Token-Based Authentication Framework for 5G MEC Mobile Networks
Abstract
:1. Introduction
- End-Users (EU). They are the parties who are using or will use the services provided in the 5G MEC environment in their professional activity or as consuming services.
- Service Providers (SP). They are all entities that are deploying service solutions into MEC hosts. Most of them deliver MEC applications that might run in multiple instances, on multiple or even on a single MEC host server. The services hosted within the MEC Platforms can support multi-tenancy, can be isolated [6] or can cooperate and mutually share resources.
- Network Providers (NP). They are physical (MNO—Mobile Network Operator) and virtual (MVNO—Mobile Virtual Network Operator) providers of wireless communications services that own or control the radio access layer and connect with external networks.
- MEC Providers. They are the entities that enable the MEC environment for 5G networks hosted by Network Providers. They can be both external organizations and Network Providers themselves.
- We give an outline of the 5G MEC security architecture and its security domains.
- We specify the authentication protocol which uses the MEC Enabler to generate and distribute security tokens.
- We present how the proposed “MEC Enabler” fits in the 5G architecture and its functions in the 5G MEC security architecture.
- We describe several existing JSON tokens schemes and the JMAT, which is the proposed token version suitable for 5G MEC access control service.
- Finally, we empirically compare the size of JMAT tokens and the time taken to generate and encrypt these tokens with an assortment of encryption algorithms and signing modes. It checks if the application in the proposed solution does not disturb MEC services’ quality requirements, such as expected latency or data transfer overhead in 5G networks.
2. The Outline of the 5G MEC Access Control Architecture and the MEC Enabler
- NAS (Network Access Security): this domain guarantee security of user data by protection (confidentiality and integrity) of signaling and user data. It is realized for Control Plane (CP), Data Plane (DP), and User Equipment (UE) network.
- NDS (Network Domain Security) this domain is responsible for the protection of signaling and user data exchange between several network areas.
- UES (User Equipment Security): it is responsible at the user’s side for hardware and software security, including user access to the mobile equipment.
- AS (Applications Security) it is responsible for the protection of communication (secure) between applications in UE and applications offered by the Service Provider. It is under the control of the end-user or the Service Provider (in the Application sub-Plane).
- AKM (Initial Authentication and Key Management): the security features that enable network functions to communicate securely. It implements authentication and key management mechanisms, which allows the realization of the unified authentication framework.
- SCM (Security Credentials Management) includes the relevant key management and service authentication between UE and the external data-transmitting network. In our model, the MEC Enabler governs this security domain.
- SIO (Security Interoperability) (also through MEC) this domain supports the openness of security capability between external Service Provider and the 5G network entity. It also includes a set of features that allows the stakeholders to know the status of security features.
- NSS (Network Slices Security) it is responsible for security of slices, for example for isolation, authorization and access control.
- MECS (MEC Security): it is responsible for the protection of software that belongs to the Service Provider, the hardware used for the realization of the MEC host and edge server, and for virtualization platform (VM).
- CLS (Cloud Security) includes all solutions to protect resources and communication inside the home domain (both the operator’s and the cloud). This domain extends the resources offered by MEC-hosted services to the external cloud resources.
- services for users which are properly authorized in the network,
- services for the protected communication (via protected links or slice),
- main security service which allows access to the MEC applications and services,
- management of access rights (for example by tokens or credentials),
- giving exchange credentials process for services realizing 5G MEC use cases,
- enabling services over the cloud or external operator’s domain.
- Administration Module: this module supports all management operations, and its responsible for configuration of other modules.
- Slice MANO (Management And Network Orchestration): this module is responsible for the management of the slice creation, updates, binding, and other operations which are connected with a slice life cycle. Another functionality of it is the reservation of slice resources for services, according to network segment information, service type, or any others, [27].
- Attribute-Based Access Control: the primary role of this module is to hold and expose policy information that can be related to MEC services, network access, slices, and others defined policy information from the MEC ecosystem [28].
- Service Management: this module is responsible for verification of available services, their current use, and the number of resources dedicated to them. Using this module will also make it possible to manage the MEC’s services lifecycle using the MEC orchestrator API in some specific use cases. However, management functionalities will be available after implementation of an additional load balancer, and analyzer of service placement [29].
- Credentials Management: it creates tokens used for authorization of the MEC resources. It is also responsible for token refreshment or deactivation according to the MEC service needs [30].
- Billing Module: the role of this module is to keep billing information and collect information about MEC usage. Information from this module can be used for the realization of different business models (for example, resource reservation or usage) [31].
- UPF MEC Configuration: this module is responsible for UPF MEC configuration, including proper network slices binding [32]. According to the network policy, it can also match operators slices with MEC resources in some use cases.
