A Review of Power System False Data Attack Detection Technology Based on Big Data
Abstract
1. Introduction
- (1)
- Keyword selection: Choose keywords that accurately reflect the topic and research content of the article. Make sure that the selected keywords cover all aspects of power system big data analysis and false data attack detection. For example: “big data”, “power system”, “false data attack”, “blockchain”, “state estimation”, “machine learning” and “data-driven”, etc.
- (2)
- Publication date of the literature: Literature published within the past 3–5 years is usually selected to ensure that the technologies and methods discussed are the latest and most relevant. Big data technology and power system security are developing rapidly, and early literature may be outdated and cannot reflect the current research progress and technical level.
- (3)
- Research quality: Consider articles published in journals or conferences with high impact factors, as well as articles that are widely cited. A higher impact factor for a journal generally means higher quality articles. Articles with many citations often have a greater impact on other research in the field. The specific evaluation method follows: Perform a preliminary screening based on the title and abstract and eliminate irrelevant articles. Find the impact factor of the journal or conference where the article was published. Use Google Scholar or other academic search engines to check the number of citations of the article.
- (4)
- Relevance of research methods: Select the literature that uses advanced big data analysis methods or power system-specific false data detection techniques in the research. Read the abstract and method section of the literature to confirm whether the methods used are relevant to big data and false data attack detection. Compare the methods of different studies and select the most innovative and practical research.
- (5)
- Importance of findings: Select studies that have a significant impact on practical applications or significantly advance the theory. Investigate whether the research results can be applied to the safety protection of actual power systems and whether the research proposes new theories and models and makes important contributions to the academic community. Read the conclusion part of the literature and analyze the practical application and theoretical contribution of its research results.
