Security Issues with In-Vehicle Networks, and Enhanced Countermeasures Based on Blockchain
Abstract
1. Introduction
- Detailed security issues with in-vehicle network protocols (CAN, FlexRay, and automotive Ethernet) are provided.
- A detailed survey of various security attacks on CAN bus networks is provided, along with the intrusion detection systems that were developed to prevent those attacks. We investigate those IDSs and address their advantages and disadvantages.
- A survey of attacks and security solutions for automotive Ethernet and FlexRay protocols is provided.
- We suggest a way to improve the security of in-vehicle networks by using a hybrid blockchain framework.
- We suggest open research issues and future research directions for in-vehicle network security.
2. In-Vehicle Networks
2.1. The Controller Area Network Protocol
CAN Bus Attack Interfaces
2.2. Automotive Ethernet Protocol
2.3. FlexRay Protocol
3. Related Works
4. Security Issues and Countermeasures for In-Vehicle Networks
4.1. Security Issues and Countermeasures for CAN
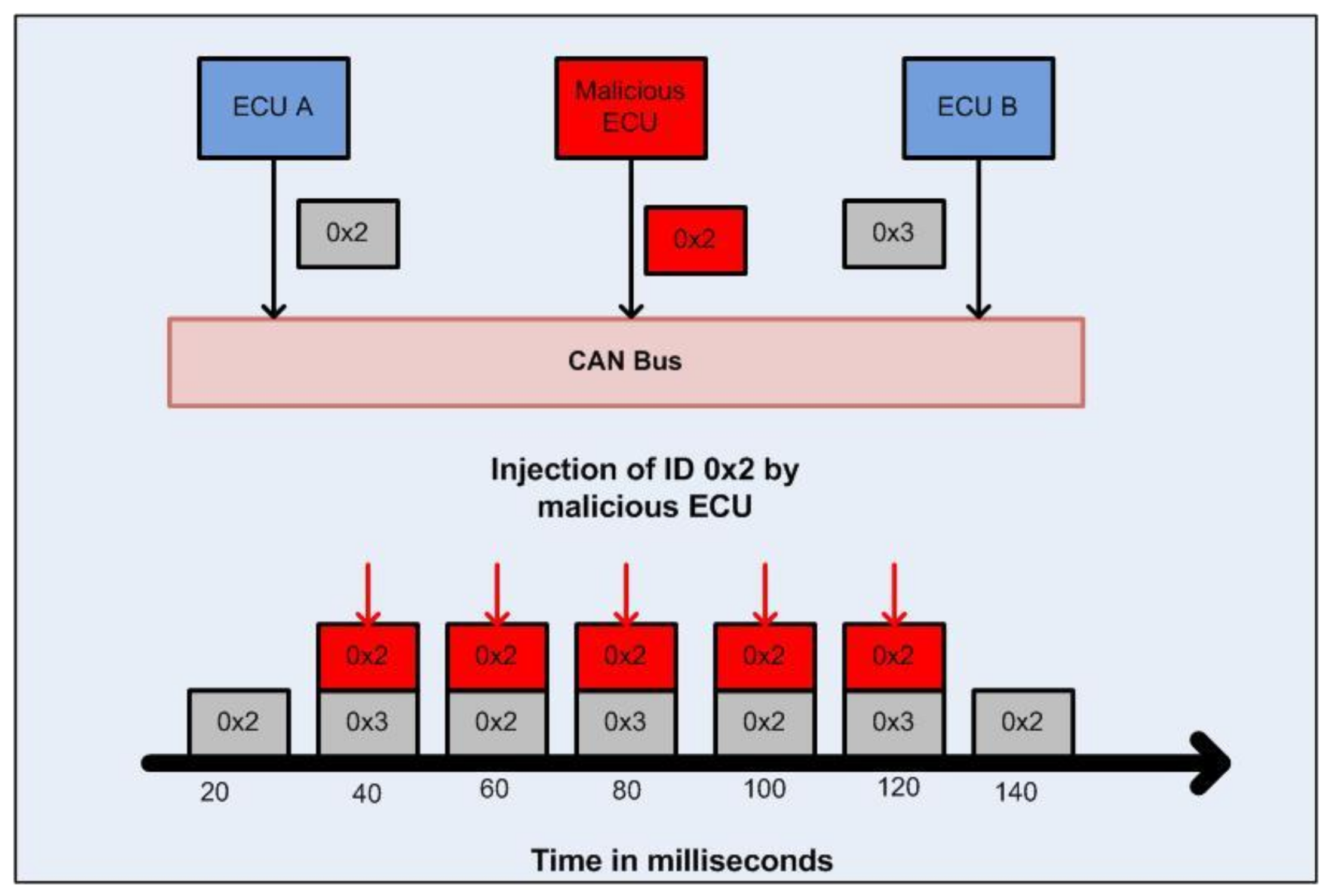
4.1.1. Security Issues
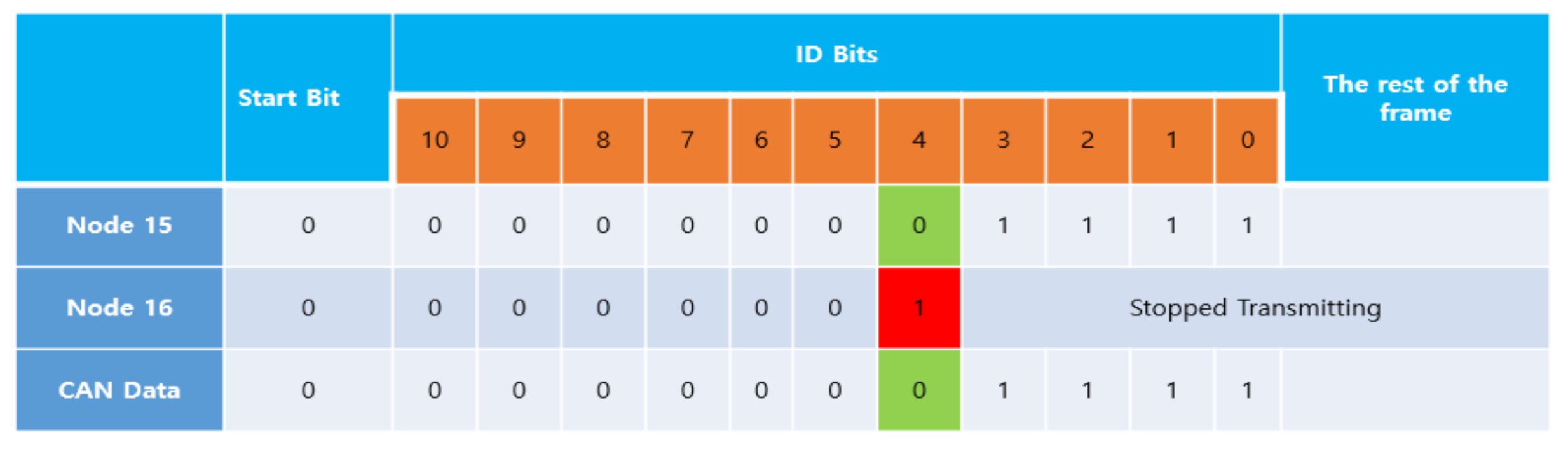
ID-Based Arbitration Mechanisms
Lack of Confidentiality
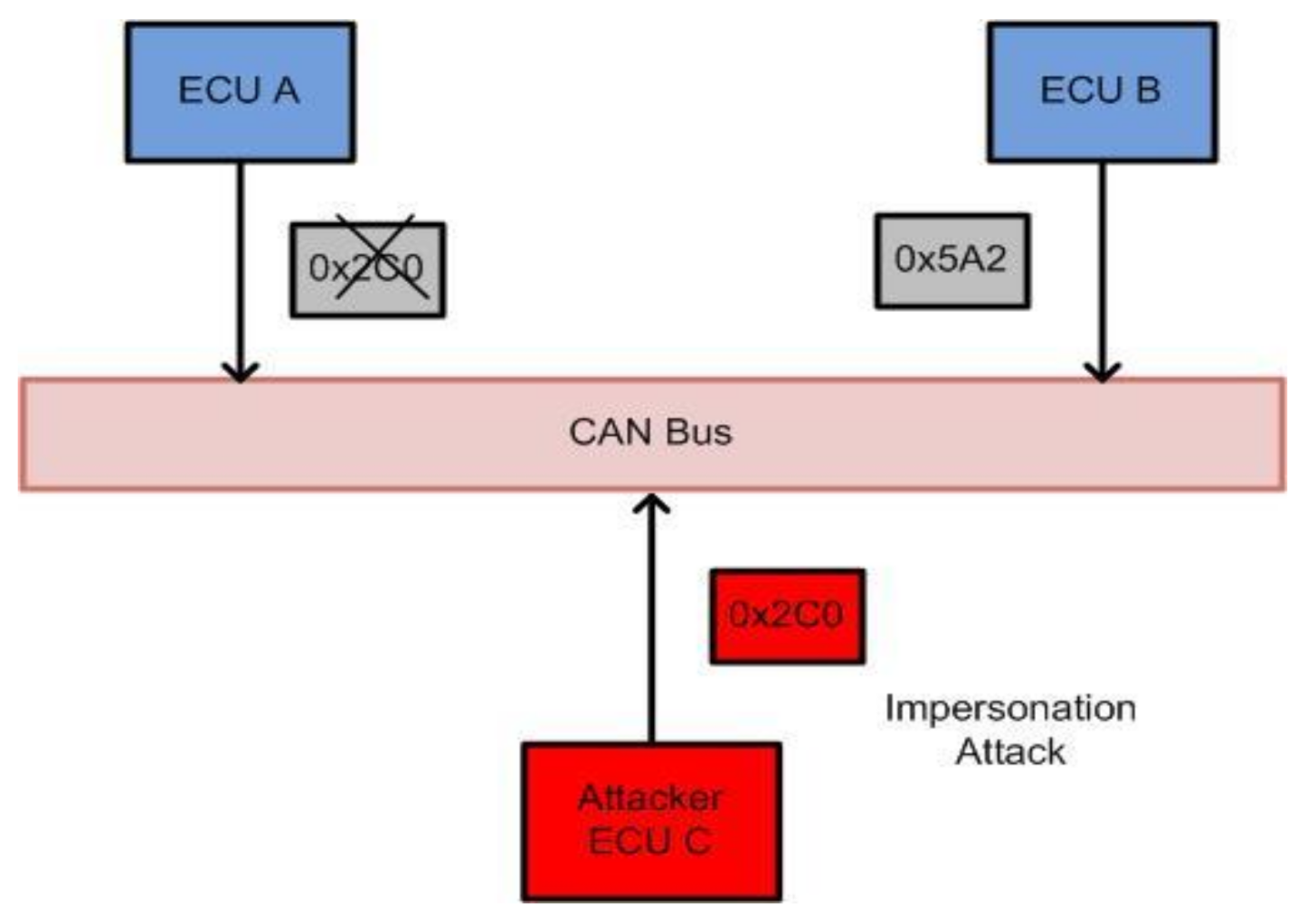
Lack of Authenticated Messages
4.1.2. Countermeasures
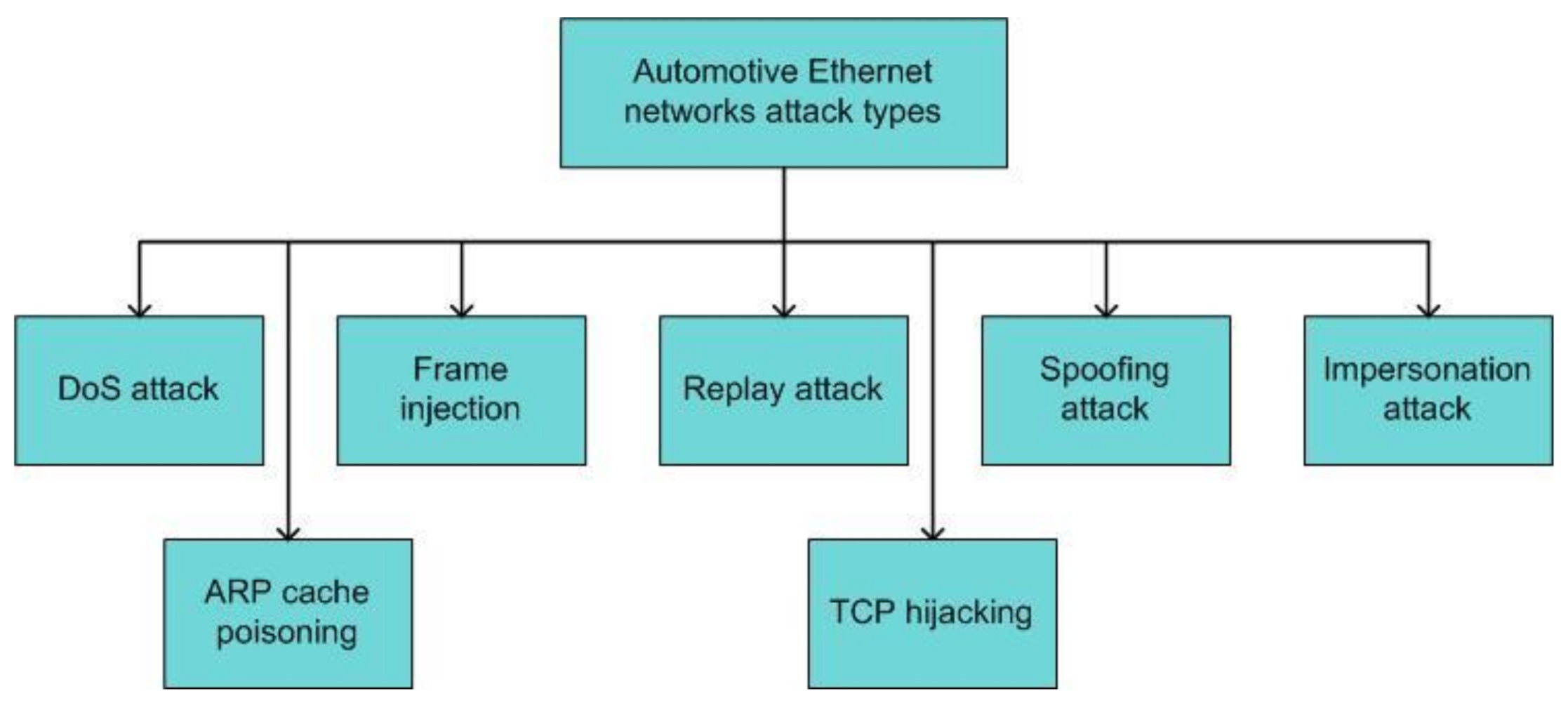
4.2. Security Issues and Countermeasures for Automotive Ethernet
4.2.1. Security Issues
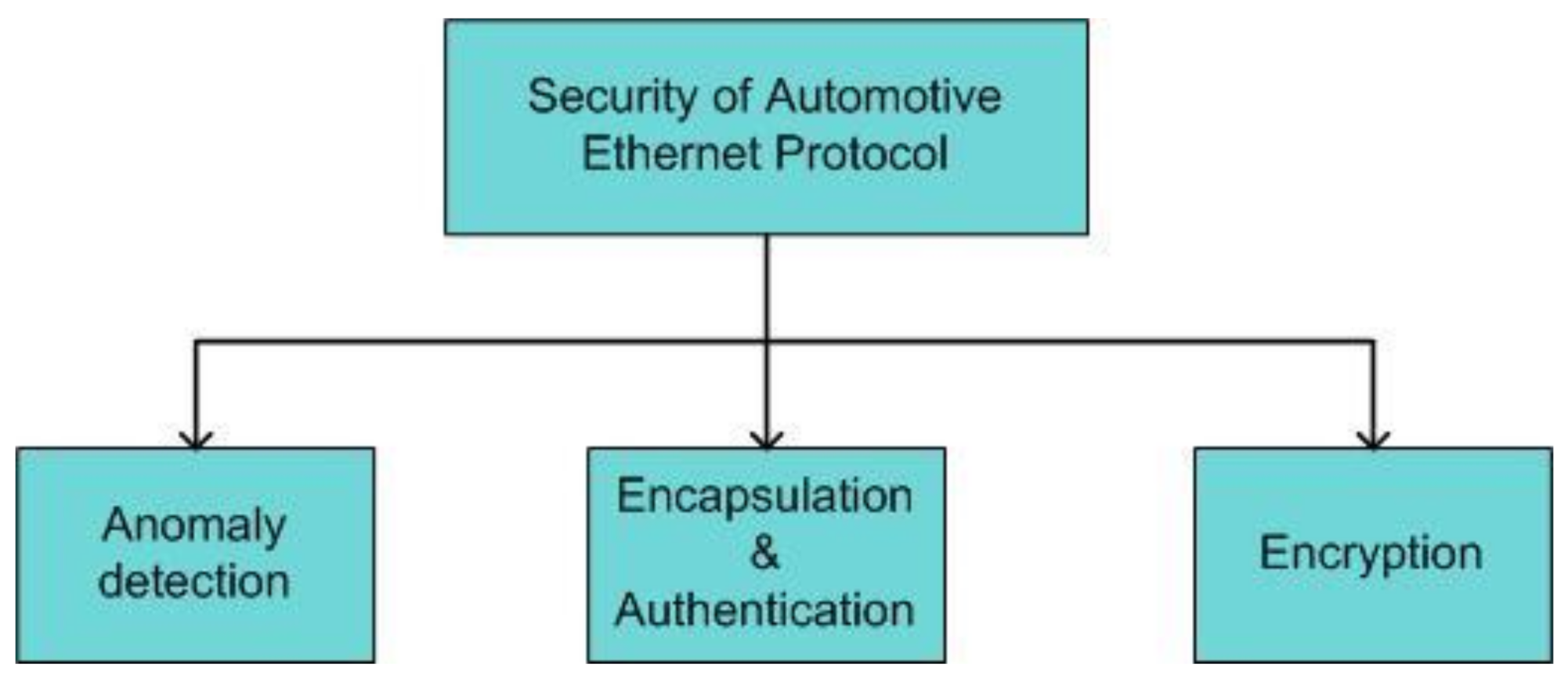
4.2.2. Countermeasures for Securing Automotive Ethernet
- Implementation of firewalls to prevent unauthorized ECUs from sending safety-critical messages
- Intrusion detection systems that can provide prompt feedback to administrators
- Secured on-board communications using authentication and integrity of critical frames based on message authentication code (MAC) with efficient key initialization and management techniques
