A Hierarchical Federated Learning-Based Intrusion Detection System for 5G Smart Grids
Abstract
:1. Introduction
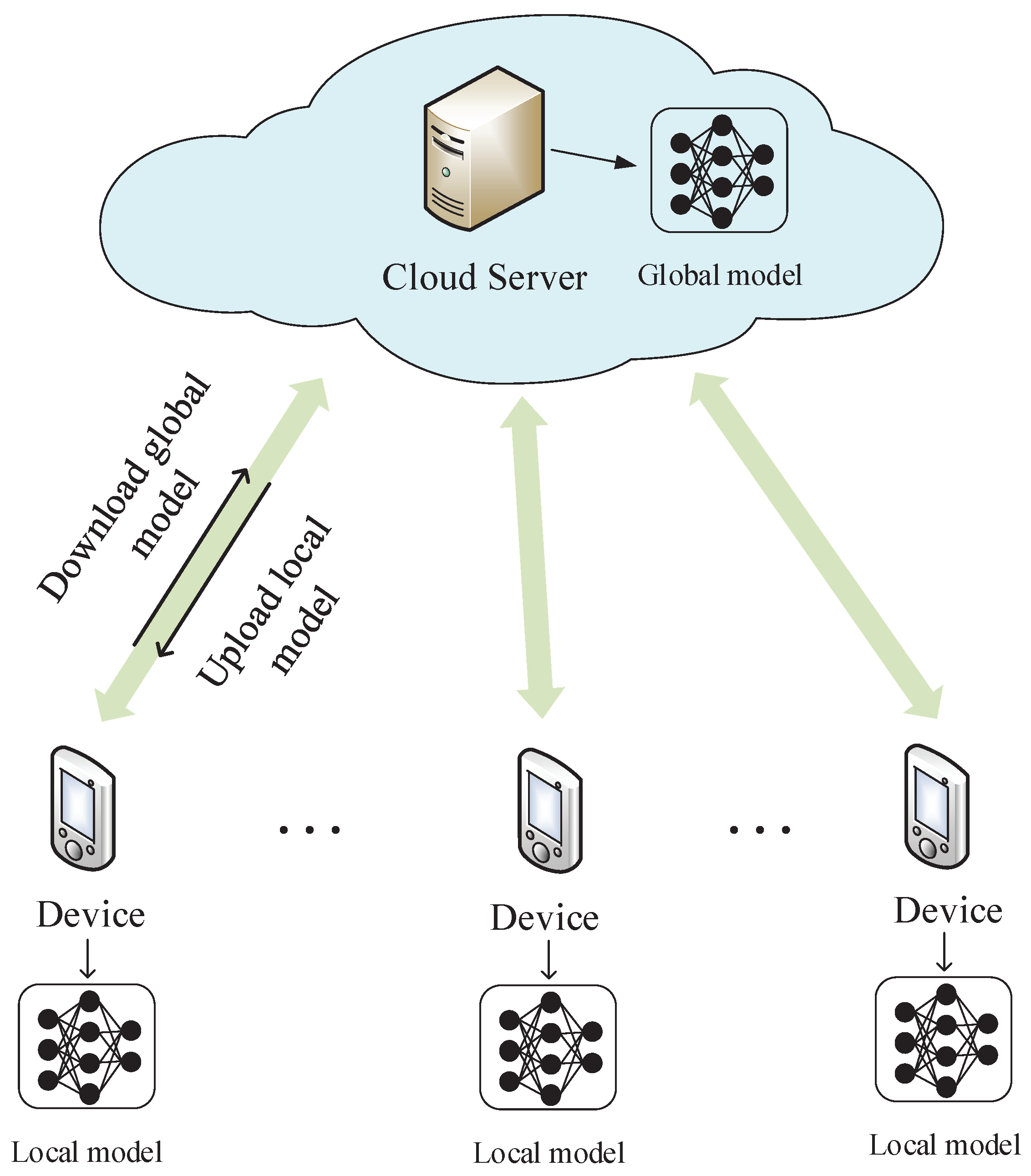
- We proposed a 5G-based AMI system, where the smart meters deployed in different locations can access 5G base stations to transmit data to the cloud server. We also propose a hierarchical federated learning-based approach in the AMI system to enable smart meters to train a shared intrusion detection model collaboratively while maintaining privacy and reducing communication costs.