2. Application Status of Big Data Technology in the Power Industry
2.1. Optimization of Energy Production
2.2. Analysis of Energy Consumption
2.3. User Service Improvements
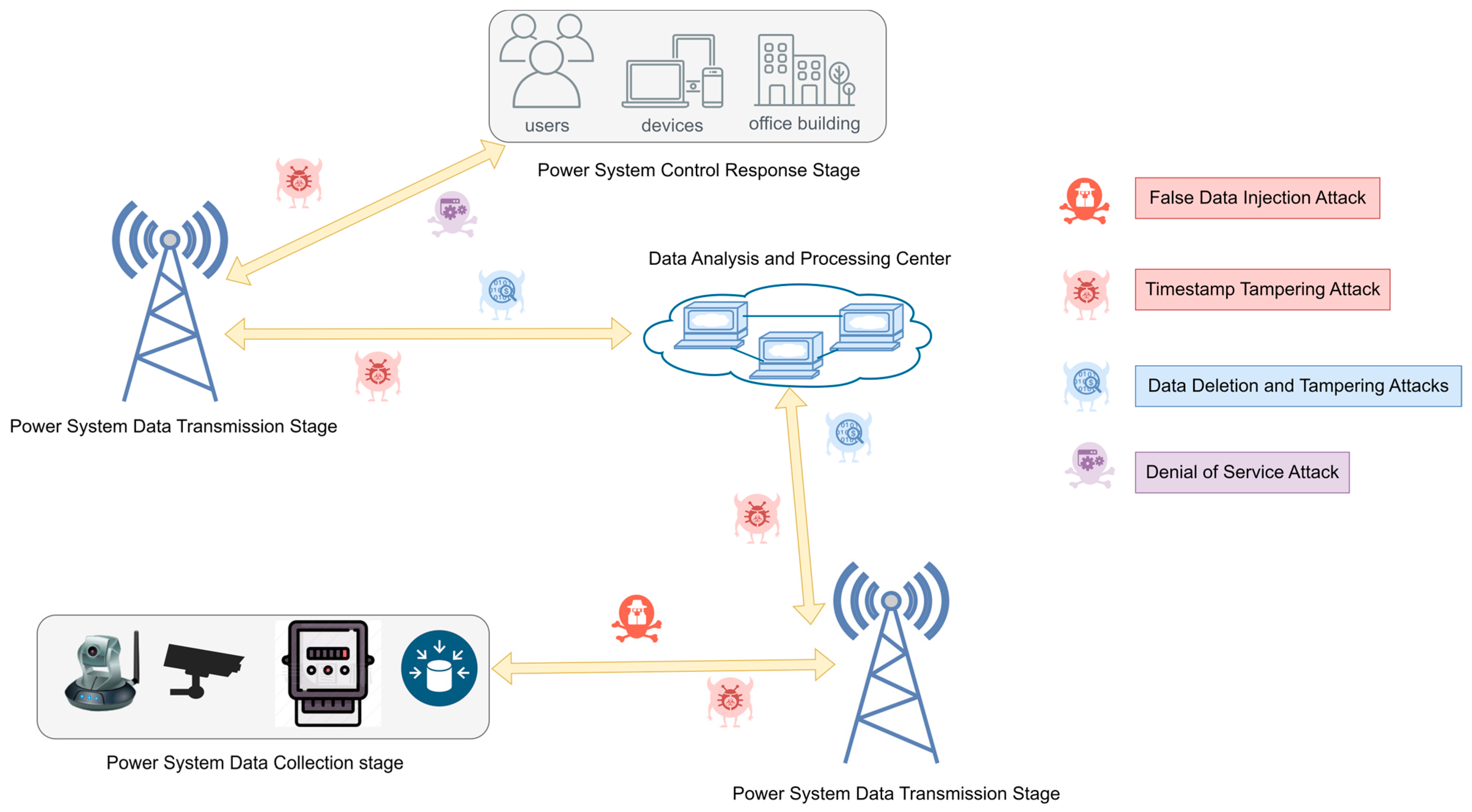
3. Overview of False Data Attacks
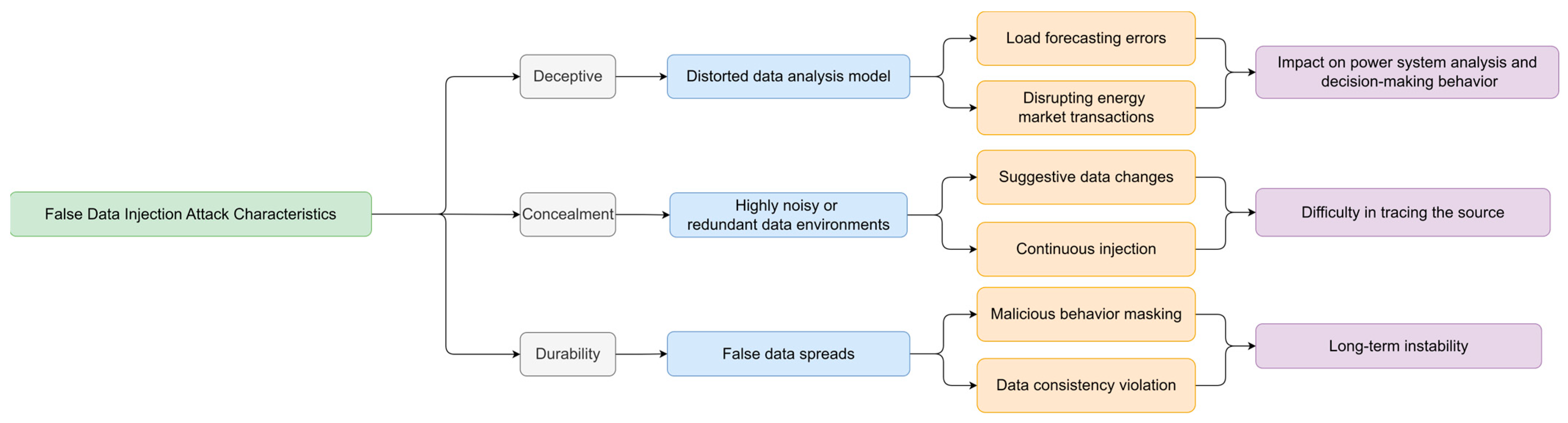
3.1. False Data Injection Attack
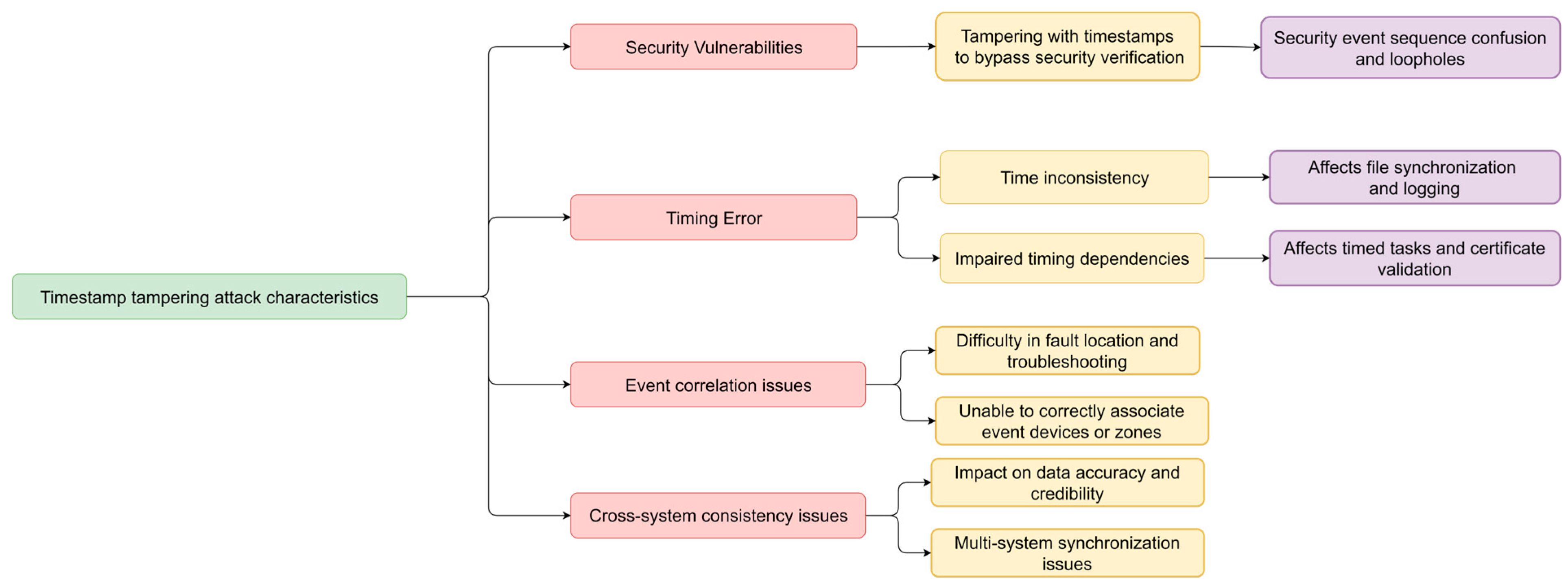
3.2. Timestamp Tampering Attack
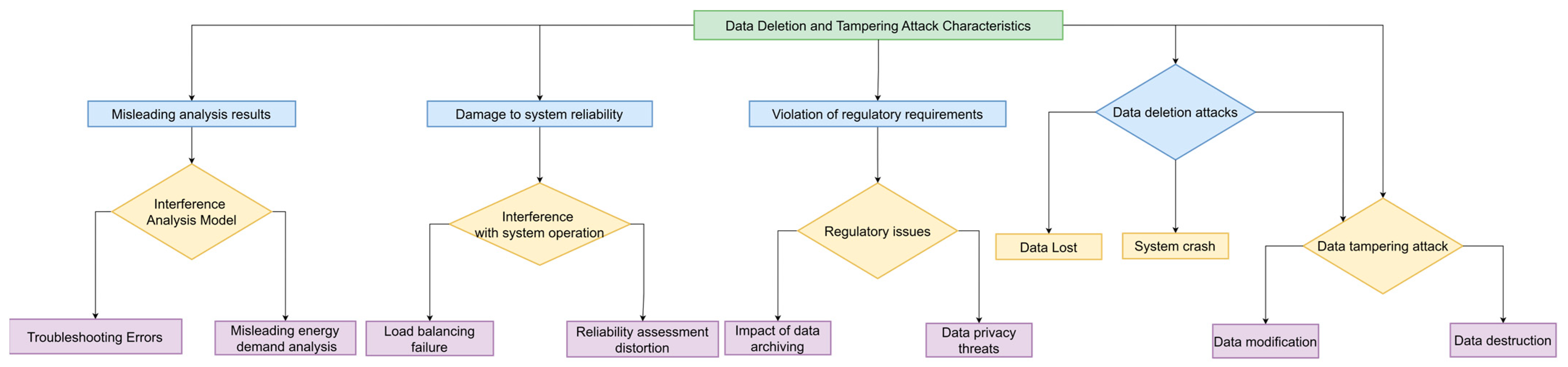
3.3. Data Deletion and Tampering Attacks
3.4. Denial of Service Attack
4. Analysis of False Data Attacks in Four Aspects of Power Big Data System
4.1. Data Collection Stage
4.1.1. State Estimation
4.1.2. Machine Learning
4.1.3. Data Driven
4.2. Data Transmission Stage
Time Synchronization Monitoring
4.3. Data Processing and Analysis Stage
- (1)
- Strengthen access control to the power system and limit the deletion and modification permissions of key data.
- (2)
- Implement data backup and disaster recovery mechanisms to ensure data reliability and durability.
- (3)
- Use secure encryption technology to protect data transmission and storage to prevent attackers from tampering with or deleting data.
- (4)
- Digitally sign or hash check key data to verify data integrity and authenticity.
- (5)
- Establish data audit and monitoring mechanisms to detect abnormal and malicious behavior promptly.
4.3.1. Data Integrity Verification
4.3.2. Blockchain Technology
4.4. Control and Response Stage
4.4.1. Traffic Supervision
4.4.2. Statistics
4.4.3. Elastic Computing
5. Research Challenges and Future Directions
5.1. Covert New Adversarial Attack Detection
5.2. How to Further Unleash the Potential of Big Data in the Power Sector
5.3. Power Big Data Security and Privacy Protection
6. Conclusions
- (1)
- The accuracy and security of data acquisition equipment and how they resist external interference and tampering.
- (2)
- Encryption and authentication technology during data transmission to ensure the integrity and confidentiality of data as it passes through different network nodes and media.
- (3)
- Algorithm robustness in the data processing and analysis phase to identify and filter out false or abnormal data.
