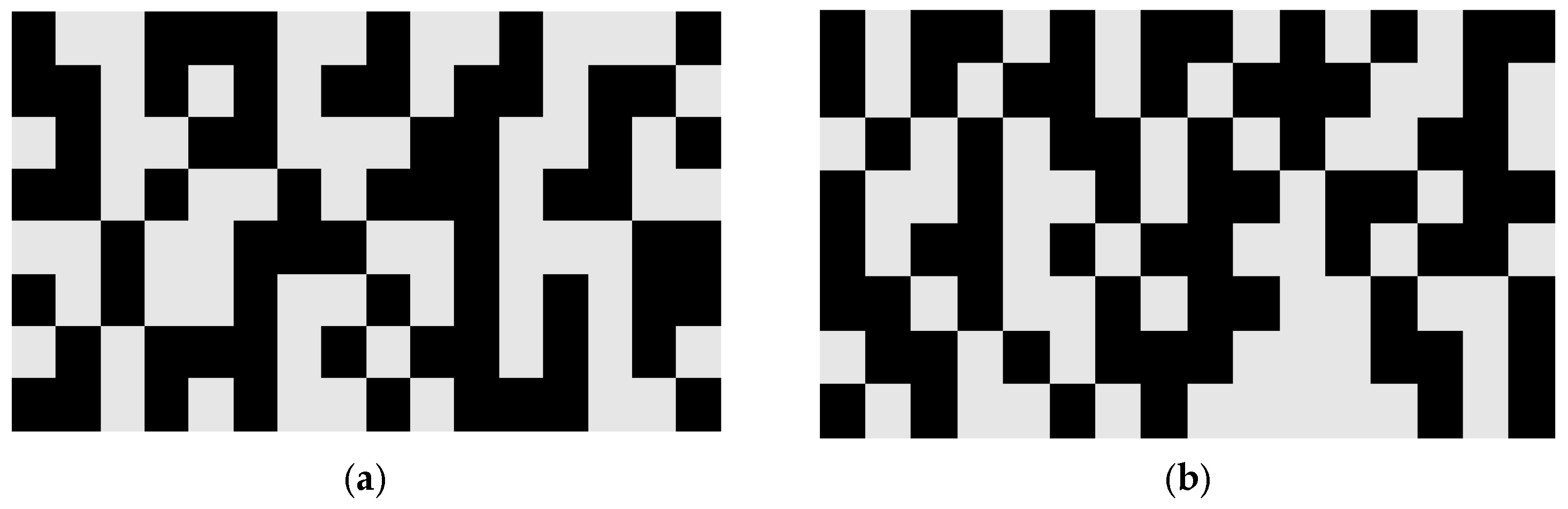1. Introduction
The privacy of information and resources in traditional networks and cloud-based networks are of the highest priority requirement in current day scenarios. As a substantially big amount of data is generated, transferred and stored, we need better and efficient security algorithms to secure them. With the advancement of the processing capabilities of the current systems and the availability of better hardwires, we should develop new security algorithms to leverage these resources. Cryptography is the most suitable tool for neutralizing security threats. Two main types of cryptographic techniques are public-key or asymmetric-key cryptography and secret-key or symmetric-key or private-key cryptography. Block ciphers and stream ciphers are two different categories of encryptions used in private-key cryptography. The data or plain text are split into multiple equal-sized blocks in a block cipher, and encryption or decryption is conducted block by block. The encryption and decryption of a stream cipher take place in a sequence of bits or bytes. A cellular automaton is a discrete parallel computation model composed of a finite array of n cells.
