Privacy-Preserving Mobility Model and Optimization-Based Advanced Cluster Head Selection (P2O-ACH) for Vehicular Ad Hoc Networks
Abstract
:1. Introduction
Contribution of the Research
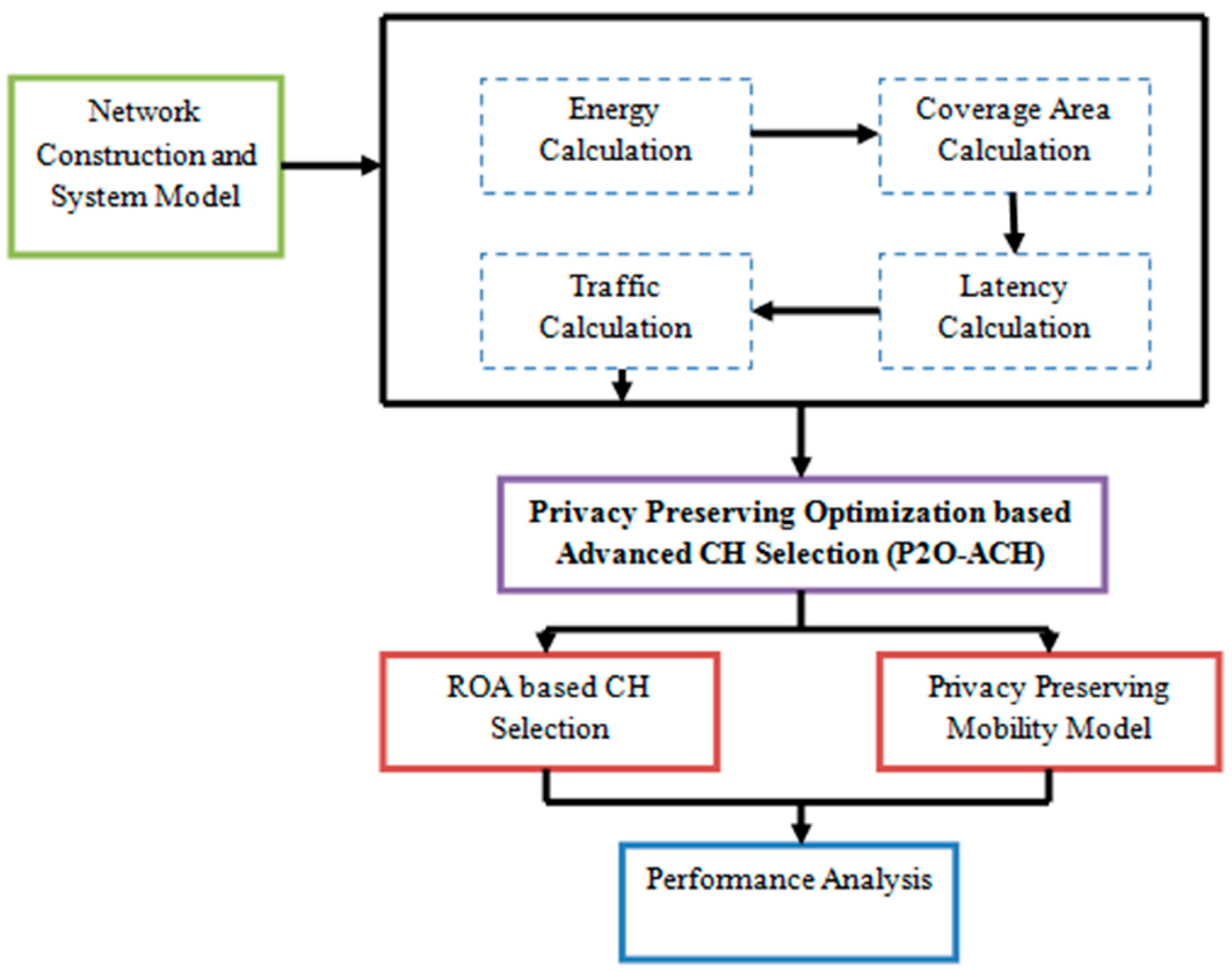
- The purpose of the development of the proposed P20-ACH method is to improve the privacy and energy efficiency of the VANETs network by reducing energy consumption, delay, and routing overhead.
