Event-Triggered Formation Tracking Control for Unmanned Aerial Vehicles Subjected to Deception Attacks
Abstract
:1. Introduction
2. System Description and Modeling
2.1. UAV Modeling
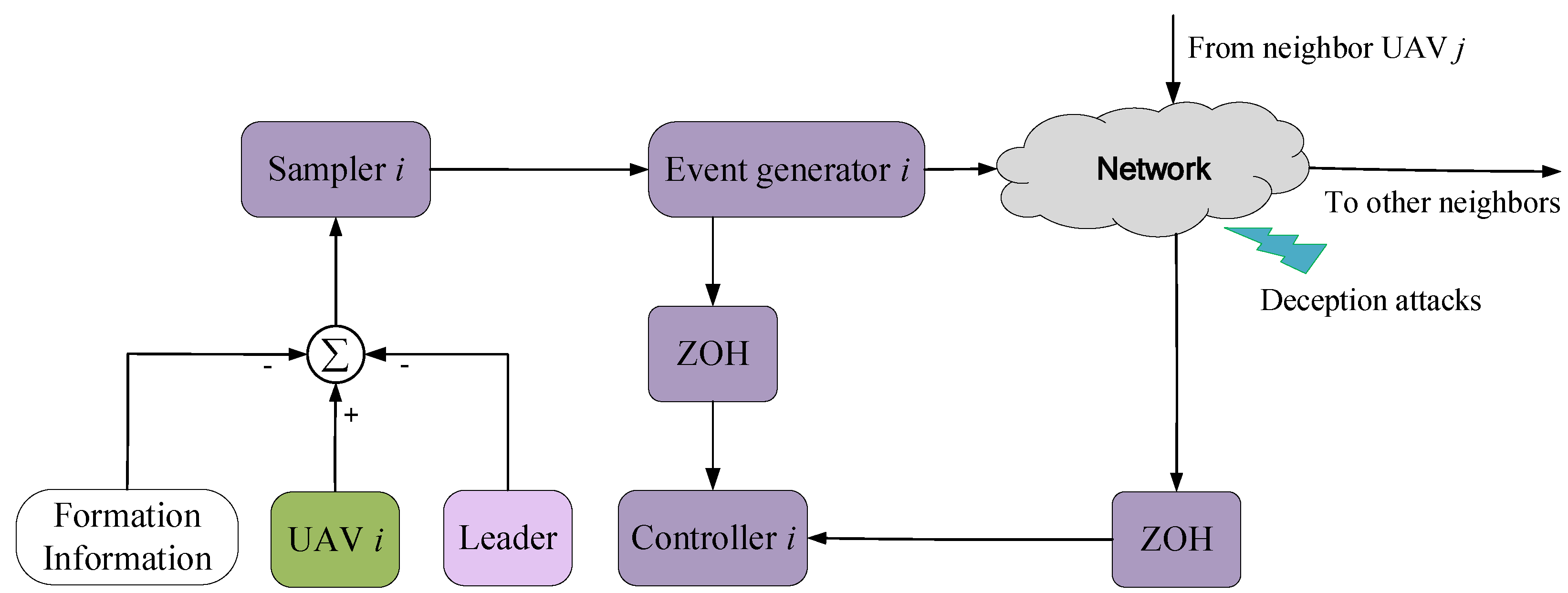
2.2. Event-Triggered Communication Scheme
2.3. Deception Attacks
2.4. Control Law and Formation Tracking Error Systems
3. Main Results
4. Simulation Example
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lin, Z.; Wang, L.; Han, Z.; Fu, M. Distributed formation control of multi-agent systems using complex laplacian. IEEE Trans. Autom. Control 2014, 59, 1765–1777. [Google Scholar] [CrossRef]
- Dong, X.; Hua, Y.; Zhou, Y.; Ren, Z.; Zhong, Y. Theory and experiment on formation-containment control of multiple multirotor unmanned aerial vehicle systems. IEEE Trans. Autom. Sci. Eng. 2019, 16, 229–240. [Google Scholar] [CrossRef]
- Zhang, J.; Yan, J.; Zhang, P. Multi-uav formation control based on a novel back-stepping approach. IEEE Trans. Veh. Technol. 2020, 69, 2437–2448. [Google Scholar] [CrossRef]
- Xiong, T.; Gu, Z. Observer-based adaptive fixed-time formation control for multi-agent systems with unknown uncertainties. Neurocomputing 2021, 423, 506–517. [Google Scholar] [CrossRef]
- Xiong, T.; Pu, Z.; Yi, J.; Tao, X. Fixed-time observer based adaptive neural network time-varying formation tracking control for multi-agent systems via minimal learning parameter approach. IET Control Theory Appl. 2020, 14, 1147–1157. [Google Scholar] [CrossRef]
- Dong, X.; Zhou, Y.; Ren, Z.; Zhong, Y. Time-varying formation tracking for second-order multi-agent systems subjected to switching topologies with application to quadrotor formation flying. IEEE Trans. Ind. Electron. 2016, 64, 5014–5024. [Google Scholar] [CrossRef]