- (4)
- The design of the control and response system so that quick action can be taken when an attack is detected.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lu, Y. Cyber Physical System (CPS)-Based Industry 4.0: A Survey. J. Ind. Intg. Mgmt. 2017, 02, 1750014. [Google Scholar] [CrossRef]
- Meyer, E.L.; Apeh, O.O.; Overen, O.K. Electrical and Meteorological Data Acquisition System of a Commercial and Domestic Microgrid for Monitoring PV Parameters. Appl. Sci. 2020, 10, 9092. [Google Scholar] [CrossRef]
- Shangguan, X.-C.; Zhang, C.-K.; He, Y.; Jin, L.; Jiang, L.; Spencer, J.W.; Wu, M. Robust Load Frequency Control for Power System Considering Transmission Delay and Sampling Period. IEEE Trans. Ind. Inf. 2021, 17, 5292–5303. [Google Scholar] [CrossRef]
- Samy, M.M.; Almamlook, R.E.; Elkhouly, H.I.; Barakat, S. Decision-Making and Optimal Design of Green Energy System Based on Statistical Methods and Artificial Neural Network Approaches. Sustain. Cities Soc. 2022, 84, 104015. [Google Scholar] [CrossRef]
- Sheidaei, F.; Ahmarinejad, A. Multi-Stage Stochastic Framework for Energy Management of Virtual Power Plants Considering Electric Vehicles and Demand Response Programs. Int. J. Electr. Power Energy Syst. 2020, 120, 106047. [Google Scholar] [CrossRef]
- Whitehead, D.E.; Owens, K.; Gammel, D.; Smith, J. Ukraine Cyber-Induced Power Outage: Analysis and Practical Mitigation Strategies. In Proceedings of the 2017 70th Annual Conference for Protective Relay Engineers (CPRE), College Station, TX, USA, 3–6 April 2017; pp. 1–8. [Google Scholar]
- Mukherjee, D.; Chakraborty, S.; Ghosh, S. Deep Learning-Based Multilabel Classification for Locational Detection of False Data Injection Attack in Smart Grids. Electr. Eng. 2022, 104, 259–282. [Google Scholar] [CrossRef]
- Xu, L.; Guo, Q.; Sheng, Y.; Muyeen, S.M.; Sun, H. On the Resilience of Modern Power Systems: A Comprehensive Review from the Cyber-Physical Perspective. Renew. Sustain. Energy Rev. 2021, 152, 111642. [Google Scholar] [CrossRef]
- Ge, X.; Han, Q.-L.; Zhang, X.-M.; Ding, D.; Yang, F. Resilient and Secure Remote Monitoring for a Class of Cyber-Physical Systems against Attacks. Inf. Sci. 2020, 512, 1592–1605. [Google Scholar] [CrossRef]
- Mota, B.; Gomes, L.; Faria, P.; Ramos, C.; Vale, Z.; Correia, R. Production Line Optimization to Minimize Energy Cost and Participate in Demand Response Events. Energies 2021, 14, 462. [Google Scholar] [CrossRef]
- Ayvaz, S.; Alpay, K. Predictive Maintenance System for Production Lines in Manufacturing: A Machine Learning Approach Using IoT Data in Real-Time. Expert Syst. Appl. 2021, 173, 114598. [Google Scholar] [CrossRef]
- Ofori-Ntow Jnr, E.; Ziggah, Y.Y.; Relvas, S. Hybrid Ensemble Intelligent Model Based on Wavelet Transform, Swarm Intelligence and Artificial Neural Network for Electricity Demand Forecasting. Sustain. Cities Soc. 2021, 66, 102679. [Google Scholar] [CrossRef]
- Somu, N.; Raman M R, G.; Ramamritham, K. A Deep Learning Framework for Building Energy Consumption Forecast. Renew. Sustain. Energy Rev. 2021, 137, 110591. [Google Scholar] [CrossRef]
- Bhatia, K.; Mittal, R.; Varanasi, J.; Tripathi, M.M. An Ensemble Approach for Electricity Price Forecasting in Markets with Renewable Energy Resources. Util. Policy 2021, 70, 101185. [Google Scholar] [CrossRef]
- Zhou, F.; Jiao, R.J.; Xu, Q.; Takahashi, K. User Experience Modeling and Simulation for Product Ecosystem Design Based on Fuzzy Reasoning Petri Nets. IEEE Trans. Syst. Man Cybern. A 2012, 42, 201–212. [Google Scholar] [CrossRef]
- Yang, B.; Liu, Y.; Chen, W. A Twin Data-Driven Approach for User-Experience Based Design Innovation. Int. J. Inf. Manag. 2023, 68, 102595. [Google Scholar] [CrossRef]
- Tong, Y.; Liang, Y.; Spasic, I.; Hicks, Y.; Hu, H.; Liu, Y. A Data-Driven Approach for Integrating Hedonic Quality and Pragmatic Quality in User Experience Modeling. J. Comput. Inf. Sci. Eng. 2022, 22, 061002. [Google Scholar] [CrossRef]
- Bu, L.; Chen, C.-H.; Ng, K.K.H.; Zheng, P.; Dong, G.; Liu, H. A User-Centric Design Approach for Smart Product-Service Systems Using Virtual Reality: A Case Study. J. Clean. Prod. 2021, 280, 124413. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z.; Li, Z. Optimal Protection Strategy Against False Data Injection Attacks in Power Systems. IEEE Trans. Smart Grid 2017, 8, 1802–1810. [Google Scholar] [CrossRef]
- Huang, R.; Li, Y. False Phasor Data Detection Under Time Synchronization Attacks: A Neural Network Approach. IEEE Trans. Smart Grid 2022, 13, 4828–4836. [Google Scholar] [CrossRef]
- Zhang, J.; Dong, C. Privacy-Preserving Data Aggregation Scheme against Deletion and Tampering Attacks from Aggregators. J. King Saud Univ.—Comput. Inf. Sci. 2023, 35, 100–111. [Google Scholar] [CrossRef]
- Chen, W.; Ding, D.; Dong, H.; Wei, G. Distributed Resilient Filtering for Power Systems Subject to Denial-of-Service Attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1688–1697. [Google Scholar] [CrossRef]
- Sayghe, A.; Hu, Y.; Zografopoulos, I.; Liu, X.; Dutta, R.G.; Jin, Y.; Konstantinou, C. Survey of Machine Learning Methods for Detecting False Data Injection Attacks in Power Systems. IET Smart Grid 2020, 3, 581–595. [Google Scholar] [CrossRef]
- Chakrabarty, S.; Sikdar, B. Unified Detection of Attacks Involving Injection of False Control Commands and Measurements in Transmission Systems of Smart Grids. IEEE Trans. Smart Grid 2022, 13, 1598–1610. [Google Scholar] [CrossRef]
- Du, D.; Chen, R.; Li, X.; Wu, L.; Zhou, P.; Fei, M. Malicious Data Deception Attacks against Power Systems: A New Case and Its Detection Method. Trans. Inst. Meas. Control 2019, 41, 1590–1599. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A. Comprehensive Survey and Taxonomies of False Data Injection Attacks in Smart Grids: Attack Models, Targets, and Impacts. Renew. Sustain. Energy Rev. 2022, 163, 112423. [Google Scholar] [CrossRef]
- Unsal, D.B.; Ustun, T.S.; Hussain, S.M.S.; Onen, A. Enhancing Cybersecurity in Smart Grids: False Data Injection and Its Mitigation. Energies 2021, 14, 2657. [Google Scholar] [CrossRef]
- Farha, F.; Ning, H.; Yang, S.; Xu, J.; Zhang, W.; Choo, K.-K.R. Timestamp Scheme to Mitigate Replay Attacks in Secure ZigBee Networks. IEEE Trans. Mob. Comput. 2020, 21, 341–351. [Google Scholar] [CrossRef]
- Wang, T.; Liu, W.; Cabrera, L.V.; Wang, P.; Wei, X.; Zang, T. A Novel Fault Diagnosis Method of Smart Grids Based on Memory Spiking Neural P Systems Considering Measurement Tampering Attacks. Inf. Sci. 2022, 596, 520–536. [Google Scholar] [CrossRef]
- Siamak, S.; Dehghani, M.; Mohammadi, M. Dynamic GPS Spoofing Attack Detection, Localization, and Measurement Correction Exploiting PMU and SCADA. IEEE Syst. J. 2021, 15, 2531–2540. [Google Scholar] [CrossRef]
