The dynamic behaviors, especially the time-varying connection relationship and the dynamic link characteristic, are the main features of SN and also pose challenges to emulate the SN environment.
4.2.2. Implementation of a Time-Varying Connection Relationship
(1) Computation Principle
The link types in SN can be classified into three categories, namely the space-based link, ground-based link, and space–terrestrial link. Due to the mobility of space platforms, the time-varying connection relationship is mainly reflected in the space-based link and space–terrestrial link. The mutual visibility between two space platforms or between a space platform and a ground-based node determines whether there exists a corresponding link. Relying on the location parameters of emulation nodes, the main controller calculates the actual position of nodes, and then achieves the mutual visibility between nodes at each time slot. The calculation principle is described as follows.
a. Space-based Link
In a space-based link, the mutual visibility is defined as the direct line of sight between two space platforms at a certain time. Considering the geometry defined in
Figure 5a, in which Sat. 1 and Sat. 2 are visible to each other.
and
are the position vectors of Sat. 1 and Sat. 2, respectively.
emanates from the Earth’s dynamical center perpendicular to
at
h and intersect the Earth’s surface at
q, where
and
are unknown vectors,
is the distance vector from Sat. 1 to
h to Sat. 2. The magnitude of
is divided into
which is the Earth’s radius and
which is the thickness of the atmosphere from the Earth’s surface to the vector
. From
Figure 5, two fundamental vector closure equations are:
According to variables, mentioned above, the magnitude of
can be described by the following equations:
Equating Equations (
3) and (
4) and then squaring twice, we obtain an analytical expression for the visibility function as:
The visibility function defined by Equation (
5) can be used to predict explicitly whether satellites are visible to one another or not. The sign of
associated with visibility can be obtained by constructing a case in which direct line-of-sight visibility is impossible, as shown in
Figure 5b. For this case we have:
Then Equation (
3) can be written as:
Hence, we can put this rule:
b. Space–terrestrial Link
In the space–terrestrial link, the mutual visibility is defined as the direct line of sight between a space platform and a ground-based node at a certain time. Considering the geometry defined in
Figure 6, in which a satellite and ground station are visible to each other. The two points represent the satellite (Sat) and ground station (GS), and then the third is the Earth’s center. The subsatellite point is indicated by T, which is the point where the joining line of the satellite and Earth’s center intersect the Earth’s surface. Distance
d represents slant range between a satellite and ground station. This range changes over time since the satellite flies too fast above the ground station. In
Figure 6a, the radius
r is:
is Earth’s radius and
H is satellite’s altitude. The line crossing point GS means the tangent plane to Earth’s surface at point GS, which by definition is in fact the ideal horizon plane. The angle formed between the ideal horizon plane and the slant range is elevation angle
.
Figure 6b is the plane form of the triangle from
Figure 6a.
Two sides of this triangle are usually known as the distance from the ground station to the Earth’s center
, and the distance from the satellite to the Earth’s center-orbital radius. The angle under which the satellite sees the ground station is called the nadir angle. There are four variables in this triangle:
is the elevation angle,
is the nadir angle,
is the central angle and
d is the slant range. As soon as two quantities are known, the others can be found with the following equations:
The most important parameter is the slant range
d which represents the distance from the ground station to the satellite. It is expressed through the elevation angle
. Applying the cosines law for the triangle at
Figure 6 yields:
Solving Equation (
5) by
d yields:
Substituting,
at Equation (
14), finally we will obtain the slant range as function of elevation angle
:
or elevation
expressed for a known slant range
d as:
When
⇒
, the maximum slant range
d is found:
If the distance between the Sat and the GS is outside of the maximum value of d, the two nodes are considered invisible.
Finally, on the basis of link establishment strategies set by researchers, these mutual visibilities are filtered to obtain connection relationships in a specific scenario.