- AAA: the role of this module is authentication, authorization, and accounting of all requests which are sent to MEC services [33]. If verification done by this module is positive, other modules start preparing network configuration by generating access tokens and API communication. Otherwise, if verification is negative, network configuration will not be applied, and finally, access to the MEC resources will not be possible. It is one of the main functionalities, which significantly improves the protection of network and MEC resources by the MEC Enabler.
| Algorithm 1: The authentication procedure with the MEC Enabler, see Figure 3. |
PROCEDURE BEGIN:
|
3. The Overview of Security Credentials Suitable for MEC Enabler
- Propagate identity between interested parties.
- Propagate user permissions between interested parties.
- Transfer data in a secure way between interested parties over an unsecured channel.
4. The Design of JWT Authentication Token Used by MEC Enabler (JMAT)
- id: an identifier of the entity that sent the request (principal).
- actor: type and context of the principal, possible values are defined by each application independently, e.g., user, tester.
- token_preferences.life_time: the timespan while the token can be accepted. It might be shorter than the (time_of_end_of_life - time_of_generation) value to support the token refreshment.
- token_preferences.nonce: the random value that prevents the reply attack.
- appid: a unique name of the application.
- slice.id: an identifier of the slice used by the service inside the application.
- slice.slice_type: an array of attributes describing the slice that might be used by the application or by the control plane.
- slice.service: an array of services’ identifiers that can be accessed by the principal using this slice. Those services are part of the application that is mentioned in this JMAT token.
- access: authorization access decision, for the scope of this article, it is the Boolean value, but might be extended to another set of possible decisions.
- time_of_generation: timestamp of the response generation, might be saved as an integer number.
- time_of_end_of_life: the access is valid before this timestamp, might be saved as an integer number.
- Unprotected (marked as U in the Tables): the payload of JMAT represented as plaintext—only for input data size compare,
- encrypted with AES-CBC, signed with HMAC using SHA-256, AES Key Wrap [24] (marked as A128),
- encrypted with AES-CBC and signed with HMAC using SHA-256, symmetric key encrypted with RSA-OAEP [24] (RSAC),
- signcrypted with AES-GCM, symmetric key encrypted with RSA-OAEP [24] (marked as RSAG),
- only signed with HMAC using SHA-256 [21] (marked as SHA).
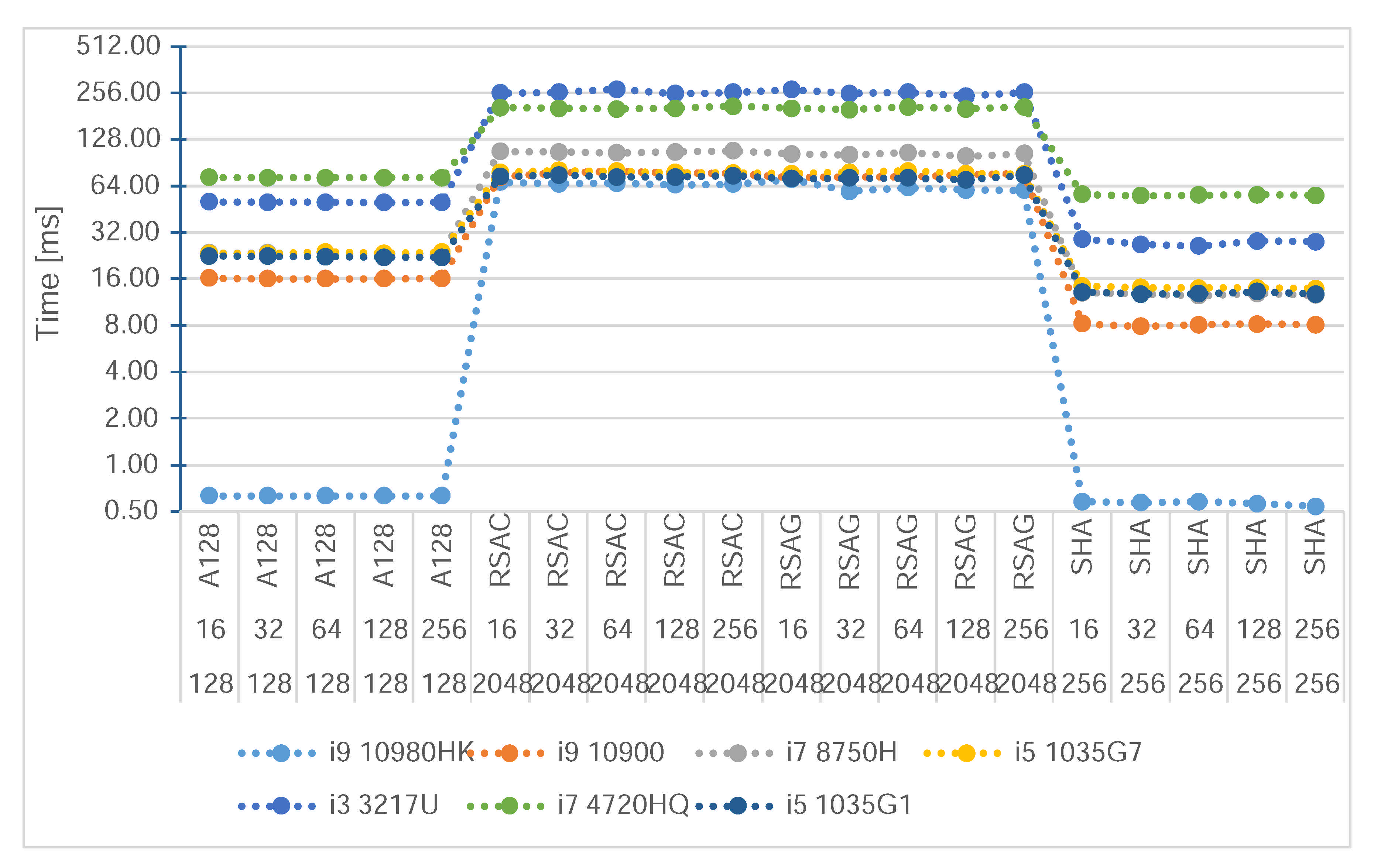
5. Generation and Validation of JMAT: Numerical Results
- For symmetric cryptography, key generation can be done together with token generation.
