Optimized Authentication System with High Security and Privacy
Abstract
1. Introduction
- Enrollment: From the data provided by the user a template is computed, which is saved in the repository/database to facilitate the user verification in future.
- Verification: Similar to the above step a user template is computed from the data provided by the user and then its similarity is computed with the template available in the repository. Depending on scores computed a person is verified.
- Revocability: By the use of the same data (biometric features) provided by the user, it must be possible to construct multiple templates.
- Diversity: There must be no similarity among the different templates generated by using the same data of the user.
- Security: Original data provided by the user must never get compromised under any scenario.
- Performance: Due to security enhancement the recognition performance of the system should not get reduced.
- A completely secure template is constructed by using the features of the fingerprint provided by a user that depicts exceptional revocability, diversity, security, and recognition performance.
- Generally during minutiae extraction, there exists a problem of missing minutiae points. The proposed technique has shown good resistance against the missing minutiae points problem.
- The proposed technique exhibits superior recognition performance in comparison to other existing techniques and has achieved 0% equal error rate (EER).
- Rotation/translation of fingerprint on the fingerprint scanner leads to variation in the fingerprint images captured, the proposed technique is highly robust against such variations.
- Mostly the fingerprint-based authentication techniques generate a user template which is not optimized. The proposed technique uses the quality of minutiae points and generates a highly optimized user template.
2. Literature Review
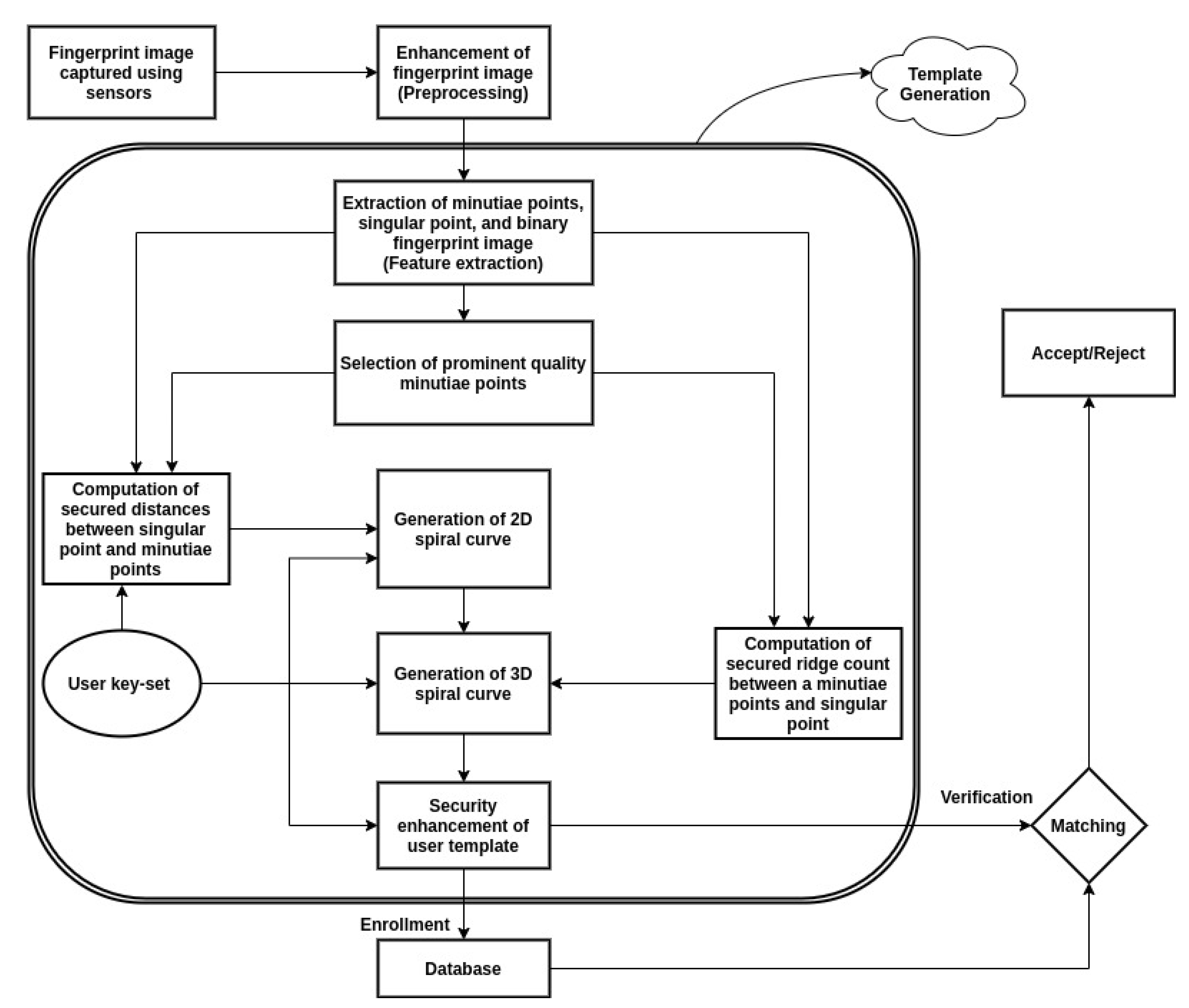
3. Proposed Technique
3.1. Features Required for Template Generation
- Singular Point: Only the location of it is used.
- Minutiae Points: Their location, orientation, and quality are used. Instead of directly using the location of a minutia point, a secured location computed corresponding to it is used.
