Trusted and Secure Blockchain-Based Architecture for Internet-of-Medical-Things
Abstract
:1. Introduction
- -
- A holistic overview of the currently applied Blockchain-based methods oriented on IoMT;
- -
- proposition of a novel trusted and secure Blockchain-based architecture for Internet-of-Medical-Things (BIoMT architecture);
- -
- analysis and discussion of the security aspects of the proposed solution with the application of the Elliptic Curve Digital Signature Algorithm (ECDSA);
- -
- implementation and experimental verification of the proposed BIoMT architecture with the use of the MultiChain platform.
2. Blockchain Technology’s Unique Benefits for IoMT Architectures
- trustworthy and secure solution;
- decentralized, trustless nodes;
- autonomous functioning.
- Trustworthiness in IoMT.
- Blockchain features such as trust, immutability, and verifiability can be applied in present IoMT systems.
- Due to decentralization, no single authority will be responsible for approving the transactions or setting specific rules for accepting them in the IoMT system with this technology.
- The distributed and consensus mechanism plays an important role in this process of acceptance.
- The tamper-proof system of the Blockchain technology meets several compliance and regulatory necessities of both industrial IoT and IoMT systems.
- Security is enhanced by Blockchain technology in IoMT systems via the use of cryptographic algorithms.
- The validation process in Blockchain uses various checks such as MHT and ECC, and is another reason for more security.
- The CIA triad is maintained using Blockchain technology in IoMT.
- Dangerous MITM attacks are less possible with the use of Blockchain technology, due to features such as being tamper-proof and malicious actors being unable to alter or manipulate the data. We know that the data is stored in multiple locations.
- Blockchain’s decentralized P2P network is highly advantageous as all the transactions are verified and validated by a consensus among peers; as a result, there is no requirement for trusting each other, thus enabling trust-free networks in IoMT.
