Cyber Resilience Meta-Modelling: The Railway Communication Case Study †
Abstract
1. Introduction
- 1.
- the emerging threats characterised by the deliberate attempt to disrupt or obfuscate the expected information flows [2];
- 2.
- triggered by a cyber-breach as a result of an attack (e.g., Distributed Denial of Service (DDoS) denying to legitimate users the access to services [3]; or
- 3.
- simply can be the results of software glitches, hardware failures or disruption, loss of connections or energy, etc.
2. Background on Cyber-Resilience
- Capacity-based: An indirect quantification through the potential (capability) for resilience [23]
2.1. Functionality-Based Approach
- Plan/Prepare: It includes all actions needed to keep the system functionality within an acceptable range of functioning during known and unknown critical events.
- Absorb: It is related to the mitigation of the impact of the assets and services disruption applying countermeasures as isolation,
- Recover: It is related to the system’s functionality restoration to the status before the disruption (bounce-back).
- Adapt: It evolves the system to a new level (bounce forward) using the new knowledge coming from the lesson learnt. Adaptation strategies may include new configurations of the system, personnel training, different decision making structures, etc.
2.2. Capacity-Based Approach
- Respond: Knowing what to do
- Monitor: Knowing what to look for
- Anticipate: Knowing what to expect
- Learn: Knowing what has happened
2.3. Merging the Views: Resilience as an Emerging Property of a Synergistic Dynamic Dual System
- Adaptive Capacity
- Coping Ability
- Assets
- Human: It includes technical skills, expertise and competencies (knowledge), as well as cognitive resources, particularly those relating to decision-making processes. These resources should be investigated within all relevant operational and managerial contexts. From an end-user perspective, both individual and collective behaviours (i.e., risk awareness, perceptions and aversion, among other aspects) are critical factors to be considered, as they may critically impact on the effectiveness and application of key outputs.
- Technology: It comprises ICT as well as built artefacts and infrastructure as implemented by the utilities (energy, oil and gas and water networks), transport networks, signalling systems, traffic control and ticketing related assets.
- Organisation: It includes hierarchical structures and formal procedures and regulations, as well as logistics elements.
- Finance: It includes the number of financial resources available in the system and their dynamics and the risk managed (assurance).
- Critical Functions
- Buffer Capacities (BC) refers to the kind/quantity of damage a system can absorb without a critical function failure.
- Flexibility (FX) reflects the capability of the system to balance between opposite critical features. An example is constituted by the need of the balance between an efficient centralised organisation and a flexible distributed one.
- Margin (MA) deals with how far the system is pushed to its limit in accomplishing its task. In other words, it is used to compute the capability of the system to tolerate some variations in parameter values.
- Tolerance (TO) is related to the distance between the system nominal performance/quality index and the actual ones. It determines if the system is able to respond to a stressor properly.
- Need of Formalisation
3. The Cyber-Resilience Meta-Model
The Cyber-Resilience Domain Model
4. Integrating and Using the Meta-Model
4.1. A Model-Driven Process
4.2. The Annotated Functional Model
4.3. Generating the Formal Quantitative Model
- R1
- Each annotated use case or component generates one binary BN variable (e.g., an {on,off} variable according to the activation state of the function/component). The only exception is constituted by adaptive capacities.
- R2
- Each “include” tagged dependency makes in a hierarchical relation two use case, and hence two BN variables. A failure of an “included” use case determines a failure of the “including” use case that includes. On the BN model side, the variable generated by the included use case is a parent for the BN variables related to the including ones.
- R3
- The same situation as R2 is for the “depends on from” dependency. In this case, the depending use case plays the role of the including one. The corresponding BN variables are in the parent–child relationship as in the previous case.
- R4
- Another situation where parent–child relationships are created in the BN model is when an “asset”-annotated component is contained into another “asset” one.
- R5
- This rule takes care of the “affects” dependency relationships occurring between a “stressor” and the “asset” that is under attack. In this case, the tagged values related to the “affects” stereotype (see Figure 7) are used to define the parent–child relationship in the BN model. First, the exploits tagged value is used to determine the component that exposes the reported vulnerability (i.e., in the example, V1). Second, the succProb is used in the CPT of the parent BN variable to determine the impact of the attack to the critical function/asset under attack. As a sample, the CPT of the C1A is reported in Table 1: is the success probability of Alpha while is the one of Green.
- R6
- The last rule is related to the resilience-related mechanisms. As an example, the relationship in the high-level model from the “protection”-annotated use case (i.e., Green in the model) to the “stressor” Alpha determines the generation of two links in the BN model. The first is related to the parent–child relationship from Alpha BN node to Green: this BN link represents the activation of the protection mechanism. The second link is instead related to the effect of the protection system to the healing effects of the resilience mechanisms, and is represented in the BN model by the link from Green to C1A (that is, the subject of the attack).
| Alpha | Green | ||
|---|---|---|---|
| 1 | 0 | ||
| 1 | 0 | ||
| 1–p1 | p1 | ||
| p2 | 1–p2 |
- The names of both UML’s Use Cases and Components can be inferred by the name property.
