Balancing Password Security and User Convenience: Exploring the Potential of Prompt Models for Password Generation
Abstract
:1. Introduction
- Firstly, we collected a sample of user passwords and analyzed the decision-making process involved in creating them to assess their strength.
- Secondly, we applied a set of rules to modify these passwords and evaluated the factors that affect the memorability of the passwords after the modifications were made.
- Thirdly, we input user information and modified passwords into a prompt model, such as ChatGPT, to generate new passwords for the users.
- Finally, we evaluated the effectiveness of using prompt models to develop stronger and more memorable passwords by applying our rules to the passwords generated by the model and assessing their memorability.
2. Materials and Methods
2.1. Research Participants
2.2. Dataset
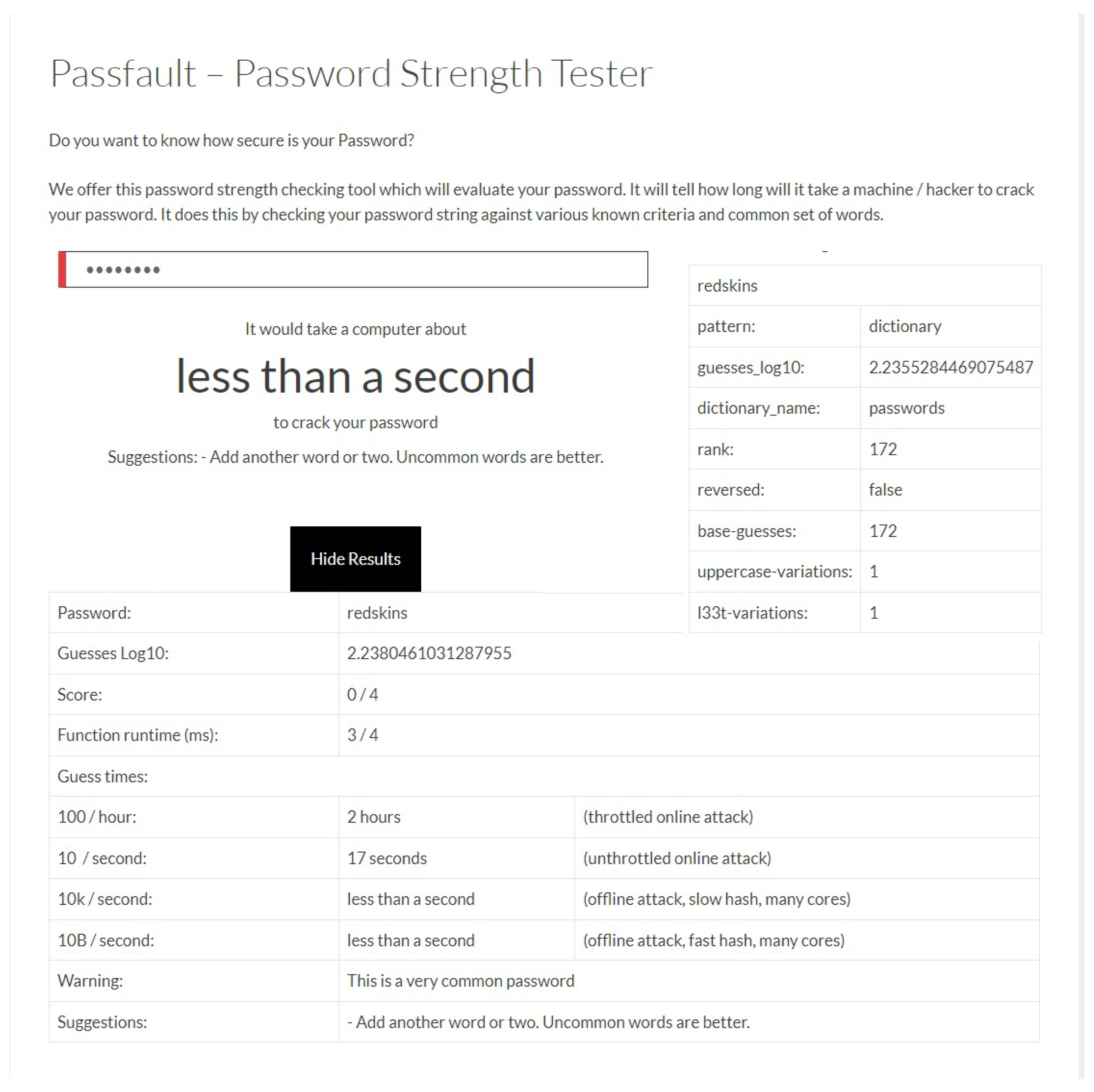
2.3. Password Strength Evaluation
2.4. Prompt Model
2.5. Passwords Modifications
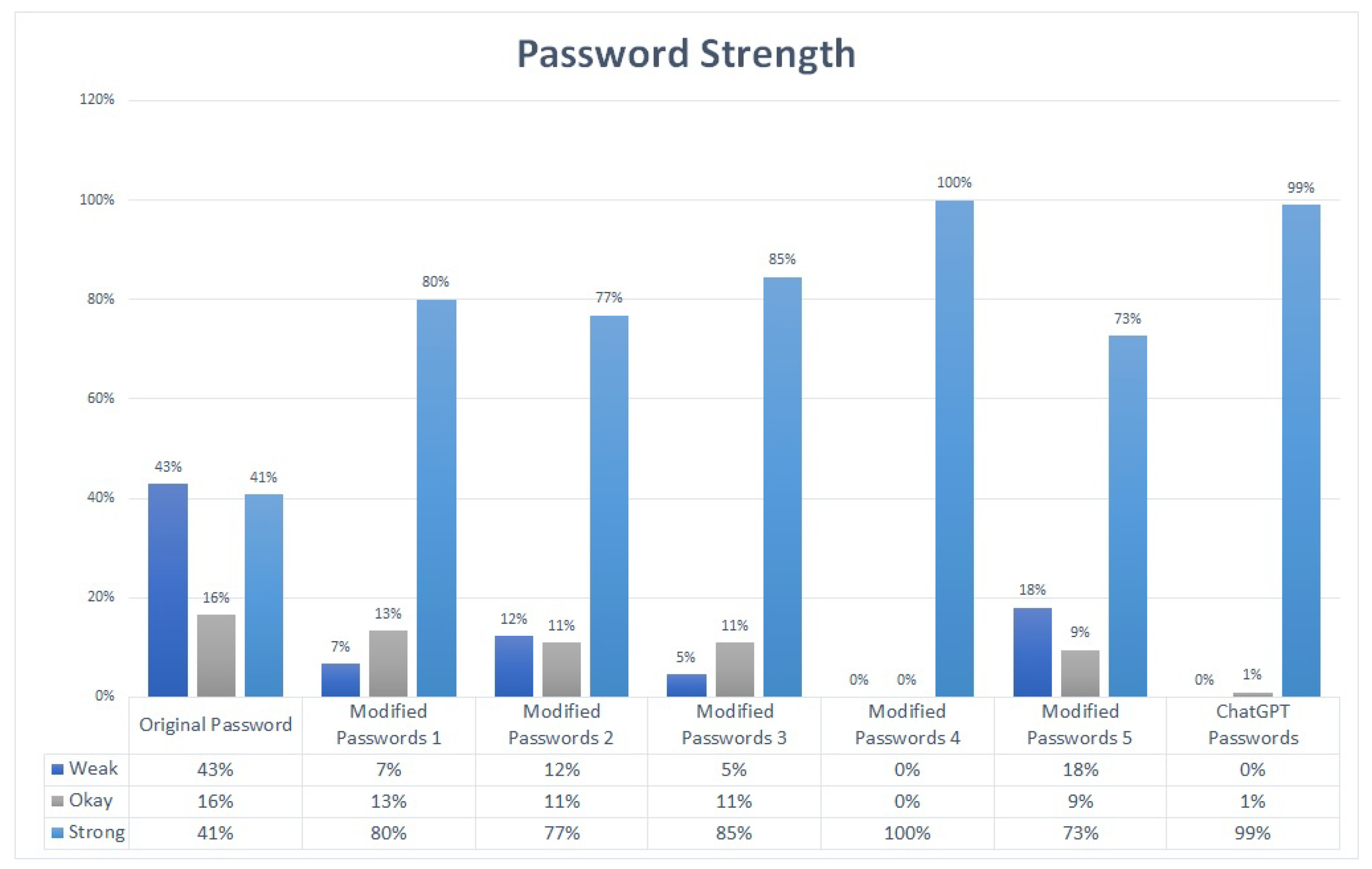
- Substituting vowels with predetermined characters: The first rule involved replacing all vowels in the password with predetermined characters. This approach helps in enhancing password security by increasing the complexity of the password. For example, the word ‘password’ can be modified as ‘p@ssw0rd’.