- Digital signatures and public key infrastructures (PKIs)
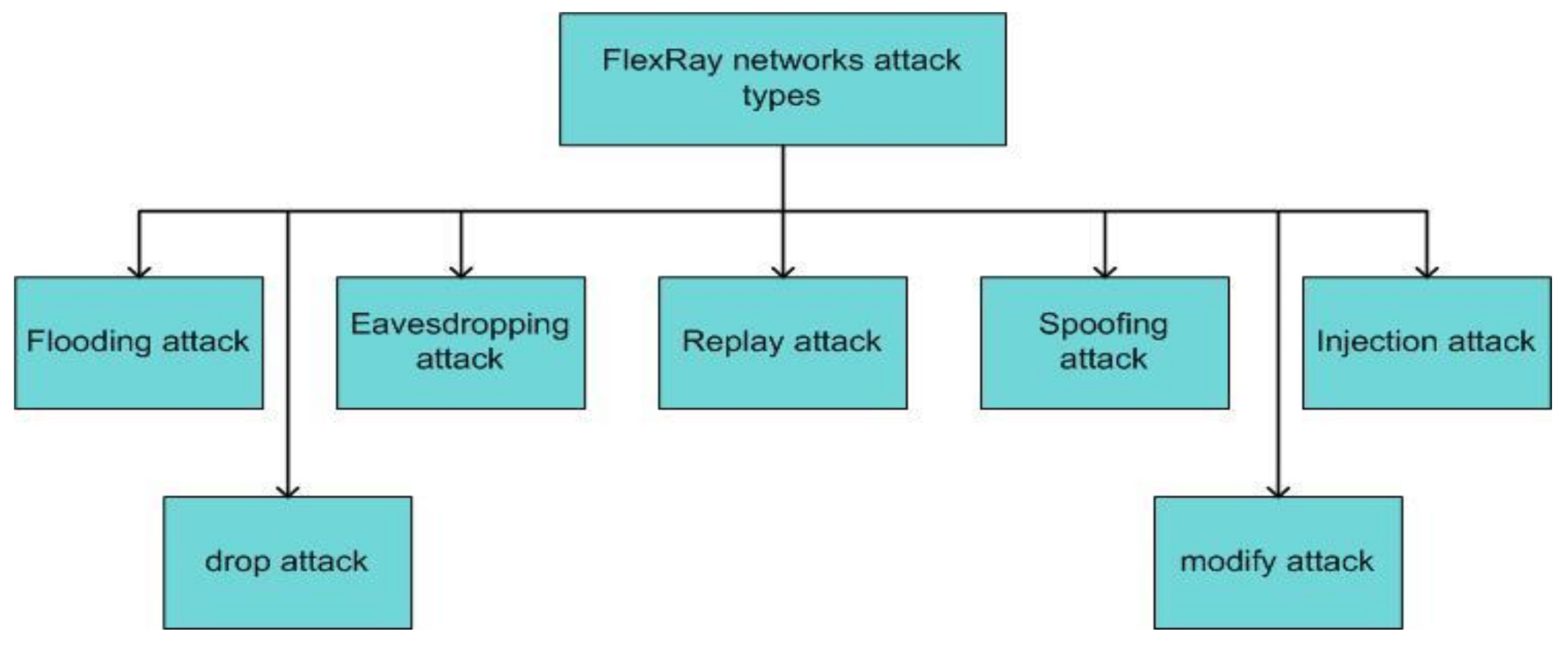
4.3. Security Issues and Countermeasures for FlexRay
4.3.1. Security Issues
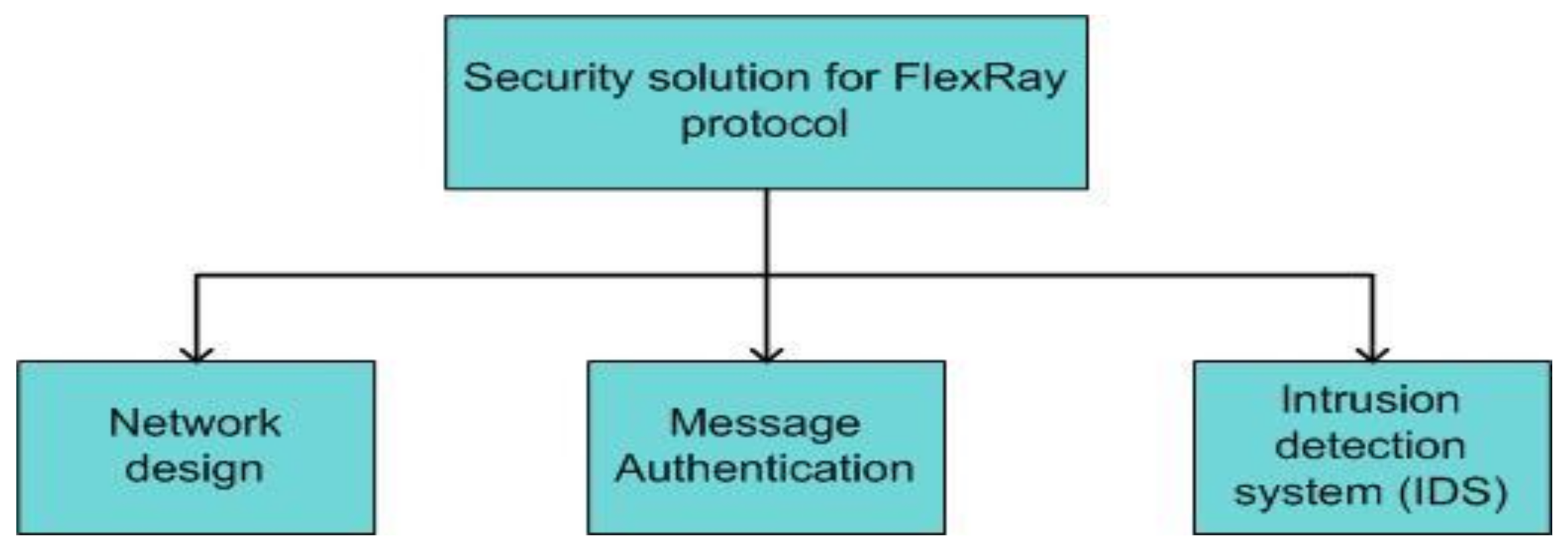
4.3.2. Countermeasures to Secure the FlexRay Protocol
5. Possible Direction for In-Vehicle Network Security
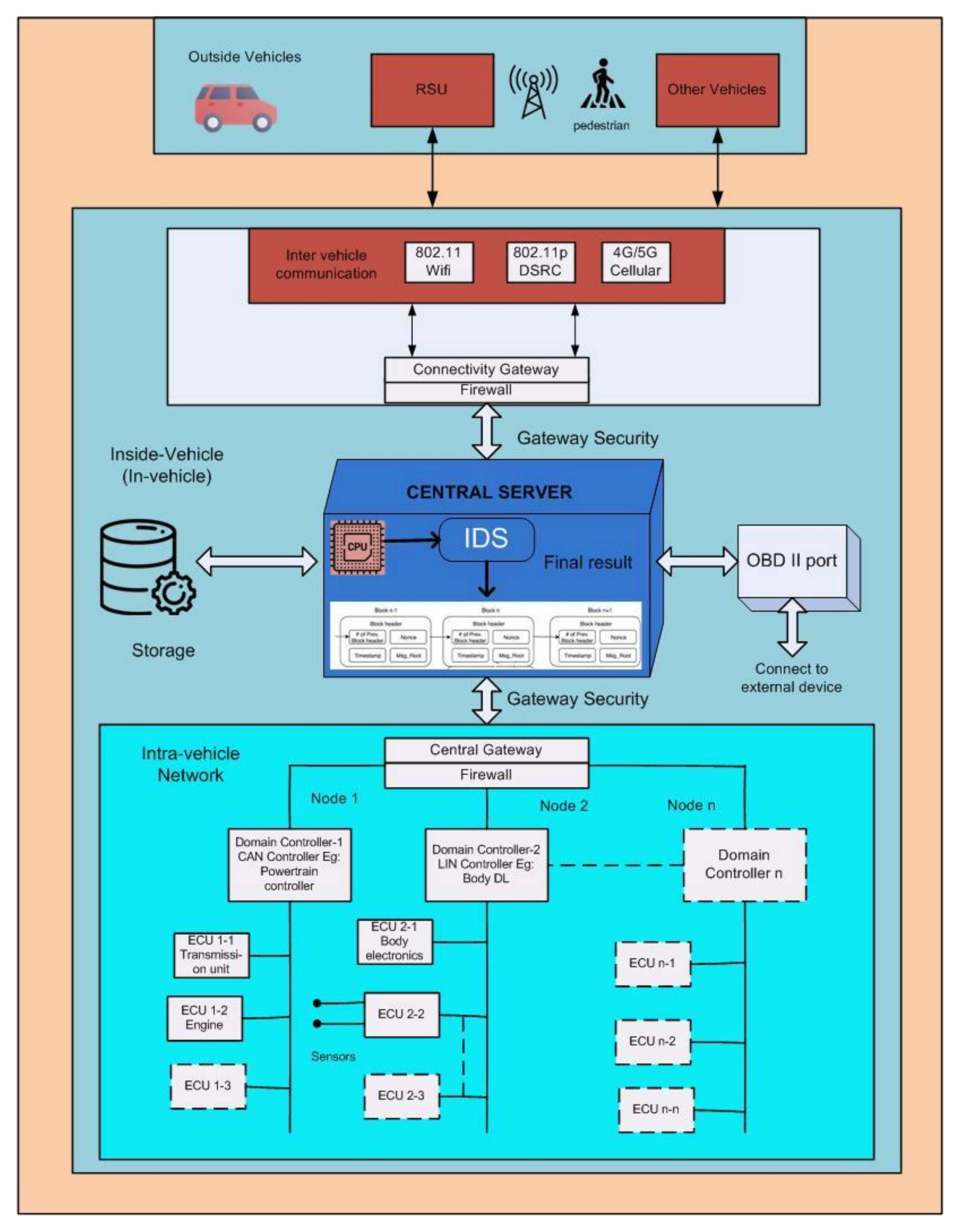
5.1. Application of Blockchain in In-Vehicle Networks
5.1.1. Private Blockchain for In-Vehicle Networks
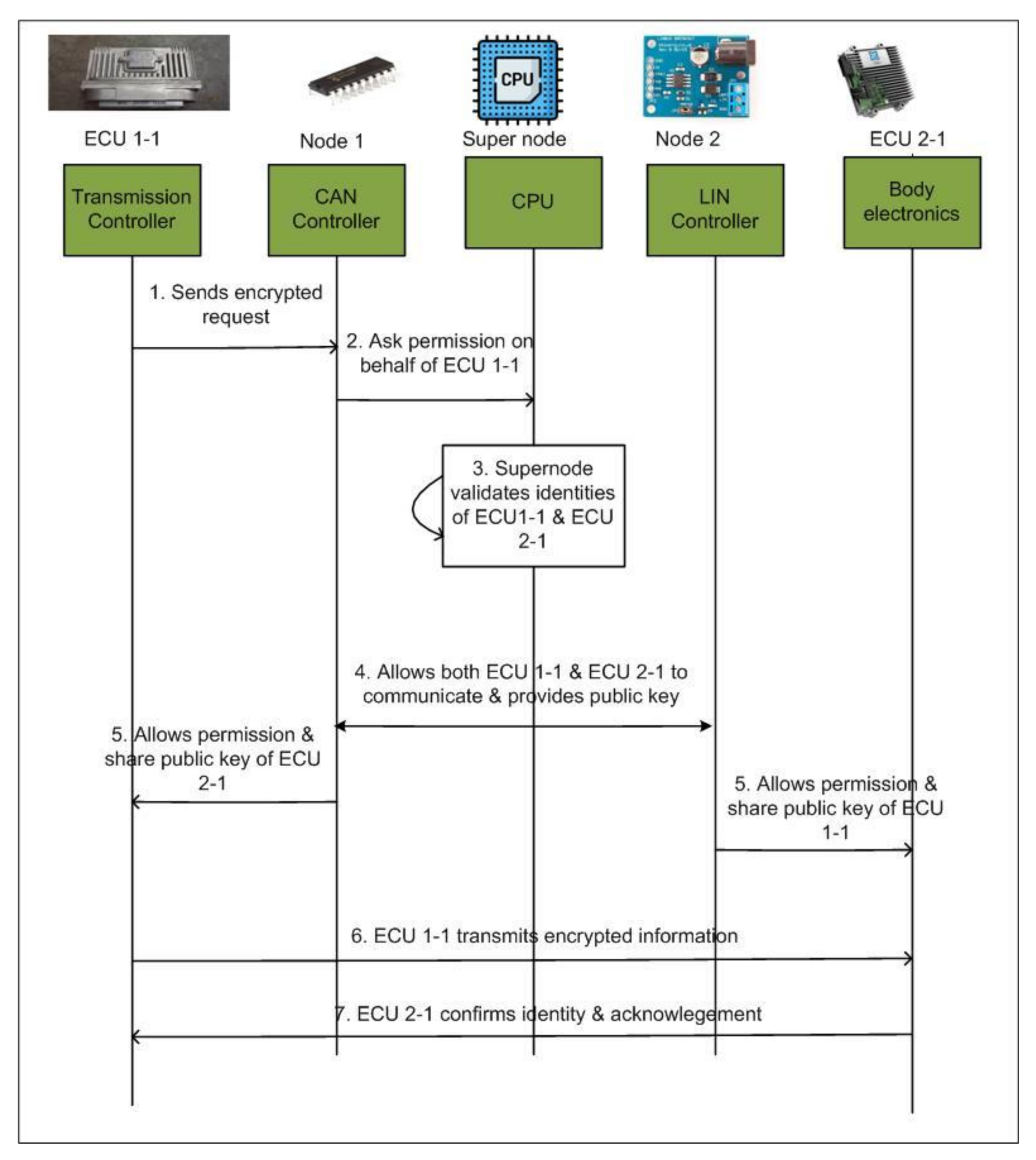
Secure Private In-Vehicle Blockchain Approach
- As a first step, the transmission unit (i.e., ECU1-1) sends a request to the CAN controller (i.e., Node 1) for communicating with body electronics (i.e., ECU2-1). All request and response messages are encrypted and signed before transmission.
- The CAN controller requests authorization from the supernode via the central gateway on behalf of ECU1-1 for communication.
- The supernode verifies the identities of ECU1-1 and ECU2-1 by checking the stored public keys and their respective signatures.
- After identity verification, the supernode allows both ECU1-1 and ECU2-1 to communicate with each other. It also provides both ECUs’ public keys to their respective domain controllers (i.e., Node 1 and Node 2 in Figure 17).
- Each domain controller allows their ECU to communicate and shares their respective public keys with the corresponding ECU for further communication.
- The transmission unit (ECU1-1) encrypts the message with the public key of body electronics (ECU2-1) and signs with its own private key. It then transmits the encrypted message to ECU2-1.
- ECU2-1 verifies the message received from ECU1-1 by checking its identity, and confirms the received message by sending an encrypted acknowledgement.