- Ridge Counts: Ridge counts, which are the number of ridges between minutiae points and a singular point are used. Instead of directly using the ridge counts, secured ridge counts are calculated, which are further used.
- Secured distance between singular point and minutiae point. Let be the distance between singular and the jth minutia point. It can be noted that is rotation/translation invariant; however, it is not secure to directly use because it is permanent and cannot be changed if compromised. Instead of using , a secured distance is used, corresponding to jth minutia point. The secured distance is generated with the help of , orientation of jth minutia, and the user keys , . This is pictorially shown in Figure 3.
- Secured ridge count between the singular and minutia point. Similar to above, it is not safe to directly use the ridge count between the jth minutia point and the singular point. Instead, a secured ridge count is calculated with the help of keys , . As shown in Figure 3.
| Algorithm 1 Secured Features Calculation. |
|
3.2. Enrollment
3.2.1. Extraction of Features
3.2.2. Template Generation
| Algorithm 2 User Template Construction. |
|
3.3. Template Matching for Verification
4. Experimental Results and Discussion
- False Acceptance Rate (FAR): Percentage of time an attacker is recognized as a genuine user.
- False Rejection Rate (FRR): Percentage of time a genuine user is not recognized as a genuine user.
- Equal Error Rate (EER): FRR or FAR value, when they both are equal.
- FAR: FRR value when the FAR value is 0.001%.
- Zero: Least value of FRR, when the FAR value is zero.
- Genuine Acceptance Rate (GAR): It is the percentage of time a genuine user is recognized correctly as a genuine user.
4.1. Revocablility and Diversity
- Attack Scenario I: Attacker possess the user template, compromised by attacking the database. A new template for the user is constructed by using the same fingerprint sample of the user with different user key-set values.
- Attack Scenario II: Attacker possess the old template, compromised by attacking the database. A new user template is computed by using the different fingerprint sample of the same user with different user key-set values.
