A Novel Authentication and Communication Protocol for Urban Traffic Monitoring in VANETs Based on Cluster Management
Abstract
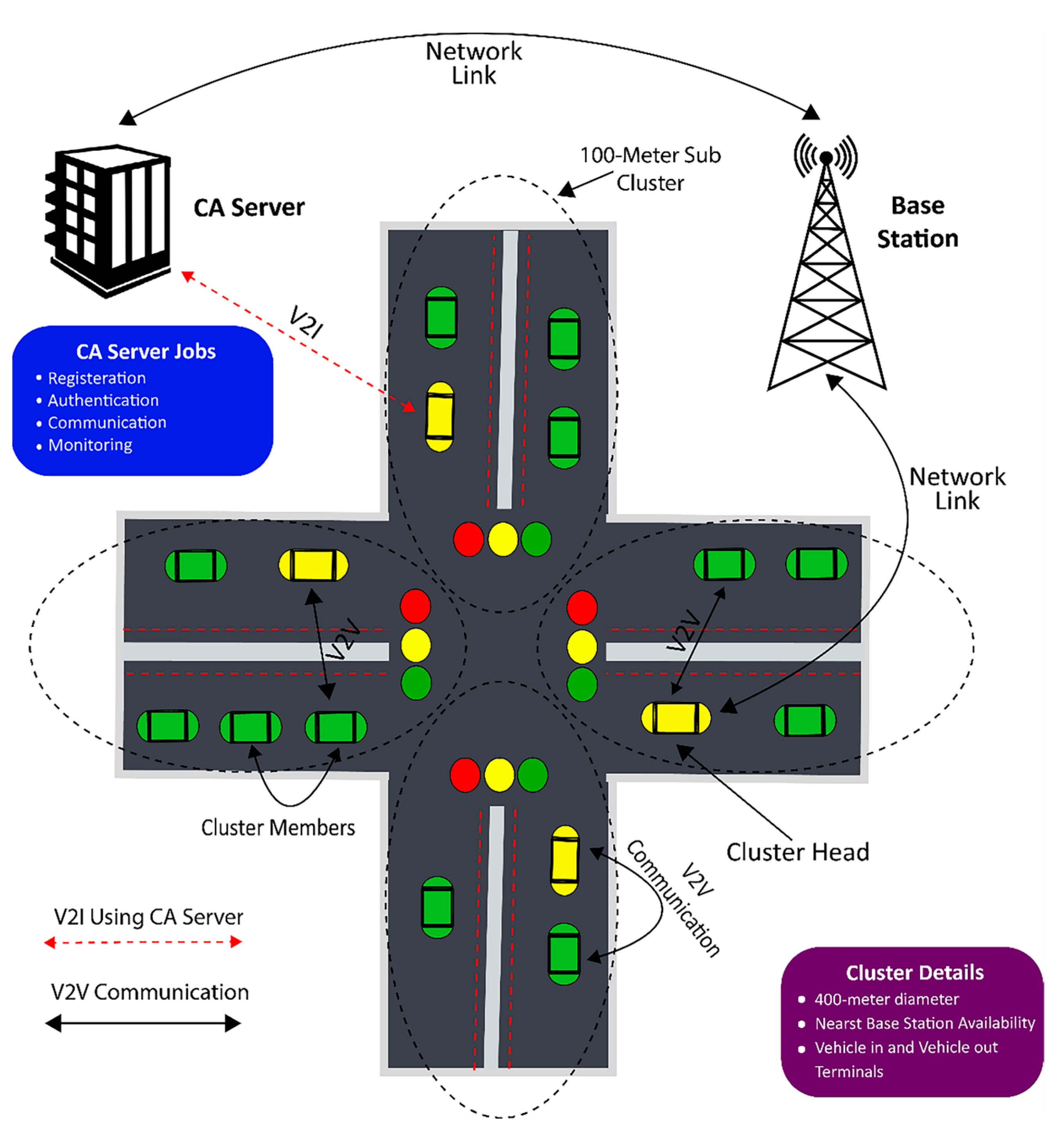
:1. Introduction
- Authentication and registration using third-party certification authority.
- V2I and V2I Communication Channel.
- Graph-Based Resource Sharing in Vehicular Communication.
2. Literature Review
- We introduce a secure authentication mechanism that relies on a trusted third-party certification authority. It ensures the integrity and authenticity of vehicles and infrastructure units participating in the communication network. By leveraging this mechanism, we enhance the overall security of V2I and V2V communications.
- Our protocols establish reliable and secure communication channels for V2I and V2V interactions. They enable efficient and seamless communication between vehicles and infrastructure units, facilitating the exchange of critical data and messages.
- We propose a novel resource-sharing approach based on graph theory principles. By modeling the VANET as a graph, we optimize the allocation of resources, such as bandwidth and power, among vehicles and infrastructure units. This ensures fair and efficient resource utilization, enhancing the overall performance of the communication network.
- By addressing these essential aspects, our research advances the security, reliability, and efficiency of V2I and V2V communications in vehicular networks. The proposed protocols and resource-sharing mechanism pave the way for more robust and secure communication systems, fostering the development and deployment of intelligent transportation solutions.
