4.1. Jellyfish Search Optimizer (JSO)
Around a world, jellyfish can be found in water that is different depths and degrees. They have a bell-like shape; many of them have a diameter of less than a centimeter, while others are rather enormous. Each of the numerous species demonstrates a unique adaption to the maritime habitat. These organisms are able to appear practically anywhere in the water due to this phenomenon, which works in conjunction with each jellyfish’s individual movements within the swarm and the ensuing tidal currents to generate jellyfish blooms. The ideal place would be determined by comparing food quantities, because the amount of food at each spot a jellyfish visits fluctuates. As a result, a novel method is created that is motivated by the searching and swimming of jellyfish in the ocean [
34]. This is called a jellyfish search optimizer (JSO). The behavior and motion of jellyfish in sea are theoretically modelled in the following sections, and an optimization method based on the numerical model is then created [
35].
The jellyfish are drawn to the tidal currents because they are rich in nutrients. By combining all the trajectories from every jellyfish in the sea to the jellyfish that really is right now in the optimal position, the trend of the ocean current is identified. Equation (1) reproduces the ocean current,
The number of jellyfish is stated as
;
is the variable that controls the attraction, and
represents the jellyfish presently in the best position in the swarms. The mean location of all jellyfish is
, and the distance among a jellyfish’s present ideal position and the average position is represented as
. Fix the
as
, because, based on this statement, mean location comprises the probability of all jellyfish, therefore Equation (2) is represented as
Thus, (
) is defined and updated as Equation (3),
The variance of the jellyfish has a uniform spatial pattern in all coordinates. Thus Equation (4) is written as
For further updating, Equation (6) is modified as
Currently, the new position of every jellyfish is specified through Equation (10)
Equation (10) is updated as Equation (11),
where
is stated as distribution coefficient, which is connected to measurement of
.
is fixed to 3.
Jellyfish move in swarms in both passive (type A) and active (type B) ways. Many jellyfish originally display type A movement whenever the swarm has just been established. They gradually start to move more in a type B manner. The movement of jellyfish within their own places is known as type A movement, and the most recent position of every jellyfish is provided by Equation (12),
The upper and lower bound are stated as
and
;
is declared the motion coefficient,
is attained from the Equation (12). This effort is deliberated as an operative manipulation of local exploration, which is expressed in Equation (13)
where
is a function of position
. Therefore,
Using a temporal control system, the type of motion over time is determined. The time control mechanism consists of constant
and a time-control function
to control the jellyfish’s ability to travel either inside the jellyfish swarm or in accordance with the ocean current. The random value of the time-control function varies over time from 0 to 1. The jellyfish float together with the current of the ocean when its value reaches
. They go inside the swarm when its value is less than
. The time control varies at random between zero and one, and the precise value of C o is unknown.
is therefore set to 0.5, the average of zero and one, which is stated as Equation (17)
Jellyfish populations are typically started at random and have drawbacks, such as slow divergence and a propensity to get stuck at a local optimum due to poor variability. One of the simplest chaotic maps, the logistic map, is created to increase the diversity of the initial population. This map offers less chance of nonlinear equations and more varied initial populations than random selection. As a result, this map is written as Equation (18),
The position’s chaotic value for the jellyfish is stated as ; the initial population is stated as , which is held in the range of 0 to 1; η is fixed as 4.0.
Oceans can be found all over the earth. Since the earth is spherically symmetric, a jellyfish would eventually get back to the contrary bound whenever it leaves the search region, which is expressed as Equation (19),
Position of jellyfish in dimension is stated as ; and are represented as upper and lower bounds. The updated position is specified as .
4.2. CH Selection
The BCR-TM-JSO is employed for CH routing and selection. The proposed BCR-TM-JSO is selected because it comes with collision avoidance as standard, making it very helpful for creating congestion-aware routing in unforeseen circumstances.
4.2.1. Fitness Function
The BCR-TM-JSO technique makes use of the trust measure, QUN (queue utilization between nodes), network quality, and distance. As a consequence, the provided cost metrics are used throughout the routing process to stop rogue nodes by placing a large emphasis on the trust value for the trust metric. Subcategories of the cost indicators such as QUN, link quality, and distance are provided to increase the overall efficiency in terms of energy usage and overhead.
