Blockchain Systems in Embedded Internet of Things: Systematic Literature Review, Challenges Analysis, and Future Direction Suggestions
Abstract
1. Introduction
- Latency: Time and processing resources need to conduct encryption on each asset in a blockchain-based ecosystem [27]. IoT ecosystems are quite varied. IoT networks are made up of devices with highly diverse processing capabilities compared to general computer networks; thus, not all can perform the same encryption methods at the appropriate pace [28];
- Data concurrency and throughput issue: IoT networks have high concurrency because the devices stream data continually [29]. Because of its intricate cryptographic protocol and consensus procedures, the blockchain’s throughput is constrained [30,31]. The main task is to increase the blockchain’s throughput in order to handle the requirement for frequent transactions in IoT devices [32,33];
- Vulnerability: There are still several outstanding problems surrounding blockchain, such as generating distributed trust, while eliminating weaknesses such as DoS assaults and the famed 51% attack [34].
- This paper’s contributions are as follows:
- Outlining a Systematic Literature Review (SLR) for blockchain systems, a model proposal for IoT, and significant developments in this area;
- Listing the deficiencies and difficulties with IoT security and trust evaluation and recommendation methodologies;
- Discussing key IoT security and trustworthiness considerations and identifying any lingering issues for further research.
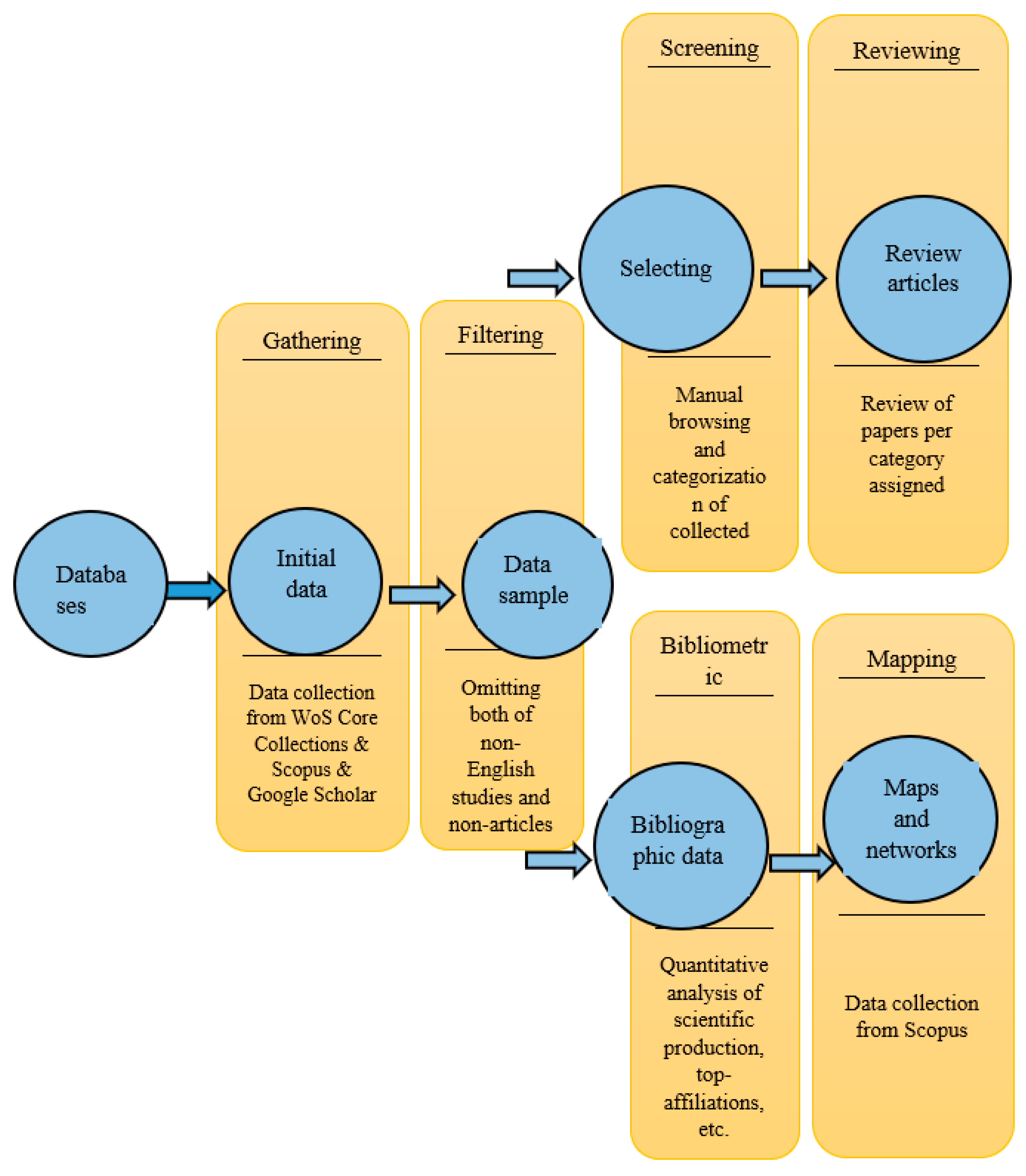
2. Research Design, Methodology, and Data Collection
2.1. Systematic Literature Review
2.2. Reviews and Surveys Category
2.2.1. Double-Blockchain Architecture
2.2.2. SDN-Based Architecture
2.2.3. Edge/Fog-Based Architecture
2.2.4. Lightweight Architecture
2.3. Bibliometric Maps
2.3.1. Distribution Based on Journal
2.3.2. Distribution Based on the Country
2.3.3. Bibliometric Analysis of Included Studies
3. Results and Analysis
3.1. Blockchain as a Solution for Securing IoT Big Data Analytics Using AI
3.2. Scalability Problem in IoT-Blockchain
3.3. Blockchain as a Solution for Securing the Software-Defined IoT
3.4. Smart Contract IoT Blockchain to Trust
3.5. Secure Data Sharing through Blockchain
3.6. Privacy and Trust Using Blockchain in IIoT
3.7. Blockchain Technology for IoT Authentication
4. Industry and Use of Blockchain Technology
5. Open Issue and Future Trends
- Although they provide a strong method for IoT security, blockchain systems are still susceptible. As a result of the disappearance of the hash power-based consensus mechanism, attackers are now able to host the blockchain. Similar to attackers being able to use private keys with low randomness to breach blockchain accounts, users must create effective strategies for safeguarding transaction privacy and avoiding competitive attacks that might lead to double-dipping during transactions [101];
- Investigators have not yet addressed several problems and difficulties, such as IoT devices’ limitations, massive data analysis, and other previously identified difficulties with integrating IoT blockchain;
- Some challenging research problems include deep learning, ML techniques, datasets for intrusion detection, scalability evaluations of blockchain-based solutions, how to select the best consensus algorithm, such as memetic algorithms, and the creation of practical and interoperable cryptographic protocols [102]. They need to be looked at more thoroughly soon [103,104];
- Providing a scalability study of blockchain-based solutions for IoT-based agriculture is one of the difficulties that needs more focus in the future;
- Future research will concentrate on improving IoT transactions to make them more suited for in-blockchain big data analytics, utilizing sophisticated Graph Neural Networks (GNN) [105,106]. These improvements will include making IoT transactions more organized, plentiful, and complete from beginning to end;
