2. Principles of Cryptographic Algorithms
In the history of the development of cryptography, classical cryptography is constructed by simple logical substitution and mathematical calculations, and modern cryptography has a strict and perfect mathematical foundation and structural system to ensure information security. The symmetric encryption algorithm AES, the asymmetric encryption algorithm ECC, and the chip authentication algorithm SRAM PUF used in this design have rigorous mathematical principles. This section will introduce the algorithm principles of AES, ECC, and PUF in detail. The introduction of the basic principles provides a solid theoretical basis for the subsequent development of the content.
2.1. AES Encryption and Decryption Principles
AES is categorized as AES-128, AES-192, or AES-256 based on the key length. The cipher of these different types share the same size of a 128-bit block, but their key sizes are 128, 192, and 256 bits, respectively. AES with a longer key takes longer to compute but is more secure for data. In field applications, the length needs to be traded off according to the encryption speed needs and the encryption level requirements.
Figure 1 illustrates the general process of AES encryption and decryption. A number of repetitions of transformation rounds convert the input plaintext into the final output ciphertext. Each round consists of several standard processing steps, including “SubBytes”, “ShiftRows”, “MixColumns”, and “AddRoundKey”. A set of reverse rounds are applied to transform ciphertext back into the original plaintext using the same encryption key.
2.2. ECC Protocols
Figure 2 illustrates the ECC algorithm structure, which can be divided into the modular computing layer, the elliptic curve arithmetic layer, and the protocol layer.
The modular computing layer constitutes the basic operations including modular multiplication(Mod Mul), modular add/sub(Mod Add/Sub) and modular inversion(Mod Inv) of binary field . The NIST-recommended binary fields of ECC include , , , and , and are most commonly used. A longer bit width leads to a stronger safety level, but the difficulty and complexity of the basic calculations also increase exponentially. In practice, the binary field of ECC needs to be traded off according to encryption speed requirements and safety level requirements.
The elliptic curve arithmetic layer includes point addition, point doubling, and point multiplication on the elliptic curve. Point multiplication is a combination of point addition and point doubling, each of which is a combination of the basic modular operations in the modular computing layer. Due to the difficulty of the elliptic curve discrete logarithm problem, the complexity of the elliptic curve PM reverse solution is much greater than the complexity of the forward solution. Based on this nature, asymmetric private-public key pairs can be generated, ensuring the security and reliability of keys.
Eventually, various ECC protocols can be accomplished by point operations in the elliptic curve arithmetic layer. The majority of these protocols include Elliptic Curve Diffie–Hellman Keyma Exchange (ECDH), the Elliptic Curve Digital Signature Algorithm (ECDSA), etc. This design implements the ECDH-based encryption algorithm and ECDSA algorithm, which are described separately.
2.2.1. ECDH-Based Encryption Algorithm
Figure 3 illustrates the overall flow of the ECDH-based encryption and decryption algorithm. Only the public key, ciphertext, and curve information are passed through the channel. Even if the eavesdroppers launch an attack, the plaintext cannot be obtained without the private key. This is a full reflection of the security advantages of asymmetric keys.
ECDH is a key exchange protocol performed on elliptic curves. Suppose that two people, Alice and Bob, wish to exchange a secret key with each other. Alice generates a private key and a public key (where G is the base point of the curve). If Alice send the public key to Bob, he can obtain with his private key . Similarly, if Bob sends the public key , Alice can obtain point . Because , Alice and Bob can obtain the same information using ECDH. Therefore if valuable secret information is encrypted by the calculated points and , any eavesdropper would only have access to the public key and the base point in the channel, which are not sufficient to obtain the real encryption key of the shared secret information.
To take this one step further, if the secret data are involved in the ECDH process, ECDH-based data encryption can be achieved. Suppose that two people, Alice and Bob, wish to exchange secret data with each other. Alice has a private key d and sends the public key H over the channel to Bob. Bob maps the plaintext m to a point on the elliptic curve using plaintext embedding. After that, Bob selects a random number r less than the order n as his private key, and calculates the point and , corresponding to the shared secret information S and the public key in the ECDH algorithm. In this way, the plaintext is mixed into shared secret information by a point addition. Finally, Bob uses and as ciphertexts and sends them back to Alice to complete the data encryption.