4.2. Security Analysis
4.3. Performance
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Huh, J.-H. Surgery Agreement Signature Authentication System for Mobile Health Care. Electronics 2020, 9, 890. [Google Scholar] [CrossRef]
- Munilla, J.; Hassan, A.; Burmester, M. 5G-Compliant Authentication Protocol for RFID. Electronics 2020, 9, 1951. [Google Scholar] [CrossRef]
- Tidrea, A.; Korodi, A.; Silea, I. Cryptographic Considerations for Automation and SCADA Systems Using Trusted Platform Modules. Sensors 2019, 19, 4191. [Google Scholar] [CrossRef] [PubMed]
- Saxena, N.; Hayes, E.; Bertino, E.; Ojo, P.; Choo, K.-K.R.; Burnap, P. Impact and Key Challenges of Insider Threats on Organizations and Critical Businesses. Electronics 2020, 9, 1460. [Google Scholar] [CrossRef]
- Kaveh, M.; Martín, D.; Mosavi, M.R. A Lightweight Authentication Scheme for V2G Communications: A PUF-Based Approach Ensuring Cyber/Physical Security and Identity/Location Privacy. Electronics 2020, 9, 1479. [Google Scholar] [CrossRef]
- Ali, S.S.; Baghel, V.S.; Ganapathi, I.I.; Prakash, S. Robust biometric authentication system with a secure user template. Image Vis. Comput. 2020, 104, 104004. [Google Scholar] [CrossRef]
- Ali, S.S.; Prakash, S. 3-Dimensional Secured Fingerprint Shell. Patt. Recogn. Lett. 2019, 126, 68–77. [Google Scholar] [CrossRef]
- Zhang, J.; Wu, M. Blockchain Use in IoT for Privacy-Preserving Anti-Pandemic Home Quarantine. Electronics 2020, 9, 1746. [Google Scholar] [CrossRef]
- Tan, H.; Kim, P.; Chung, I. Practical Homomorphic Authentication in Cloud-Assisted VANETs with Blockchain-Based Healthcare Monitoring for Pandemic Control. Electronics 2020, 9, 1683. [Google Scholar] [CrossRef]
- Noh, J.; Jeon, S.; Cho, S. Distributed Blockchain-Based Message Authentication Scheme for Connected Vehicles. Electronics 2020, 9, 74. [Google Scholar] [CrossRef]
- Knežević, M.; Tomović, S.; Mihaljević, M.J. Man-In-The-Middle Attack against Certain Authentication Protocols Revisited: Insights into the Approach and Performances Re-Evaluation. Electronics 2020, 9, 1296. [Google Scholar] [CrossRef]
- Iyappan, G.I.; Ali, S.S.; Prakash, S. Multi-resolution Local Descriptor for 3D Ear Recognition. In Proceedings of the BIOSIG 2019, Darmstadt, Germany, 18–20 September 2019; pp. 1–8. [Google Scholar]
- Iula, A.; Micucci, M. Experimental Validation of a Reliable Palmprint Recognition System Based on 2D Ultrasound Images. Electronics 2019, 80, 1393. [Google Scholar] [CrossRef]
- Nakanishi, I.; Maruoka, T. Biometrics Using Electroencephalograms Stimulated by Personal Ultrasound and Multidimensional Nonlinear Features. Electronics 2020, 9, 24. [Google Scholar] [CrossRef]
- McGoldrick, L.K.; Halámek, J. Recent Advances in Noninvasive Biosensors for Forensics, Biometrics, and Cybersecurity. Sensors 2020, 20, 5974. [Google Scholar] [CrossRef] [PubMed]
- Iyappan, G.I.; Prakash, S.; Dave, I.R.; Joshi, P.; Ali, S.S.; Shrivastava, A.M. Ear recognition in 3D using 2D curvilinear features. IET Biom. 2018, 7, 519–529. [Google Scholar]