- For asymmetric cryptography, key generation needs its separate computational thread or even a separate key generation server.
- For security reasons, the key generator in the MEC Enabler platform can be implemented without special hardware or software solutions, but it must be especially protected against data leakage.
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| 3GPP | 3rd Generation Partnership Project |
| 5G | fifth generation cellular network technology |
| AAA | Authentication, Authorization and Accounting |
| ABAC | Attribute-Based Access Control |
| AES | Advanced Encryption Standard |
| AKM | Initial Authentication and Key Management |
| AMF | Access and Mobility Management Function |
| API | Application Programming Interface |
| AS | Applications Security |
| AUSF | Authentication between UE and Authentication Server Function |
| CAPIF | Common API Framework |
| CDC | Cipher Block Chaining |
| CLS | Cloud Security |
| CN | Core Network |
| CP | Control Plane |
| CPU | Community Protection Units |
| CQRS | Command Query Responsibility Segregation |
| DP | Data Plane |
| EAP | Extensible Authentication Protocol |
| eMBB | enhanced Mobile Broadband |
| ETSI | European Telecommunications Standards Institute |
| EU | End-Users |
| HMAC | Hash Message Authentication Code |
| H-SMF | Home Session Management Function |
| JMAT | JSON MEC Access Token |
| JOSE | JavaScript Object Signing and Encryption |
| JSON | JavaScript Object Notation |
| JWE | JSON Web Encryption |
| JWS | JSON Web Signature |
| JWT | JSON Web Token |
| MANO | Management And Network Orchestration |
| MEC | Multi-Access Edge Computing |
| MECS | MEC Security |
| mMTC | massive Machine Type Communication |
| MNO | Mobile Network Operator |
| MVNO | Mobile Virtual Network Operator |
| NAS | Network Access Security |
| NDS | Network Domain Security |
| NP | Network Providers |
| NSS | Network Slices Security |
| OAEP | Optimal Asymmetric Encryption Padding |
| PDU | Protocol Data Unit |
| RAN | Radio Access Network |
| RSA | Rivest Shamir Adleman algorithm |
| SCM | Security Credentials Management |
| SDN | Software-Defined Network |
| SHA | Secure Hash Algorithm |
| SIO | Security Interoperability |
| SMF | Session Management Function |
| SP | Service Provider |
| SRM | Security-Related Metadata |
| UDM | Unified Data Management |
| UE | User Equipment |
| UES | User Equipment Security |
| UPF | User Plane Function |
| URL | Uniform Resource Locator |
| uRLLC | ultra-Reliable Low-Latency Communication |
| VM | Virtualization Machine Platform |
| V-SMF | Visited Session Management Function |
References
- Minimum Requirements Related to Technical Performance for IMT-2020 Radio Interface(s); Report ITU-R M.2410-0; ITU: Geneva, Switzerland, 2017.
- Multi-Access Edge Computing (MEC). Framework and Reference Architecture; ETSI GS MEC 003 V2.1.1; ETSI: Sophia Antipolis, France, 2020; Available online: https://www.etsi.org/deliver/etsi_gs/MEC/001_099/003/02.02.01_60/gs_MEC003v020201p.pdf (accessed on 23 May 2021).
