A Robust Framework for MADS Based on DL Techniques on the IoT
Abstract
:1. Introduction
- The proposed solution is a robust MADS based on LSTM Autoencoder that has the capabilities to detect malware and gets a high accuracy, called RoMADS.
- RoMADS model performance was evaluated and we compared its results with the previous research results in this field.
- RoMADS model is distinguished by its ability to extract the features of data and reduce dimensions.
- It is also distinguished by its ability to take sequential data which has a different or fixed length. This is appropriate for the nature of the data in the IoT environments.
- RoMADS framework helps to take advantage of the devices currently on the market and adapt them to benefit from them in the IoT environments, which contributes to the rapid spread of the IoT and the increased dependence on it.
- RoMADS model contributes to saving time and energy consumption, as it checks every device that wants to enter the IoT network and converts its traditional protocol to the IoT protocol if need. Also, RoMADS framework depends on the fog computing architecture that is based on the principle of distributing the processing, which helps to reduce the time and energy consumption.
2. Background
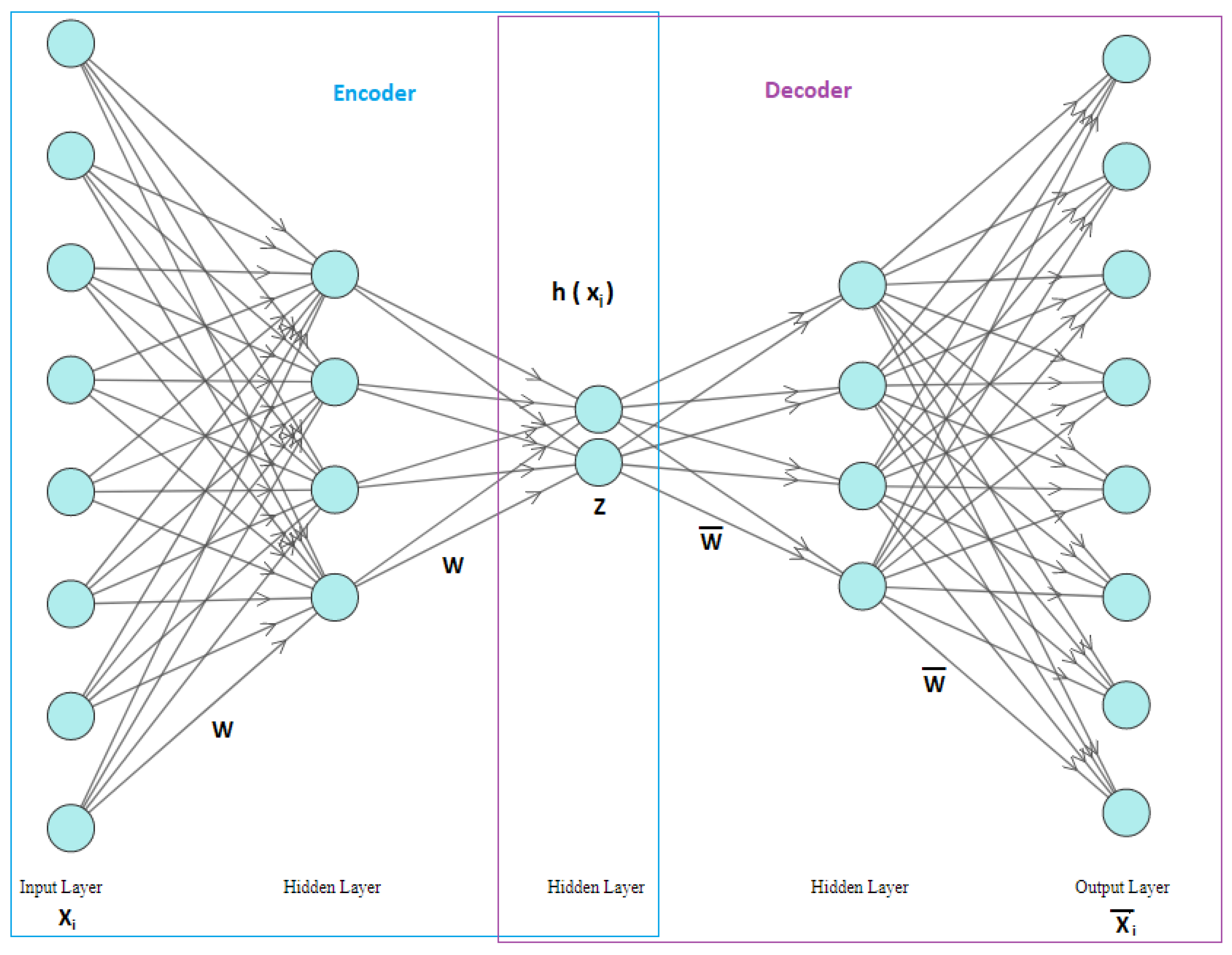
2.1. Autoencoders
- Inputs layer, the original data is entered from input layer.