- getSourceUC()-getDestUC() are methods of an “include” relationships functions returning the source and the destination use case.
- getChildern() is a method of the UML’s components returning the list of sub-components.
- getProvidedBy() is a method of the use cases able to retrieve the list of the components reported in the providedBy property.
- isStressor() and isProtection() are methods to understand whether the use case is tagged with the relative stereotypes.
- getAffected() is a method of the UML’s use case able to return the components and the use cases that are affected by the “stressor”.
- getSuccessProb() extracts the value of the successProb tagged value of a “stressor”.
- Given a “protection”, the activations() and u.protected() methods, respectively, return the lists of the use cases that activate (i.e., the stressors) and are protected by (i.e., the critical functions) the protection mechanism.
- addNode()-addLink(), given a BN, add a node and a link between two nodes, respectively.
- getNode() retrieves the node of a BN from the name while setCPT() builds and sets to a node a CPT according to the schema defined in Table 1 and on the base of a specified value of probability.
| Algorithm 1: Generation of the BN model pseudo-algorithm. |
 |
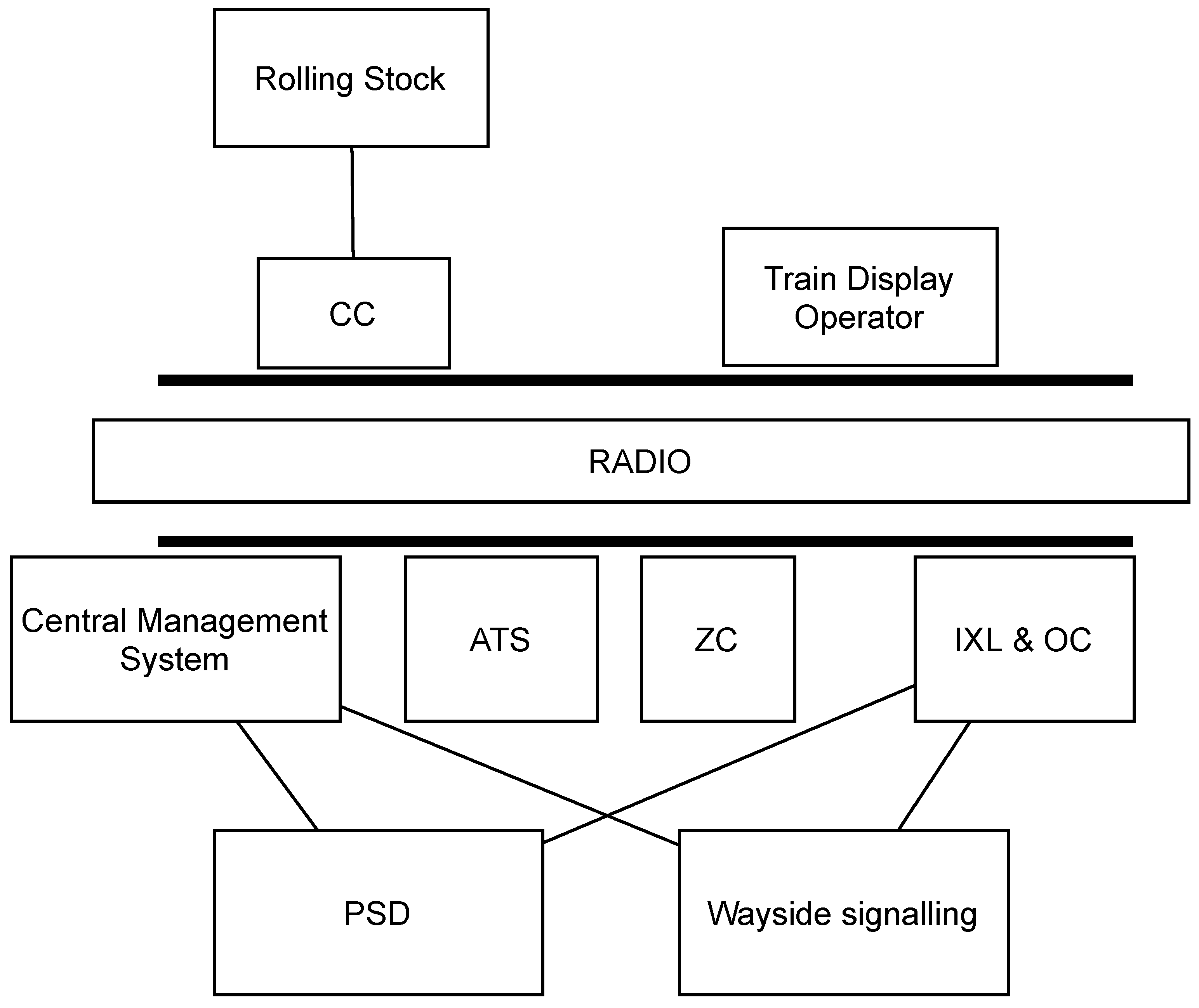
5. The Secure Metro Communication Case Study
- Signalling: The combination of the interlocking and communication system that transmits the information necessary to control the train movement to the on-board subsystem
- Automation: Trains scheduling and interface with the central operator
- Power Supply: Line electrification and supply of all civil loads in a metro system (e.g., station lighting and elevators)
- Platform Screen Doors: Doors on the platform to screen it from the train
- Passengers Information System: Communication system from centre to passengers devoted to providing timely and correct information (video-walls, monitors, speakers, etc.)