- Although IIoT-based blockchain and fog computing take advantage of both technologies’ benefits, several issues still need to be researched further to identify new opportunities. One issue is the creation of algorithms and infrastructures appropriate for such highly innovative automatic platforms [67];
- Although several strategies exist to reduce energy usage in blockchain-based systems [107], they are still ineffective when compared to the performances offered by lower-end devices [108]. The system’s overall energy utilization is directly impacted when using high-processing blockchain nodes to improve the robustness of IoT installations [109,110]. If a small number of blockchain nodes are utilized, and a mining method with a lower difficulty level is chosen, it may be kept at manageable levels. Moreover, it is necessary to minimize computational costs while utilizing various cryptosystems [111,112].
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Peng, S.-L.; Pal, S.; Huang, L. Principles of Internet of Things (IoT) Ecosystem: Insight Paradigm; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Li, A.; Spano, D.; Krivochiza, J.; Domouchtsidis, S.; Tsinos, C.G.; Masouros, C.; Chatzinotas, S.; Li, Y.; Vucetic, B.; Ottersten, B. A tutorial on interference exploitation via symbol-level precoding: Overview, state-of-the-art and future directions. IEEE Commun. Surv. Tutor. 2020, 22, 796–839. [Google Scholar] [CrossRef]
- Tseng, L.; Yao, X.; Otoum, S.; Aloqaily, M.; Jararweh, Y. Blockchain-based database in an IoT environment: Challenges, opportunities, and analysis. Clust. Comput. 2020, 23, 2151–2165. [Google Scholar] [CrossRef]
- Naen, M.F.; Adnan, M.H.M.; Yazi, N.A.; Nee, C.K. Development of Attendance Monitoring System with Artificial Intelligence Optimization in Cloud. Int. J. Artif. Intell. 2021, 8, 88–98. [Google Scholar] [CrossRef]
- Zheng, W.; Yin, L.; Chen, X.; Ma, Z.; Liu, S.; Yang, B. Knowledge base graph embedding module design for Visual question answering model. Pattern Recognit. 2021, 120, 108153. [Google Scholar] [CrossRef]
- Wu, H.; Jin, S.; Yue, W. Pricing Policy for a Dynamic Spectrum Allocation Scheme with Batch Requests and Impatient Packets in Cognitive Radio Networks. J. Syst. Sci. Syst. Eng. 2022, 31, 133–149. [Google Scholar] [CrossRef]
- Ye, C.; Cao, W.; Chen, S. Security challenges of blockchain in Internet of things: Systematic literature review. Trans. Emerg. Telecommun. Technol. 2021, 32, e4177. [Google Scholar] [CrossRef]
- Ye, R.; Liu, P.; Shi, K.; Yan, B. State damping control: A novel simple method of rotor UAV with high performance. IEEE Access 2020, 8, 214346–214357. [Google Scholar] [CrossRef]
- Mao, Y.; Zhu, Y.; Tang, Z.; Chen, Z. A Novel Airspace Planning Algorithm for Cooperative Target Localization. Electronics 2022, 11, 2950. [Google Scholar] [CrossRef]
- Ma, K.; Hu, X.; Yue, Z.; Wang, Y.; Yang, J.; Zhao, H.; Liu, Z. Voltage Regulation With Electric Taxi Based on Dynamic Game Strategy. IEEE Trans. Veh. Technol. 2022, 71, 2413–2426. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in internet of things: Challenges and solutions. arXiv 2016, arXiv:1608.05187. [Google Scholar]
- Shahidi, S.; Vahdat, S.; Atapour, A.; Reisizadeh, S.; Soltaninejad, F.; Maghami-Mehr, A. The clinical course and risk factors in COVID-19 patients with acute kidney injury. J. Fam. Med. Prim. Care 2022, 11, 6183–6189. [Google Scholar]
- Mohammadi, V.; Rahmani, A.M.; Darwesh, A.M.; Sahafi, A. Trust-based recommendation systems in Internet of Things: A systematic literature review. Hum.-Cent. Comput. Inf. Sci. 2019, 9, 1–61. [Google Scholar] [CrossRef]
- Liu, K.; Yang, Z.; Wei, W.; Gao, B.; Xin, D.; Sun, C.; Gao, G.; Wu, G. Novel detection approach for thermal defects: Study on its feasibility and application to vehicle cables. High Volt. 2022. [Google Scholar] [CrossRef]
- Jain, S. Can Blockchain Accelerate Internet of Things (IoT) Adoption. Deloitte Switzer-Land. 2021. Available online: https://www2.deloitte.com/ch/en/pages/innovation/articles/blockchain-accelerate-iot-adoption.html (accessed on 20 October 2022).
