QoS Implementation with Triple-Metric-Based Active Queue Management for Military Networks
Abstract
1. Introduction
2. Related Works
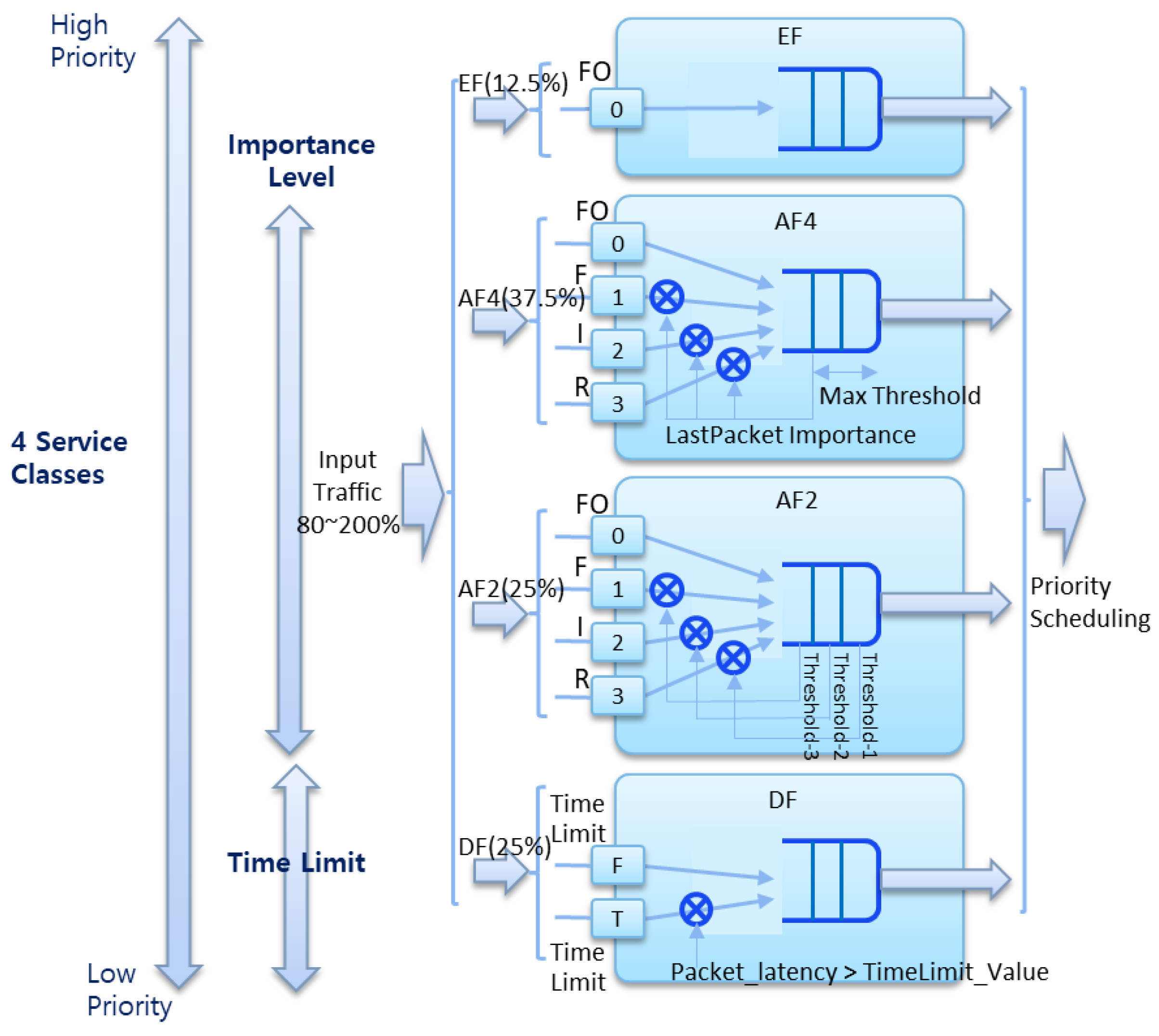
3. Triple-Metric-Based Active Queue Management Algorithms
3.1. Service Class Classification
3.2. Control Service Class Processing
3.3. Real-Time Multimedia Service Class Processing
| Algorithm 1: Real-time multimedia service class processing |
| line becomes idle if queue is not empty then dequeue; if length of queue <= min_threshold then send; else if importance of the packet == highest then send; else if importance of the packet > importance of last packet in queue then send; else drop; |
| new packet is arrived if queue is empty && line is idle then send; else if queue is full then drop; else if length of queue <= max_threshold then enqueue; else if importance of the packet == highest || importance of the packet > importance of last packet in queue then enqueue; else drop; |
3.4. Low-Latency Data Serivce Class Processing
| Algorithm 2: Low-latency data service class processing |