3. Methodology
3.1. Explanation of Notations
- The range of in varies from 1 to , i.e., , but in other notations, it varies from to i.e.,
- MD5-based secure hash function 128-bit hash value ranges from
- such that presents a set of random numbers generated using the LCG algorithm
- Linear congruential generators can be defined through recurrence relation as:
- will generate a six-digit code.
- is generated using the Fisher–Yates shuffle algorithm. Here is the pseudo representation of this algorithm:
- ○
- function fisherYatesShuffle(array)
- ○
- = length(array)
- ○
- for i from down to 1 do
- ○
- = random integer between 0 and (inclusive)
- ○
- swap and
- ○
- return array
- Explanation of Fisher–Yates Shuffle Algorithm:
- The fisherYatesShuffle function takes an array as input and returns the shuffled array.
- It initializes the variable n with the length of the array.
- The algorithm starts a loop from down to 1. This loop iterates over the elements of the array in reverse order.
- A random integer is generated inside the loop between 0 and (inclusive), where is the current iteration index.
- The elements at indices and are swapped using a temporary variable.
- After the loop completes, the shuffled array is returned.
- and are two extractor functions that extract latitude and longitude from the input location.
- contains message templates. These messages might contain the following commands:
- ○
- Please give me the way. I am on your back!
- ○
- Speed up!
- ○
- Danger ahead!
- ○
- Traffic is jammed on the road. Please adopt an alternative way.
- ○
- I run short of fuel. Please help!
- ○
- I need a mechanic.
- ○
- The tire is punctured.
- ○
- There is an accident on the road near my location.
- ○
- There is a crowd protesting on the way.
- ○
- Please give way to the ambulance!
- ○
- Stop on the way. There is a check post.
- ○
- The weather condition is bad.
- contains three values, including 0, 1, and 2. (0) means the priority of this message is nothing. It might be an informative message. 1 means normal priority, while 2 means a very high priority.
3.2. Motivations and Deployment Considerations
3.2.1. Third-Party CA for Traffic Monitoring
3.2.2. Separate Authentication Communication Scheme
3.2.3. Influence of Capacity and Speed on Network Signaling Overhead
3.2.4. Cluster Management
4. Proposed Protocol
4.1. Registration Phase
- E-mail;
- Password;
- Vehicle Registration Number.
4.2. Authentication Phase
4.3. V2I Communication
4.4. V2V Communication
4.5. Vehicle Clustering and Monitoring
4.6. Cluster Head Selection Algorithm
- Each vehicle inside a cluster announces itself as a “Cluster Head“ and displays the broadcast signal:
- Every vehicle displays the list of closest vehicles () after getting from
- is estimated by
- The weighted sum is calculated by
- The vehicle calculates the above equation’s arguments, and the range of weighted constants varies from 0 to 1. Since the weighted sum is derived from these arguments, the Cluster Head based on this sum will be the most efficient and trustworthy.
- In the end, the with the lowest is selected as the Cluster Head.
- Pseudo code for the Cluster Head Selection Algorithm:
- function select cluster head (clusterVehicles)
- lowest weight = infinity
- selected cluster head = null
- for each vehicle in clusterVehicles do
- = get Closest Vehicles List ()
- weighted sum = calculate Weighted Sum (, )
- if weighted sum < lowest weight then
- lowest weight = weighted sum
- selected cluster head =
- return selected cluster head
- Explanation:
- The select cluster head function takes the list of vehicles within the cluster as input and returns the selected cluster head.
- It initializes the lowest Weight variable with a high value (infinity) and sets the selected Cluster Head to null.
- For each vehicle in the clusterVehicles list, the algorithm retrieves the list of closest vehicles using the get Closest Vehicles List function.
- The weighted sum is calculated using the arguments (the current vehicle) and (the closest vehicles list).
- If the calculated weighted sum is lower than the current lowest Weight, the lowest Weight is updated, and the corresponding vehicle is selected as the potential cluster head.
- After processing all vehicles, the algorithm returns the selected cluster head with the lowest weighted sum.
5. Simulation Setup and Experiments
5.1. Varying the Attackers
5.2. Transmission Range
5.3. Baseline Graph-Based Resource Allocation
| Algorithm 1: Baseline Graph-Based Resource Allocation Algorithm |
| 1. Arbitrarily allocate one V2V link to every cluster from C clusters (C1, …… Cn). 2. for m = 1 to M do 3. for n = 1 to N do 4. for f = 1 to F do 5. Compute the V2I optimal transmit power using the algorithms provided by [66]. 6. Compute the V2V optimal transmit power using the algorithms provided by [66]. 7. Compute the V2I and V2V power gain capacity from the base station resource blocks with the optimized power control parameters. 8. end for 9. end for 10. end for 11. Construct a tripartite graph where M represents V2I links and N represents V2V links. 12. Return the power allocation using resource blocks. |
- Initialization: Assign an arbitrary V2V link to each cluster based on predefined criteria or randomly.
- Graph Construction: Create a graph representation where each cluster is represented as a node, and the V2V links between clusters are represented as edges. This graph captures the connectivity and relationships between clusters.
- Resource Evaluation: Evaluate the resources available within each cluster and the requirements of the V2V communication links. This assessment may include available bandwidth, signal strength, channel conditions, and quality-of-service (QoS) metrics.