- Outputs layer, the reconstructed data comes out through the output layer.
- Hidden layers, it contains several layers.
- Encoder:
- b.
- Bottleneck
- c.
- Decoder
- d.
- Reconstruction Loss
2.2. LSTM
- Forget gate (ft) (a sigmoid layer)
- b.
- Input gate
- ◦
- Input gate layer (it) (a sigmoid layer):
- ◦
- A tanh layer
- c.
- Output gate
- ◦
- Output gate layer (ot) (a sigmoid layer):
- ◦
- A tanh layer:
- d.
- Cell state
3. Literature Review
IoT Malware Attacks
- The first phase: scan and takeover
- b.
- The second phase: attack launch
- i.
- DoS Attack
- ii.
- Spam Bots Attack
- iii.
- Brickers Attack
- iv.
- Cryptomining Bots Attack
- v.
- TimpDoor Attack
- vi.
- DeepLocker Attack
- vii.
- Mirai Attack
4. Methodology
4.1. Data Set
- DS2OS Data Set
4.2. Data Processing & Cleaning
4.3. Feature Selection
4.4. Experiment Environment
5. Proposed Solution
5.1. RoMADS Architecture
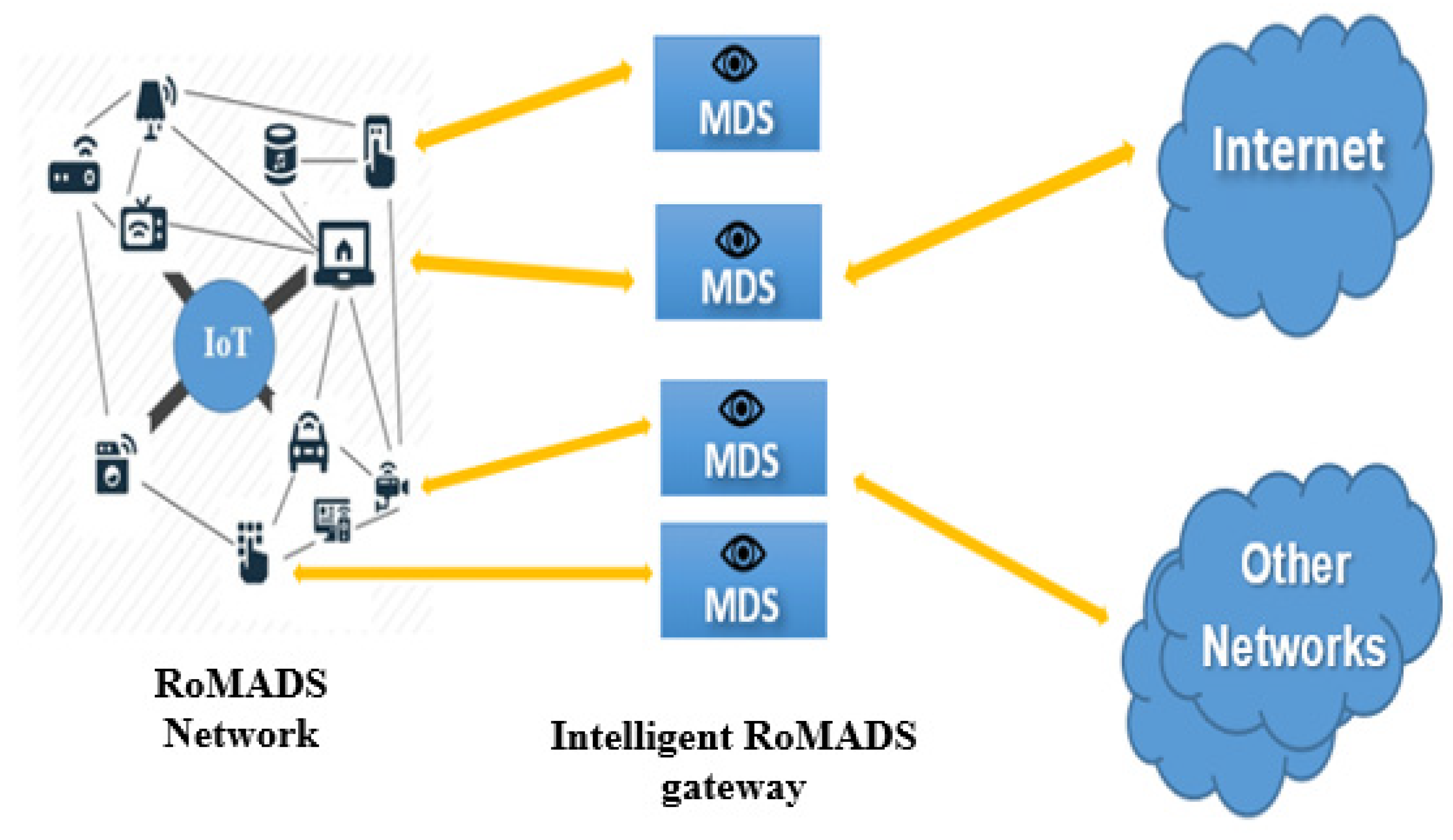
5.2. RoMADS Network
Intelligent RoMADS Gateways
5.3. RoMADS Devices
- Devices that need a high level of security because they contain sensitive data and critical user information, such as the following: passwords, user personal information, or financial information.