- Substituting the most frequently occurring vowel: In the second rule, the most frequently occurring vowel in the password was substituted with a predetermined character. This approach further strengthens the password by introducing an additional level of complexity. For instance, the word predetermined can be modified as pr1d2t3rmin4d.
- Adding a four-character mnemonic chunk: The third rule involved adding a three- to five-character mnemonic chunk to the password. This chunk is created based on a pattern, such as the first letter of each word in a phrase. This approach not only enhances password security but also makes it easier to remember. For example, the phrase ‘My favorite color is blue’ can be modified as’ ‘MfciB’.
- Combining the mnemonic chunk with vowel substitution: In the fourth rule, the addition of a mnemonic chunk was combined with the substitution of all vowels to further enhance the password strength. This approach introduces multiple levels of complexity, making it extremely challenging to predict the password. For example, the phrase ‘I love to play football’ can be modified as ‘1Lv2plFtbll#1234’.
- Removing all vowels: In the fifth and final rule, all vowels in the password were removed as an additional measure to improve password security. This approach increases the complexity of the password while making it more challenging to predict. For example, the word ’information’ can be modified as ‘nfrmtn’.
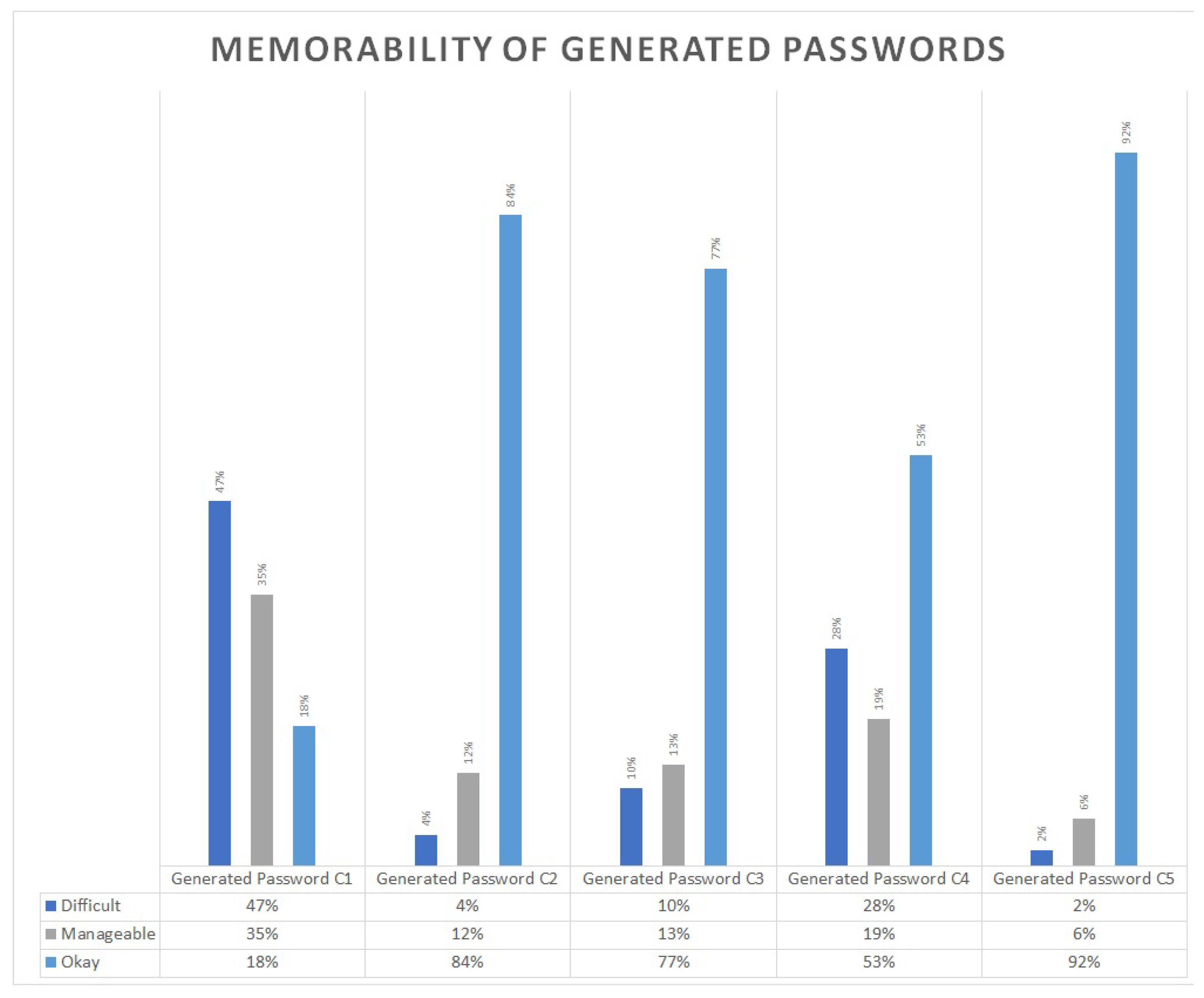
2.6. Memorability Evaluation
2.7. Study Sequence
3. Findings
3.1. Password Strength
3.2. Usability and Current Exposure
3.3. Memorability
4. Limitations and Further Recommendations
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bonneau, J.; Herley, C.; Oorschot, P.C.; Stajano, F. The quest to replace passwords: A framework for comparative evaluation of web authentication schemes. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012. [Google Scholar] [CrossRef]
- Forget, A. A World with Many Authentication Schemes. Ph.D. Thesis, Carleton University, Ottawa, ON, USA, 2012. [Google Scholar] [CrossRef]
- Herley, C.; Van Oorschot, P.C.; Patrick, A.S. Passwords: If we’re so smart, why are we still using them? In Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2009; pp. 230–237. [Google Scholar] [CrossRef]