| new packet is arrived if queue is empty && line is idle then send; else if queue is full then drop; else if length of queue < t1 enqueue; else if length of queue >= tn && importance of the packet >= n then enqueue; else drop; |
| line becomes idle if queue is not empty then dequeue; send; |
3.5. Best Effort Service Class Processing
| Algorithm 3: Best effort service class processing |
| new packet arrived if new packet with delivery_deadline flag && remain time of new packet < expected latency then drop; else if queue is empty && line is idle then send; else if queue is full then drop; else enqueue; |
| line becomes idle if queue is not empty then dequeue; if remain time of the packet < expected latency then drop; else send; |
4. Experiments
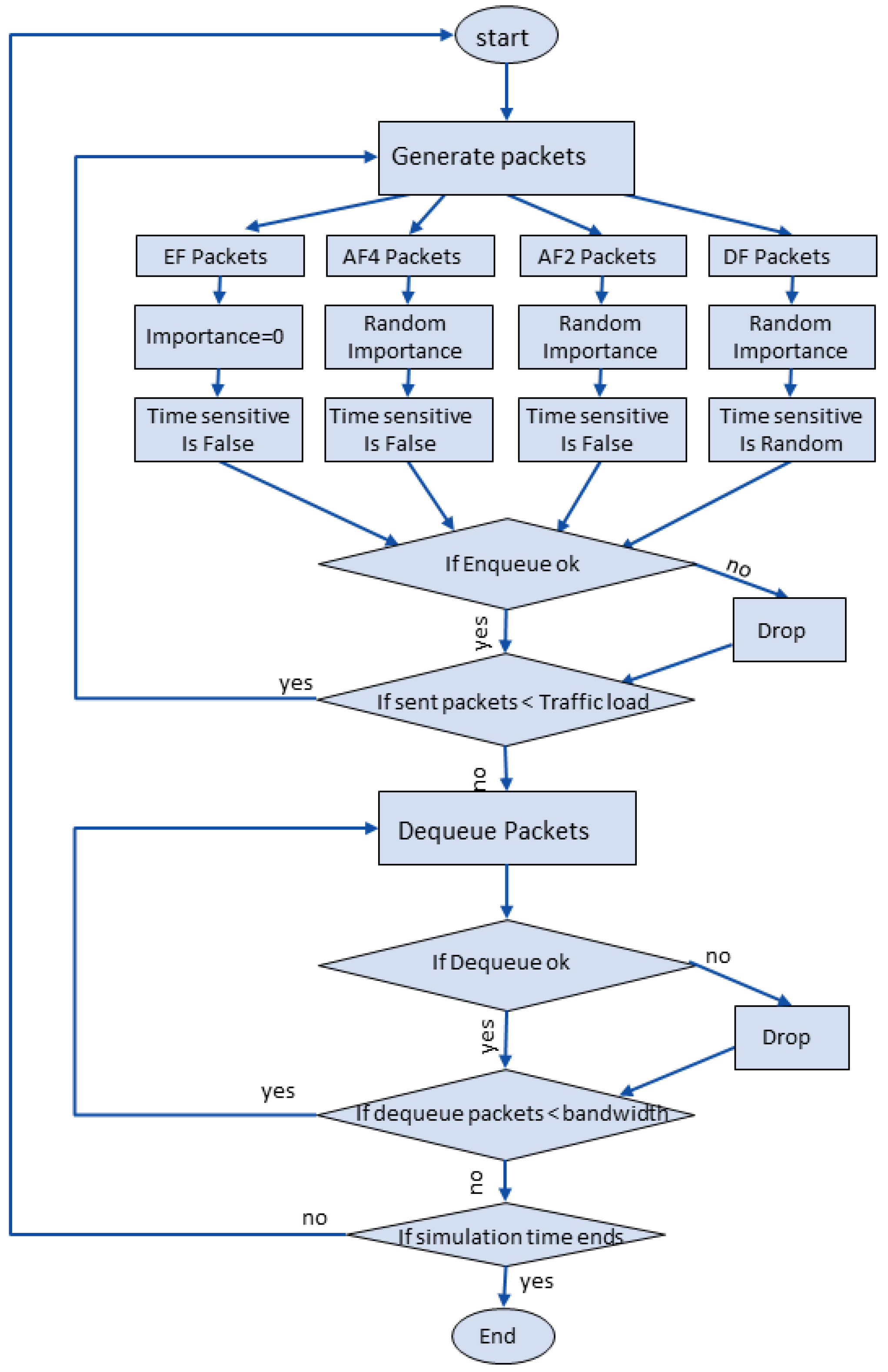
4.1. Simulation Environment
- Bandwidth: 2048 Kbps, 256 byte packet;
- Service Class Traffic Combination: EFRate 12%, AF4Rate 38%, AF2Rate 25%, DFRate 25%;
- Queue Size: EFQueueSize 1000, AF4QueueSize 1000, AF2QueueSize 1000, DFQueueSize 1000;
- Threshold: 1st_threshold 0.25, 2nd_threshold 0.51 and 3rd_threshold 0.76 of Queue size.