- Resource Allocation: Utilize graph-based algorithms to allocate resources based on connectivity and performance requirements. Various graph algorithms, such as minimum spanning tree, shortest path, or maximum flow algorithms, can be employed to optimize resource allocation.
- Optimization: Continuously evaluate and optimize the resource allocation based on dynamic changes in the network, such as variations in vehicle density, traffic conditions, or communication demands. This ensures adaptability and efficient resource utilization in real-time scenarios.
5.4. Greedy Resource Allocation
| Algorithm 2: Greedy Resource Allocation Algorithm |
| 1. Obtain V2V and V2I clustering results from the baseline graph-based resource allocation algorithm. 2. Repeat the process. for k = 1 to K do Initialize all zero vectors of length N. for n = 1 to N do If the kth V2V is not only in its current cluster C, then set Ck = n end if end for end for Return the power allocation using resource blocks. |
- Initialization: Begin with an initial set of available resources and an open allocation plan.
- Vehicle Selection: Select a vehicle from the pool of vehicles requiring resource allocation.
- Resource Evaluation: Evaluate the available resources and the requirements of the selected vehicle. This evaluation may include available bandwidth, signal quality, channel conditions, proximity to other vehicles, and communication demands.
- Resource Allocation: Allocate the resources to the selected vehicle based on the evaluation. The allocation decision is made greedily, considering the local optimization criteria. For example, the algorithm may prioritize allocating resources to vehicles with higher communication demands or vehicles experiencing poor signal quality.
- Update Resource Pool: Update the pool of available resources by subtracting the allocated resources from the total available resources.
- Repeat Steps 2–5: Repeat the vehicle selection process, resource evaluation, allocation, and resource pool update for the remaining vehicles until all vehicles have been allocated resources.
5.5. V2I and V2V Communications
6. Conclusions
7. Future Recommendations
- As security and privacy concerns remain critical in VANETs, future work should focus on developing advanced encryption and cryptographic techniques to safeguard sensitive information and prevent unauthorized access. Additionally, privacy-preserving mechanisms, such as secure data aggregation and anonymization, should be explored to protect the privacy of vehicle and driver identities.
- Conducting real-world deployments and field testing of the proposed protocol will provide valuable insights into its practical feasibility and effectiveness. Evaluating the protocol’s performance under various traffic scenarios, road conditions, and network densities will help identify potential limitations and areas for further improvement.
- In order to achieve uninterrupted communication and practical cooperation between diverse vehicles and infrastructure systems, it is imperative to establish interoperability standards. These standards will promote compatibility and collaboration among various Vehicular AdHoc Networks (VANETs), facilitating enhanced traffic management and safer interactions between vehicles and infrastructure components.
- Energy Efficiency Considerations: Energy efficiency is crucial to VANETs, as vehicles operate on limited power resources. Future research should explore energy-aware strategies and mechanisms to optimize power consumption, prolong the network’s lifetime, and reduce the carbon footprint associated with vehicular communication.
- As urban areas continue to expand, the scalability and robustness of the proposed protocol need to be thoroughly investigated. Future work should address the challenges of large-scale VANET deployments, including managing a vast number of vehicles, efficient cluster formation, and effective communication in highly dynamic environments.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Jithendra, H.; Rekha, D. Secured Trusted Authentication with Trust-Based Congestion Scheme for V2V Communication; Chapman and Hall/CRC: Boca Raton, FL, USA, 2022; pp. 157–168. [Google Scholar]
- Panigrahy, S.K.; Emany, H. A survey and tutorial on network optimization for intelligent transport system using the internet of vehicles. Sensors 2023, 23, 555. [Google Scholar] [CrossRef] [PubMed]
- Cui, J.; Wei, L.; Zhong, H.; Zhang, J.; Xu, Y.; Liu, L. Edge computing in VANETs-an efficient and privacy-preserving cooperative downloading scheme. IEEE J. Sel. Areas Commun. 2020, 38, 1191–1204. [Google Scholar] [CrossRef]
