Recent Progress of Using Knowledge Graph for Cybersecurity
Abstract
:1. Introduction
- A comprehensive review of existing application scenarios of CSKG. We propose a novel classification framework for conducting a comprehensive review of the application scenarios of CSKG based on an investigation of the background and construction technology of CSKG.
- We summarize the relevant datasets. To facilitate CSKGs’ future research, we provide a review of datasets and the analysis of open-source libraries for two tasks: the CSKG construction task and the task of information extraction.
- Future directions. This survey summarizes each category and suggests possible future study directions.
2. A Brief Overview of Construction Methods for Cybersecurity Knowledge Graph
2.1. Some Definitions
2.2. The Building Flow of KG
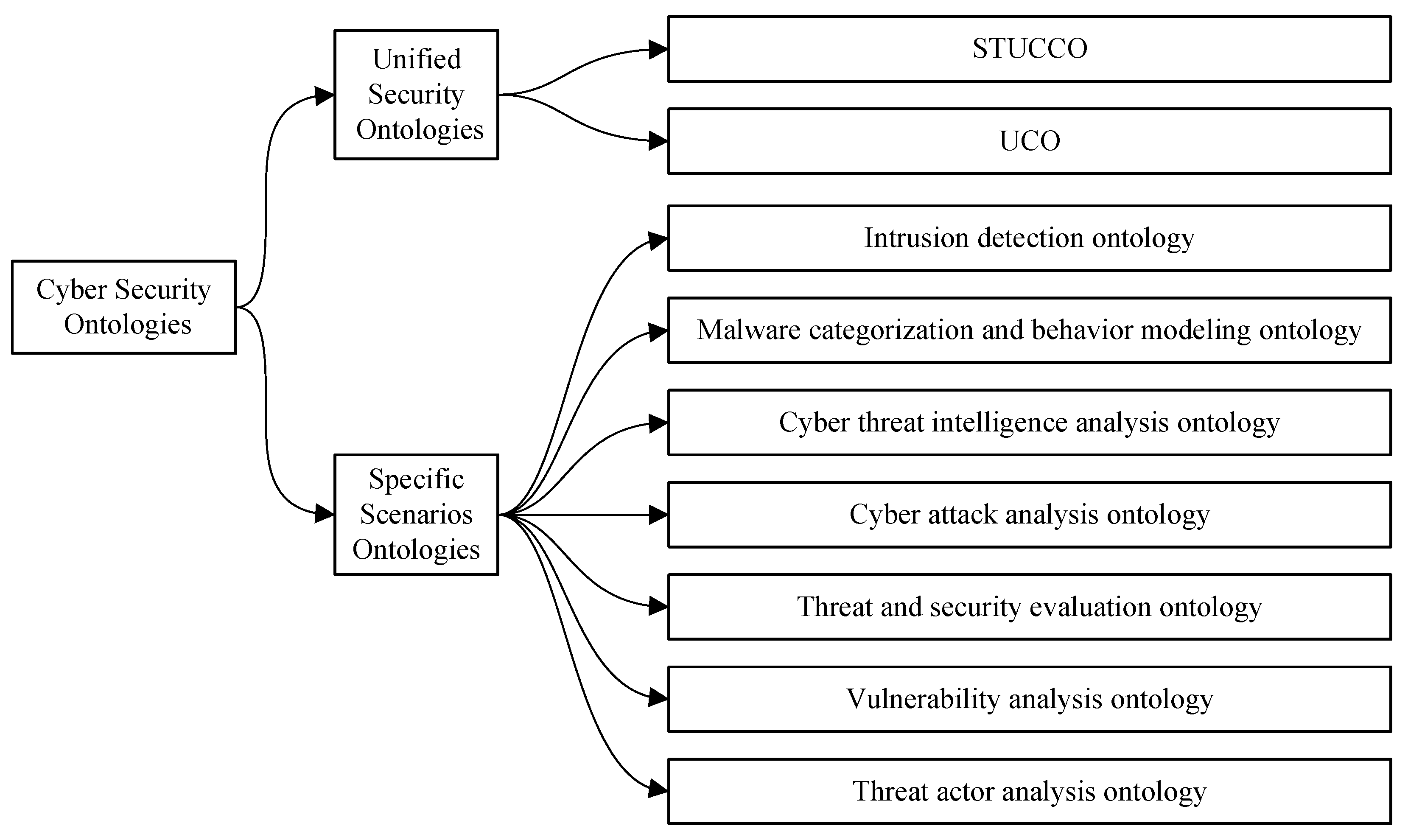
2.3. Cybersecurity Ontology
2.4. Cybersecurity Entities Extraction
2.5. Relationships Extraction of Cybersecurity Entities
3. The Datasets
3.1. The Datasets of Open-Source CSKG
3.2. The Datasets for Information Extraction Task
3.3. Other Datasets for the Application of CSKG
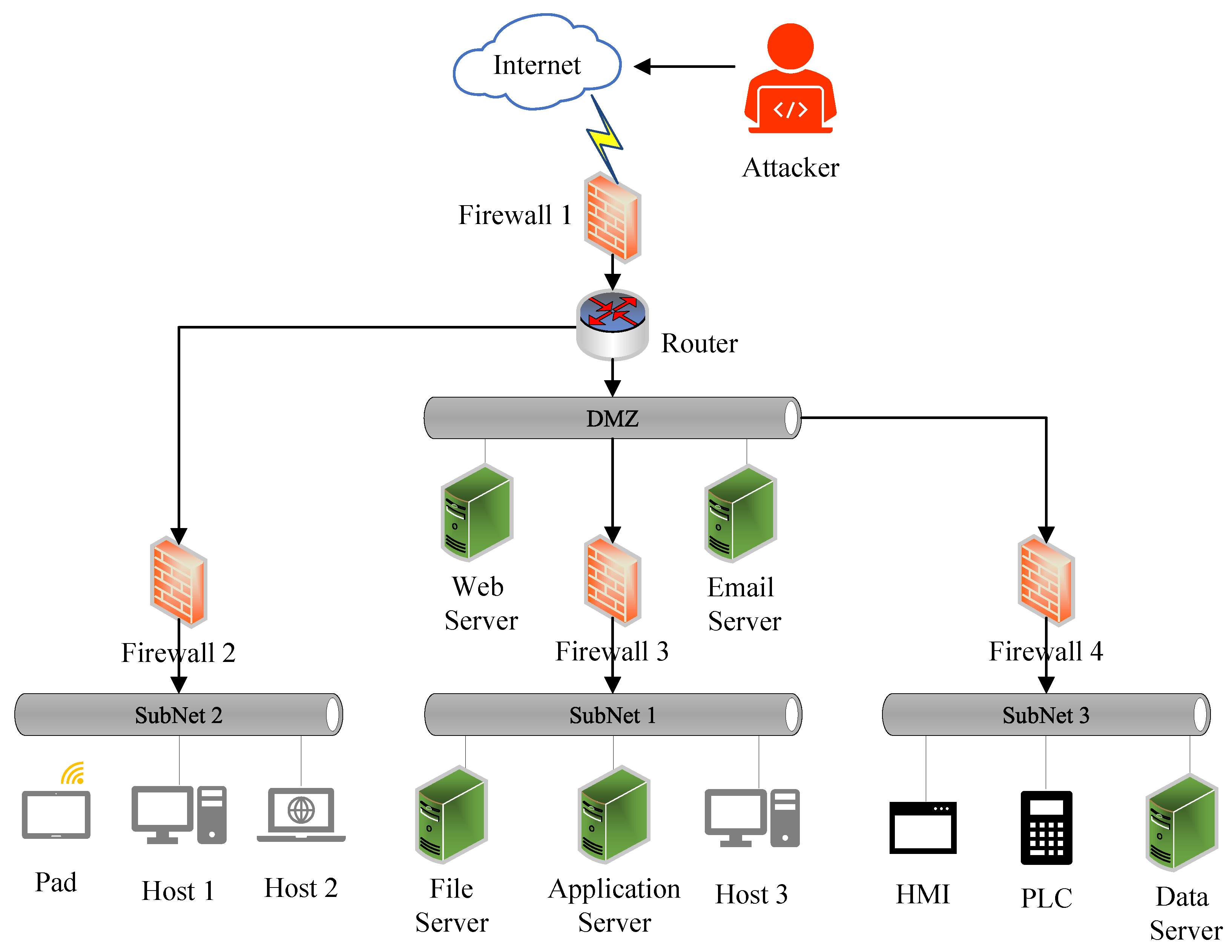
4. The Application Scenarios
4.1. Situation Awareness and Security Assessment
4.1.1. Security Awareness
4.1.2. Security Assessment
4.2. Threats Discovery
4.2.1. Attack Prediction
4.2.2. Threat Hunting
4.2.3. Intrusion Detection
4.3. Attack Investigation
4.3.1. Attack Path Analysis
4.3.2. Attack Attribution
4.3.3. Consequence Prediction
4.3.4. Attack Analysis
4.4. Intelligent Security Operation
4.4.1. Intelligent Operation
4.4.2. Security Alert or Event Correlation Analysis
4.5. Intelligent Decision-Making
4.5.1. Generation of Attack Strategy
4.5.2. Security Policy Validation
4.6. Vulnerability Management and Prediction
4.7. Malware Attribution and Analysis