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Barnawi, A.; Alzahrani, B.A. Artificial Immune Systems approaches to secure the internet of things: A systematic review of the literature and recommendations for future research. J. Netw. Comput. Appl. 2020, 157, 102537. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- El-Masri, M.; Hussain, E.M.A. Blockchain as a mean to secure Internet of Things ecosystems—A systematic literature review. J. Enterp. Inf. Manag. 2021. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Ali, M.S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M.H. Applications of blockchains in the Internet of Things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2018, 21, 1676–1717. [Google Scholar] [CrossRef]
- Lee, B.; Lee, J.-H. Blockchain-based secure firmware update for embedded devices in an Internet of Things environment. J. Supercomput. 2017, 73, 1152–1167. [Google Scholar] [CrossRef]
- Rabah, K. Convergence of AI, IoT, big data and blockchain: A review. Lake Inst. J. 2018, 1, 1–18. [Google Scholar]
- Aljofey, A.; Rasool, A.; Jiang, Q.; Qu, Q. A Feature-Based Robust Method for Abnormal Contracts Detection in Ethereum Blockchain. Electronics 2022, 11, 2937. [Google Scholar] [CrossRef]
- Fotohi, R.; Aliee, F.S. Securing communication between things using blockchain technology based on authentication and SHA-256 to improving scalability in large-scale IoT. Comput. Netw. 2021, 197, 108331. [Google Scholar] [CrossRef]
- Kakarlapudi, P.V.; Mahmoud, Q.H. Design and Development of a Blockchain-Based System for Private Data Management. Electronics 2021, 10, 3131. [Google Scholar] [CrossRef]
- Banafa, A. IoT and blockchain convergence: Benefits and challenges. IEEE Internet Things 2017, 9. Available online: https://iot.ieee.org/newsletter/january-2017/iot-and-blockchain-convergence-benefits-and-challenges.html (accessed on 20 October 2022).
- Sharma, P.K.; Kumar, N.; Park, J.H. Blockchain technology toward green IoT: Opportunities and challenges. IEEE Netw. 2020, 34, 263–269. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Malina, L.; Dzurenda, P.; Srivastava, G. Optimized blockchain model for internet of things based healthcare applications. In Proceedings of the 2019 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 1–3 July 2019; pp. 135–139. [Google Scholar]
- Zhou, Q.; Huang, H.; Zheng, Z.; Bian, J. Solutions to scalability of blockchain: A survey. IEEE Access 2020, 8, 16440–16455. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A survey on the adoption of blockchain in iot: Challenges and solutions. Blockchain Res. Appl. 2021, 2, 100006. [Google Scholar] [CrossRef]
- Bhadoria, R.S.; Das, A.P.; Bashar, A.; Zikria, M. Implementing Blockchain-Based Traceable Certificates as Sustainable Technology in Democratic Elections. Electronics 2022, 11, 3359. [Google Scholar] [CrossRef]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Doewes, R.I.; Gharibian, G.; zadeh, F.A.; Zaman, B.A.; vahdat, S.; Akhavan-Sigari, R. An updated systematic review on the effects of aerobic exercise on human blood lipid profile. Curr. Probl. Cardiol. 2022, in press. [Google Scholar] [CrossRef]
- Zadeh, F.A.; Bokov, D.O.; Yasin, G.; Vahdat, S.; Abbasalizad-Farhangi, M. Central obesity accelerates leukocyte telomere length (LTL) shortening in apparently healthy adults: A systematic review and meta-analysis. Crit. Rev. Food Sci. Nutr. 2021, 1–10. [Google Scholar] [CrossRef]
- Herrera-Franco, G.; Montalván-Burbano, N.; Carrión-Mero, P.; Jaya-Montalvo, M.; Gurumendi-Noriega, M. Worldwide research on geoparks through bibliometric analysis. Sustainability 2021, 13, 1175. [Google Scholar] [CrossRef]
- Nobanee, H.; Al Hamadi, F.Y.; Abdulaziz, F.A.; Abukarsh, L.S.; Alqahtani, A.F.; AlSubaey, S.K.; Alqahtani, S.M.; Almansoori, H.A. A bibliometric analysis of sustainability and risk management. Sustainability 2021, 13, 3277. [Google Scholar] [CrossRef]
- Quezada-Sarmiento, P.A.; Elorriaga, J.A.; Arruarte, A.; Washizaki, H. Open BOK on software engineering educational context: A systematic literature review. Sustainability 2020, 12, 6858. [Google Scholar] [CrossRef]
- Esmailiyan, M.; Amerizadeh, A.; Vahdat, S.; Ghodsi, M.; Doewes, R.I.; Sundram, Y. Effect of different types of aerobic exercise on individuals with and without hypertension: An updated systematic review. Curr. Probl. Cardiol. 2021, 101034. [Google Scholar] [CrossRef]