- A transformer-based intrusion detection model is proposed to improve the detection performance. The proposed model adopts feature extraction layers to extract numerical features and leverage transformer layers to capture the relationship between categorical features, aiming to identify intrusion information effectively.
- We conduct extensive simulations to evaluate the performance of the proposed transformer-based intrusion detection model and its performance in federated learning. The results demonstrate that the proposed model has a better performance in different situations.
2. Related Work
3. System Model and Problem Formulation
3.1. The 5G-Based Advanced Metering Infrastructure System
3.2. Federated Learning-Based Intrusion Detection System and Problem Formulation
4. Proposed Transformer-Based Intrusion Detection Model
4.1. The Transformer-IDM Model
4.2. Hierarchical Federated Learning-Based Intrusion Detection System
| Algorithm 1: HFed-IDS |
 |
5. Performance Evaluation
5.1. Dataset
5.2. Dataset Preprocessing
5.3. Evaluation Metrics
5.4. Setup
5.5. Numerical Results
6. Conclusions and Future Works
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Sun, C.C.; Cardenas, D.J.S.; Hahn, A.; Liu, C.C. Intrusion detection for cybersecurity of smart meters. IEEE Trans. Smart Grid 2020, 12, 612–622. [Google Scholar] [CrossRef]
- Zanetti, M.; Jamhour, E.; Pellenz, M.; Penna, M.; Zambenedetti, V.; Chueiri, I. A tunable fraud detection system for advanced metering infrastructure using short-lived patterns. IEEE Trans. Smart Grid 2017, 10, 830–840. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. IEEE Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Ghorbanian, M.; Dolatabadi, S.H.; Masjedi, M.; Siano, P. Communication in smart grids: A comprehensive review on the existing and future communication and information infrastructures. IEEE Syst. J. 2019, 13, 4001–4014. [Google Scholar] [CrossRef]
- Alahakoon, D.; Yu, X. Smart electricity meter data intelligence for future energy systems: A survey. IEEE Trans. Ind. Inform. 2015, 12, 425–436. [Google Scholar] [CrossRef]
- Das, H.; Saikia, L. GSM enabled smart energy meter and automation of home appliances. In Proceedings of the 2015 International Conference on Energy, Power and Environment: Towards Sustainable Growth (ICEPE), Shillong, India, 12–13 June 2015; pp. 1–5. [Google Scholar]
- Dragičević, T.; Siano, P.; Prabaharan, S. Future generation 5G wireless networks for smart grid: A comprehensive review. Energies 2019, 12, 2140. [Google Scholar]
- Pedramnia, K.; Rahmani, M. Survey of DoS Attacks on LTE infrastructure used in AMI System and Countermeasures. In Proceedings of the 2018 Smart Grid Conference (SGC), Sanandaj, Iran, 28–29 November 2018; pp. 1–6. [Google Scholar]
- Wlazlo, P.; Sahu, A.; Mao, Z.; Huang, H.; Goulart, A.; Davis, K.; Zonouz, S. Man-in-the-middle attacks and defense in a power system cyber-physical testbed. arXiv 2021, arXiv:2102.11455. [Google Scholar]
- Algin, R.; Tan, H.O.; Akkaya, K. Mitigating selective jamming attacks in smart meter data collection using moving target defense. In Proceedings of the 13th ACM Symposium on QoS and Security for Wireless and Mobile Networks, Miami, FL, USA, 21–25 November 2017; pp. 1–8. [Google Scholar]
- Tufail, S.; Batool, S.; Sarwat, A.I. False data injection impact analysis in ai-based smart grid. In Proceedings of the Southeast Con 2021, Atlanta, GA, USA, 10–13 March 2021; pp. 1–7. [Google Scholar]
- Chaudhry, J.; Qidwai, U.; Miraz, M.H. Securing big data from eavesdropping attacks in scada/ics network data streams through impulsive statistical fingerprinting. In Proceedings of the International Conference for Emerging Technologies in Computing, London, UK, 19–20 August 2019; pp. 77–89. [Google Scholar]