4.8. Connection to the Physical System
4.9. Two New Applications
4.9.1. Social Engineering
4.9.2. Combating Fake Intelligence
5. Discussion and Research Opportunities
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Osborne, C. Colonial Pipeline Paid Close to $5 Million in Ransomware Blackmail Payment. 2021. Available online: https://www.calvin.edu/library/knightcite/index.php (accessed on 3 April 2022).
- Auer, M. Lack of Experts in Cyber Security. 2020. Available online: https://www.threatq.com/lack-of-experts-in-cyber-security/ (accessed on 3 April 2022).
- Kumar, K.; Pande, B.P. Applications of machine learning techniques in the realm of cybersecurity. Cyber Secur. Digit. Forensics 2022, 295–315. [Google Scholar] [CrossRef]
- Liebetrau, T. Cyber conflict short of war: A European strategic vacuum. Eur. Secur. 2022, 1–20. [Google Scholar] [CrossRef]
- Cole, E. Advanced Persistent Threat: Understanding the Danger and How to Protect Your Organization; Newnes: Newton, MA, USA, 2012. [Google Scholar]
- Sriavstava, R.; Singh, P.; Chhabra, H. Review on cyber security intrusion detection: Using methods of machine learning and data mining. In Internet of Things and Big Data Applications; Springer: New York, NY, USA, 2020; pp. 121–132. [Google Scholar]
- Pang, G.; Shen, C.; Cao, L.; Hengel, A.V.D. Deep learning for anomaly detection: A review. ACM Comput. Surv. (CSUR) 2021, 54, 1–38. [Google Scholar] [CrossRef]
- Perdisci, R.; Ariu, D.; Fogla, P.; Giacinto, G.; Lee, W. McPAD: A multiple classifier system for accurate payload-based anomaly detection. Comput. Netw. 2009, 53, 864–881. [Google Scholar] [CrossRef] [Green Version]
- Llorens, A. 5 Best Practices to Get More from Threat Intelligence. 2021. Available online: https://www.threatq.com/5-best-practices-more-threat-intelligence/ (accessed on 3 April 2022).