- Feature such as tracking by use of Blockchain technology results in faster transactions in IoMT systems. Significant economic benefits exist for hospitals and allied industries.
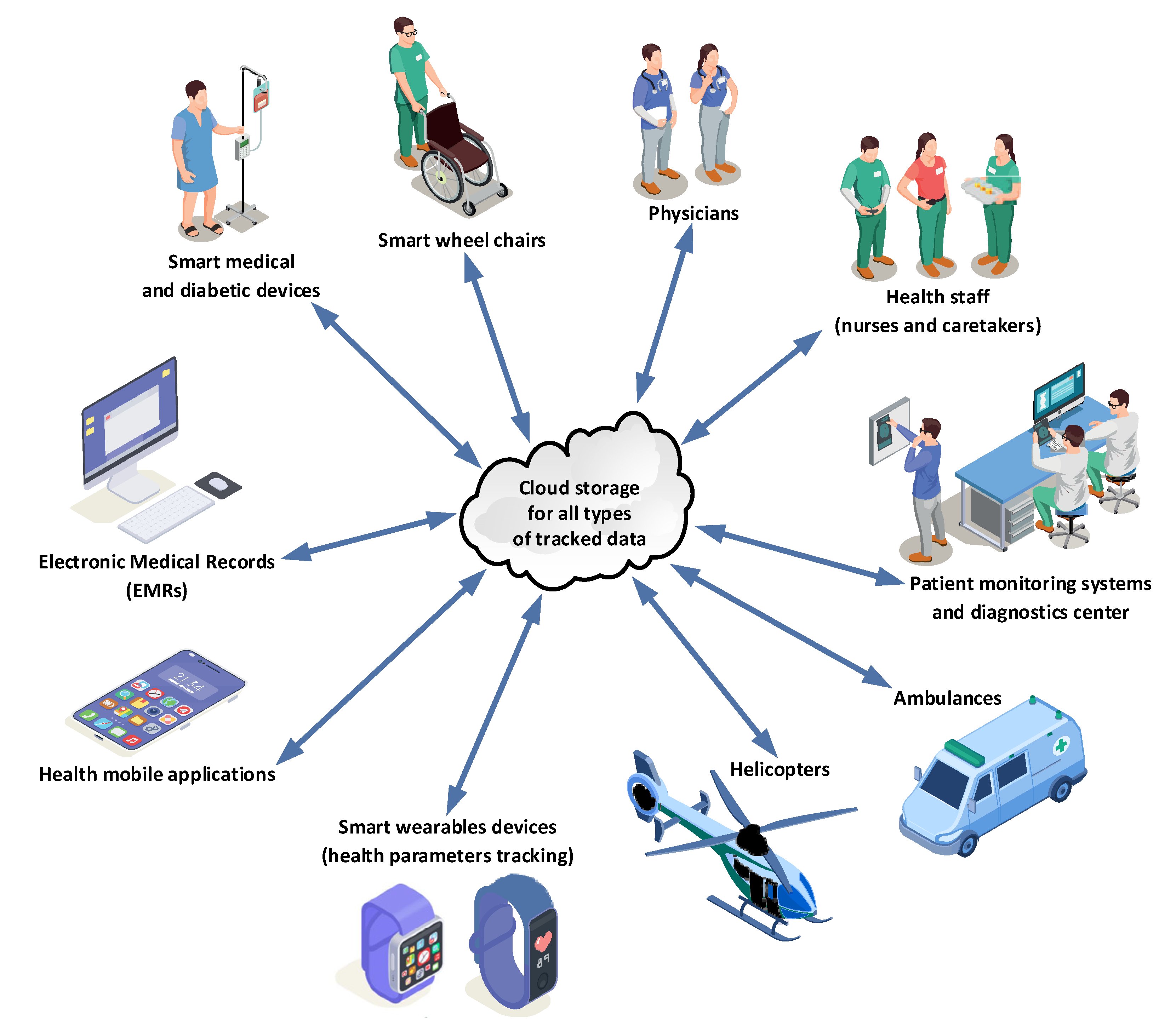
3. The Proposed Blockchain-Based IoMT Architecture
4. Experimental Verification of the Proposed Solution
4.1. The Blockchain Structure
4.2. Signing Data with ECDSA
- Let GF(f) be a prime field.
- Then let s, t ∈ GF(f) be constant such that 4s3 + 27t2 ≠ 0.
- An EC E(s, t), over GF(f), is considered the set of points (x, y) ∈ GF(f) which fulfil Equation (1), called the “short Weierstrass form” [49]:
- Generation of the Key:
- (a)
- the required chosen EC is well defined over a finite field Fc with the characteristic c, and with a base point G ∈ Ec(s, t) with an order of n;
- (b)
- select a random integer h such that 1 ≤ h ≤ n − 1;
- (c)
- compute T = h × G and finally, the public key pair is (T, h).
- (d)
- the public key pair is (T, h).
- Generation of the Signature (let m be medical records to be signed):
- (a)
- select an integer k in such a way that 1 ≤ k ≤ n − 1,
- (b)
- compute k × G = (x1, y1),
- (c)
- compute r = x1 mod n:if r = 0 then select new k.
- (d)
- compute k − 1 mod n and e = h(m).
- (e)
- compute s = p−1(e + kr):if s = 0 then go to step (2a).
- (f)
- pair (r, s) is the generated signature for the medical records m.
- Verification of the signature (r, s) of medical records m signed by verifier V:
- (a)
- verify (by V) whether r, s ϵ [1, n − 1],
- (b)
- compute e = h(m) and s−1,
- (c)
- compute u = es−1 mod n and v = rs−1 mod n,
- (d)
- compute w = (x2, y2) = uG + vT:if w = 0 then stopelse compute t = x2 mod n.
4.3. The Experimental Verification
- two addresses with permission “mine”, which are assigned to two miners responsible for confirming transactions in the blockchain;
- seven addresses with permission “send”, which represent the patient’s IoMT devices; one address for one patient’s device (e.g., smartphone) with access to the blockchain;
- two addresses with permission “send”, which represent the hospital patient monitoring system;
- one address with permission “connect”, which represents the hospital diagnostic center (this center has access to all blocks in the blockchain).