- Summers, W.C.; Bosworth, E. Password Policy: Proceedings of the Winter International SYNPOSIUM on Information and Communication Technologies. January 2004. Available online: https://dl.acm.org/doi/10.5555/984720.984724 (accessed on 28 March 2023).
- McAfee. The Past, Present, and Future of Password Security. September 2021. Available online: https://www.mcafee.com/blogs/internet-security/security-world-password-day/ (accessed on 28 March 2023).
- Alomari, R.; Thorpe, J. On password behaviours and attitudes in different populations. J. Inf. Secur. Appl. 2019, 45, 79–89. [Google Scholar] [CrossRef]
- Woods, N.; Siponen, M. Improving password memorability, while not inconveniencing the user. Int. J. -Hum.-Comput. Stud. 2019, 128, 61–71. [Google Scholar] [CrossRef]
- Alhamed, A.; Bhatia, S. VowPass: Novel method to generate secure and memorable passwords. In Proceedings of the 2021 4th International Conference on Signal Processing and Information Security (ICSPIS), Virtually, 24–25 November 2021. [Google Scholar] [CrossRef]
- Woods, N.; Siponen, M. Too many passwords? how understanding our memory can increase password memorability. Int. J. -Hum.-Comput. Stud. 2018, 111, 36–48. [Google Scholar] [CrossRef]
- Pearman, S.; Zhang, S.A.; Bauer, L.; Christin, N.; Cranor, L.F. Why People (Don’t) Use Password Managers Effectively: Proceedings of the Fifteenth USENIX Conference on Usable Privacy and Security. August 2019. Available online: https://dl.acm.org/doi/10.5555/3361476.3361500 (accessed on 28 March 2023).
- Alkaldi, N.; Renaud, K.; Mackenzie, L. Encouraging Password Manager Adoption by Meeting Adopter Self-Determination Needs. In Proceedings of the 52nd Hawaii International Conference on System Sciences (HICSS), Maui, HI, USA, 8–11 January 2019; pp. 4824–4833. [Google Scholar]
- Yıldırım, M.; Mackie, I. Encouraging users to improve password security and memorability. Int. J. Inf. Secur. 2019, 18, 741–759. [Google Scholar] [CrossRef]
- Burr, W.; Dodson, D.; Polk, W. Electronic Authentication Guideline. April 2006. Available online: https://csrc.nist.gov/publications/detail/sp/800-63/archive/2006-04-30 (accessed on 28 March 2023).
