1. Introduction
Security and privacy are critical factors of efficient access control models for healthcare systems. More importantly, the internet affects humans’ lifestyles and methods of communication, including their professional lives and social connections. The Internet of Things (IoT) is the use of tiny sensor-based devices that integrate physical and virtual domains. The application of blockchain-based frameworks provides tamper-proof and more decentralized communication among nodes. Blockchain is also called a distributed and immutable ledger [
1]. Hence, it provides applications and services, functionality, management, and on-demand access [
2]. However, the recommendations and implementations of networking devices and other things are still growing. Hence, most industries are shifting towards the IoT and the adaption of blockchain technologies [
3,
4].
Moreover, security and privacy challenges are crucial for blockchain-based models, especially systems that use the integration of healthcare systems. Security breaches consist of denial-of-service (DoS), structured query language (SQL) injection, spoofing, eavesdropping, and replay attacks, which are challenging for IoT-based systems. Such attacks affect security applications and their authorization, authenticity, and privacy. Therefore, it is very important to address these issues and to provide a novel design framework that can provide security to IoT devices that leverage blockchain applications. It is evident that weak security at any node can lead to access to patient health records. An electronic health record (
EHR) is regarded as the most important and sensitive type of data because it consists of a lot of sensitive information related to patients and diagnoses. However, the advancement and progress in digital healthcare systems has caused
EHR data to become more vulnerable to breaches [
5]; hence, security and privacy must play an important role in the case of decentralization and trust [
6].
However, a very important aspect of IoT may provide more security and applications to diverse users [
7]. Due to the ease of access to the internet and the increase in smart communication among people, objects, data, and processes, the exponential growth in the number of connected devices throughout the globe resulted in billions being recorded in the year 2020 [
8]. Therefore, the security challenges of IoT applications are the basic requirements for dealing with such issues. Consequently, there has been an improvement in their intricacies, as the great complexity of devices provides less security in the performance of access control. Access control is the basic security tool for
EHR data from any source. Therefore, it is compulsory to design access control policies for
EHR and
PHR [
9]. A blockchain-based digital healthcare framework, which is also called Hyperledger Fabric, is used for the development of patient health record (
PHR) systems. Security, privacy, and cross-domain authorization are factors that influence patient health records around the world. According to the security breach level index, every single day, million of records are stolen online [
10]. These issues need to be explored by researchers in order to investigate the security and privacy challenges related to the use of blockchain for
PHR.
In a digital healthcare system, a cross-domain organization approach can provide facilities to clinicians and patients for accessing data that are distributed among different domains. On the other hand, accessing data through a cross-domain organization requires more security and flexible authorization policies. A policy defines rules and strict conditions for the attributes of participants and data. Moreover, data can be encrypted by using cryptographic techniques. In the literature, the encryption techniques used by the researchers are based on ring signatures and group signatures. These encryption techniques have specific applications for predefined access control models, e.g., role-based access control (RBAC), access control list (ACL), discretionary access control list (DAC), and trust-based access control (TBAC). In our proposed framework, we will use an attribute-based signature (ABS) with an ABAC access control model to encrypt data. We will use the model of Sahai and Water [
11] as a benchmark for our access control model, which is completely based on ABAC.
Our main contribution in this research comprises the identification of security issues regarding the IoT and an investigation of a blockchain-based framework to overcome these issues. Our second contribution is the design of a novel algorithm for a blockchain-based IoT network in order to access electronic health records securely. Our third contribution is a novel blockchain-based framework for reading, applying, returning, and adding electronic health records using private and public blockchains.
The rest of the article is organized as follows.
Section 2 describes the literature review. In
Section 3, we explain the methodology of our proposed work.
Section 4 describes the flow of transactions in our proposed framework, and in
Section 5, we explain the proposed algorithms.
Section 6 provides the dataset and the types of data that we used.
Section 7 explains the experimental setup and analysis. In
Section 8, we provide a detailed discussion of our results. Finally, in
Section 9, we conclude our study and describe future work.
Our Contributions
Our contributions in this research paper include a secure and flexible access control based on a ring signature. Our proposed method provides more security and privacy by leveraging novel smart contract and encryption algorithms. Moreover, we used a ring signature to encrypt and decrypt data. Once a user signs a message with a ring signature, only the selected and authenticated users can decrypt it. In addition, the user does not know the identity of the signer, and this feature helps in keeping the privacy of the users in the blockchain. Moreover, this protects users from active collusion attacks. Therefore, we used an attributed-based fine-grained access control mechanism that provides more security, as only users who have the required access rights can access the data. If a user does not meet the security criteria, their request is denied.
2. Literature Review
The tremendous growth in the number of IoT devices and their impacts on social life have created a protected, open, and unique environment in which patient health records can be securely accessed. The models for IoT necessitate the utilization of a central cloud server, which results in a single point of failure (SPOF) [
12]. In order to provide solutions to such problems for sensor-based medical devices, blockchain is considered as one of the best tools and platforms for a decentralized environment. The innovation of blockchain is a huge advancement in the IoT security field [
12]. The applications of blockchain technology start from its decentralization, trust, and distributed nature from diverse points of view. The use of blockchain with IoT devices provides more a secure environment that is not dependent on a single trusting authority. During the development of IoT frameworks, there are more possibilities to have an expanded number of cooperating gadgets or things in them. These expanded numbers of gadgets attempt to communicate with each other by using Internet as a medium. This would result in numerous obstacles because most of the gathered data are kept in the focal servers of IoT systems. Therefore, in the literature, researchers have tried to cope with these issues.