- Vahdat, S.; Shahidi, S. D-dimer levels in chronic kidney illness: A comprehensive and systematic literature review. Proc. Natl. Acad. Sci. India Sect. B Biol. Sci. 2020, 90, 911–928. [Google Scholar] [CrossRef]
- Vahdat, S. A review of pathophysiological mechanism, diagnosis, and treatment of thrombosis risk associated with COVID-19 infection. IJC Heart Vasc. 2022, 41, 101068. [Google Scholar] [CrossRef]
- Li, Z.; Hao, J.; Liu, J.; Wang, H.; Xian, M. An IoT-applicable access control model under double-layer blockchain. IEEE Trans. Circuits Syst. II Express Briefs 2020, 68, 2102–2106. [Google Scholar] [CrossRef]
- Aldriwish, K. A double-blockchain architecture for secure storage and transaction on the Internet of Things networks. Int. J. Comput. Sci. Netw. Secur. 2021, 21, 119–126. [Google Scholar]
- Ren, W.; Wan, X.; Gan, P. A double-blockchain solution for agricultural sampled data security in Internet of Things network. Future Gener. Comput. Syst. 2021, 117, 453–461. [Google Scholar] [CrossRef]
- Hao, X.; Yeoh, P.L.; Ji, Z.; Yu, Y.; Vucetic, B.; Li, Y. Stochastic Analysis of Double Blockchain Architecture in IoT Communication Networks. IEEE Internet Things J. 2022, 9700–9711. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Zhang, Q.; Choo, K.-K.R. An energy-efficient SDN controller architecture for IoT networks with blockchain-based security. IEEE Trans. Serv. Comput. 2020, 13, 625–638. [Google Scholar] [CrossRef]
- Abdulqadder, I.H.; Zhou, S.; Zou, D.; Aziz, I.T.; Akber, S.M.A. Bloc-sec: Blockchain-based lightweight security architecture for 5G/B5G enabled SDN/NFV cloud of IoT. In Proceedings of the 2020 IEEE 20th International Conference on Communication Technology (ICCT), Nanning, China, 28–31 October 2020; pp. 499–507. [Google Scholar]
- Hakiri, A.; Sellami, B.; Yahia, S.B.; Berthou, P. A Blockchain architecture for SDN-enabled tamper-resistant IoT networks. In Proceedings of the 2020 Global Information Infrastructure and Networking Symposium (GIIS), Tunis, Tunisia, 28–31 October 2020; pp. 1–4. [Google Scholar]
- Hakiri, A.; Dezfouli, B. Towards a blockchain-SDN architecture for secure and trustworthy 5G massive IoT networks. In Proceedings of the 2021 ACM International Workshop on Software Defined Networks & Network Function Virtualization Security, New York, NY, USA, 28 April 2021; pp. 11–18. [Google Scholar]
- ABBASSI, Y.; Benlahmer, H. BCSDN-IoT: Towards an IoT security architecture based on SDN and Blockchain. Int. J. Electr. Comput. Eng. Syst. 2022, 13, 155–163. [Google Scholar] [CrossRef]
- Cho, H.-H.; Wu, H.-T.; Lai, C.-F.; Shih, T.K.; Tseng, F.-H. Intelligent charging path planning for IoT network over Blockchain-based edge architecture. IEEE Internet Things J. 2020, 8, 2379–2394. [Google Scholar] [CrossRef]
- Kumar, T.; Harjula, E.; Ejaz, M.; Manzoor, A.; Porambage, P.; Ahmad, I.; Liyanage, M.; Braeken, A.; Ylianttila, M. BlockEdge: Blockchain-edge framework for industrial IoT networks. IEEE Access 2020, 8, 154166–154185. [Google Scholar] [CrossRef]
- Mayer, A.H.; Rodrigues, V.F.; da Costa, C.A.; da Rosa Righi, R.; Roehrs, A.; Antunes, R.S. Fogchain: A fog computing architecture integrating blockchain and Internet of things for personal health records. IEEE Access 2021, 9, 122723–122737. [Google Scholar] [CrossRef]
- Pavithran, D.; Al-Karaki, J.N.; Shaalan, K. Edge-based blockchain architecture for event-driven IoT using hierarchical identity based encryption. Inf. Process. Manag. 2021, 58, 102528. [Google Scholar] [CrossRef]
- Fetjah, L.; Azbeg, K.; Ouchetto, O.; Andaloussi, S.J. Towards a Smart Healthcare System: An Architecture Based on IoT, Blockchain, and Fog Computing. Int. J. Healthc. Inf. Syst. Inform. 2021, 16, 1–18. [Google Scholar] [CrossRef]
- Seok, B.; Park, J.; Park, J.H. A lightweight hash-based blockchain architecture for industrial IoT. Appl. Sci. 2019, 9, 3740. [Google Scholar] [CrossRef]
- Tuli, S.; Mahmud, R.; Tuli, S.; Buyya, R. Fogbus: A blockchain-based lightweight framework for edge and fog computing. J. Syst. Softw. 2019, 154, 22–36. [Google Scholar] [CrossRef]
- Khalid, U.; Asim, M.; Baker, T.; Hung, P.C.; Tariq, M.A.; Rafferty, L. A decentralized lightweight blockchain-based authentication mechanism for IoT systems. Clust. Comput. 2020, 23, 2067–2087. [Google Scholar] [CrossRef]
- Alfrhan, A.; Moulahi, T.; Alabdulatif, A. Comparative study on hash functions for lightweight blockchain in Internet of Things (IoT). Blockchain Res. Appl. 2021, 2, 100036. [Google Scholar] [CrossRef]