Applicability Evaluation
- a.
- The delivery of MALs from ZC to CC
- b.
- The possibility of having timely and correct information in the case of emergency evacuation
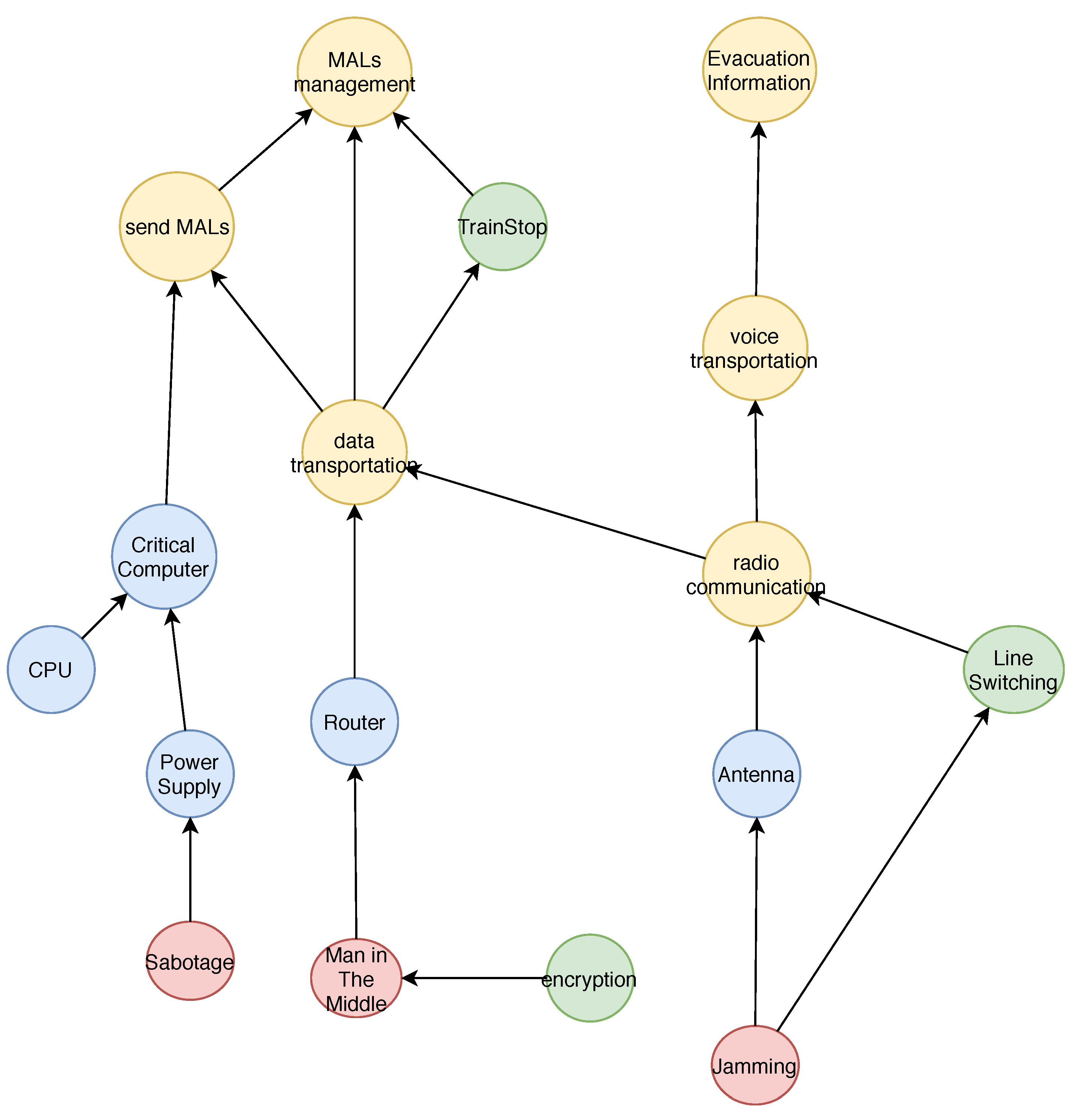
- 1.
- A man-in-the-middle attack, exploiting software vulnerabilities of the router to intrude into the communication between ZC and CC
- 2.
- A jamming attack devoted to disturbing the frequency of radio communication
- 3.
- A physical sabotage oriented to interrupt the power supply to critical wayside computers (i.e., the ZC)
6. Related Works
7. Conclusions and Future Works
- integration of the proposed modelling method into an existing industrial risk management process;
- usage of the UML Profile with another “analysis-level” formalism (e.g., Petri Nets); and
- definition of a final software package implementing the approach.