(2) Implementation Method
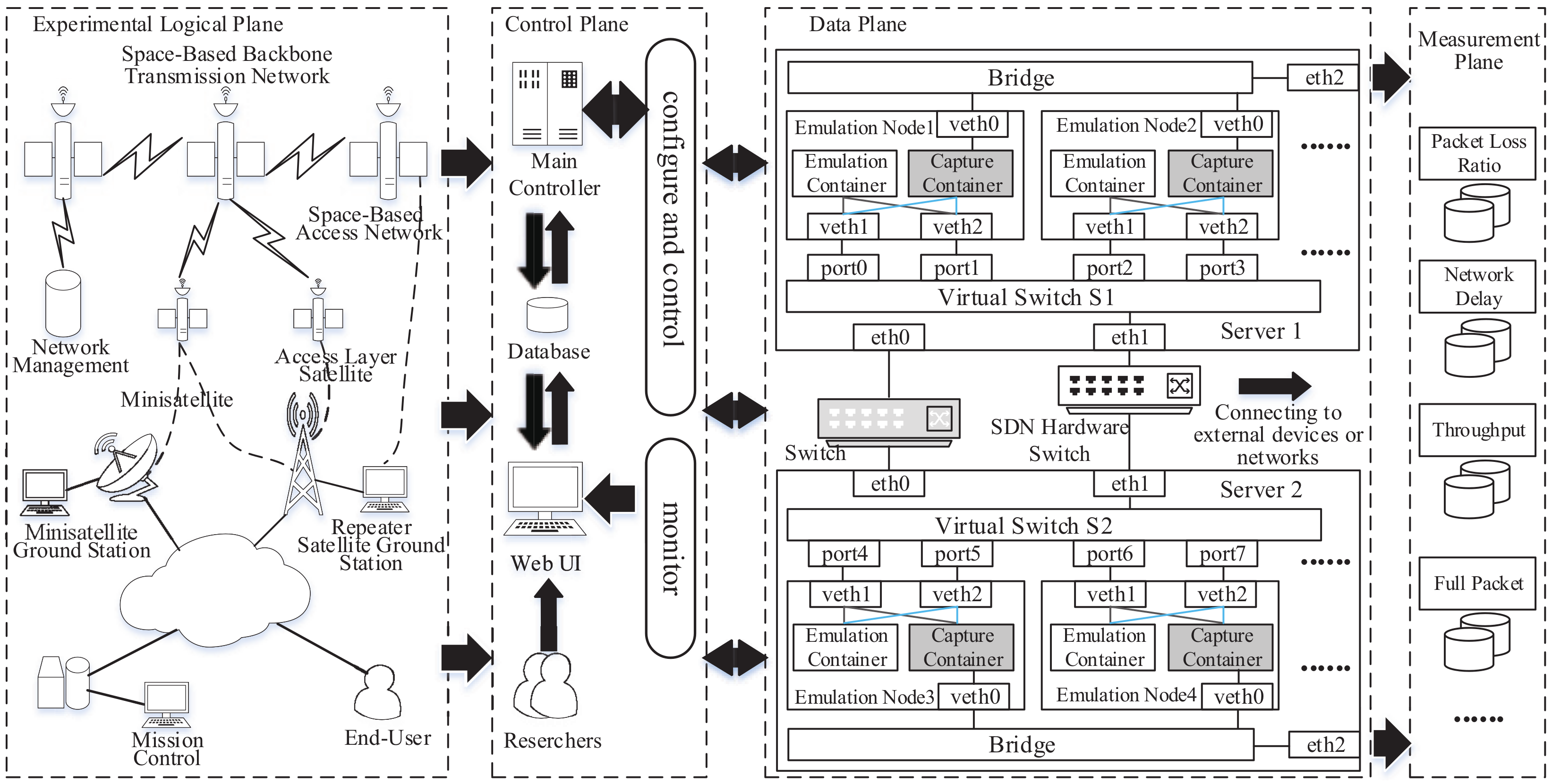
Connection relationships are stored in databases, which are formulated as follows. Link_id is the link name. Srcnode_port and dstnode_port represent the connection port of
| link_id | srcnode_port | dstnode_port | start_time | end_time |
the source node and destination node on virtual switches separately. The srcnode field in srcnode_port means the host name of the emulation node. It is the same for dstnode_port. Start_time and end_time represent the beginning and ending times of a link connection, respectively.
Emulation nodes use virtual ethernet (veth) devices [
30] to access the virtual switch on the server where it is located. Each veth represents an antenna or a communication channel in the network scenario. Veth devices are created in pairs. One device in the pair is assigned to the emulation node as a network interface and the other is assigned to the virtual programmable switch as a port. When either device is down, the link state of the pair is down. So, the variation of connection relationships between pair-wise nodes equates to deleting/adding corresponding flow entries on virtual switches to control the port up and down. However, a port-based flow entry can only control the one-way link. Thus, two flow entries are needed to control a link connection, which is two-way, on or off.