- Xue, R.; Tang, P.; Fang, S. Prediction of computer network security situation based on association rules mining. Wirel. Commun. Mob. Comput. 2022, 2022, 2794889. [Google Scholar] [CrossRef]
- Zeng, Z.; Peng, W.; Zeng, D.; Zeng, C.; Chen, Y. Intrusion detection framework based on causal reasoning for DDoS. J. Inf. Secur. Appl. 2022, 65, 103–124. [Google Scholar] [CrossRef]
- Sikos, L.F.; Philp, D.; Howard, C.; Voigt, S.; Stumptner, M.; Mayer, W. Knowledge representation of network semantics for reasoning-powered cyber-situational awareness. In AI in Cybersecurity; Springer: New York, NY, USA, 2019; pp. 19–45. [Google Scholar]
- Rastogi, N.; Dutta, S.; Zaki, M.J.; Gittens, A.; Aggarwal, C. Malont: An ontology for malware threat intelligence. In Proceedings of the International Workshop on Deployable Machine Learning for Security Defense, San Diego, CA, USA, 24 August 2020; Springer: New York, NY, USA, 2020; pp. 28–44. [Google Scholar]
- Zhao, J.; Yan, Q.; Li, J.; Shao, M.; He, Z.; Li, B. TIMiner: Automatically extracting and analyzing categorized cyber threat intelligence from social data. Comput. Secur. 2020, 95, 101867. [Google Scholar] [CrossRef]
- Husari, G.; Al-Shaer, E.; Ahmed, M.; Chu, B.; Niu, X. Ttpdrill: Automatic and accurate extraction of threat actions from unstructured text of cti sources. In Proceedings of the 33rd Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; pp. 103–115. [Google Scholar]
- Bouarroudj, W.; Boufaida, Z.; Bellatreche, L. Named entity disambiguation in short texts over knowledge graphs. Knowl. Inf. Syst. 2022, 64, 325–351. [Google Scholar] [CrossRef]
- Ji, S.; Pan, S.; Cambria, E.; Marttinen, P.; Philip, S.Y. A survey on knowledge graphs: Representation, acquisition, and applications. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 494–514. [Google Scholar] [CrossRef]
- Zhang, K.; Liu, J. Review on the application of knowledge graph in cyber security assessment. In IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2020; Volume 768, pp. 52–103. [Google Scholar]
- Noel, S. A review of graph approaches to network security analytics. In From Database to Cyber Security; Springer: Cham, Switzerland, 2018; pp. 300–323. [Google Scholar]
- Sani, M. Knowledge Graph on Cybersecurity: A Survey. 2020. Available online: https://upvdoc.univ-perp.fr/fr/congres-des-doctorants/article-maman-sani-aboubacar (accessed on 3 April 2022).
- Yan, Z.; Liu, J. A review on application of knowledge graph in cybersecurity. In Proceedings of the 2020 IEEE International Signal Processing, Communications and Engineering Management Conference (ISPCEM), Montreal, QC, Canada, 27–29 November 2020; pp. 240–243. [Google Scholar]
- Dong, C.; Jiang, B.; Lu, Z.; Liu, B.; Li, N.; Ma, P. Knowledge graph for cyberspace security intelligence: A survey. J. Cyber. Secur. 2020, 5, 56–76. [Google Scholar]
- Ding, Z.; Liu, K.; Liu, B.; Zhu, X. Survey of cyber security knowledge graph. J. Huazhong Univ. Sci. Tech. (Nat. Sci. Ed.) 2021, 49, 79–91. [Google Scholar]
- Lassila, O.; Swick, R.R. Resource Description Framework (RDF) Model and Syntax Specification. 1999. Available online: http://w3.org/TR/1999/REC-rdf-syntax-19990222 (accessed on 3 April 2022).
- Smith, K.M. OWL Web Ontology Language Guide. 2004. Available online: http://w3.org/TR/owl-guide (accessed on 3 April 2022).
- Singhal, A. Introducing the Knowledge Graph: Things, Not Strings. 2012. Available online: https://blog.google/products/search/introducing-knowledge-graph-things-not/ (accessed on 3 April 2022).
- Hogan, A.; Blomqvist, E.; Cochez, M.; d’Amato, C.; Melo, G.d.; Gutierrez, C.; Kirrane, S.; Gayo, J.E.L.; Navigli, R.; Neumaier, S.; et al. Knowledge graphs. Synth. Lect. Data Semant. Knowl. 2021, 12, 1–257. [Google Scholar] [CrossRef]
- Yang, Y.; Xu, B.; Hu, J.; Tong, M.; Zhang, P.; Zheng, L. Accurate and efficient method for constructing domain knowledge graph. J. Softw. 2018, 29, 2931–2947. [Google Scholar]
- Du, X.; Li, M.; Wang, S. A survey on ontology learning research. J. Softw. 2006, 17. [Google Scholar] [CrossRef]
- Iannacone, M.; Bohn, S.; Nakamura, G.; Gerth, J.; Huffer, K.; Bridges, R.; Ferragut, E.; Goodall, J. Developing an ontology for cyber security knowledge graphs. In Proceedings of the 10th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 7–9 April 2015; pp. 1–4. [Google Scholar]
- Syed, Z.; Padia, A.; Finin, T.; Mathews, L.; Joshi, A. UCO: A unified cybersecurity ontology. In Proceedings of the Workshops at the Thirtieth AAAI Conference on Artificial Intelligence, Phoenix, AZ, USA, 12–13 February 2016. [Google Scholar]
- Undercofer, J.; Joshi, A.; Finin, T.; Pinkston, J. A target-centric ontology for intrusion detection. In Workshop on Ontologies in Distributed Systems, Proceedings of the 18th International Joint Conference on Artificial Intelligence, Acapulco, Mexico, 9–15 August 2003; Morgan Kaufmann Pub: Burlington, MA, USA, 2003. [Google Scholar]
- Ding, Y.; Wu, R.; Zhang, X. Ontology-based knowledge representation for malware individuals and families. Comput. Secur. 2019, 87, 101574. [Google Scholar] [CrossRef]
- Grégio, A.; Bonacin, R.; Nabuco, O.; Afonso, V.M.; De Geus, P.L.; Jino, M. Ontology for malware behavior: A core model proposal. In Proceedings of the 2014 IEEE 23rd International WETICE Conference, Parma, Italy, 23–25 June 2014; pp. 453–458. [Google Scholar]
- Gao, J.; Wang, A. Research on ontology-based network threat intelligence analysis technology. Comput. Eng. Appl. 2020, 56, 112–117. [Google Scholar]
- Simmonds, A.; Sandilands, P.; Ekert, L.V. An ontology for network security attacks. In Proceedings of the Asian Applied Computing Conference, Kathmandu, Nepal, 29–31 October 2004; Springer: New York, NY, USA, 2004; pp. 317–323. [Google Scholar]
- Shuo, W.; Jianhua, W.; Guangming, T.; Qingqi, P.; Yuchen, Z.; Xiaohu, L. Intelligent and efficient method for optimal penetration path generation. J. Comput. Res. Dev. 2019, 56, 929. [Google Scholar]
- Wang, J.A.; Wang, H.; Guo, M.; Zhou, L.; Camargo, J. Ranking attacks based on vulnerability analysis. In Proceedings of the 2010 43rd Hawaii International Conference on System Sciences, Honolulu, HI, USA, 5–8 January 2010; pp. 1–10. [Google Scholar]
- Gao, J. Research on Ontology Model and Its Application in Information Security Evaluation. Ph.D. Thesis, Shanghai Jiao Tong University, Shanghai, China, 2015. [Google Scholar]
