Intelligent Intrusion Detection Using Arithmetic Optimization Enabled Density Based Clustering with Deep Learning
Abstract
:1. Introduction
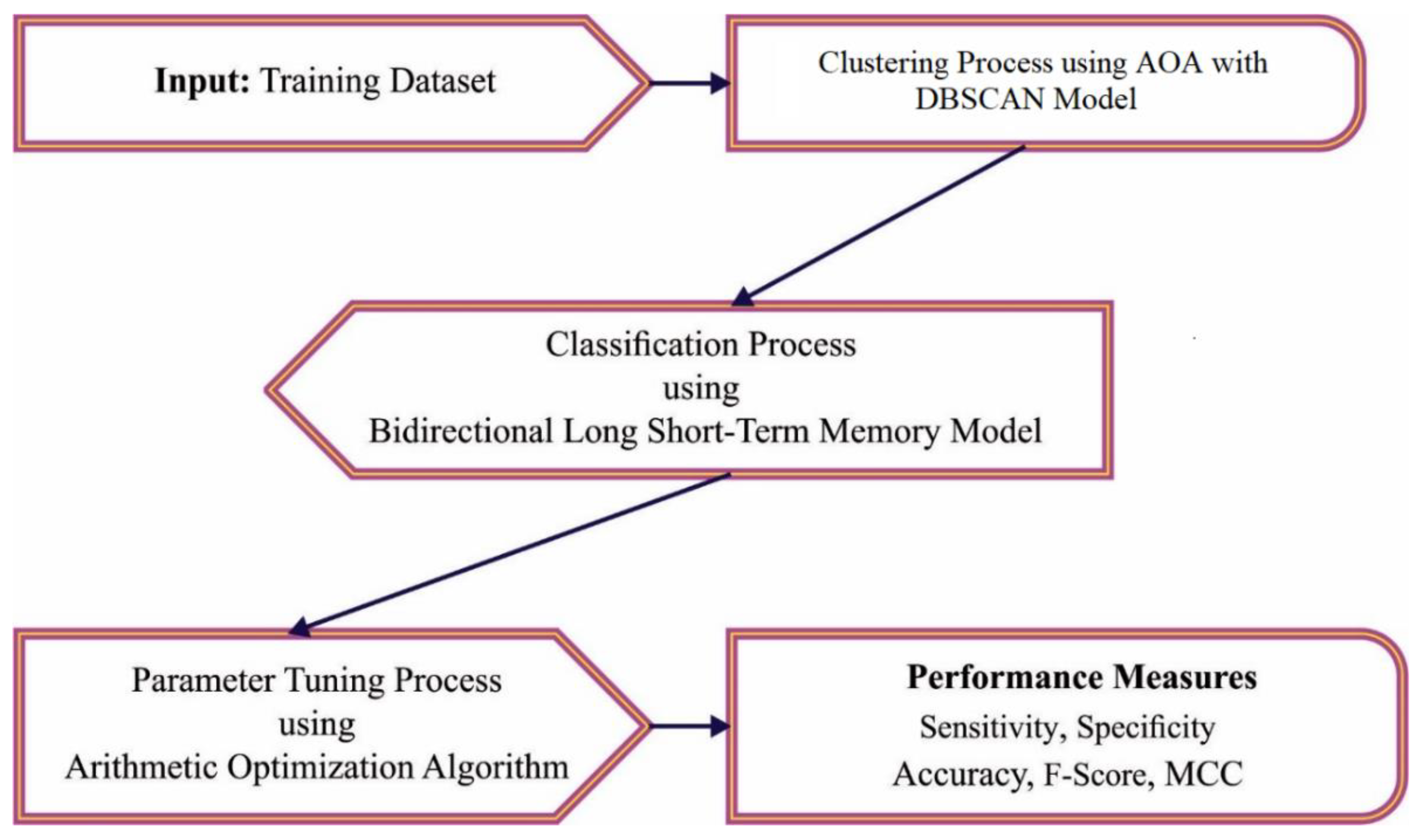
- An intelligent AOEDBC-DL model encompassing density based clustering, AOA based initial cluster set selection, BiLSTM intrusion detection, and QBA based hyperparameter tuning is presented for intrusion detection. To the best of our knowledge, the presented AOEDBC-DL model does not exist in the literature;
- AOA was derived with a density-based clustering technique to group the data points into a cluster and the AOA was used for optimal selection of initial cluster points;
- A new QBA was designed with a BiLSTM model for intrusion detection and the choice of QBA helped to appropriately select the hyperparameters of the BiLSTM model;
- The performance of the AOEDBC-DL model was validated on the WSN-DS (Wireless Sensor Networks-Dataset) dataset, which contains 15,000 samples with five class labels, namely normal, blackhole, gray hole, flooding, and scheduling attacks.