- Bandara, E.; Tosh, D.; Foytik, P.; Shetty, S.; Ranasinghe, N.; De Zoysa, K. Tikiri—Towards a lightweight blockchain for IoT. Future Gener. Comput. Syst. 2021, 119, 154–165. [Google Scholar] [CrossRef]
- Bouras, M.A.; Lu, Q.; Dhelim, S.; Ning, H. A lightweight blockchain-based IoT identity management approach. Future Internet 2021, 13, 24. [Google Scholar] [CrossRef]
- Hao, R.-B.; Lu, Z.-Q.; Ding, H.; Chen, L.-Q. A nonlinear vibration isolator supported on a flexible plate: Analysis and experiment. Nonlinear Dyn. 2022, 108, 941–958. [Google Scholar] [CrossRef]
- Dai, B.; Zhang, B.; Niu, Z.; Feng, Y.; Liu, Y.; Fan, Y. A novel ultrawideband branch waveguide coupler with low amplitude imbalance. IEEE Trans. Microw. Theory Tech. 2022, 70, 3838–3846. [Google Scholar] [CrossRef]
- Xi, Y.; Jiang, W.; Wei, K.; Hong, T.; Cheng, T.; Gong, S. Wideband RCS Reduction of Microstrip Antenna Array Using Coding Metasurface With Low Q Resonators and Fast Optimization Method. IEEE Antennas Wirel. Propag. Lett. 2021, 21, 656–660. [Google Scholar] [CrossRef]
- Hong, T.; Guo, S.; Jiang, W.; Gong, S. Highly Selective Frequency Selective Surface With Ultrawideband Rejection. IEEE Trans. Antennas Propag. 2021, 70, 3459–3468. [Google Scholar] [CrossRef]
- Bouachir, O.; Aloqaily, M.; Tseng, L.; Boukerche, A. Blockchain and fog computing for cyberphysical systems: The case of smart industry. Computer 2020, 53, 36–45. [Google Scholar] [CrossRef]
- Pourvahab, M.; Ekbatanifard, G. An efficient forensics architecture in software-defined networking-IoT using blockchain technology. IEEE Access 2019, 7, 99573–99588. [Google Scholar] [CrossRef]
- Feng, Y.; Zhang, B.; Liu, Y.; Niu, Z.; Fan, Y.; Chen, X. A D-band manifold triplexer with high isolation utilizing novel waveguide dual-mode filters. IEEE Trans. Terahertz Sci. Technol. 2022. [Google Scholar] [CrossRef]
- Zhang, J.; Zhu, C.; Zheng, L.; Xu, K. ROSEFusion: Random optimization for online dense reconstruction under fast camera motion. ACM Trans. Graph. 2021, 40, 1–17. [Google Scholar]
- Unal, D.; Hammoudeh, M.; Khan, M.A.; Abuarqoub, A.; Epiphaniou, G.; Hamila, R. Integration of federated machine learning and blockchain for the provision of secure big data analytics for Internet of Things. Comput. Secur. 2021, 109, 102393. [Google Scholar] [CrossRef]
- Zhao, H.; Zhu, C.; Xu, X.; Huang, H.; Xu, K. Learning practically feasible policies for online 3D bin packing. Sci. China Inf. Sci. 2022, 65, 1–17. [Google Scholar] [CrossRef]
- Luo, G.; Yuan, Q.; Li, J.; Wang, S.; Yang, F. Artificial intelligence powered mobile networks: From cognition to decision. IEEE Netw. 2022, 36, 136–144. [Google Scholar] [CrossRef]
- Alrehaili, A.; Namoun, A.; Tufail, A. A Comparative Analysis of Scalability Issues within Blockchain-based Solutions in the Internet of Things. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 480–490. [Google Scholar] [CrossRef]
- Atlam, H.F.; Alenezi, A.; Alassafi, M.O.; Wills, G. Blockchain with internet of things: Benefits, challenges, and future directions. Int. J. Intell. Syst. Appl. 2018, 10, 40–48. [Google Scholar] [CrossRef]
- Zheng, H.; Jin, S. A multi-source fluid queue based stochastic model of the probabilistic offloading strategy in a MEC system with multiple mobile devices and a single MEC server. Int. J. Appl. Math. Comput. Sci. 2022, 32, 125–138. [Google Scholar]
- Samaniego, M.; Deters, R. Using blockchain to push software-defined IoT components onto edge hosts. In Proceedings of the International Conference on Big Data and Advanced Wireless Technologies, Blagoevgrad, Bulgaria, 10–11 November 2016; pp. 1–9. [Google Scholar]
- Xu, K.-D.; Guo, Y.-J.; Liu, Y.; Deng, X.; Chen, Q.; Ma, Z. 60-GHz compact dual-mode on-chip bandpass filter using GaAs technology. IEEE Electron Device Lett. 2021, 42, 1120–1123. [Google Scholar] [CrossRef]
- Xu, K.-D.; Weng, X.; Li, J.; Guo, Y.-J.; Wu, R.; Cui, J.; Chen, Q. 60-GHz third-order on-chip bandpass filter using GaAs pHEMT technology. Semicond. Sci. Technol. 2022, 37, 055004. [Google Scholar] [CrossRef]
- Qiu, C.; Yu, F.R.; Yao, H.; Jiang, C.; Xu, F.; Zhao, C. Blockchain-based software-defined industrial Internet of Things: A dueling deep ${Q} $-learning approach. IEEE Internet Things J. 2018, 6, 4627–4639. [Google Scholar] [CrossRef]
- Stanciu, A. Blockchain based distributed control system for edge computing. In Proceedings of the 2017 21st International Conference on Control Systems and Computer Science (CSCS), Bucharest, Romania, 29–31 May 2017; pp. 667–671. [Google Scholar]