- Qin, S.; Chow, K. Automatic analysis and reasoning based on vulnerability knowledge graph. In Cyberspace Data and Intelligence, and Cyber-Living, Syndrome, and Health; Springer: New York, NY, USA, 2019; pp. 3–19. [Google Scholar]
- Hooi, E.K.J.; Zainal, A.; Maarof, M.A.; Kassim, M.N. TAGraph: Knowledge graph of threat actor. In Proceedings of the 2019 IEEE International Conference on Cybersecurity (ICoCSec), Negeri Sembilan, Malaysia, 25–26 September 2019; pp. 76–80. [Google Scholar]
- Sanagavarapu, L.M.; Iyer, V.; Reddy, Y.R. A deep learning approach for ontology enrichment from unstructured text. In Cybersecurity and High-Performance Computing Environments: Integrated Innovations, Practices, and Applications; CRC Press: Abingdon, UK, 2022; p. 261. [Google Scholar]
- Li, J.; Sun, A.; Han, J.; Li, C. A survey on deep learning for named entity recognition. IEEE Trans. Knowl. Data Eng. 2020, 34, 50–70. [Google Scholar] [CrossRef] [Green Version]
- Liao, X.; Yuan, K.; Wang, X.; Li, Z.; Xing, L.; Beyah, R. Acing the ioc game: Toward automatic discovery and analysis of open-source cyber threat intelligence. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 755–766. [Google Scholar]
- Jones, C.L.; Bridges, R.A.; Huffer, K.M.; Goodall, J.R. Towards a relation extraction framework for cyber-security concepts. In Proceedings of the 10th Annual Cyber and Information Security Research Conference, Ridge, TN, USA, 7–9 April 2015; pp. 1–4. [Google Scholar]
- Meng, L.; Yanling, L.; Min, L. Review of transfer learning for named entity recognition. J. Front. Comput. Sci. Technol. 2021, 15, 206. [Google Scholar]
- Georgescu, T.M. Natural language processing model for automatic analysis of cybersecurity-related documents. Symmetry 2020, 12, 354. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, Y.; Ren, X.; Zhang, Y.; Zitnik, M.; Shang, J.; Langlotz, C.; Han, J. Cross-type biomedical named entity recognition with deep multi-task learning. Bioinformatics 2019, 35, 1745–1752. [Google Scholar] [CrossRef] [Green Version]
- Huang, L.; Ji, H.; May, J. Cross-lingual multi-level adversarial transfer to enhance low-resource name tagging. In Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies, Minneapolis, MN, USA, 2–7 June 2019; Volume 1 (Long and Short Papers), pp. 3823–3833. [Google Scholar]
- Yang, Y.; Chen, W.; Li, Z.; He, Z.; Zhang, M. Distantly supervised NER with partial annotation learning and reinforcement learning. In Proceedings of the 27th International Conference on Computational Linguistics, Santa Fe, NM, USA, 20–26 August 2018; pp. 2159–2169. [Google Scholar]
- Li, J.; Ye, D.; Shang, S. Adversarial transfer for named entity boundary detection with pointer networks. In Proceedings of the International Joint Conference on Artificial Intelligence (IJCAI), Macao, China, 10–16 August 2019; pp. 5053–5059. [Google Scholar]
- Zhang, Q.; Fu, J.; Liu, X.; Huang, X. Adaptive co-attention network for named entity recognition in tweets. In Proceedings of the Thirty-Second AAAI Conference on Artificial Intelligence, New Orleans, LA, USA, 2–7 February 2018. [Google Scholar]
- Zeng, D.; Liu, K.; Lai, S.; Zhou, G.; Zhao, J. Relation classification via convolutional deep neural network. In Proceedings of the COLING 2014, the 25th International Conference on Computational Linguistics: Technical Papers, Dublin, Ireland, 23–29 August 2014; pp. 2335–2344. [Google Scholar]
- Zhang, D.; Wang, D. Relation classification via recurrent neural network. arXiv 2015, arXiv:1508.01006. [Google Scholar]
- Peng, Z.; Wei, S.; Tian, J.; Qi, Z.; Bo, X. Attention-based bidirectional long short-term memory networks for relation classification. In Proceedings of the 54th Annual Meeting of the Association for Computational Linguistics (Volume 2: Short Papers), Berlin, Germany, 7–12 August 2016; pp. 207–212. [Google Scholar]
- Vashishth, S.; Joshi, R.; Prayaga, S.S.; Bhattacharyya, C.; Talukdar, P. RESIDE: Improving distantly-supervised neural relation extraction using side information. arXiv 2018, arXiv:1812.04361. [Google Scholar]
- Zeng, D.; Kang, L.; Chen, Y.; Zhao, J. Distant supervision for relation extraction via piecewise convolutional neural networks. In Proceedings of the Conference on Empirical Methods in Natural Language Processing, Lisbon, Portugal, 17–21 September 2015; pp. 1753–1762. [Google Scholar]
- Lin, Y.; Shen, S.; Liu, Z.; Luan, H.; Sun, M. Neural relation extraction with selective attention over instances. In Proceedings of the 54th Annual Meeting of the Association for Computational Linguistics (Volume 1: Long Papers), Berlin, Germany, 7–12 August 2016; pp. 2124–2133. [Google Scholar]
- Fu, T.J.; Ma, W.Y. GraphRel: Modeling text as relational graphs for joint entity and relation extraction. In Proceedings of the ACL 2019—57th Annual Meeting of the Association for Computational Linguistics, Florence, Italy, 28 July–2 August 2019; pp. 1409–1418. [Google Scholar]
- Guo, Y.; Liu, Z.; Huang, C.; Liu, J.; Jing, W.; Wang, Z.; Wang, Y. CyberRel: Joint entity and relation extraction for cybersecurity concepts. In Proceedings of the International Conference on Information and Communications Security, Chongqing, China, 19–21 November 2021; pp. 447–463. [Google Scholar]
- Li, T.; Guo, Y.; Ju, A. Knowledge triple extraction in cybersecurity with adversarial active learning. J. Commun. 2020, 41, 80–91. [Google Scholar]
- Walker, C.; Strassel, S.; Medero, J.; Maeda, K. ACE 2005 multilingual training corpus. Prog. Theor. Phys. Suppl. 2006, 110, 261–276. [Google Scholar]
- Mitamura, T.; Liu, Z.; Hovy, E. Overview of TAC-KBP 2015 event nugget track. In Proceedings of the Text Analysis Conference, Gaithersburg, MD, USA, 16–17 November 2015. [Google Scholar]
- Sevgili, O.; Shelmanov, A.; Arkhipov, M.; Panchenko, A.; Biemann, C. Neural entity linking: A survey of models based on deep learning. arXiv 2020, arXiv:2006.00575. [Google Scholar] [CrossRef]
- Chen, X.; Jia, S.; Xiang, Y. A review: Knowledge reasoning over knowledge graph. Expert Syst. Appl. 2020, 141, 112948. [Google Scholar] [CrossRef]
- Li, X.; Lian, Y.; Zhang, H.; Huang, K. Key technologies of cyber security knowledge graph. Front. Data Domputing 2021, 3, 9–18. [Google Scholar]
- MITRE. 2022. Available online: https://www.mitre.org/ (accessed on 3 April 2022).