- Effective cluster heads are chosen using the advanced ROA-based CH selection process that results in improving network connectivity and stability that reflects in the reduction of energy consumption and delay in the network.
- To protect the vehicles from malicious activities in this paper, the privacy-preserving mobility model is introduced so that the vehicle behavior is monitored, which reflects in the increase of the trustworthiness of the network.
- Through this effective CH selection and privacy-preserving mobility model, the effectiveness of the network is highly increased, which reflects in the increase of the network lifetime.
2. Related Works
2.1. Clustering Associated Research
2.2. Optimization-Associated Research
3. System Model
3.1. Network Model Assumptions
3.2. Initial CH Selection
4. Privacy-Preserving Optimization Based on Advanced CH Selection (P2O-ACH)
4.1. Data Routing in Clustering
4.2. Conventional ROA
4.3. Enhanced ROA-Based CH Selection
| Algorithm 1. ROA-based CH selection |
| Inputs—Rider inputs Output—Optimal CH selection Start Step 1—For CH selection
Step 6—Return End. |
4.4. Privacy-Preserving Mobility Model
4.4.1. New Node Fusion
4.4.2. Node Migration Process
5. Results and Analysis
5.1. Scenarios Details
5.2. Performance Analysis Based on the Number of Vehicles
Discussion Performance Analysis Based on the Number of Vehicles
5.3. Performance Analysis Based on Speed
Results Discussion
5.4. Algorithm Comparison
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ullah, A.; Yao, X.; Shaheen, S.; Ning, H. Advances in position based routing towards ITS enabled FoG-oriented VANET-A survey. IEEE Trans. Intell. Transp. Syst. 2020, 21, 828–840. [Google Scholar] [CrossRef]
- Al-Mayouf, Y.R.B.; Mahdi, O.A.; Taha, N.A.; Abdullah, N.F.; Khan, S.; Alam, M. Accident management system based on vehicular network for an intelligent transportation system in urban environments. J. Adv. Transp. 2018, 2018, 6168981. [Google Scholar] [CrossRef]
- Abizar; Farman, H.; Jan, B.; Khan, Z.; Koubaa, A. A smart energy-based source location privacy preservation model for Internet of Things-based vehicular ad hoc networks. Trans. Emerg. Telecommun. Technol. 2020, 33, e3973. [Google Scholar] [CrossRef]
- Wei, L.; Wu, J.; Long, C.; Lin, Y.-B. The Convergence of IoE and Blockchain: Security Challenges. IT Prof. 2019, 21, 26–32. [Google Scholar] [CrossRef]
- Abbas, A.H.; Habelalmateen, M.I.; Audah, L.; Alduais, N. A Novel Intelligent Cluster-Head (ICH) to Mitigate the Handover Problem of Clustering in VANETs. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 0100627. [Google Scholar] [CrossRef] [Green Version]
- Abbas, A.H.; Mansour, H.S.; Al-Fatlawi, A.H. Self-Adaptive Efficient Dynamic Multi-Hop Clustering (SA-EDMC) Approach for Improving VANET’s Performance. Int. J. Interact. Mob. Technol. 2022, 16, 136–151. [Google Scholar] [CrossRef]
- Wang, H.; Liu, R.P.; Ni, W.; Chen, W.; Collings, I.B. VANET modeling and clustering design under practical traffic, channel and mobility conditions. IEEE Trans. Commun. 2015, 63, 870–881. [Google Scholar]