2. Literature Review
3. The Proposed Model
3.1. Data Clustering Using DBSCAN Model
| Algorithm 1: DBSCAN Algorithm |
| Input: distance , Dataset D, minimal cluster density minPts Begin For all the P points in D, data do If P is visited then Carry out subsequent P Else Set P as visited nbrPts <- points in neighborhood of P End if If then Set P as Noise Else Implement Expand_Cluster_Function (P, nbrPts, C, minPts) End if End for |
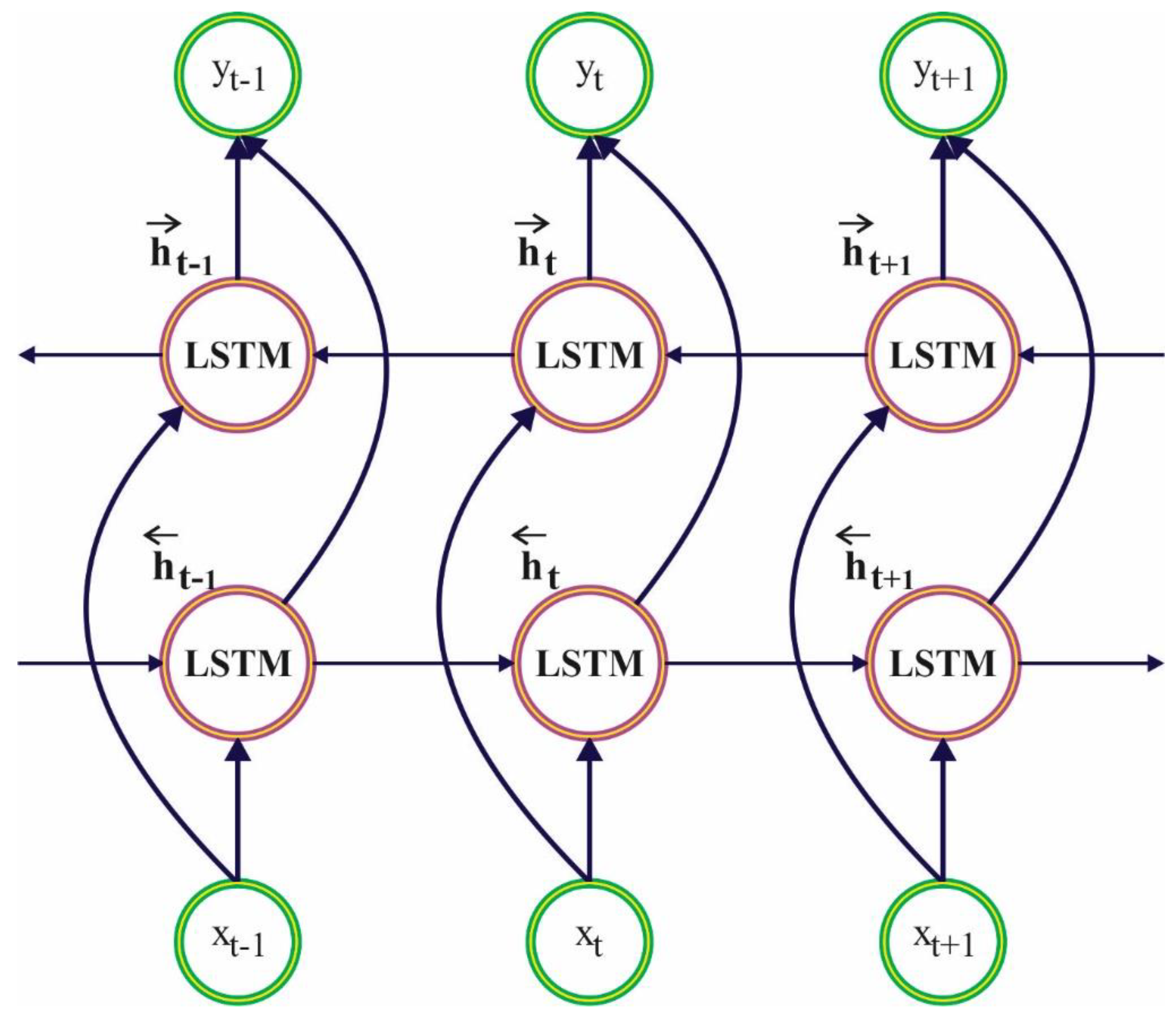
3.2. Intrusion Detection Using Optimal BiLSTM Model
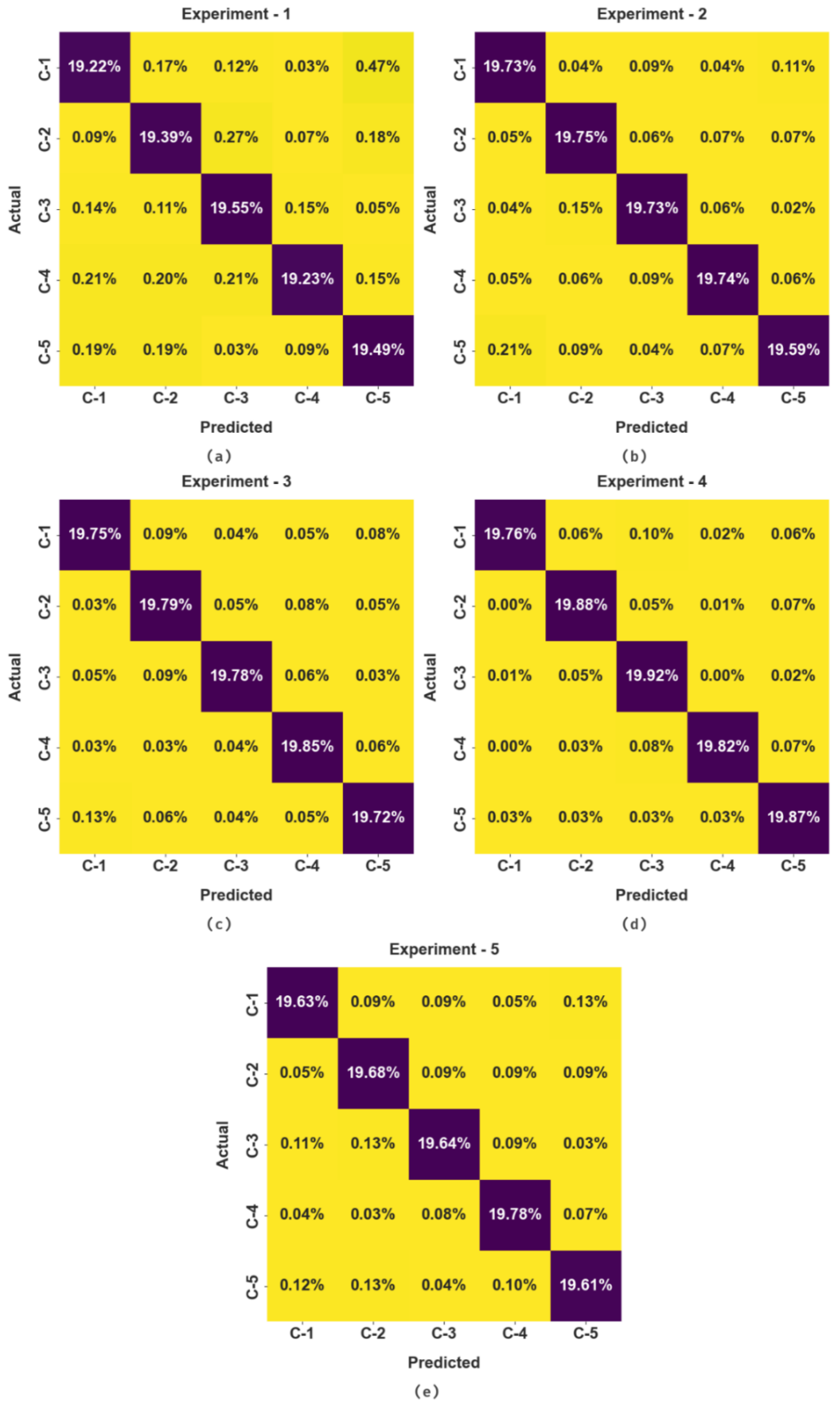
4. Performance Validation
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kalimuthan, C.; Renjit, A.J. Review on intrusion detection using feature selection with machine learning techniques. Mater. Today Proc. 2020, 33, 3794–3802. [Google Scholar] [CrossRef]
- Taher, K.A.; Jisan, B.M.Y.; Rahman, M.M. Network intrusion detection using supervised machine learning technique with feature selection. In Proceedings of the International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), Dhaka, Bangladesh, 10–12 January 2019; pp. 643–646. [Google Scholar]
- Prachi, H.M.; Sharma, P. Intrusion detection using machine learning and feature selection. Int. J. Comput. Netw. Inf. Secur. 2019, 11, 43–52. [Google Scholar]
- Wu, C.; Li, W. Enhancing intrusion detection with feature selection and neural network. Int. J. Intell. Syst. 2021, 36, 3087–3105. [Google Scholar] [CrossRef]