- Devices that need security but less than the previous one, because they do not contain any sensitive data or information.
- (a)
- High-level security (MDS + Encryption mechanism)
- ◦
- Embedded:
- ◦
- IoT Security Anchor Point (SAP):
- (b)
- Security (MDS)
5.4. RoMADS MDS Based on LSTM Autoencoder
- i.
- In LSTM encoders phase
- ii.
- In LSTM Decoders phase
6. Performance Criteria
- Model Accuracy
- True Positive (TP),
- True Negative (TN),
- False Positive (FP),
- False Negative (FN).
- b.
- Detection Rate of Malware
- c.
- Recall
- d.
- Precision
- e.
- F1-Score
- f.
- Error Rate
- ◦
- MAE
- ◦
- MSE
- ◦
- RMSE
7. Smart City Scenarios
- A.
- First Scenario: Secured RoMADS Network
| Algorithm 1: Data come from external networks to IoT network. |
| Input: Output: Malware or Normal -Data X enter to Intelligent IoT gateway { -X enter to MDS { -LSTM Encoder { -Features extraction, -Reduce the dimensions, -Fixed length } -Get latent space representation Z -LSTM Encoder { -Reconstruction of the data } -Calculation of the reconstruction error -If S > our set threshold -This is Malware { -Issuing the alarm until it is prevented from entering. -Take benefit from the features of malware that are targeted IoT in research and studies. } -Else -Normal { -Are the protocols compatible with IoT systems? { -Yes { -Cross the intelligent IoT gateway and enter the IoT network. } -No { -Convert its protocols into IoT protocols. { -Cross the intelligent IoT gateway and enter the IoT network. } } } } } } |
- B.
- Second Scenario: Secured RoMADS Device
| Algorithm 2: Data come from another IoT device in same IoT network. |
| Input: Output: Malware or Normal -Is the device built with a security layer that contains the malware detection system? { -Yes { - Continue, } -No { - Connect device to IoT SAP, - Continue, } -X enter to MDS { -LSTM Encoder { -Features extraction, -Reduce the dimensions, -Fixed length } -Get latent space representation Z -LSTM Encoder { -Reconstruction of the data } -Calculation of the reconstruction error -If S > our set threshold -This is Malware { -Issuing the alarm until it is prevented from entering. -Take benefit from the features of malware that are targeted IoT in research and studies. } -Else -Normal { -Connect to other IoT device. } } } |
8. Experiment Results and Discussion
8.1. Simulation Assumptions
8.2. Simulation Scenario
- Communication Objects: It is a term referring to the communication between the smartphone, the smart refrigerator, the smart supermarket system, as well as the bank to deduct the amount.
- Smartphone: RoMADS MDS is integrated on the same device because it is considered a smart device with high capabilities. The Smartphone may become connected to the same network with the smart refrigerator or any other network.
- Smart Refrigerator: RoMADS MDS is not integrated in the same device because of the smart refrigerator’s lack of security mechanisms. So, it connects to the IoT SAP for security mechanisms. It may become connected to the same network with the smartphone or any other network.
- Smart Supermarket System: The smart supermarket has its own IoT network, which contains smart RoMADS gateways with RoMADS MDS built into it. So, anything that has already been examined and checked is allowed to enter the IoT network or communicate with it.
- The Bank and Credit Card Information: The bank has its own IoT network, which contains smart RoMADS gateways with RoMADS MDS built into it. So, anything that has been already examined and checked is allowed to enter the IoT network or communicate with it. All users’ information must be fully encrypted and connected with a strong authentication software to ensure the user’s identity, and to make sure that they will not be breached or violated. This kind of network is classified among the highest level of security in our framework.
8.3. Case Study
8.4. Simulation Environment
8.5. Result and Discussion
9. Conclusions
- (1)
- It presents the state-of-the-art research and studies related to our study.
- (2)
- Proposed a solution based on DL techniques which is RoMADS framework, in order to improve the security and protection from malware.
- (3)
- Presented RoMADS framework architecture that combines fog computing architecture with IoT social architecture. The fog computing architecture gives RoMADS framework the concept of distrusting the load on a number of smart gateways and smart sensors, which contributes to improving the time consuming aspect. The IoT social architecture works in a similar manner to the social relations between humans and, consequently, puts preventive security measures accordingly. This helps in improving the performance of real-time systems.