4.4. Performance Evaluation
- Transaction with data stored in text form. This is a typical transaction to keep information about the patient personal data or simple test results, such as heart rate and pressure measurements. In the research, we use a CSV file that collects data from the National Lung Screening Trial [55].
- Transaction with data stored in PDF format. This kind of transaction is most often used for storing data from various patient examinations such as blood tests and urine tests. These files also contain small pictures such as the company’s logo. Moreover, most often there is also a need for digital signing of the document, and the PDF format is effective for this purpose. In the research, a signed PDF file was used, which contained example outcomes of the patient’s blood test.
- Transaction with data stored in graphical format. This type of transaction is often used for storing, for example, x-ray or computed tomography photos, as well as magnetic resonance images or electrocardiograms. In the research, we used an example x-ray image of the patient’s chest (the resolution of the image was 2048 × 2048 pixels).
4.5. Discussion of the Obtained Results
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A
| package ykarav.multichain; import ykarav.multichain.chain.Chain; import ykarav.multichain.chain.Method; import ykarav.multichain.chain.MultichainService; import java.io.*; import java.nio.file.Files; import java.nio.file.Paths; import java.util.ArrayList; import java.util.Collections; import java.util.List; public class TestApp extends Thread { public static void main(String[] args) throws IOException { //Configuration that we can connect to Blockchain Chain chain0 = Chain.initialize(“192.168.96.106”, 7762, “multichainrpc”, “J7Qm7UAeAbHWPJcYTUPfQPjC7c6QfKmsC1ApSVvowhBq”, “BIoMT”); MultichainService chainService = MultichainService.setChain(chain0); //From this address we send transactions String adress1 = “1YpnjLhP7yyYcakjRJmhjfCVLsFXDQb3buLsNp”; //Declare parameters as params List<Object> params = null; params = new ArrayList<Object>(); //Fill key list with data Object stream = new String(“HPMS”); ArrayList keys = new ArrayList(); int block_type = 2; keys.add(“block_type = “ + block_type); String data_provider = “HPMS”; keys.add(“data_provider = “ + data_provider); int data_reliability = 1; keys.add(“data_reliability = “ + data_reliability); int patient_ID = 1582; keys.add(“patient_ID = “ + patient_ID); Object options = new String(); //Files used in tests String medicalFile132mb = “C:\\Users\\k.kozdroj\\Desktop\\nlst_test.csv”; String pdfWithQSignature = “C:\\Users\\k.kozdroj\\Downloads\\blood_test.pdf”; String rtg = “C:\\Users\\k.kozdroj\\Downloads\\radiology_test.jpg”; //Convert the file to a binary table byte[] bytes = Files.readAllBytes(Paths.get(rtg)); //Declare a new List for all transactions ArrayList<Double> allTransaction = new ArrayList<Double>(); //Fill params with all necessary parameters Collections.addAll(params,adress1, stream, keys,bin2hex(bytes)); //Get start time long startTime = System.nanoTime(); //Declare loop for all transactions for(int counter = 0 ;counter <= 100; counter++) { long beforeTransaction = System.nanoTime(); String jsonInString = chainService.apiCall(params, Method.PUBLISH_FROM, chain0.getChainName()); //Convert time to seconds double currentTime = (double) (System.nanoTime() - beforeTransaction)/1_000_000_000; //Add each transaction time to the List allTransaction.add(currentTime); } //Calculate the time of all transactions and print lists of each time transaction and full time long estimatedTime = System.nanoTime() - startTime; System.out.println(allTransaction); System.out.println(estimatedTime); double elapsedTimeInSecond = (double) estimatedTime/1_000_000_000; System.out.println(elapsedTimeInSecond + “ seconds”); } //This method convert binary table to hexadecimal format public static String bin2hex(byte[] arr) { StringBuffer sb = new StringBuffer(); for (int i = 0; i < arr.length; i++) { String str = Integer.toHexString((int) arr[i]); if (str.length() == 2) sb.append(str); if (str.length() < 2) { sb.append(“0”); sb.append(str); } if (str.length() > 2) sb.append(str.substring(str.length() - 2)); } return sb.toString(); } } |
References
- Fortune Business Insights, Internet of Medical Things (IoMT) Market, October 2021. Available online: https://www.fortunebusinessinsights.com/industry-reports/internet-of-medical-things-iomt-market-101844 (accessed on 26 June 2022).