- Pal, S.; Sikdar, B.; Chow, J. Detecting Data Integrity Attacks on SCADA Systems Using Limited PMUs. In Proceedings of the 2016 IEEE International Conference on Smart Grid Communications (SmartGridComm), Sydney, Australia, 6–9 November 2016; pp. 545–550. [Google Scholar]
- Sun, C.-C.; Sebastian Cardenas, D.J.; Hahn, A.; Liu, C.-C. Intrusion Detection for Cybersecurity of Smart Meters. IEEE Trans. Smart Grid 2021, 12, 612–622. [Google Scholar] [CrossRef]
- Shen, Y.; Fei, M.; Du, D. Cyber Security Study for Power Systems under Denial of Service Attacks. Trans. Inst. Meas. Control. 2019, 41, 1600–1614. [Google Scholar] [CrossRef]
- Gupta, B.B.; Chaudhary, P.; Chang, X.; Nedjah, N. Smart Defense against Distributed Denial of Service Attack in IoT Networks Using Supervised Learning Classifiers. Comput. Electr. Eng. 2022, 98, 107726. [Google Scholar] [CrossRef]
- Huseinovic, A.; Mrdovic, S.; Bicakci, K.; Uludag, S. A Survey of Denial-of-Service Attacks and Solutions in the Smart Grid. IEEE Access 2020, 8, 177447–177470. [Google Scholar] [CrossRef]
- Li, B.; Wang, W.; Guo, J.; Ding, B. Research on Condition Operation Monitoring of Power System Based on Supervisory Control and Data Acquisition Model. Alex. Eng. J. 2024, 99, 326–334. [Google Scholar] [CrossRef]
- Pan, G.; Gu, W.; Lu, Y.; Qiu, H.; Lu, S.; Yao, S. Optimal Planning for Electricity-Hydrogen Integrated Energy System Considering Power to Hydrogen and Heat and Seasonal Storage. IEEE Trans. Sustain. Energy 2020, 11, 2662–2676. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A.N.; Tari, Z. A Taxonomy of Cyber Defence Strategies Against False Data Attacks in Smart Grids. ACM Comput. Surv. 2023, 55, 1–37. [Google Scholar] [CrossRef]
- Jadidi, S.; Badihi, H.; Zhang, Y. Active Fault-Tolerant and Attack-Resilient Control for a Renewable Microgrid Against Power-Loss Faults and Data Integrity Attacks. IEEE Trans. Cybern. 2024, 54, 2113–2128. [Google Scholar] [CrossRef] [PubMed]
- Kazemi, Z.; Safavi, A.A.; Naseri, F.; Urbas, L.; Setoodeh, P. A Secure Hybrid Dynamic-State Estimation Approach for Power Systems Under False Data Injection Attacks. IEEE Trans. Ind. Inf. 2020, 16, 7275–7286. [Google Scholar] [CrossRef]
- Chen, J.; Liang, G.; Cai, Z.; Hu, C.; Xu, Y.; Luo, F.; Zhao, J. Impact Analysis of False Data Injection Attacks on Power System Static Security Assessment. J. Mod. Power Syst. Clean Energy 2016, 4, 496–505. [Google Scholar] [CrossRef]
- Hu, P.; Gao, W.; Li, Y.; Hua, F.; Qiao, L.; Zhang, G. Detection of False Data Injection Attacks in Smart Grid Based on Joint Dynamic and Static State Estimation. IEEE Access 2023, 11, 45028–45038. [Google Scholar] [CrossRef]
- Qu, Z.; Zhang, J.; Wang, Y.; Georgievitch, P.M.; Guo, K. False Data Injection Attack Detection and Improved WLS Power System State Estimation Based on Node Trust. J. Electr. Eng. Technol. 2022, 17, 803–817. [Google Scholar] [CrossRef]
- Khalid, H.M.; Flitti, F.; Mahmoud, M.S.; Hamdan, M.M.; Muyeen, S.M.; Dong, Z.Y. Wide Area Monitoring System Operations in Modern Power Grids: A Median Regression Function-Based State Estimation Approach towards Cyber Attacks. Sustain. Energy Grids Netw. 2023, 34, 101009. [Google Scholar] [CrossRef]
- Tang, B.; Yan, J.; Kay, S.; He, H. Detection of False Data Injection Attacks in Smart Grid under Colored Gaussian Noise. In Proceedings of the 2016 IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA, 17–19 October 2016; pp. 172–179. [Google Scholar]
- Liu, Y.; Cheng, L. Relentless False Data Injection Attacks Against Kalman-Filter-Based Detection in Smart Grid. IEEE Trans. Control Netw. Syst. 2022, 9, 1238–1250. [Google Scholar] [CrossRef]
- Karimipour, H.; Leung, H. Relaxation-based Anomaly Detection in Cyber-physical Systems Using Ensemble Kalman Filter. IET Cyber-Phys. Syst. 2020, 5, 49–58. [Google Scholar] [CrossRef]
- Foroutan, S.A.; Salmasi, F.R. Detection of False Data Injection Attacks against State Estimation in Smart Grids Based on a Mixture Gaussian Distribution Learning Method. IET Cyber-Phys. Syst. 2017, 2, 161–171. [Google Scholar] [CrossRef]
- Khalaf, M.; Youssef, A.; El-Saadany, E. A Particle Filter-Based Approach for the Detection of False Data Injection Attacks on Automatic Generation Control Systems. In Proceedings of the 2018 IEEE Electrical Power and Energy Conference (EPEC), Toronto, ON, Canada, 10–11 October 2018; pp. 1–6. [Google Scholar]
- Dayananda, P.; Srikantaswamy, M.; Nagaraju, S.; Velluri, R.; Kumar, D.M. Efficient Detection of Faults and False Data Injection Attacks in Smart Grid Using a Reconfigurable Kalman Filter. IJPEDS 2022, 13, 2086. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, Z.; Ma, J.; Jin, Q. KFRNN: An Effective False Data Injection Attack Detection in Smart Grid Based on Kalman Filter and Recurrent Neural Network. IEEE Internet Things J. 2022, 9, 6893–6904. [Google Scholar] [CrossRef]
- Luo, X.; Zhu, M.; Wang, X.; Guan, X. Detection and Isolation of False Data Injection Attack via Adaptive Kalman Filter Bank. J. Control. Decis. 2022, 11, 60–72. [Google Scholar] [CrossRef]
- Rashed, M.; Kamruzzaman, J.; Gondal, I.; Islam, S. False Data Detection in a Clustered Smart Grid Using Unscented Kalman Filter. IEEE Access 2022, 10, 78548–78556. [Google Scholar] [CrossRef]
- Živković, N.; Sarić, A.T. Detection of False Data Injection Attacks Using Unscented Kalman Filter. J. Mod. Power Syst. Clean Energy 2018, 6, 847–859. [Google Scholar] [CrossRef]
- Lu, J.; Wang, W.; Li, L.; Guo, Y. Unscented Kalman Filtering for Nonlinear Systems with Sensor Saturation and Randomly Occurring False Data Injection Attacks. Asian J. Control 2021, 23, 871–881. [Google Scholar] [CrossRef]
- Nawaz, R.; Akhtar, R.; Shahid, M.A.; Qureshi, I.M.; Mahmood, M.H. Machine Learning Based False Data Injection in Smart Grid. Int. J. Electr. Power Energy Syst. 2021, 130, 106819. [Google Scholar] [CrossRef]
- Ibrahim, M.S.; Dong, W.; Yang, Q. Machine Learning Driven Smart Electric Power Systems: Current Trends and New Perspectives. Appl. Energy 2020, 272, 115237. [Google Scholar] [CrossRef]
- Liu, J.; Xu, Z.; Fan, W.N.; Wang, Y.; Mo, W. The Combination Mode of Forest and SVM for Power Network Disaster Response Failure Identification. Comput. Electr. Eng. 2024, 117, 109255. [Google Scholar] [CrossRef]
- Qu, Z.; Li, H.; Wang, Y.; Zhang, J.; Abu-Siada, A.; Yao, Y. Detection of Electricity Theft Behavior Based on Improved Synthetic Minority Oversampling Technique and Random Forest Classifier. Energies 2020, 13, 2039. [Google Scholar] [CrossRef]
- Lu, X.; Jing, J.; Wu, Y. False Data Injection Attack Location Detection Based on Classification Method in Smart Grid. In Proceedings of the 2020 2nd International Conference on Artificial Intelligence and Advanced Manufacture (AIAM), Manchester, UK, 15–17 October 2020; pp. 133–136. [Google Scholar]
