A Deep Learning Method Based on the Attention Mechanism for Hardware Trojan Detection
Abstract
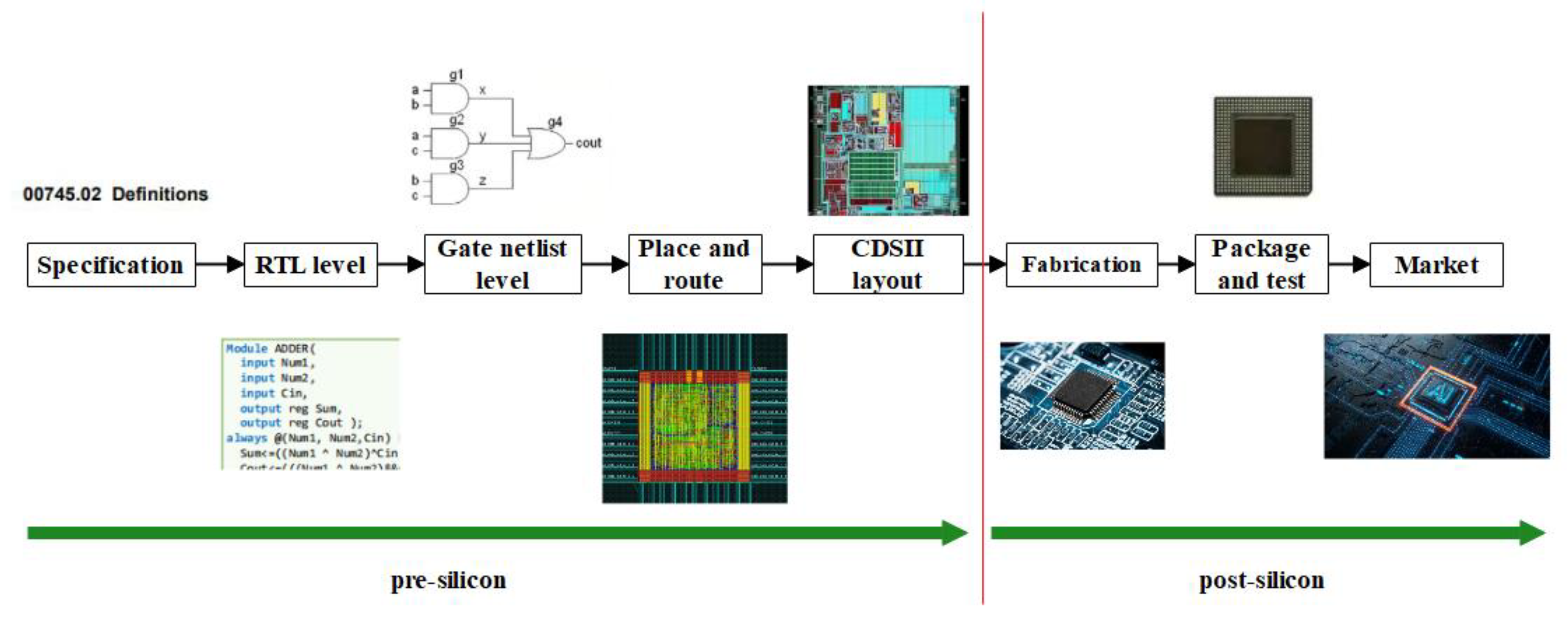
:1. Introduction
2. Background
2.1. Hardware Trojan Architecture
2.2. Hardware Trojan Detection Technology
2.2.1. Presilicon Detection
- Formal Verification
- Functional Verification
- Coding/Structure Analysis
2.2.2. Postsilicon Detection
- Reverse Engineering
- Logic Testing
- Side-Channel Analysis
2.3. Attention Mechanism
3. Hardware Trojan Detection Model
3.1. MLP-Attention Detection Model
3.2. CNN-Attention Detection Model
4. Hardware Trojan Detection Flow
- Step 1: Data Acquisition Stage
- Step 2: Model Training Stage
- Step 3: Hardware Trojan Detection Stage
5. Results
5.1. Experimental Environment
5.2. Data Acquisition and Preprocessing
5.3. Experimental Results and Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Basak, A.; Bhunia, S.; Tkacik, T.; Ray, S. Security Assurance for System-on-Chip Designs with Untrusted IPs. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1515–1528. [Google Scholar] [CrossRef]
- Gundabolu, S.; Wang, X. On-chip Data Security Against Untrustworthy Software and Hardware IPs in Embedded Systems. In Proceedings of the 2018 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Hong Kong, China, 8–11 July 2018; pp. 644–649. [Google Scholar] [CrossRef]
- Yang, Y.; Ye, J.; Cao, Y.; Zhang, J.; Li, X.; Li, H.; Hu, Y. Survey: Hardware Trojan Detection for Netlist. In Proceedings of the 2020 IEEE 29th Asian Test Symposium (ATS), Penang, Malaysia, 23–26 November 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Mal-Sarkar, S.; Karam, R.; Narasimhan, S.; Ghosh, A.; Krishna, A.; Bhunia, S. Design and Validation for FPGA Trust under Hardware Trojan Attacks. IEEE Trans. Multi-Scale Comput. Syst. 2016, 2, 186–198. [Google Scholar] [CrossRef] [Green Version]
- Li, H.; Liu, Q.; Zhang, J. A survey of hardware Trojan threat and defense. Integration 2016, 55, 426–437. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, Q.; Chen, Y.; Jiang, X. A Survey on Machine Learning Against Hardware Trojan Attacks: Recent Advances and Challenges. IEEE Access 2020, 8, 10796–10826. [Google Scholar] [CrossRef]
- Malik, S.; Subramanyan, P. Invited-Specification and modeling for systems-on-chip security verification. In Proceedings of the 53rd Annual Design Automation Conference; Association for Computing Machinery: New York, NY, USA, 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Huang, X.; Liu, G.; Guo, W.; Niu, Y.; Chen, G. Obstacle-Avoiding Algorithm in X-Architecture Based on Discrete Particle Swarm Optimization for VLSI Design. ACM Trans. Des. Autom. Electron. Syst. 2015, 20, 1–28. [Google Scholar] [CrossRef]
- Dong, C.; He, G.; Liu, X.; Yang, Y.; Guo, W. A Multi-Layer Hardware Trojan Protection Framework for IoT Chips. IEEE Access 2019, 7, 23628–23639. [Google Scholar] [CrossRef]
