A Systematic Review of Fault Injection Attacks on IoT Systems
Abstract
:1. Introduction
- Analysis of the primary studies that propose frameworks to counter fault injection attacks on IoT systems using attack detection and software vulnerability analysis identifies the limitations and research gaps for each category.
- Proposal of hybrid attack detection methods at the software level that combine concepts from both categories, such as the use of software fault injection, machine learning, and code instrumentation tools, to address the limitations and improve the security of IoT systems against fault injection attacks.
2. Background
2.1. Fault Injection Attacks on IoT Systems
2.2. Software Effects of Fault Injection Attacks in IoT
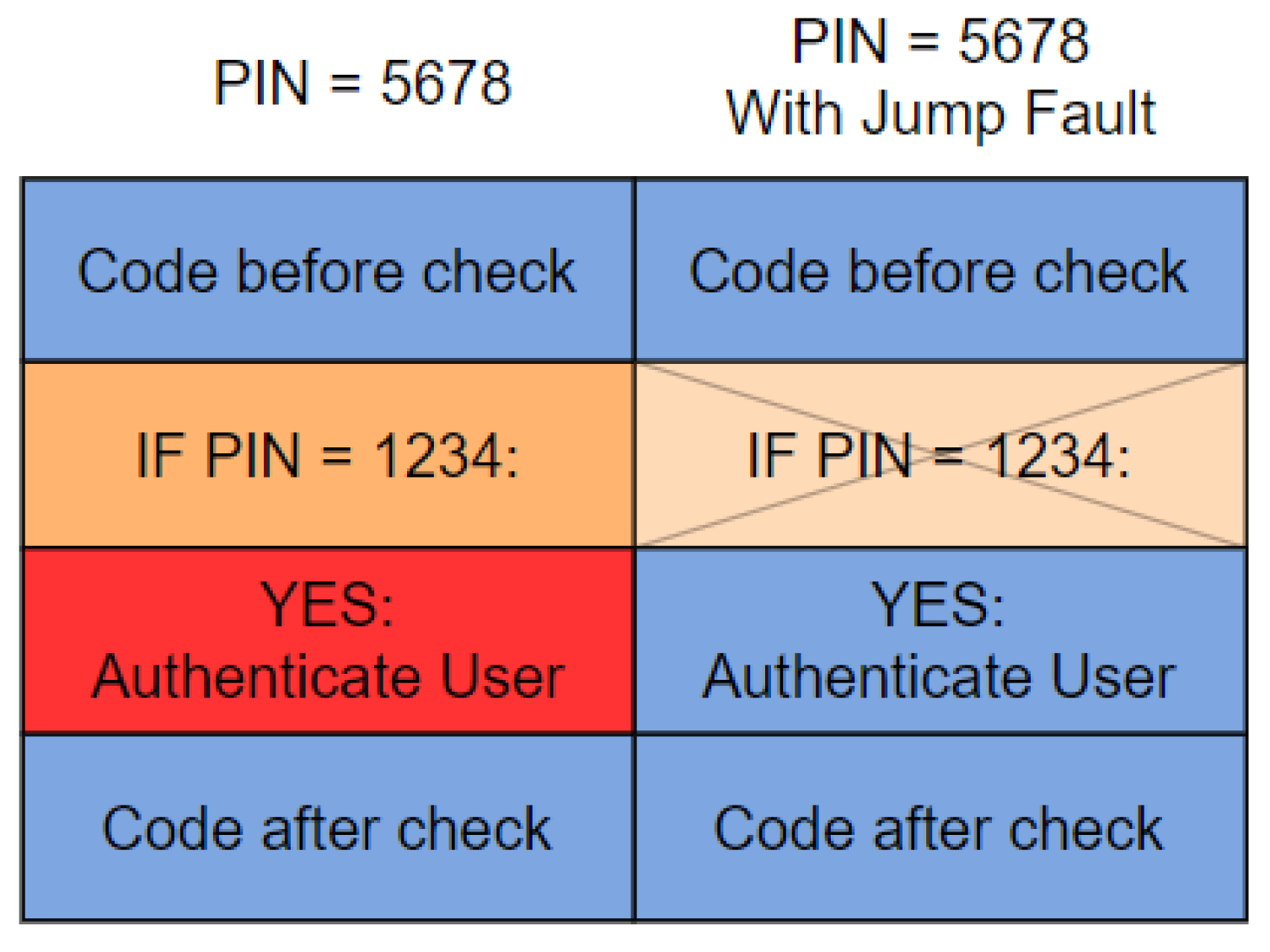
2.2.1. Control Flow Modifications
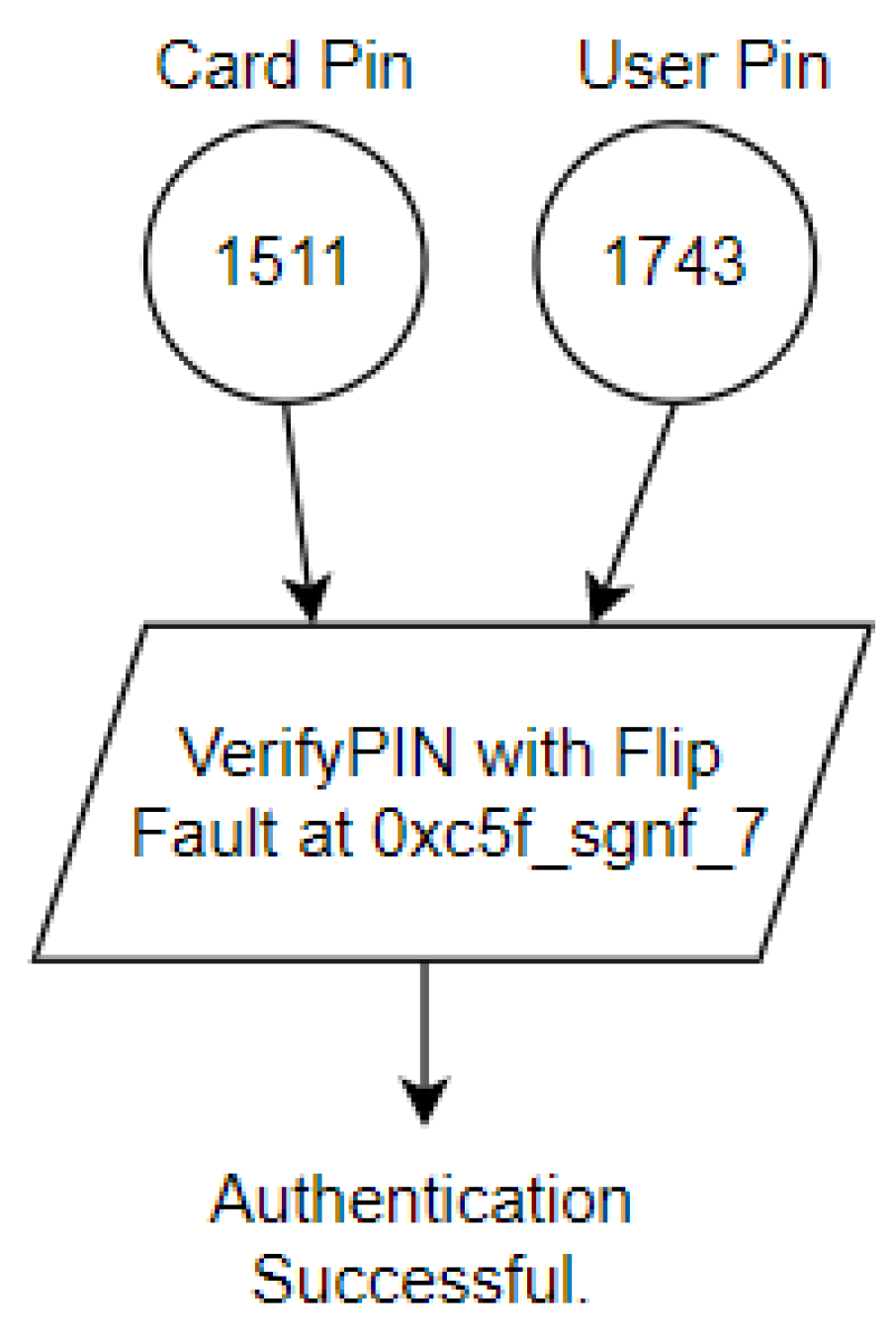
2.2.2. Data Corruption and Manipulation
2.3. Fault Models
3. Related Work
4. Method
4.1. Research Questions
- RQ1: What solutions have been proposed for dealing with fault injection attacks?
- RQ2: What are the limitations of the current solutions proposed and how can they be addressed?
- RQ3: Can the limitations of existing attack detection and software vulnerability methods be addressed by using hybrid solutions from both categories and techniques from the software testing domain?