The ECDH-based decryption algorithm works in the following way: Alice uses her private key and the received ciphertext to calculate
. Substitute the formulas
,
, and
into
to obtain:
Therefore, calculating can help to find Bob’s plaintext embedding point M and then recover the plaintext m to complete decryption.
2.2.2. ECDSA
ECDSA uses elliptic curves to create a signature on the data. The signature ensures that the message content has not been tampered with by a third party. Anyone can verify its authenticity without compromising security.
Figure 4 illustrates the overall process of the ECDSA signature and verification, which only passes the public key and signature in the channel, ensuring the privacy of the private key.
To create an ECDSA signature, the sender of the message, Alice, will perform the following steps:
Select a random number k, complete PM to obtain the point and the x coordinate of P;
Calculate the first non-zero signature value ;
Perform a HASH operation on the message m to obtain its digest value z;
Calculate the second non-zero signature value ;
Send the public key H, message m and signature to Bob.
To verify an ECDSA signature, the recipient, Bob, will perform the following steps:
Perform a HASH operation on the message m to obtain its digest value z;
Calculate and ;
Calculate ;
Compare the x coordinate value of P with the signature r. If they are equal, the verification is passed. If they are not equal, the verification fails.
The principle of the ECDSA verification can be deduced by expanding the
P:
Substitute
into the formula of
P, and the following formula can be obtained:
From the deduction above, it is clear that the P in the signature stage and the P in the verification stage are the same points obtained through different calculation methods. Therefore, whether is established can determine whether the ECDSA verification is passed.
2.3. SRAM PUF Soft-Decision Algorithm
The SRAM power-on value is unique due to random differences caused by process deviations during manufacturing. Based on this principle, SRAM PUF uses the SRAM initial value to build PUF and achieves the chip authentication function.
SRAM PUF is sensitive to noise. Ambient noise can reverse some SRAM units that are not strongly biased toward “1” or “0”, so the initial value of SRAM is different at each power-on. SRAM tests were carried out in [
41,
42] at different temperatures, which led to the conclusion that the probability of error is between 3% and 15%. As the temperature decreases, the probability of error may be higher. However, when SRAM PUF is used as a chip key or for identity authentication, a fixed value must be guaranteed for each power-on. Therefore, error correction codes are used to correct the initial SRAM power-on value and solve the problem of unstable SRAM PUF output. Bosch completed SRAM PUF error correction on hardware for the first time with the Helper Data Algorithm (HDA) [
43]. The principle of HDA is to use helper data to map the SRAM PUF to a codeword of the error correction code. Moreover, HDA can ensure that the helper data do not cause SRAM PUF information leakage.
It is stated in [
44] that the error of each bit in SRAM is not entirely random. Most of the bits are very stable, and the power-on value of only some bits changes frequently. Therefore, HDA usually uses a soft-decision method. The principle of soft-decision HDA is to sample the data multiple times and record the error probability of each bit. The error correction code can work more efficiently and generate more accurate results by considering the error probability [
44,
45]. For SRAM, error probability can be easily obtained by simply powering on and counting repeatedly, which makes soft-decision HDA very practical. The specific algorithm of soft-decision HDA is as follows, which is divided into an enrollment stage and a recovery stage, as shown in
Figure 5.
Enrollment stage: Select an SRAM initial value y as the standard value, which is the target value to be corrected during the recovery stage. Repeat the SRAM power-on 100 times and record the error probabilities of each bit between the initial value of each time and y. Then, randomly select a codeword c of Reed–Muller code, calculate the helper data , and save w, P to FLASH. Since P is the probability of an error occurring between each SRAM value, it is impossible to determine whether a particular bit is “1” or “0”, so P does not affect the overall security. The statistical process of P and the writing process of w and P should be performed at manufacturing.
