehicles (AVs). Using virtual reality (VR) technology, the study demonstrates that integrating an SPIU with an eHMI in vehicles significantly improves secure decision making for pedestrian passing and stops in shared spaces, leading to a substantial 21% reduction in response time and highlighting the positive impact on interaction dynamics in both unidirectional and bidirectional scenarios. Ennia et al. [46] focus on cyclist safety in traffic, utilizing a visual tracking tool to identify critical points in infrastructure with high distraction levels. By replicating the scenario in a bicycle simulator and comparing it to a real test conducted in Stockholm, the research objectively analyzes cycling behavior, finding the crossing as a significant critical aspect. The results, based on both objective and subjective evaluations, highlight the importance of attention and workload perception, emphasizing the potential differences in user experience between simulated and real-world cycling situations.
Diego et al. [35] propose a method for the early detection of pedestrian movement transitions using smart devices, enabling advanced protection for vulnerable road users (VRUs) by facilitating communication with intelligent vehicles and infrastructure. The study utilizes human activity recognition to categorize pedestrians into four states (waiting, starting, moving, and stopping) and employs machine learning classifiers, including a support-vector machine and XGBoost, for movement transition detection. Empirical studies based on real-world data from 11 test subjects and 79 scenes demonstrate the effectiveness of the proposed method, achieving a robust and early detection of movement transitions with an F1-score of 85%.
5. Limitations
The study primarily focuses on a set of predefined pedestrian behaviors, such as typical walking patterns. However, the real-world variability in pedestrian actions, sudden changes in direction, and interactions with the environment may not be fully captured. A broader exploration of diverse pedestrian behaviors, including unpredictable movements, is essential for a more comprehensive assessment. The proposed scheme relies on the assumption that pedestrians actively engage with their smartphones during road activities. This assumption may not align with real-world scenarios, where distractions or varying levels of smartphone usage might impact the effectiveness of V2P communication. The scheme may not thoroughly explore potential privacy concerns associated with collecting and communicating data from pedestrians’ smartphones. Balancing the need for safety with individual privacy rights is a delicate aspect that should be carefully considered in the deployment of V2P communication systems.
6. Conclusions and Future Work
Traffic accidents are a consistent tragic reality of the contemporary world. While numerous endeavors have strived to mitigate the casualties of such accidents, they still remain a significant contributor to global fatalities every year. There is a growing interest in the involvement of pedestrians as subjects in the research field of collision prevention, using vehicle-to-pedestrian (V2P) communication. In this paper, we proposed a pedestrian protection scheme based on communication between vulnerable road users’ smartphones and smart vehicles. We used NS-3 to simulate different traffic scenarios to confirm the efficiency of our scheme. We measured essential network parameters such as average throughput, processing delay, and network load. Our simulation results indicate that the overhead introduced by our scheme is minimal and acceptable. These results confirm that the proposed scheme scales well in dense traffic scenarios and will certainly contribute to the safety of vulnerable road users. Future research efforts that can be based on our work include the following:
- The study of the effect of including a synchronization server in our V2P system to measure the expected delay;
- We will study different behaviors of pedestrians to consider the differences in their patterns of motion (like children, elderly pedestrians, and disabled pedestrians);
- We will include different types of vulnerable road users other than pedestrians, like cyclists and motorized two-wheelers in our study.
By undertaking these future research efforts, we anticipate not only refining our proposed scheme but also contributing valuable insights to the broader domain of collision prevention and V2P communication. Through continuous exploration and collaboration, we strive to make meaningful strides toward enhancing the safety of vulnerable road users in diverse traffic scenarios.
