Exposure of Botnets in Cloud Environment by Expending Trust Model with CANFES Classification Approach
Abstract
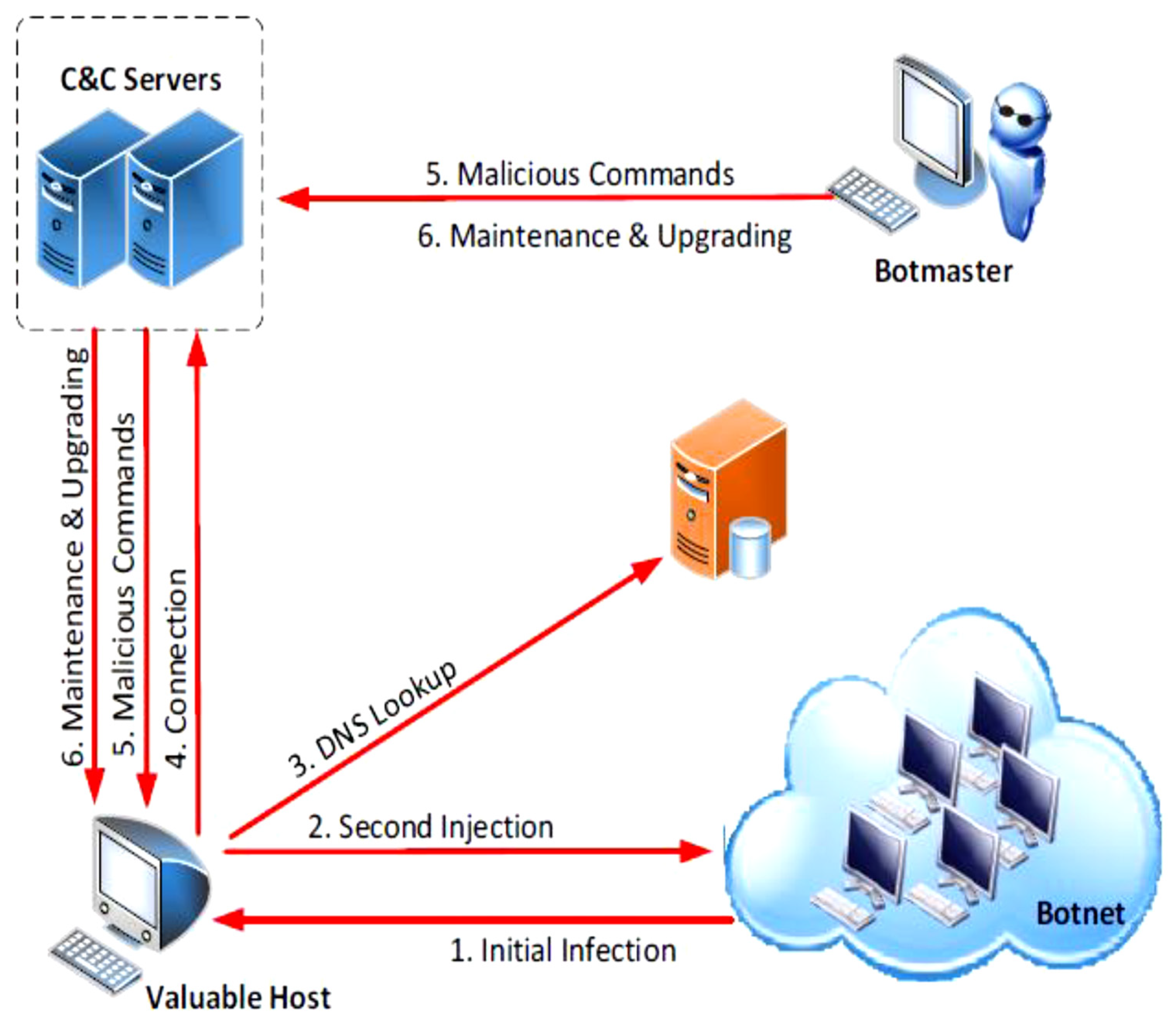
:1. Introduction
2. Related Work
2.1. Honeynets & Honeypots Based Detection System
2.2. Intrusion Detection System (IDS)
2.2.1. Signature Based Detection
2.2.2. Anomaly Based Detection
- Most of the conventional methods consume high latency to detect bots in cloud environment.
- Low detection rate for bots’ detection when the number of bots increases.