Wolfram [
1] proposed a stream cipher encryption algorithm based on cellular automation. He developed a cellular automata-based pseudorandom number generator. Guan [
2] presented a public cipher system based on cellular automation, in which the algorithm’s strength was determined by solving a series of nonlinear polynomial equations, which are difficult to solve. Das [
3] described a method for the vector space theoretic analysis of additive cellular automata, as well as its applications in the development of pseudoexhaustive test patterns. The work of S. Nandi [
4] and M. Tomassini [
5] explained different applications of cellular automata in the area of cryptography. Seredynski [
6,
7,
8] proposed a block encryption system using cellular automata and the design of an S-box using cellular automata and improved the performance of the S-box. P. Anghelescu [
9] offered a hybrid additive cellular automata technique to block encryption. D. Das and A. Ray [
10] presented a programmatically configurable parallel block encryption algorithm. The works by S. Roy and S. Nandi [
11] explained a symmetric key cryptography application of cellular automata. Suman Rani [
12] and S. Umira [
13] represented applications of quantum-dot cellular automata. Yingri Su [
14] presented a new approach for image encryption for a similarity search using cellular automata. Naskar [
15] presented a new image encryption technique using tent maps and cellular automata. A. Kumar and N. S. Raghava [
16] presented an image encryption technique based on a new substitution box. It produced very good results in real-time encryption scenarios. Nanda et al. [
17] presented a cellular automata-based algorithm based on a pair of reversible cellular automata.
Ahmed Fathy et al. [
18] Presented an enhanced AES algorithm using hardware implementation. Priyadarshini Patila et al. [
19] presented a study on different popular encryption algorithms and found that RSA was the slowest and AES was the fastest algorithm. Sarika Y. Bonde and U. S. Bhadade [
20] compared SRNN and RSA and found that RSA was the slowest. Chinnandi Arul Murugan and P. Karthigai Kumar [
21] showed that bio-cryptographic algorithms can enhance the performance of the AES algorithm. Yongzhi Fu et al. [
22] designed a new AES reconfigurable processor that produced a very high performance. Md. Ahsan Ayub et al. [
23] implemented an RSA algorithm in a parallel environment.
The recent related work shows that very little work has been conducted to improve the performance of encryption algorithms using software implementation and specially using reversible cellular automata techniques. Most of the parallel encryption algorithms focus on the design of new hardware architecture to improve performance and recent cellular automata-based encryption algorithms focus on implementation security mainly in image encryption and not on the parallel implementation of it.
In this work, we designed a throughput optimized block encryption technique using reversible cellular automata and compared its performance with Seredynski [
6] because it is similar to our proposed algorithm and can be used for the encryption of any kind of data whereas other algorithms focus on either texts or images, as was the case with our previous RCA-based algorithm [
17]. We tested its performance in both 8 core and 64 core CPU systems and found that it had a better throughput. Our encryption system produced plaintext blocks that were immune to other blocks during cryptanalysis because of segmentation and the use of the different random numbers as seeds.
The work organized as follows: Section II provides the theoretical basis for the method of cellular automation. We present our proposed work in Section III, which was to develop a reversible cellular automaton block encryption algorithm based on an optimized throughput. A discussion on the findings obtained is in Section IV. Lastly, Section V concludes the presented work and focuses on its future scope.
2. Background of Cellular Automation
Wolfram [
1] described the early examples of cellular automaton. They were very simple to implement and had a basic structure. Cellular automata were the subject of many scientific papers during the last few decades. The study of cellular automaton was carried out by various researchers from different disciplines.
In this work, we utilized cellular automata to develop an algorithm to perform cryptographic operations on the text. We selected a very strong cryptographic rule that was simple to implement.
2.1. Cellular Automation
A discrete parallel computation model built of a finite array of n cells is known as one-dimensional cellular automation. In a discrete amount of time (t), each cell communicates with its neighbors. Each center cell x updates its state s1∈ {0, 1} by applying a local rule and a radius(r1). For radius r1, the neighborhood consists of a total of 2*r1+1 numbers of cells, including the central cell x. If the radius = 1, then it is called one-dimensional cellular automation and the neighborhood consists of a central cell and one cell each towards the left and right.