- Cavoukian, A.; Stoianov, A. Biometric encryption. In Encyclopedia of Cryptography and Security; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- AlMajed, H.; AlMogren, A. A Secure and Efficient ECC-Based Scheme for Edge Computing and Internet of Things. Sensors 2020, 20, 6158. [Google Scholar] [CrossRef] [PubMed]
- Ali, S.S.; Prakash, S. Fingerprint Shell Construction with Prominent Minutiae Points. In Proceedings of the COMPUTE 2017, Bhopal, India, 16–17 November 2017; ACM: New York, NY, USA, 2017; pp. 91–98. [Google Scholar]
- Qiu, S.; Wang, D.; Xu, G.; Kumari, S. Practical and Provably Secure Three-Factor Authentication Protocol Based on Extended Chaotic-Maps for Mobile Lightweight Devices. IEEE Trans. Dependable Secur. Comput. 2020, 1. [Google Scholar] [CrossRef]
- Ali, S.S.; Prakash, S. A Few Techniques for Fingerprint Template Protection. Ph.D. Thesis, Discipline of Computer Science & Engineering, IIT Indore, Madhya Pradesh, India, 2019. [Google Scholar]
- Ratha, N.K.; Connell, J.H.; Bolle, R.M. Enhancing security and privacy in biometrics-based authentication systems. IBM Syst. J. 2001, 40, 614–634. [Google Scholar] [CrossRef]
- Ilyas, M.; Othmani, A.; Fournier, R.; Nait-ali, A. Auditory Perception Based Anti-Spoofing System for Human Age Verification. Electronics 2019, 8, 1313. [Google Scholar] [CrossRef]
- Ali, S.S.; Iyappan, G.I.; Mahyo, S.; Prakash, S. Polynomial Vault: A secure and robust fingerprint based authentication. IEEE Trans. Emerg. Top. Comput. 2019. [Google Scholar] [CrossRef]
- Nandakumar, K. A fingerprint cryptosystem based on minutiae phase spectrum. In Proceedings of the WIFS 2010, Seattle, WA, USA, 12–15 December 2010; pp. 1–6. [Google Scholar]
- Ross, A.A.; Shah, J.; Jain, A.K. Toward reconstructing fingerprints from minutiae points. In Proceedings of the SPIE Conference on Biometric Technology for Human Identification, Orlando, FL, USA, 28 March 2005; pp. 68–80. [Google Scholar]
- Ross, A.; Shah, J.; Jain, A.K. From Template to Image: Reconstructing Fingerprints from Minutiae Points. IEEE Trans. PAMI 2007, 29, 544–560. [Google Scholar] [CrossRef]
- Chen, F.; Zhou, J.; Yang, C. Reconstructing Orientation Field From Fingerprint Minutiae to Improve Minutiae-Matching Accuracy. IEEE Trans. Image Process. 2009, 18, 1665–1670. [Google Scholar] [CrossRef] [PubMed]
- Feng, J.; Jain, A.K. Fingerprint Reconstruction: From Minutiae to Phase. IEEE Trans. PAMI 2011, 33, 209–223. [Google Scholar] [CrossRef]
- Breebaart, J.; Yang, B.; Buhan-Dulman, I.; Busch, C. Biometric template protection. Datenschutz Datensicherheit DuD 2009, 33, 299–304. [Google Scholar] [CrossRef]
- Ali, S.S.; Iyappan, G.I.; Prakash, S. Fingerprint Shell construction with impregnable features. J. Intell. Fuzzy Syst. 2019, 36, 4091–4104. [Google Scholar] [CrossRef]
- Mohanraj, V.; Chakkaravarthy, S.S.; Gogul, I.; Kumar, V.S.; Kumar, R.; Vaidehi, V. Intelligent, smart and scalable cyber-physical systems. J. Intell. Fuzzy Syst. 2019, 36, 3935–3943. [Google Scholar]
- Ali, S.S.; Iyappan, G.I.; Prakash, S. Robust technique for fingerprint template protection. IET Biom. 2018, 7, 536–549. [Google Scholar] [CrossRef]
- Baghel, V.S.; Ali, S.S.; Prakash, S. A non-invertible transformation based technique to protect a fingerprint template. IET Image Process. 2021. [Google Scholar] [CrossRef]