4.2. Inclusion Criteria
- IC1: Addresses fault injection attacks on IoT systems
- IC2: Addresses detection and prevention of fault injection attacks in an IoT system or device
- IC3: Addresses software vulnerability analysis related to an IoT system or device
4.3. Search Process to Find Primary Studies
- “IoT embedded security physical fault injection attacks”
- “IoT embedded fault injection attack detection”
- “IoT embedded fault injection attack software vulnerability analysis”
4.4. Data Extraction and Analysis from Primary Studies
- The source of publication
- The authors and their institution
- The year of publication
- The task performed by the security framework
- The methodology and techniques used in the proposed solution
5. Results
5.1. Search Results
5.2. Addressing RQ1: Categorizing the Solutionss
5.2.1. Attack Detection
5.2.2. Software Vulnerability Analysis
5.3. Addressing RQ2: Analysis and Limitations
5.3.1. Attack Detection
- Standard instruments to replicate fault injection attacks on commonly used devices in IoT systems, such as ARM-based microprocessors, I/O devices, clock generators, etc.
- Generic attack detection frameworks using supervised machine-learning algorithms that provide better results but present the challenge of creating a labeled dataset. Such frameworks must be adaptable to multiple IoT systems with minor modifications.
- A generic labeled dataset generation workflow for attack detection applicable to a wide range of IoT systems and devices, preferably using emulation-based methods to avoid replicating fault injection attacks on the actual IoT system or device.
- Countering adversarial machine learning and false data injection attacks on the fault injection attack detection mechanism. Such attacks are commonly carried out on the physical properties of IoT systems, such as temperature, voltage level, electromagnetic field, and optical intensity, amongst many others.
5.3.2. Software Vulnerability Analysis
- Physical testing techniques to discover software vulnerabilities are limited by the lack of a generic hardware setup for different IoT systems and targeted fault injection attacks that trigger the software vulnerabilities.
- Simulation-based software vulnerability analysis techniques are limited by the microprocessor and instruction set architecture family supported by the software fault injection method. They are also limited by the difficulty in replicating high-level software effects of fault injection attacks by combining low-level fault models.
- There exist limited primary studies in the literature analyzing application software for vulnerabilities to fault injection attacks.
- The existing methods do not use supervised machine-learning techniques for detecting software vulnerabilities due to the lack of a generic labeled dataset generation workflow.
- The existing software vulnerability analysis techniques cannot be used in real-time to detect dynamically created software vulnerabilities.
5.4. Addressing RQ3: Future Research Directions and Solutions
5.4.1. Attack Detection
5.4.2. Software Vulnerability Analysis
5.4.3. Software-Level Attack Detection
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Yuce, B.; Schaumont, P.; Witteman, M.F. Fault Attacks on Secure Embedded Software: Threats, Design, and Evaluation. J. Hardw. Syst. Secur. 2018, 2, 111–130. [Google Scholar] [CrossRef] [Green Version]
- Barenghi, A.; Breveglieri, L.; Koren, I.; Naccache, D. Fault Injection Attacks on Cryptographic Devices: Theory, Practice, and Countermeasures. Proc. IEEE 2012, 100, 3056–3076. [Google Scholar] [CrossRef] [Green Version]
- Jiang, W. Machine Learning Methods to Detect Voltage Glitch Attacks on IoT/IIoT Infrastructures. Comput. Intell. Neurosci. 2022, 2022, 6044071. [Google Scholar] [CrossRef] [PubMed]
- Sahu, A.; Mao, Z.; Wlazlo, P.; Huang, H.; Davis, K.; Goulart, A.; Zonouz, S. Multi-Source Multi-Domain Data Fusion for Cyberattack Detection in Power Systems. IEEE Access 2021, 9, 119118–119138. [Google Scholar] [CrossRef]
- Benevenuti, F.; Kastensmidt, F.L. Evaluation of fault attack detection on SRAM-based FPGAs. In Proceedings of the 2017 18th IEEE Latin American Test Symposium (LATS), Punta del Este, Uruguay, 27–29 October 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Breier, J.; Bhasin, S.; He, W. An electromagnetic fault injection sensor using Hogge phase-detector. In Proceedings of the 2017 18th International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 14–15 March 2017; pp. 307–312. [Google Scholar] [CrossRef]