- Liu, S.; Liu, X.P.; El Saddik, A. Denial-of-service (DoS) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE PES Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar]
- Zhao, J.; Wang, J.; Yin, L. Detection and control against replay attacks in smart grid. In Proceedings of the 2016 12th International Conference on Computational Intelligence and Security (CIS), Wuxi, China, 16–19 December 2016; pp. 624–627. [Google Scholar]
- Liu, H.; Lang, B. Machine learning and deep learning methods for intrusion detection systems: A survey. Appl. Sci. 2019, 9, 4396. [Google Scholar] [CrossRef] [Green Version]
- Li, Y.; Xue, W.; Wu, T.; Wang, H.; Zhou, B.; Aziz, S.; He, Y. Intrusion detection of cyber physical energy system based on multivariate ensemble classification. Energy 2021, 218, 119505. [Google Scholar] [CrossRef]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; y Arcas, B.A. Communication-efficient learning of deep networks from decentralized data. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, Ft. Lauderdale, FL, USA, 20–22 April 2017; pp. 1273–1282. [Google Scholar]
- Alseiari, F.A.A.; Aung, Z. Real-time anomaly-based distributed intrusion detection systems for advanced Metering Infrastructure utilizing stream data mining. In Proceedings of the 2015 International Conference on Smart Grid and Clean Energy Technologies (ICSGCE), Offenburg, Germany, 20–23 October 2015; pp. 148–153. [Google Scholar]
- Hu, C.; Yan, J.; Wang, C. Advanced cyber-physical attack classification with extreme gradient boosting for smart transmission grids. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019; pp. 1–5. [Google Scholar]
- Vijayanand, R.; Devaraj, D.; Kannapiran, B. Support vector machine based intrusion detection system with reduced input features for advanced metering infrastructure of smart grid. In Proceedings of the 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017; pp. 1–7. [Google Scholar]
- Acosta, M.R.C.; Ahmed, S.; Garcia, C.E.; Koo, I. Extremely randomized trees-based scheme for stealthy cyber-attack detection in smart grid networks. IEEE Access 2020, 8, 19921–19933. [Google Scholar] [CrossRef]
- Zheng, Z.; Yang, Y.; Niu, X.; Dai, H.N.; Zhou, Y. Wide and deep convolutional neural networks for electricity-theft detection to secure smart grids. IEEE Trans. Ind. Inform. 2017, 14, 1606–1615. [Google Scholar] [CrossRef]
- Liu, G.; Zhang, J. CNID: Research of network intrusion detection based on convolutional neural network. Discret. Dyn. Nat. Soc. 2020, 2020, 4705982. [Google Scholar] [CrossRef]
- Thirimanne, S.P.; Jayawardana, L.; Yasakethu, L.; Liyanaarachchi, P.; Hewage, C. Deep Neural Network Based Real-Time Intrusion Detection System. SN Comput. Sci. 2022, 3, 145. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, X.; Wen, W.; Xia, M. Smarter Grid in the 5G Era: Integrating Power Internet of Things with Cyber Physical System. Front. Commun. Netw. 2021, 2, 23. [Google Scholar] [CrossRef]
- Konečnỳ, J.; McMahan, H.B.; Yu, F.X.; Richtárik, P.; Suresh, A.T.; Bacon, D. Federated learning: Strategies for improving communication efficiency. arXiv 2016, arXiv:1610.05492. [Google Scholar]
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, Ł.; Polosukhin, I. Attention is all you need. Adv. Neural Inf. Process. Syst. 2017, 6000–6010. [Google Scholar]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A Survey on Mobile Edge Computing: The Communication Perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef] [Green Version]
- NSL-KDD Dataset. Available online: http://nsl.cs.unb.ca/nsl-kdd/ (accessed on 1 June 2022).