Author Contributions
Writing—original draft: K.R. and M.A.A.; Methodology: K.R.; Visualization: K.R. and M.A.A.; Resources: K.R.; Software: K.R.; Validation: K.R. and R.S.; Writing—review & editing: K.R., R.S. and M.A.A.; Formal analysis: K.R.; Funding acquisition: R.S.; Project Administration: M.A.A.; Supervision: M.A.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Garcia-Roger, D.; Gonzalez, E.E.; Martín-Sacristán, D.; Monserrat, J.F. V2X support in 3GPP specifications: From 4G to 5G and beyond. IEEE Access 2020, 8, 190946–190963. [Google Scholar] [CrossRef]
- Job, R.S.; Brodie, C. Road safety evidence review: Understanding the role of speeding and speed in serious crash trauma: A case study of New Zealand. J. Road Saf. 2022, 33, 5–25. [Google Scholar] [CrossRef]
- Lakim, L.L.; Ghani, N.A. A review of road traffic hazard and risk analysis assessment. Environment 2022, 7, 297–309. [Google Scholar] [CrossRef]
- Fatality Facts 2020 Yearly Snapshot. 2020. Available online: https://www.iihs.org/topics/fatality-statistics/detail/yearly-snapshot (accessed on 8 December 2023).
- Malone, K.; Silla, A.; Johansson, C.; Bell, D. Safety, mobility and comfort assessment methodologies of intelligent transport systems for vulnerable road users. Eur. Transp. Res. Rev. 2017, 9, 21. [Google Scholar] [CrossRef]
- World Health Organization. Road Traffic Injuries. 2018. Available online: https://www.who.int/news-room/fact-sheets/detail/road-traffic-injuries (accessed on 8 December 2023).
- Gandhi, T.; Trivedi, M.M. Pedestrian protection systems: Issues, survey, and challenges. IEEE Trans. Intell. Transp. Syst. 2007, 8, 413–430. [Google Scholar] [CrossRef]
- Reynolds, C.C.; Harris, M.A.; Teschke, K.; Cripton, P.A.; Winters, M. The impact of transportation infrastructure on bicycling injuries and crashes: A review of the literature. Environ. Health 2009, 8, 47. [Google Scholar] [CrossRef] [PubMed]
- Vanparijs, J.; Panis, L.I.; Meeusen, R.; De Geus, B. Exposure measurement in bicycle safety analysis: A review of the literature. Accid Anal. Prev. 2015, 84, 9–19. [Google Scholar] [CrossRef] [PubMed]
- Teng, T.; Ngo, V.L.; Nguyen, H. Design of pedestrian friendly vehicle bumper. J. Mech. Sci. Technol. 2010, 24, 2067–2073. [Google Scholar] [CrossRef]
- Lumos. Ride the Brightest with a LUMOS Helmet, 2020. Available online: https://ridelumos.com/ (accessed on 8 December 2023).
- Zackees. Zackees Turn Signal Gloves 2.0. 2020. Available online: https://www.bicycling.com/bikes-gear/g34706221/10-cutting-edge-gifts-for-tech-loving-cyclists-1605659452/ (accessed on 14 August 2023).
- Hovding. The World’s Safest Bicycle Helmet Isnt a Helmet. 2020. Available online: https://hovding.com/ (accessed on 8 December 2023).