- Pranto, T.H.; Noman, A.A.; Mahmud, A.; Haque, A.B. Blockchain and smart contract for IoT enabled smart agriculture. PeerJ Comput. Sci. 2021, 7, e407. [Google Scholar] [CrossRef] [PubMed]
- Manzoor, A.; Liyanage, M.; Braeke, A.; Kanhere, S.S.; Ylianttila, M. Blockchain based proxy re-encryption scheme for secure IoT data sharing. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Korea, 14–17 May 2019; pp. 99–103. [Google Scholar]
- Shi, P.; Wang, H.; Yang, S.; Chen, C.; Yang, W. Blockchain-based trusted data sharing among trusted stakeholders in IoT. Softw. Pract. Exp. 2021, 51, 2051–2064. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Dai, Y.; Maharjan, S.; Zhang, Y. Blockchain and federated learning for privacy-preserved data sharing in industrial IoT. IEEE Trans. Ind. Inform. 2019, 16, 4177–4186. [Google Scholar] [CrossRef]
- Miller, D. Blockchain and the internet of things in the industrial sector. IT Prof. 2018, 20, 15–18. [Google Scholar] [CrossRef]
- Barbosa, P.; Brito, A.; Almeida, H. A technique to provide differential privacy for appliance usage in smart metering. Inf. Sci. 2016, 370, 355–367. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Privacy preservation in blockchain based IoT systems: Integration issues, prospects, challenges, and future research directions. Future Gener. Comput. Syst. 2019, 97, 512–529. [Google Scholar] [CrossRef]
- Ashraf, A.; Elmedany, W. Authentication in IoT devices using blockchain technology: A review. In Proceedings of the 4th Smart Cities Symposium (SCS 2021), Zallaq, Bahrain, 21–23 November 2021; pp. 545–551. [Google Scholar]
- Sinha, D. Authentication and Privacy Preservation in IoT Based Forest Fire Detection by Using Blockchain—A Review. In Proceedings of the 4th International Conference on Internet of Things and Connected Technologies (ICIoTCT), Jaipur, India, 9–10 May 2019; Internet of Things and Connected Technologies. p. 133. [Google Scholar]
- Leelasantitham, A. A business model guideline of electricity utility systems based on blockchain technology in thailand: A case study of consumers, prosumers and SMEs. Wirel. Pers. Commun. 2020, 115, 3123–3136. [Google Scholar] [CrossRef]
- Liu, Y.; Xu, K.-D.; Li, J.; Guo, Y.-J.; Zhang, A.; Chen, Q. Millimeter-wave E-plane waveguide bandpass filters based on spoof surface plasmon polaritons. IEEE Trans. Microw. Theory Tech. 2022, 70, 4399–4409. [Google Scholar] [CrossRef]
- Lin, Y.; Song, H.; Ke, F.; Yan, W.; Liu, Z.; Cai, F. Optimal caching scheme in D2D networks with multiple robot helpers. Comput. Commun. 2022, 181, 132–142. [Google Scholar] [CrossRef]
- Mengelkamp, E.; Gärttner, J.; Rock, K.; Kessler, S.; Orsini, L.; Weinhardt, C. Designing microgrid energy markets: A case study: The Brooklyn Microgrid. Appl. Energy 2018, 210, 870–880. [Google Scholar] [CrossRef]
- Wongsamerchue, T.; Leelasantitham, A. An Electronic Double Auction of Prepaid Electricity Trading Using Blockchain Technology. J. Mob. Multimed. 2022, 18, 1829–1850. [Google Scholar] [CrossRef]
- Novianti, D.; Arkeman, Y.; Almunawar, M.N.; Haditjaroko, L.; Ismayana, A. Designing a Transparent Distributed Systems for Halal Supply Chains Using Blockchain Technology. J. Bus. Econ. Anal. 2020, 3, 151–170. [Google Scholar] [CrossRef]
- Abidin, N.Z.; Perdana, F.F.P. A proposed conceptual framework for blockchain technology in Halal food product verification. J. Halal Ind. Serv. 2020, 3. [Google Scholar] [CrossRef]
- Alamsyah, A.; Hakim, N.; Hendayani, R. Blockchain-Based Traceability System to Support the Indonesian Halal Supply Chain Ecosystem. Economies 2022, 10, 134. [Google Scholar] [CrossRef]
- Li, A.; Masouros, C.; Swindlehurst, A.L.; Yu, W. 1-bit massive MIMO transmission: Embracing interference with symbol-level precoding. IEEE Commun. Mag. 2021, 59, 121–127. [Google Scholar] [CrossRef]
- Li, D.; Kar, P. B-Spot: Blockchain and Steganography based Robust and Secure Photo Transmission Mechanism. J. Mob. Multimed. 2022, 18, 1677–1708. [Google Scholar] [CrossRef]
- Singh, S.; Hosen, A.S.; Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed iot network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Zheng, W.; Liu, X.; Ni, X.; Yin, L.; Yang, B. Improving visual reasoning through semantic representation. IEEE Access 2021, 9, 91476–91486. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Yang, X.; Derhab, A.; Maglaras, L. Security and privacy for green IoT-based agriculture: Review, blockchain solutions, and challenges. IEEE Access 2020, 8, 32031–32053. [Google Scholar] [CrossRef]