Trust has been utilized to improve security against malicious nodes and is a significant cost value for routing through an IoT-based WSN. An IoT-based WSN’s mobile nodes communicate with one another by depending on the mutual trust those nodes have built up over time. Direct trust is a packet-forwarding method depending on the number and percentage of data packets received
and delivered
. Equation (20) is used to calculate the direct trust degree.
- b
QUN and link quality
QUN is demarcated as the ratio amongst the number of packets engaged in the queue of
jth node
and quantity of obtainable packets in the particular node’s queue
. Equation (21) is utilized to calculate the QUN.
The fraction of transmissions and retransmissions requirements for successful data transfer between nodes
and
is referred to as link quality.
and state the forward and reverse information delivery.
- c
Distance
To identify the direct route over the IoT-WSN, the Euclidean distance between the nodes is decided by Equation (23).
and are the coordinates of the nodes and , respectively.
In BCR-TM-JSO, a weight value (
) is considered for each cost value to convert into a single cost value as shown in the Equation (24).
Thus, 0.35, 0.25, 0.25 and 0.15 are the weighted mean for and , respectively. While creating the data transmission, the malicious nodes that cause packet drops are avoided by employing the trust metric. The QUN and link quality are then considered in the cost measure to create a route with less traffic. This increases packet delivery and lowers the possibility of a network collision. Additionally, to lower the nodes’ energy consumption, the shortest distance is found.
4.2.2. Route Selection
In WSN, a client that receives data registers its ID in the routing table. Once all the information has been collected, the client starts sending it to the intended location. In the event that the source consumer obtains several detection warnings from its neighbors, BCR-TM-JSO assesses the route with the highest pheromone rate. Clients with a one-hop connectivity to the router send data directly, whereas clients more distant from the router use the BCR-TM-JSO for modular connection. Data packets are therefore sent along the route with the strongest signal. After the routing path has been constructed using BCR-TM-JSO, the transmission of data packets begins. Data are transported via a network with less congestion when the queue length used in routing is used to provide a collision-free path. The route’s mean is then calculated based on the packets transmitted and received and the link quality. As a result, the optimum data-transmission path is determined by utilizing the aforementioned fitness characteristics.
4.3. Blockchain Data Structure for Malicious Node Detection
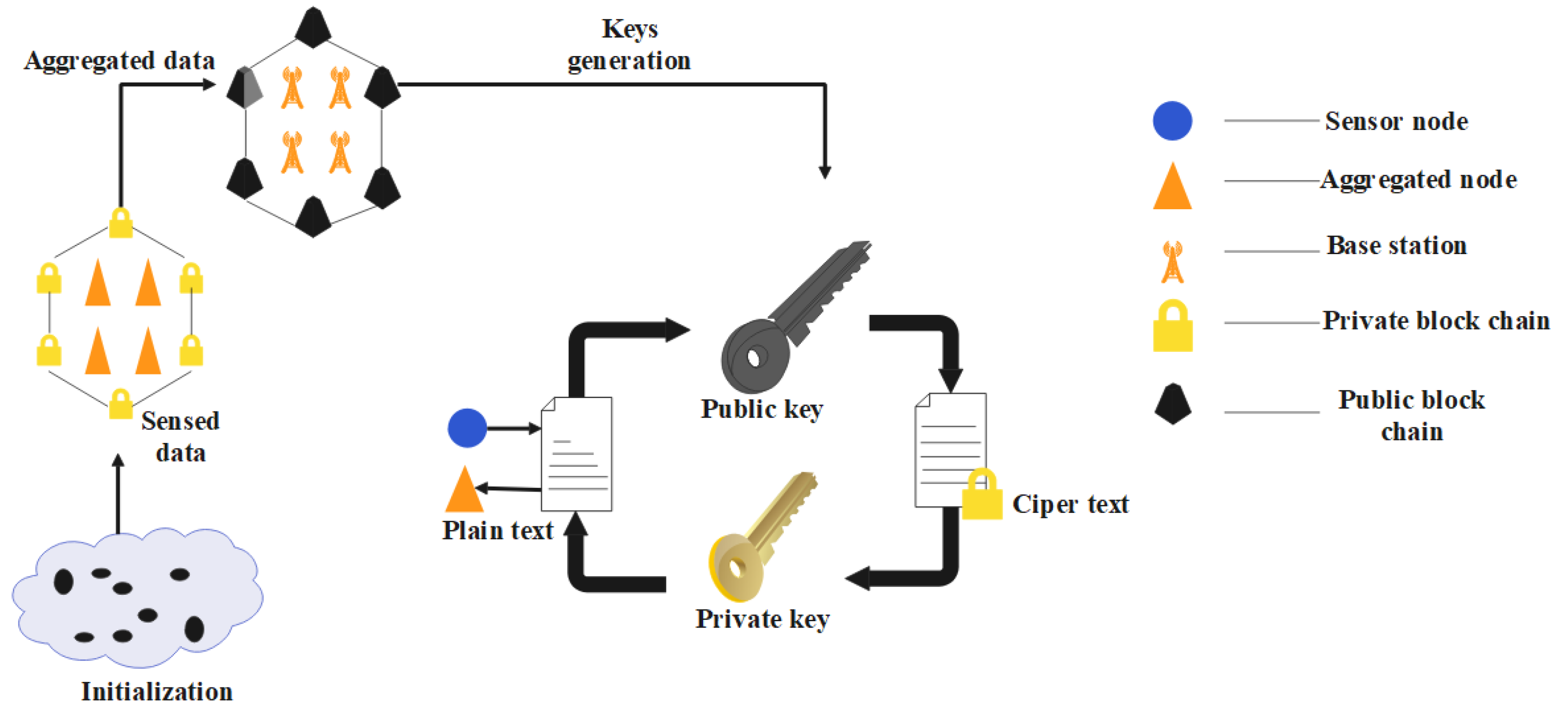