- (4)
- To reduce the energy and time consumed, RoMADS framework checks and converts the traditional protocols to IoT protocols for all the packages coming to the IoT system.
- (5)
- RoMADS framework has the ability to deal with the sequential of data with different lengths. It works to reduce the dimensions, remove the noise, and extract the main features.
- (6)
- RoMADS framework has the ability to remember and store the important features of data for a long time, which contributes to obtaining an intelligent model that has a high capacity of detection, understanding, and analysis.
- (7)
- RoMADS framework helps to exploit the devices currently available on markets by adapting and exploiting them in IoT environments. This helps to speed up the transition to smart IoT environments, which provides a comfortable and healthy life for humanity.
- (8)
- RoMADS model results were as follows: 99.03% for Accuracy, 99.99% for Recall & Detection rate, 99.00% for F1-Score, 99.04% for Precision, 0.0096% for MAE, 0.0096 for MSE, and 0.0980 for RMSE.
- (9)
- The RoMADS model experiment results surpassed eighteen models of previous research works related to this field. RoMADS framework is scalable, evolvable, and adaptable when it is applied in different real IoT environments.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| Ref. | References |
| MDS | Malware Detection System |
| ADS | Anomaly Detection System |
| ML | Machine Learning |
| ANN | Artificial Neural Network |
| CNN | Convolutional Neural Network |
| Ars | Association Rules |
| DL | Deep Learning |
| DBN | Deep Belief Network |
| DNN | Deep Neural Network |
| LSTM | Long Short-Term Memory |
| GAN | Generative Adversarial Network |
| KNN | K-Nearest Neighbor |
| NB | Naive Bayes |
| PCA | Principal Component Analysis |
| SAEs | Neural Network-Stacked AutoEncoders |
| RNN | Recurrent Neural Network |
| SVMs | Support Vector Machines |
| LSTM | Long Short-Term Memory |
| MAE | Mean Absolute Error |
| MSE | Mean Square Error |
| RMSE | Root Mean Square Error |
| DT | Decision Tree |
References
- Talal, H.; Zagrouba, R. MADS Based on DL Techniques on the Internet of Things (IoT): Survey. Electronics 2021, 10, 2598. [Google Scholar] [CrossRef]
- Thalesgroup. IoT Security Issues in 2021: A Business Perspective. 2021. Available online: https://www.thalesgroup.com/en/markets/digital-identity-and-security/iot/magazine/internet-threats (accessed on 16 August 2021).
- Balogh, S.; Gallo, O.; Ploszek, R.; Špaček, P.; Zajac, P. IoT Security Challenges: Cloud and Blockchain, Postquantum Cryptography, and Evolutionary Techniques. Electronics 2021, 10, 2647. [Google Scholar] [CrossRef]
- Kaspersky IoT Under Fire: Kaspersky Detects More Than 100 Million Attacks on Smart Devices in H1 2019. Available online: https://www.kaspersky.com/about/press-releases/2019_iot-under-fire-kaspersky-detects-more-than-100-million-attacks-on-smart-devices-in-h1-2019 (accessed on 8 June 2021).
- Cisco What Is Malware? 2020. Available online: https://www.cisco.com/c/en/us/products/security/advanced-malware-protection/what-is-malware.html (accessed on 20 June 2021).
- Rouse, M. What Is Malware? 2019. Available online: https://searchsecurity.techtarget.com/definition/malware (accessed on 18 June 2021).
- Goodfelow, I.; Bengio, Y.; Courville, A. Autoencoders. In Deep Learning; MIT Press: Cambridge, MA, USA, 2016; pp. 499–523. [Google Scholar]
- Ciha, T. PCA Autoencoders: Algorithms Everyone Can Understand. Towards Data Science. 2018. Available online: https://towardsdatascience.com/understanding-pca-autoencoders-algorithms-everyone-can-understand-28ee89b570e2 (accessed on 20 August 2021).
- Badr, W. Auto-Encoder: What Is It? And What Is It Used for? (Part 1). Towards Data Science. 2019. Available online: https://towardsdatascience.com/auto-encoder-what-is-it-and-what-is-it-used-for-part-1-3e5c6f017726 (accessed on 20 June 2021).
- Dertat, A. Applied Deep Learning—Part 3: Autoencoders. Towards Data Science. 2017. Available online: https://towardsdatascience.com/applied-deep-learning-part-3-autoencoders-1c083af4d798 (accessed on 21 June 2021).
- Luo, T.; Nagarajan, S.G. Distributed Anomaly Detection Using Autoencoder Neural Networks in WSN for IoT. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Stewart, M. Comprehensive Introduction to Autoencoders. Towards Data Science. 2019. Available online: https://towardsdatascience.com/generating-images-with-autoencoders-77fd3a8dd368 (accessed on 25 August 2021).