- Esposito, C.; De Santis, A.; Tortora, G.; Chang, H.; Choo, K.-K.R. Blockchain: A Panacea for Healthcare Cloud-Based Data Security and Privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar] [CrossRef]
- Rodrigues, J.J.P.C.; Segundo, D.B.D.R.; Junqueira, H.A.; Sabino, M.H.; Prince, R.M.; Al-Muhtadi, J.; De Albuquerque, V.H.C. Enabling Technologies for the Internet of Health Things. IEEE Access 2018, 6, 13129–13141. [Google Scholar] [CrossRef]
- Sun, W.; Cai, Z.; Li, Y.; Liu, F.; Fang, S.; Wang, G. Security and Privacy in the Medical Internet of Things: A Review. Secur. Commun. Netw. 2018, 2018, 5978636. [Google Scholar] [CrossRef]
- Hölbl, M.; Kompara, M.; Kamišalić, A.; Nemec Zlatolas, L. A Systematic Review of the Use of Blockchain in Healthcare. Symmetry 2018, 10, 470. [Google Scholar] [CrossRef]
- Sundaravadivel, P.; Kougianos, E.; Mohanty, S.P.; Ganapathiraju, M.K. Everything You Wanted to Know about Smart Health Care: Evaluating the Different Technologies and Components of the Internet of Things for Better Health. IEEE Consum. Electron. Mag. 2018, 7, 18–28. [Google Scholar] [CrossRef]
- Zhang, J.; Xue, N.; Huang, X. A Secure System For Pervasive Social Network-Based Healthcare. IEEE Access 2016, 4, 9239–9250. [Google Scholar] [CrossRef]
- Ahram, T.; Sargolzaei, A.; Sargolzaei, S.; Daniels, J.; Amaba, B. Blockchain technology innovations. In Proceedings of the IEEE Technology & Engineering Management Conference (TEMSCON), Santa Clara, CA, USA, 8–10 June 2017; pp. 137–141. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Li, X. A Lightweight and Efficient Secure Hybrid RSA (SHRSA) Messaging Scheme with Four-Layered Authentication Stack. IEEE Access 2019, 7, 30487–30506. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and Secure Sharing of Personal Health Records in Cloud Computing Using Attribute-Based Encryption. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 131–143. [Google Scholar] [CrossRef]
- More, S.; Chaudhari, S. Third Party Public Auditing Scheme for Cloud Storage. Procedia Comput. Sci. 2016, 79, 69–76. [Google Scholar] [CrossRef]
- Li, C.-T.; Lee, C.-C.; Weng, C.-Y. A Secure Cloud-Assisted Wireless Body Area Network in Mobile Emergency Medical Care System. J. Med. Syst. 2016, 40, 117. [Google Scholar] [CrossRef]
- Lounis, A.; Hadjidj, A.; Bouabdallah, A.; Challal, Y. Healing on the cloud: Secure cloud architecture for medical wireless sensor networks. Future Gener. Comput. Syst. 2016, 55, 266–277. [Google Scholar] [CrossRef]
- Kowalski, M.; Wiśniewski, R. Security Analysis of One-Time Pad Secure Algorithm Based on the Double Memory Technique, 2018. In Proceedings of the International Conference of Computational Methods in Sciences and Engineering-ICCMSE 2018, Thessaloniki, Greece, 14–18 March 2018; AIP Publishing: Melville, NY, USA, 2018. AIP Conference Proceedings. Volume 2040. [Google Scholar] [CrossRef]
- Wiśniewski, R.; Grobelny, M.; Grobelna, I.; Bazydło, G. IoT Security with One-Time Pad Secure Algorithm Based on the Double Memory Technique, 2017. In Proceedings of the International Conference of Computational Methods in Sciences and Engineering-ICCMSE 2017, Thessaloniki, Greece, 21–25 April 2017; AIP Publishing: Melville, NY, USA, 2017. AIP Conference Proceedings. Volume 1906, ISBN 9780735415966. [Google Scholar] [CrossRef]