- Hamzah, M.; Islam, M.M.; Hassan, S.; Akhtar, M.N.; Ferdous, M.J.; Jasser, M.B.; Mohamed, A.W. Distributed Control of Cyber Physical System on Various Domains: A Critical Review. Systems 2023, 11, 208. [Google Scholar] [CrossRef]
- Goyal, A.K.; Agarwal, G.; Tripathi, A.K.; Sharma, G. Systematic Study of VANET: Applications, Challenges, Threats, Attacks, Schemes and Issues in Research. In Green Computing in Network Security; CRC Press: Boca Raton, FL, USA, 2022; pp. 33–52. [Google Scholar]
- Singh, M.; Kumar, C.; Nath, P. P2P Applications in 4G/5G Networks Using D2D Communication Based on Social Attributes of Users. In Proceedings of the Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 730–738. [Google Scholar]
- Hamdi, M.M.; Audah, L.; Rashid, S.A.; Mohammed, A.H.; Alani, S.; Mustafa, A.S. A review of applications, characteristics and challenges in vehicular ad hoc networks (VANETs). In Proceedings of the International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 26–28 June 2020; pp. 1–7. [Google Scholar]
- Hsieh, F.-S. Improving Acceptability of Cost Savings Allocation in Ridesharing Systems Based on Analysis of Proportional Methods. Systems 2023, 11, 187. [Google Scholar] [CrossRef]
- Shen, X.; Lu, Y.; Zhang, Y.; Liu, X.; Zhang, L. An Innovative Data Integrity Verification Scheme in the Internet of Things assisted information exchange in transportation systems. Clust. Comput. 2022, 25, 1791–1803. [Google Scholar] [CrossRef]
- Sharma, S.K.; Rao, R.S.; Singh, P.; Khan, S.A. Evaluation of VANETs routing protocols for data-based smart health monitoring in intelligent transportation systems. Int. J. Math. Eng. Manag. Sci. 2022, 7, 211. [Google Scholar] [CrossRef]
- Gao, Z.; Xu, X.; Hu, Y.; Wang, H.; Zhou, C.; Zhang, H. Based on Improved NSGA-II Algorithm for Solving Time-Dependent Green Vehicle Routing Problem of Urban Waste Removal with the Consideration of Traffic Congestion: A Case Study in China. Systems 2023, 11, 173. [Google Scholar] [CrossRef]
- Lim, K.; Tuladhar, K.M.; Kim, H. Detecting location spoofing using ADAS sensors in VANETs. In Proceedings of the 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–4. [Google Scholar]
- Ku, I.; Lu, Y.; Gerla, M.; Gomes, R.L.; Ongaro, F.; Cerqueira, E. Towards software-defined VANET: Architecture and services. In Proceedings of the 13th Annual Mediterranean ad Hoc Networking Workshop (MED-HOC-NET), Piran, Slovenia, 2–4 June 2014; pp. 103–110. [Google Scholar]
- Open Connectivity Foundation. Unlocking the Massive Opportunity in the Internet of Things. Available online: https://openconnectivity.org/technology/iotivity/ (accessed on 25 January 2023).
- Yang, L.; Li, H. Vehicle-to-vehicle communication based on a peer-to-peer network with graph theory and consensus algorithm. IET Intell. Transp. Syst. 2018, 13, 280–285. [Google Scholar] [CrossRef]
- Appiahene, P.; Serwah, S.; Mensah, C.; Kesse-Yaw, B. Application of Wireless Ad-Hoc Networks Model to provide Education to rural Communities in Ghana. In Proceedings of the International Conference on Applied Science and Technology Conference Proceedings, Bali, Indonesia, 24–25 October 2019; pp. 114–121. [Google Scholar]
- Bossauer, P.; Neifer, T.; Stevens, G.; Pakusch, C. Trust versus Privacy: Using Connected Car Data in Peer-to-Peer Carsharing. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 25–30 April 2020; pp. 1–13. [Google Scholar]
- Shah, S.A.A.; Ahmed, E.; Imran, M.; Zeadally, S. 5G for vehicular communications. IEEE Commun. Mag. 2018, 56, 111–117. [Google Scholar] [CrossRef]
- Meneguette, R.I.; Boukerche, A. Peer-to-peer protocol for allocated resources in vehicular cloud based on V2V communication. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Singh, P.K.; Nandi, S.K.; Nandi, S. A tutorial survey on vehicular communication state of the art, and future research directions. Veh. Commun. 2019, 18, 100164. [Google Scholar] [CrossRef]
- Hussein, A.; Elhajj, I.H.; Chehab, A.; Kayssi, A. SDN VANETs in 5G: An architecture for resilient security services. In Proceedings of the Fourth International Conference on Software Defined Systems (SDS), Valencia, Spain, 8–11 May 2017; pp. 67–74. [Google Scholar]
- Balamurugan, M.; Anand, M.S.; Kumar, D.S.; Devi, A.S. Anonymous Location-Support and Self-Reliance Routing Protocol For Manet. Indian J. Public Health Res. Dev. 2018, 9, 323–326. [Google Scholar] [CrossRef]
- Edge, S.W.; Cheng, H.; Zisimopoulos, H. Systems and Methods for 5G Location Support Using Service Based Interfaces. U.S. Patent 11,128,985, 21 September 2022. [Google Scholar]
- Salem, F.M.; Ali, A.S. SOS: Self-organized secure framework for VANET. Int. J. Commun. Syst. 2020, 33, e4317. [Google Scholar] [CrossRef]