Recovery stage: After the chip is delivered to the user, a random SRAM initial value is obtained during each power-on. Due to the initial value bit error rate, the SRAM initial value is different from y. Calculate , and the result is an RM codeword with an error. Use P and for RM soft-decision error correction to obtain the correct code word c. The P provides more information for the RM code, thereby improving the error correction ability. After the error correction is complete, the correct PUF value can be calculated.
3. Optimization and Application of Cryptographic Algorithms Based on Image Real-Time Acquisition Chips
For modern high-resolution real-time images, the data throughput is enormous. For example, in the image processing of 5 RGB888 consecutive images per second with a resolution of 4K, the throughput is as high as
132.7 MB/s. The JPEG algorithm’s image throughput with a 50% compression ratio is also as high as 66.4 MB/s. To support this throughput on a digital circuit with a clock frequency of 500 MHz, the encryption rate requirement is as high as
bits per cycle. Symmetric encryption algorithms operate faster than asymmetric encryption algorithms and can meet the requirement of such data throughput. The hardware design of AES-128 can complete encryption every ten cycles [
46], which can be seen as a processing speed of
bits per cycle, meeting the encryption rate requirement of
bits per cycle and leaving enough of a margin. On the contrary, even the fastest ECC hardware implementation requires thousands of cycles to complete encryption on
[
17], which can be seen as less than 0.1 bits per cycle, and is far from meeting the speed requirement of real-time image encryption. Therefore, the symmetric encryption algorithm AES is a better choice in a real-time image encryption scenario. However, there is a risk of exposure to AES private keys during transmission. Once the key is intercepted by an attacker, the security of the entire chip is under threat. Therefore a solution to increase the security level of AES is necessary. In this design, the asymmetric algorithm ECC is used to encrypt the AES private key to solve this problem. To further guarantee the safety of the entire high-speed hardware design, the secure chip authentication PUF algorithm is also required to prevent chip cloning.