- Oubabas, S.; Aoudjit, R.; Rodrigues, J.J.P.C.; Talbi, S. Secure and stable Vehicular Ad Hoc Network clustering algorithm based on hybrid mobility similarities and trust management scheme. Veh. Commun. 2018, 13, 128–138. [Google Scholar] [CrossRef]
- Zhang, D.; Ge, H.; Zhang, T.; Cui, Y.-Y.; Liu, X.; Mao, G. New Multi-Hop Clustering Algorithm for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2018, 20, 1517–1530. [Google Scholar] [CrossRef]
- Tseng, H.-W.; Wu, R.-Y.; Lo, C.-W. A stable clustering algorithm using the traffic regularity of buses in urban VANET scenarios. Wirel. Networks 2019, 26, 2665–2679. [Google Scholar] [CrossRef]
- Bylykbashi, K.; Elmazi, D.; Matsuo, K.; Ikeda, M.; Barolli, L. Effect of security and trust- worthiness for a fuzzy cluster management system in VANETs’. Cogn. Syst. Res. 2019, 55, 153–163. [Google Scholar] [CrossRef]
- Touil, A.; Ghadi, F. Efficient dissemination based on passive approach and dynamic clustering for VANET. Procedia Comput. Sci. 2018, 127, 369–378. [Google Scholar] [CrossRef]
- Khan, A.A.; Abolhasan, M.; Ni, W. An evolutionary game theoretic approach for stable and optimized clustering in VANETs. IEEE Trans. Veh. Technol. 2018, 67, 4501–4513. [Google Scholar] [CrossRef]
- Otrok, H.; Mourad, A.; Robert, J.M.; Moati, N.; Sanadiki, H. A cluster-based model for QoS-OLSR protocol for urban vehicular ad hoc networks. In Proceedings of the 2011 7th International Wireless Communications and Mobile Computing Conference, Istanbul, Turkey, 4–8 July 2011; pp. 1099–1104. [Google Scholar]
- Tan, H.; Zheng, W.; Vijayakumar, P.; Sakurai, K.; Kumar, N. An Efficient Vehicle-Assisted Aggregate Authentication Scheme for Infrastructure-Less Vehicular Networks. IEEE Trans. Intell. Transp. Syst. 2022, 1–11. [Google Scholar] [CrossRef]
- Tan, H.; Kim, P.; Chung, I. Practical Homomorphic Authentication In Cloud-Assisted Vanets With Blockchain-Based Healthcare Monitoring For Pandemic Control. Electronics 2022, 9, 1683. [Google Scholar] [CrossRef]
- Xue, K.; Luo, X.; Ma, Y.; Li, J.; Liu, J.; Wei, D.S.L. A Distributed Authentication Scheme Based on Smart Contract for Roaming Service in Mobile Vehicular Networks. IEEE Trans. Veh. Technol. 2022, 71, 5284–5297. [Google Scholar] [CrossRef]
- Alami, E.H.; Najid, A. ECH: An Enhanced Clustering Hierarchy Approach to Maximize Lifetime of Wireless Sensor Networks. IEEE Access 2019, 7, 107142–107153. [Google Scholar] [CrossRef]
- Awan, K.A.; Din, I.U.; Almogren, A.; Guizani, M.; Khan, S. StabTrust-A Stable and Centralized Trust-Based Clustering Mechanism for IoT Enabled Vehicular Ad-Hoc Networks. IEEE Access 2020, 8, 21159–21177. [Google Scholar] [CrossRef]
- Du, M.; Ding, S.; Xue, Y.; Shi, Z. A novel density peaks clustering with sensitivity of local density and density-adaptive metric. Knowl. Inf. Syst. 2018, 59, 285–309. [Google Scholar] [CrossRef]
- Tambawal, A.B.; Noor, R.; Salleh, R.; Chembe, C.; Oche, M. Enhanced weight-based clustering algorithm to provide reliable delivery for VANET safety applications. PLoS ONE 2019, 14, e0214664. [Google Scholar] [CrossRef]
- Alsuhli, G.H.; Khattab, A.; Fahmy, Y.A. Double-Head Clustering for Resilient VANETs. Wirel. Commun. Mob. Comput. 2019, 2019, 2917238. [Google Scholar] [CrossRef]