- The highest importance (FO) is assigned to the EF traffic;
- Four importance values (FO, F, I, R) are randomly assigned to the AF4 and AF2 traffic;
- Delivery time-limit flags (true, false) are randomly assigned to the DF traffic. A false delivery time-limit flag is fixedly assigned to the EF, AF4, and AF2 traffic.
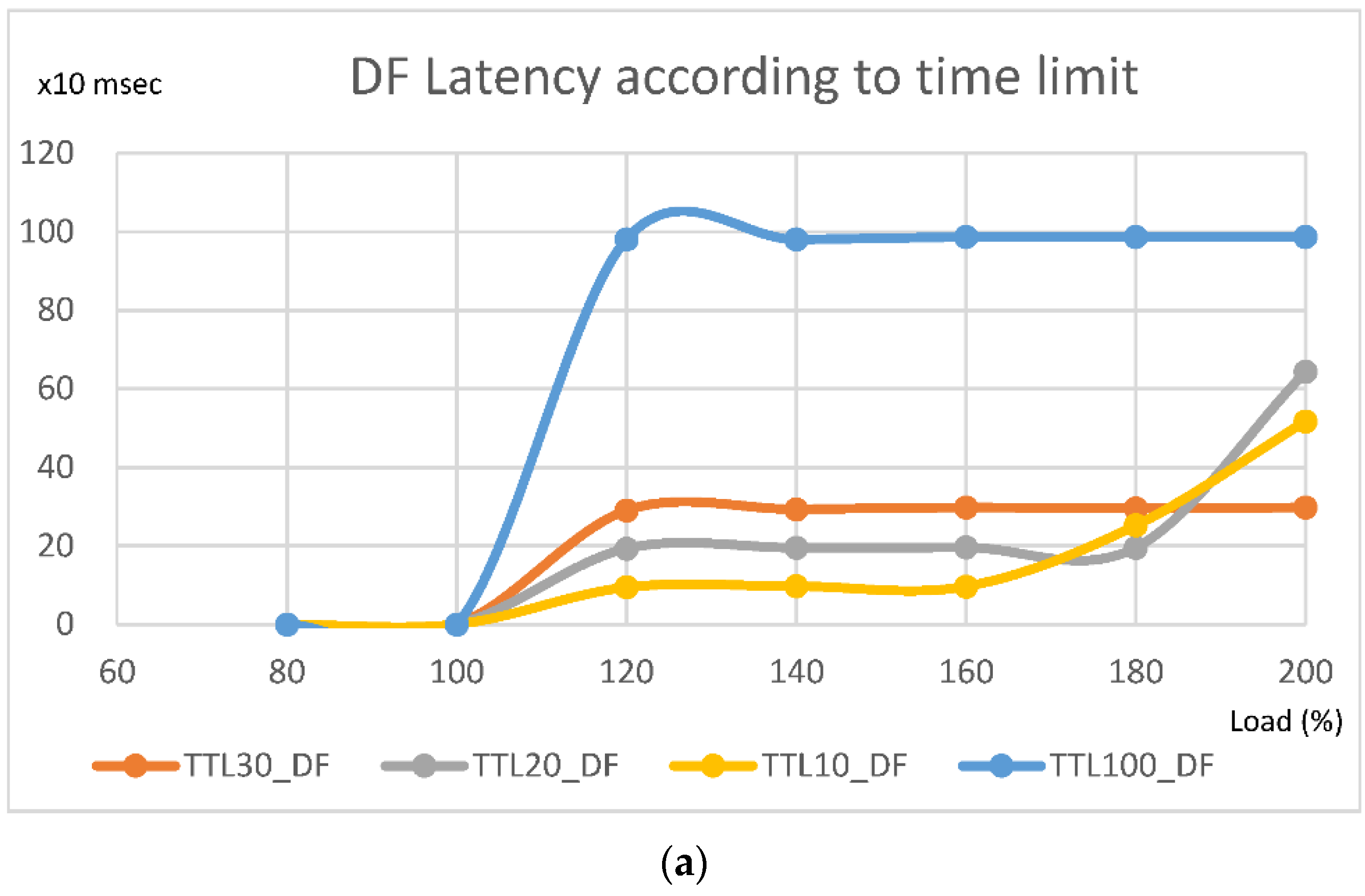
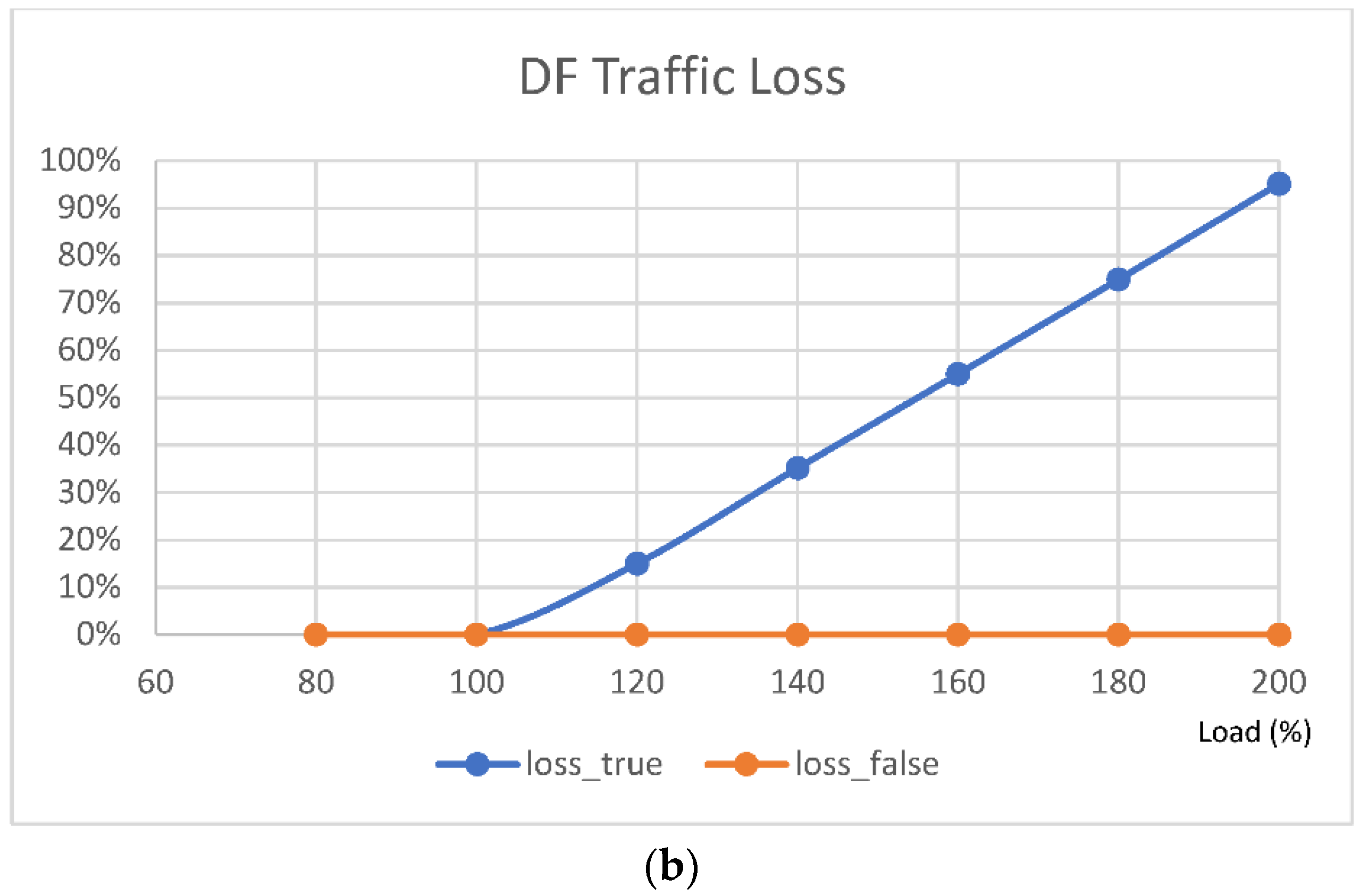
4.2. Performance of Non Real-Time Traffic (DF)
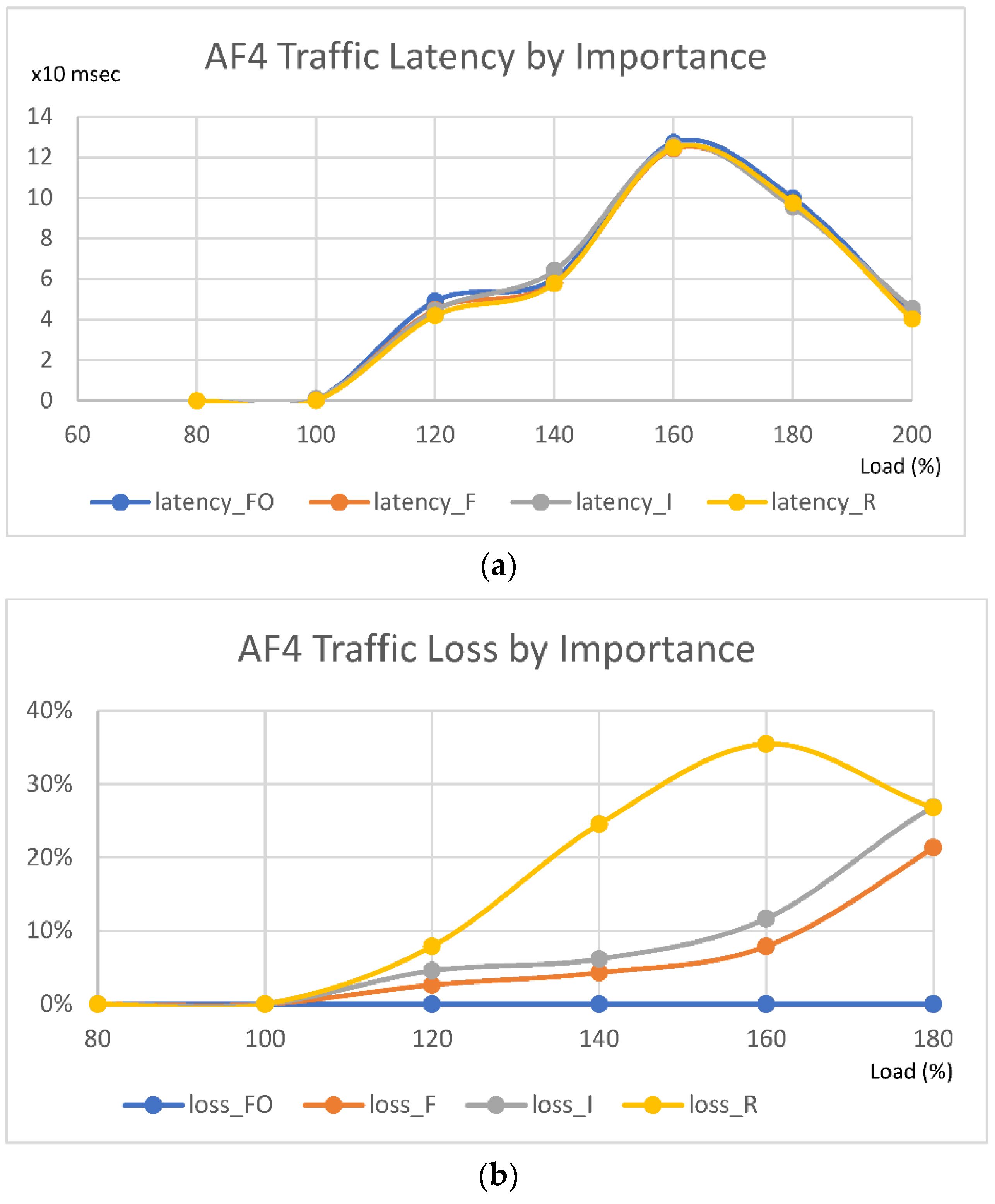
4.3. Performance of Real-Time Traffic (AF4)
4.4. Performance of Low-Latency Traffic (AF2)
- 0~100%: there should be no loss of traffic;
- 100~133.3%: only part of the R traffic is lost;
- 133~200%: 100% of the R traffic is lost and some of the I traffic is lost;
- 200% or more: some of the F traffic is lost.