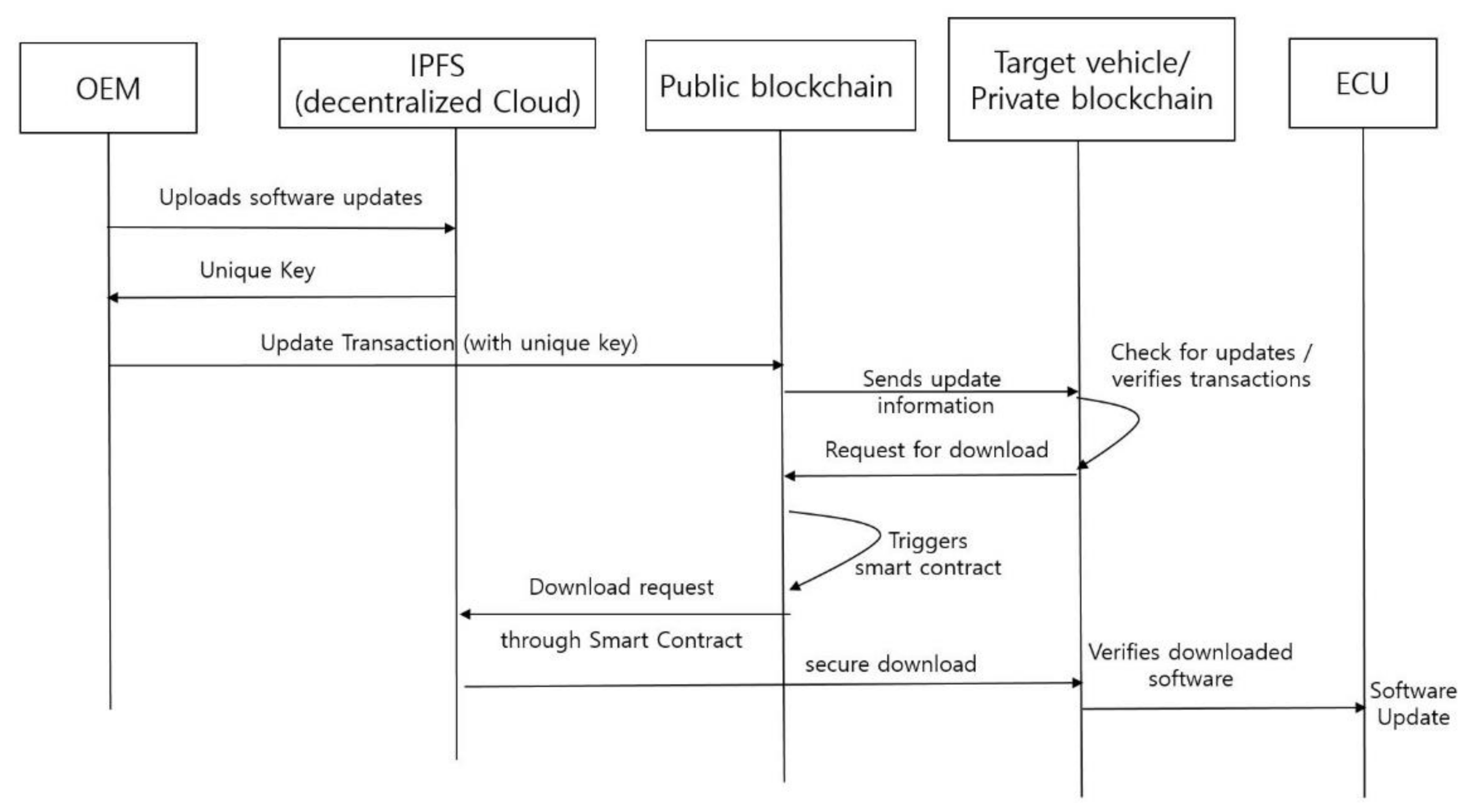
5.1.2. Public Blockchain for Inter-Vehicle Networks
6. Open Challenges and Future Works
- Supervised learning and labeled datasets: With the advancements in technology, new attacks are generated, often in a real-time scenario. Deploying a supervised learning model will only be able to detect pre-defined attacks, and the labeling of a dataset is a difficult task because in-vehicle data frames are generated in intervals of milliseconds.
- Single-layer security: Most of the existing work focuses on either physical layer or application layer security, and the efficiency of these processes is not sufficient to provide secure data communications for in-vehicle networks.
- Computational complexity: The limitations on memory storage and the computation power of in-vehicle computing systems are not considered by the existing research. Most of the existing work used deep learning-based approaches, which require a lot of computation time, compared to the time budget available in practical situations.
- Diverse attack types: Most of the prevalent attacks against in-vehicle networks are message injection, which is easy to detect. In the future, hackers might adopt more advanced attacks that cannot be detected easily. For example, attacks might manipulate CAN frame semantics. Thus, an IDS needs to be designed to cover as many attack patterns as possible.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Hartenstein, H.; Laberteaux, K.P. VANET: Vehicular Applications and Inter-Networking Technologies; John Wiley & Sons: Chichester, UK, 2009. [Google Scholar]
- Zeng, W.; Khalid, M.A.S.; Chowdhury, S. In-Vehicle Networks Outlook: Achievements and Challenges. IEEE Commun. Surv. Tutorials 2016, 18, 1552–1571. [Google Scholar] [CrossRef]
- Rathee, G.; Sharma, A.; Iqbal, R.; Aloqaily, M.; Jaglan, N.; Kumar, R. A Blockchain Framework for Securing Connected and Autonomous Vehicles. Sensors 2019, 19, 3165. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y. Regional Blockchain for Vehicular Networks to Prevent 51% Attacks. IEEE Access 2019, 7, 95033–95045. [Google Scholar] [CrossRef]
- Greenberg, A. Hackers Remotely Kill a Jeep on the Highway-with Me in It. Available online: https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/ (accessed on 21 July 2015).
- Kim, S.; Shrestha, R. Security and Privacy in Intelligent Autonomous Vehicles. In Automotive Cyber Security; J.B. Metzler: Stuttgart, Germany, 2020; pp. 35–66. [Google Scholar]
- Lokman, S.-F.; Othman, A.T.; Abu-Bakar, M.-H. Intrusion detection system for automotive Controller Area Network (CAN) bus system: A review. EURASIP J. Wirel. Commun. Netw. 2019, 2019. [Google Scholar] [CrossRef]
- Lin, I.-C.; Liao, T.-C. A survey of blockchain security issues and challenges. Int. J. Netw. Sec. 2017, 19, 653–659. [Google Scholar]
- Shrestha, R.; Nam, S.Y.; Bajracharya, R.; Kim, S. Evolution of V2X Communication and Integration of Blockchain for Security Enhancements. Electronics 2020, 9, 1338. [Google Scholar] [CrossRef]
- Jeon, B.; Ju, H.; Jung, B.; Kim, K.; Lee, D. A Study on Traffic Characteristics for Anomaly Detection of Ethernet-based IVN. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 16–18 October 2019; pp. 951–953. [Google Scholar]
- Kimm, H.; Ham, H.-S. Integrated Fault Tolerant System for Automotive Bus Networks. In Proceedings of the 2010 Second International Conference on Computer Engineering and Applications; Institute of Electrical and Electronics Engineers (IEEE), Bali, Indonesia, 19–21 March 2010; Volume 1, pp. 486–490. [Google Scholar]
- Nilsson, D.; Larson, U.; Phung, P. Vehicle ECU classification based on safety-security characteristics. In Proceedings of the IET Road Transport Information and Control Conference and the ITS United Kingdom Members’ Conference (RTIC 2008), Manchester, UK, 20–22 May 2008; p. 102. [Google Scholar]
- Brunner, S.; Roder, J.; Kucera, M.; Waas, T. Automotive E/E-architecture enhancements by usage of ethernet TSN. In Proceedings of the 2017 13th Workshop on Intelligent Solutions in Embedded Systems (WISES), Hamburg, Germany, 12–13 June 2017; pp. 9–13. [Google Scholar]
- Navet, N.; Simonot-Lion, F.; Delong, C. In-Vehicle Communication Networks: A Historical Perspective and Review; Apple Academic Press: Palm Bay, FL, USA, 2017; pp. 50–51. [Google Scholar]
- Lee, H.; Jeong, S.H.; Kim, H.K. OTIDS: A Novel Intrusion Detection System for In-vehicle Network by Using Remote Frame. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 57–5709. [Google Scholar]
- Bosch. Can Specifications. 1991. Available online: https://www.kvaser.com/software/7330130980914/V1/can2spec.pdf (accessed on 5 January 2021).
- Aliwa, E.; Rana, O.; Perera, C.; Burnap, P. Cyberattacks and Countermeasures for In-Vehicle Networks. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Kim, S.; Shrestha, R. Intelligent Autonomous Vehicle. In Automotive Cyber Security; J.B. Metzler: Stuttgart, Germany, 2020; pp. 15–33. [Google Scholar]
- Kim, S.; Shrestha, R. In-Vehicle Communication and Cyber Security. In Automotive Cyber Security; J.B. Metzler: Stuttgart, Germany, 2020; pp. 67–96. [Google Scholar]
- Talic, A. Security analysis of ethernet in cars. Master’s Thesis, Department of Communication Systems, KTH Royal Institute of Technology, Stockholm, Sweden, 2017. Available online: https://people.kth.se/~maguire/DEGREE-PROJECT-REPORTS/171006-Ammar_Talic_with_cover.pdf (accessed on 15 January 2021).