- Sterpone, L.; Violante, M. A new reliability-oriented place and route algorithm for SRAM-based FPGAs. IEEE Trans. Comput. 2006, 55, 732–744. [Google Scholar] [CrossRef]
- Lu, J.; Taskin, B. From RTL to GDSII: An ASIC design course development using Synopsys® University Program. In Proceedings of the 2011 IEEE International Conference on Microelectronic Systems Education, San Diego, CA, USA, 5–6 June 2011; pp. 72–75. [Google Scholar] [CrossRef]
- Mitra, S.; Seshia, S.A.; Nicolici, N. Post-silicon validation opportunities, challenges and recent advances. In Proceedings of the Design Automation Conference, Anaheim, CA, USA, 13–18 June 2010; pp. 12–17. [Google Scholar] [CrossRef] [Green Version]
- Bian, R.; Xue, M.; Wang, J. A Novel Golden Models-Free Hardware Trojan Detection Technique Using Unsupervised Clustering Analysis. In International Conference on Cloud Computing and Security; Springer: Cham, Switzerland, 2018; pp. 634–646. [Google Scholar] [CrossRef]
- Worley, K.; Rahman, T. Supervised Machine Learning Techniques for Trojan Detection with Ring Oscillator Network. In Proceedings of the 2019 SoutheastCon, Huntsville, AL, USA, 11–14 April 2019; pp. 1–7. [Google Scholar] [CrossRef] [Green Version]
- Xue, M.; Bian, R.; Wang, J.; Liu, W. A Co-training Based Hardware Trojan Detection Technique by Exploiting Unlabeled ICs and Inaccurate Simulation Models. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1452–1457. [Google Scholar] [CrossRef]
- Choo, H.S.; Ooi, C.Y.; Inoue, M.; Ismail, N.; Moghbel, M.; Kok, C.H. Register-Transfer-Level Features for Machine-Learning-Based Hardware Trojan Detection. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2020, E103.A, 502–509. [Google Scholar] [CrossRef]
- Inoue, T.; Hasegawa, K.; Kobayashi, Y.; Yanagisawa, M.; Togawa, N. Designing Subspecies of Hardware Trojans and Their Detection Using Neural Network Approach. In Proceedings of the 2018 IEEE 8th International Conference on Consumer Electronics-Berlin (ICCE-Berlin), Berlin, Germany, 2–5 September 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Pavlidis, A.; Faehn, E.; Louerat, M.-M.; Stratigopoulos, H.-G. Run-Time Hardware Trojan Detection in Analog and Mixed-Signal ICs. In Proceedings of the 40th IEEE VLSI Test Symposium 2022, San Diego, CA, USA, 25–27 April 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Niu, Z.; Zhong, G.; Yu, H. A review on the attention mechanism of deep learning. Neurocomputing 2021, 452, 48–62. [Google Scholar] [CrossRef]
- Jin, Y.; Kupp, N.; Makris, Y. Experiences in Hardware Trojan design and implementation. In Proceedings of the 2009 IEEE International Workshop on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 27 July 2009; pp. 50–57. [Google Scholar] [CrossRef]
- Baumgarten, A.; Steffen, M.; Clausman, M.; Zambreno, J. A case study in hardware Trojan design and implementation. Int. J. Inf. Secur. 2010, 10, 1–14. [Google Scholar] [CrossRef]