- NVD National Vulnerability Database. 2022. Available online: https://nvd.nist.gov/ (accessed on 3 April 2022).
- MITRE. Common Attack Pattern Enumeration and Classification. 2022. Available online: https://capec.mitre.org/ (accessed on 3 April 2022).
- Nan, S. CWE Knowledge Graph Based Twitter Data Analysis for Cybersecurity. 2019. Available online: https://github.com/nansunsun/CWE-Knowledge-Graph-Based-Twitter-Data-Analysis-for-Cybersecurity (accessed on 4 April 2022).
- Cheng, X. Visualization Web Page of Vulnerability Knowledge Graph. 2021. Available online: https://cinnqi.github.io/Neo4j-D3-VKG/ (accessed on 4 April 2022).
- Sarhan, I.; Spruit, M. Open-CyKG. 2021. Available online: https://github.com/IS5882/Open-CyKG (accessed on 4 April 2022).
- Rastogi, N.; Dutta, S.; Christian, R.; Gridley, J.; Zaki, M.; Gittens, A.; Aggarwal, C. Predicting malware threat intelligence using KGs. arXiv 2021, arXiv:2102.05571. [Google Scholar]
- SEPSES. The SEPSES Cyber-KB. 2019. Available online: https://sepses.ifs.tuwien.ac.at/dumps/version/102019/ (accessed on 3 April 2022).
- Kiesling, E.; Ekelhart, A.; Kurniawan, K.; Ekaputra, F. The SEPSES knowledge graph: An integrated resource for cybersecurity. In Proceedings of the International Semantic Web Conference, Auckland, New Zealand, 26–30 October 2019; Springer: New York, NY, USA, 2019; pp. 198–214. [Google Scholar]
- Di, W. CyberSecurity Knowledge Graph. 2020. Available online: https://github.com/HoloLen/CyberSecurity_Knowledge_graph (accessed on 3 April 2022).
- Qi, Y. Knowledge Graph for Vulnerabilities of Industrial Control Systems (ICSKG). 2020. Available online: https://github.com/QYue/Athena-ICSKG-master (accessed on 4 April 2022).
- Sarhan, I.; Spruit, M. Open-cykg: An open cyber threat intelligence knowledge graph. Knowl. Based Syst. 2021, 233, 107524. [Google Scholar] [CrossRef]
- Rastogi, N.; Dutta, S.; Zaki, M.; Gittens, A.; Aggarwal, C. Open-CyKG. 2021. Available online: https://github.com/liujie40/MalKG-1 (accessed on 4 April 2022).
- Lal, R. Information Extraction of Security Related Entities and Concepts from Unstructured Text. 2013. Available online: https://ebiquity.umbc.edu/paper/html/id/626/Information-Extraction-of-Security-related-entities-and-concepts-from-unstructured-text- (accessed on 4 April 2022).
- Bridges, R.A.; Jones, C.L.; Iannacone, M.D.; Testa, K.M.; Goodall, J.R. Automatic labeling for entity extraction in cyber security. arXiv 2013, arXiv:1308.4941. [Google Scholar]
- Lim, S.K.; Muis, A.O.; Lu, W.; Ong, C.H. Malwaretextdb: A database for annotated malware articles. In Proceedings of the 55th Annual Meeting of the Association for Computational Linguistics (Volume 1: Long Papers), Vancouver, BC, Canada, 30 July–4 August 2017; pp. 1557–1567. [Google Scholar]
- Kim, G.; Lee, C.; Jo, J.; Lim, H. Automatic extraction of named entities of cyber threats using a deep Bi-LSTM-CRF network. Int. J. Mach. Learn. Cybern. 2020, 11, 2341–2355. [Google Scholar] [CrossRef]
- Runzi, Z.; Wenmao, L. An intelligent security operation technology system framework AISecOps. Front. Data Domputing 2021, 3, 32–47. [Google Scholar]
- Zenglin, X.; Yongpan, S.; Lirong, H.; Yafang, W. Review on knowledge graph techniques. J. Univ. Electron. Sci. Technol. China 2016, 45, 589–606. [Google Scholar]
- Noel, S.; Harley, E.; Tam, K.H.; Limiero, M.; Share, M. CyGraph: Graph-based analytics and visualization for cybersecurity. In Handbook of Statistics; Elsevier: Amsterdam, The Netherlands, 2016; Volume 35, pp. 117–167. [Google Scholar]
- Chen, X. Design and Implementation of Network Attack Situation Detection System Based on Knowledge Graph. Master’s Thesis, Beijing University of Posts and Telecommunications, Beijing, China, 2020. [Google Scholar]
- Wang, Y. Research and Implementation of NSSA Technology Based on Knowledge Graph. Master’s Thesis, University of Electronic Science and Technology of China, Chengdu, China, 2020. [Google Scholar]
- Wang, B.; Wu, L.; Hu, X.; He, Y. Satellite cyber situational understanding based on knowledge reasoning. Syst. Eng. Electron. 2022, 44, 1562–1571. [Google Scholar]
- Wu, S.; Zhang, Y.; Cao, W. Network security assessment using a semantic reasoning and graph based approach. Comput. Electr. Eng. 2017, 64, 96–109. [Google Scholar] [CrossRef]
- Philpot, M. Cyber Intelligence Ontology. 2015. Available online: https://github.com/daedafusion/cyber-ontology (accessed on 4 April 2022).