- Missinglink. Deep Learning Long Short-Term Memory (LSTM) Networks: What You Should Remember. Available online: https://missinglink.ai/guides/neural-network-concepts/deep-learning-long-short-term-memory-lstm-networks-remember/ (accessed on 18 August 2021).
- Olah, C. Understanding LSTM Networks. 2015. Available online: http://colah.github.io/posts/2015-08-Understanding-LSTMs/ (accessed on 16 August 2021).
- Chawla, A.; Lee, B.; Jacob, P.; Fallon, S. Bidirectional LSTM Autoencoder for Sequence Based Anomaly Detection in Cyber Security. Int. J. Simul. Syst. Sci. Technol. 2019, 1–6. [Google Scholar] [CrossRef]
- Kapur, R.; Rohan, L. Recurrent Neural Networks & LSTMs. Ayearofai. 2017. Available online: https://ayearofai.com/rohan-lenny-3-recurrent-neural-networks-10300100899b (accessed on 11 August 2021).
- Srivastava, P. Essentials of Deep Learning: Introduction to Long Short Term Memory. 2017. Available online: https://www.analyticsvidhya.com/blog/2017/12/fundamentals-of-deep-learning-introduction-to-lstm/ (accessed on 10 August 2021).
- Korneev, E. LSTM Neural Networks for Anomaly Detection Medium. 2018. Available online: https://medium.com/datadriveninvestor/lstm-neural-networks-for-anomaly-detection-4328cb9b6e27 (accessed on 25 June 2021).
- Larzalere, B. LSTM Autoencoder for Anomaly Detection. Towards Data Science. 2019. Available online: https://towardsdatascience.com/lstm-autoencoder-for-anomaly-detection-e1f4f2ee7ccf (accessed on 23 June 2021).
- Vacca, J.R. Network and System Security; Elsevier: Amsterdam, The Netherlands, 2014. [Google Scholar]
- Perry, J.S. Anatomy of an IoT Malware Attack IBM. 2019. Available online: https://developer.ibm.com/articles/iot-anatomy-iot-malware-attack/ (accessed on 6 July 2021).
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Malge, S.; Singh, P. Internet of Things IoT: Security Perspective. Int. J. Trend Sci. Res. Dev. 2019, 1041–1043. [Google Scholar] [CrossRef] [Green Version]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT Security Techniques Based on Machine Learning: How Do IoT Devices Use AI to Enhance Security? IEEE Signal Process. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]
- Xiao, F.; Lin, Z.; Sun, Y.; Ma, Y. Malware Detection Based on Deep Learning of Behavior Graphs. Math. Probl. Eng. 2019, 2019, 8195395. [Google Scholar] [CrossRef] [Green Version]
- Dovom, E.M.; Azmoodeh, A.; Dehghantanha, A.; Newton, D.E.; Parizi, R.M.; Karimipour, H. Fuzzy pattern tree for edge malware detection and categorization in IoT. J. Syst. Arch. 2019, 97, 1–7. [Google Scholar] [CrossRef]
- Cui, Z.; Du, L.; Wang, P.; Cai, X.; Zhang, W. Malicious code detection based on CNNs and multi-objective algorithm. J. Parallel Distrib. Comput. 2019, 129, 50–58. [Google Scholar] [CrossRef]
- Ham, H.-S.; Kim, H.-H.; Kim, M.-S.; Choi, M.-J. Linear SVM-Based Android Malware Detection. Lect. Notes Electr. Eng. 2014, 301, 575–585. [Google Scholar] [CrossRef]
- Alam, M.S.; Vuong, S.T. Random Forest Classification for Detecting Android Malware. In Proceedings of the 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, Beijing, China, 20–23 August 2013; pp. 663–669. [Google Scholar]
- Vinayakumar, R.; Alazab, M.; Srinivasan, S.; Pham, Q.-V.; Padannayil, S.K.; Simran, K. A Visualized Botnet Detection System Based Deep Learning for the Internet of Things Networks of Smart Cities. IEEE Trans. Ind. Appl. 2020, 56, 4436–4456. [Google Scholar] [CrossRef]
- Aubet, F.-X. DS2OS Traffic Traces Kaggle. 2018. Available online: https://www.kaggle.com/francoisxa/ds2ostraffictraces/ (accessed on 20 July 2021).
- Pedregosa, F. Scikit-learn: Machine Learning in Python. J. Mach. Learn. Res. 2011, 12, 2825–2830. [Google Scholar]
- Zipporah Luna Feature Selection in Machine Learning: Correlation Matrix, Univariate Testing, RFECV Medium 2021. Available online: https://medium.com/geekculture/feature-selection-in-machine-learning-correlation-matrix-univariate-testing-rfecv-1186168fac12 (accessed on 15 September 2021).