- Blanco, B.; Fajardo, J.O.; Giannoulakis, I.; Kafetzakis, E.; Peng, S.; Pérez-Romero, J.; Trajkovska, I.; Khodashenas, P.S.; Goratti, L.; Paolino, M.; et al. Technology pillars in the architecture of future 5G mobile networks: NFV, MEC and SDN. Comput. Stand. Interfaces 2017, 54, 216–228. [Google Scholar] [CrossRef] [Green Version]
- Hu, Y.C.; Patel, M.; Sabella, D.; Sprecher, N.; Young, V. Mobile Edge Computing. A key technology towards 5G. ETSI White Pap. 2015, 11, 1–16. [Google Scholar]
- Nowak, T.W.; Sepczuk, M.; Kotulski, Z.; Niewolski, W.; Artych, R.; Bocianiak, K.; Osko, T.; Wary, J.-P. Verticals in 5G MEC-Use Cases and Security Challenges. IEEE Access 2021, 9, 87251–87298. [Google Scholar] [CrossRef]
- Kotulski, Z.; Nowak, T.W.; Sepczuk, M.; Tunia, M.A. 5G networks: Types of isolation and their parameters in RAN and CN slices. Comput. Netw. 2020, 171, 107135. [Google Scholar] [CrossRef]
- Li, J.; Della Penda, D.; Sahlin, H.; Schliwa-Bertling, P.; Folke, M.; Stattin, M. An Overview of 5G System Accessibility Differentiation and Control. arXiv 2020, arXiv:2012.05520. [Google Scholar]
- Wang, C.; Zhang, Y.; Chen, X.; Liang, K.; Wang, Z. SDN-Based Handover Authentication Scheme for MEC in Cyber-Physical Systems. IEEE Internet Things J. 2019, 6, 8692–8701. [Google Scholar] [CrossRef]
- Jia, X.; He, D.; Kumar, N.; Choo, K.-K.R. A Provably Secure and Efficient Identity-Based Anonymous Authentication Scheme for MEC. IEEE Syst. J. 2020, 14, 560–571. [Google Scholar] [CrossRef]
- Ali, A.; Lin, Y.-D.; Li, C.-Y.; Lai, Y.-C. Transparent 3rd-Party Authentication with Application Mobility for 5G Mobile Edge Computing. In Proceedings of the European Conference on Networks and Communications (EuCNC): Network Softwarisation (NET), Dubrovnik, Croatia, 15–18 June 2020. [Google Scholar]
- Fotiou, N.; Siris, V.A.; Polyzos, G.C. Capability-based access control for multi-tenant systems using OAuth 2.0 and Verifiable Credentials. arXiv 2021, arXiv:2104.11515. [Google Scholar]
- Li, C.-Y.; Lin, Y.-D.; Lai, Y.-C.; Chien, H.-T.; Huang, Y.-S.; Huang, P.-H.; Liu, H.-Y. Transparent AAA Security Design for Low-Latency MEC-Integrated Cellular Networks. IEEE Trans. Veh. Technol. 2020, 69, 3231–3243. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Kaddoum, G.; Guizani, M.; Jayakody, D.N.K. A Lightweight and Privacy-Preserving Authentication Protocol for Mobile Edge Computing. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Li, Y.; Cheng, Q.; Liu, X.; Li, X. A Secure Anonymous Identity-Based Scheme in New Authentication Architecture for Mobile Edge Computing. IEEE Syst. J. 2021, 15, 935–946. [Google Scholar] [CrossRef]
- Lee, J.; Kim, D.; Park, J.; Park, H. A Multi-Server Authentication Protocol Achieving Privacy Protection and Traceability for 5G Mobile Edge Computing. In Proceedings of the IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 10–12 January 2021; pp. 1–4. [Google Scholar]
- Behrad, S.; Bertin, E.; Tuffin, S.; Crespi, N. A new scalable authentication and access control mechanism for 5G-based IoT. Futur. Gener. Comput. Syst. 2020, 108, 46–61. [Google Scholar] [CrossRef] [Green Version]
- Qiu, Q.; Liu, S.; Xu, S.; Yu, S. Study on Security and Privacy in 5G-Enabled Applications. Wirel. Commun. Mob. Comput. 2020, 2020, 8856683. [Google Scholar] [CrossRef]
- Kotulski, Z.; Niewolski, W.; Nowak, T.W.; Sepczuk, M. New Security Architecture of Access Control in 5G MEC. In Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2021; pp. 77–91. [Google Scholar]
- Ji, X.; Huang, K.; Jin, L.; Tang, H.; Liu, C.; Zhong, Z.; You, W.; Xu, X.; Zhao, H.; Wu, J.; et al. Overview of 5G security technology. Sci. China Inf. Sci. 2018, 61, 081301. [Google Scholar] [CrossRef] [Green Version]
- 5G; Security Architecture and Procedures for 5G System; ETSI TS 133 501 V16.5.0; ETSI: Sophia Antipolis, France, 2021; Available online: https://www.etsi.org/deliver/etsi_ts/133500_133599/133501/16.05.00_60/ts_133501v160500p.pdf (accessed on 23 May 2021).