- Cappelli, R.; Ferrara, M.; Maltoni, D. Minutia Cylinder-Code: A New Representation and Matching Technique for Fingerprint Recognition. IEEE Trans. PAMI 2010, 32, 2128–2141. [Google Scholar] [CrossRef] [PubMed]
- Ferrara, M.; Maltoni, D.; Cappelli, R. Noninvertible Minutia Cylinder-Code Representation. IEEE Trans. IFS 2012, 7, 1727–1737. [Google Scholar] [CrossRef]
- Ferrara, M.; Maltoni, D.; Cappelli, R. A two-factor protection scheme for MCC fingerprint templates. In Proceedings of the BIOSIG 2014, Darmstadt, Germany, 10–12 September 2014; pp. 1–8. [Google Scholar]
- Liu, E.; Zhao, Q. Encrypted domain matching of fingerprint minutia cylinder-code (MCC) with l1 minimization. Neurocomputing 2017, 259, 3–13. [Google Scholar] [CrossRef]
- Nurtantio, A.P.; Catur, S.; Septino, N. Image compression based on SVD for BoVW model in fingerprint classification. J. Intell. Fuzzy Syst. 2018, 34, 2513–2519. [Google Scholar]
- Feng, R.; Wang, Z.; Li, Z.; Ma, H.; Chen, R.; Pu, Z.; Chen, Z.; Zeng, X. A Hybrid Cryptography Scheme for NILM Data Security. Electronics 2020, 9, 1128. [Google Scholar] [CrossRef]
- Trivedi, A.K.; Thounaojam, D.M.; Pal, S. Non-Invertible cancellable fingerprint template for fingerprint biometric. Comput. Secur. 2020, 90, 101690. [Google Scholar] [CrossRef]
- Azzakhnini, S.; Ballihi, L.; Aboutajdine, D. Combining Facial Parts For Learning Gender, Ethnicity, and Emotional State Based on RGB-D Information. ACM Trans. Multimed. Comput. Commun. Appl. 2018, 14, 19:1–19:14. [Google Scholar] [CrossRef]
- Yang, H.; Lin, B.; Chang, K.; Chen, C. Joint Estimation of Age and Expression by Combining Scattering and Convolutional Networks. ACM Trans. Multimed. Comput. Commun. Appl. 2018, 14, 9:1–9:19. [Google Scholar] [CrossRef]
- Balazia, M.; Sojka, P. Gait Recognition from Motion Capture Data. ACM Trans. Multimed. Comput. Commun. Appl. 2018, 14, 22:1–22:18. [Google Scholar] [CrossRef]
- Dave, I.R.; Iyappan, G.I.; Prakash, S.; Ali, S.S.; Shrivastava, A.M. 3D Ear Biometrics: Acquisition and Recognition. In Proceedings of the INDICON 2018, Coimbatore, India, 16–18 December 2018. [Google Scholar]
- Kumar, G.; Tulyakov, S.; Govindaraju, V. Combination of symmetric hash functions for secure fingerprint matching. In Proceedings of the ICPR 2010, Istanbul, Turkey, 23–26 August 2010; pp. 890–893. [Google Scholar]
- Iyappan, G.I.; Ali, S.S.; Prakash, S. Geometric statistics-based descriptor for 3D ear recognition. Visual Comput. 2020, 36, 161–173. [Google Scholar]
- Sandhya, M.; Prasad, M.V.N.K. k-Nearest Neighborhood Structure (k-NNS) based alignment-free method for fingerprint template protection. In Proceedings of the ICB 2015, Phuket, Thailand, 19–22 May 2015; pp. 386–393. [Google Scholar]
- Sandhya, M.; Prasad, M.V.N.K.; Chillarige, R.R. Generating cancellable fingerprint templates based on Delaunay triangle feature set construction. IET Biom. 2016, 5, 131–139. [Google Scholar] [CrossRef]
- Sandhya, M.; Prasad, M.V.N.K. Securing fingerprint templates using fused structures. IET Biom. 2017, 6, 173–182. [Google Scholar] [CrossRef]