- Khosrowjerdi, H.; Meinke, K.; Rasmusson, A. Virtualized-Fault Injection Testing: A Machine Learning Approach. In Proceedings of the 2018 IEEE 11th International Conference on Software Testing, Verification and Validation (ICST), Vasteras, Sweden, 9–13 April 2018; pp. 297–308. [Google Scholar] [CrossRef]
- TGiven-Wilson; Jafri, N.; Legay, A. Combined software and hardware fault injection vulnerability detection. Innov. Syst. Softw. Eng. 2020, 16, 101–120. [Google Scholar] [CrossRef]
- Rivière, L.; Potet, M.-L.; Le, T.-H.; Bringer, J.; Chabanne, H.; Puys, M. Combining High-Level and Low-Level Approaches to Evaluate Software Implementations Robustness Against Multiple Fault Injection Attacks. Found. Pract. Secur. 2015, 8930, 92–111. [Google Scholar]
- Delarea, S.; Oren, Y. Practical, Low-Cost Fault Injection Attacks on Personal Smart Devices. Appl. Sci. 2022, 12, 417. [Google Scholar] [CrossRef]
- Papadimitriou, A.; Nomikos, K.; Psarakis, M.; Aerabi, E.; Hely, D. You can detect but you cannot hide: Fault Assisted Side Channel Analysis on Protected Software-based Block Ciphers. In Proceedings of the 2020 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT), Frascati, Italy, 19–21 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Valencia, F.; Oder, T.; Güneysu, T.; Regazzoni, F. Exploring the Vulnerability of R-LWE Encryption to Fault Attacks. In Proceedings of the Fifth Workshop on Cryptography and Security in Computing Systems, Online, 24 January 2018; pp. 7–12. [Google Scholar] [CrossRef]
- Barbu, G.; Thiebeauld, H.; Guerin, V. Attacks on Java Card 3.0 Combining Fault and Logical Attacks. In International Conference on Smart Card Research and Advanced Applications; Springer: Berlin/Heidelberg, Germany, 2010; pp. 148–163. [Google Scholar]
- Dehbaoui, A.; Mirbaha, A.-P.; Moro, N.; Dutertre, J.-M.; Tria, A. Electromagnetic Glitch on the AES Round Counter. In Constructive Side-Channel Analysis and Secure Design; Springer: Berlin/Heidelberg, Germany, 2013; pp. 17–31. [Google Scholar]
- Dutertre, J.-M.; Menu, A.; Potin, O.; Rigaud, J.-B.; Danger, J.-L. Experimental analysis of the electromagnetic instruction skip fault model and consequences for software countermeasures. Microelectron. Reliab. 2021, 121, 114133. [Google Scholar] [CrossRef]
- Menu, A.; Dutertre, J.-M.; Potin, O.; Rigaud, J.-B.; Danger, J.-L. Experimental Analysis of the Electromagnetic Instruction Skip Fault Model. In Proceedings of the 2020 15th Design Technology of Integrated Systems in Nanoscale Era (DTIS), Marrakesh, Morocco, 1–3 April 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Breier, J.; Jap, D.; Chen, C.-N. Laser Profiling for the Back-Side Fault Attacks: With a Practical Laser Skip Instruction Attack on AES. In Proceedings of the 1st ACM Workshop on Cyber-Physical System Security, Denver, CO, USA, 16 October 2015; pp. 99–103. [Google Scholar] [CrossRef]
- Joye, M.; Tunstall, M. Fault Analysis in Cryptography; Springer: Berlin/Heidelberg, Germany, 2012; p. 147. [Google Scholar]
- Kazemi, Z.; Hely, D.; Fazeli, M.; Beroulle, V. A Review on Evaluation and Configuration of Fault Injection Attack Instruments to Design Attack Resistant MCU-Based IoT Applications. Electronics 2020, 9, 1153. [Google Scholar] [CrossRef]
- Polychronou, N.-F.; Thevenon, P.-H.; Puys, M.; Beroulle, V. A Comprehensive Survey of Attacks without Physical Access Targeting Hardware Vulnerabilities in IoT/IIoT Devices, and Their Detection Mechanisms. ACM Trans. Des. Autom. Electron. Syst. 2021, 27, 1–35. [Google Scholar] [CrossRef]
- Dureuil, L.; Potet, M.-L.; de Choudens, P.; Dumas, C.; Clédière, J. From Code Review to Fault Injection Attacks: Filling the Gap Using Fault Model Inference. In Smart Card Research and Advanced Applications; Springer: Berlin/Heidelberg, Germany, 2016; pp. 107–124. [Google Scholar]
- Eslami, M.; Ghavami, B.; Raji, M.; Mahani, A. A survey on fault injection methods of digital integrated circuits. Integration 2020, 71, 154–163. [Google Scholar] [CrossRef]
- Qasem, A.; Shirani, P.; Debbabi, M.; Wang, L.; Lebel, B.; Agba, B.L. Automatic Vulnerability Detection in Embedded Devices and Firmware: Survey and Layered Taxonomies. ACM Comput. Surv. 2021, 54, 1–42. [Google Scholar] [CrossRef]
- Lou, X.; Zhang, T.; Jiang, J.; Zhang, Y. A Survey of Microarchitectural Side-Channel Vulnerabilities, Attacks, and Defenses in Cryptography. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Potestad-Ordóñez, F.E.; Tena-Sánchez, E.; Acosta-Jiménez, A.J.; Jiménez-Fernández, C.J.; Chaves, R. Hardware Countermeasures Benchmarking against Fault Attacks. Appl. Sci. 2022, 12, 2443. [Google Scholar] [CrossRef]