- Shannon, C.E. Prediction and entropy of printed english. Bell Syst. Tech. J. 1951, 30, 50–64. [Google Scholar] [CrossRef]
- Adams, A.; Sasse, M.A. Users are not the enemy. Commun. ACM 1999, 42, 40–46. [Google Scholar] [CrossRef]
- Keith, M.; Shao, B.; Steinbart, P.J. The usability of passphrases for authentication: An empirical field study. Int. J. -Hum.-Comput. Stud. 2007, 65, 17–28. [Google Scholar] [CrossRef]
- Inglesant, P.G.; Sasse, M.A. The true cost of unusable password policies. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Atlanta, GA, USA, 10–15 April 2010. [Google Scholar] [CrossRef]
- Komanduri, S.; Shay, R.; Kelley, P.G.; Mazurek, M.L.; Bauer, L.; Christin, N.; Cranor, L.F.; Egelman, S. Of passwords and people. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Vancouver, BC, Canada, 7–12 May 2011. [Google Scholar] [CrossRef]
- Grawemeyer, B.; Johnson, H. Using and managing multiple passwords: A week to a View. Interact. Comput. 2011, 23, 256–267. [Google Scholar] [CrossRef]
- Weir, M.; Aggarwal, S.; Collins, M.; Stern, H. Testing metrics for password creation policies by attacking large sets of revealed passwords. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010. [Google Scholar] [CrossRef]
- Florêncio, D.; Herley, C. Where do security policies come from? In Proceedings of the Sixth Symposium on Usable Privacy and Security, Redmond, WA, USA, 14–16 July 2010. [CrossRef]
- Anon. Cracking Passwords in the Cloud: Insights on Password Policies. Available online: http://news.electricalchemy.net/2009/10/password-cracking-in-cloud-part-5.html (accessed on 28 March 2023).
- Grassi, P.; Garcia, M.; Fenton, J. Digital Identity Guidelines. March 2020. Available online: https://csrc.nist.gov/publications/detail/sp/800-63/3/final (accessed on 28 March 2023).
- Anon. Password Policy Best Practices for Strong Security in AD. Available online: https://www.netwrix.com/password_best_practice.html (accessed on 28 March 2023).
- Weir, M.; Aggarwal, S.; de Medeiros, B.; Glodek, B. Password cracking using probabilistic context-free grammars. In Proceedings of the 2009 30th IEEE Symposium on Security and Privacy, Oakland, CA, USA, 17–20 May 2009. [Google Scholar] [CrossRef]
- Wheeler, D.L. Zxcvbn: Low-Budget Password Strength Estimation. In Proceedings of the 25th USENIX Security Symposium (USENIX), Austin, TX, USA, 10–12 August 2016; pp. 157–173. [Google Scholar]
- Melicher, W.; Ur, B.; Segreti, S.M.; Komanduri, S.; Bauer, L.; Christin, N.; Cranor, L.F. Fast, Lean, and Accurate: Proceedings of the 25th USENIX Conference on Security Symposium. August 2016. Available online: https://dl.acm.org/doi/10.5555/3241094.3241109 (accessed on 28 March 2023).
- Shay, R.; Komanduri, S.; Durity, A.L.; Huh, P.S.; Mazurek, M.L.; Segreti, S.M.; Ur, B.; Bauer, L.; Christin, N.; Cranor, L.F. Designing password policies for strength and usability. ACM Trans. Inf. Syst. Secur. 2016, 18, 1–34. [Google Scholar] [CrossRef]
- Schweitzer, D.; Boleng, J.; Hughes, C.; Murphy, L. Visualizing Keyboard Pattern passwords. In Proceedings of the 2009 6th International Workshop on Visualization for Cyber Security, Atlantic City, NJ, USA, 11 October 2009. [Google Scholar] [CrossRef]
- Shay, R.; Komanduri, S.; Durity, A.L.; Huh, P.S.; Mazurek, M.L.; Segreti, S.M.; Ur, B.; Bauer, L.; Christin, N.; Cranor, L.F. Can long passwords be secure and usable? In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Toronto, ON, Canada, 26 April–1 May 2014. [Google Scholar] [CrossRef]
- Lee, K.; Sjöberg, S.; Narayanan, A. Password policies of most top websites fail to follow best practices. In Proceedings of the 2022 ACM Conference on Computer and Communications Security (CCS ’22), Virtual Event, 24–28 October 2022; pp. 1075–1090. [Google Scholar]
- Murray, H.; Malone, D. Evaluating password advice. In Proceedings of the 2017 28th Irish Signals and Systems Conference (ISSC), Killarney, Ireland, 20–21 June 2017. [Google Scholar] [CrossRef]
- Barton, B.F.; Barton, M.S. User-friendly password methods for computer-mediated information systems. Comput. Secur. 1984, 3, 186–195. [Google Scholar] [CrossRef]
- Miller, G.A. The magical number seven, plus or minus two: Some limits on our capacity for processing information. 1956. Available online: https://pubmed.ncbi.nlm.nih.gov/8022966/ (accessed on 28 March 2023).