- JSON Web Signature (JWS); RFC 7515; IETF: Fremont, CA, USA, 2015; Available online: https://tools.ietf.org/html/rfc7515 (accessed on 23 May 2021).
- JSON Web Encryption (JWE); RFC 7516; IETF: Fremont, CA, USA, 2015; Available online: https://tools.ietf.org/html/rfc7516 (accessed on 23 May 2021).
- JSON Web Key (JWK); RFC 7517; IETF: Fremont, CA, USA, 2015; Available online: https://tools.ietf.org/html/rfc7517 (accessed on 23 May 2021).
- JSON Web Algorithms (JWA); RFC 7518; IETF: Fremont, CA, USA, 2015; Available online: https://tools.ietf.org/html/rfc7518 (accessed on 23 May 2021).
- JSON Web Token (JWT); RFC 7519; IETF: Fremont, CA, USA, 2015; Available online: https://tools.ietf.org/html/rfc7519 (accessed on 23 May 2021).
- Functional Architecture and Information Flows to Support Common API Framework for 3GPP Northbound APIs. 3GPP TS 23.222 V17.4.0; The 3rd Generation Partnership Project. 2021. Available online: https://www.3gpp.org/ftp/Specs/archive/23_series/23.222/23222-h40.zip (accessed on 23 May 2021).
- Kotulski, Z.; Nowak, T.W.; Sepczuk, M.; Tunia, M.; Artych, R.; Bocianiak, K.; Osko, T.; Wary, J.-P. Towards constructive approach to end-to-end slice isolation in 5G networks. EURASIP J. Inf. Secur. 2018, 2018, 2. [Google Scholar] [CrossRef] [Green Version]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute Based Access Control; NIST SP 1800-3, Second Draft; NIST: Gaithersburg, MD, USA, 2017. [Google Scholar]
- Brik, B.; Frangoudis, P.A.; Ksentini, A. Service-Oriented MEC Applications Placement in a Federated Edge Cloud Architecture. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Grassi, P.A.; Garcia, M.E.; Fenton, J.L. Digital Identity Guidelines; NIST SP 800-63-3; NIST: Gaithersburg, MD, USA, 2017. Available online: https://csrc.nist.gov/csrc/media/publications/sp/800-63/3/draft/documents/sp800-63-3-draft.pdf (accessed on 23 May 2021).
- Multi-Access Edge Computing (MEC); Phase 2: Use Cases and Requirements; ETSI GS MEC 002 V2.1.1; ETSI: Sophia Antipolis, France, 2018; Available online: https://www.etsi.org/deliver/etsi_gs/mec/001_099/002/02.01.01_60/gs_mec002v020101p.pdf (accessed on 23 May 2021).
- Multi-Access Edge Computing (MEC). MEC 5G Integration; ETSI GR MEC 031 V2.1.1; ETSI: Sophia Antipolis, France, 2020; Available online: https://www.etsi.org/deliver/etsi_gr/MEC/001_099/031/02.01.01_60/gr_MEC031v020101p.pdf (accessed on 23 May 2021).
- Behrad, S.; Bertin, E.; Crespi, N. A survey on authentication and access control for mobile networks: From 4G to 5G. Ann. Telecommun. 2019, 74, 593–603. [Google Scholar] [CrossRef]
- 5G; Procedures for the 5G System (5GS); ETSI TS 123 501 V16.5.0; ETSI: Sophia Antipolis, France, 2020; Available online: https://www.etsi.org/deliver/etsi_ts/123500_123599/123502/16.05.00_60/ts_123502v160500p.pdf (accessed on 23 May 2021).
- Procedures for the 5G System; 3GPP TS 23.502 V17.0.0; ETSI: Sophia Antipolis, France, 2021; Available online: https://www.3gpp.org/ftp/Specs/archive/23_series/23.502/23502-h00.zip (accessed on 23 May 2021).
- Hu, V.C.; Ferraiolo, D.; Kuhn, R.; Schnitzer, A.; Sandlin, K.; Miller, R.; Scarfone, K. Guide to Attribute Based Access Control (ABAC) Definition and Considerations; NIST SP 800-162; NIST: Gaithersburg, MD, USA, 2014. Available online: https://nvlpubs.nist.gov/nistpubs/specialpublications/NIST.sp.800-162.pdf (accessed on 23 May 2021).