- Cao, B.; Zhang, W.; Wang, X.; Zhao, J.; Gu, Y.; Zhang, Y. A memetic algorithm based on two_Arch2 for multi-depot heterogeneous-vehicle capacitated arc routing problem. Swarm Evol. Comput. 2021, 63, 100864. [Google Scholar] [CrossRef]
- Zheng, W.; Liu, X.; Yin, L. Sentence representation method based on multi-layer semantic network. Appl. Sci. 2021, 11, 1316. [Google Scholar] [CrossRef]
- Li, J.; Xu, K.; Chaudhuri, S.; Yumer, E.; Zhang, H.; Guibas, L. Grass: Generative recursive autoencoders for shape structures. ACM Trans. Graph. 2017, 36, 1–14. [Google Scholar] [CrossRef]
- Sankaran, S.; Sanju, S.; Achuthan, K. Towards realistic energy profiling of blockchains for securing internet of things. In Proceedings of the 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–6 July 2018; pp. 1454–1459. [Google Scholar]
- Wang, Y.; Han, X.; Jin, S. MAP based modeling method and performance study of a task offloading scheme with time-correlated traffic and VM repair in MEC systems. Wirel. Netw. 2022, 1–22. [Google Scholar] [CrossRef]
- Kouzinopoulos, C.S.; Spathoulas, G.; Giannoutakis, K.M.; Votis, K.; Pandey, P.; Tzovaras, D.; Katsikas, S.K.; Collen, A.; Nijdam, N.A. Using blockchains to strengthen the security of internet of things. In Proceedings of the International ISCIS Security Workshop, London, UK, 27–28 February 2018; pp. 90–100. [Google Scholar]
- Ma, K.; Li, Z.; Liu, P.; Yang, J.; Geng, Y.; Yang, B.; Guan, X. Reliability-constrained throughput optimization of industrial wireless sensor networks with energy harvesting relay. IEEE Internet Things J. 2021, 8, 13343–13354. [Google Scholar] [CrossRef]
- Roy, S.; Ashaduzzaman, M.; Hassan, M.; Chowdhury, A.R. Blockchain for IoT security and management: Current prospects, challenges and future directions. In Proceedings of the 2018 5th International Conference on Networking, Systems and Security (NSysS), Dhaka, Bangladesh, 18–20 December 2018; pp. 1–9. [Google Scholar]
- Rahulamathavan, Y.; Phan, R.C.-W.; Rajarajan, M.; Misra, S.; Kondoz, A. Privacy-preserving blockchain based IoT ecosystem using attribute-based encryption. In Proceedings of the 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Bhubaneswar, India, 17–20 December 2017; pp. 1–6. [Google Scholar]




| Phrase | Abbreviation |
|---|---|
| Internet of Things | IoT |
| Inter Planetary File System | IPFS |
| Software Defined Networks | SDN |
| Denial of Service | DoS |
| Peer to Peer | P2P |
| Address Resolution Protocol | ARP |
| Proof-of-Work | POW |
| Network Function Virtualization | NFV |
| Decentralized Autonomous Organization | DAO |
| Hierarchical Identity Based Encryption | HIBE |
| Industrial IoT | IIoT |
|
|
|---|---|
|
|
|
|
|
|
| Title | Type | Authors | Journal | Classification | Keywords | Ref No. |
|---|---|---|---|---|---|---|
|
|
|
|
|
| [43] |
|
|
|
|
|
| [44] |
|
|
|
|
|
| [45] |
|
|
|
|
|
| [46] |
|
|
|
|
|
| [47] |
|
|
|
|
|
| [48] |
|
|
|
|
|
| [49] |
|
|
|
|
|
| [50] |
|
|
|
|
|
| [51] |
|
|
|
|
|
| [52] |
|
|
|
|
|
| [53] |
|
|
|
|
|
| [54] |
|
|
|
|
|
| [55] |
|
|
|
|
|
| [56] |
|
|
|
|
|
| [57] |
|
|
|
|
|
| [58] |
|
|
|
|
|
| [59] |
|
|
|
|
|
| [60] |
|
|
|
|
|
| [61] |
|
|
|
|
|
| [62] |
| Ref No. | Case Study | Technique | Achievement | Tools |
|---|---|---|---|---|
| [43] |
|
|
|
|
| [44] |
|
|
|
|
| [45] |
|
|
|
|
| [46] |
|
|
|
|
| Ref No. | Case Study | Technique | Achievement | Tools |
|---|---|---|---|---|
| [47] |
|
|
|
|
| [49] |
|
|
|
|
| [48] |
|
|
|
|
| [50] |
|
|
|
|
| [51] |
|
|
|
|
| Ref No. | Case Study | Technique | Achievement | Tools |
|---|---|---|---|---|
| [52] |
|
|
|
|
| [53] |
|
|
|
|
| [54] |
|
|
|
|
| [55] |
|
|
|
|
| [56] |
|
|
|
|
| Ref No. | Case Study | Technique | Achievement | Tools |
|---|---|---|---|---|
| [57] |
|
|
|
|
| [58] |
|
|
|
|
| [59] |
|
|
|
|
| [60] |
|
|
|
|
| [61] |
|
|
|
|
| [62] |
|
|
|
|
| Journal Name | Number of Articles | Percentage | Citation (Total Cited) |
|---|---|---|---|
| IEEE Internet of Things Journal | 132 | 12.3% | 3968 |
| IEEE Access | 70 | 6.5% | 2833 |
| IEEE Transactions on Industrial Informatics | 46 | 4.2% | 2807 |
| Sensors Switzerland | 36 | 3.3% | 1603 |
| Wireless Communications and Mobile Computing | 34 | 3.1% | 210 |
| Sensors | 31 | 2.8% | 166 |
| Electronics Switzerland | 23 | 2.1% | 232 |
| Future Generation Computer Systems | 20 | 1.8% | 2779 |
| Transactions on Emerging Telecommunications Technologies | 19 | 1.7% | 221 |