- Corbett, C.; Schoch, E.; Kargl, F.; Felix, P. Automotive ethernet: Security opportunity or challenge? Sicherheit 2016 - Sicherheit, Schutz und Zuverlässigkeit, Bonn, Gesellschaft für Informatik e.V. 2016, pp. 45–54. Available online: https://dl.gi.de/bitstream/handle/20.500.12116/880/45.pdf?sequence=1 (accessed on 27 January 2021).
- Hank, P.; Muller, S.; Vermesan, O.; Keybus, J.V.D. Automotive Ethernet: In-vehicle Networking and Smart Mobility. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 18–22 March 2013; Volume 2013, pp. 1735–1739. [Google Scholar]
- Glass, M.; Herrscher, D.; Meier, H.; Piastowski, M.; Schoo, P. “Seis”—Security in Embedded IP-Based Systems; ATZ Elektron Worldw: Berlin/Heidelberg, Germany, 2010; Volume 5, pp. 36–40. [Google Scholar]
- Lee, H.-Y.; Lee, D.-H. Security of Ethernet in Automotive Electric/Electronic Architectures. J. Inst. Internet Broadcast. Commun. 2016, 16, 39–48. [Google Scholar] [CrossRef]
- Le, V.H.; Hartog, J.D.; Zannone, N. Security and privacy for innovative automotive applications: A survey. Comput. Commun. 2018, 132, 17–41. [Google Scholar] [CrossRef]
- Nilsson, D.K.; Larson, U.E.; Picasso, F.; Jonsson, E. A First Simulation of Attacks in the Automotive Network Communications Protocol FlexRay. In Proceedings of the Advances in Computer Science and Education; J.B. Metzler: Stuttgart, Germany, 2008; Volume 53, pp. 84–91. [Google Scholar]
- Bozdal, M.; Samie, M.; Aslam, S.; Jennions, I. Evaluation of CAN Bus Security Challenges. Sensors 2020, 20, 2364. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A Survey of Intrusion Detection for In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Tomlinson, A.; Bryans, J.; Shaikh, S.A. Towards viable intrusion detection methods for the automotive controller area network. In Proceedings of the 2nd ACM Computer Science in Cars Symposium, Munich, Germany, 13–14 September 2018. [Google Scholar]
- Avatefipour, O.; Malik, H. State-of-the-Art Survey on in-Vehicle Network Communication (CAN-Bus) Security and Vulnerabilities. arXiv 2018, arXiv:1802.01725. [Google Scholar]
- Carsten, P.; Andel, T.R.; Yampolskiy, M.; McDonald, J.T. In-Vehicle networks: Attacks, vulnerabilities, and proposed solutions. In Proceedings of the 10th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 7–9 April 2015. [Google Scholar]
- Liu, J.; Zhang, S.; Sun, W.; Shi, Y. In-Vehicle Network Attacks and Countermeasures: Challenges and Future Directions. IEEE Netw. 2017, 31, 50–58. [Google Scholar] [CrossRef]
- Hoppe, T.; Kiltz, S.; Dittmann, J. Security threats to automotive CAN networks—Practical examples and selected short-term countermeasures. Reliab. Eng. Syst. Saf. 2011, 96, 11–25. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Lee, D.H. A Practical Wireless Attack on the Connected Car and Security Protocol for In-Vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2014, 16, 1–14. [Google Scholar] [CrossRef]
- Miller, C.; Valasek, C. Remote Exploitation of an Unaltered Passenger Vehicle; BlackHat: Las Vegas, NV, USA, 2015. [Google Scholar]
- Nie, S.; Liu, L.; Du, Y.; Zhang, W. Over-the-Air: How We Remotely Compromised the Gateway, BCM, and Autopilot ECUs of Tesla Cars; BlackHat: Las Vegas, NV, USA, 2018. [Google Scholar]
- Avatefipour, O.; Al-Sumaiti, A.S.; El-Sherbeeny, A.M.; Awwad, E.M.; Elmeligy, M.A.; Mohamed, M.A.; Malik, H. An Intelligent Secured Framework for Cyberattack Detection in Electric Vehicles’ CAN Bus Using Machine Learning. IEEE Access 2019, 7, 127580–127592. [Google Scholar] [CrossRef]
- CAN Bus. Available online: https://en.wikipedia.org/wiki/CAN_bus (accessed on 8 February 2021).
- Song, H.M.; Woo, J.; Kim, H.K. In-vehicle network intrusion detection using deep convolutional neural network. Veh. Commun. 2020, 21, 100198. [Google Scholar] [CrossRef]
- Biron, Z.A.; Dey, S.; Pisu, P. Real-Time Detection and Estimation of Denial of Service Attack in Connected Vehicle Systems. IEEE Trans. Intell. Transp. Syst. 2018, 19, 3893–3902. [Google Scholar] [CrossRef]
- Xiao, J.; Wu, H.; Li, X. Internet of Things Meets Vehicles: Sheltering In-Vehicle Network through Lightweight Machine Learning. Symmetry 2019, 11, 1388. [Google Scholar] [CrossRef]
- Hoppe, T.; Kiltz, S.; Dittmann, J. Applying intrusion detection to automotive it-early insights and remaining challenges. J. Inf. Assur. Sec. 2009, 4, 226–235. [Google Scholar]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Chekoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Berkeley/Oakland, CA, USA, 16–19 May 2010. [Google Scholar]
- Checkoway, S.; Damon, M.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive experimental analyses of automotive attack surfaces. In Proceedings of the USENIX Security Symposium, San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Miller, C.; Valasek, C. A Survey of Remote Automotive Attack Surfaces; BlackHat: Las Vegas, NV, USA, 2014. [Google Scholar]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016. [Google Scholar]
- Gmiden, M.; Gmiden, M.H.; Trabelsi, H. An intrusion detection method for securing in-vehicle CAN bus. In Proceedings of the 2016 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA), Sousse, Tunisia, 19–21 December 2016. [Google Scholar]
- Young, C.; Olufowobi, H.; Bloom, G.; Zambreno, J. Automotive Intrusion Detection Based on Constant CAN Message Frequencies Across Vehicle Driving Modes. In Proceedings of the ACM Workshop on Automotive Cybersecurity, Richardson, TX, USA, 27 March 2019; pp. 9–14. [Google Scholar]
- Taylor, A.; Japkowicz, N.; Leblanc, S. Frequency-based anomaly detection for the automotive CAN bus. In Proceedings of the 2015 World Congress on Industrial Control Systems Security (WCICSS), London, UK, 14–16 December 2015; pp. 45–49. [Google Scholar]
- Halder, S.; Conti, M.; Das, S.K. COIDS: A clock offset based intrusion detection system for Controller Area Networks. In Proceedings of the 21st International Conference on Distributed Computing and Networking, Kolkata, India, 4–7 January 2020. [Google Scholar]
- Alshammari, A.; Zohdy, M.A.; Debnath, D.; Corser, G. Classification Approach for Intrusion Detection in Vehicle Systems. Wirel. Eng. Technol. 2018, 9, 79–94. [Google Scholar] [CrossRef]
- Nazakat, I.; Khurshid, K. Intrusion Detection System for In-Vehicular Communication. In Proceedings of the 2019 15th International Conference on Emerging Technologies (ICET), Peshawar, Pakistan, 2–3 December 2019; pp. 1–6. [Google Scholar]
- Kang, M.-J.; Kang, J.-W. Intrusion Detection System Using Deep Neural Network for In-Vehicle Network Security. PLoS ONE 2016, 11, e0155781. [Google Scholar] [CrossRef]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based Intrusion Detection System for In-Vehicle Network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; pp. 1–6. [Google Scholar]
- Hossain, D.; Inoue, H.; Ochiai, H.; Fall, D.; Kadobayashi, Y. LSTM-Based Intrusion Detection System for In-Vehicle Can Bus Communications. IEEE Access 2020, 8, 185489–185502. [Google Scholar] [CrossRef]
- Hossain, D.; Inoue, H.; Ochiai, H.; Fall, D.; Kadobayashi, Y. Long Short-Term Memory-Based Intrusion Detection System for In-Vehicle Controller Area Network Bus. In Proceedings of the 2020 IEEE 44th Annual Computers Software and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020; pp. 10–17. [Google Scholar]