- Wang, S.; Deng, G.; Hu, J. A partial Hadamard transform approach to the design of cancelable fingerprint templates containing binary biometric representations. Patt. Recogn. 2017, 61, 447–458. [Google Scholar] [CrossRef]
- Derman, E.; Keskinoz, M. Normalized cross-correlation based global distortion correction in fingerprint image matching. In Proceedings of the IWSSIP 2016, Bratislava, Slovakia, 23–25 May 2016; pp. 1–4. [Google Scholar]
- Wang, S.; Hu, J. Alignment-free cancelable fingerprint template design: A densely infinite-to-one mapping (DITOM) approach. Patt. Recogn. 2012, 45, 4129–4137. [Google Scholar] [CrossRef]
- Si, X.; Feng, J.; Yuan, B.; Zhou, J. Dense registration of fingerprints. Patt. Recogn. 2017, 63, 87–101. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K.K.R. Unified Biometric Privacy Preserving Three-Factor Authentication and Key Agreement for Cloud-Assisted Autonomous Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-Factor Authentication with Security beyond Conventional Bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Wang, S.; Hu, J. A blind system identification approach to cancelable fingerprint templates. Patt. Recogn. 2016, 54, 14–22. [Google Scholar] [CrossRef]
- Ahn, D.; Kong, S.G.; Chung, Y.S.; Moon, K.Y. Matching with secure fingerprint templates using non-invertible transform. In Proceedings of the CISP 2008, Sanya, China, 27–30 May 2008; Volume 2, pp. 29–33. [Google Scholar]
- Tran, M.H.; Duong, T.N.; Nguyen, D.M.; Dang, Q.H. A local feature vector for an adaptive hybrid fingerprint matcher. In Proceedings of the ICIC 2017, Hanoi, Vietnam, 26–28 June 2017; pp. 249–253. [Google Scholar]
- Wang, S.; Yang, W.; Hu, J. Design of Alignment-Free Cancelable Fingerprint Templates with Zoned Minutia Pairs. Patt. Recogn. 2017, 66, 295–301. [Google Scholar] [CrossRef]
- Boult, T.E.; Scheirer, W.J.; Woodworth, R. Revocable fingerprint biotokens: Accuracy and security analysis. In Proceedings of the CVPR 2007, Minneapolis, MN, USA, 18–23 June 2007; pp. 1–8. [Google Scholar]
- Khan, T.M.; Bailey, D.G.; Khan, M.A.U.; Kong, Y. Efficient Hardware Implementation For Fingerprint Image Enhancement Using Anisotropic Gaussian Filter. IEEE Trans. Image Process. 2017, 26, 2116–2126. [Google Scholar] [CrossRef]
- Ali, S.S.; Iyappan, G.I.; Prakash, S.; Consul, P.; Mahyo, S. Securing biometric user template using modified minutiae attributes. Patt. Recogn. Lett. 2020, 129, 263–270. [Google Scholar] [CrossRef]
- Moujahdi, C.; Bebis, G.; Ghouzali, S.; Rziza, M. Fingerprint shell: Secure representation of fingerprint template. Patt. Recogn. Lett. 2014, 45, 189–196. [Google Scholar] [CrossRef]
- Ali, S.S.; Prakash, S. Enhanced Fingerprint Shell. In Proceedings of the SPIN 2015, Noida, India, 19–20 February 2015; pp. 801–805. [Google Scholar]
- Lee, S.; Jeong, I.R. On the Unlinkability of Fingerprint Shell. Secur. Commun. Netw. 2020, 2020, 8256929. [Google Scholar] [CrossRef]
- Taha, A.A.; Hanbury, A. An Efficient Algorithm for Calculating the Exact Hausdorff Distance. IEEE Trans. PAMI 2015, 37, 2153–2163. [Google Scholar] [CrossRef]
- NIST. NBIS. 2017. Available online: https://www.nist.gov/services-resources/software/nist-biometric-image-software-nbis (accessed on 1 December 2020).