Figure 1 depicts the transition of states in finite-size cellular automata with periodic boundaries. The center cell’s transition from stage 0 to stage 1 is determined by the stage 0 neighborhood and a transition function known as the “cellular automata rule”. The pseudorandom number was generated by Wolfram [
1] using rule 30 of cellular automata with a radius of one. The working procedure of cellular automation with a periodic boundary using rule 90 and a radius = 1 is shown in
Figure 1.
2.2. Reversible Cellular Automata
In reversible cellular automata, by implementing a rule to individual cells Ci of a configuration CF
i, we can produce a new configuration CF
i+1. This change in state or configuration is represented by a universal transition function. In reversible cellular automaton, the universal transition function is 1 to 1, which means that for every configuration there exists only one forward configuration and one backward configuration. In one-dimensional cellular automation with r1 as the radius, we can generate 2
n numbers of rules, where n = 2
2*r1+1. Therefore, for the radius of one, we can generate 256 cellular automata rules. All these 256 rules do not show the reversible property. The study shows that only six rules out of all the possible rules are reversible and can be used in cryptographic applications. Reversible cellular automata rules are a pair of rules where one rule helps us to transit in the forward direction and the other one in its opposite direction, and therefore may be utilized successfully in cryptographic encryption and decryption.
Figure 2 depicts the fundamental concept of forward and reverse iteration in cryptography.
Wolfram [
1] categorized all cellular automata rules into different classes and one of the classes belonged to the reversible category. If R1 is one rule, then the reversible rule R2 can be easily calculated by the following equation:
3. Proposed Algorithm
The cellular automata-based algorithms [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17] inherently support parallel computing architecture but their implementation never focuses on parallel computation. The traditional popular security algorithms are designed to achieve more security, but performance is not a criterion, as it uses a complex operation during implementation and uses multiple keys. The parallel encryption techniques [
18,
19,
20,
21,
22,
23] focus more on new hardware design than software implementation. The shortcomings of the previous algorithms are more complex processes, a lack of effective parallel computation and the use of many keys. Private key cryptography is used in the suggested algorithm. This algorithm uses two pairs of keys, Key-1 and Key-2, with its reversible keys. Both Key-1 and Key-2 are private and mutually shared with the senders and receivers. This algorithm is based on the encryption of 128 bit blocks of data but it can be easily extended to higher numbers of bits, which are multiples of two. The usage of a 128-bit random number, which may be produced by any efficient random number generator, is the most significant component of this technique.
The algorithm uses simple operations and is straightforward, which results in modularity and helps us provide individual blocks of plaintext to execute in multiple cores to produce a better throughput. The operation and algorithms are simple but the use of a 128 bit random number with each block and use of CBC mode makes the algorithm very difficult to break. In CBC, the input to the encryption algorithm is the result of an XOR operation with the previous ciphertext block and the current plaintext block. To encrypt the first plaintext block, we used an initialization vector (IV) as well as an XOR IV with the plaintext block and gave the input to the encryption process to produce the first ciphertext block. Then, the first ciphertext block was used with XOR with the second plaintext block as the input to the encryption process to produce the second ciphertext block.
Initially, we converted the plain text into a sequence of binary bits and subsequently broke the binary sequence into several batches having a size of 16,384 bits. A random number was generated, which acted like a seed value or initial configuration for the algorithm. One-dimensional cellular automation with a radius = 1 produced 256 rules and out of the 256 rules only 6 rules showed the complete reversible property. Therefore, we used these six rules as the keys with 36 different possible combinations. If the last block was incomplete, we used any filter character, which was used rarely as data. The detailed process of encryption and decryption is represented in
Section 3.1 and
Section 3.2, respectively.
3.1. Encryption Algorithm
The following is a description of the encryption method and processes utilized in this project:
Initialization: plain texts were divided into batches of 2048 bytes and each batch was further divided into 128 blocks of 128 bits each. The seed value was a random number for the first block of each batch.
S1: XOR selected plain text block with a seed value to obtain the next-stage data.
S2: Repeat S1 for N times.
S3: Consider the output of the Nth iterations as a seed value and N-1th as a ciphertext.