- Shah, I.A.; Rajper, S.; ZamanJhanjhi, N. Using ML and Data-Mining Techniques in Automatic Vulnerability Software Discovery. Int. J. Adv. Trends Comput. Sci. Eng. 2021, 10, 2109–2126. [Google Scholar] [CrossRef]
- Eceiza, M.; Flores, J.L.; Iturbe, M. Fuzzing the Internet of Things: A Review on the Techniques and Challenges for Efficient Vulnerability Discovery in Embedded Systems. IEEE Internet Things J. 2021, 8, 10390–10411. [Google Scholar] [CrossRef]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering—A systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Igarashi, H.; Shi, Y.; Yanagisawa, M.; Togawa, N. Concurrent faulty clock detection for crypto circuits against clock glitch based DFA. In Proceedings of the 2013 IEEE International Symposium on Circuits and Systems (ISCAS), Beijing, China, 19–23 May 2013; pp. 1432–1435. [Google Scholar] [CrossRef]
- Moro, N.; Heydemann, K.; Encrenaz, E.; Robisson, B. Formal verification of a software countermeasure against instruction skip attacks. J. Cryptogr. Eng. 2014, 4, 145–156. [Google Scholar] [CrossRef] [Green Version]
- Potet, M.-L.; Mounier, L.; Puys, M.; Dureuil, L. Lazart: A Symbolic Approach for Evaluation the Robustness of Secured Codes against Control Flow Injections. In Proceedings of the 2014 IEEE Seventh International Conference on Software Testing, Verification and Validation, Cleveland, OH, USA, 31 March–4 April 2014; pp. 213–222. [Google Scholar] [CrossRef] [Green Version]
- Shrivastwa, R.-R.; Guilley, S.; Danger, J.-L. Multi-source Fault Injection Detection Using Machine Learning and Sensor Fusion. In Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2021; pp. 93–107. [Google Scholar]
- Köylü, T.Ç.; Reinbrecht, C.R.W.; Hamdioui, S.; Taouil, M. RNN-Based detection of fault attacks on RSA. In Proceedings of the IEEE International Symposium on Circuits and Systems, Daegu, Korea, 22–28 May 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Richter-Brockmann, J.; Shahmirzadi, A.R.; Sasdrich, P.; Moradi, A.; Güneysu, T. Fiver–robust verification of countermeasures against fault injections. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2021, 2021, 447–473. [Google Scholar] [CrossRef]
- Lacombe, G.; Feliot, D.; Boespflug, E.; Potet, M.-L. Combining Static Analysis and Dynamic Symbolic Execution in a Toolchain to detect Fault Injection Vulnerabilities. September 2021. Available online: https://www.proofs-workshop.org/2021/papers/paper2.pdf (accessed on 20 April 2022).
- Bréjon, J.-B.; Heydemann, K.; Encrenaz, E.; Meunier, Q.; Vu, S.-T. Fault Attack Vulnerability Assessment of Binary Code. In Proceedings of the Sixth Workshop on Cryptography and Security in Computing Systems, Valencia, Spain, 21 January 2019; pp. 13–18. [Google Scholar] [CrossRef]
- Mahmoud, A.; Venkatagiri, R.; Ahmed, K.; Misailovic, S.; Marinov, D.; Fletcher, C.W.; Adve, S.V. Minotaur: Adapting Software Testing Techniques for Hardware Errors. In Proceedings of the Twenty-Fourth International Conference on Architectural Support for Programming Languages and Operating Systems, Providence, RI, USA, 13–17 April 2019; pp. 1087–1103. [Google Scholar] [CrossRef]
- Deshpande, C.; Yuce, B.; Ghalaty, N.F.; Ganta, D.; Schaumont, P.; Nazhandali, L. A Configurable and Lightweight Timing Monitor for Fault Attack Detection. In Proceedings of the 2016 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Pittsburgh, PA, USA, 11–13 July 2016; pp. 461–466. [Google Scholar] [CrossRef]
- Kaliorakis, M.; Tselonis, S.; Chatzidimitriou, A.; Gizopoulos, D. Accelerated microarchitectural Fault Injection-based reliability assessment. In Proceedings of the 2015 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFTS), Amherst, MA, USA, 12–14 October 2015; pp. 47–52. [Google Scholar] [CrossRef]
- Höller, A.; Krieg, A.; Rauter, T.; Iber, J.; Kreiner, C. QEMU-Based Fault Injection for a System-Level Analysis of Software Countermeasures Against Fault Attacks. In Proceedings of the 2015 Euromicro Conference on Digital System Design, Madeira, Portugal, 26–28 August 2015; pp. 530–533. [Google Scholar] [CrossRef]
- Rivière, L.; Bringer, J.; Le, T.-H.; Chabanne, H. A novel simulation approach for fault injection resistance evaluation on smart cards. In Proceedings of the 2015 IEEE Eighth International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Graz, Austria, 13–17 April 2015; pp. 1–8. [Google Scholar] [CrossRef]
- Facon, A.; Guilley, S.; Ngo, X.; Nguyen, R.; Perianin, T.; Shrivastwa, R. High Precision EMFI Detector using Machine Learning and Sensor Fusion. Available online: https://www.cesar-conference.org/wp-content/uploads/2019/10/resume_IAD_soum15-2.pdf (accessed on 12 April 2022).