- Behera, T.M.; Mohapatra, S.K.; Samal, U.C.; Khan, M.S.; Daneshmand, M.; Gandomi, A.H. Residual Energy-Based Cluster-Head Selection in WSNs for IoT Application. IEEE Internet Things J. 2019, 6, 5132–5139. [Google Scholar] [CrossRef] [Green Version]
- Elira, B.; Keerthana, K.P.; Balaji, K. Clustering scheme and destination aware context based routing protocol for VANET. Int. J. Intell. Netw. 2021, 2, 148–155. [Google Scholar] [CrossRef]
- Kandali, K.; Bennis, L.; Bennis, H. A New Hybrid Routing Protocol Using a Modified K-Means Clustering Algorithm and Continuous Hopfield Network for VANET. IEEE Access 2021, 9, 47169–47183. [Google Scholar] [CrossRef]
- Jabbar, M.K.; Trabelsi, H. A Novelty of Hypergraph Clustering Model (HGCM) for Urban Scenario in VANET. IEEE Access 2022, 10, 66672–66693. [Google Scholar] [CrossRef]
- Alsarhan, A.; Kilani, Y.; Al-Dubai, A.; Zomaya, A.Y.; Hussain, A. Novel Fuzzy and Game Theory Based Clustering and Decision Making for VANETs. IEEE Trans. Veh. Technol. 2019, 69, 1568–1581. [Google Scholar] [CrossRef] [Green Version]
- Ardakani, S.P.; Kwong, C.F.; Kar, P.; Liu, Q.; Li, L. CNN: A Cluster-Based Named Data Routing for Vehicular Networks. IEEE Access 2021, 9, 159036–159047. [Google Scholar] [CrossRef]
- Sewalkar, P.; Seitz, J. MC-COCO4V2P: Multi-Channel Clustering-Based Congestion Control for Vehicle-to-Pedestrian Communication. IEEE Trans. Intell. Veh. 2020, 6, 523–532. [Google Scholar] [CrossRef]
- Rashid, S.A.; Alhartomi, M.; Audah, L.; Hamdi, M.M. Reliability-Aware Multi-Objective Optimization-Based Routing Protocol for VANETs Using Enhanced Gaussian Mutation Harmony Searching. IEEE Access 2022, 10, 26613–26627. [Google Scholar] [CrossRef]
- Hossain, M.A.; Noor, R.M.; Yau, K.-L.A.; Azzuhri, S.R.; Z’Abar, M.R.; Ahmedy, I.; Jabbarpour, M.R. Multi-Objective Harris Hawks Optimization Algorithm Based 2-Hop Routing Algorithm for CR-VANET. IEEE Access 2021, 9, 58230–58242. [Google Scholar] [CrossRef]
- Javed, A.R.; Hassan, M.A.; Shahzad, F.; Ahmed, W.; Singh, S.; Baker, T.; Gadekallu, T.R. Integration of Blockchain Technology and Federated Learning in Vehicular (IoT) Networks: A Comprehensive Survey. Sensors 2022, 22, 4394. [Google Scholar] [CrossRef] [PubMed]
- Singh, G.D.; Prateek, M.; Kumar, S.; Verma, M.; Singh, D.; Lee, H.-N. Hybrid Genetic Firefly Algorithm-Based Routing Protocol for VANETs. IEEE Access 2022, 10, 9142–9151. [Google Scholar] [CrossRef]
- Sindhwani, M.; Singh, R.; Sachdeva, A.; Singh, C. Improvisation of optimization technique and AODV routing protocol in VANET. Mater. Today: Proc. 2021, 49, 3457–3461. [Google Scholar] [CrossRef]
- Islam, M.; Khan, M.T.R.; Saad, M.M.; Tariq, M.A.; Kim, D. Dynamic positioning of UAVs to improve network coverage in VANETs. Veh. Commun. 2022, 36, 100498. [Google Scholar] [CrossRef]
- Fahad, M.; Aadil, F.; Rehman, Z.; Khan, S.; Shah, P.A.; Muhammad, K.; Lloret, J.; Wang, H.; Lee, J.W.; Mehmood, I. Grey wolf optimization based clustering algorithm for vehicular ad-hoc networks. Comput. Electr. Eng. 2018, 70, 853–870. [Google Scholar] [CrossRef]