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ATC | Automatic Train Control |
| ATO | Automatic Train Operation |
| ATP | Automatic Train Protection |
| ATS | Automatic Train Supervision |
| BC | Buffer Capacities |
| BN | Bayesian Network |
| Bot | Internet Robots |
| CBD | Contract Based Design |
| CTBC | Communication-Based Train Control |
| CC | Carborne Controller |
| C&C | Command and Control |
| CODOT | Colorado Department of Transport |
| CPT | Conditional Probability Table |
| DAG | Direct Acyclic Graph |
| DDoS | Distributed Denial of Service |
| DSML | Domain Specific Modelling Language |
| FBC | Function Buffer Capacities |
| FDC | Function Dumping Capacity |
| FF | Function Flexibility |
| FM | Function Margin |
| FRAM | Functional Resonance Analysis Method |
| FTO | Function Tolerance |
| FT | Fault Tree |
| FX | Flexibility |
| GSPN | Generalised Stochastic Petri Nets |
| HCPS | Human-Cyber-Physical Systems |
| IoT | Internet of Things |
| IXL | Interlocking |
| MA | Margin |
| MALs | Movement Authority Limits |
| MDE | Model-Driven Engineering |
| MDP | Markov Decision Process |
| NAS | National Academy of Science |
| OC | Object Controller |
| PSDs | Platform Screen Doors |
| POMDP | Partially Observable Markov Decision Process |
| PPS | Physical Protection System |
| RC | Resilience Contracts |
| TO | Tolerance |
| UML | Unified Modelling Language |
| UTS | Urban Transport System |
| V&V | Verification and Validation |
| ZC | Zone Controller |
References
- Vespignani, A. Complex networks: The fragility of interdependency. Nature 2010, 464, 984–985. [Google Scholar] [CrossRef]
- Linkov, I.; Baiardi, F.; Florin, M.V.; Greer, S.; Lambert, J.; Pollock, M.; Rickli, J.M.; Roslycky, L.; Seager, T.; Thorisson, H.; et al. Applying Resilience to Hybrid Threats. IEEE Secur. Priv. 2019, 17, 78–83. [Google Scholar] [CrossRef]
- Shiaeles, S.; Papadaki, M. FHSD: An improved IP spoof detection method for web DDoS attacks. Comput. J. 2015, 58, 892–903. [Google Scholar] [CrossRef]
- Bellini, E.; Gaitanidou, E.; Bekiaris, E.; Ferreira, P. The RESOLUTE project’s European Resilience Management Guidelines for Critical Infrastructure: Development, operationalisation and testing for the urban transport system. Environ. Syst. Decis. 2020, 40, 321–341. [Google Scholar] [CrossRef]
- Bellini, E.; Bellini, A.; Pirri, F.; Coconea, L. Towards a Trusted Virtual Smart Cities Operation Center Using the Blockchain Mirror Model. In Internet Science; El Yacoubi, S., Bagnoli, F., Pacini, G., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 283–291. [Google Scholar]
- Bellini, A.; Bellini, E.; Gherardelli, M.; Pirri, F. Enhancing IoT Data Dependability through a Blockchain Mirror Model. Future Internet 2019, 11, 117. [Google Scholar] [CrossRef]
- Brotsis, S.; Kolokotronis, N.; Limniotis, K.; Shiaeles, S.; Kavallieros, D.; Bellini, E.; Pavué, C. Blockchain Solutions for Forensic Evidence Preservation in IoT Environments. In Proceedings of the 2019 IEEE Conference on Network Softwarization (NetSoft), Paris, France, 24–28 June 2019; pp. 110–114. [Google Scholar] [CrossRef]
- Díaz-Verdejo, J.; Lei, C.; Zhang, H.Q.; Tan, J.L.; Zhang, Y.C.; Liu, X.H. Moving Target Defense Techniques: A Survey. Secur. Commun. Netw. 2018. [Google Scholar] [CrossRef]
- Bellini, E.; Marrone, S. Towards a Novel Conceptualization of Cyber Resilience. In Proceedings of the 2020 IEEE World Congress on Services (SERVICES), Beijing, China, 18–23 October 2020. [Google Scholar]
- Jackson, S. Architecting Resilient Systems: Accident Avoidance and Survival and Recovery from Disruptions; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2009; pp. 1–297. [Google Scholar] [CrossRef]
- Vugrin, E.; Warren, D.; Ehlen, M.; Camphouse, R. A Framework for Assessing the Resilience of Infrastructure and Economic Systems. In Sustainable and Resilient Critical Infrastructure Systems; Gopalakrishnan, K., Peeta, S., Eds.; Springer: Berlin, Germany, 2010; pp. 77–116. [Google Scholar] [CrossRef]
- Linkov, I.; Kott, A. Fundamental Concepts of Cyber Resilience: Introduction and Overview. In Cyber Resilience of Systems and Networks; Kott, A., Linkov, I., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 1–25. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. NIST Cybersecurity Framework; NIST: Gaithersburg, MD, USA, 2018. [Google Scholar]