- Dutertre, J.-M.; Mirbaha, A.-P.; Naccache, D.; Ribotta, A.-L.; Tria, A.; Vaschalde, T. Fault Round Modification Analysis of the advanced encryption standard. In Proceedings of the 2012 IEEE International Symposium on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 3–4 June 2012; pp. 140–145. [Google Scholar] [CrossRef]
- Lee, H. Framework and development of fault detection classification using IoT device and cloud environment. J. Manuf. Syst. 2017, 43, 257–270. [Google Scholar] [CrossRef]
- Jiang, W.; Wen, L.; Zhan, J.; Jiang, K. Design optimization of confidentiality-critical cyber physical systems with fault detection. J. Syst. Archit. 2020, 107, 101739. [Google Scholar] [CrossRef]
- Kazemi, Z.; Fazeli, M.; Hely, D.; Beroulle, V. Hardware Security Vulnerability Assessment to Identify the Potential Risks in A Critical Embedded Application. In Proceedings of the 2020 IEEE 26th International Symposium on On-Line Testing and Robust System Design (IOLTS), Napoli, Italy, 13–15 July 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Qiu, P.; Wang, D.; Lyu, Y.; Tian, R.; Wang, C.; Qu, G. VoltJockey: A New Dynamic Voltage Scaling-Based Fault Injection Attack on Intel SGX. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2021, 40, 1130–1143. [Google Scholar] [CrossRef]
- Chen, Z.; Vasilakis, G.; Murdock, K.; Dean, E.; Oswald, D.; Garcia, F.D. VoltPillager: Hardware-based fault injection attacks against Intel SGX Enclaves using the SVID voltage scaling interface. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Virtual, CA, USA, 11–13 August 2021; pp. 699–716. [Google Scholar]
- Bossuet, L.; de Laulanié, L.; Chassagne, B. Multi-Spot Laser Fault Injection Setup: New Possibilities for Fault Injection Attacks. In Proceedings of the Smart Card Research and Advanced Applications: 20th International Conference, CARDIS 2021, Lübeck, Germany, 11–12 November 2021. [Google Scholar]
- Zavalyshyn, I.; Given–Wilson, T.; Legay, A.; Sadre, R.; Rivière, E. Chaos Duck: A Tool for Automatic IoT Software Fault-Tolerance Analysis. In Proceedings of the 2021 40th International Symposium on Reliable Distributed Systems (SRDS), Chicago, IL, USA, 20–23 September 2021; pp. 46–55. [Google Scholar] [CrossRef]
- Grycel, J.; Schaumont, P. SimpliFI: Hardware Simulation of Embedded Software Fault Attacks. Cryptography 2021, 5, 15. [Google Scholar] [CrossRef]
- Lattner, C.; Adve, V. LLVM: A compilation framework for lifelong program analysis & transformation. In Proceedings of the International Symposium on Code Generation and Optimization, CGO, San Jose, CA, USA, 20–24 March 2004; pp. 75–86. [Google Scholar] [CrossRef]
- Patel, A.; Afram, F.; Ghose, K. Marss-x86: A qemu-based micro-architectural and systems simulator for x86 multicore processors. In Proceedings of the 1st International Qemu Users’ Forum, Grenoble, France, 18 March 2011; pp. 29–30. [Google Scholar]
- Given-Wilson, T.; Jafri, N.; Lanet, J.-L.; Legay, A. An Automated Formal Process for Detecting Fault Injection Vulnerabilities in Binaries and Case Study on PRESENT. In Proceedings of the 2017 IEEE Trustcom/BigDataSE/ICESS, Sydney, Australia, 1–4 August 2017; pp. 293–300. [Google Scholar] [CrossRef] [Green Version]
- Padmanabhuni, B.M.; Tan, H.B.K. Buffer Overflow Vulnerability Prediction from x86 Executables Using Static Analysis and Machine Learning. In Proceedings of the 2015 IEEE 39th Annual Computer Software and Applications Conference, Washington, DC, USA, 1–5 July 2015; Volume 2, pp. 450–459. [Google Scholar] [CrossRef]