- Boyaci, O.; Umunnakwe, A.; Sahu, A.; Narimani, M.R.; Ismail, M.; Davis, K.R.; Serpedin, E. Graph Neural Networks Based Detection of Stealth False Data Injection Attacks in Smart Grids. IEEE Syst. J. 2022, 16, 2946–2957. [Google Scholar] [CrossRef]
- Miraftabzadeh, S.M.; Colombo, C.G.; Longo, M.; Foiadelli, F. K-Means and Alternative Clustering Methods in Modern Power Systems. IEEE Access 2023, 11, 119596–119633. [Google Scholar] [CrossRef]
- Roy, S.D.; Debbarma, S. A Novel OC-SVM Based Ensemble Learning Framework for Attack Detection in AGC Loop of Power Systems. Electr. Power Syst. Res. 2022, 202, 107625. [Google Scholar] [CrossRef]
- Sharma, R.; Joshi, A.M.; Sahu, C.; Nanda, S.J. Detection of False Data Injection in Smart Grid Using PCA Based Unsupervised Learning. Electr. Eng. 2023, 105, 2383–2396. [Google Scholar] [CrossRef]
- Ashrafuzzaman, M.; Das, S.; Chakhchoukh, Y.; Shiva, S.; Sheldon, F.T. Detecting Stealthy False Data Injection Attacks in the Smart Grid Using Ensemble-Based Machine Learning. Comput. Secur. 2020, 97, 101994. [Google Scholar] [CrossRef]
- Farajzadeh-Zanjani, M.; Hallaji, E.; Razavi-Far, R.; Saif, M.; Parvania, M. Adversarial Semi-Supervised Learning for Diagnosing Faults and Attacks in Power Grids. IEEE Trans. Smart Grid 2021, 12, 3468–3478. [Google Scholar] [CrossRef]
- Zhou, Q.; Duan, L. Semi-Supervised Recommendation Attack Detection Based on Co-Forest. Comput. Secur. 2021, 109, 102390. [Google Scholar] [CrossRef]
- Ahmadi, A.; Nabipour, M.; Taheri, S.; Mohammadi-Ivatloo, B.; Vahidinasab, V. A New False Data Injection Attack Detection Model for Cyberattack Resilient Energy Forecasting. IEEE Trans. Ind. Inf. 2023, 19, 371–381. [Google Scholar] [CrossRef]
- Umar, S.; Felemban, M. Rule-Based Detection of False Data Injections Attacks against Optimal Power Flow in Power Systems. Sensors 2021, 21, 2478. [Google Scholar] [CrossRef]
- Dong, F.; Chen, S.; Demachi, K.; Yoshikawa, M.; Seki, A.; Takaya, S. Attention-Based Time Series Analysis for Data-Driven Anomaly Detection in Nuclear Power Plants. Nucl. Eng. Des. 2023, 404, 112161. [Google Scholar] [CrossRef]
- Sahu, A.; Mao, Z.; Wlazlo, P.; Huang, H.; Davis, K.; Goulart, A.; Zonouz, S. Multi-Source Multi-Domain Data Fusion for Cyberattack Detection in Power Systems. IEEE Access 2021, 9, 119118–119138. [Google Scholar] [CrossRef]
- Zhao, Z.; Huang, Y.; Zhen, Z.; Li, Y. Data-Driven False Data-Injection Attack Design and Detection in Cyber-Physical Systems. IEEE Trans. Cybern. 2021, 51, 6179–6187. [Google Scholar] [CrossRef] [PubMed]
- Chen, Y.; Huang, S.; Liu, F.; Wang, Z.; Sun, X. Evaluation of Reinforcement Learning-Based False Data Injection Attack to Automatic Voltage Control. IEEE Trans. Smart Grid 2019, 10, 2158–2169. [Google Scholar] [CrossRef]
- Isah, H.; Zulkernine, F. A Scalable and Robust Framework for Data Stream Ingestion. In Proceedings of the 2018 IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, 10–13 December 2018; pp. 2900–2905. [Google Scholar]
- Yan, H.; Paynabar, K.; Shi, J. Real-Time Monitoring of High-Dimensional Functional Data Streams via Spatio-Temporal Smooth Sparse Decomposition. Technometrics 2018, 60, 181–197. [Google Scholar] [CrossRef]
- Silva, B.; Khan, M.; Jung, C.; Seo, J.; Muhammad, D.; Han, J.; Yoon, Y.; Han, K. Urban Planning and Smart City Decision Management Empowered by Real-Time Data Processing Using Big Data Analytics. Sensors 2018, 18, 2994. [Google Scholar] [CrossRef]
- Hallaji, E.; Razavi-Far, R.; Wang, M.; Saif, M.; Fardanesh, B. A Stream Learning Approach for Real-Time Identification of False Data Injection Attacks in Cyber-Physical Power Systems. IEEE Trans. Inform. Forensics Secur. 2022, 17, 3934–3945. [Google Scholar] [CrossRef]
- Gong, S.; Lee, C. Cyber Threat Intelligence Framework for Incident Response in an Energy Cloud Platform. Electronics 2021, 10, 239. [Google Scholar] [CrossRef]
- Moradi, M.; Jahangir, A.H. A New Delay Attack Detection Algorithm for PTP Network in Power Substation. Int. J. Electr. Power Energy Syst. 2021, 133, 107226. [Google Scholar] [CrossRef]
- Moussa, B.; Kassouf, M.; Hadjidj, R.; Debbabi, M.; Assi, C. An Extension to the Precision Time Protocol (PTP) to Enable the Detection of Cyber Attacks. IEEE Trans. Ind. Inf. 2020, 16, 18–27. [Google Scholar] [CrossRef]
- Alghamdi, W.; Schukat, M. A Security Enhancement of the Precision Time Protocol Using a Trusted Supervisor Node. Sensors 2022, 22, 3671. [Google Scholar] [CrossRef] [PubMed]
- Qiu, T.; Liu, X.; Han, M.; Ning, H.; Wu, D.O. A Secure Time Synchronization Protocol Against Fake Timestamps for Large-Scale Internet of Things. IEEE Internet Things J. 2017, 4, 1879–1889. [Google Scholar] [CrossRef]
- Wu, Q.; Han, Z.; Mohiuddin, G.; Ren, Y. Distributed Timestamp Mechanism Based on Verifiable Delay Functions. Comput. Syst. Sci. Eng. 2023, 44, 1633–1646. [Google Scholar] [CrossRef]
- Moussa, B.; Robillard, C.; Zugenmaier, A.; Kassouf, M.; Debbabi, M.; Assi, C. Securing the Precision Time Protocol (PTP) Against Fake Timestamps. IEEE Commun. Lett. 2019, 23, 278–281. [Google Scholar] [CrossRef]
- He, T.; Zheng, Y.; Ma, Z. Study of Network Time Synchronisation Security Strategy Based on Polar Coding. Comput. Secur. 2021, 104, 102214. [Google Scholar] [CrossRef]
- Hymlin Rose, S.G.; Jayasree, T. Detection of Jamming Attack Using Timestamp for WSN. Ad Hoc Networks 2019, 91, 101874. [Google Scholar] [CrossRef]
- Wang, H.; Zhang, J. Blockchain Based Data Integrity Verification for Large-Scale IoT Data. IEEE Access 2019, 7, 164996–165006. [Google Scholar] [CrossRef]
- Ateniese, G.; Burns, R.; Curtmola, R.; Herring, J.; Kissner, L.; Peterson, Z.; Song, D. Provable Data Possession at Untrusted Stores. In Proceedings of the Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 28 October 2007; pp. 598–609.
- Shen, J.; Shen, J.; Chen, X.; Huang, X.; Susilo, W. An Efficient Public Auditing Protocol With Novel Dynamic Structure for Cloud Data. IEEE Trans. Inform. Forensics Secur. 2017, 12, 2402–2415. [Google Scholar] [CrossRef]
- Erway, C.C.; Küpçü, A.; Papamanthou, C.; Tamassia, R. Dynamic Provable Data Possession. ACM Trans. Inf. Syst. Secur. 2015, 17, 1–29. [Google Scholar] [CrossRef]
- Liu, C.; Ranjan, R.; Yang, C.; Zhang, X.; Wang, L.; Chen, J. MuR-DPA: Top-Down Levelled Multi-Replica Merkle Hash Tree Based Secure Public Auditing for Dynamic Big Data Storage on Cloud. IEEE Trans. Comput. 2015, 64, 2609–2622. [Google Scholar] [CrossRef]
- Jayaraman, I.; Mohammed, M. Secure Privacy Conserving Provable Data Possession (SPC-PDP) Framework. Inf. Syst. E-Bus Manag. 2020, 18, 351–377. [Google Scholar] [CrossRef]
- Juels, A.; Kaliski, B.S. Pors: Proofs of Retrievability for Large Files. In Proceedings of the Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 28 October 2007; pp. 584–597.