| Security and Communication Networks | 18 | 1.6% | 633 |
| IEEE Network | 18 | 1.6% | 759 |
| International Journal of Advanced Computer Science and Applications | 16 | 1.4% | 96 |
| Applied Sciences Switzerland | 15 | 1.3% | 212 |
| IEEE Transactions on Computational Social Systems | 14 | 1.3% | 497 |
| Computers Materials and Continua | 13 | 1.2% | 91 |
| P2P Networking and Applications | 12 | 1.1% | 144 |
| Sustainability Switzerland | 11 | 1.0% | 144 |
| Future Internet | 11 | 1.0% | 183 |
| Cluster Computing | 11 | 1.0% | 232 |
| Journal of Parallel and Distributed Computing | 10 | 0.9% | 269 |
| International Journal of Recent Technology and Engineering | 10 | 0.9% | 44 |
| Keywords | Occurrences | Total Link Strength | Keywords | Occurrences | Total Link Strength | Keywords | Occurrences | Total Link Strength |
|---|---|---|---|---|---|---|---|---|
| AI | 15 | 58 | Deep reinforcement learning (DRL) | 7 | 16 | IIoT | 10 | 29 |
| Big data | 15 | 64 | Edge computing | 55 | 194 | IoT | 220 | 572 |
| Blockchain technology | 36 | 77 | Energy efficiency | 8 | 21 | Mobile edge computing | 8 | 18 |
| Cloud computing | 31 | 144 | Fog computing | 40 | 162 | Permissioned blockchain | 8 | 21 |
| Cryptography | 16 | 75 | Industrial IoT | 41 | 91 | Privacy protection | 9 | 31 |
| Data models | 9 | 62 | Industry 4.0 | 18 | 63 | Smart city | 17 | 52 |
| Data privacy | 12 | 55 | IoT | 152 | 355 | Blockchains | 72 | 379 |
| Deep learning | 10 | 33 | Performance evaluation | 7 | 24 | Computational modeling | 7 | 48 |
| Encryption | 9 | 45 | SDN | 8 | 35 | Computer architecture | 8 | 37 |
| Federated learning | 15 | 71 | Security and privacy | 12 | 31 | Industrial IoT | 27 | 101 |
| Healthcare | 21 | 97 | Software-defined-networking (SDN) | 7 | 15 | Industrial IoT | 12 | 39 |
| IoT | 11 | 45 | Access control | 57 | 182 | Optimization | 8 | 32 |
| ML | 17 | 61 | Cloud | 10 | 35 | P2P computing | 10 | 56 |
| Privacy preservation | 10 | 30 | Consensus mechanism | 11 | 29 | Resource management | 7 | 36 |
| Privacy-preserving | 13 | 54 | Consortium blockchain | 10 | 14 | Sensors | 10 | 39 |
| Bitcoin | 12 | 46 | Data integrity | 9 | 29 | Servers | 22 | 140 |
| Consensus | 24 | 59 | Decentralized | 7 | 24 | Supply chain | 17 | 44 |
| Consensus algorithm | 11 | 35 | Ethereum | 22 | 75 | Task analysis | 8 | 41 |
| Data security | 7 | 17 | Identity management | 7 | 26 | Authentication | 54 | 183 |
| Decentralization | 14 | 46 | IoT | 325 | 926 | Authorization | 8 | 34 |
| Distributed ledger | 13 | 42 | IPFS | 7 | 32 | Privacy | 71 | 293 |
| Distributed systems | 7 | 28 | Smart contract | 81 | 244 | Security | 185 | 678 |
| IoT security | 16 | 35 | Trust | 22 | 77 | Smart contracts | 41 | 159 |
| Scalability | 26 | 95 | 5G | 8 | 32 | Trust management | 13 | 57 |
| Smart cities | 15 | 55 | COVID-19 | 8 | 30 | |||
| Smart grid | 7 | 17 | Cybersecurity | 11 | 34 | |||
| Smart home | 8 | 24 | Data sharing | 22 | 69 | |||
| Throughput | 7 | 39 | Deep information learning | 7 | 16 | |||
| Blockchain | 753 | 1842 | Hyperledger fabric | 23 | 75 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Darbandi, M.; Al-Khafaji, H.M.R.; Hosseini Nasab, S.H.; AlHamad, A.Q.M.; Ergashevich, B.Z.; Jafari Navimipour, N. Blockchain Systems in Embedded Internet of Things: Systematic Literature Review, Challenges Analysis, and Future Direction Suggestions. Electronics 2022, 11, 4020. https://doi.org/10.3390/electronics11234020
Darbandi M, Al-Khafaji HMR, Hosseini Nasab SH, AlHamad AQM, Ergashevich BZ, Jafari Navimipour N. Blockchain Systems in Embedded Internet of Things: Systematic Literature Review, Challenges Analysis, and Future Direction Suggestions. Electronics. 2022; 11(23):4020. https://doi.org/10.3390/electronics11234020
Chicago/Turabian StyleDarbandi, Mehdi, Hamza Mohammed Ridha Al-Khafaji, Seyed Hamid Hosseini Nasab, Ahmad Qasim Mohammad AlHamad, Beknazarov Zafarjon Ergashevich, and Nima Jafari Navimipour. 2022. "Blockchain Systems in Embedded Internet of Things: Systematic Literature Review, Challenges Analysis, and Future Direction Suggestions" Electronics 11, no. 23: 4020. https://doi.org/10.3390/electronics11234020
APA StyleDarbandi, M., Al-Khafaji, H. M. R., Hosseini Nasab, S. H., AlHamad, A. Q. M., Ergashevich, B. Z., & Jafari Navimipour, N. (2022). Blockchain Systems in Embedded Internet of Things: Systematic Literature Review, Challenges Analysis, and Future Direction Suggestions. Electronics, 11(23), 4020. https://doi.org/10.3390/electronics11234020