- Wang, R.; Dong, X.; Li, Q.; Ren, Z. Distributed time-varying formation control for multiagent systems with directed topology using an adaptive output-feedback approach. IEEE Trans. Ind. 2019, 15, 4676–4685. [Google Scholar] [CrossRef]
- Wang, R.; Dong, X.; Li, Q.; Ren, Z. Distributed time-varying output formation control for general linear multiagent systems with directed topology. IEEE Trans. Control Netw. Syst. 2019, 6, 609–620. [Google Scholar] [CrossRef]
- Wang, Z.; Zhuang, Z.; Liu, Y.; Ding, F.; Tang, M. Color Classification and Texture Recognition System of Solid Wood Panels. Forests. 2021, 12, 1154. [Google Scholar] [CrossRef]
- Yue, D.; Won, S. Delay-dependent robust stability of stochastic uncertain systems with time delay and markovian jump parameters. Circuits Syst. Signal Process. 2003, 22, 351–365. [Google Scholar] [CrossRef]
- Li, X.; Dong, X.; Li, Q.; Ren, Z. Event-triggered time-varying formation control for general linear multi-agent systems. J. Franklin Inst. 2019, 356, 10179–10195. [Google Scholar] [CrossRef]
- Gu, Z.; Park, J.H.; Yue, D.; Wu, Z.-G.; Xie, X. Event-triggered security output feedback control for networked interconnected systems subject to cyber-attacks. IEEE Trans. Syst. Man Cybern. 2020, 51, 6197–6206. [Google Scholar] [CrossRef]
- Gu, Z.; Shi, P.; Yue, D. An adaptive event-triggering scheme for networked interconnected control system with stochastic uncertainty. Int. J. Robust Nonlinear Control. 2017, 27, 236–251. [Google Scholar] [CrossRef]
- Hu, S.; Yue, D.; Yin, X.; Xie, X.; Ma, Y. Adaptive event-triggered control for nonlinear discrete-time systems. Int. J. Robust Nonlinear Control 2016, 26, 4104–4125. [Google Scholar] [CrossRef]
- Li, J.; Li, C.; Yang, X.; Chen, W. Event-triggered containment control of multi-agent systems with high-order dynamics and input delay. Electronics 2018, 7, 343. [Google Scholar] [CrossRef] [Green Version]