- Wang, Q.; Wang, C.; Ren, K.; Lou, W.; Li, J. Enabling Public Auditability and Data Dynamics for Storage Security in Cloud Computing. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 847–859. [Google Scholar] [CrossRef]
- Ge, X.; Yu, J.; Zhang, H.; Hu, C.; Li, Z.; Qin, Z.; Hao, R. Towards Achieving Keyword Search over Dynamic Encrypted Cloud Data with Symmetric-Key Based Verification. IEEE Trans. Dependable Secur. Comput. 2021, 18, 490–504. [Google Scholar] [CrossRef]
- Liu, Q.; Tian, Y.; Wu, J.; Peng, T.; Wang, G. Enabling Verifiable and Dynamic Ranked Search over Outsourced Data. IEEE Trans. Serv. Comput. 2022, 15, 69–82. [Google Scholar] [CrossRef]
- Fu, A.; Li, Y.; Yu, S.; Yu, Y.; Zhang, G. DIPOR: An IDA-Based Dynamic Proof of Retrievability Scheme for Cloud Storage Systems. J. Netw. Comput. Appl. 2018, 104, 97–106. [Google Scholar] [CrossRef]
- Lian, J.; Wang, S.; Xie, Y. TDRB: An Efficient Tamper-Proof Detection Middleware for Relational Database Based on Blockchain Technology. IEEE Access 2021, 9, 66707–66722. [Google Scholar] [CrossRef]
- Chen, S.; Yang, L.; Zhao, C.; Varadarajan, V.; Wang, K. Double-Blockchain Assisted Secure and Anonymous Data Aggregation for Fog-Enabled Smart Grid. Engineering 2022, 8, 159–169. [Google Scholar] [CrossRef]
- Pourvahab, M.; Ekbatanifard, G. An Efficient Forensics Architecture in Software-Defined Networking-IoT Using Blockchain Technology. IEEE Access 2019, 7, 99573–99588. [Google Scholar] [CrossRef]
- Martino, R.; Cilardo, A. Designing a SHA-256 Processor for Blockchain-Based IoT Applications. Internet Things 2020, 11, 100254. [Google Scholar] [CrossRef]
- Nunoo-Mensah, H.; Boateng, K.O.; Gadze, J.D. Tamper-aware Authentication Framework for Wireless Sensor Networks. IET Wirel. Sens. Syst. 2017, 7, 73–81. [Google Scholar] [CrossRef]
- Ren, Y.; Qi, J.; Liu, Y.; Wang, J.; Kim, G.-J. Integrity Verification Mechanism of Sensor Data Based on Bilinear Map Accumulator. ACM Trans. Internet Technol. 2021, 21, 1–19. [Google Scholar] [CrossRef]
- Bos, J.W.; Halderman, J.A.; Heninger, N.; Moore, J.; Naehrig, M.; Wustrow, E. Elliptic Curve Cryptography in Practice. In Financial Cryptography and Data Security; Christin, N., Safavi-Naini, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; pp. 157–175. [Google Scholar]
- Romailler, Y.; Pelissier, S. Practical Fault Attack against the Ed25519 and EdDSA Signature Schemes. In Proceedings of the 2017 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Taipei, Taiwan, 25 September 2017; pp. 17–24. [Google Scholar]
- Li, J.; Wu, J.; Chen, L. Block-Secure: Blockchain Based Scheme for Secure P2P Cloud Storage. Inf. Sci. 2018, 465, 219–231. [Google Scholar] [CrossRef]
- Shi, C.; Wang, H.; Hu, Y.; Li, X. A Novel NMF-Based Authentication Scheme for Encrypted Speech in Cloud Computing. Multimed. Tools Appl. 2021, 80, 25773–25798. [Google Scholar] [CrossRef]
- Rijmen, V.; Daemen, J. Advanced encryption standard. Proc. Fed. Inf. Process. Stand. Publ. Natl. Inst. Stand. Technol. 2001, 19, 22. [Google Scholar]
- Da Silva, L.E.; Coury, D.V. Network Traffic Prediction for Detecting DDoS Attacks in IEC 61850 Communication Networks. Comput. Electr. Eng. 2020, 87, 106793. [Google Scholar] [CrossRef]
- Raja, D.J.S.; Sriranjani, R.; Parvathy, A.; Hemavathi, N. A Review on Distributed Denial of Service Attack in Smart Grid. In Proceedings of the 2022 7th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 22–24 June 2022; pp. 812–819. [Google Scholar]
- Mousavi, S.M.; St-Hilaire, M. Early Detection of DDoS Attacks against SDN Controllers. In Proceedings of the 2015 International Conference on Computing, Networking and Communications (ICNC), Garden Grove, CA, USA, 16–19 February 2015; pp. 77–81. [Google Scholar]
- Aladaileh, M.A.; Anbar, M.; Hintaw, A.J.; Hasbullah, I.H.; Bahashwan, A.A.; Al-Sarawi, S. Renyi Joint Entropy-Based Dynamic Threshold Approach to Detect DDoS Attacks against SDN Controller with Various Traffic Rates. Appl. Sci. 2022, 12, 6127. [Google Scholar] [CrossRef]
- David, J.; Thomas, C. Efficient DDoS Flood Attack Detection Using Dynamic Thresholding on Flow-Based Network Traffic. Comput. Secur. 2019, 82, 284–295. [Google Scholar] [CrossRef]
- Tsobdjou, L.D.; Pierre, S.; Quintero, A. An Online Entropy-Based DDoS Flooding Attack Detection System With Dynamic Threshold. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1679–1689. [Google Scholar] [CrossRef]
- Baskar, M.; Ramkumar, J.; Karthikeyan, C.; Anbarasu, V.; Balaji, A.; Arulananth, T.S. Low Rate DDoS Mitigation Using Real-Time Multi Threshold Traffic Monitoring System. J. Ambient Intell. Humaniz. Comput. 2021, 1–9. [Google Scholar] [CrossRef]
- Amma, N.G.B.; Selvakumar, S.; Velusamy, R.L. A Statistical Approach for Detection of Denial of Service Attacks in Computer Networks. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2511–2522. [Google Scholar] [CrossRef]
- Qu, X.; Yang, L.; Guo, K.; Ma, L.; Feng, T.; Ren, S.; Sun, M. Statistics-Enhanced Direct Batch Growth Self-Organizing Mapping for Efficient DoS Attack Detection. IEEE Access 2019, 7, 78434–78441. [Google Scholar] [CrossRef]
- Bouyeddou, B.; Kadri, B.; Harrou, F.; Sun, Y. DDOS-Attacks Detection Using an Efficient Measurement-Based Statistical Mechanism. Eng. Sci. Technol. Int. J. 2020, 23, 870–878. [Google Scholar] [CrossRef]
- Mishra, S.K.; Sahoo, B.; Parida, P.P. Load Balancing in Cloud Computing: A Big Picture. J. King Saud Univ.—Comput. Inf. Sci. 2020, 32, 149–158. [Google Scholar] [CrossRef]
- Priya, V.; Sathiya Kumar, C.; Kannan, R. Resource Scheduling Algorithm with Load Balancing for Cloud Service Provisioning. Appl. Soft Comput. 2019, 76, 416–424. [Google Scholar] [CrossRef]
- Powroźnik, P.; Szcześniak, P.; Piotrowski, K. Elastic Energy Management Algorithm Using IoT Technology for Devices with Smart Appliance Functionality for Applications in Smart-Grid. Energies 2021, 15, 109. [Google Scholar] [CrossRef]
- Powroźnik, P.; Szcześniak, P.; Turchan, K.; Krysik, M.; Koropiecki, I.; Piotrowski, K. An Elastic Energy Management Algorithm in a Hierarchical Control System with Distributed Control Devices. Energies 2022, 15, 4750. [Google Scholar] [CrossRef]
- Chen, Y.; Tan, Y.; Deka, D. Is Machine Learning in Power Systems Vulnerable? In Proceedings of the 2018 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aalborg, Denmark, 29–31 October 2018.