- Constant, A.; Lagarde, E. Protecting vulnerable road users from injury. PLoS Med. 2010, 7, e1000228. [Google Scholar] [CrossRef]
- Anaya, J.J.; Merdrignac, P.; Shagdar, O.; Nashashibi, F.; Naranjo, J.E. Vehicle to pedestrian communications for protection of vulnerable road users. In Proceedings of the 2014 IEEE Intelligent Vehicles Symposium Proceedings, Dearborn, MI, USA, 8–11 June 2014; pp. 1037–1042. [Google Scholar]
- Heinovski, J.; Stratmann, L.; Buse, D.S.; Klingler, F.; Franke, M.; Oczko, M.C.H.; Sommer, C.; Scharlau, I.; Dressler, F. Modeling Cycling Behavior to Improve Bicyclists’ Safety at Intersections—A Networking Perspective. In Proceedings of the IEEE 20th International Symposium on a World of Wireless, Mobile and Multimedia Networks(WoWMoM), Washington, DC, USA, 10–12 June 2019; pp. 1–8. [Google Scholar]
- Habibovic, A.; Davidsson, J. Causation mechanisms in car-to-vulnerable road user crashes: Implications for active safety systems. Accid Anal. Prev. 2012, 49, 493–500. [Google Scholar] [CrossRef]
- Hasan, K.F.; Wang, C.; Feng, Y.; Tian, Y.C. Time synchronization in vehicular ad-hoc networks: A survey on theory and practice. Veh. Commun. 2018, 14, 39–51. [Google Scholar] [CrossRef]
- Rufino, J.; Silva, L.; Fernandes, B.; Almeida, J.; Ferreira, J. Empowering Vulnerable Road Users in C-ITS. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018. [Google Scholar]
- Johan Scholliers, M.v.S.; Moerman, K. Integration of vulnerable road users in cooperative ITS systems. Eur. Transp. Res. Rev. 2017, 9, 15. [Google Scholar] [CrossRef]
- Rabieh, K.; Aydogan, A.F.; Azer, M.A. Towards Safer Roads: An Efficient VANET-based Pedestrian Protection Scheme. In Proceedings of the 2021 International Conference on Communications, Computing, Cybersecurity, and Informatics (CCCI), Beijing, China, 15–17 October 2021; pp. 1–6. [Google Scholar] [CrossRef]
- NS3. The Network Simulator NS3. Available online: https://www.nsnam.org/ (accessed on 8 December 2023).
- SUMO. Simulation of Urban Mobility (SUMO) Documentation. Available online: https://sumo.dlr.de/docs/Tools/Trip.html (accessed on 8 December 2023).
- Petit, J.; Mammeri, Z. Authentication and consensus overhead in vehicular ad hoc networks. Telecommun. Syst. 2013, 52, 2699–2712. [Google Scholar] [CrossRef]
- Petit, J. Analysis of ecdsa authentication processing in vanets. In Proceedings of the 2009 3rd International Conference on New Technologies, Mobility and Security, Cairo, Egypt, 20–23 December 2009; pp. 1–5. [Google Scholar]
- Chen, R.; Ma, D.; Regan, A. TARI: Meeting delay requirements in VANETs with efficient authentication and revocation. In Proceedings of the 2nd International Conference on Wireless Access in Vehicular Environments (WAVE), Shanghai, China, 21–22 December 2009. [Google Scholar]
- Chantaksinopas, I.; Lee, W.; Prayote, A.; Oothongsap, P. Delay-sensitive applications in vanet and seamless connectivity: The limitation of UMTS network. Int. J. Comput. Sci. 2012, 12, 54–61. [Google Scholar]
- Soto, I.; Jiménez, F.; Calderón, M.; Naranjo, J.E.; Anaya, J.J. Reducing unnecessary alerts in pedestrian protection systems based on p2v communications. Electronics 2019, 8, 360. [Google Scholar] [CrossRef]
- Rashdan, I.; de Ponte Müller, F.; Jost, T.; Sand, S.; Caire, G. Large-scale fading characteristics and models for vehicle-to-pedestrian channel at 5-GHz. IEEE Access 2019, 7, 107648–107658. [Google Scholar] [CrossRef]
- Béduneau, G.; Jaber, G.; Ducourthial, B. A method for predicting ITS cooperative applications performances. Comput. Netw. 2022, 216, 109148. [Google Scholar] [CrossRef]
- Lara, T.; Yáñez, A.; Umaña, S.C.; Hafid, A.S. Impact of safety message generation rules on the awareness of vulnerable road users. Sensors 2021, 21, 3375. [Google Scholar] [CrossRef] [PubMed]