- Takashi, T.; Takumi, M.; Taku, Y.; Olivier, F. Performance Evaluation of Multi-Hop Communication on Inter-vehicular P2P Network. IEICE Tech. Rep. 2020, 119, 135–140. [Google Scholar]
- Zhang, R.; Lu, Y.; Liu, B. Pricing Decisions and Game Analysis on Advanced Delivery and Cross-Channel Return in a Dual-Channel Supply Chain System. Systems 2023, 11, 155. [Google Scholar] [CrossRef]
- Mondal, A.; Mitra, S. Security Issues in Vehicular Ad Hoc Networks for Evolution Towards Internet of Vehicles; Springer: Berlin/Heidelberg, Germany, 2020; pp. 253–307. [Google Scholar]
- Zhong, S.; Zhong, H.; Huang, X.; Yang, P.; Shi, J.; Xie, L.; Wang, K. Connecting Things to Things in Physical-World: Security and Privacy Issues in Vehicular Ad-Hoc Networks; Springer: Berlin/Heidelberg, Germany, 2019; pp. 101–134. [Google Scholar]
- Stepień, K.; Poniszewska-Marańda, A. Towards the security measures of the vehicular ad-hoc networks. In Proceedings of the International Conference on Internet of Vehicles, Paris, France, 20–22 November 2018; pp. 233–248. [Google Scholar]
- Ayaz, S.B.; Tian, H.; Gao, S.; Fisher, D.L. Proactive route choice with real-time information: Learning and effects of network complexity and cognitive load. Transp. Res. Part C Emerg. Technol. 2023, 149, 104035. [Google Scholar] [CrossRef]
- Zhang, K.; Leng, S.; Peng, X.; Pan, L.; Maharjan, S.; Zhang, Y. Artificial intelligence inspired transmission scheduling in cognitive vehicular communications and networks. IEEE Internet Things J. 2018, 6, 1987–1997. [Google Scholar] [CrossRef]
- Liang, L.; Li, G.Y.; Xu, W. Resource allocation for D2D-enabled vehicular communications. IEEE Trans. Commun. 2017, 65, 3186–3197. [Google Scholar] [CrossRef]
- Zhang, K.; Mao, Y.; Leng, S.; He, Y.; Zhang, Y. Mobile-edge computing for vehicular networks: A promising network paradigm with predictive off-loading. IEEE Veh. Technol. Mag. 2017, 12, 36–44. [Google Scholar] [CrossRef]
- Burg, A.; Chattopadhyay, A.; Lam, K.-Y. Wireless communication and security issues for cyber–physical systems and the Internet-of-Things. Proc. IEEE 2017, 106, 38–60. [Google Scholar] [CrossRef]
- Al-Kinani, A.; Wang, C.-X.; Zhou, L.; Zhang, W. Optical wireless communication channel measurements and models. IEEE Commun. Surv. Tutor. 2018, 20, 1939–1962. [Google Scholar] [CrossRef]
- Rahman, M.S.; Abdel-Aty, M. Longitudinal safety evaluation of connected vehicles’ platooning on expressways. Accid. Anal. Prev. 2018, 117, 381–391. [Google Scholar] [CrossRef]
- Masini, B.M.; Bazzi, A.; Zanella, A. A survey on the roadmap to mandate on board connectivity and enable V2V-based vehicular sensor networks. Sensors 2018, 18, 2207. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Liang, L.; Peng, H.; Li, G.Y.; Shen, X. Vehicular communications: A physical layer perspective. IEEE Trans. Veh. Technol. 2017, 66, 10647–10659. [Google Scholar] [CrossRef]
- Yan, G.; Rawat, D.B. Vehicle-to-vehicle connectivity analysis for vehicular ad-hoc networks. Ad Hoc Networks 2017, 58, 25–35. [Google Scholar] [CrossRef] [Green Version]
- Liu, G.; Qi, N.; Chen, J.; Dong, C.; Huang, Z. Enhancing clustering stability in VANET: A spectral clustering based approach. China Commun. 2020, 17, 140–151. [Google Scholar] [CrossRef]
- Abdelatif, S.; Derdour, M.; Ghoualmi-Zine, N.; Marzak, B. VANET: A novel service for predicting and disseminating vehicle traffic information. Int. J. Commun. Syst. 2020, 33, e4288. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Yassin, A.A. Vppcs: Vanet-based privacy-preserving communication scheme. IEEE Access 2020, 8, 150914–150928. [Google Scholar] [CrossRef]
- Xiao, H.; Zhang, Q.; Ouyang, S.; Chronopoulos, A.T. Connectivity probability analysis for VANET freeway traffic using a cell transmission model. IEEE Syst. J. 2020, 15, 1815–1824. [Google Scholar] [CrossRef]
- Khatri, S.; Vachhani, H.; Shah, S.; Bhatia, J.; Chaturvedi, M.; Tanwar, S.; Kumar, N. Machine learning models and techniques for VANET based traffic management: Implementation issues and challenges. Peer-to-Peer Netw. Appl. 2021, 14, 1778–1805. [Google Scholar] [CrossRef]
- Alaya, B.; Sellami, L. Clustering method and symmetric/asymmetric cryptography scheme adapted to securing urban VANET networks. J. Inf. Secur. Appl. 2021, 58, 102779. [Google Scholar] [CrossRef]
- Mirsadeghi, F.; Rafsanjani, M.K.; Gupta, B.B. A trust infrastructure based authentication method for clustered vehicular ad hoc networks. Peer-to-Peer Netw. Appl. 2021, 14, 2537–2553. [Google Scholar] [CrossRef]
- Alkhalidy, M.; Al-Serhan, A.F.; Alsarhan, A.; Igried, B. A new scheme for detecting malicious nodes in vehicular ad hoc networks based on monitoring node behavior. Future Internet 2022, 14, 223. [Google Scholar] [CrossRef]