- Bhasin, S.; Danger, J.-L.; Guilley, S.; Ngo, X.T.; Sauvage, L. Hardware Trojan Horses in Cryptographic IP Cores. In Proceedings of the 2013 Workshop on Fault Diagnosis and Tolerance in Cryptography, Los Alamitos, CA, USA, 20 August 2013; pp. 15–29. [Google Scholar] [CrossRef] [Green Version]
- Dong, C.; Liu, Y.; Chen, J.; Liu, X.; Guo, W.; Chen, Y. An Unsupervised Detection Approach for Hardware Trojans. IEEE Access 2020, 8, 158169–158183. [Google Scholar] [CrossRef]
- Saravanan, P.; Mehtre, B.M. A Novel Approach to Detect Hardware Malware Using Hamming Weight Model and One Class Support Vector Machine. In VLSI Design and Test. VDAT 2018. Communications in Computer and Information Science; Rajaram, S., Balamurugan, N., Gracia Nirmala Rani, D., Singh, V., Eds.; Springer: Singapore, 2019; Volume 892, pp. 159–172. [Google Scholar] [CrossRef]
- Veeranna, N.; Schafer, B.C. Hardware Trojan Detection in Behavioral Intellectual Properties (IP’s) Using Property Checking Techniques. IEEE Trans. Emerg. Top. Comput. 2016, 5, 576–585. [Google Scholar] [CrossRef]
- Rathmair, M.; Schupfer, F.; Krieg, C. Applied formal methods for hardware Trojan detection. In Proceedings of the 2014 IEEE International Symposium on Circuits and Systems (ISCAS), Melbourne, VIC, Australia, 1–5 June 2014; pp. 169–172. [Google Scholar] [CrossRef]
- Xiao, K.; Forte, D.; Jin, Y.; Karri, R.; Bhunia, S.; Tehranipoor, M.M. Hardware Trojans: Lessons learned after one decade of research. ACM Trans. Des. Autom. Electron. Syst. 2016, 22, 1–23. [Google Scholar] [CrossRef]
- Zhang, X.; Tehranipoor, M. RON: An on-chip ring oscillator network for hardware Trojan detection. In Proceedings of the 2011 Design, Automation & Test in Europe, Grenoble, France, 14–18 March 2011; pp. 1–6. [Google Scholar] [CrossRef]
- Torrance, R.; James, D. The State-of-the-Art in IC Reverse Engineering. In Cryptographic Hardware and Embedded Systems-CHES 2009; Lecture Notes in Computer, Science; Clavier, C., Gaj, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5747, pp. 363–381. [Google Scholar] [CrossRef] [Green Version]
- Bao, C.; Forte, D.; Srivastava, A. On Reverse Engineering-Based Hardware Trojan Detection. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2015, 35, 49–57. [Google Scholar] [CrossRef]
- Bazzazi, A.; Shalmani, M.T.M.; Hemmatyar, A.M.A. Hardware Trojan Detection Based on Logical Testing. J. Electron. Test. 2017, 33, 381–395. [Google Scholar] [CrossRef]
- Nourian, M.A.; Fazeli, M.; Hely, D. Hardware Trojan Detection Using an Advised Genetic Algorithm Based Logic Testing. J. Electron. Test. 2018, 34, 461–470. [Google Scholar] [CrossRef]