- Anwer, H.M.; Farouk, M.; Abdel-Hamid, A. April. A framework for efficient network anomaly intrusion detection with features selection. In Proceedings of the 9th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 3–5 April 2018; pp. 157–162. [Google Scholar]
- Alhakami, W.; ALharbi, A.; Bourouis, S.; Alroobaea, R.; Bouguila, N. Network anomaly intrusion detection using a nonparametric Bayesian approach and feature selection. IEEE Access 2019, 7, 52181–52190. [Google Scholar] [CrossRef]
- Pranto, M.B.; Ratul, M.H.A.; Rahman, M.M.; Diya, I.J.; Zahir, Z.B. Performance of machine learning techniques in anomaly detection with basic feature selection strategy-a network intrusion detection system. J. Adv. Inf. Technol. 2022, 13. [Google Scholar] [CrossRef]
- Chen, H.; Miao, F.; Chen, Y.; Xiong, Y.; Chen, T. A hyperspectral image classification method using multifeature vectors and optimized KELM. J. Sel. Top. Appl. Earth Obs. Remote Sens. 2021, 14, 2781–2795. [Google Scholar] [CrossRef]
- Wu, D.; Wu, C. Research on the Time-Dependent Split Delivery Green Vehicle Routing Problem for Fresh Agricultural Products with Multiple Time Windows. Agriculture 2022, 12, 793. [Google Scholar] [CrossRef]
- Deng, W.; Shang, S.; Cai, X.; Zhao, H.; Zhou, Y.; Chen, H.; Deng, W. Quantum differential evolution with cooperative coevolution framework and hybrid mutation strategy for large scale optimization. Knowl.-Based Syst. 2021, 224, 107080. [Google Scholar] [CrossRef]