- SPARQL. Virtuoso SPARQL Query Editor. 2022. Available online: https://w3id.org/sepses/sparql (accessed on 4 April 2022).
- Pang, T.; Song, Y.; Shen, Q. Research on security threat assessment for power iot terminal based on knowledge graph. In Proceedings of the 2021 IEEE 5th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Xi’an, China, 15–17 October 2021; Volume 5, pp. 1717–1721. [Google Scholar]
- FireEye. Common Vulnerability Scoring System. 2018. Available online: https://www.fireeye.com/content/dam/collateral/en/mtrends-2018.pdf (accessed on 4 April 2022).
- Narayanan, S.N.; Ganesan, A.; Joshi, K.; Oates, T.; Joshi, A.; Finin, T. Early detection of cybersecurity threats using collaborative cognition. In Proceedings of the 2018 IEEE 4th International Conference on Collaboration and Internet Computing (CIC), Philadelphia, PA, USA, 18–20 October 2018; pp. 354–363. [Google Scholar]
- Sun, C.; Hu, H.; Yang, Y.; Zhang, H. Prediction method of 0 day attack path based on cyber defense knowledge graph. Chin. J. Netw. Inf. Secur. 2022, 8, 151–166. [Google Scholar]
- Gao, P.; Shao, F.; Liu, X.; Xiao, X.; Qin, Z.; Xu, F.; Mittal, P.; Kulkarni, S.R.; Song, D. Enabling efficient cyber threat hunting with cyber threat intelligence. In Proceedings of the 2021 IEEE 37th International Conference on Data Engineering (ICDE), Chania, Greece, 19–22 April 2021; pp. 193–204. [Google Scholar]
- Chen, J. DDoS attack detection based on knowledge graph. J. Inf. Secur. Res. 2020, 6, 91–96. [Google Scholar]
- Feiyang, L.; Kun, L.; Fei, S.; Chunhua, Z. Distributed DDoS attacks malicious behavior knowledge base construction. Telecommun. Sci. 2021, 37, 17–32. [Google Scholar]
- Garrido, J.S.; Dold, D.; Frank, J. Machine learning on knowledge graphs for context-aware security monitoring. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; pp. 55–60. [Google Scholar]
- SENKI. Open Source Threat Intelligence Feeds. 2020. Available online: https://www.senki.org/operators-security-toolkit/open-source-threat-intelligence-feeds/ (accessed on 4 April 2022).
- Jian, S.; Lu, Z.; Du, D.; Jiang, B.; Li, B. Overview of network intrusion detection technology. J. Inf. Secur. 2020, 5, 96–122. [Google Scholar]
- Kovalenko, O.; Wimmer, M.; Sabou, M.; Lüder, A.; Ekaputra, F.J.; Biffl, S. Modeling automationml: Semantic web technologies vs. In model-driven engineering. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–4. [Google Scholar]
- Noel, S.; Harley, E.; Tam, K.H.; Gyor, G. Big-Data Architecture for Cyber Attack Graphs Representing Security Relationships in Nosql Graph Databases. 2015. Available online: https://csis.gmu.edu/noel/pubs/2015_IEEE_HST.pdf (accessed on 4 April 2022).
- Ye, Z.; Guo, Y.; Li, T.; Ju, A.K. Extended attack graph generation method based on knowledge graph. Comput. Sci. 2019, 46, 165–173. [Google Scholar]
- Chen, Z.; Dong, N.; Zhong, S.; Hou, B.; Chang, J. Research on the power network security vulnerability expansion attack graph based on knowledge map. Inf. Technol. 2022, 46, 30–35. [Google Scholar]
- Zhu, Z.; Jiang, R.; Jia, Y.; Xu, J.; Li, A. Cyber security knowledge graph based cyber attack attribution framework for space-ground integration information network. In Proceedings of the 2018 IEEE 18th International Conference on Communication Technology (ICCT), Chongqing, China, 8–11 October 2018; pp. 870–874. [Google Scholar]
- Xue, J. Attack Attribution: Provenance Graph Construction Technology Based on Causation. 2020. Available online: http://blog.nsfocus.net/attack-investigation-0907/ (accessed on 4 April 2022).
- Han, Z.; Li, X.; Liu, H.; Xing, Z.; Feng, Z. Deepweak: Reasoning common software weaknesses via knowledge graph embedding. In Proceedings of the 2018 IEEE 25th International Conference on Software Analysis, Evolution and Reengineering (SANER), Campobasso, Italy, 20–23 March 2018; pp. 456–466. [Google Scholar]
- Datta, P.; Lodinger, N.; Namin, A.S.; Jones, K.S. Cyber-attack consequence prediction. arXiv 2020, arXiv:2012.00648. [Google Scholar]
- Vukotic, A.; Watt, N.; Abedrabbo, T.; Fox, D.; Partner, J. Neo4j in Action; Manning Publications Co.: Shelter Island, NY, USA, 2015; Volume 22. [Google Scholar]
- Ruohonen, J. A look at the time delays in cvss vulnerability scoring. Appl. Comput. Inform. 2017, 15, 129–135. [Google Scholar] [CrossRef]
- Mitre. Common Weakness Enumeration. 2022. Available online: https://cwe.mitre.org/ (accessed on 4 April 2022).