- Accenture. The Nature of Effective Defense: Shifting from Cybersecurity to Cyber Resilience; Accenture: Dublin, Ireland, 2018. [Google Scholar]
- Bellini, E.; Ceravolo, P.; Nesi, P. Quantify resilience enhancement of UTS through exploiting connected community and internet of everything emerging technologies. ACM Trans. Internet Technol. 2017, 18, 1–34. [Google Scholar] [CrossRef]
- Bellini, E.; Nesi, P.; Pantaleo, G.; Venturi, A. Functional Resonance Analysis Method Based-Decision Support Tool for Urban Transport System Resilience Management. In Proceedings of the IEEE International Smart Cities Conference (ISC2), Trento, Italy, 12–15 September 2016. [Google Scholar]
- CISCO. Cyber-Resilience: Safeguarding the Digital Organization; CISCO: San Jose, CA, USA, 2016. [Google Scholar]
- Bodeau, D.J.; Graubart, R. Cyber Resiliency Engineering Framework; MITRE Corporation: McLean, VA, USA, 2011. [Google Scholar]
- Committee on Payments and Market Infrastructures Board of the International Organization of Securities Commissions. Guidance on Cyber-Resilience for Financial Market Infrastructures; Bank for International Settlements and International Organization of Securities Commissions: Basel, Switzerland, 2016. [Google Scholar]
- Hinkel, J. Indicators of vulnerability and adaptive capacity: Towards a clarification of the science-policy interface. Glob. Environ. Chang. 2011, 21, 198–208. [Google Scholar] [CrossRef]
- Ganin, A.; Massaro, E.; Gutfraind, A.; Steen, N.; Keisler, J.; Kott, A.; Mangoubi, R.; Linkov, I. Operational resilience: Concepts, design and analysis. Sci. Rep. 2016, 6, 1–12. [Google Scholar] [CrossRef] [PubMed]
- Cimellaro, G.; Reinhorn, A.; Bruneau, M. Framework for analytical quantification of disaster resilience. Eng. Struct. 2010, 32, 3639–3649. [Google Scholar] [CrossRef]
- Bellini, E.; Coconea, L.; Nesi, P. A Functional Resonance Analysis Method Driven Resilience Quantification for Socio-Technical Systems. IEEE Syst. J. 2020, 14, 1234–1244. [Google Scholar] [CrossRef]
- Linkov, I.; Eisenberg, D.; Plourde, K.; Seager, T.; Allen, J.; Kott, A. Resilience metrics for cyber systems. Environ. Syst. Decis. 2013, 33, 471–476. [Google Scholar] [CrossRef]
- Aven, T. Quantitative Risk Assessment: The Scientific Platform; Cambridge University Press: Cambridge, UK, 2011; pp. 1–211. [Google Scholar] [CrossRef]
- Kahan, J.; Allen, A.; George, J. An Operational Framework for Resilience. J. Homel. Secur. Emerg. Manag. 2009, 6, 1–48. [Google Scholar] [CrossRef]
- Como, G.; Savla, K.; Acemoglu, D.; Dahleh, M.; Frazzoli, E. Robust distributed routing in dynamical networks-part II: Strong resilience, equilibrium selection and cascaded failures. IEEE Trans. Autom. Control. 2013, 58, 333–348. [Google Scholar] [CrossRef]
- Ouyang, M.; Dueñas-Osorio, L.; Min, X. A three-stage resilience analysis framework for urban infrastructure systems. Struct. Saf. 2012, 36–37, 23–31. [Google Scholar] [CrossRef]
- Henry, D.; Emmanuel Ramirez-Marquez, J. Generic metrics and quantitative approaches for system resilience as a function of time. Reliab. Eng. Syst. Saf. 2012, 99, 114–122. [Google Scholar] [CrossRef]
- Baroud, H.; Ramirez-Marquez, J.; Barker, K.; Rocco, C. Stochastic Measures of Network Resilience: Applications to Waterway Commodity Flows. Risk Anal. 2014, 34, 1317–1335. [Google Scholar] [CrossRef]
- Jovanovic, A.S.; Schmid, N.; Klimek, P.; Choudhary, A. Use of Indicators for Assessing Resilience of Smart Critical Infrastructures; Resource Guide on Resilience; EPFL International Risk Governance Center: Lausanne, Switzerland, 2016. [Google Scholar]
- Wilson, J.; Ryan, B.; Schock, A.; Ferreira, P.; Smith, S.; Pitsopoulos, J. Understanding safety and production risks in rail engineering planning and protection. Ergonomics 2009, 52, 774–790. [Google Scholar] [CrossRef]
- Ferreira, P.; Bellini, E. Managing Interdependencies in Critical Infrastructures: A Cornerstone for System Resilience; Safety and Reliability-Safe Societies in a Changing World. In Proceedings of the 28th International European Safety and Reliability Conference, ESREL 2018, Trondheim, Norway, 17–21 June 2018; pp. 2687–2692. [Google Scholar]