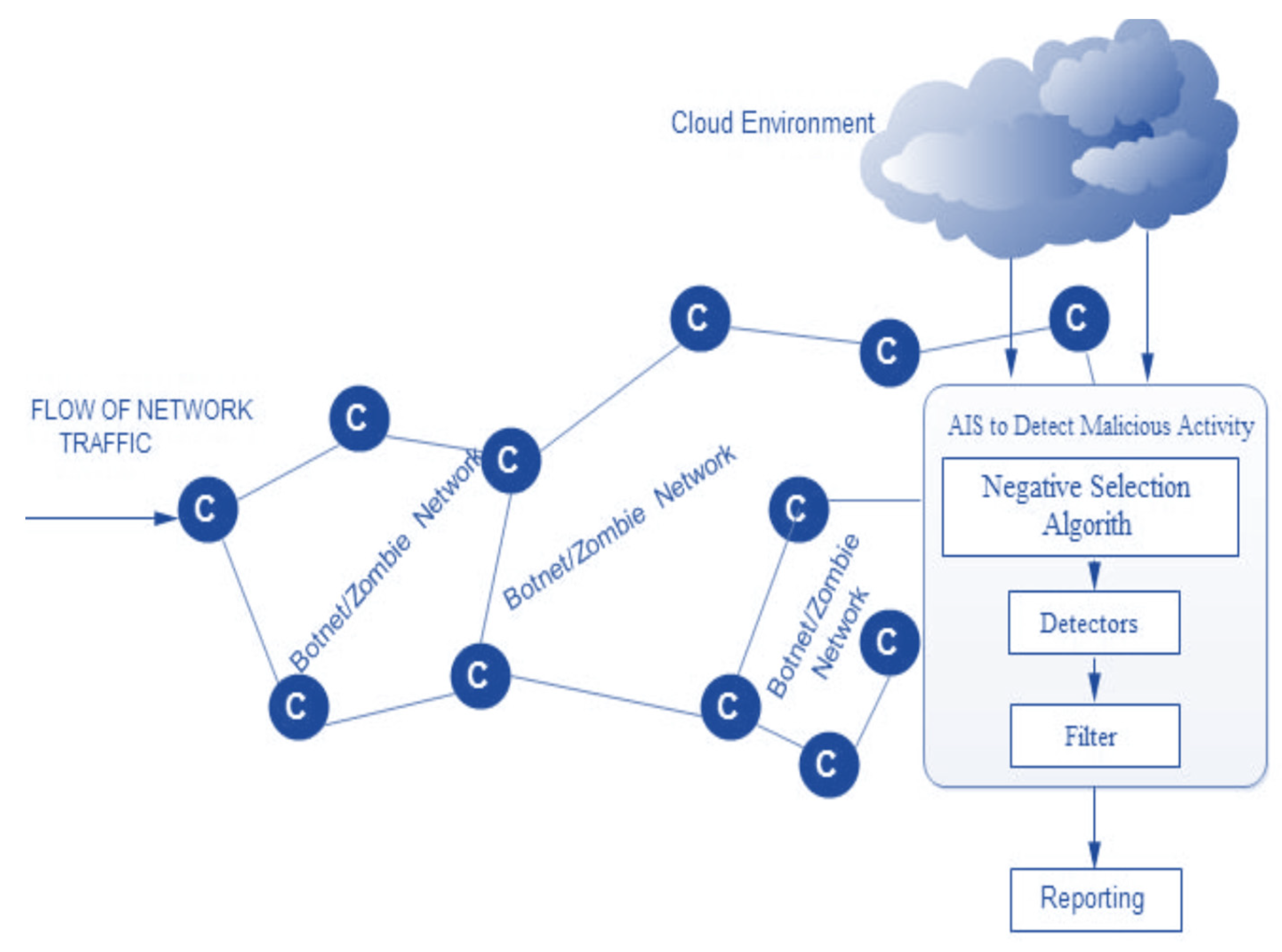
3. Proposed Method
- Port Access Verification
- Back-off trust features
- Classifications
3.1. Heuristic Factorizing Algorithm
3.2. Back-Off Trust Features
3.3. Classification
4. Result Discussion on Performance Analysis
4.1. Latency
4.2. Malicious Packet Detection Rate
4.3. Packet Delivery Ratio (PDR)
4.4. Energy Availability
4.5. Precision
5. Conclusions
- The efficiency of the proposed bot detection methodology in the cloud environment will be improved by detecting and mitigating dead and selfish nodes.