- Google. Google Colaboratory. 2020. Available online: https://colab.research.google.com/notebooks/welcome.ipynb (accessed on 25 July 2021).
- Derhamy, H.; Eliasson, J.; Delsing, J.; Priller, P. A survey of commercial frameworks for the Internet of Things. In Proceedings of the 2015 IEEE 20th International Conference on Emerging Technologies & Factory Automation (ETFA 2015), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The Social Internet of Things (SIoT)—When social networks meet the Internet of Things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Gregersen, C. A Complete Guide to IoT Protocols & Standards in 2021. 2020. Available online: https://www.nabto.com/guide-iot-protocols-standards/ (accessed on 25 August 2021).
- Ranjan, C. LSTM Autoencoder for Extreme Rare Event Classification in Keras. Towards Data Science. 2019. Available online: https://towardsdatascience.com/lstm-autoencoder-for-extreme-rare-event-classification-in-keras-ce209a224cfb (accessed on 5 July 2021).
- Ranjan, C.; Reddy, M.; Mustonen, M.; Paynabar, K.; Pourak, K. Dataset: Rare Event Classification in Multivariate Time Series. arXiv 2018, arXiv:1809.10717. [Google Scholar]
- Brownlee, J. A Gentle Introduction to LSTM Autoencoders. Machine Learning Mastery. 2018. Available online: https://machinelearningmastery.com/lstm-autoencoders/ (accessed on 15 July 2021).
- Baranwal, V.M.A.; Bagwe, B.R. Machine Learning in Python: Diabetes Prediction Using Machine Learning. In Handbook of Research on Applications and Implementations of Machine Learning Techniques; IGI Global: Hershey, PA, USA, 2019. [Google Scholar]
- Hartson, R.; Pyla, P. Chapter 28—Background: UX Evaluation. In The UX Book, 2nd ed.; Hartson, R., Pyla, P., Eds.; Morgan Kaufmann: Boston, MA, USA, 2019; pp. 601–621. [Google Scholar]
- Yunqian, M.; Haibo, H. Imbalanced Learning: Foundations, Algorithms, and Applications, 1st ed.; Wiley-IEEE Press: Hoboken, NJ, USA, 2013. [Google Scholar]
- Pascual, C. Understanding Regression Error Metrics in Python Data Quest 2018. Available online: https://www.dataquest.io/blog/understanding-regression-error-metrics/ (accessed on 20 September 2021).
- Kampakis, S. Performance Measures: RMSE and MAE. The Data Scientist. 2020. Available online: https://thedatascientist.com/performance-measures-rmse-mae/ (accessed on 20 September 2021).
- Yuan, Z.; Lu, Y.; Xue, Y. Droiddetector: Android malware characterization and detection using deep learning. Tsinghua Sci. Technol. 2016, 21, 114–123. [Google Scholar] [CrossRef]
- Villanueva, J.A.; Juanatas, R.; Lacatan, L.L. Malware predictor using machine learning techniques. Test Eng. Manag. 2020, 82, 5665–5674. [Google Scholar]
- Adamu, U.; Awan, I. Ransomware Prediction Using Supervised Learning Algorithms. In Proceedings of the 2019 7th International Conference on Future Internet of Things and Cloud (FiCloud), Istanbul, Turkey, 26–28 August 2019; pp. 57–63. [Google Scholar]
- Adebayo, O.S.; Aziz, N.A. Improved Malware Detection Model with Apriori Association Rule and Particle Swarm Optimization. Secur. Commun. Netw. 2019, 2019, 2850932. [Google Scholar] [CrossRef] [Green Version]
- HaddadPajouh, H.; Dehghantanha, A.; Khayami, R.; Choo, K.-K.R. A deep Recurrent Neural Network based approach for Internet of Things malware threat hunting. Future Gener. Comput. Syst. 2018, 85, 88–96. [Google Scholar] [CrossRef]
- Su, J.; Vasconcellos, V.D.; Prasad, S.; Daniele, S.; Feng, Y.; Sakurai, K. Lightweight Classification of IoT Malware Based on Image Recognition. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018; Volume 2, pp. 664–669. [Google Scholar] [CrossRef] [Green Version]
- Kim, J.-Y.; Bu, S.-J.; Cho, S.-B. Zero-day malware detection using transferred generative adversarial networks based on deep autoencoders. Inf. Sci. 2018, 460–461, 83–102. [Google Scholar] [CrossRef]
- Azmoodeh, A.; Dehghantanha, A.; Conti, M.; Choo, K.-K.R. Detecting crypto-ransomware in IoT networks based on energy consumption footprint. J. Ambient. Intell. Humaniz. Comput. 2018, 9, 1141–1152. [Google Scholar] [CrossRef]