Ali et al. [
1] proposed a system based on a patient monitoring system and an interference-aware system for the IoT. The authors also provided a comparative analysis with the benchmark models and traditional central-authority-dependent models, which rely on a central authority node. The authors also proposed a lightweight ring-signature-based consensus algorithm for a sensor-based blockchain network. Ali et al. also proposed the idea of a decentralized medical-data-sharing scheme for cross-domain use with the Hyperledger Fabric platform. The authors provided many details about the application of this blockchain tool in an IoT-based environment and peer-to-peer networks. They also designed a P2P-based record-sharing protocol that supports smart-contract-based access control polices. The authors of [
13] highlighted recent issues and developed an access control policy for digital medical records through a fine-grained access control system. A novel architecture was designed by authors in the literature to secure electronic healthcare records based on a distributed ledger technology and also improved the interoperability of health records between different organizations [
14]. However, the authors also provided a performance evaluation by using a blockchain tool and proposed some endorsement policies. In [
15], the authors explored the performance metrics of the Hyperledger Fabric framework. Some researchers provided optimization of security and performance by using a blockchain platform with sensor-based networks. The authors of these research works provided a complete justification for enhanced performance with minimal computation time. Last but not least, the authors of [
16] devised a searchable encryption scheme for electronic healthcare records using blockchain. They designed an algorithm for indexing healthcare records and a two-part evaluation scheme.
Dwivedi et al. [
14] proposed a peer-to-peer network in order to improve privacy and security when connecting remote medical sensors and devices. The authors designed a framework of modified blockchain models while considering IoT sensor devices. In summary, the contributions of the authors were the resolution of the issues of using a blockchain with sensors. Irving et al. [
17] designed a method for using a blockchain in a doctor-and-patient setup and for booking for patients. Srivastava et al. [
3] proposed a modified blockchain based on directed acyclic graphs, which were proposed by Zohar and Somplisnky [
18]. However, the transaction protocol was for a private blockchain, and the author also provided a comparative analysis between private and public blockchains. The main contribution of this research design was the provision of solution to some types of security breaches. The authors attained a better efficiency and scalability. Yazdinejad et al. [
19] presented a blockchain-based framework for software-defined networking (SDN) [
20,
21]. These works have provided a road map to 5G technology, and they reduced the execution time and the delay for re-authentication in 5G and advanced networks [
22].
2.1. Smart Cities
Over the last decade, the applications of technology and IoT have brought improvements to human life and social activities. Various fields, such as weather prediction, geographical changes, and resource utilization, are managed smartly now. According to recent reports and a survey on IoT [
22], it is predicted that by 2050, most devices will be connected through the IoT and sensor networks, which will be known as the Internet of Energies. For future purposes, more and more researchers are analyzing and planning resource utilization in a more intelligent manner, especially for IoT models because IoT devices are run with battery power. Smart cities have been implemented and designed in developed countries, and they have shown the best results for human life and healthy lifestyles, especially in noise-free environments [
23]. Rathore, Kwon [
24] designed a peer-to-peer network and proposed a security protocol for software-defined networking (SDN) using blockchain technology for IoT applications in smart cities. The authors integrated IoT devices and blockchain in different scenarios, such as SDN or mobile edge and fog computing [
23]. In the case of SDN [
25], the authors provided and deployed a prototype for their proposed framework [
26]. In their research, the authors of [
27] explored the maximum utilization of blockchain technology to provide a solution to the IoT security challenges in a 5G cell framework. The research mainly focused on a multi-layer security framework for an IoT arrangement that was dependent on blockchain [
26]. The proposed framework supported the relatively real sending of the blockchain applications through the integration of the IoT network into a multi-layer decentralized framework [
28]. The authors used machine learning techniques and a classification algorithm to classify the users who did not have access to the
EHR data through the blockchain. The high security and believable confirmation of the blockchain technology provided a validation system for clustering the correspondence of heads with one another and a base solution through a neighborhood blockchain [
29].
The idea of a power grid system using blockchain was proposed in [
30,
31]. It was observed and justified that blockchain technology will be more useful in the utilization of available power and resources through its decentralized nature [
32]. Using blockchain can provide more efficiency and security. In the literature related to blockchain, some researchers proposed the idea of integrating electronic technologies, such as an inverter with blockchain, which can be more helpful in smart cities by providing efficiency and a low cost [
26]. This is proof that blockchain can provide better solutions to solar-system-based power grids [
33].
2.2. Smart Healthcare
Recently, the blockchain-based IoT has provided more security and ease of management for sensor data, which has led to more advancement in the IoT field [
34,
35]. One great application is the integration of blockchain into the healthcare domain. Using blockchain, patients and doctors can access electronic health records in a secure manner. A doctor can add an
EHR to the blockchain for a patient, and it can also be provided for future usage. Medical sensors are used in such applications to gather sensor data [
36]. Most developed countries, such as China, the USA, and the UK, are integrating blockchain with their digital healthcare systems because, it helps in the transformation from a traditional medical system towards a digital healthcare system.