- Hollnagel, E.; Woods, D.; Leveson, N. Resilience engineering: Concepts and Precepts; Ashgate Publishing Limited: Hampshire, UK, 2006; pp. 1–397. [Google Scholar]
- Sutcliffe, K.; Vogus, T.; Sutcliffe, K.M.; Vogus, T.J. Organizing for Resilience. In Positive Organizational Scholarship: Foundations of a New Discipline; Cameron, K.S., Dutton, J.E., Quinn, R.E., Eds.; Berrett-Koehler: San Francisco, CA, USA, 2003; pp. 94–110. [Google Scholar]
- Hollnagel, E.; Pariés, J.; Woods, D.; Wreathall, J. Resilience Engineering in Practice: A Guidebook; CRC Press: Boca Raton, FL, USA, 2011; pp. 1–322. [Google Scholar]
- Bellini, E.; Nesi, P.; Coconea, L.; Ferreira, P.; Simoes, A.; Gaitanidou, E.; Candelieri, A. Towards resilience operationalization in Urban Transport System: The RESOLUTE project approach. In Proceedings of the 26th European Safety and Reliability Conference on Risk, Reliability and Safety: Innovating Theory and Practice, Glasgow, Scotland, 25–29 September 2016. [Google Scholar]
- Bellini, E.; Bellini, P.; Cenni, D.; Nesi, P.; Pantaleo, G.; Paoli, I.; Paolucci, M. An IoE and Big Multimedia Data Approach for Urban Transport System Resilience Management in Smart Cities. Sensors 2021, 21, 435. [Google Scholar] [CrossRef] [PubMed]
- Sikula, N.; Mancillas, J.; Linkov, I.; McDonagh, J. Risk management is not enough: A conceptual model for resilience and adaptation-based vulnerability assessments. Environ. Syst. Decis. 2015, 35, 219–228. [Google Scholar] [CrossRef]
- Marrone, S.; Nardone, R.; Tedesco, A.; D’Amore, P.; Vittorini, V.; Setola, R.; De Cillis, F.; Mazzocca, N. Vulnerability modeling and analysis for critical infrastructure protection applications. Int. J. Crit. Infrastruct. Prot. 2013, 6, 217–227. [Google Scholar] [CrossRef]
- Drago, A.; Marrone, S.; Mazzocca, N.; Nardone, R.; Tedesco, A.; Vittorini, V. A model-driven approach for vulnerability evaluation of modern physical protection systems. Softw. Syst. Model. 2019, 18, 523–556. [Google Scholar] [CrossRef]
- Flammini, F.; Marrone, S.; Mazzocca, N.; Nardone, R.; Vittorini, V. Model-driven V&V processes for computer based control systems: A unifying perspective. In International Symposium On Leveraging Applications of Formal Methods, Verification and Validation; Springer: Berlin/Heidelberg, Germany, 2012; pp. 190–204. [Google Scholar] [CrossRef]
- Nardone, R.; Rodriguez, R.; Marrone, S. Formal Security Assessment of Modbus Protocol. In Proceedings of the 2016 11th International Conference for Internet Technology and Secured Transactions (ICITST), Barcelona, Spain, 5–7 December 2017; pp. 142–147. [Google Scholar]
- Bernardi, S.; Gentile, U.; Marrone, S.; Merseguer, J.; Nardone, R. Security modelling and formal verification of survivability properties: Application to cyber–physical systems. J. Syst. Softw. 2020, 171, 110746. [Google Scholar] [CrossRef]
- Charniak, E. Bayesian Networks Without Tears: Making Bayesian Networks More Accessible to the Probabilistically Unsophisticated. AI Mag. 1991, 12, 50–63. [Google Scholar]
- Weber, P.; Medina-Oliva, G.; Simon, C.; Lung, B. Overview on Bayesian Networks Applications for Dependability, Risk Analysis and Maintenance Areas. Eng. Appl. Artif. Intell. 2012, 25, 671–682. [Google Scholar] [CrossRef]
- Frigault, M.; Wang, L. Measuring Network Security Using Bayesian Network-Based Attack Graphs. In Proceedings of the 32th Annual IEEE International Computer Software and Applications Conference, Turku, Finland, 28 July–1 August 2008; pp. 698–703. [Google Scholar] [CrossRef]
- Gentile, U.; Marrone, S.; Nardone, R.; Bellini, E. Computer-aided security assessment of water networks monitoring platforms. Int. J. Crit. Infrastruct. Prot. 2020, 31. [Google Scholar] [CrossRef]
- IEEE Standard for Communications-Based Train Control (CBTC) Performance and Functional Requirements. In IEEE Std 1474.1-2004 (Revision of IEEE Std 1474.1-1999); IEEE: Piscataway Township, NJ, USA, 2004; pp. 1–45. [CrossRef]
- Sterbenz, J.P. Smart city and IoT resilience, survivability, and disruption tolerance: Challenges, modelling, and a survey of research opportunities. In Proceedings of the 2017 9th International Workshop on Resilient Networks Design and Modeling (RNDM), Alghero, Italy, 4–6 September 2017; pp. 1–6. [Google Scholar]