- Agrawal, R.; Stokes, J.W.; Selvaraj, K.; Marinescu, M. Attention in Recurrent Neural Networks for Ransomware Detection. In Proceedings of the ICASSP 2019—2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brighton, UK, 12–17 May 2019; pp. 3222–3226. [Google Scholar]
- Vinayakumar, R.; Alazab, M.; Soman, K.P.; Poornachandran, P.; Venkatraman, S. Robust Intelligent Malware Detection Using Deep Learning. IEEE Access 2019, 7, 46717–46738. [Google Scholar] [CrossRef]
- Yuxin, D.; Siyi, Z. Malware detection based on deep learning algorithm. Neural Comput. Appl. 2017, 31, 461–472. [Google Scholar] [CrossRef]
- Cui, Z.; Xue, F.; Cai, X.; Cao, Y.; Wang, G.-G.; Chen, J. Detection of Malicious Code Variants Based on Deep Learning. IEEE Trans. Ind. Inform. 2018, 14, 3187–3196. [Google Scholar] [CrossRef]
- Rhode, M.; Burnap, P.; Jones, K. Early-stage malware prediction using recurrent neural networks. Comput. Secur. 2018, 77, 578–594. [Google Scholar] [CrossRef]


























| Ref. | Proposed Solutions | Techniques | ML/DL | Detection Approaches | Dataset | Scalability | Result |
|---|---|---|---|---|---|---|---|
| [25] | MDS based on DL called BDLF, which combines behavior graphs of API calls with the SAEs model. | SAEs, DT, KNN, NB, and SVM | DL, ML | Anomaly | Collected the dataset sample by VX Heaven | The system is scalable due to its dependence cloud | The results of the experiment showed an improvement in the detection precision of the model. |
| [26] | Using Fuzzy pattern and the fast Fuzzy pattern for MDS | Fuzzy pattern | ML | Anomaly | They used four datasets, which are IoT, Vx-Heaven, Kaggle, and Ransomware | - | they have proven the effectiveness of their proposed. |
| [27] | Converting the binary codes of the malware into images | CNN | DL | Anomaly | Malware image data from Vision Research Lab | - | High accuracy and low loss ratio |
| [28] | Building a MDS for Android devices based on SVM | SVM | ML | Anomaly | Create dataset using application in the actual mobile environment | - | The results proved outperforms other ML techniques. |
| [29] | Building a MDS for Android devices | Random Forest algorithm | ML | Anomaly | Antimalware dataset | - | Their model has yielded promising results |
| [30] | A framework that is a botnet detection system based on two-level DL framework. The first level is responsible for similarity measures in the DNS services based on a predefined threshold to deter the most common DNS information over Ethernet connections. In the second level, they proposed to add an algorithm for a domain generation depending on DL architectures to use it for classifying the domain names into normal and abnormal ones. | Number of DL techniques | DL | Anomaly | The similarity checker dataset is called DS1, and the DGA detection dataset is called DS2. | Highly scalable due to use the DNS big data. | The result of their experiment ensured the improvements in detection rate, F1-score, and false alarm rate. |
| Features | Type |
|---|---|
| sourceID | String [] |
| sourceAddress | String [] |
| sourceType | String [] |
| sourceLocation | String [] |
| destinationServiceAddress | String [] |
| destinationServiceType | String [] |
| destinationLocation | String [] |
| accessedNodeAddress | String [] |
| accessedNodeType | String [] |
| operation | String [] |
| value | String [] |
| timestamp | Integer [] |
| normality | String [] |
| Features | Type | Description |
|---|---|---|
| sourceID | String [] | The ID of the source. |
| sourceAddress | String [] | The Address of the source. |
| destinationServiceAddress | String [] | The Address of the destination Service. |
| accessedNodeAddress | String [] | The Address of the accessed Node. |
| value | String [] | The value of the package. |
| normality | String [] | This column contains normal and six different types of malware. We used it as a target column. |