2.3. Smart Homes
Smart homes play a vital role in human life and in social economics [
37]. Smart homes are important applications of the IoT and sensor networks [
38]. Blockchain-based sensor networks and smart cities can be applied for improvements in smart homes [
39]. In the following literature, these applications were discussed. An IoT-based sensor network consisting of distributed but connected sensors that broadcasted data to the connected nodes, which was called a cluster head, was presented in [
15]. Blockchain has gained great importance in various fields, but there are security issues. Moreover, there are challenges related to access control and performance. In an IoT-based network, data are verified through a centralized system that manages the security of the data. According to the security breach level index, millions of peoples’ data are stolen worldwide [
40]. DoS attacks, device spoofing, and Byzantine fault tolerance are some of the most prominent security breaches related to sensors and IoT-based networks. In this paper, we provided the security challenges related to sensor networks and the application of blockchain technology with integrated sensor networks [
40]. We designed a novel smart-contract-based algorithm that checks the security of the users, and if the requested users have enough rights, then access is granted; otherwise, it is denied. In this research, we replaced the central authority of the network, as the blockchain technology was integrated as a backbone of the IoT and sensor network in order to obtain the optimum privacy and cope with security issues [
41]. Blockchain technology plays a vital role in present technologies; most significantly, in the IoT, it improves a network by consolidating various sorts of sensors and things to produce connections among things without human involvement [
42]. Frequently, the devices of the IoT have restricted network storage, capacities, and computing processors. Therefore, they have more opportunities to be attacked. The reliability, security, and privacy of data are three basic issues in the field of IoT security [
43]. The blockchain-technology-based IoT supports flexible access control policies for users who want to securely access data from the IoT. Blockchain is an important technology for the administration and storage of the metadata of patients, smart healthcare, and clinician data [
36]. Recently, blockchain technology has been used to increase the applications of IoT technology. The reason is that blockchain technology contains numerous aspects that can improve the security of IoT devices, which are restricted by limited resources [
44,
45]. Dorri, Kanhere [
37] designed a lightweight scalable blockchain (LSB) framework for IoT industries. They integrated the application of a lightweight consensus mechanism in the IoT and smart homes [
14].
2.4. Smart Government
The IoT has widespread use in smart governments to ease the maintenance of policies; hence, people can easily approach the available facilities provided by the government [
46]. One application that has been implemented regarding this aspect is the improvement of smart services and reaching vital destinations [
47]. Nowadays, there are many applications in this filed of research. For example, this provides easiness to the administration of government polices and rules [
48]. First, the privacy rights of patients correspond to the access rights of materials. Doctors or professionals who have access to read a patient’s data are granted access to the patient’s health records. Using an attribute-based access control policy corresponds to a patient privacy information system or healthcare system, and the
PHR access behavior corresponds to the application of patient privacy. A user’s interaction with a healthcare system and the behavior returned by our proposed framework ultimately correspond to a patient privacy return action. Moreover, reading access corresponds to the action of reading the patient’s private data [
44]. Similarly, private patient data must be read after using the access control and security policy that were designed. The patient privacy copyright records are applied for and returned in the smart contract system, which comprises four sub-modules in the proposed system, i.e., (1) the patient module, (2) the private blockchain module, (3) the proposed smart contract module, and the (4) healthcare module. The comprehensive patient query subsystem provides management related to patient privacy copyright records and serves functions for querying and linking various systems. The blockchain subsystem includes a private blockchain for doctors and the healthcare system with patient privacy.
Table 1 shows a comparative analysis of the benchmark models.
2.5. Research Gap
The existing blockchain-based frameworks, i.e., Medrec [
49], Medblock [
50], and Medchain [
51], use blockchain for data storage. These existing techniques only focus on the storage of data. The issue with the existing approaches is that they do not provide security and privacy for users by using encryption techniques. Moreover, the computational cost of these approaches is very high due to the encryption techniques used for their implementation, and the transactions are delayed. Hence, in this paper, we provide a novel security and privacy mechanism, a ring-signature-based flexible access control framework, which provides anonymity and flexibility to its users. Moreover, our proposed framework provides access to users based on their attributes.
3. Proposed Methodology
In this section, we explain our proposed scheme. We propose and design a patient query sub-module that consists of a private blockchain sub-module, a healthcare smart contract sub-module, and a healthcare database sub-module. In our proposed framework, the patient sub-module plays a very important role and provides assistance to users for accessing patient privacy copyright records. Moreover, it serves functions for querying and linking various systems. The blockchain subsystem includes a private blockchain for doctors and healthcare systems with patient privacy.
Figure 1 shows the sub-module of the the proposed healthcare module. In
Figure 1, we describe the detailed structure of the sub-module of the system, which operates according to the following steps.
Step 1. In our proposed framework, the user first logs into the system through a blockchain application programming interface (API), and then requests the desired patient health record.
Step 2. In this step, the smart contract is triggered for the privacy check. This smart contract will check for the security and access control rights. If the applicant making the request has authorized user rights, then they are provided with access to a specific
PHR; otherwise, access is denied.