- Anthi, E.; Williams, L.; Rhode, M.; Burnap, P.; Wedgbury, A. Adversarial Attacks on Machine Learning Cybersecurity Defences in Industrial Control Systems. J. Inf. Secur. Appl. 2021, 58, 102717. [Google Scholar] [CrossRef]
- Adiban, M.; Safari, A.; Salvi, G. STEP-GAN: A One-Class Anomaly Detection Model with Applications to Power System Security. In Proceedings of the ICASSP 2021—2021 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Toronto, ON, Canada, 6 June 2021; pp. 2605–2609. [Google Scholar]
- Liu, Z.; Wang, Q.; Ye, Y.; Tang, Y. A GAN-Based Data Injection Attack Method on Data-Driven Strategies in Power Systems. IEEE Trans. Smart Grid 2022, 13, 3203–3213. [Google Scholar] [CrossRef]
- Mohammadpourfard, M.; Ghanaatpishe, F.; Mohammadi, M.; Lakshminarayana, S.; Pechenizkiy, M. Generation of False Data Injection Attacks Using Conditional Generative Adversarial Networks. In Proceedings of the 2020 IEEE PES Innovative Smart Grid Technologies Europe (ISGT-Europe), The Hague, The Netherlands, 26–28 October 2020; pp. 41–45. [Google Scholar]
- Wu, Y.; Wang, Q.; Guo, N.; Tian, Y.; Li, F.; Su, X. Efficient Multi-Source Self-Attention Data Fusion for FDIA Detection in Smart Grid. Symmetry 2023, 15, 1019. [Google Scholar] [CrossRef]
- Ganjkhani, M.; Gholami, A.; Giraldo, J.; Srivastava, A.K.; Parvania, M. Multi-Source Data Aggregation and Real-Time Anomaly Classification and Localization in Power Distribution Systems. IEEE Trans. Smart Grid 2024, 15, 2191–2202. [Google Scholar] [CrossRef]
- Cheng, G.; Lin, Y.; Abur, A.; Gómez-Expósito, A.; Wu, W. A Survey of Power System State Estimation Using Multiple Data Sources: PMUs, SCADA, AMI, and Beyond. IEEE Trans. Smart Grid 2024, 15, 1129–1151. [Google Scholar] [CrossRef]
- Mehedi, S.T.; Anwar, A.; Rahman, Z.; Ahmed, K.; Islam, R. Dependable Intrusion Detection System for IoT: A Deep Transfer Learning Based Approach. IEEE Trans. Ind. Inf. 2023, 19, 1006–1017. [Google Scholar] [CrossRef]
- Himeur, Y.; Elnour, M.; Fadli, F.; Meskin, N.; Petri, I.; Rezgui, Y.; Bensaali, F.; Amira, A. Next-Generation Energy Systems for Sustainable Smart Cities: Roles of Transfer Learning. Sustain. Cities Soc. 2022, 85, 104059. [Google Scholar] [CrossRef]
- Xu, M.; Li, X.; Wang, Y.; Luo, B.; Guo, J. Privacy-preserving Multisource Transfer Learning in Intrusion Detection System. Trans. Emerg. Telecommun. Technol. 2021, 32, e3957. [Google Scholar] [CrossRef]
- Liu, Z.; Wang, Q.; Tang, Y. Design of a Cosimulation Platform With Hardware-in-the-Loop for Cyber-Attacks on Cyber-Physical Power Systems. IEEE Access 2020, 8, 95997–96005. [Google Scholar] [CrossRef]
- Sahu, A.; Wlazlo, P.; Mao, Z.; Huang, H.; Goulart, A.; Davis, K.; Zonouz, S. Design and Evaluation of a Cyber-Physical Testbed for Improving Attack Resilience of Power Systems. IET Cyber-Phys. Syst. Theory Appl. 2021, 6, 208–227. [Google Scholar] [CrossRef]
- Makhdoom, I.; Zhou, I.; Abolhasan, M.; Lipman, J.; Ni, W. PrivySharing: A Blockchain-Based Framework for Privacy-Preserving and Secure Data Sharing in Smart Cities. Comput. Secur. 2020, 88, 101653. [Google Scholar] [CrossRef]
- Yang, Q.; Wang, H.; Wang, T.; Zhang, S.; Wu, X.; Wang, H. Blockchain-Based Decentralized Energy Management Platform for Residential Distributed Energy Resources in a Virtual Power Plant. Appl. Energy 2021, 294, 117026. [Google Scholar] [CrossRef]
- Li, J.; Herdem, M.S.; Nathwani, J.; Wen, J.Z. Methods and Applications for Artificial Intelligence, Big Data, Internet of Things, and Blockchain in Smart Energy Management. Energy AI 2023, 11, 100208. [Google Scholar] [CrossRef]
- Iqbal, R.; Doctor, F.; More, B.; Mahmud, S.; Yousuf, U. Big Data Analytics: Computational Intelligence Techniques and Application Areas. Technol. Forecast. Soc. Chang. 2020, 153, 119253. [Google Scholar] [CrossRef]
- AL-Jumaili, A.H.A.; Muniyandi, R.C.; Hasan, M.K.; Paw, J.K.S.; Singh, M.J. Big Data Analytics Using Cloud Computing Based Frameworks for Power Management Systems: Status, Constraints, and Future Recommendations. Sensors 2023, 23, 2952. [Google Scholar] [CrossRef] [PubMed]
- Wu, H.; Zhang, Z.; Guan, C.; Wolter, K.; Xu, M. Collaborate Edge and Cloud Computing With Distributed Deep Learning for Smart City Internet of Things. IEEE Internet Things J. 2020, 7, 8099–8110. [Google Scholar] [CrossRef]
- Zhao, S.; Li, F.; Li, H.; Lu, R.; Ren, S.; Bao, H.; Lin, J.-H.; Han, S. Smart and Practical Privacy-Preserving Data Aggregation for Fog-Based Smart Grids. IEEE Trans. Inf. Forensics Secur. 2021, 16, 521–536. [Google Scholar] [CrossRef]
- Zhu, T.; Ye, D.; Wang, W.; Zhou, W.; Yu, P.S. More Than Privacy: Applying Differential Privacy in Key Areas of Artificial Intelligence. IEEE Trans. Knowl. Data Eng. 2022, 34, 2824–2843. [Google Scholar] [CrossRef]
- Yang, P.; Xiong, N.; Ren, J. Data Security and Privacy Protection for Cloud Storage: A Survey. IEEE Access 2020, 8, 131723–131740. [Google Scholar] [CrossRef]
- Syed, D.; Zainab, A.; Ghrayeb, A.; Refaat, S.S.; Abu-Rub, H.; Bouhali, O. Smart Grid Big Data Analytics: Survey of Technologies, Techniques, and Applications. IEEE Access 2021, 9, 59564–59585. [Google Scholar] [CrossRef]
- Muhtadi, A.; Pandit, D.; Nguyen, N.; Mitra, J. Distributed Energy Resources Based Microgrid: Review of Architecture, Control, and Reliability. IEEE Trans. Ind. Appl. 2021, 57, 2223–2235. [Google Scholar] [CrossRef]
- Wu, Y.; Wu, Y.; Guerrero, J.M.; Vasquez, J.C. Digitalization and Decentralization Driving Transactive Energy Internet: Key Technologies and Infrastructures. Int. J. Electr. Power Energy Syst. 2021, 126, 106593. [Google Scholar] [CrossRef]
- Arif, A.; Alghamdi, T.A.; Khan, Z.A.; Javaid, N. Towards Efficient Energy Utilization Using Big Data Analytics in Smart Cities for Electricity Theft Detection. Big Data Res. 2022, 27, 100285. [Google Scholar] [CrossRef]
- Nikam, V.; Kalkhambkar, V. A Review on Control Strategies for Microgrids with Distributed Energy Resources, Energy Storage Systems, and Electric Vehicles. Int. Trans. Electr. Energy Syst. 2021, 31. [Google Scholar] [CrossRef]
- Kaur, M.; Munjal, A. Data Aggregation Algorithms for Wireless Sensor Network: A Review. Ad Hoc Netw. 2020, 100, 102083. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential Privacy Techniques for Cyber Physical Systems: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 746–789. [Google Scholar] [CrossRef]
- Murthy, S.; Abu Bakar, A.; Abdul Rahim, F.; Ramli, R. A Comparative Study of Data Anonymization Techniques. In Proceedings of the 2019 IEEE 5th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing, (HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS), Washington, DC, USA, 27–29 May 2019; pp. 306–309. [Google Scholar]
- Zhou, Y.; Chen, X.; Chen, M. Privacy-Preserving Multidimensional Data Aggregation Scheme for Smart Grid. Secur. Commun. Netw. 2020, 2020, 8845959. [Google Scholar] [CrossRef]