- Lam, H.K.; Hou, Z.; Yau, W.Y.; Chen, T.P.; Li, J. A systematic topological method for fingerprint singular point detection. In Proceedings of the ICCARV 2008, Hanoi, Vietnam, 17–20 December 2008; pp. 967–972. [Google Scholar]
- Zhu, E.; Guo, X.; Yin, J. Walking to singular points of fingerprints. Patt. Recogn. 2016, 56, 116–128. [Google Scholar] [CrossRef]
- Wilcox, R. Kolmogoro-Smirnov Test. In Encyclopedia of Biostatistics; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2005. [Google Scholar]
- Eberz, S.; Rasmussen, K.B.; Lenders, V.; Martinovic, I. Evaluating Behavioral Biometrics for Continuous Authentication: Challenges and Metrics. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security (ASIA CCS’17), Abu Dhabi, United Arab Emirates, 2–6 April 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 386–399. [Google Scholar]
- Maio, D.; Maltoni, D.; Cappelli, R.; Wayman, J.L.; Jain, A.K. FVC2000: Fingerprint verification competition. IEEE Trans. PAMI 2002, 24, 402–412. [Google Scholar] [CrossRef]
- Jun, B.K.; Jaihie, K.; Ig-Jae, K.; Teoh, A.B.J. Cancelable fingerprint template design with randomized non-negative least squares. Pattern Recognit. 2019, 91, 245–260. [Google Scholar]
- Wang, D.; Gu, Q.; Huang, X.; Wang, P. Understanding Human-Chosen PINs: Characteristics, Distribution and Security. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security (ASIA CCS’17), Abu Dhabi, United Arab Emirates, 2–6 April 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 372–385. [Google Scholar]
- Sadeghi, K.; Banerjee, A.; Sohankar, J.; Gupta, K.S.S. Geometrical Analysis of Machine Learning Security in Biometric Authentication Systems. In Proceedings of the 2017 16th IEEE International Conference on Machine Learning and Applications (ICMLA), Cancun, Mexico, 18–21 December 2017; pp. 309–314. [Google Scholar] [CrossRef]
- Feng, Y.C.; Yuen, P.C. Binary Discriminant Analysis for Generating Binary Face Template. IEEE Trans. Inf. Forensics Secur. 2012, 7, 613–624. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s Law in Passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Inthavisas, K.; Lopresti, D. Secure speech biometric templates for user authentication. IET Biom. 2012, 1, 46–54. [Google Scholar] [CrossRef]
- Bonneau, J.; Herley, C.; van Oorschot, P.C.; Stajano, F. The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012; pp. 553–567. [Google Scholar]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Informatics 2018, 14, 4081–4092. [Google Scholar] [CrossRef]











| Database | Ali and Prakash [7] | Ali et al. [31] | Proposed Technique | |||
|---|---|---|---|---|---|---|
| Scenario I | Scenario II | Scenario I | Scenario II | Scenario I | Scenario II | |
| FVC2000 DB1 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| FVC2000 DB2 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| FVC2002 DB1 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| FVC2002 DB2 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| FVC2002 DB3 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| FVC2002 DB4 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| FVC2004 DB1 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| FVC2004 DB2 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| IIT KANPUR | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| Techniques | FVC2000 DB1 | FVC2000 DB2 | FVC2002 DB1 | FVC2002 DB2 | FVC2002 DB3 | FVC2002 DB4 | FVC2004 DB1 | FVC2004 DB2 | IIT Kanpur (Large Database) | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | |
| Cappelli et al. [35] | - | - | - | - | - | - | 1.64 | 1.00 | 3.18 | 0.68 | 0.49 | 0.89 | 7.18 | 3.14 | 8.96 | 5.75 | 3.00 | 7.46 | - | - | - | - | - | - | - | - | - |