- Kwon, W.; Baek, J. Novel summation-type triggering condition on event-based memory output feedback control for networked control systems. Electronics 2020, 9, 779. [Google Scholar] [CrossRef]
- Zheng, B.-C.; Fei, S.; Liu, X. Event-triggered and memory-based sliding mode variable structure control for memristive systems. Electronics 2018, 7, 253. [Google Scholar] [CrossRef] [Green Version]
- Yang, J.; Xiao, F.; Chen, T. Event-triggered formation tracking control of nonholonomic mobile robots without velocity measurements. Automatica 2020, 112, 108671. [Google Scholar] [CrossRef]
- Yin, X.; Yue, D.; Hu, S.; Zhang, H. Distributed adaptive model-based event-triggered predictive control for consensus of multiagent systems. Int. J. Robust Nonlinear Control 2018, 28, 6180–6201. [Google Scholar] [CrossRef]
- Yue, D.; Tian, E.; Han, Q.-L. A delay system method for designing event-triggered controllers of networked control systems. IEEE Trans. Autom. Control 2012, 58, 475–481. [Google Scholar] [CrossRef]
- Liu, J.; Wei, L.; Xie, X.; Tian, E.; Fei, S. Quantized stabilization for t–s fuzzy systems with hybrid-triggered mechanism and stochastic cyber-attacks. IEEE Trans. Fuzzy Syst. 2018, 26, 3820–3834. [Google Scholar] [CrossRef]
- Ye, D.; Chen, M.; Yang, H. Distributed adaptive event-triggered fault-tolerant consensus of multiagent systems with general linear dynamics. IEEE Trans. Cybern. 2018, 49, 757–767. [Google Scholar] [CrossRef]
- Tian, E.; Peng, C. Memory-based event-triggering H∞ load frequency control for power systems under deception attacks. IEEE Trans. Cybern. 2020, 50, 4610–4618. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, H.; Cai, Y.; Wang, W. Consensus control for nonlinear multi-agent systems with event-triggered communications. Appl. Math. Comput. 2021, 408, 126341. [Google Scholar]