- Khan, Z.; Fang, S.; Koubaa, A.; Fan, P.; Abbas, F.; Farman, H. Street-centric routing scheme using ant colony optimization-based clustering for bus-based vehicular ad-hoc network. Comput. Electr. Eng. 2020, 86, 106736. [Google Scholar] [CrossRef]
- Fatemidokht, H.; Rafsanjani, M.K. QMM-VANET: An efficient clustering algorithm based on QoS and monitoring of malicious vehicles in vehicular ad hoc networks. J. Syst. Softw. 2020, 165, 110561. [Google Scholar] [CrossRef]
- Alazab, M.; Lakshmanna, K.; Reddy, T.; Pham, Q.-V.; Maddikunta, P.K.R. Multi-objective cluster head selection using fitness averaged rider optimization algorithm for IoT networks in smart cities. Sustain. Energy Technol. Assess. 2021, 43, 100973. [Google Scholar] [CrossRef]
- Sharef, B.; Alsaqour, R.; Alawi, M.; Abdelhaq, M.; Sundararajan, E. Robust and trust dynamic mobile gateway selection in heterogeneous VANET-UMTS network. Veh. Commun. 2018, 12, 75–87. [Google Scholar] [CrossRef]
- Abbas, A.H.; Ahmed, A.J.; Rashid, S.A. A Cross-Layer Approach MAC/NET with Updated-GA (MNUG-CLA)-Based Routing Protocol for VANET Network. World Electr. Veh. J. 2022, 13, 87. [Google Scholar] [CrossRef]
















| Ref. No | Method | Advantage | Disadvantage |
|---|---|---|---|
| [24] | Destination aware context-based routing scheme | Packet delivery ratio is high and network delay is low | Throughput is low |
| [25] | Modified k-means algorithm and maximum stable set problem | Packet delivery ratio is high and throughput is high | Overhead and delay is high |
| [26] | Hyper graph clustering model | Efficiency, throughput, and packet delivery ratio is high | Delay and routing overhead is high |
| [27] | Fuzzy and game theory-based clustering | Lifetime and efficiency are high | Throughput and packet delivery ratio is low |
| [28] | Cluster-based routing protocol | Packet delivery ratio is high and network delay is low | Overhead is more and throughput is low |
| [29] | Multi-channel clustering-based congestion control algorithm | Energy consumption is low and energy efficiency is high | Throughput is low |
| [30] | Reliability aware multi-objective optimization | Packet delivery ratio is high | Routing overhead is high |
| [31] | Multi-objective Harris Hawks optimization | Packet delivery ratio is high, throughput is high, and network delay is low | Not suitable for a network with huge dynamic mobility model |
| [32] | Cuckoo search optimization | Packet delivery ratio is high | Overhead is more and throughput is low |
| [33] | Hybrid Genetic Firefly Algorithm-based Routing Protocol | Convergence speed of the network is high | Throughput is low |
| [34] | AODV with ant colony optimization | Throughput is high, packet loss is low | Routing overhead is high |
| [35] | Particle swarm optimization algorithm | Packet delivery ratio is high and throughput is high | Overhead is more |
| [36] | A grey wolf optimization-based clustering algorithm | Throughput is high | Efficiency is low |
| [37] | Ant colony optimization (ACO)-based clustering | Computational cost and end-to-end delay are low | Routing overhead is high, throughput is moderate |