Step 3. In this step, the contract confirms that the users have eligible privacy and access control rights, and the
PHR is provided to the user.
Step 4. In this step, the authorization level is checked according to the access control policy for each participant. This depends upon the users’ access control rights; a user can read, write, delete, add, or update.
Step 5. In this step, the smart contract monitors the behavior of a patient and records the session and interaction.
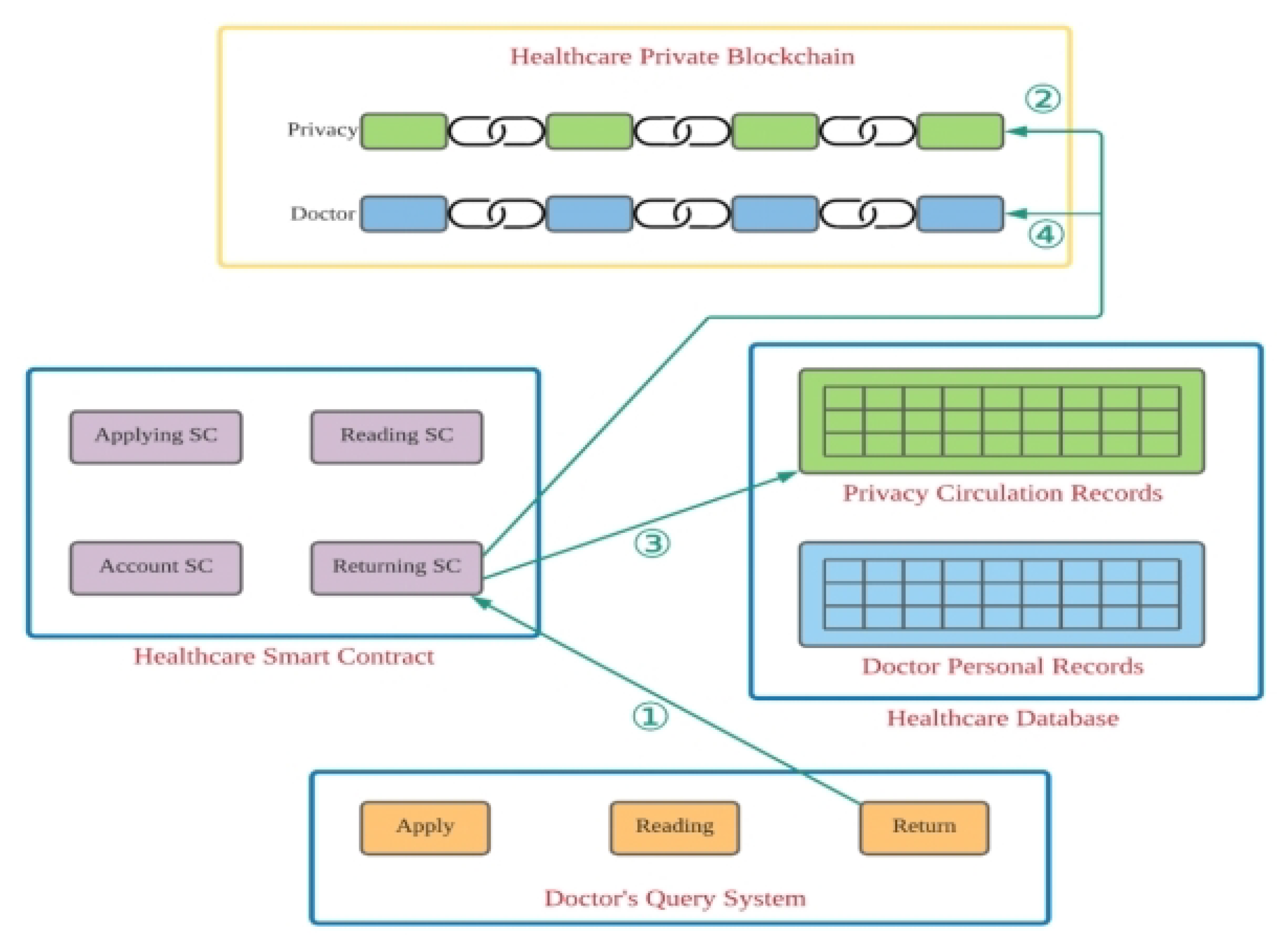
Figure 2 shows the return process of the sub-module of the framework. In the following, we explain it step by step.
Step 1. In this step, the participant first logs into our proposed system and then searches for the desired patient privacy record.
Step 2. In this step, the smart contract is triggered in order to check the privacy and access rights. The smart contract checks if the session is overdue; if it is overdue, then it is returned to the return sub-module for privacy updates.
Step 3. In this step, the smart contract updates the PHR and modifies it.
Step 4. Then, the returning smart contract performs recalculations, updates the latest status for the PHR, and maintains its privacy.