- Komamiya, W.; Tang, S.; Obana, S. Radiation angle estimation and high-precision pedestrian positioning by tracking change of channel state information. Sensors 2020, 20, 1430. [Google Scholar] [CrossRef] [PubMed]
- Wang, P.; Zhou, M.; Ding, Z. A VRU Collision Warning System with Kalman-Filter-Based Positioning Accuracy Improvement. In Proceedings of the 2021 IEEE International Conference on Information Communication and Software Engineering (ICICSE), Chengdu, China, 19–21 March 2021; pp. 191–198. [Google Scholar]
- Hashim, Z.; Zaidan, A.; Ahmed, M.A.; Bahaa, B.; Albahri, O.; Alamoodi, A.; Malik, R.; Albahri, A.; Ameen, H.; Garfan, S.; et al. An approach to pedestrian walking behaviour classification in wireless communication and network failure contexts. Complex Intell. Syst. 2022, 8, 909–931. [Google Scholar]
- Botache, D.; Dandan, L.; Bieshaar, M.; Sick, B. Early Pedestrian Movement Detection Using Smart Devices Based on Human Activity Recognition. In INFORMATIK 2019: 50 Jahre Gesellschaft für Informatik—Informatik für Gesellschaft (Workshop-Beiträge); Gesellschaft für Informatik eV: Bonn, Germany, 2019; pp. 229–238. [Google Scholar] [CrossRef]
- Morold, M.; Nguyen, Q.H.; Bachmann, M.; David, K.; Dressler, F. Requirements on delay of VRU context detection for cooperative collision avoidance. In Proceedings of the 2020 IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), Victoria, BC, Canada, 18 November–16 December 2020; pp. 1–5. [Google Scholar]
- Nguyen, Q.H.; Morold, M.; David, K.; Dressler, F. Car-to-Pedestrian communication with MEC-support for adaptive safety of Vulnerable Road Users. Comput. Commun. 2020, 150, 83–93. [Google Scholar] [CrossRef]
- Quang-Huy, N.; Michel, M.; Klaus, D.; Falko, D. Adaptive Safety Context Information for Vulnerable Road Users with MEC Support. In Proceedings of the 15th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Wengen, Switzerland, 22–24 January 2019; pp. 28–35. [Google Scholar]
- Malinverno, M.; Avino, G.; Casetti, C.; Chiasserini, C.F.; Malandrino, F.; Scarpina, S. MEC-based collision avoidance for vehicles and vulnerable users. arXiv 2019, arXiv:1911.05299. [Google Scholar]
- Babar, M.; Tariq, M.U.; Almasoud, A.; Alshehri, M. Privacy-Aware Data Forensics of VRUs Using Machine Learning and Big Data Analytics. Secur. Commun. Netw. 2021, 2021, 3320436. [Google Scholar] [CrossRef]
- Kabil, A.; Rabieh, K.; Kaleem, F.; Azer, M.A. Vehicle to Pedestrian Systems: Survey, Challenges and Recent Trends. IEEE Access 2022, 10, 123981–123994. [Google Scholar] [CrossRef]
- Tahmasbi-Sarvestani, A.; Nourkhiz Mahjoub, H.; Fallah, Y.P.; Moradi-Pari, E.; Abuchaar, O. Implementation and Evaluation of a Cooperative Vehicle-to-Pedestrian Safety Application. IEEE Intell. Transp. Syst. Mag. 2017, 9, 62–75. [Google Scholar] [CrossRef]
- Sewalkar, P.; Seitz, J. Vehicle-to-Pedestrian Communication for Vulnerable Road Users: Survey, Design Considerations, and Challenges. Sensors 2019, 19, 358. [Google Scholar] [CrossRef] [PubMed]
- Rettenmaier, M.; Schulze, J.; Bengler, K. How Much Space Is Required? Effect of Distance, Content, and Color on External Human-Machine Interface Size. Information 2020, 11, 346. [Google Scholar] [CrossRef]
- Chauhan, V.; Chang, C.M.; Javanmardi, E.; Nakazato, J.; Lin, P.; Igarashi, T.; Tsukada, M. Fostering Fuzzy Logic in Enhancing Pedestrian Safety: Harnessing Smart Pole Interaction Unit for Autonomous Vehicle-to-Pedestrian Communication and Decision Optimization. Electronics 2023, 12, 4207. [Google Scholar] [CrossRef]
- Acerra, E.M.; Shoman, M.; Imine, H.; Brasile, C.; Lantieri, C.; Vignali, V. The Visual Behaviour of the Cyclist: Comparison between Simulated and Real Scenarios. Infrastructures 2023, 8, 92. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).