| [38] | Quality of service (QoS)-based mobility management | Packet delivery ratio and network stability is high | Throughput is moderate |
| Symbols | Descriptions |
|---|---|
| CH | Cluster Head |
| Normalized Residual Energy | |
| Objective Function for Velocity | |
| Objective Function for Coverage Area | |
| Objective Function for Latency | |
| RE | Residual Energy |
| IE | Initial Energy |
| Average Speed | |
| Transmission Time | |
| Sink Node | |
| Anchor Node | |
| E | Event |
| Threshold Value of the Event | |
| K | Probability Factor |
| BR | Bypass Rider |
| F | Follower |
| O | Overtaker |
| AT | Attacker |
| Communication Type | Communication Items | Model Type |
|---|---|---|
| Short-Distance Communication | Between CM and CH | Free Space Mobility Model |
| Long-Distance Communication | Between CH and | Multi-Path Fading Model |
| Parameters | Values |
|---|---|
| Simulator Version | NS-2.35 |
| Simulation Time | 200 ms |
| Simulation Coverage Area | 1500 m × 1500 m |
| MAC Interface | MAC/802.11 |
| Number of Vehicles | 150 Vehicles |
| Cluster Radius | 500 m |
| Transmission Range | 150 m |
| Vehicle Speed Range | 10 m/s to 35 m/s |
| Channel | Channel/Wireless |
| Radio Propagation Model | Two-Ray Propagation Model |
| Antenna Type | Omni-Directional Antenna |
| Queue Type | DropTail |
| Initial Power | 1000 Joules |
| Transmission Power | 0.005 Joules |
| Receiving Power | 0.001 Joules |
| Data Packet Size | 512 bytes |
| Agent Type | Transmission Control Protocol |
| S. No | GWO-CH | ACO-SCRS | QMM-VANET | P2O-ACH |
|---|---|---|---|---|
| Energy Efficiency | 357 Joules | 598 Joules | 657 Joules | 864 Joules |
| Energy Consumption | 658 Joules | 486 Joules | 358 Joules | 157 Joules |
| S. No | GWO-CH | ACO-SCRS | QMM-VANET | P2O-ACH |
|---|---|---|---|---|
| Packet Loss | 1578 Packets | 1248 Packets | 867 Packets | 458 Packets |
| Network Lifetime | 65.22% | 71.86% | 85.47% | 97.46% |
| S. No | GWO-CH | ACO-SCRS | QMM-VANET | P2O-ACH |
|---|---|---|---|---|
| Packet Delivery Ratio | 75.12% | 81.28% | 89.46% | 95.13% |
| Latency | 681.92 ms | 546.23 ms | 502.48 ms | 253.79 ms |
| S. No | GWO-CH | ACO-SCRS | QMM-VANET | P2O-ACH |
|---|---|---|---|---|
| Routing Overhead | 7658 Packets | 5967 Packets | 3467 Packets | 2547 Packets |
| Network Throughput | 301.124 Kbps | 457.128 Kbps | 857.845 Kbps | 1047.467 Kbps |
| Parameters | Speed (m/s) | GWO-CH | ACO-SCRS | QMM-VANET | P2O-ACH |
|---|---|---|---|---|---|
| Energy Efficiency (%) | 10 | 72.86 | 75.16 | 88.18 | 97.17 |
| 15 | 68.17 | 72.18 | 87.35 | 96.35 | |
| 20 | 65.17 | 71.96 | 86.89 | 95.92 | |
| 25 | 61.23 | 66.86 | 85.27 | 96.75 | |
| 30 | 58.39 | 65.19 | 82.17 | 94.17 | |
| 35 | 55.84 | 62.11 | 78.16 | 91.17 | |
| Energy Consumption (%) | 10 | 18.46 | 15.43 | 11.75 | 8.26 |
| 15 | 25.79 | 22.76 | 15.63 | 11.76 | |
| 20 | 31.22 | 27.13 | 21.75 | 14.86 | |
| 25 | 35.46 | 32.49 | 29.43 | 16.78 | |
| 30 | 41.74 | 35.55 | 31.28 | 18.85 | |
| 35 | 48.32 | 41.76 | 33.86 | 22.17 | |
| Packet Loss (packets) | 10 | 169 | 153 | 125 | 86 |
| 15 | 218 | 196 | 149 | 113 | |