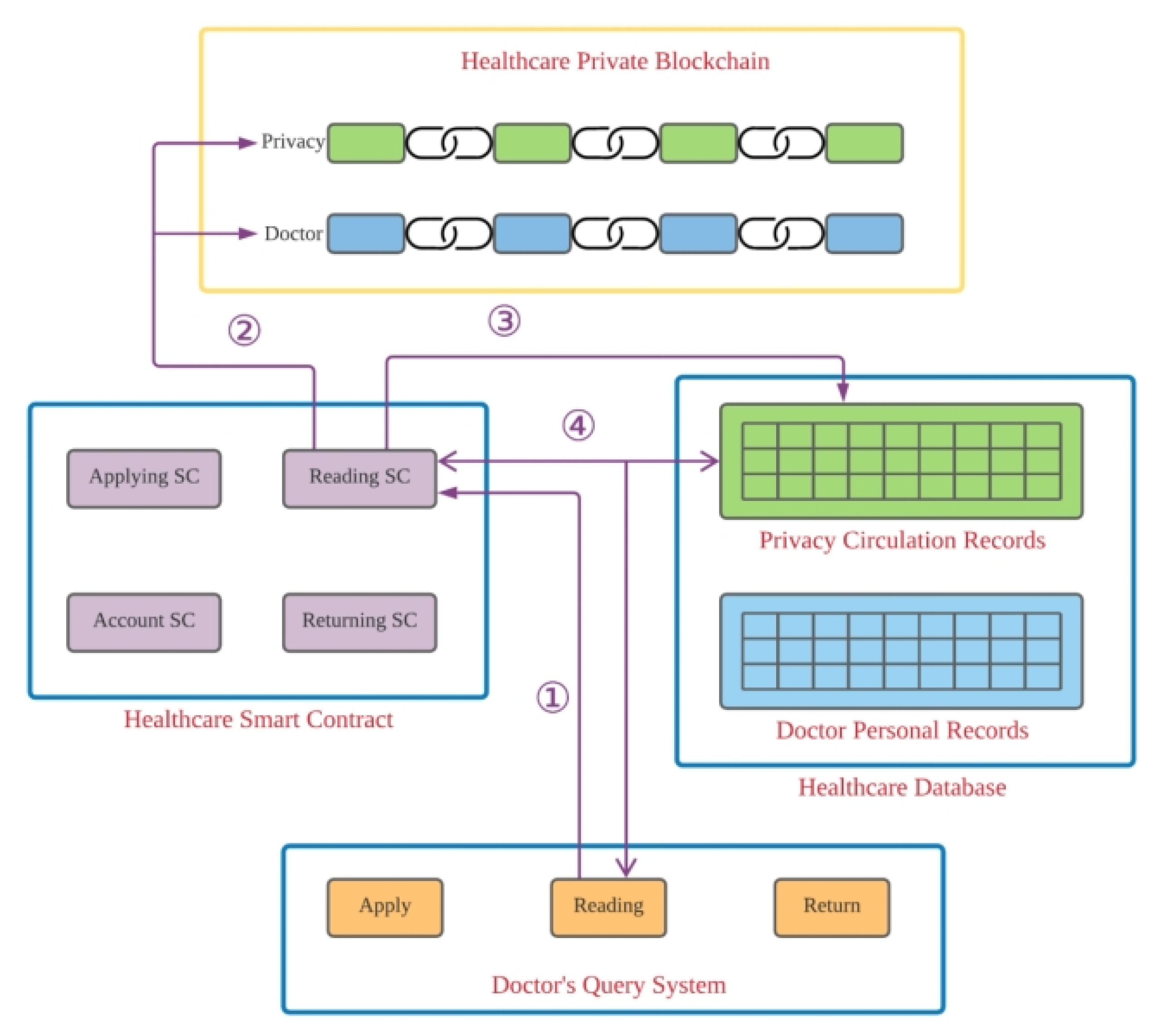
Next, we explain the reading sub-module of our proposed system. The reading process is shown in
Figure 3, and it acts according to the following steps.
Step 1. Participants first log into our proposed framework and then search for their desired PHR.
Step 2. When the smart contract for reading is triggered, it checks the privacy.
Step 3. Our proposed smart contract verifies the reading platform for privacy purposes. Then, after checking the privacy and access control rights, participants are informed that they can read the information.
Step 4. In this step, the smart contract will regularly check whether or not the usage period is still valid.
In the next sub-module, the participant checks the privacy record during the loan period. The participant can try to connect to the healthcare reading platform at any time to read the requested documents. The reading processes are explained in
Figure 3, and they use the following steps.
Step 1. Users first try to log into the system and search for the desired health records.
Step 2. The smart contract for reading is activated; it will first check the private blockchain of the healthcare system to verify the participant’s access rights.
Step 3. The reading smart contract checks the reading platform. Then, the private blockchain is connected for reading.
Step 4. During the reading process, the smart contract regularly verifies whether or not the time limit has been reached. This is clearly described in
Figure 3.
System Architecture
Figure 3 shows the system architecture, which consists of a user interface, local domain, and public domain. We can also call these a local blockchain and a global blockchain. Our proposed system architecture consists of three layers. We call this a three-layer internet topology. The first layer is the user layer, the second layer is the local domain, and the third layer is called the global domain. If a user wants to store polices in the blockchain, the smart contract is triggered according to the request. The initial block in the blockchain is known as the Genesis block. It has no previous hash address. Its hash address is considered to be zero. If the user wants to store access control policies in the local domain, then the local smart contract is triggered, and the local smart contract adds a new block in the local domain to store it. Otherwise, the global smart contract is triggered to add a new block in the global domain and store the policies.