- Triantafyllou, A.; Jimenez, J.A.P.; Torres, A.D.R.; Lagkas, T.; Rantos, K.; Sarigiannidis, P. The Challenges of Privacy and Access Control as Key Perspectives for the Future Electric Smart Grid. IEEE Open J. Commun. Soc. 2020, 1, 1934–1960. [Google Scholar] [CrossRef]
- Jiang, C.; Fan, T.; Gao, H.; Shi, W.; Liu, L.; Cérin, C.; Wan, J. Energy Aware Edge Computing: A Survey. Comput. Commun. 2020, 151, 556–580. [Google Scholar] [CrossRef]
- Jithish, J.; Alangot, B.; Mahalingam, N.; Yeo, K.S. Distributed Anomaly Detection in Smart Grids: A Federated Learning-Based Approach. IEEE Access 2023, 11, 7157–7179. [Google Scholar] [CrossRef]
- Liu, J.; Tian, Y.; Zhou, Y.; Xiao, Y.; Ansari, N. Privacy Preserving Distributed Data Mining Based on Secure Multi-Party Computation. Comput. Commun. 2020, 153, 208–216. [Google Scholar] [CrossRef]

| Author | Method | Advantages | Disadvantages |
|---|---|---|---|
| Chen et al. [41] | Multi-level static estimation | Fast state estimation | Difficulty in selecting different interface quantities between subsystems |
| Qu et al. [43] | Trust worthiness WLS algorithm | Improving the robustness of state estimation | Additional computational burden and potential false positives |
| Khalid et al. [44] | Median Regression Function | Comprehensively consider various factors that affect state estimation | Difficult to respond quickly |
| Tang et al. [45] | Generalized Likelihood Ratio Test (GLRT) Detector | Can flexibly adapt to different data distributions and model assumptions | Inaccurate estimates for small samples |
| Author | Method | Advantages | Disadvantages |
|---|---|---|---|
| Dayananda et al. [50] | Reconfigurable Kalman Filter | Flexible and adaptable to dynamic environments | Sensitivity of threshold selection |
| Wang et al. [51] | KFRNN | Able to handle complex attack scenarios | New attack detection not applicable |
| Luo et al. [52] | Adaptive Kalman Filter Library | Reduced latency and no prior knowledge required | Adaptive threshold parameter adjustment is difficult |
| Rashed et al. [53] | Cluster partition state estimation technology | Dynamic and static combined state estimation method | Lack of anti-attack ability |
| Živković et al. [54] | UKF-WLS | Quickly identify fake data attacks | Differences between noise impact estimates |
| Lu et al. [55] | Improved Unscented Kalman Filter | Improve state estimation accuracy and robustness | Limited forecast accuracy |
| Author | Method | Advantages | Disadvantages |
|---|---|---|---|
| Moradi et al. [79] | Clock comparison PTP attack detection | Detects multiple types of PTP attacks | Affected by third-party time sources and GPS signals |
| Moussa et al. [80] | Extending PTP to detect time synchronization attacks | Enhance the security of the PTP protocol and reduce the attack surface | The UPPAAL model checker has limited portability and applicability |
| Alghamdi et al. [81] | Trusted Supervisor Node (TSN) approach | TSN can detect abnormal patterns that point to attacks, improving detection accuracy | Inability to detect external or advanced attacks |
| Qiu et al. [82] | Secure Time Synchronization Protocol | Reduce the impact of malicious nodes on the network | Protocol compatibility issues need to be considered |
| Wu et al. [83] | Distributed timestamp mechanism | Continuously verifiable to enhance the credibility of timestamps | High deployment complexity |
| Moussa et al. [84] | Simple Network Management Protocol (SNMP) | Easy to use and cost effective | Difficult to apply to large-scale networks |
| He et al. [85] | Polarization Coded Synchronization Security Strategy | Polar encoding can encrypt timestamps | High network overhead |
| Hymlin et al. [86] | Clustering-based timestamp mechanism | Dynamic clustering adapts to network changes | Unable to respond to new types of attacks |
| Author | Method | Advantages | Disadvantages |
|---|---|---|---|
| Wang et al. [87] | MAC | Reduced additional delay | Difficulty in key distribution |
| Ateniese et al. [88] | RSA | Simple key management | The key length requirement is high |
| Shen et al. [89] | BLS | Scalability | Undo is not supported |
| Erway et al. [90] | Dynamic Operation | Simplify data management | Data availability risks |
| Liu et al. [91] | Multiple copies | Has a certain ability to resist attacks | Synchronization delay |
| Jayaraman et al. [92] | privacy protection | Emphasis on anonymity | Difficulty balancing privacy protection and data utility |
| Wang et al. [94] | TPA dynamic data integrity verification | Improve the efficiency of the verification process | There is a risk of third-party auditors |
| Ge et al. [95] | Dynamic search of symmetric keys | Able to meet the needs of frequent data changes | Increase system resource consumption |
| Liu et al. [96] | VDERS | Meets the need for data sorting and searching | Not applicable when dealing with large-scale datasets |
| Fu et al. [97] | DIPOR | Improved data availability and integrity | Not applicable when dealing with large-scale datasets |
| Author | Method | Advantages | Disadvantages |
|---|---|---|---|
| Mousavi et al. [111] | Fixed Threshold | Easy to use | General limitations |
| Aladaileh et al. [112] | Dynamic threshold based on the combined entropy of benevolence and righteousness | Dynamic adaptability | Unable to respond to new types of attacks |
| David et al. [113] | Traffic characteristics + dynamic threshold | Lower false positive rate | Threshold adjustment strategies require careful consideration |
| Tsobdjou et al. [114] | Dynamic Threshold of Online Entropy | Reduce false positives and false negatives | Entropy instability |
| Baskar et al. [115] | Multi-threshold traffic analysis | High detection rate | Unable to respond to new types of attacks |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chang, Z.; Wu, J.; Liang, H.; Wang, Y.; Wang, Y.; Xiong, X. A Review of Power System False Data Attack Detection Technology Based on Big Data. Information 2024, 15, 439. https://doi.org/10.3390/info15080439
Chang Z, Wu J, Liang H, Wang Y, Wang Y, Xiong X. A Review of Power System False Data Attack Detection Technology Based on Big Data. Information. 2024; 15(8):439. https://doi.org/10.3390/info15080439
Chicago/Turabian StyleChang, Zhengwei, Jie Wu, Huihui Liang, Yong Wang, Yanfeng Wang, and Xingzhong Xiong. 2024. "A Review of Power System False Data Attack Detection Technology Based on Big Data" Information 15, no. 8: 439. https://doi.org/10.3390/info15080439
APA StyleChang, Z., Wu, J., Liang, H., Wang, Y., Wang, Y., & Xiong, X. (2024). A Review of Power System False Data Attack Detection Technology Based on Big Data. Information, 15(8), 439. https://doi.org/10.3390/info15080439