- Zhang, A.; Zhou, D.; Yang, P.; Yang, M. Event-triggered finite-time consensus with fully continuous communication free for second-order multi-agent systems. Int. J. Control. Autom. Syst. 2019, 17, 836–846. [Google Scholar] [CrossRef]
- Gu, Z.; Yue, D.; Tian, E. On designing of an adaptive event-triggered communication scheme for nonlinear networked interconnected control systems. Inf. Sci. 2018, 422, 257–270. [Google Scholar] [CrossRef]
- Hu, S.; Yue, D.; Chen, X.; Cheng, Z.; Xie, X. Resilient H∞ filtering for event-triggered networked systems under nonperiodic dos jamming attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 1392–1403. [Google Scholar] [CrossRef]
- Liu, J.; Wang, Y.; Cao, J.; Yue, D.; Xie, X. Secure adaptive-event-triggered filter design with input constraint and hybrid cyber attack. IEEE Trans. Cybern. 2021, 51, 4000–4010. [Google Scholar] [CrossRef]
- Peng, C.; Yue, D.; Yang, T.-C.; Tian, E.G. On delay-dependent approach for robust stability and stabilization of t–s fuzzy systems with constant delay and uncertainties. IEEE Trans. Fuzzy Syst. 2009, 17, 1143–1156. [Google Scholar] [CrossRef]
- Peng, C.; Han, Q.-L.; Yue, D. Communication-delay-distribution-dependent decentralized control for large-scale systems with ip-based communication networks. IEEE Trans. Control Syst. Technol. 2013, 21, 820–830. [Google Scholar] [CrossRef]
- Yang, Y.; Yue, D.; Xue, Y. Decentralized adaptive neural output feedback control of a class of large-scale time-delay systems with input saturation. J. Frankl. Inst. 2015, 352, 2129–2151. [Google Scholar] [CrossRef]