- Li, J.; Yang, Y.; Sun, J.S.; Tomsovic, K.; Qi, H. ConAML: Constrained Adversarial Machine Learning for Cyber-Physical Systems. In Proceedings of the 2021 ACM Asia Conference on Computer and Communications Security, Hong Kong, China, 7–11 June 2021; pp. 52–66. [Google Scholar] [CrossRef]
- Gravellier, J.; Dutertre, J.-M.; Teglia, Y.; Moundi, P.L.; Olivier, F. Remote Side-Channel Attacks on Heterogeneous SoC. In Smart Card Research and Advanced Applications; Springer: Berlin/Heidelberg, Germany, 2020; pp. 109–125. [Google Scholar]
- Shepherd, C.; Markantonakis, K.; van Heijningen, N.; Aboulkassimi, D.; Gaine, C.; Heckmann, T.; Naccache, D. Physical fault injection and side-channel attacks on mobile devices: A comprehensive analysis. Comput. Secur. 2021, 111, 102471. [Google Scholar] [CrossRef]
- Höller, R.; Haselberger, D.; Ballek, D.; Rössler, P.; Krapfenbauer, M.; Linauer, M. Open-Source RISC-V Processor IP Cores for FPGAs—Overview and Evaluation. In Proceedings of the 2019 8th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 10–14 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Gray, J. GRVI Phalanx: A Massively Parallel RISC-V FPGA Accelerator Accelerator. In Proceedings of the 2016 IEEE 24th Annual International Symposium on Field-Programmable Custom Computing Machines (FCCM), Washington, DC, USA, 1–3 May 2016; pp. 17–20. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.; Chen, H.; Young, J.; Kim, H. RISC-V FPGA Platform Toward ROS-Based Robotics Application. In Proceedings of the 2020 30th International Conference on Field-Programmable Logic and Applications (FPL), Gothenburg, Sweden, 31 August–4 September 2020; p. 370. [Google Scholar] [CrossRef]
- Nashimoto, S.; Homma, N.; Hayashi, Y.; Takahashi, J.; Fuji, H.; Aoki, T. Buffer overflow attack with multiple fault injection and a proven countermeasure. J. Cryptogr. Eng. 2017, 7, 35–46. [Google Scholar] [CrossRef]
- Dureuil, L.; Petiot, G.; Potet, M.-L.; Le, T.-H.; Crohen, A.; de Choudens, P. FISSC: A Fault Injection and Simulation Secure Collection. In Computer Safety, Reliability, and Security; Springer: Cham, Switzerland, 2016; pp. 3–11. [Google Scholar]
- Tramer, F.; Boneh, D. Adversarial training and robustness for multiple perturbations. In Advances in Neural Information Processing Systems; Curran Associates Inc.: Vancouver, BC, Canada, 2019; p. 32. [Google Scholar] [CrossRef]
- Zhang, H.; Wang, J. Defense against adversarial attacks using feature scattering-based adversarial training. In Advances in Neural Information Processing Systems; Curran Associates Inc.: Vancouver, BC, Canada, 2019; p. 32. [Google Scholar] [CrossRef]
- Miyato, T.; Maeda, S.; Koyama, M.; Ishii, S. Virtual adversarial training: A regularization method for supervised and semi-supervised learning. IEEE Trans. Pattern Anal. Mach. Intell. 2018, 41, 1979–1993. [Google Scholar] [CrossRef] [Green Version]
- Yamaguchi, F.; Maier, A.; Gascon, H.; Rieck, K. Automatic Inference of Search Patterns for Taint-Style Vulnerabilities. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 797–812. [Google Scholar] [CrossRef]
- Kim, S.; Kim, R.Y.C.; Park, Y.B. Software vulnerability detection methodology combined with static and dynamic analysis. Wirel. Pers. Commun. 2016, 89, 777–793. [Google Scholar] [CrossRef]
- Luk, C.-K.; Cohn, R.; Muth, R.; Patil, H.; Klauser, A.; Lowney, G.; Wallace, S.; Reddi, V.J.; Hazelwood, K. Pin: Building Customized Program Analysis Tools with Dynamic Instrumentation. SIGPLAN Not. 2005, 40, 190–200. [Google Scholar] [CrossRef]
- Bruening, D.; Zhao, Q.; Kleckner, R. DynamoRIO: Dynamic Instrumentation Tool Platform. February 2009. Available online: https://www.dynamorio.org (accessed on 25 April 2022).