In summary, this section provided the algorithm base of a triple-hybrid encryption system with the combinations of AES, ECC, and PUF. In addition, these three classic encryption algorithms are optimized according to the image real-time acquisition chip scenario to increase safety performance, calculation speed, and resource utilization. The proposed optimized algorithms include modified AES with private key encryption by ECC, a modified AES-based pseudo-random number generator (PRNG), ECC PM optimization, custom ECDSA algorithm, and a fast ECDSA-PUF algorithm. In the following subsection, the triple-hybrid encryption system is introduced first. Afterward, the principle and function of each optimized algorithm in the triple-hybrid encryption system are introduced in detail.
3.1. Proposed Triple-Hybrid Encryption System Based on Image Encryption
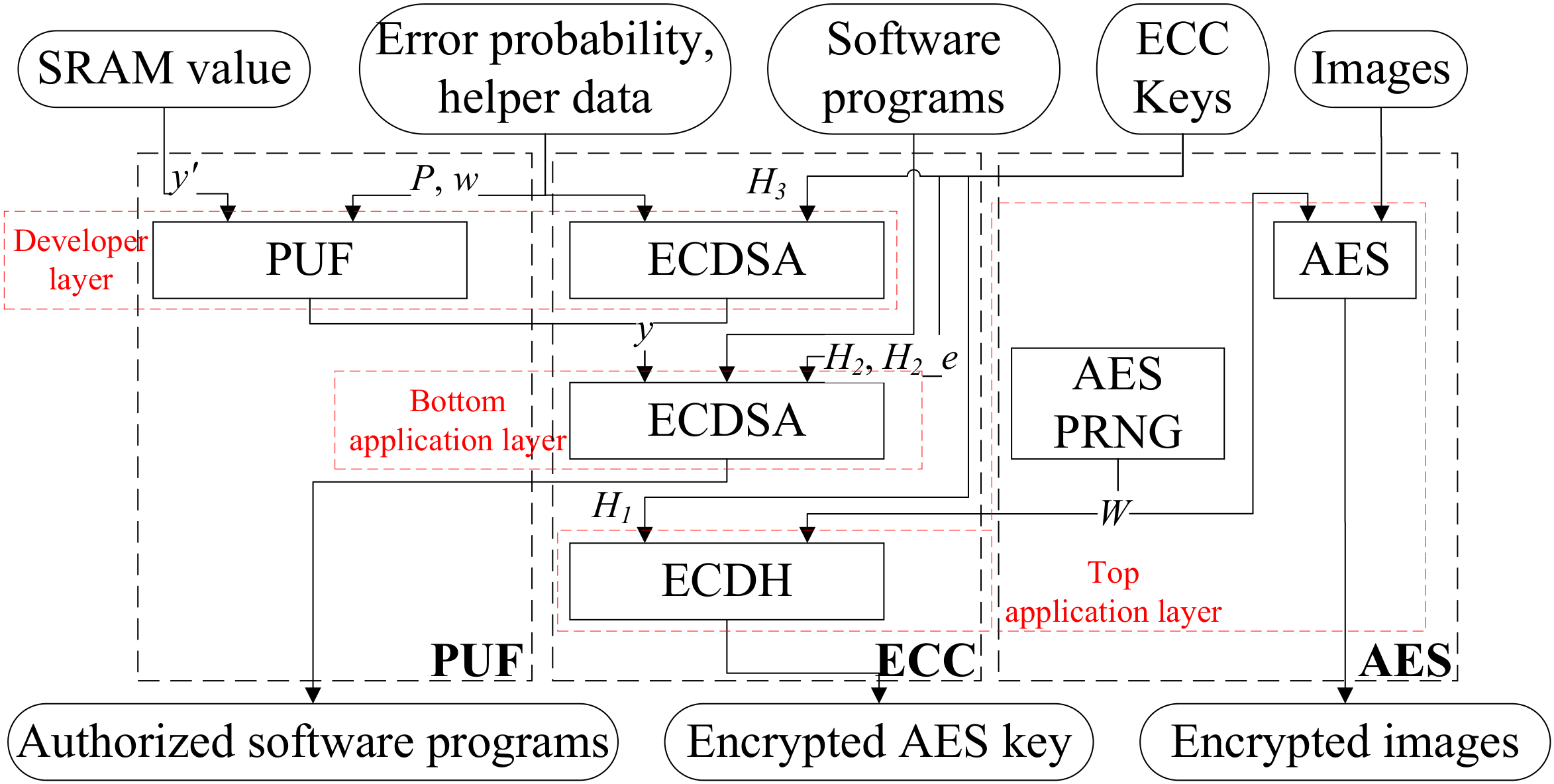
Figure 6 illustrates the proposed original triple-hybrid encryption system. The encryption system has three layers. The top application layer based on ECC and AES algorithms is responsible for image data encryption. The bottom application layer is responsible for hardware authorization by using the ECC algorithm. The developer layer is responsible for generating PUF and it involves ECC and PUF algorithms. The details of the three layers of the encryption system are introduced in the following parts.
Figure 7 illustrates the overall flow.
The top application layer uses the ECDH algorithm to encrypt the AES private key, which is then used to encrypt image data. The specific steps are as follows:
The user saves an ECC private key in the host computer, which then generates an ECC public key and sends it to the real-time image acquisition chip.
The image real-time acquisition chip uses a modified AES-based PRNG hardware which consists of one LSFR and two AES to generate a random number W as the private key of the AES used to encrypt image data. The AES private key and the received public key undergo ECDH-based encryption, and the results are sent back to the host computer.
After receiving the “ECDH-encrypted AES private key” and “AES encrypted image data”, the host computer uses the ECC private key to decrypt the AES private key, which is then used to decrypt the image data.
If the users want to update the AES private key, the image real-time acquisition chip repeats step 2. A new pair of “AES private key cipher after ECDH encryption and AES encrypted image datum” is obtained and the host computer reads the new pair of datum for decryption.