- Xie, X.; Yue, D.; Zhang, H.; Xue, Y. Fault estimation observer design for discrete-time takagi–sugeno fuzzy systems based on homogenous polynomially parameter-dependent lyapunov functions. IEEE Trans. Cybern. 2017, 47, 2504–2513. [Google Scholar] [CrossRef]
- Gu, Z.; Sun, X.; Lam, H.-K.; Yue, D.; Xie, X. Event-based secure control of t-s fuzzy based 5-dof active semi-vehicle suspension systems subject to dos attacks. IEEE Trans. Fuzzy Syst. 2021. to be published. [Google Scholar] [CrossRef]
- Gu, Z.; Ahn, C.K.; Yue, D.; Xie, X. Event-triggered H∞ filtering for t-s fuzzy-model-based nonlinear networked systems with multisensors against dos attacks. IEEE Trans. Cybern. 2020. to be published. [Google Scholar] [CrossRef] [PubMed]
- Yan, S.; Gu, Z.; Nguang, S.K. Memory-event-triggered H∞ output control of neural networks with mixed delays. IEEE Trans. Neural Netw. Learn. Syst. 2021. to be published. [Google Scholar] [CrossRef] [PubMed]
- Zhang, M. Tracking control for unmanned aerial vehicles with time-delays based on event-triggered mechanism. J. Control Eng. Appl. Inf. 2019, 21, 12–19. [Google Scholar]
- Zhang, D.; Ling, R.; Wang, Q.; Yu, L.; Feng, Y. Sensor-network-based distributed stabilization of nonlinear large-scale systems with energy constraints and random sensor faults. J. Frankl. Institute 2015, 352, 3345–3365. [Google Scholar] [CrossRef]
- Gu, Z.; Shi, P.; Yue, D.; Yan, S.; Xie, X. Memory-based continuous event-triggered control for networked t-s fuzzy systems against cyber-attacks. IEEE Trans. Fuzzy Syst. 2020, 29, 3118–3129. [Google Scholar] [CrossRef]
- Hu, S.; Yue, D.; Han, Q.-L.; Xie, X.; Chen, X.; Dou, C. Observer-based event-triggered control for networked linear systems subject to denial-of-service attacks. IEEE Trans. Cybern. 2019, 50, 1952–1964. [Google Scholar] [CrossRef]