This study suggests a block data structure centered on a malicious node identification blockchain to best understand the blockchain. It is distinct from conventional WSNs in which it cannot consistently be discovered. The data structure in this case is mostly split into two sections. On the one side, the block header primarily carries the earlier block’s hash value, which is used to link the current block to it and maintain the blockchain’s integrity. The major data for the wireless sensor node in the block, including its position, ID, and condition, is instead contained in the block body. The block’s hash value is created using this data, the preceding block’s hash value, and a random number. Here, Hash1 is the hash pointer of the D1 sensor data, Hash12 is the hash pointer of Hash1 + Hash2, the layer stack is then added, and lastly, the distinct Merkle tree is produced. In addition to using a “block + chain” chain-data structure, it also employs a hash pointer to create a Merkle tree to store the data gathered by each block. When using such a data structure, it is feasible to modify the block’s hash pointer after any block’s contents are modified, ensuring that the data cannot be altered. In order to further limit the likelihood of malicious exploitation, assure security and integrity, and enhance the simplicity of the detection phase, the data are also collected by numerous sensors utilizing this data format whenever the entire network is deployed. The blockchain’s data format for identifying nodes is shown in
Figure 2.
The blockchain is a decentralized public ledger that has a rigorously encrypted method for member interoperability. A blockchain is really merely a data structure comprised of a singly linked list of network nodes, each of which contains a number of blocks that each include the cryptographic information from the block before it. The structure of block header and Merkle root function is shown in
Figure 3. In
Figure 3, when block header is created, a new block is created, and a hash is generated using pairs of keys and a digital signature. A hashing technique is then used to continuously construct new blocks using the hash of the previous block. A hash is generated using the private, public keys and the hash guarantees the integrity of the blocks.
4.4. SHA256 Algorithm
The SHA256 hash algorithm creates a message digest, which is a hash value with a length of 256 bits, for messages that are no longer than 264 bits in length. A 64-character hexadecimal string is able to describe the 32-byte array known as the (e digest. Five stages make up the SHA256 algorithm’s computation:
Increase the input data’s number of 0 bits till it reaches 448 bits. (After that, increase the input data’s length by 64 bits to 512 bits.
Separate the 512-bit data into 16 classes: .
Reset the vectors and , and its initial values of and are set as .
Fix the variable
t to loop from 0 to 63; then mentioned as Equation (25)
Consider Output .
From the above-stated process,
,
are logical functions, and
is updated as Equation (26)
It is clear that the SHA256 execution provides a solution that involves updating the variables of and , which calls for a number of addition processes and 64 iterations. Therefore, a key factor in lowering the algorithm’s running time will be the optimization of these two variables.