S4: XOR ciphertext with Key-1 to compute the Encrypted Cipher Text (ECT).
S5: XOR seed with Key-2 to generate the encrypted seed. This acts as a seed for the next plain text block.
S6: Repeat steps S1 to S5 for all the blocks in a batch
S7: Combine the ECTs from each block to generate an ECT for the batch
S8: Repeat steps S1 to S7 for each batch and combine the generated ECTs to produce the final ECT.
S9: End.
3.2. Decryption Algorithm
The following is a description of the decryption method and processes utilized in this project:
Initialization: the encrypted ciphertexts are divided into batches of 2048 bytes and each batch is further divided into 128 blocks of 128 bits each. The encrypted seed generated at the end of the encryption process will be used as the initial seed for decryption.
S1: XOR encrypted seed with RKey-2 to generate the seed.
S2: XOR encrypted ciphertext with RKey-1 to generate the ciphertext.
S3: XOR ciphertext and seed to obtain the next-stage data.
S4: Repeat S1 for N times.
S5: The Nth iterations output is considered as the encrypted seed value which will be used in the following up block and the N-1th as-required plain text.
S6: Repeat S1 to S5 for all the blocks in a batch
S7: Combine plain texts from each block to generate the actual plain text for the batch
S8: Repeat S1 to S7 for each batch and combine the generated plain texts to produce the final plain texts.
S9: End.
Figure 3 represents a block diagram for the entire process of encryption. Initially, the plain text is split into several batches of 128X128 bits. Each batch can be assigned with a separate core for parallel computation. This process enhances the throughput of the algorithm. Each batch can be processed without depending on the other batch.
4. Results Analysis
The proposed algorithm was implemented in two different configurations. Configuration 1 consisted of a system having an Intel i7 processor with 8 cores and 8 GB RAM. Configuration 2 was an HPC cluster. The HPC cluster had an Intel Xeon scalable processor with 96 cores and 64 GB RAM. For configuration 2 we dedicatedly allocated 64 cores of processing capacity.
We implemented three algorithms in the python language with both configurations to obtain results for comparison. The first algorithm was the block encryption proposed by Seredynski [
6], the second one was the previously published work of ours [
17] and the third one was the proposed algorithm. We tested all three algorithms with a standard file that was 13.6 MB in size. We used cellular automata rule 153 as Key-1 and rule 195 as Key-2.
Figure 4a represents the encryption of a plain text block that is 128 bits and
Figure 4b represents its decryption. The binary bit 1 is represented by the black color cell and binary 0 is represented by the grey color cell.
We implemented all the algorithms in both the configurations and the results showed that the throughput-optimized algorithm executed faster than the other two algorithms. Again, in configuration 2, the proposed algorithm executed eight times faster than in configuration 1. This shows that the proposed throughput optimized algorithm provided an enhanced throughput in a high-performance system.
Figure 5a,b shows a performance comparison among the different algorithms in both configurations.
Figure 6 shows an almost equal distribution of 1′s and 0′s before and after the encryption process. A good encryption algorithm must show a uniform distribution of 1′s and 0′s.
The strength of the algorithm is that it makes a brute-force attack extremely difficult. A brute-force attack for the algorithm required n2 × 2128 different permutations, where n is the number of cellular automata rules, and we are using a random number of size 128 bits. This is more difficult if we scale this algorithm to 256 bits or more. Another strength of this algorithm is that each block of encryption and decryption is immune to other blocks due to the use of different random numbers as seeds for each block. So, a cryptanalysis of one block will not reveal information about another block.
The results of the multiple avalanche test produced an average of 50.605 avalanche values and hence we conclude that these algorithms were statistically independent of the input values. The result of the multiple avalanche test is shown in
Figure 7.
To test the pseudorandom behavior of the algorithms, we used a statistical test suite NIST. We obtained
p-values from the test and found that all the values were within the range of 0.001 to 0.999 and hence passed this test. The different parameters of the NIST test were found to be around 0.5 to 0.57. The details of the NIST statistical test results are shown in
Figure 8.