- Sun, H.; Peng, C.; Zhang, W.; Yang, T.; Wang, Z. Security-based resilient event-triggered control of networked control systems under denial of service attacks. J. Frankl. Inst. 2019, 356, 10277–10295. [Google Scholar] [CrossRef]
- Ye, D.; Zhang, T.-Y.; Guo, G. Stochastic coding detection scheme in cyber-physical systems against replay attack. Inf. Sci. 2019, 481, 432–444. [Google Scholar] [CrossRef]
- Wang, H.; Ying, Y.; Lu, R.; Xue, A. Network-based H∞ control for singular systems with event-triggered sampling scheme. Inf. Sci. 2016, 329, 540–551. [Google Scholar] [CrossRef]
- Ding, D.; Wang, Z.; Ho, D.W.; Wei, G. Distributed recursive filtering for stochastic systems under uniform quantizations and deception attacks through sensor networks. Automatica 2017, 78, 231–240. [Google Scholar] [CrossRef]
- Han, F.; Dong, H.; Wang, Z.; Li, G. Local design of distributed H∞-consensus filtering over sensor networks under multiplicative noises and deception attacks. Int. J. Robust Nonlinear Control 2019, 29, 2296–2314. [Google Scholar] [CrossRef]
- Zhang, D.; Liu, L.; Feng, G. Consensus of heterogeneous linear multiagent systems subject to aperiodic sampled-data and dos attack. IEEE Trans. Cybern. 2018, 49, 1501–1511. [Google Scholar] [CrossRef] [PubMed]
- Porter, M.; Hespanhol, P.; Aswani, A.; Johnson-Roberson, M.; Vasudevan, R. Detecting generalized replay attacks via time-varying dynamic watermarking. IEEE Trans. Autom. Control 2020, 66, 3502–3517. [Google Scholar] [CrossRef]
- Zhang, D.; Wang, Q.; Feng, G.; Shi, Y.; Vasilakos, A.V. A survey on attack detection, estimation and control of industrial cyber–physical systems. ISA Trans. 2021, 116, 1–16. [Google Scholar] [CrossRef]
- Yao, W.; Nan, J.; Zhao, Y.; Fang, J.; Ai, X.; Zuo, W.; Wen, J.; Cheng, S. Resilient wide-area damping control for inter-area oscillations to tolerate deception attacks. IEEE Trans. Smart Grid 2021, 12, 4238–4249. [Google Scholar] [CrossRef]