- Albulayhi, K.; Abu Al-Haija, Q.; Alsuhibany, S.A.; Jillepalli, A.A.; Ashrafuzzaman, M.; Sheldon, F.T. IoT Intrusion Detection Using Machine Learning with a Novel High Performing Feature Selection Method. Appl. Sci. 2022, 12, 5015. [Google Scholar] [CrossRef]
- Al-Yaseen, W.L.; Idrees, A.K.; Almasoudy, F.H. Wrapper feature selection method based differential evolution and extreme learning machine for intrusion detection system. Pattern Recognit. 2022, 132, 108912. [Google Scholar] [CrossRef]
- Li, X.; Chen, W.; Zhang, Q.; Wu, L. Building auto-encoder intrusion detection system based on random forest feature selection. Comput. Secur. 2020, 95, 101851. [Google Scholar] [CrossRef]
- Gopalakrishnan, B.; Purusothaman, P. A new design of intrusion detection in IoT sector using optimal feature selection and high ranking-based ensemble learning model. Peer-to-Peer Netw. Appl. 2022, 15, 2199–2226. [Google Scholar] [CrossRef]
- Faysal, J.A.; Mostafa, S.T.; Tamanna, J.S.; Mumenin, K.M.; Arifin, M.M.; Awal, M.A.; Shome, A.; Mostafa, S.S. January. XGB-RF: A hybrid machine learning approach for IoT intrusion detection. Telecom 2022, 3, 52–69. [Google Scholar] [CrossRef]
- Upadhyay, D.; Manero, J.; Zaman, M.; Sampalli, S. Gradient boosting feature selection with machine learning classifiers for intrusion detection on power grids. IEEE Trans. Netw. Serv. Manag. 2020, 18, 1104–1116. [Google Scholar] [CrossRef]
- Çavuşoğlu, Ü. A new hybrid approach for intrusion detection using machine learning methods. Appl. Intell. 2019, 49, 2735–2761. [Google Scholar] [CrossRef]