The bottom application layer is used to authorize hardware and prevent attackers from using unauthorized hardware. {Program, PUF value y} (concatenate Program and y) are verified by custom-ECDSA to prove that the hardware belongs to authorized users, an original algorithm proposed in this paper. Only when the custom-ECDSA verification is passed can the software program jump to the main function flow. Otherwise, the CPU will not be able to run the software program. The hardware authorization process is divided into the user enrollment stage and the user activation stage.
At the user enrollment stage, the authorization of the hardware has not been completed. The developer holds the private key and users cannot obtain it. The custom ECDSA verification uses the solidified public key , so only the developer can make the program pass the verification and enter the main function. To authorize users, the developer assigns a pair of key and to users and write to the one-time programmable (OTP) device. At the user activation stage, the authorized user signs {Program, y} with provided by the developer. The hardware verifies the {Program, y} with , which has been solidified in the OTP device. Passing the verification indicates that the program is valid and proves that the current user has been authorized.
In the bottom application layer, we proposed an innovative application of PUF technology. Since the PUF value is used as a part of the message, the same software program and signature cannot be successfully verified on different chips due to changes in the PUF value, which further prevents unauthorized attackers from using the chip. If an attacker steals an authorized user’s software program and signature, the software program will still not execute properly on another unauthorized hardware.
The developer layer uses fast ECDSA-PUF, an originally proposed algorithm, to prevent an attacker from tampering with the PUF to pass the custom ECDSA of the bottom application layer. The developer signs the error probability P and the helper data w with an ECC private key . The hardware uses public key in the ROM to verify P and w. If the verification is passed, the PUF value y is valid.
In summary, the triple-hybrid encryption system mixes AES, ECC, and PUF algorithms. In terms of performance, the chip executes the bottom application layer and developer layer only once in the software bootloader. After that, the chip repeatedly performs the image encryption requests at the top application layer. The encryption system does not reduce the efficiency due to the multi-level algorithm, which ensures the system’s performance. In terms of security, each layer of the system is interconnected. As shown in
Figure 8, problems at the upper layer are resolved in the lower layers. The failure of any link in the system will lead to authentication failure of the entire system, which significantly increases the difficulty of attacking and improves the system security.
In the following subsections, the principles of each optimized algorithm used in the triple-hybrid encryption system are introduced sequentially.
3.2. AES Optimization and Application
3.2.1. AES Key Encryption
To solve the security problem of AES key, it is common practice to encrypt this key with an asymmetric encryption algorithm [
32]. The novelty in this paper lies in the slow ECDH encryption used to encrypt the key. Since the slow process will only execute once in AES key encryption and once in AES key decryption, while the data encryption and decryption use the fast AES algorithm, the security problem is solved without dragging down the data processing speed.
3.2.2. Modified AES-Based PRNG
Since PRNG is used to generate AES keys in the triple-hybrid encryption system, it is essential to pay attention to the security of PRNG. PRNG needs to be practical and lightweight. The Linear Feedback Shift Register (LFSR) has a minor hardware overhead and is widely used to generate random numbers. However, Meier and Staffelbach proposed a rapidly related attack method for LFSR [
47], which reduced the time complexity of cracking LFSR to
. Todo optimized the rapid correlation attack method to achieve a more effective attack on LFSR [
48]. Therefore, using the output of LFSR as the key of the cryptography system poses a great threat.
To further protect LFSR, an AES-based PRNG is proposed, based on the research result of [
49], which states that random numbers will have sufficient redundancy after two AES encryption processes and cannot be inferred.
Figure 9 illustrates the proposed AES-based PRNG. LFSR generates two different random numbers from two different cycles, one is used as the plaintext of the first AES, and the other is used as the key of the first AES. The first AES generates two ciphertexts from two cycles, which are used as the plaintext and the key of the second AES. Eventually, the ciphertext output of the second AES is the secure random number. Since an AES module already exists in the AES key encryption circuit, that AES module can be re-used in this AES-based PRNG encryption when that part is idle. In this way, the reliability of the random generator is greatly increased without adding additional hardware overhead.