- Di Pierro, M. What Is the Blockchain? Comput. Sci. Eng. 2017, 19, 92–95. [Google Scholar] [CrossRef]
- Samaniego, M.; Jamsrandorj, U.; Deters, R. Blockchain as a Service for IoT. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15–18 December 2016; pp. 433–436. [Google Scholar] [CrossRef]
- Zubaydi, H.D.; Chong, Y.-W.; Ko, K.; Hanshi, S.M.; Karuppayah, S. A Review on the Role of Blockchain Technology in the Healthcare Domain. Electronics 2019, 8, 679. [Google Scholar] [CrossRef]
- Viriyasitavat, W.; Xu, L.D.; Bi, Z.; Pungpapong, V. Blockchain and Internet of Things for Modern Business Process in Digital Economy—The State of the Art. IEEE Trans. Comput. Soc. Syst. 2019, 6, 1420–1432. [Google Scholar] [CrossRef]
- Johng, H.; Kim, D.; Hill, T.; Chung, L. Using Blockchain to Enhance the Trustworthiness of Business Processes: A Goal-Oriented Approach. In Proceedings of the 2018 IEEE International Conference on Services Computing (SCC), San Francisco, CA, USA, 2–7 July 2018; pp. 249–252. [Google Scholar] [CrossRef]
- Truong, N.B.; Sun, K.; Lee, G.M.; Guo, Y. GDPR-Compliant Personal Data Management: A Blockchain-Based Solution. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1746–1761. [Google Scholar] [CrossRef]
- Haber, S.; Stornetta, W.S. How to time-stamp a digital document. J. Cryptol. 1991, 3, 99–111. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-To-Peer Electronic Cash System; Decentralized Business Review; HN Publishing: Amsterdam, The Netherlands, 2008; p. 21260. [Google Scholar]
- Zaman, U.; Imran; Mehmood, F.; Iqbal, N.; Kim, J.; Ibrahim, M. Towards Secure and Intelligent Internet of Health Things: A Survey of Enabling Technologies and Applications. Electronics 2022, 11, 1893. [Google Scholar] [CrossRef]
- Abdelmaboud, A.; Ahmed, A.I.A.; Abaker, M.; Eisa, T.A.E.; Albasheer, H.; Ghorashi, S.A.; Karim, F.K. Blockchain for IoT Applications: Taxonomy, Platforms, Recent Advances, Challenges and Future Research Directions. Electronics 2022, 11, 630. [Google Scholar] [CrossRef]
- Khan, A.A.; Shaikh, Z.A.; Baitenova, L.; Mutaliyeva, L.; Moiseev, N.; Mikhaylov, A.; Laghari, A.A.; Idris, S.A.; Alshazly, H. QoS-Ledger: Smart Contracts and Metaheuristic for Secure Quality-of-Service and Cost-Efficient Scheduling of Medical-Data Processing. Electronics 2021, 10, 3083. [Google Scholar] [CrossRef]
- Mani, V.; Manickam, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. Hyperledger Healthchain: Patient-Centric IPFS-Based Storage of Health Records. Electronics 2021, 10, 3003. [Google Scholar] [CrossRef]
- Imran, M.; Zaman, U.; Imran; Imtiaz, J.; Fayaz, M.; Gwak, J. Comprehensive Survey of IoT, Machine Learning, and Blockchain for Health Care Applications: A Topical Assessment for Pandemic Preparedness, Challenges, and Solutions. Electronics 2021, 10, 2501. [Google Scholar] [CrossRef]
- Bazydło, G.; Wiśniewski, R.; Kozdrój, K. Trusted and Secure Blockchain-Based Durable Medium Electronic Service. Cryptography 2022, 6, 10. [Google Scholar] [CrossRef]