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- Tian, Y.; Mirzabagheri, M.; Bamakan, S.M.H.; Wang, H.; Qu, Q. Ramp loss one-class support vector machine; a robust and effective approach to anomaly detection problems. Neurocomputing 2018, 310, 223–235. [Google Scholar] [CrossRef]
- Serpen, G.; Aghaei, E. Host-based misuse intrusion detection using PCA feature extraction and kNN classification algorithms. Intell. Data Anal. 2018, 22, 1101–1114. [Google Scholar] [CrossRef]
- Panda, M.; Abraham, A.; Patra, M.R. Discriminative multinomial naive bayes for network intrusion detection. In Proceedings of the 2010 Sixth International Conference on Information Assurance and Security, Atlanta, GA, USA, 23–25 August 2010. [Google Scholar]
- Mirzaee, P.H.; Shojafar, M.; Pooranian, Z.; Asefy, P.; Cruickshank, H.; Tafazolli, R. FIDS: A Federated Intrusion Detection System for 5G Smart Metering Network. In Proceedings of the 2021 17th International Conference on Mobility, Sensing and Networking (MSN), Exeter, UK, 13–15 December 2021. [Google Scholar]
- Xu, C.; Shen, J.; Du, X.; Zhang, F. An intrusion detection system using a deep neural network with gated recurrent units. IEEE Access 2018, 6, 48697–48707. [Google Scholar] [CrossRef]





| Type of Features | Features |
|---|---|
| Categorical features | ‘protocol_type’, ‘service’, ‘flag’ |
| Numerical features | ‘duration’, ‘src_bytes’, ‘dst_bytes’, ‘land’, ‘logged_in’, ‘is_host_login’, ‘is_guest_login’, ’wrong_fragment’, ‘urgent’, ‘hot’, ‘num_failed_logins’, ‘num_compromised’, ‘root_shell’, ‘su_attempted’, ‘num_root’, ‘num_file_creations’, ‘num_shells’, ‘num_access_files’, ‘num_outbound_cmds’, ‘count’, ‘srv_count’, ‘serror_rate’, ‘srv_serror_rate’, ‘rerror_rate’, ‘srv_rerror_rate’, ‘same_srv_rate’, ‘diff_srv_rate’, ‘srv_diff_host_rate’, ‘dst_host_count’, ‘dst_host_srv_count’, ‘dst_host_same_srv_rate’, ‘dst_host_diff_srv_rate’, ‘dst_host_same_src_port_rate’, ‘dst_host_srv_diff_host_rate’, ‘dst_host_serror_rate’, ‘dst_host_srv_serror_rate’, ‘dst_host_rerror_rate’, ‘dst_host_srv_rerror_rate’ |
| Dos | Probe | R2L | U2R | Normal |
|---|---|---|---|---|
| back land Neptune pod smurf teardrop | ipsweep nmap portsweep satan | spy warezclient ftpwrite guesspasswd imap multihop phf warezmaster | bufferoverflow loadmodule perl rootkit | normal |
| Attack Categories | Description |
|---|---|
| Denial of service (DoS) | This attack occupies too many computing or memory resources so that the machine cannot handle legitimate requests and access. |
| Probing scanning (Probe) | This attack gathers information about potential vulnerabilities of the target system that can be used to launch attacks lately. |
| Remote to local (R2L) | Attacker does not have access to the victim’s machine, and hence tries to gain local access as a user of that machine. |
| User to root (U2R) | Using this attack, attackers access the system as a normal user and exploit some vulnerability to gain root access to the system. |
| Main Categories | NSL KDD | Training Set | Testing Set |
|---|---|---|---|
| Normal | 67,343 | 33,732 | 33,611 |
| Dos | 45,927 | 22,821 | 23,106 |
| Probe | 11,656 | 5933 | 5723 |
| R2L | 995 | 473 | 522 |
| U2R | 52 | 27 | 25 |
| Total | 125,973 | 62,986 | 62,987 |
| Evaluation Metrics (%) | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Models | ||||||||||||