- The security of the botnet detection system will be improved by implementing various cryptographic techniques at both client and server end.
- The bots and bot master detected ratio will be increased by implementing optimization techniques such as Genetic Algorithm (GA) and Particle Swarm Optimization (PSO) technique. These optimization techniques select the optimum feature set from the set of extracted features which increases the detection ratio of the bots and bot master in cloud environment.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Feily, M.; Alireza, S.; Sureswaran, R. A Survey of Botnet and Botnet Detection. In Proceedings of the Third International Conference on Emerging Security Information, Systems and Technologies, Athens, Glyfada, 18–23 June 2009. [Google Scholar] [CrossRef]
- Sgbau, A. A Review-Botnet Detection and Suppression in Clouds. J. Inf. Eng. Appl. 2013, 3, 1686–1691. [Google Scholar]
- Iftikhar, U.; Asrar, K.; Waqas, M.; Abbas, S. BOTNETs: A Network Security Issue. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 432–436. [Google Scholar] [CrossRef]
- Jiang, Y.; Huang, J.; Ding, J.; Liu, Y. Method of fault detection in cloud computing systems. Int. J. Grid Distrib. Comput. 2014, 7, 205–212. [Google Scholar] [CrossRef]
- Nagendra Prabhu, S.; Shanthi, D. Examining zeus botnet by adopting key extraction and malicious traffic detection framework using DNS. Int. J. Appl. Eng. Res. 2015, 10, 6987–7007. [Google Scholar]
- Tan, K.M.C.; Killourhy, K.S.; Maxion, R.A. Undermining an Anomaly-Based Intrusion Detection System Using Common Exploits. In Recent Advances in Intrusion Detection; RAID 2002. Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2000; Volume 2516, pp. 54–73. [Google Scholar]
- Liu, C.P.; Lin, I. A Survey of Botnet Architecture and Botnet Detection Techniques. Int. J. Netw. Secur. 2014, 16, 81–89. [Google Scholar]
- Alshamkhany, M.; Alshamkhany, W.; Mansour, M.; Khan, M.; Dhou, S.; Aloul, F. Botnet Attack Detection Using Machine Learning. In Proceedings of the 14th IEEE International Conference on Innovations in Information Technology (IIT), Al Ain, United Arab Emirates, 17–18 November 2020. [Google Scholar] [CrossRef]
- Elhoseny, M.; Thilakarathne, N.N.; Alghamdi, M.I.; Mahendran, R.K.; Gardezi, A.A.; Weerasinghe, H.; Welhenge, A. Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions. Sustainability 2021, 13, 11645. [Google Scholar] [CrossRef]
- Han, Z.; Chen, H.; Liang, Y. A distributed botnets suppression system. In Proceedings of the IEEE ICDCS workshop on the First International Workshop on Network Forensics, Security and Privacy (NFSP), Macau, China, 18–21 June 2012; pp. 634–639. [Google Scholar]
- Dilara, A.; Muttukrishnan, R.; Nikos, K.; Zarpelão, B. Modelling the Spread of Botnet Malware in IoT-Based Wireless Sensor Networks. Hindawi Secur. Commun. Netw. 2019, 2019, 3745619. [Google Scholar] [CrossRef]
- Subramaniam, T.K.; Deepa, B. A Multi-Level Security for Preventing Attacks in Cloud Enviroments. Int. J. Mach. Learn. Appl. 2016, 3, 19–31. [Google Scholar]
- Mahendran, R.K.; Velusamy, P. A secure fuzzy extractor based biometric key authentication scheme for Body Sensor Network in internet of medical things. Comput. Commun. 2020, 153, 545–552. [Google Scholar] [CrossRef]
- Truong, D.T.; Cheng, G.; Jakalan, A.; Guo, X.J.; Zhou, A.P. Detecting DGA-Based Botnet with DNS Traffic Analysis in Monitored Network. J. Internet Technol. 2016, 17, 217–230. [Google Scholar]