| Ref. | Classifier | Accuracy (%) | Recall & Detection Rate (%) | F1-Score (%) | Precision (%) | Error Value | ||
|---|---|---|---|---|---|---|---|---|
| MAE | MSE | RMSE | ||||||
| [25] | SAE-DT | - | 99.2 | 98.9 | 98.6 | - | - | - |
| [46] | DBN | 96.76 | 97.84 | - | 95.77 | - | - | - |
| [47] | Random forst | 89.03 | 98.0 | 94.2 | 98.0 | 0.1097 | - | - |
| [47] | SVM | 85.43 | 85.5 | 85.4 | 85.3 | 0.1532 | - | - |
| [48] | ANN | 86.0 | - | - | - | - | 0.041 | 0.202 |
| [49] | Neural Network | 91.14 | 95.01 | 93.32 | - | - | - | 0.3983 |
| [49] | Multiple Association Rule | 66.70 | 78.84 | 79.74 | - | - | - | 0.5747 |
| [49] | Bayesian | 84.11 | 94.89 | 85.98 | 0.1695 | 0.3668 | ||
| [50] | RNN (LSTM) | 94.0 | - | - | - | - | - | - |
| [51] | CNN | 94.0 | 94.67 | - | - | - | ||
| [52] | Deep autoencoder (DAE + GAN) | 95.74 | - | - | - | - | - | - |
| [53] | Neural Networks | 75.93 | 73.33 | 67.01 | 61.68 | - | - | - |
| [54] | ARI-LSTM | 93.0 | - | - | - | - | - | - |
| [55] | CNN | 96.6 | 98.4 | 96.2 | 94.0 | - | - | - |
| [55] | DNN | 91.0 | 91.1 | 90.9 | 90.6 | - | - | - |
| [56] | DBN—decision tree | 96.0 | - | 96.0 | - | - | - | - |
| [57] | CNN | 94.5 | 94.5 | - | 94.6 | - | - | - |
| [58] | RNN | 96.01 | - | - | - | - | - | - |
| The proposed model RoMADS | AE-LSTM | 99.0385720855369 | 99.99709795841374 | 99.00 | 99.0414187577247 | 0.00961427914463095 | 0.00961427914463095 | 0.09805243059012331 |
| With Shifting | Without Shifting | |
|---|---|---|
| Epoch | 200 | 200 |
| Timesteps | 5 | 5 |
| Batch size | 64 | 64 |
| LSTM Layer 1 | (None, 5, 32) | (None, 5, 32) |
| LSTM Layer 2 | (None, 16) | (None, 16) |
| LSTM Layer 3 | (None, 5, 16) | (None, 5, 16) |
| LSTM Layer 4 | (None, 5, 32) | (None, 5, 32) |
| ACC (%) | 99.0385720855369 | 97.22854708257086 |
| TPR (%) | 99.99709795841374 | 1.0 |
| PPV (%) | 99.0414187577247 | 97.2285083675579 |
| Recall (%) | 99.0 | 97.0 |
| F1-score (%) | 99.0 | 96.0 |
| MAE | 0.00961427914463095 | 0.027714529174291423 |
| MSE | 0.00961427914463095 | 0.027714529174291423 |
| RMSE | 0.09805243059012331 | 0.16647681272264742 |
| 1 | 2 | 3 | 4 | |
|---|---|---|---|---|
| Epoch | 200 | 400 | 90 | 1 |
| Timesteps | 5 | 5 | 5 | 1 |
| Batch Size | 64 | 64 | 64 | 32 |
| LSTM Layer 1 | (None, 5, 32) | (None, 5, 32) | (None, 5, 64) | (None, 5, 32) |
| LSTM Layer 2 | (None, 16) | (None, 16) | (None, 32) | (None, 16) |
| LSTM Layer 3 | (None, 5, 16) | (None, 5, 16) | (None, 5, 32) | (None, 5, 16) |
| LSTM Layer 4 | (None, 5, 32) | (None, 5, 32) | (None, 5, 64) | (None, 5, 32) |
| ACC | 99.0385720855369 | 99.0385720855369 | 99.0385720855369 | 99.0385720855369 |
| TPR | 99.99709795841374 | 99.99709795841374 | 99.99709795841374 | 99.99709795841374 |
| Precision | 99.0414187577247 | 99.0414187577247 | 99.0414187577247 | 99.0414187577247 |
| Recall | 99.00 | 99.00 | 99.00 | 99.00 |
| F1-Score | 99.00 | 99.00 | 99.00 | 99.00 |
| MAE | 0.00961427914463095 | 0.00958553690503564 | 0.009599908024833294 | 0.009700366458288425 |
| MSE | 0.00961427914463095 | 0.00958553690503564 | 0.009599908024833294 | 0.009700366458288425 |
| RMSE | 0.09805243059012331 | 0.09790575521916799 | 0.09797912035139576 | 0.09849043841047934 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Talal, H.; Zagrouba, R. A Robust Framework for MADS Based on DL Techniques on the IoT. Electronics 2021, 10, 2723. https://doi.org/10.3390/electronics10212723
Talal H, Zagrouba R. A Robust Framework for MADS Based on DL Techniques on the IoT. Electronics. 2021; 10(21):2723. https://doi.org/10.3390/electronics10212723
Chicago/Turabian StyleTalal, Hussah, and Rachid Zagrouba. 2021. "A Robust Framework for MADS Based on DL Techniques on the IoT" Electronics 10, no. 21: 2723. https://doi.org/10.3390/electronics10212723
APA StyleTalal, H., & Zagrouba, R. (2021). A Robust Framework for MADS Based on DL Techniques on the IoT. Electronics, 10(21), 2723. https://doi.org/10.3390/electronics10212723