- Bijalwan, A.; Purohit, K.C.; Malik, P.; Mittal, M. A Self-Adaptable Angular Based K-Medoid Clustering Scheme (SAACS) for Dynamic VANETs. Electronics 2022, 11, 3071. [Google Scholar] [CrossRef]
- Ouallane, A.A.; Bakali, A.; Bahnasse, A.; Broumi, S.; Talea, M. Fusion of engineering insights and emerging trends: Intelligent urban traffic management system. Inf. Fusion 2022, 88, 218–248. [Google Scholar] [CrossRef]
- Rajeswari, R.; Rajesh, S. Enhance Security and Privacy in VANET Based Sensor Monitoring and Emergency Services. Cybern. Syst. 2023, 1, 1–22. [Google Scholar] [CrossRef]
- Hireche, S.; Dennai, A.; Kadri, B. Toward a Novel RESTFUL Big Data-Based Urban Traffic Incident Data Web Service for Connected Vehicles. Comput. J. 2023, 1. [Google Scholar] [CrossRef]
- Narayanan, K.L.; Naresh, R. An efficient key validation mechanism with VANET in real-time cloud monitoring metrics to enhance cloud storage and security. Sustain. Energy Technol. Assess. 2023, 56, 102970. [Google Scholar]
- Nazib, R.A.; Moh, S. Routing Protocols for Unmanned Aerial Vehicle-Aided Vehicular Ad Hoc Networks: A Survey. IEEE Access 2020, 8, 77535–77560. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Bashir, F.; Abdullah, A.H. Distance and signal quality aware next hop selection routing protocol for vehicular ad hoc networks. Neural Comput. Appl. 2020, 32, 2351–2364. [Google Scholar] [CrossRef]
- Jaiswal, R.K. Position-based routing protocol using Kalman filter as a prediction module for vehicular ad hoc networks. Comput. Electr. Eng. 2020, 83, 106599. [Google Scholar] [CrossRef]
- Eldin, K.Y.E.; Ahwal, A.A. A Comparative Study On Vehicular Ad-Hoc Networks Topology Based Routing Protocols. Eng. Res. J. 2020, 1, 111–117. [Google Scholar]
- Obaidat, M.; Khodjaeva, M.; Holst, J.; Zid, M.B. Security and Privacy Challenges in Vehicular Ad Hoc Networks; Springer: Berlin/Heidelberg, Germany, 2020; pp. 223–251. [Google Scholar]
- Sugumar, R.; Rengarajan, A.; Jayakumar, C. Trust based authentication technique for cluster based vehicular ad hoc networks (VANET). Wirel. Netw. 2018, 24, 373–382. [Google Scholar] [CrossRef]
- Kolandaisamy, R.; Noor, R.M.; Kolandaisamy, I.; Ahmedy, I.; Kiah, M.L.M.; Tamil, M.E.M.; Nandy, T. A stream position performance analysis model based on DDoS attack detection for cluster-based routing in VANET. J. Ambient. Intell. Humaniz. Comput. 2020, 12, 6599–6612. [Google Scholar] [CrossRef]
- Deshmukh, A.R.; Dhawale, S.A.; Dorle, S. Analysis of Cluster Based Routing Protocol (CBRP) for Vehicular Adhoc Network (VANet) in Real Geographic Scenario. In Proceedings of the IEEE International Conference on Electronics, Computing and Communication Technologies (CONECCT), Bangalore, India, 2–4 July 2020; pp. 1–5. [Google Scholar]
- Yogarayan, S.; Razak, S.F.A.; Azman, A.; Abdullah, M.F.; Ibrahim, S.Z.; Raman, K.J. A Review of Routing Protocols for Vehicular Ad-Hoc Networks (VANETs). In Proceedings of the 8th International Conference on Information and Communication Technology (ICoICT), Yogyakarta, Indonesia, 24–26 June 2020; pp. 1–7. [Google Scholar]
- Srivastava, A.; Prakash, A.; Tripathi, R. Location based routing protocols in VANET: Issues and existing solutions. Veh. Commun. 2020, 23, 100231. [Google Scholar] [CrossRef]
- Ariffin, R.N.R.; Zahari, R.K. Perceptions of the urban walking environments. Procedia-Soc. Behav. Sci. 2013, 105, 589–597. [Google Scholar] [CrossRef] [Green Version]
- Hillnhütter, H. Stimulating urban walking environments–Can we measure the effect? Environ. Plan. B Urban Anal. City Sci. 2022, 49, 275–289. [Google Scholar] [CrossRef]
- dos Santos, P.M.S. Wireless Protocols and Channel Estimation for Data Gathering with Mobile Nodes. Ph.D. Thesis, Universidade do Porto, Porto, Portugal, 2017. [Google Scholar]
- Liang, L.; Xie, S.; Li, G.Y.; Ding, Z.; Yu, X. Graph-based resource sharing in vehicular communication. IEEE Trans. Wirel. Commun. 2018, 17, 4579–4592. [Google Scholar] [CrossRef]







| Keyword | Meanings |
|---|---|
| ITS | Intelligent Transportation System |
| VANETs | Vehicular AdHoc Networks |
| V2V | Vehicle-to-Vehicle |
| V2I | Vehicle-to-Infrastructure |
| V2X | Vehicle-to-Everything |
| RSU | Road Side Units |
| E2E | End-to-End |
| PDR | Packet Delivery Ratio |
| RR | Route Reliability |
| P2P | Peer-to-Peer |
| TRPs | Topological Routing Protocols |
| GRPs | Geographic Routing Protocols |
| 5G | Fifth Generation |
| SDN | Software-Defined Network |
| DDoS | Distributed Denial of Services |
| MANETs | Mobile AdHoc Networks |
| CA | Certification Authority |
| LCG | Linear Congruential Generator |
| FYS | Fisher–Yates Shuffle |
| API | Application Programming Interface |
| OTP | One-Time Password |