5. Proposed Algorithms
Our proposed
PHR access control system has four types of users. These users mainly consist of administrators (
Admin), patients (
Pt), clinicians (
Cl), and lab staff (
Ls). The details of the execution of the administrative part in our proposed framework are presented in Algorithm 1. This part consists of enrollment certificates (
EC). The certification authority is responsible for the enrollment certificates. The administrative module can access the system with exclusive rights. The administrative part can read, write, update, and revoke any participants. If the physician, patients, or laboratory staff provide valid attributes, then the administrator has the right to issue a relevant
ID to each participant (authorized user) to provide access to the proposed framework. If a user’s behavior is found to be wrong, then the administrator has the right to remove that participant from the Hyperledger blockchain network with a remark. We illustrate all the notations with explanations in
Table 2.
Algorithm 2 describes the workings of the patient sub-module. To log into a patient node, the procedure is to request a private key from an administrator. After access to the blockchain network is granted, the patient can read, write, and revoke access to the PHR. In this algorithm, the module uses its attributes as the key to identifying an authorized user as a patient. In the following algorithm, CID stands for the clinician id, BN stands for the blockchain network, and UName stands for the username.
We designed new algorithms, i.e., Algorithms 3 and 4, for the encryption and access control policies. We used a ring signature in order to encrypt the
PHR. Our access control policies are based on attributes and identities. If a user meets both the identity and attribute requirements, then he/she is granted access; otherwise, access is denied. This is clearly mentioned in Algorithms 3 and 4.
| Algorithm 1: Admin Node |
- 1:
- 2:
ifthen - 3:
Add - 4:
else - 5:
Add(BN, CID) - 6:
Grant access (CID, UName, PK) - 7:
end if
|
| Algorithm 2: Patient Node |
- 1:
Input: ID and key requested from N − admin - 2:
Output: Get access to PHL transactions - 3:
Initialization: PHL should be a valid node. PHL can read/write/grant/revoke EHR records. - 4:
procedure Patient() - 5:
while (True) do - 6:
if then - 7:
if (PHL does not exist ) then - 8:
Create (, , ) - 9:
else - 10:
Update (, , ) - 11:
Read (, , , , ) - 12:
end if - 13:
else - 14:
Not() - 15:
end if - 16:
if (Visit (, , , )) then - 17:
= Medrecord - 18:
if ( PHL then - 19:
Grant records - 20:
else - 21:
(, ) ← NOTIFY(“Medical record does not exist”) - 22:
end if - 23:
if (, Treatment-Completed ()) then - 24:
Revokerecords (, , , , ) - 25:
else - 26:
(, ) ← NOTIFY (“ voluntary revoke P-ID”) - 27:
Revokerecords (, , , , ) - 28:
end if - 29:
else - 30:
Not Visit - 31:
end if - 32:
end while end procedure
|
| Algorithm 3: Attribute-Based Identification Algorithm |
- 1:
Input: Public Key - 2:
Output: Verification result: succeed or fail. - 3:
Generate a random integer r ∈ [1, ] - 4:
Compute in and convert the data type of w into a bit string - 5:
Compute integer - 6:
Compute integer ; if l = 0, go to step (2); - 7:
Compute element in - 8:
Convert the data type of h and S into a byte string, and output as the signature on message M
|
| Algorithm 4: Attribute-Based Signing Algorithm |
- 1:
Input: Master public signature key (Ppubs) of domain, system parameters of domain, message (M0), e’s identity (IDe), and digital signature (h0, S0) - 2:
Output: Verification result: succeed or fail. - 3:
Convert the data type of h0 into an integer; if h0 ∈ [1, ] does not hold, the verification fails; - 4:
Compute element t = g h0 in GT; - 5:
Compute integer h = H2(M||w, N) - 6:
Compute integer l = (r − h) mod N; if l = 0, go to step 2 - 7:
Compute integer h1 = H1(IDe||hid, N) - 8:
Compute element P = [h1]P2 + Ppubs in G2 - 9:
Compute element u = e(S0, P) in GT - 10:
Compute element w0 = u • t in GT, converts the data type of w0 into a bit string - 11:
Compute integer h2 = H2(M0||w0, N). If h2 = h0 holds, the verification succeeds. Otherwise, the verification fails
|
Authentication Mechanism
We proposed our own authentication method where we used a ring signature mechanism. An entity to be authenticated needs to prove its claimed attributes by declaring that it is eligible and its corresponding private signature key.
(1) Unilateral authentication: Only one pass is needed in unilateral authentication, where only one of the two communicating entities is authenticated by others. A simplified authentication mechanism is shown in
Figure 4. In the unilateral authentication mechanism, the authentication process is initiated by the claimant
, and it is authenticated by the verifier
. The form of
is:
=
ext
, where
X) indicates the signing on the message
X using the private signature key
of claimant
.
is a non-repeating random number that is used to prevent valid authentication information from being accepted at a later time. is not a necessary data field for authentication, but it can be added for other purposes. Claimant initiates the authentication process by sending to the verifier . Upon receiving , the verifier first ensures that it possesses a valid public key of the claimant . Then, the verifier verifies by generating a signature on the unsigned message through a further comparison with the signature received in .