- Qi, Y.; Jiang, R.; Jia, Y.; Li, A. Attack analysis framework for cyber-attack and defense test platform. Electronics 2020, 9, 1413. [Google Scholar] [CrossRef]
- Alsaheel, A.; Nan, Y.; Ma, S.; Yu, L.; Walkup, G.; Celik, Z.B.; Zhang, X.; Xu, D. ATLAS: A sequence-based learning approach for attack investigation. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Vancouver, BC, Canada, 11–13 August 2021; pp. 3005–3022. [Google Scholar]
- Wang, W.; Zhou, H.; Li, K.; Tu, Z.; Liu, F. Cyber-attack behavior knowledge graph based on CAPEC and CWE towards 6G. In Proceedings of the International Symposium on Mobile Internet Security, Jeju Island, Korea, 7–9 October 2021; Springer: New York, NY, USA, 2021; pp. 352–364. [Google Scholar]
- NEFOCUS. Security Knowledge Graph Technology White Paper. 2022. Available online: https://www.nsfocus.com.cn/html/2022/92_0105/166.html (accessed on 4 April 2022).
- Xue, J. Attack Reasoning: Dilemma of Application of Security Knowledge Graph. 2020. Available online: http://blog.nsfocus.net/stucco-cyber/ (accessed on 4 April 2022).
- Wang, W.; Jiang, R.; Jia, Y.; Li, A.; Chen, Y. KGBIAC: Knowledge graph based intelligent alert correlation framework. In Proceedings of the International Symposium on Cyberspace Safety and Security, Xi’an, China, 23–25 October 2017; Springer: New York, NY, USA, 2017; pp. 523–530. [Google Scholar]
- Wang, W. Research for Algorithm of Distributed Security Event Correlation Based on Knowledge Graph. Master’s Thesis, National University of Defense Technology, Changsha, China, 2018. [Google Scholar]
- Qi, Y.; Jiang, R.; Jia, Y.; Li, R.; Li, A. Association analysis algorithm based on knowledge graph for space-ground integrated network. In Proceedings of the 2018 IEEE 18th International Conference on Communication Technology (ICCT), Chongqing, China, 8–11 October 2018; pp. 222–226. [Google Scholar]
- Ekelhart, A.; Ekaputra, F.J.; Kiesling, E. Automated Knowledge Graph Construction from Raw Log Data. 2020. Available online: http://ceur-ws.org/Vol-2721/paper552.pdf (accessed on 4 April 2022).
- Ou, Y.; Zhou, T.; Zhu, J. Recommendation of cyber attack method based on knowledge graph. In Proceedings of the 2020 IEEE International Conference on Computer Engineering and Intelligent Control (ICCEIC), Chongqing, China, 6–8 November 2020; pp. 60–65. [Google Scholar]
- Chen, X.; Shen, W.; Yang, G. Automatic generation of attack strategy for multiple vulnerabilities based on domain knowledge graph. In Proceedings of the IECON 2021–47th IEEE Annual Conference of the IEEE Industrial Electronics Society, Toronto, ON, Canada, 13–16 October 2021; pp. 1–6. [Google Scholar]
- Vassilev, V.; Sowinski-Mydlarz, V.; Gasiorowski, P.; Ouazzane, K.; Phipps, A. Intelligence graphs for threat intelligence and security policy validation of cyber systems. In Proceedings of the International Conference on Artificial Intelligence and Applications, Suzhou, China, 15–17 October 2021; Springer: New York, NY, USA, 2021; pp. 125–139. [Google Scholar]
- Syed, R. Cybersecurity vulnerability management: A conceptual ontology and cyber intelligence alert system. Inf. Manag. 2020, 57, 103334. [Google Scholar] [CrossRef]
- Tao, Y.; Jia, X.; Wu, Y. A research method of industrial Internet security vulnerabilities based on knowledge map. J. Inf. Technol. Netw. Secur. 2020, 39, 6–13. [Google Scholar]
- Wang, L. Research on Software Security Vulnerability Mining Technology Based on Knowledge Graph. Master’s Thesis, Xi’an Technological University, Xi’an, China, 2021. [Google Scholar]
- Wang, L. Research on Construction of Vulnerability Knowledge Graph and Vulnerability Situation Awareness. Master’s Thesis, University of Chinese Academy of Sciences, Beijing, China, 2020. [Google Scholar]
- Najafi, P.; Mühle, A.; Pünter, W.; Cheng, F.; Meinel, C. MalRank: A measure of maliciousness in SIEM-based knowledge graphs. In Proceedings of the 35th Annual Computer Security Applications Conference, San Juan, PR, USA, 9–13 December 2019; pp. 417–429. [Google Scholar]
- Dutta, S.; Rastogi, N.; Yee, D.; Gu, C.; Ma, Q. Malware knowledge graph generation. arXiv 2021, arXiv:2102.05583. [Google Scholar]
- Wang, Z.; Sun, L.; Zhu, H. Defining social engineering in cybersecurity. IEEE Access 2020, 8, 85094–85115. [Google Scholar] [CrossRef]
- Wang, Z.; Zhu, H.; Liu, P.; Sun, L. Social engineering in cybersecurity: A domain ontology and knowledge graph application examples. Cybersecurity 2021, 4, 1–21. [Google Scholar] [CrossRef]
- Mitra, S.; Piplai, A.; Mittal, S.; Joshi, A. Combating fake cyber threat intelligence using provenance in cybersecurity knowledge graphs. In Proceedings of the 2021 IEEE International Conference on Big Data (Big Data), Orlando, FL, USA, 15–18 December 2021; pp. 3316–3323. [Google Scholar]
- Xiao, H.; Xing, Z.; Li, X.; Guo, H. Embedding and predicting software security entity relationships: A knowledge graph based approach. In Proceedings of the International Conference on Neural Information Processing, Sydney, Australia, 12–15 December 2019; Springer: New York, NY, USA, 2019; pp. 50–63. [Google Scholar]
- Shang, H.; Jiang, R.; Li, A.; Wang, W. A framework to construct knowledge base for cyber security. In Proceedings of the 2017 IEEE Second International Conference on Data Science in Cyberspace (DSC), Shenzhen, China, 26–29 June 2017; pp. 242–248. [Google Scholar]
- Liu, Q.; Li, Y.; Duan, H.; Liu, Y.; Qin, Z. Knowledge graph construction techniques. J. Comput. Res. Dev. 2016, 53, 582. [Google Scholar]




| Name and Year | Purpose | Data sources | Ref. |
|---|---|---|---|