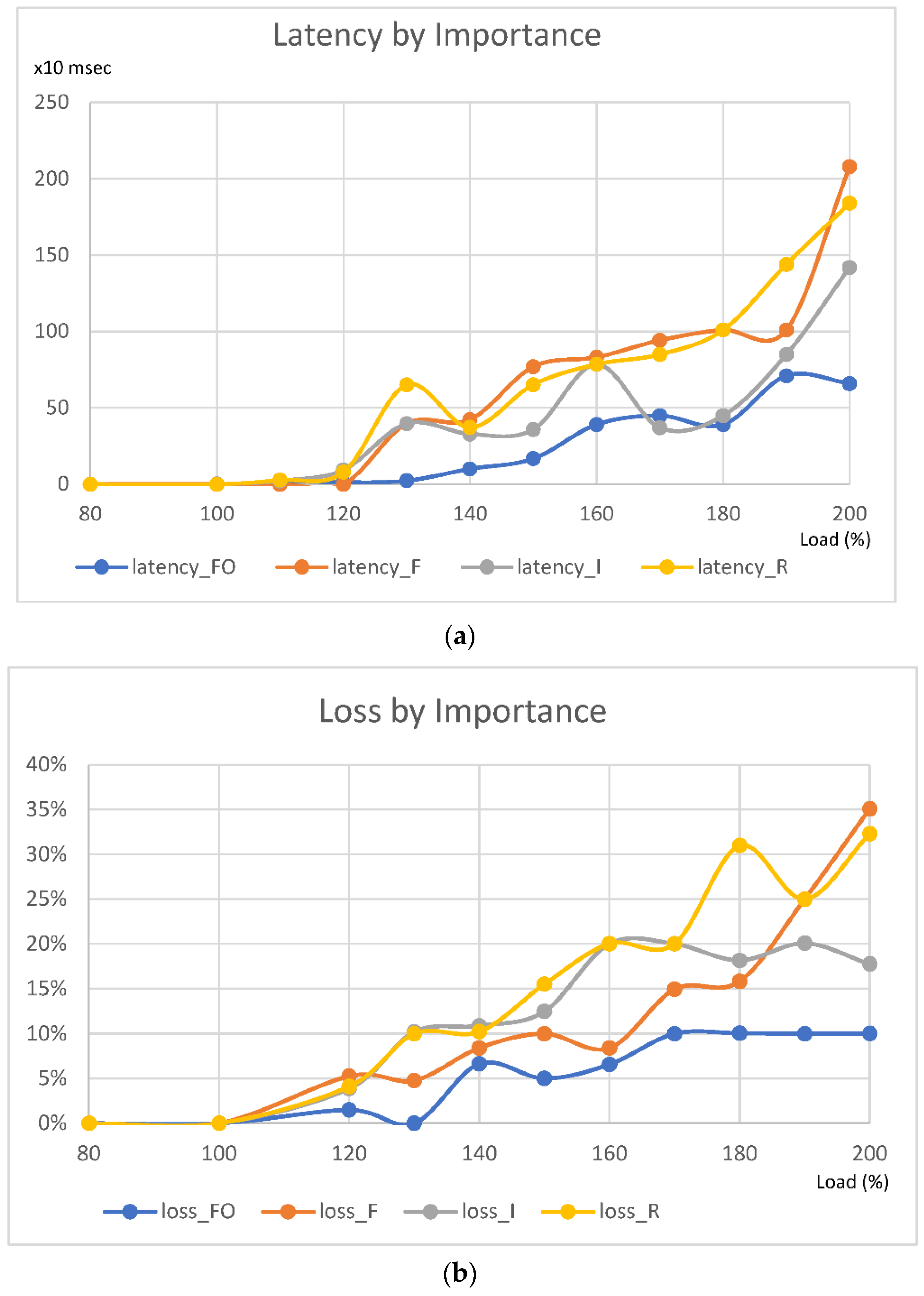
4.5. Performance of Latency and Loss by Service Class
- Loss of the DF traffic occurs when input exceeds 100%;
- Loss of the AF2 traffic occurs when input exceeds 133.3%;
- Loss of the AF4 traffic occurs when input exceeds 200%.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Vesa, K.; Syrjänen, M. Modelling Utility of Networked Services in Military Environments. In Proceedings of the 2019 International Conference on Military Communications and Information Systems (ICMCIS), Budva, Montenegro, 14–15 May 2019; pp. 1–6. [Google Scholar]
- Park, G.; Jeon, H.; Lee, G.M.; Jeon, B. A Study on Implementation and Improvement of Triple-Metric Based QoS for Military Networks. J. Korean Inst. Commun. Inf. Sci. 2022, 47, 1025–1035. [Google Scholar] [CrossRef]
- CJCSI 6211.02D; Defense Information Systems Network (DISN) Responsibilities, JCS J. 24 January 2012. Available online: https://www.jcs.mil/Portals/36/Documents/Library/Instructions/6211_02a.pdf?ver=2016-02-05-175050-653 (accessed on 1 September 2022).
- DoD Architecture Framework 1.5, DoD, April 2007. Available online: https://dodcio.defense.gov/Portals/0/Documents/DODAF/DoDAF_Volume_I.pdf (accessed on 1 September 2022).
- Choi, E.; Lim, B.; Kim, J.; Kim, Y.; Choi, H.; Kim, B.; Nam, S. A Study on Measures to Ensure the Information Exchange between Weapon Systems on the All-IP Tactical Network. Ph.D. Thesis, Ajou University, Suwon-si, Republic of Korea, 2014. [Google Scholar]
- Blake, S.; Black, D.; Carlson, M.; Davies, E.; Wang, Z.; Weiss, W. An Architecture for Differentiated Services, IETF RFC 2475, December 1998. Available online: https://www.rfc-editor.org/rfc/rfc2475 (accessed on 1 September 2022).