- Ali, B.; Gregory, M.A.; Li, S. Multi-Access Edge Computing Architecture, Data Security and Privacy: A Review. IEEE Access 2021, 9, 18706–18721. [Google Scholar] [CrossRef]
- Bhatt, S.; Tawalbeh, L.A.; Chhetri, P.; Bhatt, P. Authorizations in Cloud-Based Internet of Things: Current Trends and Use Cases. In Proceedings of the Fourth International Conference on Fog and Mobile Edge Computing (FMEC), Rome, Italy, 10–13 June 2019; pp. 241–246. [Google Scholar]
- Zhu, Y.; Gan, G.; Guo, R.; Huang, D.; Ruiqi, G. PHE: An efficient traitor tracing and revocation for encrypted file syncing-and-sharing in cloud. IEEE Trans. Cloud Comput. 2018, 6, 1110–1124. [Google Scholar] [CrossRef]
- Zhang, Q.; Wang, S.; Zhang, D.; Wang, J.; Zhang, Y. Time and Attribute Based Dual Access Control and Data Integrity Verifiable Scheme in Cloud Computing Applications. IEEE Access 2019, 7, 137594–137607. [Google Scholar] [CrossRef]
- Hao, J.; Liu, J.; Wang, H.; Liu, L.; Xian, M.; Shen, X. Efficient Attribute-Based Access Control with Authorized Search in Cloud Storage. IEEE Access 2019, 7, 182772–182783. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Piro, G.; Caldarola, D.; Boggia, G.; Bianchi, G. OAuth-IoT: An access control framework for the Internet of Things based on open standards. In Proceedings of the IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; pp. 676–681. [Google Scholar]
- Gupta, D.; Bhatt, S.; Gupta, M.; Kayode, O.; Tosun, A.S. Access Control Model for Google Cloud IoT. In Proceedings of the 2020 IEEE 6th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing, (HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS), Baltimore, MD, USA, 25–27 May 2020; pp. 198–208. [Google Scholar]
- Krishna, S. JSON Web Token (JWT) based client authentication in Message Queuing Telemetry Transport (MQTT). arXiv 2019, arXiv:1903.02895. [Google Scholar]
- Ahmed, S.; Mahmood, Q. An authentication based scheme for applications using JSON web token. In Proceedings of the 22nd International Multitopic Conference (INMIC), Islamabad, Pakistan, 29–30 November 2019; pp. 1–6. [Google Scholar]
- Ethelbert, O.; Moghaddam, F.F.; Wieder, P.; Yahyapour, R. A JSON Token-Based Authentication and Access Management Schema for Cloud SaaS Applications. In Proceedings of the IEEE 5th International Conference on Future Internet of Things and Cloud (FiCloud), Prague, Czech Republic, 21–23 August 2017; pp. 47–53. [Google Scholar]
- Alkhulaifi, A.; El-Alfy, E.M. Exploring Lattice-based Post-Quantum Signature for JWT Authentication: Review and Case Study. In Proceedings of the IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 25–28 May 2020; pp. 1–5. [Google Scholar]
- Rahmatulloh, A.; Gunawan, R.; Nursuwars, F.M.S. Performance comparison of signed algorithms on JSON Web Token. IOP Conf. Ser. Mater. Sci. Eng. 2019, 550, 012023. [Google Scholar] [CrossRef]
- Talukdar, T.; Batra, G.; Vaidya, J.; Atluri, V.; Sural, S. Efficient Bottom-Up Mining of Attribute Based Access Control Policies. In Proceedings of the IEEE 3rd International Conference on Collaboration and Internet Computing (CIC), San Jose, CA, USA, 15–17 October 2017; pp. 339–348. [Google Scholar]
- Aldy, P.A.; Alam, R.; Nur, A. Stateless Authentication with JSON Web Tokens using RSA-512 Algorithm. J. Infotel. 2019, 11, 36–42. [Google Scholar] [CrossRef]
- Guo, L.; Yang, X.; Yau, W.C. TABE-DAC: Efficient Traceable Attribute-Based Encryption Scheme with Dynamic Access Control Based on Blockchain. IEEE Access 2021, 9, 8479–8490. [Google Scholar] [CrossRef]
- Zhu, Y.; Yu, R.; Ma, D.; Chu, W.C.-C. Cryptographic Attribute-Based Access Control (ABAC) for Secure Decision Making of Dynamic Policy With Multiauthority Attribute Tokens. IEEE Tran. Reliab. 2019, 68, 1330–1346. [Google Scholar] [CrossRef]
- Chang, D.; Sun, W.; Yang, Y.; Wang, T. An E-ABAC-Based SDN Access Control Method. In Proceedings of the 6th International Conference on Information Science and Control Engineering (ICISCE), Shanghai, China, 20–22 December 2019; pp. 668–672. [Google Scholar]
- Pencheva, E.; Asenov, I.; Atanasov, I.; Trifonov, D.V. Programmability of Policy Control at the Edge of the Mobile Network. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Nife, F.N.; Kotulski, Z. Application-Aware Firewall Mechanism for Software Defined Networks. J. Netw. Syst. Manag. 2020, 28, 605–626. [Google Scholar] [CrossRef] [Green Version]
- Ayache, M.; Gawanmeh, A.; Al-Karaki, J.N. XBAC: A Unified Access Control Model for Heterogeneous Multi-Tenancy Cloud Environments. In Proceedings of the 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 1872–1878. [Google Scholar]
- JWCrypto Documentation, Rev. 4e08b661. Available online: https://jwcrypto.readthedocs.io/ (accessed on 23 May 2021).