- Al-Jarrah, O.Y.; Alhussein, O.; Yoo, P.D.; Muhaidat, S.; Taha, K.; Kim, K. Data Randomization and Cluster-Based Partitioning for Botnet Intrusion Detection. IEEE Trans. Cybern. 2016, 46, 1796–1806. [Google Scholar] [CrossRef] [PubMed]
- Nagendra, S.; Shanthi, D.; Chandrasekar, V.; Shanthi, S. Recognition of botnet by examining link failures in cloud network by exhausting canfes classifier approach. Adv. Intell. Syst. Comput. 2021, 1171, 179–189. [Google Scholar]
- Saravanan, S.; Thirumurugan, P. Performance Analysis of Glioma Brain Tumor Segmentation using Ridgelet Transform and CANFES Methodology. J. Med. Imaging Health Inform. 2020, 10, 2642–2648. [Google Scholar] [CrossRef]
- Calheiros, R.N.; Ranjan, R.; De Rose, C.A.; Buyya, R. CloudSim: A Novel Framework for Modeling and Simulation of Cloud Computing Infrastructures and Services. Grid Computing and Distributed Systems Laboratory; The University of Melbourne: Parkville, Australia, 2009. [Google Scholar]







| Constraints | Preliminary Value |
|---|---|
| Determined packets | 1500 |
| Throughput | 100 kb/s |
| Energy consumption | 100 mJ per cycle |
| Total no. LANs | 2 |
| No. of computers in Each LAN | 25 |
| Total no. WAN s | 2 |
| No. of computers in Each LAN | 30 |
| No. of Bots | Latency (ms) |
|---|---|
| 10 | 2.17 |
| 20 | 3.92 |
| 30 | 4.18 |
| 40 | 7.39 |
| 50 | 8.72 |
| 60 | 9.01 |
| 70 | 9.47 |
| 80 | 10.76 |
| 90 | 12.84 |
| 100 | 14.74 |
| No. of Bots | Detection Rate (%) |
|---|---|
| 10 | 98 |
| 20 | 97 |
| 30 | 96 |
| 40 | 95 |
| 50 | 94 |
| 60 | 93 |
| 70 | 92 |
| 80 | 91 |
| 90 | 89 |
| 100 | 87 |
| Organizations | Latency (ms) | Detection Rate (%) |
|---|---|---|
| Proposed methodology | 14.74 | 87 |
| Subramaniam et al. (2016) [12] | 17.54 | 81 |
| Omar Y et al. (2016) [15] | 18.95 | 85 |
| Dilara et al. (2019) [11] | 19.38 | 80 |
| Number of Bots | PDR (%) | |||
|---|---|---|---|---|
| Proposed Method | Subramaniam et al. (2016) [12] | Omar Y et al. (2016) [15] | Dilara et al. (2019) [11] | |
| 10 | 99.1 | 96.2 | 95.1 | 92.5 |
| 20 | 98.7 | 95.1 | 94.6 | 91.6 |
| 30 | 97.6 | 92.1 | 93.2 | 87.6 |
| 40 | 96.5 | 87.6 | 91.7 | 85.3 |
| 50 | 94.7 | 85.4 | 86.9 | 82.7 |
| 60 | 93.1 | 84.2 | 85.4 | 79.9 |
| Average | 96.6 | 90.1 | 91.1 | 86.6 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Selvaraj, N.P.; Paulraj, S.; Ramadass, P.; Kaluri, R.; Shorfuzzaman, M.; Alsufyani, A.; Uddin, M. Exposure of Botnets in Cloud Environment by Expending Trust Model with CANFES Classification Approach. Electronics 2022, 11, 2350. https://doi.org/10.3390/electronics11152350
Selvaraj NP, Paulraj S, Ramadass P, Kaluri R, Shorfuzzaman M, Alsufyani A, Uddin M. Exposure of Botnets in Cloud Environment by Expending Trust Model with CANFES Classification Approach. Electronics. 2022; 11(15):2350. https://doi.org/10.3390/electronics11152350
Chicago/Turabian StyleSelvaraj, Nagendra Prabhu, Sivakumar Paulraj, Parthasarathy Ramadass, Rajesh Kaluri, Mohammad Shorfuzzaman, Abdulmajeed Alsufyani, and Mueen Uddin. 2022. "Exposure of Botnets in Cloud Environment by Expending Trust Model with CANFES Classification Approach" Electronics 11, no. 15: 2350. https://doi.org/10.3390/electronics11152350
APA StyleSelvaraj, N. P., Paulraj, S., Ramadass, P., Kaluri, R., Shorfuzzaman, M., Alsufyani, A., & Uddin, M. (2022). Exposure of Botnets in Cloud Environment by Expending Trust Model with CANFES Classification Approach. Electronics, 11(15), 2350. https://doi.org/10.3390/electronics11152350