| HTTP | Hypertext Transfer Protocol |
| UR | Ultra-Reliability |
| IoT | Internet of Things |
| AI | Artificial Intelligence |
| MD5 | Media-Digest Algorithm for Encryption |
| SUMO | Simulation of Urban Mobility |
| API | Application Program Interface |
| TCP | Transfer Control Protocol |
| Transmission Strategy | Route Formation | Routing Protocols |
|---|---|---|
| Single-hop Broadcasting | Proactive | Beacon-Vector (BV) |
| Global Internet Connectivity for Vehicular AdHoc Networks (GLOVE) | ||
| Position-based Opportunistic Routing (POR) | ||
| Reactive | Intersection-based Routing (IBR) | |
| Traffic-aware Routing for Isolated Nodes (TRAIN) | ||
| Emergency Message Transmission Protocol (EMTP) | ||
| Multi-hop Unicast | Proactive | Distance-Based Clustering (DBC) |
| Clustering Routing Protocol (CRP) | ||
| Dynamic Source Routing (DSR) | ||
| Reactive | AdHoc On-Demand Distance Vector (AODV) | |
| Temporally Ordered Routing Algorithm (TORA) | ||
| Dynamic Destination-Sequenced Distance Vector (DSDV) | ||
| Multi-hop Broadcast | Proactive | Flooding-based Routing (FBR) |
| Geographical and Temporal Routing (GTR) | ||
| Vehicular Opportunistic Routing (VOR) | ||
| Reactive | Broadcast Storm Avoidance Routing (BSA) | |
| Counter-Based Broadcast Scheme (CBS) | ||
| Probability-Based Broadcasting (PBB) |
| Ref. No. | Key Contribution | V2V | V2X |
|---|---|---|---|
| [31] | AI transmission scheduling in cognitive vehicular communication and vehicular communication modes | ✔ | ✔ |
| [32] | Resource allocation and power-sharing with several optimal resource allocation algorithms | ✔ | ✔ |
| [33] | Mobile edge computing framework and a network paradigm with predictive off-loading | ✔ | ✔ |
| [34] | Hierarchy of wireless networks and network standards, cumulative smart grid model, and IoT security analysis | ✽ | ✽ |
| [35] | Models and communication channel measurement metrics for wireless infrared networks | ✽ | ✽ |
| [36] | Longitudinal safety assessment of connected vehicles and intelligent driver model in a connected vehicle network | ✔ | ✽ |
| [37] | Survey on V2V-based vehicular sensor networks communications and discussion on issues and challenges in V2C communication | ✔ | ✽ |
| [38] | A physical layer perspective of vehicular communications | ✽ | ✔ |
| [39] | A short-range model for vehicle-to-vehicle communication on Vehicular AdHoc Networks through the showcase of Vehicle-to-Vehicle communication probability analysis | ✔ | ✗ |
| [40] | A hybrid clustering algorithm and simulation of the proposed algorithm on SUMO | ✽ | ✽ |
| [41] | A distributed cloud structure for urban traffic management through a cloud service handled message algorithm | ✽ | ✽ |
| [42] | Implementation of the Markov renewal process and classification of message passing between Road Side Units (RSU) and vehicles | ✽ | ✔ |
| [43] | Proposed a Cell Transmission Model for expressway traffic | ✽ | ✔ |
| [42] | Proposed a distributed cloud-based architecture for Vehicular AdHoc Networks performance and an additional mathematical model for solid communication of vehicles | ✗ | ✔ |
| [42] | A secure communication scheme for Vehicular AdHoc Networks | ✔ | ✔ |
| [44] | Highlighted the difficulties in implementing VANET systems due to traffic, communication, and safety concerns, and investigated how machine learning techniques may help address these challenges | ✔ | ✔ |
| [45] | Maximized global criteria while simultaneously boosting class longevity, information transmission speed, and lowering inter-class overload and provided an Efficient Key Management Scheme (KMSUNET) based on symmetric and asymmetric encryption to solve the performance and security issues of the UVANET environment | ✔ | ✽ |
| [46] | The suggested approach aims to establish reliable and steady clusters contributing to the network’s overall reliability | ✔ | ✔ |
| [47] | Over time, the percentage of malicious nodes in a vehicle AdHoc network may be reduced thanks to this scheme’s capability to identify and remove them | ✔ | ✽ |
| [48] | A novel self-adaptive Angular-based k-medoid Clustering Algorithm (SAACS) is created to generate flexible clusters. The network latency decrease, and clusters are built using informed predictions about route lengths and signal ranges. | ✔ | ✔ |
| [49] | This comprehensive review encompasses the many methods explored in current literature as prospective solutions for addressing the pervasive problem of traffic congestion. | ✔ | ✽ |
| [50] | Scholars are now more responsible for safeguarding individuals’ private data and information and put forward the Key Agreement Protocol for Urbanized Block Chains (UB-KAP) | ✔ | ✽ |