(2) Mutual authentication: When two participants are mutually authenticated by each other, one more inverse pass is involved, as described in the algorithm and the mathematical equation. The form of is: = || ||Text|| ( || ||Text). After is authenticated by , the two parties exchange their roles with each other, which means that becomes the verifier and becomes the claimant. initializes another round of the authentication process and sends to the verifier . Upon receiving , the verifier first ensures that it posses a valid public key from . Then, the verifier verifies by generating a signature on the unsigned message and further compares it with the signature received in .
8. Results and Discussion
We implemented our proposed smart contract and access control policies using Node.js and the Postman web API. Similarly, we tested our simulations for concurrent requests of m with 50, 200, 400, 600, and 800 nodes. We kept the total number of requests to 800 and the total number of policies to 1100. For our initial simulation, we tested the results for 250 nodes.
Figure 8 shows the simulation results when the average authentication time took 240 ms. We set the time for authorization to 30 ms, and the ‘‘access control policy’’ took 120 ms. We also observed that our proposed policy for the delegation and revocation took 87 ms. With our proposed method and in the experiments, we achieved significant improvements by running the simulations from 200 to 800 rounds, respectively. The results are shown in
Figure 8 and
Figure 9, respectively. We also tested the proposed policies that were mentioned earlier for the number of rounds, which ranged from
50 to 800 clients. The results show that the throughput of the proposed framework increased with an increase in the number of concurrent requests. Our proposed method provides an efficient access control policy as compared to the other existing benchmark methods.
Figure 8 and
Figure 9 show that the execution time of user authentication and policy creation was not affected much by the increase in the number of policies. However, the user authorization time and policy revocation time increased due to the increase in the time required to search for a specific policy in a long chain of policies. We also performed experiments for the user authentication, authorization, and delegation policies. We further divided our policies into creation and revocation operations. We evaluated our experiments for the same requests and ran the simulations from
0 to 4000 concurrent requests.
N shows the total number of concurrent requests. The total number of delegation policies was kept constant, i.e.,
. Initially, 500 concurrent virtual client requests were tested. The average authentication time took 240 ms, the authorization time took 30 ms, the “delegation policy” creation time took 120 ms, and the “delegation policy” revocation time took 87 ms. Then, the experiment was repeated for
200, 400, 600, and 800, as shown in
Figure 9.
Figure 10 and
Figure 11 describe the encryption and decryption time taken for different formats of electronic health records. From
Figure 10, it is clear that the increase is not significant if we increase the file size to 864 kb, while more time is taken if the
size increases to 4329 MB. Taking the encryption time into account, we used the ring signature for the encryption and decryption, which was shown to take less time compared to the group signature and traditional signature methods. Moreover, we also conducted an analysis of the encryption and decryption time for three different formats—Malay, English, and Urdu. It took much less time if the file was in the Malay language. However, the average encryption and decryption time for these three formats remained the same when using the ring signature.
In
Figure 12, we provide an experimental analysis of the number of evaluation reports for the executions carried out for each evaluation request. We kept the number of evaluation requests between 10 and 90. In
Figure 13, we provide the simulation results for the amount of throughput with respect to the number of evaluation requests and number of blocks transferred.
Figure 13 presents the simulation results for the execution throughput for 20 matched evaluation requests.
Figure 13 shows that, for 10 and 30 evaluations, the percentage of confirmed transactions was same, and this proved that our proposed framework provides high throughput in the cases of 10, 30, and 50 evaluation requests under cross-domain conditions. It can also be observed that our proposed framework has some limitations at the initial stage, i.e., for large numbers of evaluation requests the throughput is affected more, as shown by the yellow line.
Figure 10 presents the number of dead nodes and the number of rounds for our proposed framework. We ran our simulations for 2500 rounds, and the number of dead nodes reached 100. In this case of sensors deployed in a healthcare system, we can see that our proposed smart contracts provide better efficiency because we observed that for 100 sensor nodes, the number of rounds can reach 1200.
We also evaluated our proposed framework for the number of packets sent to the base station and the number of rounds. The X-axis represents the number of rounds (
N), and the Y-axis represents the number of packets sent to the cluster head. It is very clear in
Figure 11 that with 2500 rounds, the number of packets sent is 8000. This shows the greater efficiency compared to the benchmark models in the literature.
Figure 12 presents the number of rounds and the number of packets sent to the cluster head (
) when using medical sensors to gather patient data through the blockchain. We ran our transactions with up to 2500 rounds and evaluated the performance of our proposed system; we found that our system performed efficiently for the maximum number of rounds by sending
and
to the cluster heads.
In
Figure 13, we provide a comparative analysis our proposed framework with the benchmark models when embedded with medical sensors. The benchmark models taken in this case are Medrec and Medblock, which are blockchain-based technologies. From these simulations, we can see that the number of dead nodes in the case of our proposed framework is less than those of the benchmark models. For the same number of dead nodes, our proposed framework delivers more transactions. Hence, this justifies that our proposed approach is more efficient in terms of throughput.