- Du, D.; Narasimhan, S.; Chakraborty, R.S.; Bhunia, S. Self-referencing: A Scalable Side-Channel Approach for Hardware Trojan Detection. In International Workshop on Cryptographic Hardware and Embedded Systems; CHES, 2010; Lecture Notes in Computer, Science; Mangard, S., Standaert, F.X., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6225, pp. 173–187. [Google Scholar] [CrossRef]
- Narasimhan, S.; Du, D.; Chakraborty, R.S.; Paul, S.; Wolff, F.G.; Papachristou, C.A.; Roy, K.; Bhunia, S. Hardware Trojan Detection by Multiple-Parameter Side-Channel Analysis. IEEE Trans. Comput. 2012, 62, 2183–2195. [Google Scholar] [CrossRef]
- Huang, Y.; Bhunia, S.; Mishra, P. Scalable Test Generation for Trojan Detection Using Side Channel Analysis. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2746–2760. [Google Scholar] [CrossRef]
- Li, X.; Zhang, W.; Ding, Q. Understanding and improving deep learning-based rolling bearing fault diagnosis with attention mechanism. Signal Process. 2019, 161, 136–154. [Google Scholar] [CrossRef]
- Lashgari, E.; Ott, J.; Connelly, A.; Baldi, P.; Maoz, U. An end-to-end CNN with attentional mechanism applied to raw EEG in a BCI classification task. J. Neural Eng. 2021, 18, 0460e3. [Google Scholar] [CrossRef]
- Kruse, R.; Mostaghim, S.; Borgelt, C.; Braune, C.; Steinbrecher, M. Multi-layer Perceptrons. In Computational Intelligence; Texts in Computer Science; Springer: Cham, Switzerland, 2022; pp. 53–124. [Google Scholar] [CrossRef]
- Alsmadi, M.K.; Bin Omar, K.; Noah, S.A.; Almarashdah, I. Performance Comparison of Multi-layer Perceptron (Back Propagation, Delta Rule and Perceptron) algorithms in Neural Networks. In Proceedings of the 2009 IEEE International Advance Computing Conference, Patiala, India, 6–7 March 2009; pp. 296–299. [Google Scholar] [CrossRef]
- Hasegawa, K.; Yanagisawa, M.; Togawa, N. Empirical Evaluation and Optimization of Hardware-Trojan Classification for Gate-Level Netlists Based on Multi-Layer Neural Networks. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2018, E101.A, 2320–2326. [Google Scholar] [CrossRef]
- O’Shea, K.; Nash, R. An introduction to convolutional neural networks. arXiv 2015, arXiv:1511.08458. [Google Scholar] [CrossRef]
- Yamashita, R.; Nishio, M.; Do, R.K.G.; Togashi, K. Convolutional neural networks: An overview and application in radiology. Insights Into Imaging 2018, 9, 611–629. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- He, J.; Ma, H.; Liu, Y.; Zhao, Y. Golden Chip-Free Trojan Detection Leveraging Trojan Trigger’s Side-Channel Fingerprinting. ACM Trans. Embed. Comput. Syst. 2021, 20, 1–18. [Google Scholar] [CrossRef]
- He, J.; Zhao, Y.; Guo, X.; Jin, Y. Hardware Trojan Detection Through Chip-Free Electromagnetic Side-Channel Statistical Analysis. IEEE Trans. Very Large Scale Integr. Syst. 2017, 25, 2939–2948. [Google Scholar] [CrossRef]
- Machine Learning Techniques for Hardware Trojan Detection. Available online: https://github.com/Kkalais/Hardware-Trojan-Detection (accessed on 24 September 2020).