- Adams, R. Active Queue Management: A Survey. IEEE Commun. Surv. Tutor. 2013, 15, 1425–1476. [Google Scholar] [CrossRef]
- Jung, S.; Kim, J.; Kim, J.-H. Intelligent Active Queue Management for Stabilized QoS Guarantees in 5G Mobile Networks. IEEE Syst. J. 2021, 15, 4293–4302. [Google Scholar] [CrossRef]
- Braden, R.; Clark, D.; Shenker, S. Integrated Services in the Internet Architecture: An Overview, IETF RFC 1633, June 1994. Available online: https://www.rfc-editor.org/rfc/rfc1633 (accessed on 1 September 2022).
- Joung, J.; Kwon, J. Zero Jitter for Deterministic Networks Without Time-Synchronization. IEEE Access 2021, 9, 49398–49414. [Google Scholar] [CrossRef]
- Satka, Z.; Ashjaei, M.; Fotouhi, H.; Daneshtalab, M.; Sjödin, M.; Mubeen, S. QoS-MAN: A Novel QoS Mapping Algorithm for TSN-5G Flows. In Proceedings of the 2022 IEEE 28th International Conference on Embedded and Real-Time Computing Systems and Applications (RTCSA), Online, 23–25 August 2022; pp. 220–227. [Google Scholar]
- Xin, J.; Xu, S.; Zhang, H.; Xiong, S. A review of Time Sensitive Communication Technology. In Proceedings of the 2022 International Conference on Computer Engineering and Artificial Intelligence (ICCEAI), Shijiazhuang, China, 22–24 July 2022; pp. 844–848. [Google Scholar]
- Thomas, L.; Mifdaoui, A.; Boudec, J.-Y.L. Worst-Case Delay Bounds in Time-Sensitive Networks With Packet Replication and Elimination. in IEEE/ACM Trans. Netw. 2022, 30, 2701–2715. [Google Scholar] [CrossRef]
- Yu, H.; Taleb, T.; Zhang, J. Deterministic Latency/Jitter-Aware Service Function Chaining Over Beyond 5G Edge Fabric. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2148–2162. [Google Scholar] [CrossRef]
- Prados-Garzon, J.; Taleb, T.; Bagaa, M. Optimization of Flow Allocation in Asynchronous Deterministic 5G Transport Networks by Leveraging Data Analytics. IEEE Trans. Mob. Comput. 2021. [Google Scholar] [CrossRef]
- Nasrallah, A.; Thyagaturu, A.S.; Alharbi, Z.; Wang, C.; Shao, X.; Reisslein, M.; El Bakoury, H. Ultra-Low Latency (ULL) Networks: The IEEE TSN and IETF DetNet Standards and Related 5G ULL Research. IEEE Commun. Surv. Tutor. 2019, 21, 88–145. [Google Scholar] [CrossRef]
- Liu, J. Design and Implementation of Vo IPQoS Model Combining IntServ and DiffServ Based on Network Processor IXP2400. In Proceedings of the 2021 7th Annual International Conference on Network and Information Systems for Computers (ICNISC), Guiyang, China, 23–25 July 2021; pp. 60–64. [Google Scholar]
- Aureli, D.; Cianfrani, A.; Diamanti, A.; Vilchez, J.M.S.; Secci, S. Going Beyond DiffServ in IP Traffic Classification. In Proceedings of the NOMS 2020—2020 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 20–24 April 2020; pp. 1–6. [Google Scholar]
- Aureli, D.; Cianfrani, A.; Listanti, M.; Polverini, M.; Secci, S. Augmenting DiffServ operations with dynamically learned classes of services. Comput. Netw. 2022, 202, 108624. [Google Scholar] [CrossRef]
- Huang, Y.-F.; Lin, C.-B.; Chung, C.-M.; Chen, C.-M. Research on QoS Classification of Network Encrypted Traffic Behavior Based on Machine Learning. Electronics 2021, 10, 1376. [Google Scholar] [CrossRef]
- Masaki, H.; Nguyen, K.; Sekiya, H. A QoS-guaranteed System with Software Defined Networking and Micropayment. In Proceedings of the 2021 26th IEEE Asia-Pacific Conference on Communications (APCC), Kuala Lumpur, Malaysia, 11–13 October 2021; pp. 94–98. [Google Scholar]
- da Cruz de Lima, J.C.; Rodrigues, E.B. Quality of Service Control in Software-Defined 5G Networks. In Proceedings of the 2021 IEEE International Conference on Automation/XXIV Congress of the Chilean Association of Automatic Control (ICA-ACCA), Valparaíso, Chile, 22–26 March 2021; pp. 1–6. [Google Scholar]
- Ppallan, J.M.; Arunachalam, K.; Gantha, S.S.; Jaiswal, S.; Song, S.; Nigam, A. A Method for Enabling Context-Awareness at Transport Layer for Improved Quality-of-Service Control. IEEE Access 2021, 9, 123987–123998. [Google Scholar] [CrossRef]