- Li, S.S. An improved DBSCAN algorithm based on the neighbor similarity and fast nearest neighbor query. IEEE Access 2020, 8, 47468–47476. [Google Scholar] [CrossRef]
- Ullah, S.; Khan, M.A.; Ahmad, J.; Jamal, S.S.; e Huma, Z.; Hassan, M.T.; Pitropakis, N.; Buchanan, W.J. HDL-IDS: A hybrid deep learning architecture for intrusion detection in the Internet of Vehicles. Sensors 2022, 22, 1340. [Google Scholar] [CrossRef]
- Otoum, Y.; Liu, D.; Nayak, A. DL-IDS: A deep learning-based intrusion detection framework for securing IoT. Trans. Emerg. Telecommun. Technol. 2022, 33, e3803. [Google Scholar]
- Mendonça, R.V.; Silva, J.C.; Rosa, R.L.; Saadi, M.; Rodriguez, D.Z.; Farouk, A. A lightweight intelligent intrusion detection system for industrial internet of things using deep learning algorithms. Expert Syst. 2022, 39, e12917. [Google Scholar] [CrossRef]
- Nasir, M.; Javed, A.R.; Tariq, M.A.; Asim, M.; Baker, T. Feature engineering and deep learning-based intrusion detection framework for securing edge IoT. J. Supercomput. 2022, 78, 8852–8866. [Google Scholar] [CrossRef]
- Khatir, S.; Tiachacht, S.; Le Thanh, C.; Ghandourah, E.; Mirjalili, S.; Wahab, M.A. An improved Artificial Neural Network using Arithmetic Optimization Algorithm for damage assessment in FGM composite plates. Compos. Struct. 2021, 273, 114287. [Google Scholar] [CrossRef]
- Liu, X.; Liu, S.; Li, X.; Zhang, B.; Yue, C.; Liang, S.Y. Intelligent tool wear monitoring based on parallel residual and stacked bidirectional long short-term memory network. J. Manuf. Syst. 2021, 60, 608–619. [Google Scholar] [CrossRef]