- Cryptography Documentation. Available online: https://cryptography.io/en/latest/hazmat/backends/openssl/ (accessed on 23 May 2021).
- OpenSSL Documentation. “Frequently Asked Questions”. Available online: https://www.openssl.org/docs/faq.html#MISC (accessed on 23 May 2021).
- AbdAllah, E.G.; Kuang, Y.R.; Huang, C. Advanced Encryption Standard New Instructions (AES-NI) Analysis: Security, Performance, and Power Consumption. In Proceedings of the 2020 12th International Conference on Computer and Automation Engineering (ICCAE), Sydney, Australia, 14–16 February 2020; pp. 167–172. [Google Scholar]
- Kotulski, Z.; Szczepinski, W. Error Analysis with Applications in Engineering; Springer: Dordrecht, The Netherlands, 2010. [Google Scholar]
- Use of Public Standards for the Secure Sharing of Information among National Security Systems. CNSS Advisory Memorandum, Information Assurance 02-15. July 2015. Available online: https://cryptome.org/2015/08/CNSS_Advisory_Memo_02-15.pdf (accessed on 23 May 2021).
- Srinivasa, R.; Naidu, N.K.S.; Maheshwari, S.; Bharathi, C.; Kumar, A.R.H. Minimizing Latency for 5G Multimedia and V2X Applications using Mobile Edge Computing. In Proceedings of the 2nd International Conference on Intelligent Communication and Computational Techniques (ICCT), Jaipur, India, 28–29 September 2019; pp. 213–217. [Google Scholar]







| Approach | MEC | Features | Summary |
|---|---|---|---|
| SDN-based authentication scheme [8] | **** | secret key distribution, authentication | This paper proposes an SDN-based handover authentication scheme for MEC in cyber-physical systems. An authentication handover module in the SDN controller is applied for key distribution and authentication management. The parties apply the 3-way handshake protocol to achieve mutual authentication and secret key confidentiality. |
| Identity-Based Anonymous Authentication Scheme [9] | **** | mutual authentication, anonymity, untraceability | The paper focuses on achieving mutual authentication with anonymity and untraceability. It presents a single message exchange round identity-based anonymous authenticated key agreement protocol for the MEC environment. The protocol achieves mutual authentication and assures both user anonymity and untraceability. |
| 3rd-Party Authentication [10] | **** | low latency, token-based | The paper proposes two solutions: Token-based Cookie transfer, 3rd-party Authentication and Token-based State transfer, 3rd-party Authentication for resolution of authentication and application mobility issues while achieving low latency. |
| Capability-based access control [11] | *** | compatibility (OAuth 2.0, Verifiable Credentials) | The paper proposes a capability-based access control technique for sharing Web resources, based on Verifiable Credentials (VCs) and OAuth 2.0. It proposes a new form of OAuth 2.0 access token based on VCs. |
| AAA Security Design [12] | **** | low latency, compatibility (OIDC) | The paper proposes a transparent security design called MECsec to secure the MEC with low latency in the cellular network. It contains three main components: cellular-based OpenID Connect (OIDC) authentication, bitmap-based authorization/accounting, and two-tier hash-based access control. |
| Privacy-Preserving Protocol [13] | *** | lightweight, mutual authentication | This paper proposes a lightweight mutual authentication protocol for MEC environments based on Elliptic Curve Cryptography, one-way hash functions and concatenation operations. |
| Authentication Architecture [14] | *** | lightweight, identity-based | The authors design a new authentication architecture for MEC environment, which provides an anonymous identity-based scheme suitable for lightweight devices. |
| Multi-Server Authentication Protocol [15] | **** | mutual authentication, scalability | This paper proposes a user authentication protocol in the MEC environment providing anonymous mutual authentication between mobile devices and application servers operating on the MEC platform while ensures that the trusted MEC server can securely track users on behalf of service providers. |