- Ichikawa, D.; Kashiyama, M.; Ueno, T. Tamper-Resistant Mobile Health Using Blockchain Technology. JMIR Mhealth Uhealth 2017, 5, e111. [Google Scholar] [CrossRef]
- Ahmad, L.; Khanji, S.; Iqbal, F.; Kamoun, F. 2020. Blockchain-based chain of custody: Towards real-time tamper-proof evidence management. In Proceedings of the 15th International Conference on Availability, Reliability and Security (ARES ‘20), Dublin, Ireland, 25–28 August 2020; Association for Computing Machinery: New York, NY, USA, 2020. Article 48. pp. 1–8. [Google Scholar] [CrossRef]
- Nayak, A.; Dutta, K. Blockchain: The perfect data protection tool. In Proceedings of the 2017 International Conference on Intelligent Computing and Control (I2C2), Coimbatore, India, 23–24 June 2017; pp. 1–3. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and Privacy on Blockchain. ACM Comput. Surv. 2019, 52, 1–34. [Google Scholar] [CrossRef]
- Wang, Z.; Lin, J.; Cai, Q.; Wang, Q.; Zha, D.; Jing, J. Blockchain-Based Certificate Transparency and Revocation Transparency. IEEE Trans. Dependable Secur. Comput. 2022, 19, 681–697. [Google Scholar] [CrossRef]
- Abe, R.; Watanabe, H.; Ohashi, S.; Fujimura, S.; Nakadaira, A. Storage Protocol for Securing Blockchain Transparency. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018; pp. 577–581. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Wang, J.; Li, X. Security Challenges and Concerns of Internet of Things (IoT). In Cyber-Physical Systems: Architecture, Security and Application, EAI/Springer Innovations in Communication and Computing; Guo, S., Zeng, D., Eds.; Springer: Cham, Switzerland, 2018; pp. 153–185. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Wang, J.; Li, X. Secure IoT Structural Design for Smart Homes, Chapter 13. In Smart Cities Cybersecurity and Privacy; Elsevier: Amsterdam, The Netherlands, 2019; pp. 187–201. ISBN 9780128150320. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Wang, J.; Li, X. Present Scenarios of IoT Projects with Security Aspects Focused. In Digital Twin Technologies and Smart Cities. Internet of Things; Farsi, M., Daneshkhah, A., Hosseinian-Far, A., Jahankhani, H., Eds.; Springer: Cham, Switzerland, 2020. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Wang, J.; Li, X. CoAP—Application Layer Connection-Less Lightweight Protocol for the Internet of Things (IoT) and CoAP-IPSEC Security with DTLS Supporting CoAP. In Digital Twin Technologies and Smart Cities; Farsi, M., Daneshkhah, A., Hosseinian-Far, A., Jahankhani, H., Eds.; Internet of Things; Springer: Cham, Switzerland, 2020. [Google Scholar] [CrossRef]
- Wiśniewski, R.; Wiśniewski, R. Representation of Primes in the Form p = 6 “ x=1 and its Application to the RSA Prime Factorization, 2018. In Proceedings of the International Conference of Computational Methods in Sciences and Engineering-ICCMSE 2018, Thessaloniki, Greece, 14–18 March 2018; AIP Publishing: New York, NY, USA, 2018. AIP Conference Proceedings. Volume 2040. [Google Scholar] [CrossRef]