The main controller later allocates corresponding network parameters for network interfaces at the emulation node, including IP addresses, MAC addresses, interface names, etc. The neighboring veths which are connected with each other in one hop have the same subnetwork segment. Whenever corresponding forwarding rules between these veths are deployed, the links between neighboring emulation nodes are working.
Upon the emulation starts, flow entities are issued by the main controller. As shown in
Figure 7, each dynamic link corresponds to a timer and two flow entities. At the start time of emulation, several timers are activated and the on/off time points of each dynamic link are set within them. When the timers expire, the link connection or disconnection functions are executed to deploy corresponding connection or delete corresponding flow entities on virtual switches.
A problem which must be taken into consideration is to emulate the dynamic link connection at the distributed virtual server cluster. When deploying two emulation nodes in a connection link, there are two relative position situations: two nodes located at the same server, and two nodes located at different servers. For the former, the main controller can directly deploy two flow entries at the same virtual switches. Meanwhile, this deployment method is no longer applicable when two emulation nodes are linked to different virtual switches. To solve this issue, the placement of the emulation node in the server cluster and the corresponding host name is recorded when creating the emulation node. Integrated with the fields of srcnode_port and dstnode_port, the corresponding relationship between flow entries and virtual switches can be cleared.
Figure 8 and
Figure 9 show the change of link connection in timeslots TS1 and TS2. When Node3 disconnects with Node2 and connects with Node1 directly, the main controller first deletes the bidirectional flow entries between S1-4 and S2-6 ports, and then adds the bidirectional forwarding rules between S1-2 and S2-5 ports in S1 and S2 separately. Because the forwarding rule is a map between two physical ports in the programmable switch, we can emulate the connectivity of link connections in the physical layer easily.
4.2.3. Implementation of Dynamic Link Characteristic
(1) Computation Principle
On the basis of the signal modulation method and
, the bit error rate (BER) can be gained. The modulation method is a parameter of the emulation node, including FSK, PSK, DPSK, and etc. For example, BER of 2PSK can be expressed by (
18).
is described in Formula (
19), representing the received energy per bit over noise power density.
In Formula (
19),
is the transmitter effective isotropic radiated power, in dBW.
is the receiver antenna gain divided by the receiver system noise temperature, in dB/K.
is the sum of all path losses, described by Formula (
20), in dB.
k is a constant and equal to −228.6 dB.
R is the transmission code rate loss which can be expressed by Formula (
21), and
is bandwidth, in bps. As parameters of the satellite node,
,
,
f, and
are known values. When calculating the mutual visibility between nodes, mentioned in
Section 4.2.2,
d can also be obtained. Thus,
is a computable value.
(2) Implementation Method
In our emulation architecture, the SDN switch only offers the topology management and do not support the simulation of link characteristics. So, another supplementary method is needed to fulfill this function.
All emulation nodes installed the Linux-based operation system in advance. The link characteristic configuration is performed via the Linux traffic control (TC) mechanism [
31]. NetEm is part of TC and supports the emulation of network delay, packet loss ratio, etc. This mechanism also includes a Token Bucket Filter (TBF) for bandwidth limitation. TC has been evaluated in [
32] and has been found to emulate most parameters accurately.
TC can classify different parts of the data packet according to its characteristics and provide different traffic control mechanisms for these packets. The queuing rule is one of the most important parts in TC which can be used to realize the classification function. Before packets are sent by network interfaces, they are added to different send queues according to the characteristics of packets. Then the kernel takes packets from these queues and delivers packets to network interfaces to complete the process of data transmission.
The FIFO algorithm forms the basis for the default queuing disciplines (qdisc) on all Linux network interfaces. It transmits packets as soon as it can receive and queue them, as shown in
Figure 10. A real FIFO qdisc must have a size parameter to prevent it from overflowing in case it is unable to dequeue packets as quickly as it receives them, i.e., when we have a requirement to emulate a high bandwidth with a certain delay, we need to calculate the queue size to avoid discarding packets. The size of the queue is defined by the parameter
, and the unit of
is the packet in TC. We consider the value of
in the worst case. The
would be greater than the average delay
t multiplied by the maximum packet rate. The maximum packet rate equals to the maximum bandwidth
B divided by the maximum transmission unit (MTU). MTU is the largest length of the frame. Its default value is 1500 bytes and this value can be changed according to the needs of experiments.
Via the Formula (
3), the setting value of
in a specific network scenario can be obtained.