Figure 14 provides the simulation results for the number of live sensor nodes based on our proposed framework and the benchmark models. It is evident from Figure 18 that, for the same delay and transaction endorsement time, the number of live nodes is greater than those of the benchmark models. With this comparative analysis, it is proved that our proposed approach is better than the benchmark models for the use of blockchain for
.
Figure 15 provides a classification of users interactions with our proposed method. We used machine learning techniques, such as K-nearest neighbors (KNN), to classify users according to their behaviors and interactions. We set a threshold value of trust, which was 1.0, and if a user’s interaction with the system is good enough, then the system would provide a value of 1; otherwise, this would be 0.5 or 1. We divided the participants into three major groups based on the classification of their interactions. This provided more security and alerts regarding trust and access to the
. For the number of rounds and cluster head selection, we used the following equations:
The mathematical model above consists of four equation, and it describes the cluster head selection based on the remaining energy from the live nodes. We used the following KNN technique to classify the users into different groups.
Here, in the euclidean distance equation, which is denoted by , and represent the two groups of datasets.
In
Figure 16, we present a comparative analysis of our proposed scheme with respect to the benchmark models. In
Figure 16a, we present a comparison of our proposed framework and the benchmark models in terms of the number of dead nodes and the time for execution taken by each framework for various policies and transactions. It can be easily observed that our proposed framework performs better than the benchmark models [
49,
50]. Moreover
Figure 16b shows the simulation results for the number of dead nodes and the time for execution taken by each framework for concurrent access control policies. The greater the number of live nodes is, the greater the efficiency of the framework will be. In addition, in
Figure 16c, we show our comparative analysis based on the number of packets sent versus the execution time for each sent packet. From
Figure 16c, it is evident that our proposed framework has significant improvements over the benchmark models [
49,
51]. The equations for the number of dead and live nodes are as follows:
So, the energy of all nodes in the blockchain-based network will be equal:
In the above equation, E represents the energy and Adv represents the advance nodes’ energy. Int represents the intermediate nodes’ energy, whereas n represents the normal nodes.
In
Figure 17, we provide the simulation results for the number of transactions sent versus the number of
transferred per transaction. From the simulations, it is very clear that the proposed framework provides more efficiency compared to the benchmark model with respect to
.
In
Figure 18, we provide a comparative analysis of the proposed method for different domains while using sensors to monitor health records and share them through a blockchain network. We used medial sensors, such as sensors for the pulse and heartbeat, as well as temperature sensors. Each sensor collected data and sent it to the base station using smart contracts. The smart contracts delivered the transmitted patient data to the BS, and then they were stored in the blockchain ledger. We can easily observe from the simulations that the sending of packets through our proposed framework in the case of medical sensor nodes took less time for confirmation; hence, the throughput was significantly greater than that of the benchmark models.
In
Figure 19, we show the intensive simulations and experiments carried out in the cross-domain case. We used different types of domains, and we evaluated the number of query requests versus the time taken. It can be observed that, as we used lightweight encryption techniques with flexible access control policies, the throughput in the cross-domain case was very efficient. From
Figure 19, it is very clear that our proposed framework can provide efficient throughput up to 70 domains. Our proposed framework is thus limited to 70 domains. In comparison, Medrec and Medchain can support up to 8 and 10 domains, respectively. Hence, our method surpasses the previous schemes because they can only support 8 to 10 domains. So, in order to provide more security for patients, they can only access data,
, or
in up to 70 domains.
In
Figure 20, we provide the cumulative simulations and comparative analyses of our proposed framework and the benchmark models. We used different scenarios and parameters, such as dead nodes, live nodes, sensor energy, and throughput, to evaluate the efficiency and security of the proposed framework.
selection was performed on a probabilistic basis; each node generated a random number
r, which was inclusive of 0 and 1. If the value was less than the threshold value, then it was considered as a cluster head (
). Threshold formula is given below:
In these mathematical equations,
P represents the power of the sensor node.
represents the transmission power through a sensor nodes.
N represents the number of nodes.
is a constant value used for the delay in the transactions. In
Figure 20, we justify the efficiency and throughput of our proposed framework and the benchmark models [
49,
50,
51]. The number of rounds in
Figure 20 ranges up to 300, and the total number of packets sent is 8000. From
Figure 20, it can be observed that by using our proposed framework and the smart contracts that we have proposed, more packets can be sent within the same number of rounds in comparison with the benchmark models [
49,
50,
51].
Figure 21 represents the simulation results for the comparative analysis of the proposed framework and the benchmark models. We carried out a comparison of the number of rounds and the number of transactions. From
Figure 21, it is clear that the number of transactions sent with the proposed method was greater than that with the benchmark models. Through the proposed smart contracts, the delay was comparatively small, and hence, this led to a greater number of transactions with the sink.
Figure 22 shows a comparison based on the number of dead nodes versus the number of rounds. The simulation results show that the number of dead nodes is lower compared to those obtained with Medrec, Medchain, and Medblock.
Figure 23 presents the number of rounds and number of live rounds based on simulations. We carried out our experiments for up to 300 rounds, and the value of the number of live nodes reached 5000. From the simulations, it is evident that for a specific number of rounds, the number of live nodes is greater with the proposed method. Hence, our proposed framework provides more efficiency compared to the benchmark models.