3.3. ECC Optimization and Application
Since the ECC in our design does not affect the system encryption speed, its design purpose is more cost-dominant. As a result, ECC is implemented on the binary field , which has the lowest bit-width and thus lowest complexity in all NIST-recommended binary field ECC. Since the difficulty of cracking ECC on is still much bigger than cracking AES, such selection will reduce the hardware yield, but will not affect the system’s safety.
Since modular inversion operation is one of the most complex and resource-consuming operations in ECC, and no projected coordinate system can avoid it, this paper proposes a new method that completely removes modular inversion calculations in ECDSA hardware. The proposed method is custom ECDSA, which modifies some ECDSA steps while ensuring safety. The ECDSA protocol can be modified because both the sender and receiver of ECDSA in a triple-hybrid encryption system are the hardware owners. The local-based protocol does not need to agree with the receiver in the open channel so that the protocol can be customized. Furthermore, the proposed protocol customization method is non-public, which also increases the difficulty of cracking.
Custom ECDSA removes two modular inversions in the protocol.
Figure 10 illustrates the process of custom ECDSA, where Alice is the host computer and Bob is the chip. The first modular inversion to be removed is the calculation of
in ECDSA verification when the projected coordinate system is restored to the affine coordinate system. The custom ECDSA protocol verifies whether
is equal to
X (
are the projected coordinate values of the point
P) instead of whether
is equal to
r. The second modular inversion to be removed is the calculation of
in the ECDSA signature formula. In the triple-hybrid encryption system, the image real-time acquisition chip only needs to perform the verification, and the signature is completed on the host computer. Therefore,
can be calculated in advance on the host computer, and then sent to the chip and saved as a signature. Similarly,
can also be pre-calculated on the host and sent to the chip. Based on the improvements above, the optimized verification no more has modular inversion operation, which reduces the overhead of the image real-time acquisition chip and improves the speed.
3.4. SRAM PUF Optimization and Application
3.4.1. Risks of SRAM PUF
SRAM PUF soft-decision is based on the premise that SRAM is secure and invisible outside the chip. However, SRAM is directly connected to the CPU in the image real-time acquisition chip. Attackers can read it using software or even probes or SEM for invaded forced reads. Once the attacker reads the SRAM, is fetched. The attacker then uses the same method to read FLASH to obtain w and P and calculates with . Finally the attacker obtains all SRAM PUF-related data y, , c. Since the soft-decision algorithm adds P, the attacker can modify P to indirectly control the corrected c to modify y, achieving the effect of cloning PUF.
3.4.2. Optimized Fast ECDSA-PUF
The triple-hybrid encryption system proposes an ECDSA-based soft-decision SRAM PUF (ECDSA-PUF) algorithm, which signs the helper data w and the error probability P with ECDSA. SRAM PUF must perform ECDSA verification on w and P before each generation. Under the protection of ECDSA, even if an attacker modifies w and P in FLASH, it is impossible to generate a valid ECDSA signature and verify SRAM PUF successfully. In this way, a cloning attack is prevented.
Figure 11 illustrates the optimized fast ECDSA-PUF algorithm. The fast ECDSA-PUF algorithm reuses the custom ECDSA already in the triple-hybrid encryption system, so only a small area increment is induced. As for speed, since some steps in custom ECDSA are moved to the enrollment stage which is calculated before leaving the factory, the computation time it takes in the recovery stage on the chip is shorter than normal ECDSA. Therefore, integrating custom ECDSA in PUF greatly increases the safety level of SRAM PUF, at the price of a little more boot time, which is bearable.
Since the custom ECDSA verification in ECDSA-PUF uses the result whether
X is equal to
, such a single-bit signal is vulnerable to direct attack and modification in the circuit layout, which will thereby modify the correctness of the entire ECDSA-PUF. In order to solve this problem, the ECDSA-PUF adds
X and
in different places of the algorithm’s formula, as highlighted in red in
Figure 11. If
, two XOR will be eliminated, and the correct PUF value can eventually be obtained. This optimization method can improve the overall complexity and safety level without adding redundant circuits.