- Rong, N.; Wang, Z. Event-based impulsive control of it2 t–s fuzzy interconnected system under deception attacks. IEEE Trans. Fuzzy Syst. 2021, 29, 1615–1628. [Google Scholar] [CrossRef]
- Yoo, S.J. Neural-network-based adaptive resilient dynamic surface control against unknown deception attacks of uncertain nonlinear time-delay cyberphysical systems. IEEE Trans. Neural Netw. Learn. Syst. 2020, 31, 4341–4353. [Google Scholar] [CrossRef]
- Gu, Z.; Zhou, X.; Zhang, T.; Yang, F.; Shen, M. Event-triggered filter design for nonlinear cyber–physical systems subject to deception attacks. ISA Trans. 2020, 104, 130–137. [Google Scholar] [CrossRef] [PubMed]
- Cui, Y.; Liu, Y.; Zhang, W.; Alsaadi, F.E. Sampled-based consensus for nonlinear multiagent systems with deception attacks: The decoupled method. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 561–573. [Google Scholar] [CrossRef]
- Wang, W.; Han, Z.; Liu, K.; Lü, J. Distributed adaptive resilient formation control of uncertain nonholonomic mobile robots under deception attacks. IEEE Trans. Circuits Syst. Regul. Pap. 2021, 68, 3822–3835. [Google Scholar] [CrossRef]
- Wei, L.; Chen, M.; Li, T. Dynamic event-triggered cooperative formation control for uavs subject to time-varying disturbances. IET Control Appl. 2020, 14, 2514–2525. [Google Scholar] [CrossRef]
- Xiong, T.; Gu, Z.; Yi, J.; Pu, Z. Fixed-time adaptive observer-based time-varying formation control for multi-agent systems with directed topologies. Neurocomputing 2021, 463, 483–494. [Google Scholar] [CrossRef]
- Liu, J.; Yin, T.; Cao, J.; Yue, D.; Karimi, H.R. Security control for ts fuzzy systems with adaptive event-triggered mechanism and multiple cyber-attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 6544–6554. [Google Scholar] [CrossRef]