We scaled up the algorithm to work with 256 bits of block size and found a 5% increase in performance in configuration 2 and an increased performance by 1.6% in configuration 1.
5. Conclusions and Future Work
The comparison of different algorithms’ performance showed that the proposed throughput-optimized algorithm produced an enhanced throughput in a high-performance system as compared with other algorithms. This algorithm worked in an application layer, it was highly secure and a brute-force attack was extremely difficult because we used 128 bits keys and the random numbers used in every batch were different and had a size of 128 bits. This encryption system produced plaintext blocks that were immune to other blocks during cryptanalysis because of segmentation and the use of the different random numbers as seeds. Each block of encryption used a cipher block chaining mode and was hence more secure and effective. This algorithm was highly scalable, and we designed the algorithm for 128 bit blocks but it can be easily scaled to any size that is a multiple of two. Its hardware and software implementation is straightforward and has a low cost. In the future, we want to optimize the segmentation of the plain text into multiple batches because it is one of the bottlenecks for better performance. We want to design an alternative approach where the sender and receiver can use different keys in different batches. Additionally, we want to implement this algorithm in different application areas such as medical data, military data, satellite data, etc.
Author Contributions
Conceptualization, S.K.N. and S.M.; methodology, S.K.N.; software, S.M.; validation, P.K.P. and S.M.; formal analysis, S.K.N.; investigation, P.K.P.; resources, M.S.; data curation, S.M.; writing—original draft preparation, S.K.N.; writing—review and editing, P.K.P. and M.S. visualization, S.M.; supervision, S.M. and P.K.P.; project administration, M.S.; funding acquisition, M.S. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Dongseo University “Dongseo Cluster Project” Research Fund of 2022 (DSU-20220006).
Conflicts of Interest
The authors declare that there is no conflict of interest regarding the publication of this paper.
References
- Wolfram, S. Cryptography with Cellular Automata. In Lecture Notes in Computer Science; Hugh, C.W., Ed.; Springer: Berlin/Heidelberg, Germany, 1986; Volume 218, pp. 429–432. [Google Scholar]
- Guan, P. Cellular Automaton Public-Key Cryptosystem. Complex Syst. 1987, 1, 51–56. [Google Scholar]
- Das, A.K.; Chaudhuri, P.P. Vector space theoretic analysis of additive cellular automata and its application for pseudoexhaustive test pattern generation. IEEE Trans. Comput. 1993, 42, 340–352. [Google Scholar] [CrossRef]
- Nandi, S.; Kar, B.; Chaudhuri, P.P. Theory and applications of cellular automata in cryptography. IEEE Trans. Comput. 1994, 43, 1346–1357. [Google Scholar] [CrossRef] [Green Version]
- Tomassini, M.; Perrenoud, M. Cryptography with cellular automata. Appl. Soft Comput. 2001, 1, 151–160. [Google Scholar] [CrossRef]
- Seredynski, M.; Bouvry, P. Block cipher based on reversible cellular automata. New Gener. Comput. 2005, 23, 245–258. [Google Scholar] [CrossRef] [Green Version]
- Szaban, M.; Seredynski, F. Cellular Automata-Based S-Boxes vs. des S-Boxes. In Lecture Notes in Computer Science; Malyshkin, V., Ed.; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5698, pp. 269–283. [Google Scholar]
- Szaban, M.; Seredynski, F. Improving quality of DES S-boxes by cellular automata-based S-boxes. J. Supercomput. 2010, 57, 216–226. [Google Scholar] [CrossRef]