- Yang, S.; Ji, S.; Beyah, R. DPPG: A dynamic password policy generation system. IEEE Trans. Inf. Forensics Secur. 2018, 13, 545–558. [Google Scholar] [CrossRef]
- Furnell, S.; Khern-am-nuai, W.; Esmael, R.; Yang, W.; Li, N. Enhancing security behaviour by supporting the user. Comput. Secur. 2018, 75, 1–9. [Google Scholar] [CrossRef]
- He, D.; Yang, X.; Zhou, B.; Wu, Y.; Cheng, Y.; Guizani, N. Password enhancement based on Semantic Transformation. IEEE Netw. 2020, 34, 116–121. [Google Scholar] [CrossRef]
- Kakarla, T.; Mairaj, A.; Javaid, A.Y. A real-world password cracking demonstration using Open source tools for instructional use. In Proceedings of the 2018 IEEE International Conference on Electro/Information Technology (EIT), Rochester, MI, USA, 3–5 May 2018. [Google Scholar] [CrossRef]
- Li, H.; Chen, M.; Yan, S.; Jia, C.; Li, Z. Password guessing via neural language modeling. In Proceedings of the Machine Learning for Cyber Security: Second International Conference, ML4CS 2019. Xi’an, China, 19–21 September 2019; pp. 78–93. [Google Scholar] [CrossRef]
- Schroeder, W. DeepPass-Finding Passwords with Deep Learning. June 2022. Available online: https://posts.specterops.io/deeppass-finding-passwords-with-deep-learning-4d31c534cd00 (accessed on 28 March 2023).
- Anon. Passfault—Password Strength Tester. March 2023. Available online: https://www.malwarefox.com/passfault/ (accessed on 28 March 2023).
- Rodrigues, B.; Paiva, J.; Gomes, V.; Morris, C.; Calixto, W. Passfault: An Open Source Tool for Measuring Password Complexity and Strength. In Proceedings of the 8th International Multi-Conference on Complexity, Informatics and Cybernetics (IMCIC), Orlando, FL, USA, 21–24 March 2017. [Google Scholar]
- Anon. Introducing Chatgpt. Available online: https://openai.com/blog/chatgpt (accessed on 28 March 2023).
- Anon. GPT-3 Powers the Next Generation of Apps. Available online: https://openai.com/blog/gpt-3-apps/ (accessed on 28 March 2023).
- Sutskever, I.; Vinyals, O.; Le, Q.V. Sequence to Sequence Learning with Neural Networks: Proceedings of the 27th International Conference on Neural Information Processing Systems—Volume 2. December 2014. Available online: https://dl.acm.org/doi/10.5555/2969033.2969173 (accessed on 28 March 2023).
- Vaswani, A.; Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, Ł.; Polosukhin, I. Attention Is All You Need: Proceedings of the 31st International Conference on Neural Information Processing Systems. December 2017. Available online: https://dl.acm.org/doi/10.5555/3295222.3295349 (accessed on 28 March 2023).
- Vu, K.L.; Proctor, R.W.; Bhargav-Spantzel, A.; Tai, B.; Cook, J.; Schultz, E.E. 2007. Improving password security and memorability to protect personal and organizational information. Int. J. -Hum.-Comput. Stud. 2007, 65, 744–757. [Google Scholar] [CrossRef]
- Chiasson, S.; Forget, A.; Stobert, E.; van Oorschot, P.C.; Biddle, R. Multiple password interference in text passwords and click-based graphical passwords. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Umejiaku, A.P.; Dhakal, P.; Sheng, V.S. Balancing Password Security and User Convenience: Exploring the Potential of Prompt Models for Password Generation. Electronics 2023, 12, 2159. https://doi.org/10.3390/electronics12102159
Umejiaku AP, Dhakal P, Sheng VS. Balancing Password Security and User Convenience: Exploring the Potential of Prompt Models for Password Generation. Electronics. 2023; 12(10):2159. https://doi.org/10.3390/electronics12102159
Chicago/Turabian StyleUmejiaku, Afamefuna P., Prastab Dhakal, and Victor S. Sheng. 2023. "Balancing Password Security and User Convenience: Exploring the Potential of Prompt Models for Password Generation" Electronics 12, no. 10: 2159. https://doi.org/10.3390/electronics12102159