- Yang, X.-S. A new metaheuristic bat-inspired algorithm. In Nature Inspired Cooperative Strategies for Optimization (NICSO 2010); Springer: Cham, Switzerland, 2010; pp. 65–74. [Google Scholar]
- Islam, J.; Nazir, A.; Hossain, M.M.; Alhitmi, H.K.; Kabir, M.A.; Jallad, A.H.M. A Surrogate Assisted Quantum-behaved Algorithm for Well Placement Optimization. IEEE Access 2022, 10, 17828–17844. [Google Scholar] [CrossRef]
- Almomani, I.; Al-Kasasbeh, B.; Al-Akhras, M. WSN-DS: A Dataset for Intrusion Detection Systems in Wireless Sensor Networks. J. Sens. 2016, 2016, 4731953. [Google Scholar] [CrossRef] [Green Version]
- Liu, G.; Zhao, H.; Fan, F.; Liu, G.; Xu, Q.; Nazir, S. An Enhanced Intrusion Detection Model Based on Improved kNN in WSNs. Sensors 2022, 22, 1407. [Google Scholar] [CrossRef]


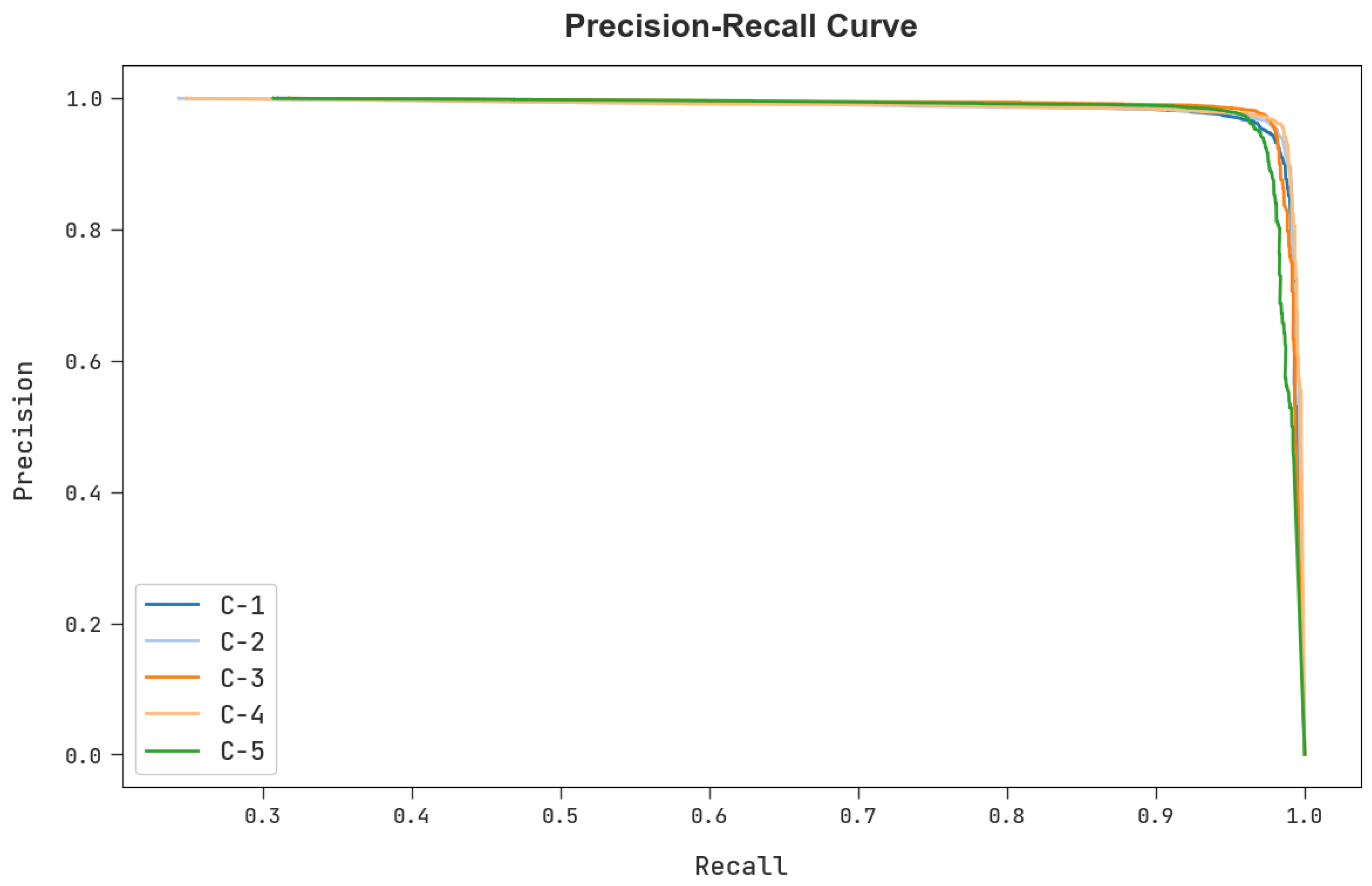
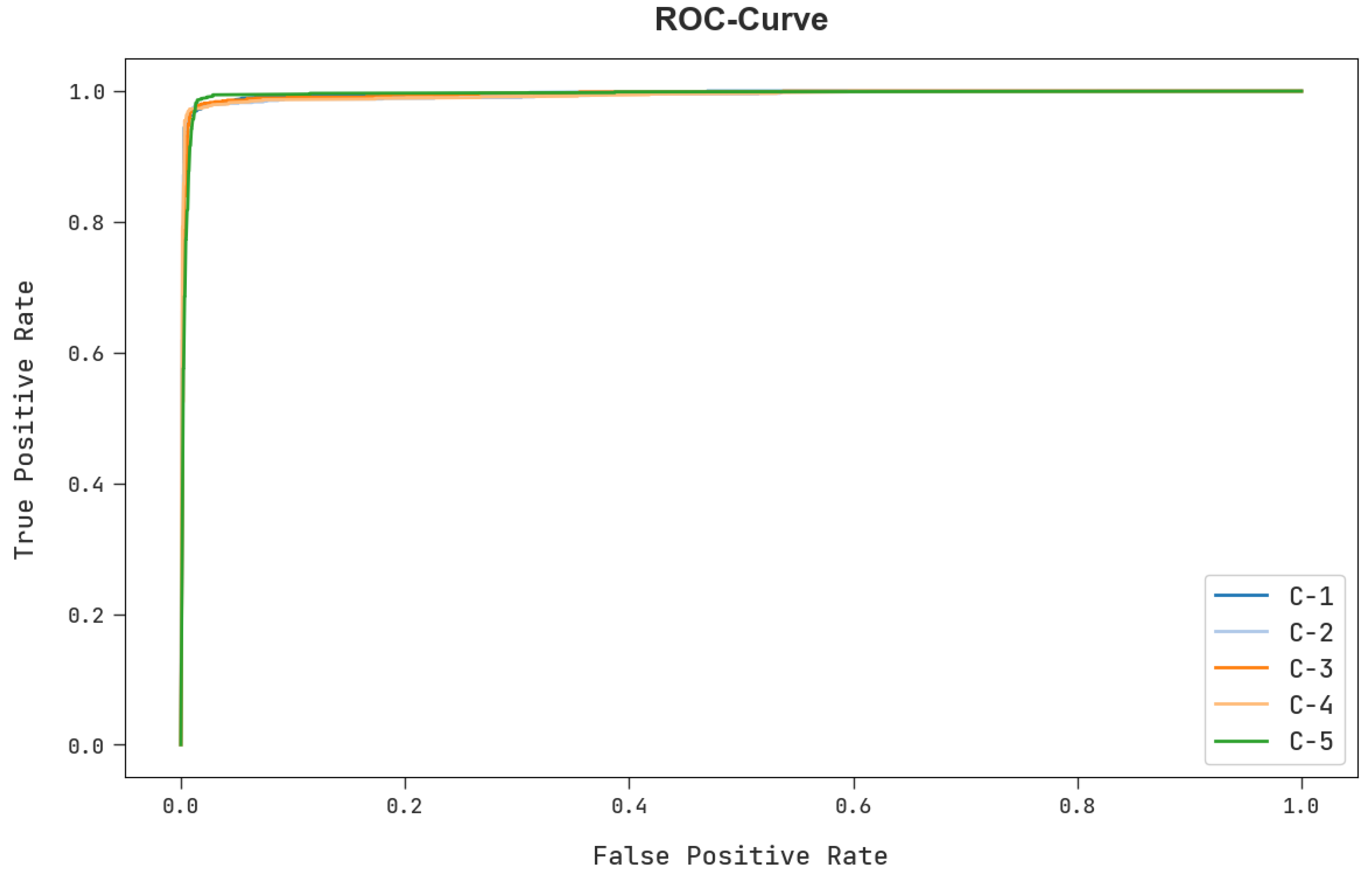

| Label | Class | No. of Samples for Experiment |
|---|---|---|
| C-1 | Normal | 3000 |
| C-2 | Blackhole | 3000 |
| C-3 | Grayhole | 3000 |
| C-4 | Flooding | 3000 |
| C-5 | Scheduling Attacks | 3000 |
| Total Number of Samples | 15,000 | |
| Labels | Accuracy | Sensitivity | Specificity | Fscore | MCC |
|---|---|---|---|---|---|
| Experiment-1 | |||||
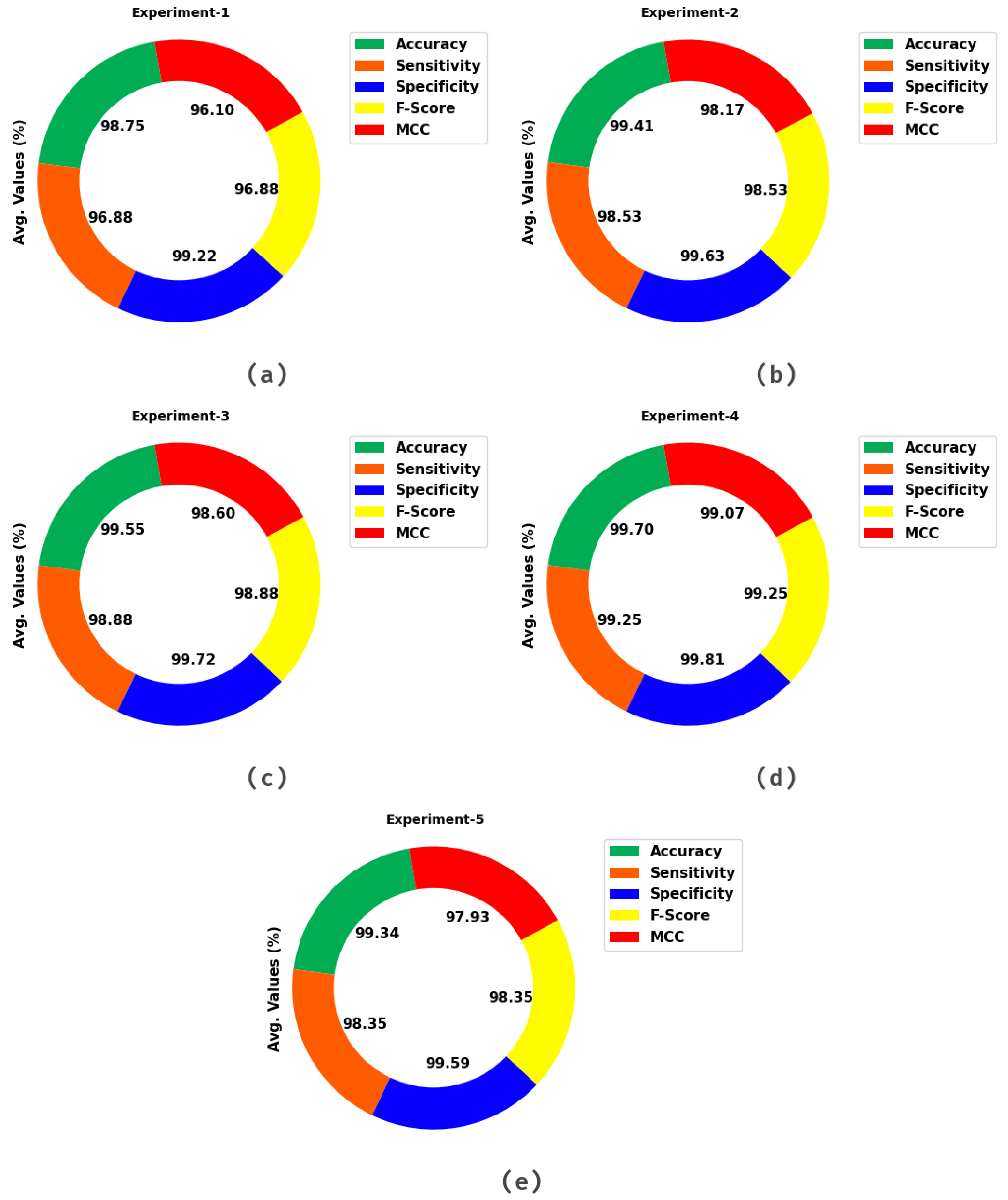
| C-1 | 98.59 | 96.10 | 99.21 | 96.45 | 95.57 |
| C-2 | 98.73 | 96.93 | 99.18 | 96.82 | 96.02 |
| C-3 | 98.91 | 97.73 | 99.21 | 97.30 | 96.62 |
| C-4 | 98.89 | 96.17 | 99.58 | 97.20 | 96.52 |
| C-5 | 98.64 | 97.47 | 98.93 | 96.63 | 95.78 |