- Bukasa, S.K.; Lashermes, R.; Lanet, J.-L.; Leqay, A. Let’s Shock Our IoT’s Heart: ARMv7-M under (Fault) Attacks. In Proceedings of the ARES 2018: Proceedings of the 13th International Conference on Availability, Reliability and Security, Online, 27 August 2018; p. 33. [Google Scholar] [CrossRef] [Green Version]

| Primary Study | Year | Source | Type |
|---|---|---|---|
| Shrivastwa et al. [32] | 2021 | Springer | B |
| Richter-Brockmann et al. [34] | 2021 | IACR | J |
| Lacombe et al. [35] | 2021 | HAL | C |
| Dutertre et al. [15] | 2021 | ScienceDirect | J |
| Wei et al. [3] | 2020 | ScienceDirect | J |
| Given-Wilson et al. [8] | 2020 | Springer | J |
| Koylu et al. [33] | 2020 | IEEE Xplore | C |
| Brejon et al. [36] | 2019 | ACM | C |
| Mahmoud et al. [37] | 2019 | ACM | C |
| Khosrowjerdi et al. [7] | 2018 | IEEE Xplore | C |
| Benevenuti et al. [2] | 2017 | IEEE Xplore | J |
| Deshpande et al. [38] | 2016 | IEEE Xplore | C |
| Kaliorakis et al. [39] | 2015 | IEEE Xplore | C |
| Rivière et al. [9] | 2015 | Springer | C |
| Holler et al. [40] | 2015 | IEEE Xplore | C |
| Riviere et al. [41] | 2015 | IEEE Xplore | C |
| Potet et al. [31] | 2014 | IEEE Xplore | C |
| Moro et al. [30] | 2014 | Springer | J |
| Hiroaki et al. [29] | 2013 | IEEE Xplore | C |
| Primary Study | Type | Details |
|---|---|---|
| Shrivastwa et al. [32] | AD | EMFI and CGFI detection with FPGA-based sensor fusion monitoring |
| Facon et al. [42] | AD | EMFI detection with FPGA-based digital smart monitor |
| Deshpande et al. [38] | AD | FPGA-based monitor for clock glitch attack |
| Hiroaki et al. [29] | AD | Faulty clock monitor for crypto device |
| Benevenuti et al. [2] | AD | For SRAM FPGAs using functional redundancy |
| Wei et al. [3] | AD | Semi-supervised detection of voltage glitch attacks using neural network |
| Richter-Brockmann et al. [34] | SVA | Using physical fault injection framework |
| Given-Wilson et al. [8] | SVA | Formal methods and model checking |
| Brejon et al. [36] | SVA | Model checking based vulnerability analysis |
| Kaliorakis et al. [39] | SVA | Using micro-architectural fault injection simulation |
| Potet et al. [31] | SVA | Using model checking and dynamic symbolic execution against laser attacks |
| Rivière et al. [9] | SVA | Combined source code and assembly code analysis |
| Lacombe et al. [35] | SVA | Combined toolchain for static and symbolic program analysis |
| Holler et al. [40] | SVA | Using QEMU-based microarchitectural simulator |
| Riviere et al. [41] | SVA | EFS + Lazart for multi-level simulation |
| Khosrowjerdi et al. [7] | SVA | Learning-based fault injection test case prioritization |
| Dutertre et al. [15] | SVA | For multiple instruction skips on AES using EMFI simulation |
| Koylu et al. [33] | SVA | RNN-based control flow modification detection in RSA |
| Moro et al. [30] | SVA | Using instruction skip attacks on cryptography software |
| Mahmoud et al. [37] | SVA | Silent data corruption detection using software testing techniques |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gangolli, A.; Mahmoud, Q.H.; Azim, A. A Systematic Review of Fault Injection Attacks on IoT Systems. Electronics 2022, 11, 2023. https://doi.org/10.3390/electronics11132023
Gangolli A, Mahmoud QH, Azim A. A Systematic Review of Fault Injection Attacks on IoT Systems. Electronics. 2022; 11(13):2023. https://doi.org/10.3390/electronics11132023
Chicago/Turabian StyleGangolli, Aakash, Qusay H. Mahmoud, and Akramul Azim. 2022. "A Systematic Review of Fault Injection Attacks on IoT Systems" Electronics 11, no. 13: 2023. https://doi.org/10.3390/electronics11132023
APA StyleGangolli, A., Mahmoud, Q. H., & Azim, A. (2022). A Systematic Review of Fault Injection Attacks on IoT Systems. Electronics, 11(13), 2023. https://doi.org/10.3390/electronics11132023