- Bozed, K.A.; Elbeskri, A.M.; Zreg, J.R.A.; Zerek, A.R. Investigation the Performance Effect of QOS in MPLS-TE Network. In Proceedings of the 2021 IEEE 2nd International Conference on Signal, Control and Communication (SCC), Tunis, Tunisia, 20–22 December 2021; pp. 361–367. [Google Scholar]
- McCarthy, J.; Chaudhry, S.R.; Kuppuudaiyar, P.; Loomba, R.; Clarke, S. QoSA-ICN: An information-centric approach to QoS in vehicular environments. Veh. Commun. 2021, 30, 100351. [Google Scholar] [CrossRef]
- Rayani, M.; Ebrahimzadeh, A.; Glitho, R.H.; Elbiaze, H. Ensuring Profit and QoS When Dynamically Embedding Delay-Constrained ICN and IP Slices for Content Delivery. IEEE Trans. Netw. Sci. Eng. 2022, 9, 769–782. [Google Scholar] [CrossRef]
- Zhou, Z.; Shojafar, M.; Alazab, M.; Abawajy, J.; Li, F. AFED-EF: An Energy-Efficient VM Allocation Algorithm for IoT Applications in a Cloud Data Center. IEEE Trans. Green Commun. Netw. 2021, 5, 658–669. [Google Scholar] [CrossRef]
- Zhou, Z.; Abawajy, J.; Chowdhury, M.; Hu, Z.; Li, K.; Cheng, H.; Alelaiwi, A.A.; Li, F. Minimizing SLA violation and power consumption in Cloud data centers using adaptive energy-aware algorithms. Future Gener. Comput. Syst. 2018, 86, 836–850. [Google Scholar] [CrossRef]
- Zhou, Z.; Shojafar, M.; Alazab, M.; Li, F. IECL: An Intelligent Energy Consumption Model for Cloud Manufacturing. IEEE Trans. Ind. Inform. 2022, 18, 8967–8976. [Google Scholar] [CrossRef]
- Yu, C.; Shen, S.; Yang, H.; Zhang, K.; Zhao, H. Leveraging Energy, Latency, and Robustness for Routing Path Selection in Internet of Battlefield Things. IEEE Internet Things J. 2022, 9, 12601–12613. [Google Scholar] [CrossRef]
- Nichols, K.; Blake, S.; Baker, F.; Black, D. Definition of the Differentiated Services Field (DS Field) in the IPv4 and IPv6 Headers, IETF RFC 2474, December 1998. Available online: https://www.rfc-editor.org/rfc/rfc2474 (accessed on 1 September 2022).
- Nagle, J. On Packet Switches with Infinite Storage. IEEE Trans. Commun. 1987, 35, 435–438. [Google Scholar] [CrossRef]
- ITU-T Recommendation, Network performance objectives for IP-based services, Y.1541, February 2006. Available online: https://www.itu.int/rec/T-REC-Y.1541 (accessed on 1 September 2022).




| Service Class | Examples | Note |
|---|---|---|
| Control | Network Control | - |
| Real-Time Multimedia | Telephony, Conferencing | Inelastic |
| Low-Latency Data | Chatting, Messenger, Web Application | Elastic |
| Best Effort | Others | Elastic |
| Service Class | Tolerance to | ||
|---|---|---|---|
| Loss | Latency | Jitter | |
| Control | Low | Low | Very Low |
| Real-Time Multimedia | Very Low | Very Low | Very Low |
| Low-Latency Data | Low | Low | - |
| Best Effort | - | - | - |
| Level | Telephony/Conferencing | Data |
|---|---|---|
| FO (Flash Override) | Commander | Commander/Emergency |
| F (Flash) | Survival related | Operation Supporting |
| I (Immediate) | Security related | Mission Supporting |
| R (Routine) | Official | Administrative |
| Delivery Deadline | Code |
|---|---|
| Yes | 00 |
| No | 01 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, G.; Jeon, B.; Lee, G.M. QoS Implementation with Triple-Metric-Based Active Queue Management for Military Networks. Electronics 2023, 12, 23. https://doi.org/10.3390/electronics12010023
Park G, Jeon B, Lee GM. QoS Implementation with Triple-Metric-Based Active Queue Management for Military Networks. Electronics. 2023; 12(1):23. https://doi.org/10.3390/electronics12010023
Chicago/Turabian StylePark, Gyudong, Byungchun Jeon, and Gyu Myoung Lee. 2023. "QoS Implementation with Triple-Metric-Based Active Queue Management for Military Networks" Electronics 12, no. 1: 23. https://doi.org/10.3390/electronics12010023
APA StylePark, G., Jeon, B., & Lee, G. M. (2023). QoS Implementation with Triple-Metric-Based Active Queue Management for Military Networks. Electronics, 12(1), 23. https://doi.org/10.3390/electronics12010023