| Average | 98.75 | 96.88 | 99.22 | 96.88 | 96.10 |
| Experiment-2 | |||||
| C-1 | 99.37 | 98.63 | 99.55 | 98.42 | 98.02 |
| C-2 | 99.41 | 98.73 | 99.58 | 98.52 | 98.15 |
| C-3 | 99.46 | 98.67 | 99.66 | 98.65 | 98.31 |
| C-4 | 99.51 | 98.70 | 99.71 | 98.77 | 98.46 |
| C-5 | 99.33 | 97.93 | 99.68 | 98.31 | 97.89 |
| Average | 99.41 | 98.53 | 99.63 | 98.53 | 98.17 |
| Experiment-3 | |||||
| C-1 | 99.51 | 98.73 | 99.71 | 98.78 | 98.48 |
| C-2 | 99.53 | 98.93 | 99.68 | 98.82 | 98.52 |
| C-3 | 99.61 | 98.90 | 99.79 | 99.03 | 98.79 |
| C-4 | 99.61 | 99.23 | 99.70 | 99.02 | 98.77 |
| C-5 | 99.50 | 98.60 | 99.72 | 98.75 | 98.44 |
| Average | 99.55 | 98.88 | 99.72 | 98.88 | 98.60 |
| Experiment-4 | |||||
| C-1 | 99.71 | 98.80 | 99.94 | 99.28 | 99.10 |
| C-2 | 99.71 | 99.40 | 99.78 | 99.27 | 99.08 |
| C-3 | 99.66 | 99.60 | 99.68 | 99.15 | 98.94 |
| C-4 | 99.77 | 99.10 | 99.93 | 99.41 | 99.27 |
| C-5 | 99.66 | 99.37 | 99.73 | 99.15 | 98.94 |
| Average | 99.70 | 99.25 | 99.81 | 99.25 | 99.07 |
| Experiment-5 | |||||
| C-1 | 99.31 | 98.17 | 99.60 | 98.28 | 97.85 |
| C-2 | 99.30 | 98.40 | 99.52 | 98.25 | 97.82 |
| C-3 | 99.34 | 98.20 | 99.62 | 98.35 | 97.94 |
| C-4 | 99.45 | 98.90 | 99.58 | 98.62 | 98.28 |
| C-5 | 99.29 | 98.07 | 99.60 | 98.23 | 97.79 |
| Average | 99.34 | 98.35 | 99.59 | 98.35 | 97.93 |
| Methods | Accuracy | Sensitivity | Specificity | Fscore |
|---|---|---|---|---|
| AOEDBC-DL | 99.70 | 99.25 | 99.81 | 99.25 |
| KNN | 98.16 | 98.32 | 97.01 | 98.54 |