| Scalable authentication and access control [16] | *** | slicing support, IoT applicable | The paper proposes a Slice Specific Authentication and Access Control mechanism that makes use of the flexibility provided by virtualization technologies. This mechanism allows the authentication and access control of IoT devices to be delegated to the 3rd parties providing these devices. |
| 5G reference security architecture [17] | *** | general approach, risks identification | This paper gives the system reference architecture and overall security and privacy solutions for 5G applications. Based on the three major application scenarios of eMBB, uRLLC, and mMTC. It also provides specific suggestions for coping with security and privacy risks. |
| MEC Enabler-based solution [18] | ***** | scalability, sovereignty, compatibility (OAuth 2.0), adaptability (ABAC) | The paper proposes the high-level security architecture of 5G MEC networks, which provides security solutions for the network’s components and establishes secure access to all cooperating entities. The solution is based on the MEC Enabler, a new network’s module, which manages security credentials required to access resources of MEC-hosted services. |
| This paper | ***** | high security, compatibility (JWT, JWS) | For the security architecture proposed in [18], this paper defines the token reference pattern called JSON MEC Access Token (JMAT) suitable for MEC-hosted services in 5G networks. |
| No. | No. of Apps | No. of Slices | No. of Par. | U | A128 [kB] | RSAC [kB] | RSAG [kB] | SHA [kB] |
|---|---|---|---|---|---|---|---|---|
| 1 | 16 | 64 | 64 | 335.84 | 246.77 | 247.05 | 247.03 | 447.87 |
| 2 | 32 | 64 | 64 | 335.84 | 246.67 | 246.95 | 246.93 | 447.87 |
| 3 | 64 | 16 | 64 | 84.12 | 62.27 | 62.55 | 62.53 | 112.24 |
| 4 | 64 | 32 | 64 | 168.05 | 123.75 | 124.03 | 124.01 | 224.15 |
| 5 | 64 | 64 | 16 | 87.48 | 63.04 | 63.32 | 63.31 | 116.72 |
| 6 | 64 | 64 | 32 | 170.25 | 124.23 | 124.51 | 124.49 | 227.08 |
| 7 | 64 | 64 | 64 | 335.87 | 246.87 | 247.16 | 247.14 | 447.90 |
| 8 | 64 | 64 | 128 | 667.01 | 490.44 | 490.72 | 490.70 | 889.42 |
| 9 | 64 | 64 | 256 | 1329.25 | 977.14 | 977.43 | 977.40 | 1772.41 |
| 10 | 64 | 128 | 64 | 671.42 | 492.25 | 492.53 | 492.52 | 895.30 |
| 11 | 64 | 256 | 64 | 1342.62 | 983.77 | 984.05 | 984.03 | 1790.24 |
| 12 | 128 | 64 | 64 | 335.81 | 246.48 | 246.76 | 246.73 | 447.83 |
| 13 | 256 | 64 | 64 | 335.85 | 246.64 | 246.93 | 246.91 | 447.88 |
| Alg. | key gen. [ms] | std. dev. [ms] | var. | gen. [ms] | std. dev. [ms] | var. | valid. [ms] | std. dev. [ms] | var. |
|---|---|---|---|---|---|---|---|---|---|
| A128 | 0.02 | 0.004 | 0.20 | 11.33 | 0.083 | 0.01 | 4.65 | 0.371 | 0.08 |
| RSAC | 62.76 | 42.671 | 0.68 | 11.43 | 0.448 | 0.04 | 5.49 | 0.374 | 0.07 |
| RSAG | 56.73 | 39.116 | 0.69 | 11.03 | 0.249 | 0.02 | 5.12 | 1.144 | 0.22 |
| SHA | 0.02 | 0.006 | 0.27 | 2.22 | 0.814 | 0.37 | 5.84 | 1.052 | 0.18 |
| Key Size [Bits] | Key Generation [ms] | Token Generation [ms] | Ratio |
|---|---|---|---|
| 1024 | 12.33 | 11.08 | 1.11 |
| 2048 | 59.75 | 11.23 | 5.32 |
| 3072 | 226.81 | 11.34 | 20.00 |
| 4096 | 545.61 | 11.35 | 48.05 |
| 8192 | 6670.35 | 11.68 | 571.33 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Niewolski, W.; Nowak, T.W.; Sepczuk, M.; Kotulski, Z. Token-Based Authentication Framework for 5G MEC Mobile Networks. Electronics 2021, 10, 1724. https://doi.org/10.3390/electronics10141724
Niewolski W, Nowak TW, Sepczuk M, Kotulski Z. Token-Based Authentication Framework for 5G MEC Mobile Networks. Electronics. 2021; 10(14):1724. https://doi.org/10.3390/electronics10141724
Chicago/Turabian StyleNiewolski, Wojciech, Tomasz W. Nowak, Mariusz Sepczuk, and Zbigniew Kotulski. 2021. "Token-Based Authentication Framework for 5G MEC Mobile Networks" Electronics 10, no. 14: 1724. https://doi.org/10.3390/electronics10141724
APA StyleNiewolski, W., Nowak, T. W., Sepczuk, M., & Kotulski, Z. (2021). Token-Based Authentication Framework for 5G MEC Mobile Networks. Electronics, 10(14), 1724. https://doi.org/10.3390/electronics10141724