| SEPSES CKB [74], 2019 | SEPSES CSKG with detailed instance data | CVE, CWE, CAPEC, CPE, CVSS. | [75] |
| CWE-KG [70], 2019 | A CWE KG supporting Twitter data analysis | CWE, CAPEC, Twitter data | - |
| CSKG [76], 2020 | Cybersecurity KG | CVE, CWE, CAPEC | - |
| ICSKG [77], 2020 | KG for vulnerabilities of industrial control systems | CVE, CWE, CPE, CERT | - |
| Vulnerability KG [71], 2021 | Visualization web page of vulnerability KG | CVE, CWE | - |
| Open-CyKG [72], 2021 | An open cyber threat intelligence KG | APT reports, CTI reports | [78] |
| MalKG [79], 2021 | Open-source KG for malware threat intelligence | CVE, Malware reports | [73] |
| Dataset and Year | Task | Entity Types | Data Sources | |
|---|---|---|---|---|
| NER | RE | |||
| Lal [80], 2013 | ✓ | - | Software, Network_terms, Attack, File_name, Hardware, Other_technical_terms, NER_modifier | Blogs, Official Security, Bulletins, CVE |
| Bridges et al. [81], 2013 | ✓ | - | Vendor, Product, Version, Language, vulnerability, and vulnerability relevant term | NVD, OSVBD, Exploit DB |
| Lim et al. [82], 2017 | ✓ | - | Action, Subject, Object, Modifier | APT reports |
| Kim et al. [83], 2020 | ✓ | - | Malware, IP, Domain/URL, Hash, their categories | CTI reports |
| Rastogi et al. [73], 2021 | ✓ | ✓ | Malware, MalwareFamily, Attacker, AttackerGroup, ExploitTarget, Indicator, etc. | CVE, Malware reports |
| Ref. and Year | Purpose | Method Description |
|---|---|---|
| [90], 2017 | Generating attack graphs; Identifying the possible attacks; Assessing network security | Providing a novel cybersecurity ontology Providing a graph-based methodology for the purposes |
| [75], 2019 | Estimating the possible effect of new vulnerability | Constructing a CSKG SPARQL query method |
| [93], 2021 | Power IOT terminals’ security assessment | Building a CSKG with three dimensions Correlation analysis of monitoring information |
| Tasks | Ref. and Year | Purpose | Method Description |
|---|---|---|---|
| Attack prediction | [95], 2018 | Identify cyber-attacks early | SWRL method The UCO ontology extension Combining multi-information into KG Reasoning model |
| [96], 2022 | Discover the possible 0-day attack | Building a cyber defense KG with 3 aspects Path ranking algorithm | |
| Threat hunting | [97], 2021 | Log-based cyber threat hunting with external OSCTI knowledge | Pipeline IE model for building threat behavior KG A querying method based on system auditing A threat behavior query language (TBQL) A query synthesis technique |
| Intrusion detection | [75], 2019 | Estimating the possible effect of new vulnerability | A SPARQL query method Link NIDS alerts to SEPSES KG |
| [98], 2020 | Detecting the DDoS attacks TCP traffic | Expressing the connection between 2 hosts Calculating the 1-way transmission propensity value Finding the host of the initiator of a DDoS attack | |
| [99], 2021 | Detecting malicious traffic generated by DDoS attacks | DDoS attack malicious behavior KG creation Behavior reasoning based on the KG | |
| [100], 2021 | Identifying unusual behaviors in industrial automation systems | Using a readily available ontology to build a KG Combining 3 major sources of knowledge into KG Machine learning abnormal detection based on KG |
| Tasks | Ref. and Year | Purpose | Method Description |
|---|---|---|---|
| Attack path analysis | [104], 2015 | Predicting possible attack paths | A unique model of attack graph Predicting possible attack paths based on events Correlating attack events with attack paths |
| [105], 2019 | Generating an attack path and improving the assessment of vulnerability | Building cyber-attack KG with 4 types of entities Determining penetration paths with graph method | |
| [37], 2019 | The penetration path generation | Providing a two-layer threat penetration graph Description of attack-related resources of hosts Generation of the penetration path | |
| [106], 2022 | Obtaining the maximum probability vulnerability path | Providing an expansion attack graph Obtaining maximum probability vulnerability path Providing the success rate of attacking and the loss | |
| [96], 2022 | Representing and generating 0-day attack paths | Approach of link prediction Path ranking algorithm | |
| Attack attribution | [107], 2018 | Attack attribution | CSKG of space-ground information network An automated cyberattack attributing framework Attack attribution by querying the CSKG |
| [108], 2020 | Attack attribution based on provenance graph construction | Provenance graph construction from 3 dimensions Causal analysis based on provenance graph Extending the graph from single host to multi-host | |
| Consequence prediction | [109], 2018 | Predicting the links, CWE triples and threat consequences based on CWE KG | Vector embedding generation Building a KG-based CWE data 3 different reasoning methods based on CSKG |
| [110], 2020 | Attack consequence prediction | Building machine learning classification models Providing dataset includes 93 different attacks |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, K.; Wang, F.; Ding, Z.; Liang, S.; Yu, Z.; Zhou, Y. Recent Progress of Using Knowledge Graph for Cybersecurity. Electronics 2022, 11, 2287. https://doi.org/10.3390/electronics11152287
Liu K, Wang F, Ding Z, Liang S, Yu Z, Zhou Y. Recent Progress of Using Knowledge Graph for Cybersecurity. Electronics. 2022; 11(15):2287. https://doi.org/10.3390/electronics11152287
Chicago/Turabian StyleLiu, Kai, Fei Wang, Zhaoyun Ding, Sheng Liang, Zhengfei Yu, and Yun Zhou. 2022. "Recent Progress of Using Knowledge Graph for Cybersecurity" Electronics 11, no. 15: 2287. https://doi.org/10.3390/electronics11152287