- Lin, Y.; Chen, C.; Xiao, F.; Avatefipour, O.; AlSubhi, K.; Yunianta, A. An Evolutionary Deep Learning Anomaly Detection Framework for In-Vehicle Networks—CAN Bus. IEEE Trans. Ind. Appl. 2020, 1. [Google Scholar] [CrossRef]
- Zhu, K.; Chen, Z.; Peng, Y.; Zhang, L. Mobile Edge Assisted Literal Multi-Dimensional Anomaly Detection of In-Vehicle Network Using LSTM. IEEE Trans. Veh. Technol. 2019, 68, 4275–4284. [Google Scholar] [CrossRef]
- Fenzl, F.; Rieke, R.; Chevalier, Y.; Dominik, A.; Kotenko, I. Continuous fields: Enhanced in-vehicle anomaly detection using machine learning models. Simul. Model. Pr. Theory 2020, 105, 102143. [Google Scholar] [CrossRef]
- Tariq, S.; Lee, S.; Kim, H.K.; Woo, S.S. CAN-ADF: The controller area network attack detection framework. Comput. Secur. 2020, 94, 101857. [Google Scholar] [CrossRef]
- Al-Saud, M.; Eltamaly, A.M.; Mohamed, M.A.; Fard, A.K. An Intelligent Data-Driven Model to Secure Intravehicle Communications Based on Machine Learning. IEEE Trans. Ind. Electron. 2019, 67, 5112–5119. [Google Scholar] [CrossRef]
- Hanselmann, M.; Strauss, T.; Dormann, K.; Ulmer, H. CANet: An Unsupervised Intrusion Detection System for High Dimensional CAN Bus Data. IEEE Access 2020, 8, 58194–58205. [Google Scholar] [CrossRef]
- Lokman, S.F.; Othman, A.T.; Musa, S.; Abu Bakar, M.H. Deep Contractive Autoencoder-Based Anomaly Detection for In-Vehicle Controller Area Network (CAN). Prop. Charact. Mod. Mater. 2019, 119, 195–205. [Google Scholar] [CrossRef]
- Baldini, G. On the Application of Entropy Measures with Sliding Window for Intrusion Detection in Automotive In-Vehicle Networks. Entropy 2020, 22, 1044. [Google Scholar] [CrossRef] [PubMed]
- Wu, W.; Huang, Y.; Kurachi, R.; Zeng, G.; Xie, G.; Li, R.; Li, K. Sliding Window Optimized Information Entropy Analysis Method for Intrusion Detection on In-Vehicle Networks. IEEE Access 2018, 6, 45233–45245. [Google Scholar] [CrossRef]
- Barletta, V.S.; Caivano, D.; Nannavecchia, A.; Scalera, M. Intrusion Detection for In-Vehicle Communication Networks: An Unsupervised Kohonen SOM Approach. Futur. Internet 2020, 12, 119. [Google Scholar] [CrossRef]
- Olufowobi, H.; Young, C.; Zambreno, J.; Bloom, G. SAIDuCANT: Specification-Based Automotive Intrusion Detection Using Controller Area Network (CAN) Timing. IEEE Trans. Veh. Technol. 2019, 69, 1484–1494. [Google Scholar] [CrossRef]
- Olufowobi, H.; Ezeobi, U.; Muhati, E.; Robinson, G.; Young, C.; Zambreno, J.; Bloom, G. Anomaly Detection Approach Using Adaptive Cumulative Sum Algorithm for Controller Area Network. In Proceedings of the ACM Workshop on Automotive Cybersecurity, Richardson, TX, USA, 27 March 2019; pp. 25–30. [Google Scholar]
- Islam, R.; Refat, R.U.D.; Yerram, S.M.; Malik, H. Graph-Based Intrusion Detection System for Controller Area Networks. IEEE Trans. Intell. Transp. Syst. 2020, 1–10. [Google Scholar] [CrossRef]
- Han, M.L.; Kwak, B.I.; Kim, H.K. Anomaly intrusion detection method for vehicular networks based on survival analysis. Veh. Commun. 2018, 14, 52–63. [Google Scholar] [CrossRef]
- Zhang, L.; Shi, L.; Kaja, N.; Ma, D. A two-stage deep learning approach for can intrusion detection. In Proceedings of the Ground Vehicle Systems Engineering and Technology Symposium, Novi, Michigan, 7–9 August 2018. [Google Scholar]
- Katragadda, S.; Darby, P.J.; Roche, A.; Gottumukkala, R. Detecting Low-Rate Replay-Based Injection Attacks on In-Vehicle Networks. IEEE Access 2020, 8, 54979–54993. [Google Scholar] [CrossRef]
- Zhang, J.; Li, F.; Zhang, H.; Li, R.; Li, Y.; Jiayan, Z.; Fei, L.; Haoxi, Z.; Ruxiang, L.; Yalin, L. Intrusion detection system using deep learning for in-vehicle security. Ad Hoc Netw. 2019, 95, 101974. [Google Scholar] [CrossRef]
- Jichici, C.; Groza, B.; Murvay, P.-S. Integrating Adversary Models and Intrusion Detection Systems for In-vehicle Networks in CANoe. In Proceedings of the Lecture Notes in Computer Science; J.B. Metzler: Stuttgart, Germany, 2020; pp. 241–256. [Google Scholar]
- Jichici, C.; Groza, B.; Murvay, P.-S. Examining the Use of Neural Networks for Intrusion Detection in Controller Area Networks. In Proceedings of the Lecture Notes in Computer Science; J.B. Metzler: Stuttgart, Germany, 2019; pp. 109–125. [Google Scholar]
- Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal. Smart Cities 2020, 3, 2. [Google Scholar] [CrossRef]
- Gupta, A. Security Risk Analysis of Automotive Ethernet Networks. 2017. Available online: https://essay.utwente.nl/73894/1/Gupta_MS_EEMCS.pdf (accessed on 10 February 2021).
- Lee, T.-Y.; Lin, I.-A.; Liao, R.-H. Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks. Sensors 2020, 20, 641. [Google Scholar] [CrossRef]
- Grimm, D.; Weber, M.; Sax, E. An Extended Hybrid Anomaly Detection System for Automotive Electronic Control Units Communicating via Ethernet—Efficient and Effective Analysis using a Specification- and Machine Learning-based Approach. In Proceedings of the 4th International Conference on Vehicle Technology and Intelligent Transport Systems, Funchal, Madeira, Portugal, 16–18 March 2018; pp. 462–473. [Google Scholar]
- Yang, H.; Liu, M.-Z.; Xu, Y.-H.; Wu, Y.-J.; Xu, Y.-N. Research of Automotive Ethernet Security Based on Encryption and Authentication Method. Int. J. Comput. Theory Eng. 2019, 11, 1–5. [Google Scholar] [CrossRef]
- Kishikawa, T.; Hirano, R.; Ujiie, Y.; Haga, T.; Matsushima, H.; Fujimura, K.; Anzai, J. Vulnerability of FlexRay and Countermeasures. SAE Int. J. Transp. Cybersecur. Priv. 2019, 2, 21–33. [Google Scholar] [CrossRef]
- Kishikawa, T.; Hirano, R.; Ujiie, Y.; Haga, T.; Matsushima, H.; Fujimura, K.; Anzai, J. Intrusion detection and prevention system for flexray against spoofed frame injection. In Proceedings of the 17th Escar Europe: Embedded Security in Cars Conference (Konferenzveröffentlichung), Detroit, MI, USA, 19–20 November 2019; pp. 59–73. [Google Scholar] [CrossRef]
- Mousa, A.R.; Noureldeen, P.; Azer, M.; Allam, M. Lightweight Authentication Protocol Deployment over FlexRay. In Proceedings of the 10th International Conference on Predictive Models in Software Engineering, Turin, Italy, 17 September 2014; pp. 233–239. [Google Scholar]
- Han, G.; Zeng, H.; Li, Y.; Dou, W. SAFE: Security-aware flexray scheduling engine. In Proceedings of the 2014 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 24–28 March 2014. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain challenges and opportunitiees: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Qadri, Y.A.; Nauman, A.; Bin Zikria, Y.; Vasilakos, A.V.; Kim, S.W. The Future of Healthcare Internet of Things: A Survey of Emerging Technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1121–1167. [Google Scholar] [CrossRef]
- Jiang, T.; Fang, H.; Wang, H. Blockchain-Based Internet of Vehicles: Distributed Network Architecture and Performance Analysis. IEEE Internet Things J. 2019, 6, 4640–4649. [Google Scholar] [CrossRef]
- Kim, S.; Shrestha, R. Internet of Vehicles, Vehicular Social Networks, and Cybersecurity. In Automotive Cyber Security; J.B. Metzler: Stuttgart, Germany, 2020; pp. 149–181. [Google Scholar]
- Cebe, M.; Erdin, E.; Akkaya, K.; Aksu, H.; Uluagac, S. Block4Forensic: An Integrated Lightweight Blockchain Framework for Forensics Applications of Connected Vehicles. IEEE Commun. Mag. 2018, 56, 50–57. [Google Scholar] [CrossRef]