| KNN-PSO | 97.60 | 98.62 | 96.58 | 95.98 |
| KNN-AOA | 97.15 | 96.30 | 98.64 | 96.27 |
| AdaBoost | 96.97 | 97.19 | 97.40 | 95.81 |
| Gradient Boosting | 96.59 | 97.96 | 95.60 | 98.28 |
| XGBoost | 95.41 | 96.05 | 98.47 | 96.52 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alrowais, F.; Marzouk, R.; Nour, M.K.; Mohsen, H.; Hilal, A.M.; Yaseen, I.; Alsaid, M.I.; Mohammed, G.P. Intelligent Intrusion Detection Using Arithmetic Optimization Enabled Density Based Clustering with Deep Learning. Electronics 2022, 11, 3541. https://doi.org/10.3390/electronics11213541
Alrowais F, Marzouk R, Nour MK, Mohsen H, Hilal AM, Yaseen I, Alsaid MI, Mohammed GP. Intelligent Intrusion Detection Using Arithmetic Optimization Enabled Density Based Clustering with Deep Learning. Electronics. 2022; 11(21):3541. https://doi.org/10.3390/electronics11213541
Chicago/Turabian StyleAlrowais, Fadwa, Radwa Marzouk, Mohamed K. Nour, Heba Mohsen, Anwer Mustafa Hilal, Ishfaq Yaseen, Mohamed Ibrahim Alsaid, and Gouse Pasha Mohammed. 2022. "Intelligent Intrusion Detection Using Arithmetic Optimization Enabled Density Based Clustering with Deep Learning" Electronics 11, no. 21: 3541. https://doi.org/10.3390/electronics11213541
APA StyleAlrowais, F., Marzouk, R., Nour, M. K., Mohsen, H., Hilal, A. M., Yaseen, I., Alsaid, M. I., & Mohammed, G. P. (2022). Intelligent Intrusion Detection Using Arithmetic Optimization Enabled Density Based Clustering with Deep Learning. Electronics, 11(21), 3541. https://doi.org/10.3390/electronics11213541