| Kumar et al. [46] | - | - | - | - | - | - | - | - | - | - | 4.98 | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - |
| Derman and Keskinoz [52] | - | - | - | - | - | - | - | 6 | - | - | 6 | - | - | 14 | - | - | 7 | - | - | - | - | - | - | - | - | - | - |
| Ali and Prakash [19] | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | 0.001 | - |
| Ferrara et al. [36] | - | - | - | - | - | - | 3.14 | 1.88 | 5.07 | 1.43 | 0.99 | 2.54 | 10.04 | 5.24 | 12.43 | 9.75 | 4.84 | 11.89 | - | - | - | - | - | - | - | - | - |
| Moujahdi et al. [64] | - | - | - | - | - | - | 4.18 | 2.03 | 6.36 | 1.39 | 1.01 | 2.21 | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - |
| Ali and Prakash [65] | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | 0.001 | - |
| Ferrara et al. [37] | - | - | - | - | - | - | 3.1 | 2.0 | 4.3 | 1.3 | 1.1 | 1.4 | 8.4 | 4.4 | 11.8 | 5.0 | 3.1 | 6.6 | 6.8 | 3.0 | 9.1 | - | - | - | - | - | - |
| Ahn et al. [58] | - | - | - | - | - | - | - | 7.18 | - | - | 3.61 | - | - | 11.80 | - | - | 11.46 | - | - | - | - | - | - | - | - | - | - |
| Khan et al. [62] | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | 9.03 | - | - | 9.71 | - | - | - | - |
| Si et al. [54] | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | 1.96 | 0.89 | 3.36 | - | - | - |
| Boult et al. [61] | - | 2.9 | - | - | 2.5 | - | - | 2.1 | - | - | 1.2 | - | - | - | - | - | - | - | - | 8.6 | - | - | 7.5 | - | - | - | - |
| Ali et al. [31] | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Ali and Prakash [7] | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Tran et al. [59] | - | - | - | - | - | - | - | - | - | 0.67 | 0.49 | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - |
| Proposed Technique | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Techniques | FVC2002 | IIT Kanpur (Large Database) | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| DB1 | DB2 | DB3 | DB4 | ||||||||||||
| FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | FMR | EER | Zero | |
| Sandhya et al. [49] | - | 0 | - | - | 0 | - | - | 1.65 | - | - | - | - | - | - | - |
| Cappelli et al. [35] | 0 | 0 | 0 | 0 | 0 | 0 | 3 | 2 | 5 | 5 | 3.48 | 5 | - | - | - |
| Sandhya et al. [50] | - | 0 | - | - | 0 | - | - | 1.65 | - | - | - | - | - | - | - |
| Ferrara et al. [36] | 0 | 0 | 0 | 0 | 0.02 | 1 | 4 | 3.43 | 5 | 9 | 3.37 | 11 | - | - | - |
| Sandhya et al. [48] | - | 0 | - | - | 0 | - | - | 3.65 | - | - | - | - | - | - | - |
| Ali et al. [33] | - | 0 | - | - | 0 | - | - | 0 | - | - | - | - | - | - | - |
| Liu and Zhao [38] | 0 | - | 0 | 0 | - | 0 | - | - | - | - | - | - | - | - | - |
| Ali et al. [31] | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Ali and Prakash [7] | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Proposed Technique | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sharma, U.; Tomar, P.; Ali, S.S.; Saxena, N.; Bhadoria, R.S. Optimized Authentication System with High Security and Privacy. Electronics 2021, 10, 458. https://doi.org/10.3390/electronics10040458
Sharma U, Tomar P, Ali SS, Saxena N, Bhadoria RS. Optimized Authentication System with High Security and Privacy. Electronics. 2021; 10(4):458. https://doi.org/10.3390/electronics10040458
Chicago/Turabian StyleSharma, Uttam, Pradeep Tomar, Syed Sadaf Ali, Neetesh Saxena, and Robin Singh Bhadoria. 2021. "Optimized Authentication System with High Security and Privacy" Electronics 10, no. 4: 458. https://doi.org/10.3390/electronics10040458
APA StyleSharma, U., Tomar, P., Ali, S. S., Saxena, N., & Bhadoria, R. S. (2021). Optimized Authentication System with High Security and Privacy. Electronics, 10(4), 458. https://doi.org/10.3390/electronics10040458