- Liu, X.; Zhao, G.; Wang, X.; Lin, Y.; Zhou, Z.; Tang, H.; Chen, B. MDP-Based Quantitative Analysis Framework for Proof of Authority. In Proceedings of the 2019 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Guilin, China, 17–19 October 2019. [Google Scholar]
- Salem, M.; Mohammed, M.; Ali, R. Security Approach for In-Vehicle Networking Using Blockchain Technology BT—Advances in Internet, Data and Web Technologies. In Proceedings of the International Conference on Emerging Internetworking Data & Web Technologies, United Arab Emirates, 26–28 February 2019. [Google Scholar]
- Shrestha, R.; Bajracharya, R.; Shrestha, A.P.; Nam, S.Y. A new type of blockchain for secure message exchange in VANET. Digit. Commun. Netw. 2020, 6, 177–186. [Google Scholar] [CrossRef]
- Shrestha, R.; Bajracharya, R.; Nam, S.Y. Blockchain-based Message Dissemination in VANET. In Proceedings of the 2018 IEEE 3rd International Conference on Computing, Communication and Security (ICCCS), Kathmandu, Nepal, 25–27 October 2018; pp. 161–166. [Google Scholar]
- Xiao, Y.; Zhang, N.; Lou, W.; Hou, Y.T. A Survey of Distributed Consensus Protocols for Blockchain Networks. IEEE Commun. Surv. Tutorials 2020, 22, 1432–1465. [Google Scholar] [CrossRef]
- Steger, M.; Dorri, A.; Kanhere, S.S.; Römer, K.; Jurdak, R.; Karner, M. Secure Wireless Automotive Software Updates Using Blockchains: A Proof of Concept. In Road Vehicle Automation 3; J.B. Metzler: Stuttgart, Germany, 2017; pp. 137–149. [Google Scholar]
- Hasan, S.S.; Sultan, N.H.; Barbhuiya, F.A. Cloud Data Provenance using IPFS and Blockchain Technology. In Proceedings of the SCC ’19: Proceedings of the Seventh International Workshop on Security in Cloud Computing, Auckland, New Zealand, 7–12 July 2019. [Google Scholar]
- Rouf, I.; Miller, R.; Mustafa, H.; Taylor, T.; Oh, S.; Xu, W.; Gruteser, M.; Trappe, W.; Seskar, I. Security and privacy vulnerabilities of in-car wireless networks: A tire pressure monitoring system case study. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 11–13 August 2010. [Google Scholar]







| Abbreviation | Full Form |
|---|---|
| ABS | Anti-lock Braking System |
| BCMs | Body Control Modules |
| CAN | Controller Area Network |
| CNN | Convolutional Neural Network |
| CPU | Central Processing Unit |
| CRC | Cyclic Redundancy Check |
| CAEVs | Connected and Autonomous Electric Vehicles |
| DoS | Denial of Service |
| DPoS | Delegated Proof of Stake |
| DNN | Deep Neural Network |
| DCU | Domain Controller Unit |
| ECU | Electronic Control Unit |
| E/E | Electrical and Electronics |
| GAN | Generative Adversarial Network |
| IVN | In-Vehicle Network |
| IoV | Internet of Vehicles |
| ID | Identifier |
| IPFS | Interplanetary File System |
| LSTM | Long Short-Term Memory |
| LIN | Local Interconnect Network |
| OBD | On-Board Diagnostics |
| PuBC | Public Blockchain |
| PvBC | Private Blockchain |
| PoA | Proof of Authority |
| PCA | Principal Component Analysis |
| ReLU | Rectified Linear Unit |
| RNN | Recurrent Neural Network |
| SVM | Support Vector Machine |
| TCU | Transmission Control Unit |
| V2X | Vehicle to Everything |
| VANETs | Vehicular Ad Hoc Networks |
| Protocol | Bandwidth | Application Domain | Advantages | Disadvantages |
|---|---|---|---|---|
| CAN | 125 Kbps–1 Mbps | Widely used in powertrain and body control domains | Low cost, no need of central coordinator | Less bandwidth |
| LIN | 1 Kbps–20 Kbps | Widely used in simple and less time-critical applications | Low cost, easy to implement | Low speed |
| FlexRay | 10 Mbps | Widely used in advanced chassis control | High speed, better fault tolerance than CAN and Lin | High cost |
| MOST | 24 Mbps | Widely used in infotainment applications | High speed | High cost |
| ETHERNET | 100 Mbps | Widely used in the future in applications requiring high bandwidths | High speed (100 times faster than CAN bus) | High cost per node |
| Reference | In-Vehicle Network Vulnerability Analysis | Detailed Survey of IDSs in IVNs Based on Various Attack Types | Includes a Blockchain-Based IDS Suggestion for In-Vehicle Network | Discusses Open Issues and Future Works |
|---|---|---|---|---|
| Zeng et al. [2] | ✓ | ✕ | ✕ | ✓ |
| Avatefipour and Malik [30] | ✓ | ✕ | ✕ | ✕ |
| Wu et al. [28] | ✓ | ✕ | ✕ | ✓ |
| Bozdal et al. [27] | ✓ | ✕ | ✕ | ✕ |
| Lokman et al. [7] | ✓ | ✕ | ✕ | ✕ |
| Tomlinson et al. [29] | ✕ | ✕ | ✕ | ✓ |
| This article | ✓ | ✓ | ✓ | ✓ |
| References | Detection Algorithm | Detection Speed (milliseconds) | Detection Accuracy (%) | Algorithm Complexity | Learning Time (seconds) | Robustness | Detection Coverage |
|---|---|---|---|---|---|---|---|
| Song et al. [39] | DCNN | N.A. | >80 | High | N.A. | Medium | DoS, fuzzy, spoofing |
| Seo et al. [54] | GAN | <500 | >90 | High | N.A. | High | DoS, fuzzy, spoofing |
| Hossain et al. [55] | LSTM | N.A. | >90 | High | N.A. | Medium | DoS, fuzzy, spoofing |
| Kang et al. [53] | DNN | <10 | >90 | High | <15 | High | N.A. |
| Lin et al. [57] | Deep Learning | N.A. | >80 | High | N.A. | Medium | DoS, fuzzy, impersonation |
| Zhu et al. [58] | LSTM | <10 | >80 | High | N.A. | Medium | Spoofing, replay, flood |
| Xiao et al. [41] | RNN | N.A. | >90 | High | N.A. | High | DoS, fuzzy, impersonation |
| Song et al. [46] | Time interval based IDS | N.A. | >90 | Low | N.A. | High | DoS |
| Katragadda et al. [72] | Frequency Analysis based IDS | <155 | N.A. | Medium | 9.04 | Medium | Replay |
| References | Security Mechanisms | Detection Speed | Detection Accuracy (%) | Algorithm Complexity | Learning Time (seconds) | Robustness | Detection Coverage |
|---|---|---|---|---|---|---|---|
| Jeon et al. [10] | Anomaly detection | N.A. | N.A. | N.A. | N.A. | N.A. | N.A. |
| Grimm et al. [79] | OCSVM | N.A. | >90 | Medium | N.A. | High | Replay attack |
| Grimm et al. [79] | PCA | N.A. | >90 | Low | N.A. | High | Replay attack |
| Yang et al. [80] | Authentication and encryption | N.A. | N.A. | Low | N.A. | N.A. | N.A. |
| References | Security Mechanisms | Detection Speed | Detection Accuracy (%) | Algorithm Complexity | Learning Time (seconds) | Robustness | Detection Coverage |
|---|---|---|---|---|---|---|---|
| Kishikawa et al. [82] | IDPS | N.A. | Medium | N.A. | N.A. | Low | Spoofing attack |
| Mousa et al. [83] | Message authentication | N.A. | N.A. | Low | N.A. | High | N.A. |
| Han et al. [84] | Message authentication | N.A. | N.A. | Medium | N.A. | N.A. | N.A. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khatri, N.; Shrestha, R.; Nam, S.Y. Security Issues with In-Vehicle Networks, and Enhanced Countermeasures Based on Blockchain. Electronics 2021, 10, 893. https://doi.org/10.3390/electronics10080893
Khatri N, Shrestha R, Nam SY. Security Issues with In-Vehicle Networks, and Enhanced Countermeasures Based on Blockchain. Electronics. 2021; 10(8):893. https://doi.org/10.3390/electronics10080893
Chicago/Turabian StyleKhatri, Narayan, Rakesh Shrestha, and Seung Yeob Nam. 2021. "Security Issues with In-Vehicle Networks, and Enhanced Countermeasures Based on Blockchain" Electronics 10, no. 8: 893. https://doi.org/10.3390/electronics10080893
APA StyleKhatri, N., Shrestha, R., & Nam, S. Y. (2021). Security Issues with In-Vehicle Networks, and Enhanced Countermeasures Based on Blockchain. Electronics, 10(8), 893. https://doi.org/10.3390/electronics10080893