| DoS | Probing | R2L | U2R | DoS | Probing | R2L | U2R | DoS | Probing | R2L | U2R | |
| SVM | 99.04 | 96.63 | 80.33 | 64.28 | 98.21 | 95.05 | 55.56 | 35.00 | 98.63 | 95.83 | 65.69 | 46.15 |
| LR | 99.08 | 97.28 | 79.35 | 72.73 | 97.89 | 95.70 | 75.09 | 32.00 | 98.48 | 96.48 | 77.16 | 44.44 |
| KNN | 98.77 | 98.68 | 87.16 | 61.54 | 99.45 | 96.69 | 67.62 | 32.00 | 99.11 | 97.67 | 76.16 | 42.11 |
| MultinomialNB | 97.72 | 56.31 | 26.63 | 16.36 | 84.24 | 91.32 | 31.23 | 36.00 | 90.48 | 96.67 | 28.75 | 22.50 |
| DNN-3 | 99.73 | 98.06 | 79.33 | 15.79 | 98.38 | 97.45 | 72.80 | 12.00 | 99.03 | 97.76 | 75.92 | 13.63 |
| GRU+MLP | 99.30 | 97.53 | 78.45 | 11.76 | 98.05 | 96.54 | 54.41 | 8.00 | 98.67 | 97.03 | 64.25 | 9.52 |
| DNN-16 | 99.55 | 98.61 | 81.79 | 18.75 | 99.46 | 98.74 | 55.94 | 12.00 | 99.51 | 98.67 | 66.44 | 14.63 |
| Transformer-IDM | 99.85 | 98.76 | 87.21 | 78.57 | 99.91 | 98.85 | 87.55 | 44.00 | 99.88 | 98.81 | 87.38 | 56.41 |
| Models | P (%) | (%) | F (%) | (%) |
|---|---|---|---|---|
| SVM | 97.76 | 97.8 | 97.76 | 97.81 |
| LR | 97.94 | 97.95 | 97.94 | 97.95 |
| KNN | 98.76 | 98.79 | 98.76 | 98.79 |
| MultinomialNB | 91.09 | 88.65 | 89.31 | 88.65 |
| DNN-3 | 98.48 | 98.49 | 98.48 | 98.5 |
| GRU+MLP | 97.98 | 98.04 | 97.99 | 98.05 |
| DNN-16 | 98.86 | 98.91 | 98.86 | 98.92 |
| Transformer-IDM | 99.49 | 99.49 | 99.49 | 99.48 |
| Evaluation Metrics (%) | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Models | ||||||||||||
| DoS | Probing | R2L | U2R | DoS | Probing | R2L | U2R | DoS | Probing | R2L | U2R | |
| Fed-DNN-3 | 99.74 | 97.99 | 81.34 | 21.05 | 98.33 | 97.39 | 74.33 | 16.00 | 99.03 | 97.69 | 77.68 | 18.18 |
| Fed-GRU+MLP | 99.39 | 97.51 | 79.82 | 20.00 | 97.94 | 96.37 | 52.29 | 16.00 | 98.66 | 96.93 | 63.19 | 17.78 |
| Fed-DNN-16 | 99.75 | 98.57 | 80.25 | 25.00 | 98.70 | 98.62 | 72.41 | 16.00 | 99.22 | 98.59 | 76.13 | 19.51 |
| Fed-Transformer-IDM | 99.87 | 98.86 | 87.36 | 80.00 | 99.91 | 98.64 | 87.36 | 48.00 | 99.89 | 98.75 | 87.36 | 60.00 |
| Models | P (%) | (%) | F (%) | (%) | Total_Params |
|---|---|---|---|---|---|
| Fed-DNN-3 | 98.50 | 98.51 | 98.5 | 98.51 | 26,935 |
| Fed-GRU+MLP | 97.98 | 98.03 | 97.97 | 98.03 | 105,557 |
| Fed-DNN-16 | 98.76 | 98.78 | 98.76 | 98.78 | 636,037 |
| Fed-Transformer-IDM | 99.49 | 99.49 | 99.49 | 99.49 | 20,503 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, X.; Tang, Z.; Du, M.; Deng, C.; Lin, W.; Chen, J.; Qi, Q.; Zheng, H. A Hierarchical Federated Learning-Based Intrusion Detection System for 5G Smart Grids. Electronics 2022, 11, 2627. https://doi.org/10.3390/electronics11162627
Sun X, Tang Z, Du M, Deng C, Lin W, Chen J, Qi Q, Zheng H. A Hierarchical Federated Learning-Based Intrusion Detection System for 5G Smart Grids. Electronics. 2022; 11(16):2627. https://doi.org/10.3390/electronics11162627
Chicago/Turabian StyleSun, Xin, Zhijun Tang, Mengxuan Du, Chaoping Deng, Wenbin Lin, Jinshan Chen, Qi Qi, and Haifeng Zheng. 2022. "A Hierarchical Federated Learning-Based Intrusion Detection System for 5G Smart Grids" Electronics 11, no. 16: 2627. https://doi.org/10.3390/electronics11162627
APA StyleSun, X., Tang, Z., Du, M., Deng, C., Lin, W., Chen, J., Qi, Q., & Zheng, H. (2022). A Hierarchical Federated Learning-Based Intrusion Detection System for 5G Smart Grids. Electronics, 11(16), 2627. https://doi.org/10.3390/electronics11162627