- Campanile, L.; Gribaudo, M.; Iacono, M.; Marulli, F.; Mastroianni, M. Computer network simulation with ns-3: A systematic literature review. Electronics 2020, 9, 272. [Google Scholar] [CrossRef]
- Avižienis, A.; Laprie, J.C.; Randell, B.; Landwehr, C. Basic concepts and taxonomy of dependable and secure computing. IEEE Trans. Dependable Secur. Comput. 2004, 1, 11–33. [Google Scholar] [CrossRef]
- Orojloo, H.; Azgomi, M. Modelling and evaluation of the security of cyber-physical systems using stochastic Petri nets. IET Cyber-Phys. Syst. Theory Appl. 2019, 4, 50–57. [Google Scholar] [CrossRef]
- Albasrawi, M.; Jarus, N.; Joshi, K.; Sarvestani, S. Analysis of Reliability and Resilience for Smart Grids. In Proceedings of the 38th Annual Computer Software and Applications Conference, Vasteras, Sweden, 21–25 July 2014; pp. 529–534. [Google Scholar]
- Hosseini, S.; Barker, K. Modeling infrastructure resilience using Bayesian networks: A case study of inland waterway ports. Comput. Ind. Eng. 2016, 93, 252–266. [Google Scholar] [CrossRef]
- Camara, J.; De Lemos, R. Evaluation of Resilience in Self-Adaptive Systems using Probabilistic Model-Checking. In Proceedings of the 7th International Symposium on Software Engineering for Adaptive and Self-Managing Systems (SEAMS), Zurich, Switzerland, 4–5 June 2012; pp. 53–62. [Google Scholar] [CrossRef]
- LeMay, E.; Ford, M.; Keefe, K.; Sanders, W.; Muehrcke, C. Model-based Security Metrics Using ADversary VIew Security Evaluation (ADVISE). In Proceedings of the 8th International Conference on Quantitative Evaluation of SysTems, Aachen, Germany, 5–8 September 2011; pp. 191–200. [Google Scholar] [CrossRef]
- Bagheri, E.; Ghorbani, A.A. UML-CI: A reference model for profiling critical infrastructure systems. Inf. Syst. Front. 2010, 12, 115–139. [Google Scholar] [CrossRef]
- Lund, M.S.; Solhaug, B.; Stølen, K. Risk analysis of changing and evolving systems using CORAS. In Foundations of Security Analysis and Design VI; Springer: Berlin/Heidelberg, Germany, 2011; pp. 231–274. [Google Scholar] [CrossRef]
- Jürjens, J. Secure Systems Development with UML; Springer: Berlin/Heidelberg, Germany, 2005; pp. 1–309. [Google Scholar]
- OMG. UML Profile for MARTE: Modeling and Analysis of Real-time Embedded Systems; Object Management Group: Needham, MA, USA, 2011. [Google Scholar]
- Bernardi, S.; Merseguer, J.; Petriu, D.C. A dependability profile within MARTE. Softw. Syst. Model. 2011, 10, 313–336. [Google Scholar] [CrossRef]
- Do, C.; Tran, N.; Hong, C.; Kamhoua, C.; Kwiat, K.; Blasch, E.; Ren, S.; Pissinou, N.; Iyengar, S. Game theory for cyber security and privacy. ACM Comput. Surv. 2017, 50, 30–37. [Google Scholar] [CrossRef]
- Halpern, J. Beyond Nash Equilibrium: Solution Concepts for the 21st Century. In Proceedings of the 27th ACM symposium on Principles of distributed computing, Toronto, ON, Canada, 18–21 August 2008; pp. 1–9. [Google Scholar]
- Bellini, E.; Bagnoli, F.; Ganin, A.A.; Linkov, I. Cyber Resilience in IoT Network: Methodology and Example of Assessment through Epidemic Spreading Approach. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; Volume 2642-939X, pp. 72–77. [Google Scholar] [CrossRef]
- Bagnoli, F.; Bellini, E.; Massaro, E. A self-organized method for computing the epidemic threshold in computer networks. In International Conference on Internet Science; Springer: Cham, Switzerland, 2018; pp. 119–130. [Google Scholar] [CrossRef]
- Bagnoli, F.; Bellini, E.; Massaro, E. Risk Perception and Epidemics in Complex Computer Networks. In Proceedings of the 2018 IEEE Workshop on Complexity in Engineering (COMPENG), Florence, Italy, 10–12 October 2018. [Google Scholar]
- Farooq, M.J.; Zhu, Q. On the Secure and Reconfigurable Multi-Layer Network Design for Critical Information Dissemination in the Internet of Battlefield Things (IoBT). IEEE Trans. Wirel. Commun. 2018, 17, 2618–2632. [Google Scholar] [CrossRef]
- Madni, A.; Erwin, D.; Sievers, M. Constructing models for systems resilience: Challenges, concepts, and formal methods. Systems 2020, 8, 3. [Google Scholar] [CrossRef]
- Sangiovanni-Vincentelli, A.; Damm, W.; Passerone, R. Taming Dr. Frankenstein: Contract-based design for cyber-physical systems. Eur. J. Control. 2012, 18, 217–238. [Google Scholar] [CrossRef]