- Liu, J.; Gu, Y.; Xie, X.; Yue, D.; Park, J.H. Hybrid-driven-based H∞ control for networked cascade control systems with actuator saturations and stochastic cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 2452–2463. [Google Scholar] [CrossRef]
- Liu, J.; Gu, Y.; Zha, L.; Liu, Y.; Cao, J. Event-triggered h∞ load frequency control for multiarea power systems under hybrid cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1665–1678. [Google Scholar] [CrossRef]
- Zhou, X.; Gu, Z.; Yang, F. Resilient event-triggered output feedback control for load frequency control systems subject to cyber attacks. IEEE Access 2019, 7, 58951–58958. [Google Scholar] [CrossRef]


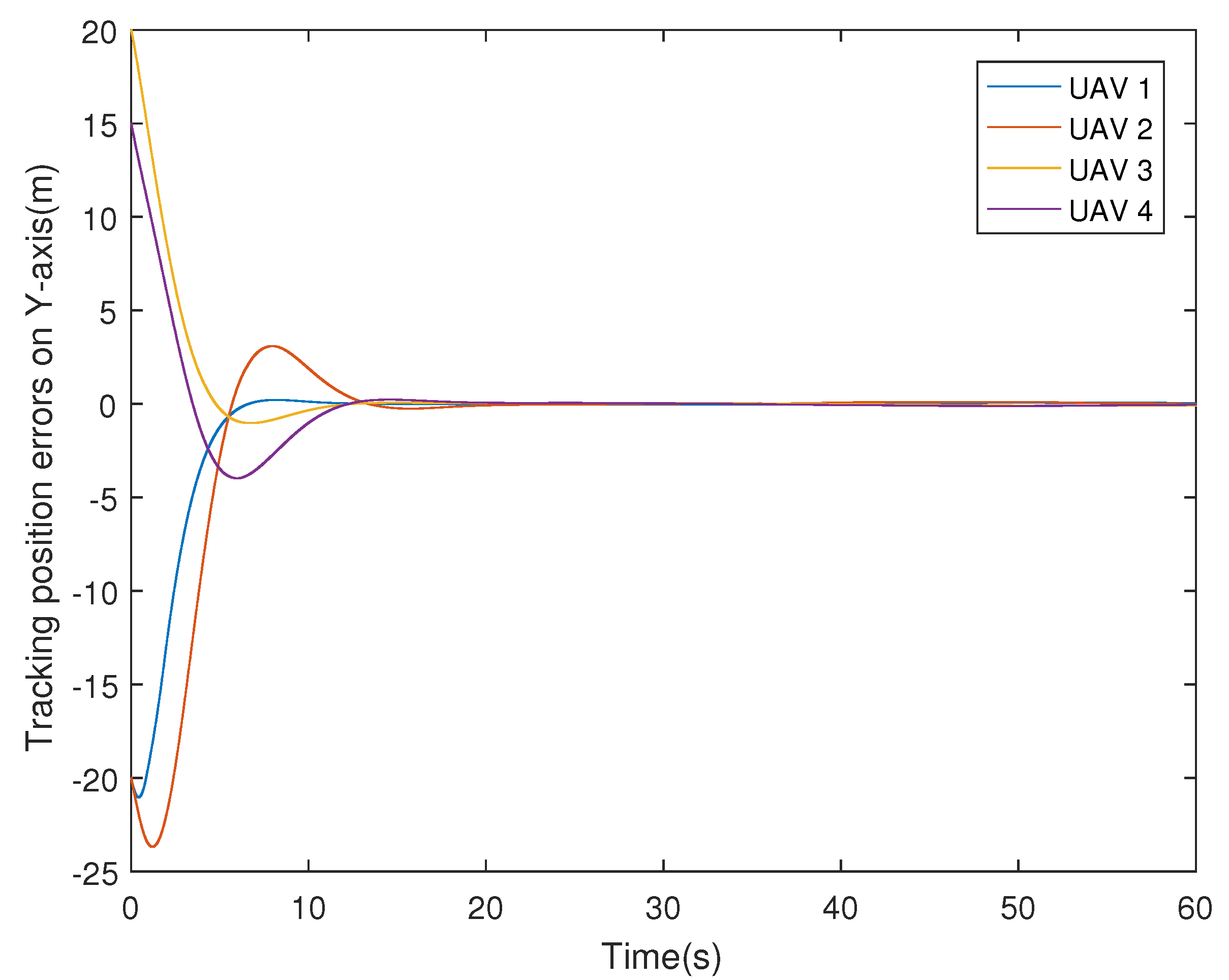


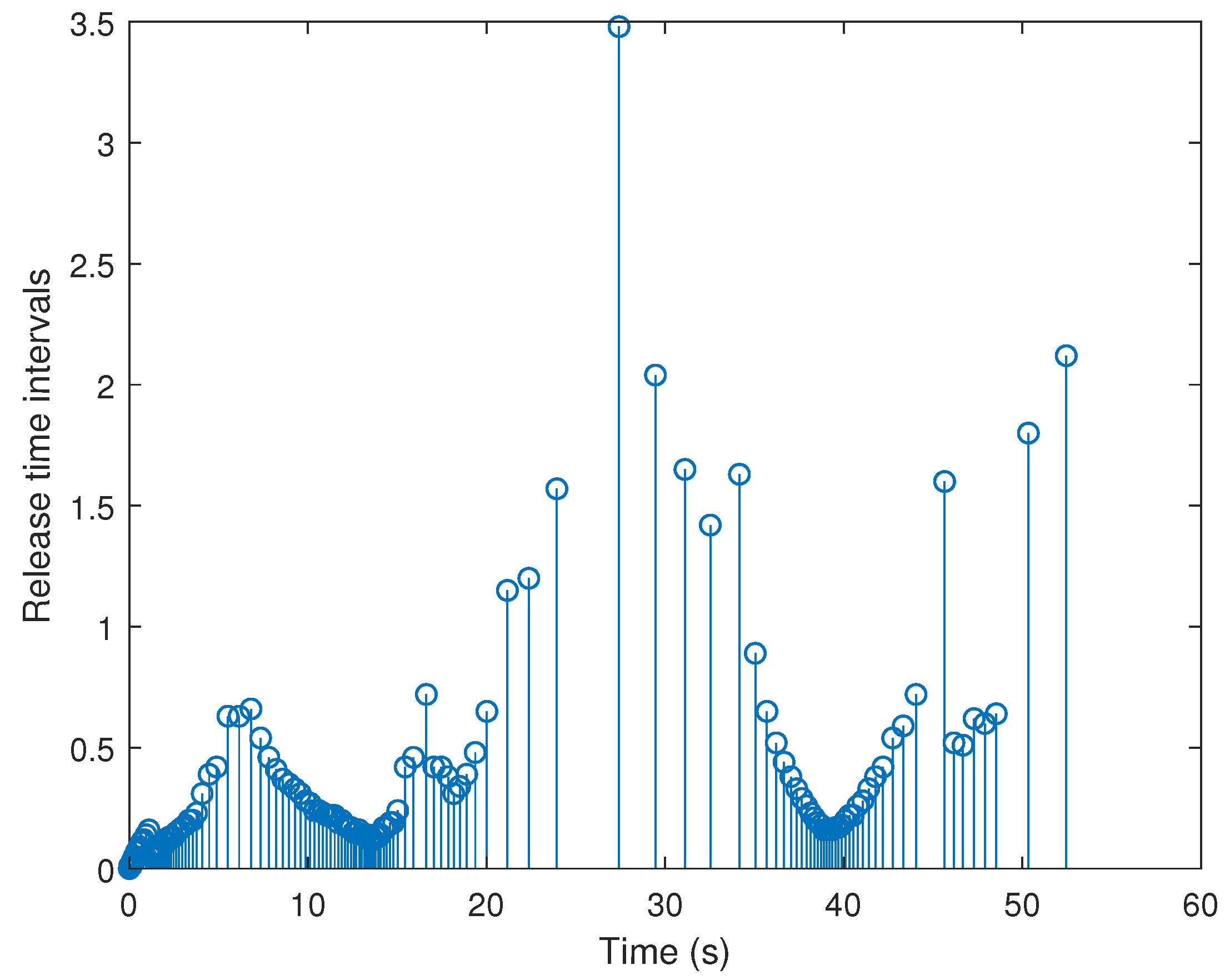
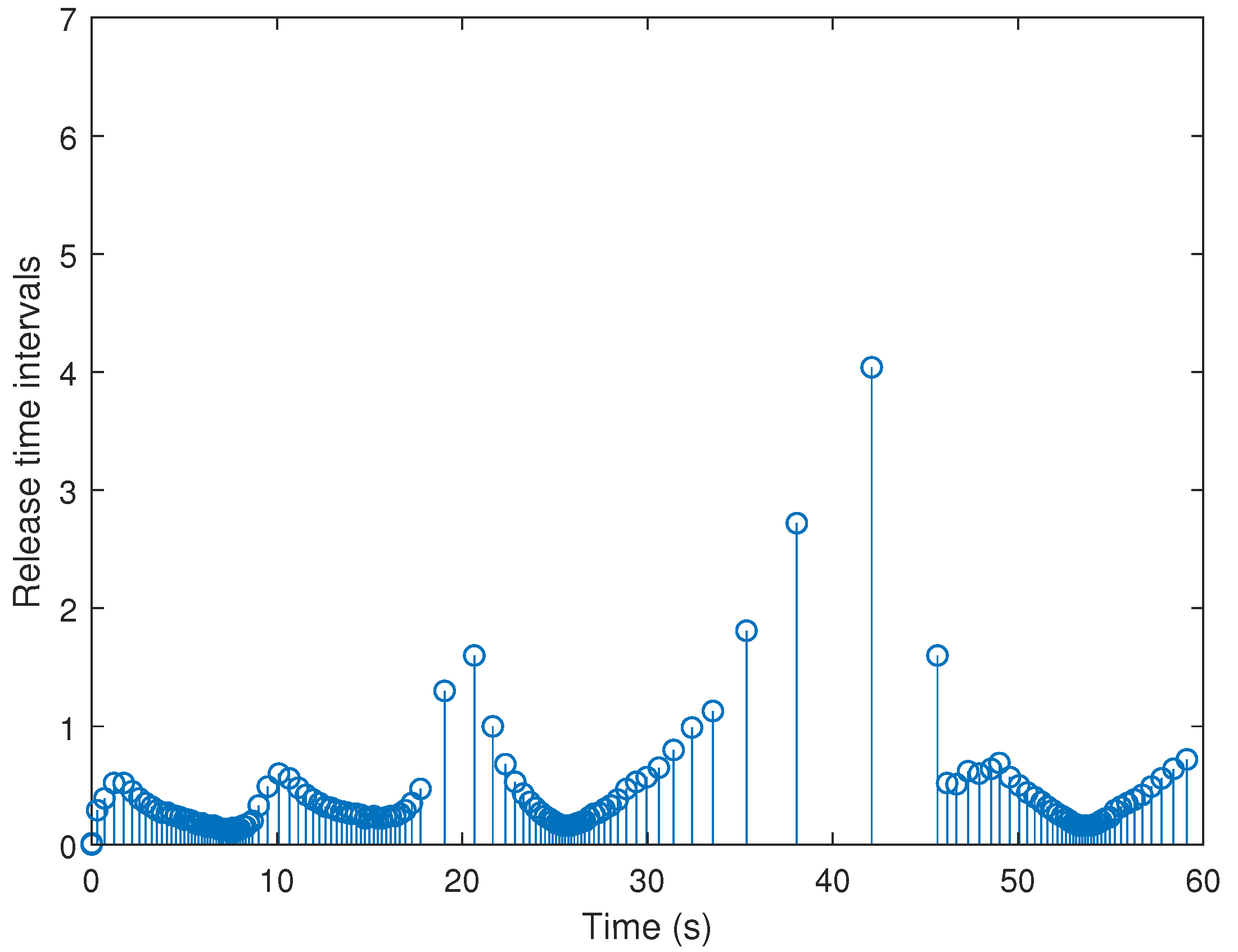
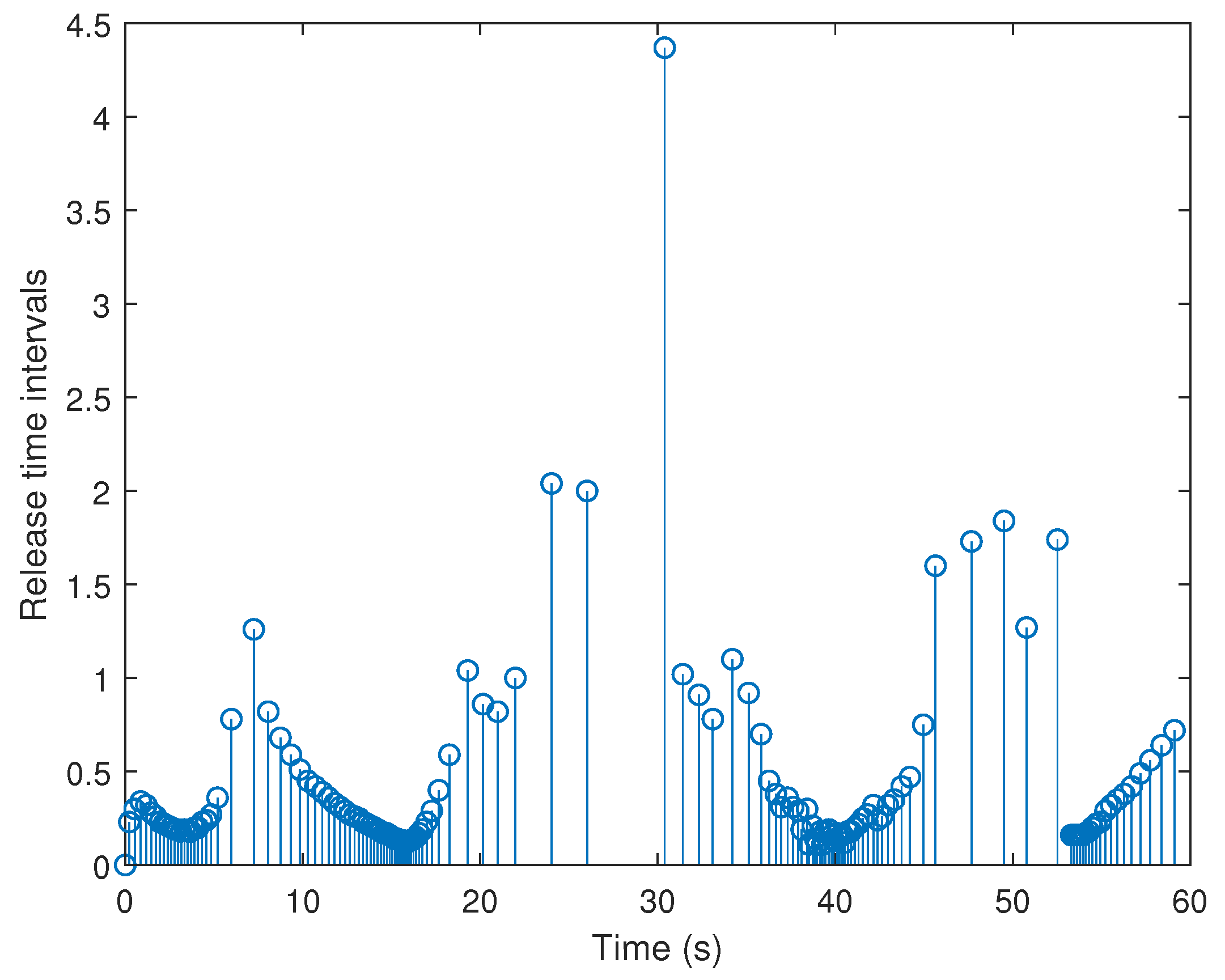

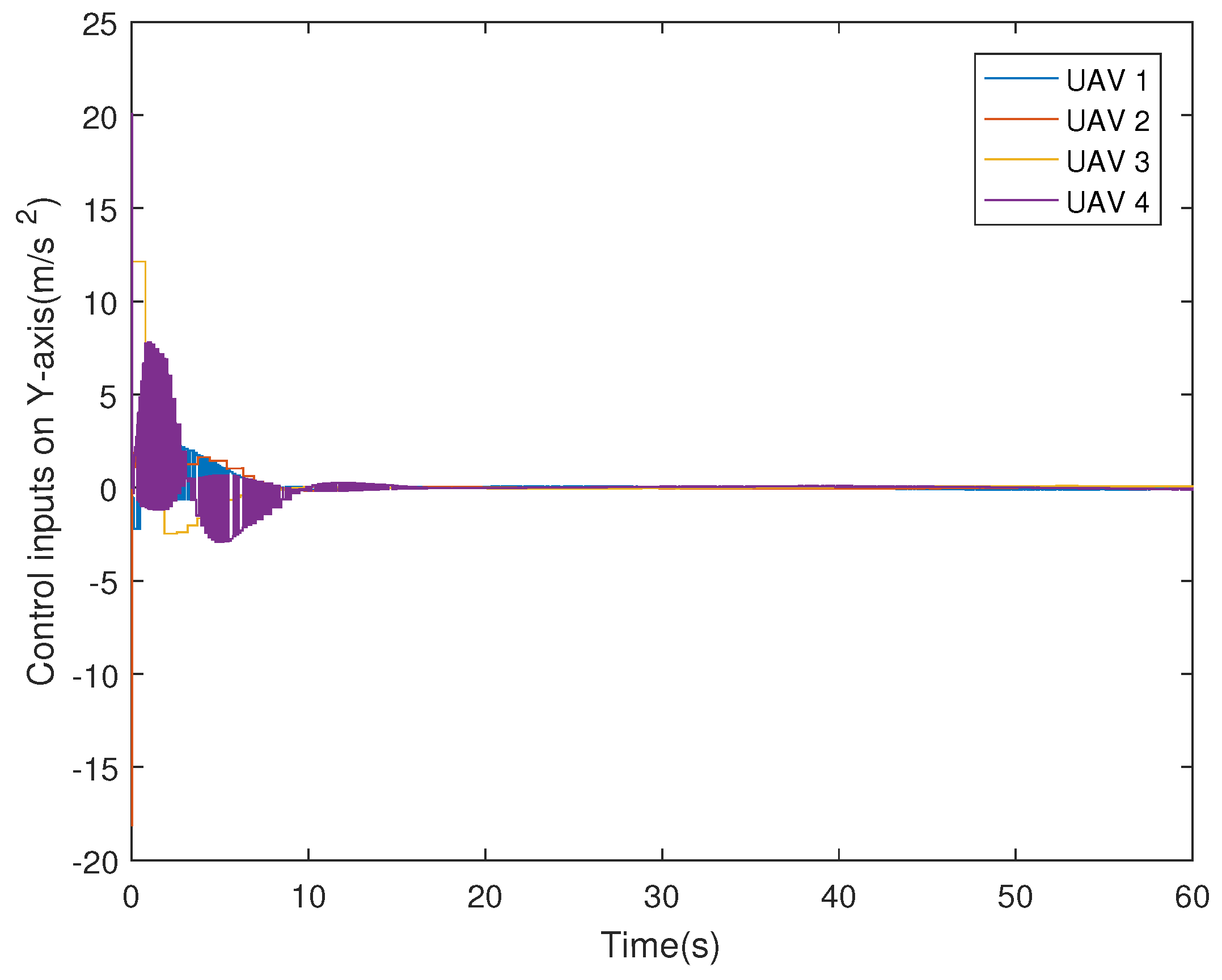
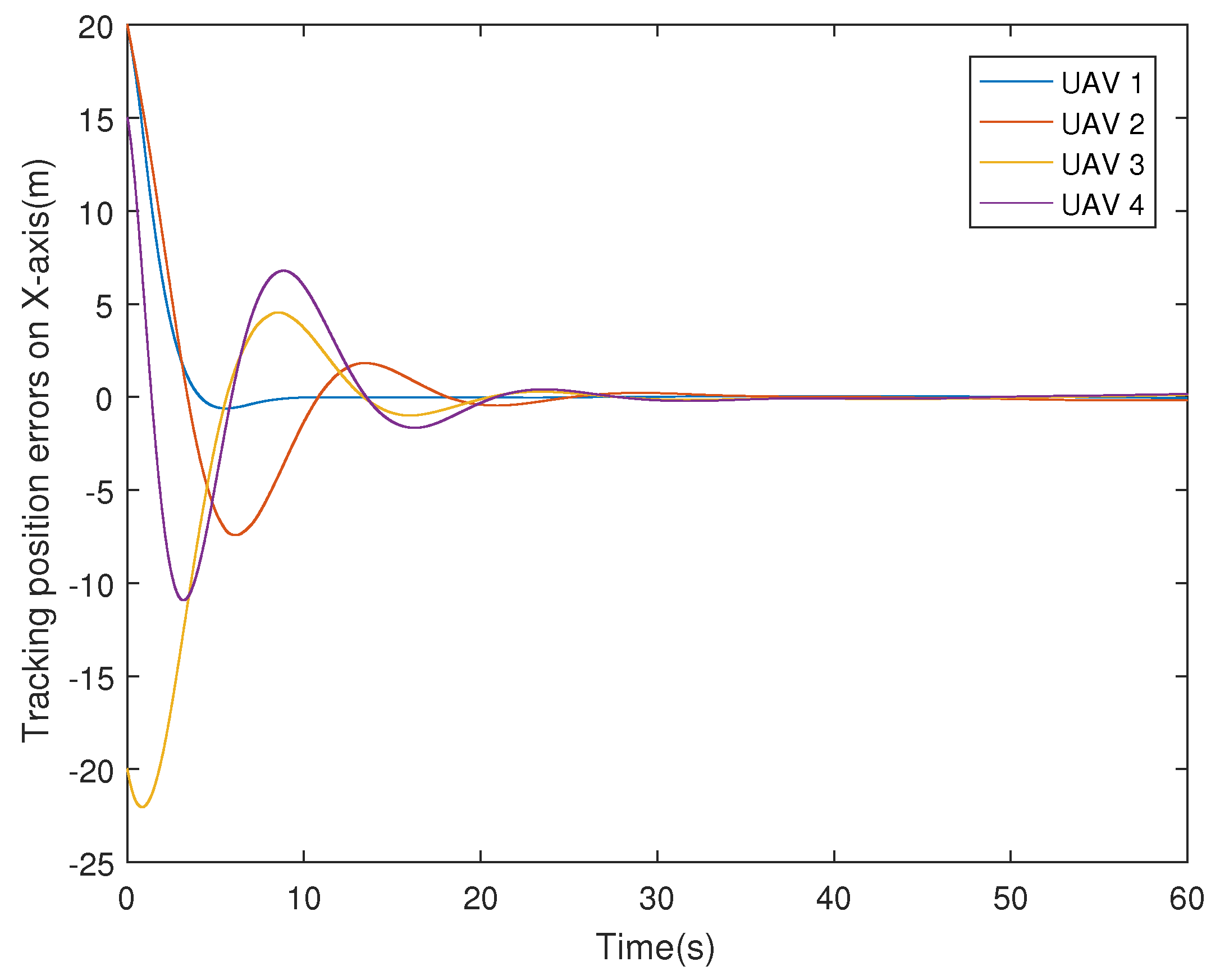

| On X-Axis | On Y-Axis | |
|---|---|---|
| ETM | 151.5 | 174.25 |
| TTM | 6001 | 6001 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, B.; Gu, Z.; Xiong, T. Event-Triggered Formation Tracking Control for Unmanned Aerial Vehicles Subjected to Deception Attacks. Electronics 2021, 10, 2736. https://doi.org/10.3390/electronics10222736
Sun B, Gu Z, Xiong T. Event-Triggered Formation Tracking Control for Unmanned Aerial Vehicles Subjected to Deception Attacks. Electronics. 2021; 10(22):2736. https://doi.org/10.3390/electronics10222736
Chicago/Turabian StyleSun, Biao, Zhou Gu, and Tianyi Xiong. 2021. "Event-Triggered Formation Tracking Control for Unmanned Aerial Vehicles Subjected to Deception Attacks" Electronics 10, no. 22: 2736. https://doi.org/10.3390/electronics10222736