- Rivest, R.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Ekparinya, P.; Gramoli, V.; Jourjon, G. Impact of Man-In-The-Middle Attacks on Ethereum. In Proceedings of the 2018 IEEE 37th Symposium on Reliable Distributed Systems (SRDS), Salvador, Brazil, 2–5 October 2018; pp. 11–20. [Google Scholar] [CrossRef]
- Vanstone, S.A. Responses to NIST’s proposal. Commun. ACM 1992, 35, 41–54. [Google Scholar] [CrossRef]
- Long, T.; Liu, X. Two Improvements to Digital Signature Scheme Based on the Elliptic Curve Cryptosystem. In Proceedings of the International Workshop on Information Security and Application (IWISA 2009), Toyama, Japan, 25–27 August 2009; Academy Publisher: Bengaluru, India, 2009. [Google Scholar]
- Bi, W.; Jia, X.; Zheng, M. A Secure Multiple Elliptic Curves Digital Signature Algorithm for Blockchain. arXiv 2018. [Google Scholar] [CrossRef]
- Cano, M.; Cañavate-Sanchez, A. Preserving Data Privacy in the Internet of Medical Things Using Dual Signature ECDSA. Secur. Commun. Netw. 2020, 2020, 4960964. [Google Scholar] [CrossRef]
- Salim, M.M.; Kim, I.; Doniyor, U.; Lee, C.; Park, J.H. Homomorphic Encryption Based Privacy-Preservation for IoMT. Appl. Sci. 2021, 11, 8757. [Google Scholar] [CrossRef]
- Blake, I.; Seroussi, G.; Smart, N.P. Advances in Elliptic Curve Cryptography; London Mathematical Society Lecture Note Series; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar] [CrossRef]
- Bekyel, E. The density of elliptic curves having a global minimal Weierstrass equation. J. Number Theory 2004, 109, 41–58. [Google Scholar] [CrossRef]
- Hankerson, D.; Menezes, A. Elliptic Curve Discrete Logarithm Problem. In Encyclopedia of Cryptography and Security; van Tilborg, H.C.A., Jajodia, S., Eds.; Springer: Boston, MA, USA, 2011. [Google Scholar] [CrossRef]
- Caelli, W.J.; Dawson, E.P.; Rea, S.A. PKI, elliptic curve cryptography, and digital signatures. Comput. Secur. 1999, 18, 47–66. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.; Rompolos, K.; Sarigiannidis, P.; Argyriou, V.; Lagkas, T.; Sarigiannidis, A.; Goudos, S.K.; Wan, S. Modeling, Detecting, and Mitigating Threats Against Industrial Healthcare Systems: A Combined Software Defined Networking and Reinforcement Learning Approach. IEEE Trans. Ind. Inform. 2022, 18, 2041–2052. [Google Scholar] [CrossRef]
- Chenthara, S.; Ahmed, K.; Wang, H.; Whittaker, F. Security and Privacy-Preserving Challenges of e-Health Solutions in Cloud Computing. IEEE Access 2019, 7, 74361–74382. [Google Scholar] [CrossRef]
- MultiChain Project Website. Available online: https://www.multichain.com/ (accessed on 26 June 2022).
- National Lung Screening Trial (Cancer Imaging Archive) Website. Available online: https://wiki.cancerimagingarchive.net/display/NLST/ (accessed on 9 August 2022).
- Yaqoob, T.; Abbas, H.; Atiquzzaman, M. Security Vulnerabilities, Attacks, Countermeasures, and Regulations of Networked Medical Devices—A Review. IEEE Commun. Surv. Tutor. 2019, 21, 3723–3768. [Google Scholar] [CrossRef]
- Croman, K.; Eyal, I. On Scaling Decentralized Blockchains (PDF). Financial Cryptography and Data Security. Lect. Notes Comput. Sci. 2016, 9604, 106–125. [Google Scholar] [CrossRef]
- IPFS Project Website. Available online: https://ipfs.tech/ (accessed on 9 August 2022).