- Anghelescu, P.; Ionita, S.; Sofron, E. Block Encryption Using Hybrid Additive Cellular Automata. In Proceedings of the 7th International Conference on Hybrid Intelligent Systems (HIS 2007), Kaiserslautern, Germany, 17–19 September 2007; pp. 132–137. [Google Scholar]
- Das, D.; Ray, A. A Parallel Encryption Algorithm for Block Ciphers Based on Reversible Programmable Cellular Automata. J. Comput. Sci. Eng. 2010, 1, 82. [Google Scholar]
- Roy, S.; Nandi, S.; Dansana, J.; Pattnaik, P.K. Application of Cellular Automata in Symmetric Key Cryptography. In Proceedings of the International Conference on Communication and Signal Processing, ICCSP 2014—Proceedings, Melmaruvathur, India, 3–5 April 2014; pp. 572–576. [Google Scholar]
- Rani, S.; Sasamal, T.N. A New Clocking Scheme for Quantum-dot Cellular Automata Based Designs with Single or Regular Cells. Energy Procedia 2017, 117, 466–473. [Google Scholar] [CrossRef]
- Qadri, S.U.R.; Bangi, Z.A.; Banday, M.T.; Bhat, G.M.; Beigh, M.R. A novel comparator—A cryptographic design in quantum dot cellular automata. Int. J. Digit. Signals Smart Syst. 2020, 4, 113. [Google Scholar] [CrossRef]
- Su, Y.; Wo, Y.; Han, G. Reversible cellular automata image encryption for similarity search. Signal Process. Image Commun. 2018, 72, 134–147. [Google Scholar] [CrossRef]
- Naskar, P.K.; Bhattacharyya, S.; Nandy, D.; Chaudhuri, A. A robust image encryption scheme using chaotic tent map and cellular automata. Nonlinear Dyn. 2020, 100, 2877–2898. [Google Scholar] [CrossRef]
- Kumar, A.; Raghava, N.S. An efficient image encryption scheme using elementary cellular automata with novel permutation box. Multimed. Tools Appl. 2021, 80, 21727–21750. [Google Scholar] [CrossRef]
- Nanda, S.K.; Mohanty, S.; Pattnaik, P.K. Design of Cryptographic Algorithm Based on a Pair of Reversible Cellular Automata Rules. In Machine Learning and Information Processing. Advances in Intelligent Systems and Computing; Swain, D., Pattnaik, P.K., Athawale, T., Eds.; Springer: Singapore, 2021; Volume 1311. [Google Scholar] [CrossRef]
- Fathy, N.A.; Tarrad, F.I.; Hamed, A.H.F.; Awad, I.A. Advanced Encryption Standard Algorithm: Issues and Implementation Aspects, Advanced Machine Learning Technologies and Applications. AMLTA 2012. In Communications in Computer and Information Science; Hassanien, A.E., Ramadan, R., Abdel-Badeeh, M.S., Tai-hoon, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 322. [Google Scholar]
- Patil, P.; Narayankar, P.; Narayan, D.G.; Meena, S.M. A Comprehensive Evaluation of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Comput. Sci. 2016, 78, 617–624. [Google Scholar] [CrossRef] [Green Version]
- Bonde, S.Y.; Bhadade, U. Analysis of Encryption Algorithms (RSA, SRNN and 2 Key Pair) for Information Security. In Proceedings of the 2017 International Conference on Computing, Communication, Control and Automation (ICCUBEA), Pune, India, 17–18 August 2017; pp. 1–5. [Google Scholar]
- Murugan, A.C.; Karthigai, K.P. Survey on Image Encryption Schemes, Bio cryptography and Efficient Encryption Algorithms. Mob. Netw. Appl. 2018, 1–6. [Google Scholar] [CrossRef]
- Yongzhi, F.; Hao, L.; Zhang, X.; Yang, R. Design of an Extremely High-Performance Counter Mode AES Reconfigurable Processor. In Proceedings of the Second International Conference on Embedded Software and Systems (ICESS′05), Xian, China, 16–18 December 2005; p. 7. [Google Scholar]
- Ayub, M.A.; Ahmed, O.Z.; Smith, S. Parallelized RSA Algorithm: An Analysis with Performance Evaluation using OpenMP Library in High-Performance Computing Environment. In Proceedings of the 22nd International Conference on Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 18–20 December 2019; pp. 1–6. [Google Scholar]
| Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).