| [51] | An innovative REST web service for visualizing data is proposed, and also the Fundamental Safety Messages were put through their paces in a Big Data lab. The authors discussed proper behavior concerning packet loss, packet delivery, and communication latency was shown. | ✔ | ✔ |
| [52] | For this reason, the AWCP EE-WOA model analysis includes a vehicular network at a predetermined velocity and location. | ✔ | ✽ |
| Notation | Description |
|---|---|
| A Vehicle | |
| Certification Authority Server | |
| Vehicle ID | |
| Vehicle Registration Number | |
| Extract Numeric Values from a String | |
| Vehicle Numeric Code extracted from the Registration Number | |
| Vehicle e-mail | |
| Vehicle Password | |
| Concatenation | |
| One-Way Hash Function | |
| Vehicle Timestamp | |
| Server-Side Timestamp | |
| LCG-Based Random Numbers | |
| Vehicle Code generated by the server | |
| Shuffled Vehicle Code using the FYS algorithm | |
| The Result computed on the Server-Side | |
| Secured Password for Vehicle | |
| Updated Vehicle Code | |
| Updated Vehicle Code generated by the server | |
| Vehicle Reference | |
| Shuffling of Updated Vehicle Code generated by the server | |
| Vehicle Code for Authentication generated by the server | |
| OTP-Like Vehicle Code generated by the server | |
| Vehicle Session Key generated by the server | |
| Vehicle Authentication Method | |
| Vehicle Authentication Status | |
| Server Response Against HTTP Request | |
| Not Equal Operator | |
| Latitude | |
| Longitude | |
| Current location of the vehicle moving on the road | |
| Vehicle Threshold Location Interval | |
| Server Interval Table | |
| Server Log Table | |
| The function that will extract latitude from the location | |
| The function that will extract longitude from the location | |
| Message Priority | |
| Message Template | |
| Receiver ID | |
| Sender ID |
| OBU | CA Server | |
|---|---|---|
| Registration: Computes | ||
inside vehicle OBU | Generates |
| Vehicle OBU | CA Server | |
|---|---|---|
| Login and authentication: Computes | Checks with DB Updates logs table with DB Updates logs table | |
| Vehicle | CA Server | |
|---|---|---|
| V2I Communication: Computes | Updating logs |
| Vehicle A | Vehicle B | |
| V2V Communication: Computes | Replies: Computes |
| Notations | |
|---|---|
| A Vehicle | |
| Vehicle Unique Identity | |
| Closest Vehicle | |
| Vehicle-ID | |
| Closest Vehicles List | |
| Distance Between Vi and Vj | |
| Number of Closest Vehicles to Vj | |
| Range of Dynamic Transmission | |
| Moving Vehicle Direction | |
| Vehicle Speed | |
| Assumed Weights | |
| Vehicle-to-Infrastructure (V2I) | |||||
|---|---|---|---|---|---|
| Attributes | 1st Request | 2nd Request | 3rd Request | 4th Request | 5th Request |
| Status (status code) | 200 | 200 | 200 | 200 | 200 |
| Response Size (bytes) | 289 | 289 | 289 | 289 | 289 |
| Socket Initialization (milliseconds) | 2.18 | 2.07 | 1.77 | 2.12 | 1.40 |
| DNS Lookup (milliseconds) | 4.11 | 3.19 | 2.95 | 2.17 | 1.62 |
| TCP Handshake (milliseconds) | 1.47 | 1.25 | 1.06 | 0.92 | 0.76 |
| Transfer Start (milliseconds) | 91.38 | 98.18 | 88.02 | 82.33 | 80.91 |
| Download (milliseconds) | 20.24 | 4.19 | 3.35 | 4.81 | 3.73 |
| Vehicle-to-Vehicle (V2V) | |||||
| Status (status code) | 200 | 200 | 200 | 200 | 200 |
| Response Size (bytes) | 289 | 289 | 289 | 289 | 289 |
| Socket Initialization (milliseconds) | 11.24 | 4.22 | 1.68 | 1.36 | 1.04 |
| DNS Lookup (milliseconds) | 1.19 | 0.48 | 0.77 | 0.47 | 0.89 |
| TCP Handshake (milliseconds) | 3.03 | 1.48 | 2.49 | 2.63 | 2.41 |
| Transfer Start (milliseconds) | 91.75 | 93.56 | 83.26 | 62.03 | 58.95 |
| Download (milliseconds) | 12.61 | 4.49 | 2.89 | 3.32 | 3.45 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Latif, R.M.A.; Jamil, M.; He, J.; Farhan, M. A Novel Authentication and Communication Protocol for Urban Traffic Monitoring in VANETs Based on Cluster Management. Systems 2023, 11, 322. https://doi.org/10.3390/systems11070322
Latif RMA, Jamil M, He J, Farhan M. A Novel Authentication and Communication Protocol for Urban Traffic Monitoring in VANETs Based on Cluster Management. Systems. 2023; 11(7):322. https://doi.org/10.3390/systems11070322
Chicago/Turabian StyleLatif, Rana Muhammad Amir, Muhammad Jamil, Jinliao He, and Muhammad Farhan. 2023. "A Novel Authentication and Communication Protocol for Urban Traffic Monitoring in VANETs Based on Cluster Management" Systems 11, no. 7: 322. https://doi.org/10.3390/systems11070322
APA StyleLatif, R. M. A., Jamil, M., He, J., & Farhan, M. (2023). A Novel Authentication and Communication Protocol for Urban Traffic Monitoring in VANETs Based on Cluster Management. Systems, 11(7), 322. https://doi.org/10.3390/systems11070322