| 20 | 249 | 238 | 182 | 135 | |
| 25 | 283 | 276 | 205 | 148 | |
| 30 | 329 | 309 | 246 | 161 | |
| 35 | 359 | 350 | 287 | 182 | |
| Lifetime (%) | 10 | 72.86 | 78.06 | 85.98 | 98.17 |
| 15 | 70.17 | 76.18 | 84.31 | 97.25 | |
| 20 | 68.17 | 75.96 | 86.19 | 96.12 | |
| 25 | 66.23 | 72.86 | 85.07 | 96.85 | |
| 30 | 66.39 | 72.19 | 84.25 | 95.07 | |
| 35 | 65.84 | 71.11 | 81.25 | 94.65 |
| Parameters | Speed (km/h) | GWO-CH | ACO-SCRS | QMM-VANET | P2O-ACH |
|---|---|---|---|---|---|
| Packet Delivery Ratio (%) | 10 | 68.16 | 73.19 | 88.14 | 98.15 |
| 15 | 65.17 | 72.45 | 87.16 | 98.01 | |
| 20 | 62.17 | 71.26 | 86.29 | 97.46 | |
| 25 | 58.29 | 68.46 | 86.11 | 96.17 | |
| 30 | 57.19 | 69.17 | 85.13 | 95.44 | |
| 35 | 57.24 | 65.24 | 84.25 | 95.02 | |
| Latency (ms) | 10 | 168.2 | 142.7 | 102.41 | 55.13 |
| 15 | 171.2 | 145.8 | 114.80 | 72.19 | |
| 20 | 189.2 | 153.2 | 129.76 | 78.14 | |
| 25 | 201.3 | 152.4 | 141.27 | 81.25 | |
| 30 | 221.5 | 164.2 | 145.76 | 85.76 | |
| 35 | 243.6 | 167.2 | 151.23 | 88.76 | |
| Overhead (packets) | 10 | 1356 | 1243 | 865 | 568 |
| 15 | 1475 | 1386 | 874 | 567 | |
| 20 | 1538 | 1427 | 892 | 586 | |
| 25 | 1689 | 1628 | 964 | 625 | |
| 30 | 1758 | 1625 | 1028 | 645 | |
| 35 | 1869 | 1689 | 1142 | 692 | |
| Throughput (Kbps) | 10 | 121.3 | 153.4 | 212.45 | 356.2 |
| 15 | 129.4 | 158.3 | 221.35 | 386.1 | |
| 20 | 136.2 | 161.2 | 235.27 | 425.1 | |
| 25 | 137.1 | 165.2 | 245.69 | 452.1 | |
| 30 | 141.8 | 171.4 | 249.38 | 486.2 | |
| 35 | 156.7 | 175.2 | 259.36 | 489.2 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdulsattar, N.F.; Mohammed, D.A.; Alkhayyat, A.; Hamed, S.Z.; Hariz, H.M.; Abosinnee, A.S.; Abbas, A.H.; Hassan, M.H.; Jubair, M.A.; Abbas, F.H.; et al. Privacy-Preserving Mobility Model and Optimization-Based Advanced Cluster Head Selection (P2O-ACH) for Vehicular Ad Hoc Networks. Electronics 2022, 11, 4163. https://doi.org/10.3390/electronics11244163
Abdulsattar NF, Mohammed DA, Alkhayyat A, Hamed SZ, Hariz HM, Abosinnee AS, Abbas AH, Hassan MH, Jubair MA, Abbas FH, et al. Privacy-Preserving Mobility Model and Optimization-Based Advanced Cluster Head Selection (P2O-ACH) for Vehicular Ad Hoc Networks. Electronics. 2022; 11(24):4163. https://doi.org/10.3390/electronics11244163
Chicago/Turabian StyleAbdulsattar, Nejood Faisal, Dheyaa Abdulameer Mohammed, Ahmed Alkhayyat, Shemaha Z. Hamed, Hussein Muhi Hariz, Ali S. Abosinnee, Ali Hashim Abbas, Mustafa Hamid Hassan, Mohammed Ahmed Jubair, Fatima Hashim Abbas, and et al. 2022. "Privacy-Preserving Mobility Model and Optimization-Based Advanced Cluster Head Selection (P2O-ACH) for Vehicular Ad Hoc Networks" Electronics 11, no. 24: 4163. https://doi.org/10.3390/electronics11244163
APA StyleAbdulsattar, N. F., Mohammed, D. A., Alkhayyat, A., Hamed, S. Z., Hariz, H. M., Abosinnee, A. S., Abbas, A. H., Hassan, M. H., Jubair, M. A., Abbas, F. H., Algarni, A. D., Soliman, N. F., & El-Shafai, W. (2022). Privacy-Preserving Mobility Model and Optimization-Based Advanced Cluster Head Selection (P2O-ACH) for Vehicular Ad Hoc Networks. Electronics, 11(24), 4163. https://doi.org/10.3390/electronics11244163