| Name | Abbreviation |
|---|---|
| Address Resolution Protocol | ARP |
| Blockchain-based Internet-of-Medical-Things | BIoMT |
| Blockchain-based architecture for Internet-of-Medical-Things | BIoMT architecture |
| Confidentiality, Integrity, and Availability | CIA triad |
| Discrete Logarithm Problem | DLP |
| Distributed Denial-of-Service | DDoS |
| Elliptic Curve | EC |
| Elliptic Curve Cryptography | ECC |
| Elliptic Curve Digital Signature Algorithm | ECDSA |
| Elliptic Curve Discrete Logarithm Problem | ECDLP |
| Industrial Internet-of-Things | IIoT |
| Internet-of-Medical-Things | IoMT |
| Internet-of-Things | IoT |
| Interplanetary File System | IPFS |
| Man-in-the-Middle | MITM |
| Merkle Hash Tree | MHT |
| Proof-of-Work | PoW |
| Public Key Cryptography | PKC |
| Public Key Infrastructure | PKI |
| Peer-to-Peer | P2P |
| Trusted Third Party | TTP |
| Parameter | Value | Meaning |
|---|---|---|
| Chain name | BIoMT | The name of the blockchain. |
| Blockchain type | Private | The blockchain could be public or private; in the proposed approach the blockchain should not be public, so the chosen type is private. |
| Chain protocol | Multichain | The protocol could be multichain or bitcoin-style; to use streams, the multichain should be chosen. |
| Consensus type | Proof-of-Work | Type of consensus used in the blockchain. |
| Mining diversity | 0.3 | Determines how many required miners (with the permission “mine”) must participate in the transaction confirmation (0.0 means no constraint, while 1.0 means that every miner must participate). |
| Mine empty rounds | 10 | If there are no new transactions, the parameter defines how many empty rounds will be generated (these empty rounds have a positive impact on building a reliable and resilient blockchain). |
| Number of streams | 5 | The number of generated streams. |
| Number of addresses | 10 | The number of generated addresses (each of the streams can have several publishers/addresses). |
| Number of blocks | 218 | The number of generated blocks in the blockchain. |
| Number of transactions | 10,383 | The number of generated transactions kept in all blocks. |
| Parameter | Transactions with Text Data | Transactions with Signed Mixed (Text and Graphics) Data | Transactions with JPG Data |
|---|---|---|---|
| File format to store data | CSV | JPG | |
| The size of the file | 1,392,133 bytes | 516,510 bytes | 342,303 bytes |
| Number of generated transactions | 101 | 101 | 101 |
| Total time of all generated transactions | 21.7924 s | 10.5303 s | 6.5877 s |
| Arithmetic mean of 1 transaction generation time | 0.2158 s | 0.1043 s | 0.0652 s |
| Median of 1 transaction generation time | 0.2046 s | 0.0906 s | 0.0606 s |
| Number of used blocks used to store all generated transactions | 18 | 7 | 5 |
| The average number of transactions per block | 5.61 | 14.43 | 20.20 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bhattacharjya, A.; Kozdrój, K.; Bazydło, G.; Wisniewski, R. Trusted and Secure Blockchain-Based Architecture for Internet-of-Medical-Things. Electronics 2022, 11, 2560. https://doi.org/10.3390/electronics11162560
Bhattacharjya A, Kozdrój K, Bazydło G, Wisniewski R. Trusted and Secure Blockchain-Based Architecture for Internet-of-Medical-Things. Electronics. 2022; 11(16):2560. https://doi.org/10.3390/electronics11162560
Chicago/Turabian StyleBhattacharjya, Aniruddha, Kamil Kozdrój, Grzegorz Bazydło, and Remigiusz Wisniewski. 2022. "Trusted and Secure Blockchain-Based Architecture for Internet-of-Medical-Things" Electronics 11, no. 16: 2560. https://doi.org/10.3390/electronics11162560
APA StyleBhattacharjya, A., Kozdrój, K., Bazydło, G., & Wisniewski, R. (2022). Trusted and Secure Blockchain-Based Architecture for Internet-of-Medical-Things. Electronics, 11(16), 2560. https://doi.org/10.3390/electronics11162560