- Le Traon, Y.; Baudry, B.; Jézéquel, J.M. Design by contract to improve software vigilance. IEEE Trans. Softw. Eng. 2006, 32, 571–586. [Google Scholar] [CrossRef]
- Cimatti, A.; Tonetta, S. A Property-Based Proof System for Contract-Based Design. In Proceedings of the 38th Euromicro Conference on Software Engineering and Advanced Applications, Cesme, Turkey, 5–8 September 2012; pp. 21–28. [Google Scholar] [CrossRef]
- Büchi, J.R. Symposium on Decision Problems: On a Decision Method in Restricted Second Order Arithmetic. Stud. Log. Found. Math. 1966, 44, 1–11. [Google Scholar] [CrossRef]
- Hossain, N.; Nagahi, M.; Jaradat, R.; Shah, C.; Buchanan, R.; Hamilton, M. Modeling and assessing cyber resilience of smart grid using Bayesian network-based approach: A system of systems problem. J. Comput. Des. Eng. 2020, 7, 352–366. [Google Scholar] [CrossRef]
- Wang, Y. Resilience Quantification for Probabilistic Design of Cyber-Physical System Networks. Asce-Asme J. Risk Uncertain. Eng. Syst. Part Mech. Eng. 2018, 4. [Google Scholar] [CrossRef]
- Patriarca, R.; Falegnami, A.; Costantino, F.; Di Gravio, G.; De Nicola, A.; Villani, M. WAx: An integrated conceptual framework for the analysis of cyber-socio-technical systems. Saf. Sci. 2021, 136. [Google Scholar] [CrossRef]
- Katsikeas, S.; Hacks, S.; Johnson, P.; Ekstedt, M.; Lagerström, R.; Jacobsson, J.; Wällstedt, M.; Eliasson, P. An Attack Simulation Language for the IT Domain. In International Workshop on Graphical Models for Security; Springer: Cham, Switzerland, 2020; pp. 67–86. [Google Scholar] [CrossRef]
- Gossen, F.; Margaria, T.; Neubauer, J.; Steffen, B. A model-driven and generative approach to holistic security. In Resilience of Cyber-Physical Systems; Flammini, F., Ed.; Springer: Cham, Switzerland, 2019; pp. 123–147. [Google Scholar] [CrossRef]













| Reference | Topic | Improvement of This Paper |
|---|---|---|
| [74] | The work provides a method for modelling and evaluation of cyber resilience with BNs. | This paper introduces a wider model-driven approach. |
| [63,64] | The work is based on game theory. | This paper provides a modelling framework easier to use. |
| [40] | The work presents a UML Profile for modelling and analysis of physical security. | This paper also deals with cyber assets. |
| [41] | Model-driven approach for survivability evaluation by means of UML and BN. | The scope of the introduced domain model/UML Profile is wider than the presented scope. |
| [53] | The work is based on GSPNs | The presented work introduces a model-driven approach. |
| [54] | This work is based on FT. | FT demonstrated their limitation since they allow just few analysis and do not have advanced modelling features (i.e., common cause, multi-state variables, etc.). |
| [55,75] | The work uses BNs | The work does not apply any model-driven principle. Low level modelling is an error-prone activity. |
| [76] | It defines a conceptual model for cyber resilience | This paper does not provide any practical modelling and analysis approach. |
| [77] | It defines a DSML for the modelling of a computer-based infrastructure. | This work is based on simulation while the presented work is based on a formal—more powerful—analysis method. |
| [78] | This work presents a model-driven approach for generating code skeletons for injecting security in complex software-based systems | The presented approach can be used during the design-time phases. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bellini, E.; Marrone, S.; Marulli, F. Cyber Resilience Meta-Modelling: The Railway Communication Case Study. Electronics 2021, 10, 583. https://doi.org/10.3390/electronics10050583
Bellini E, Marrone S, Marulli F. Cyber Resilience Meta-Modelling: The Railway Communication Case Study. Electronics. 2021; 10(5):583. https://doi.org/10.3390/electronics10050583
Chicago/Turabian StyleBellini, Emanuele, Stefano Marrone, and Fiammetta Marulli. 2021. "Cyber Resilience Meta-Modelling: The Railway Communication Case Study" Electronics 10, no. 5: 583. https://doi.org/10.3390/electronics10050583
APA StyleBellini, E., Marrone, S., & Marulli, F. (2021). Cyber Resilience Meta-Modelling: The Railway Communication Case Study. Electronics, 10(5), 583. https://doi.org/10.3390/electronics10050583