- Madden, K.; Harkin, J.; McDaid, L.; Nugent, C. Adding Security to Networks-on-Chip using Neural Networks. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bangalore, India, 18–21 November 2018; pp. 1299–1306. [Google Scholar] [CrossRef]
- Reshma, K.; Priyatharishini, M.; Devi, M.N. Hardware Trojan Detection Using Deep Learning Technique. In Soft Computing and Signal Processing; Advances in Intelligent Systems and, Computing; Wang, J., Reddy, G., Prasad, V., Reddy, V., Eds.; Springer: Singapore, 2019; Volume 898, pp. 671–680. [Google Scholar] [CrossRef]
- Hu, T.; Dian, S.; Jiang, R. Hardware Trojan detection based on long short-term memory neural network. Comput. Eng. 2020, 46, 110–115. [Google Scholar] [CrossRef]






| Hyperparameter | Value |
|---|---|
| Epoch | 80 |
| Learning_rate | 0.001 |
| Filters1 | 16 |
| Kernel_size1 | 8 |
| Filters2 | 64 |
| Kernel_size2 | 4 |
| Filters3 | 256 |
| Kernel_size3 | 4 |
| Dropout_rate | 0.3 |
| Dense_units | 128 |
| Output_units | 2 |
| Acronym | Definition |
|---|---|
| CNN | Convolutional neural network |
| CNN-Att | CNN-Attention |
| GB | Gradient boosting |
| KNN | K-nearest neighbors |
| LR | Logistic regression |
| MLP | Multilayer perceptron |
| MLP-Att | MLP-Attention |
| RF | Random forest |
| SVM | Support vector machine |
| Model Name | Model Parameters | |
|---|---|---|
| GB | Number of decision trees | 6 |
| Learning rate | 0.1 | |
| KNN | Number of neighbors | 8 |
| Distance measure | ED 1 | |
| LR | Number of decision trees | 6 |
| Learning rate | 0.1 | |
| RF | Max depth of tree | 10 |
| Number of decision trees | 10 | |
| Model Name | Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) |
|---|---|---|---|---|
| CNN | 80.31 | 81.20 | 80.77 | 80.93 |
| CNN-Att | 85.17 | 85.50 | 85.36 | 84.22 |
| GB | 68.09 | 66.94 | 63.22 | 63.28 |
| KNN | 66.55 | 66.07 | 62.48 | 62.43 |
| LR | 63.79 | 62.88 | 57.36 | 55.21 |
| MLP | 76.08 | 75.90 | 69.86 | 72.63 |
| MLI-Att | 84.87 | 85.13 | 84.87 | 84.89 |
| RF | 68.21 | 66.80 | 63.80 | 64.01 |
| SVM | 62.46 | 60.00 | 54.69 | 51.44 |
| Mix of Trojan | Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) |
|---|---|---|---|---|
| 1-2 | 84.32 | 82.35 | 85.25 | 83.77 |
| 1-3 | 85.32 | 85.61 | 86.12 | 85.71 |
| 1-4 | 82.11 | 82.67 | 81.76 | 80.05 |
| 2-3 | 84.20 | 83.23 | 82.93 | 82.77 |
| 2-4 | 84.16 | 84.49 | 84.22 | 81.65 |
| 3-4 | 84.36 | 83.78 | 82.67 | 82.91 |
| 1-2-3 | 84.53 | 83.16 | 87.78 | 85.41 |
| 1-2-4 | 84.17 | 83.55 | 86.29 | 84.90 |
| 1-3-4 | 84.36 | 84.63 | 86.03 | 85.32 |
| 2-3-4 | 81.25 | 81.25 | 89.32 | 85.09 |
| 1-2-3-4 | 82.68 | 82.10 | 84.56 | 83.34 |
| Model Name | Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) |
|---|---|---|---|---|
| 1-2 | 84.50 | 84.31 | 84.22 | 81.87 |
| 1-3 | 85.20 | 85.99 | 83.29 | 83.79 |
| 1-4 | 82.15 | 82.06 | 80.58 | 79.80 |
| 2-3 | 82.31 | 81.44 | 85.36 | 83.36 |
| 2-4 | 82.02 | 82.34 | 82.80 | 82.46 |
| 3-4 | 83.95 | 83.12 | 83.05 | 83.09 |
| 1-2-3 | 84.57 | 86.01 | 92.43 | 87.62 |
| 1-2-4 | 85.68 | 82.74 | 85.30 | 85.45 |
| 1-3-4 | 87.52 | 87.38 | 84.27 | 85.80 |
| 2-3-4 | 86.27 | 86.84 | 87.03 | 86.94 |
| 1-2-3-4 | 83.73 | 83.33 | 82.60 | 82.97 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tang, W.; Su, J.; He, J.; Gao, Y. A Deep Learning Method Based on the Attention Mechanism for Hardware Trojan Detection. Electronics 2022, 11, 2400. https://doi.org/10.3390/electronics11152400
Tang W, Su J, He J, Gao Y. A Deep Learning Method Based on the Attention Mechanism for Hardware Trojan Detection. Electronics. 2022; 11(15):2400. https://doi.org/10.3390/electronics11152400
Chicago/Turabian StyleTang, Wenjing, Jing Su, Jiaji He, and Yuchan Gao. 2022. "A Deep Learning Method Based on the Attention Mechanism for Hardware Trojan Detection" Electronics 11, no. 15: 2400. https://doi.org/10.3390/electronics11152400
APA StyleTang, W., Su, J., He, J., & Gao, Y. (2022). A Deep Learning Method Based on the Attention Mechanism for Hardware Trojan Detection. Electronics, 11(15), 2400. https://doi.org/10.3390/electronics11152400






