TEEDAG: A High-Throughput Distributed Ledger Based on TEE and Directed Acyclic Graph
Abstract
1. Introduction
2. Related Work
3. System Design
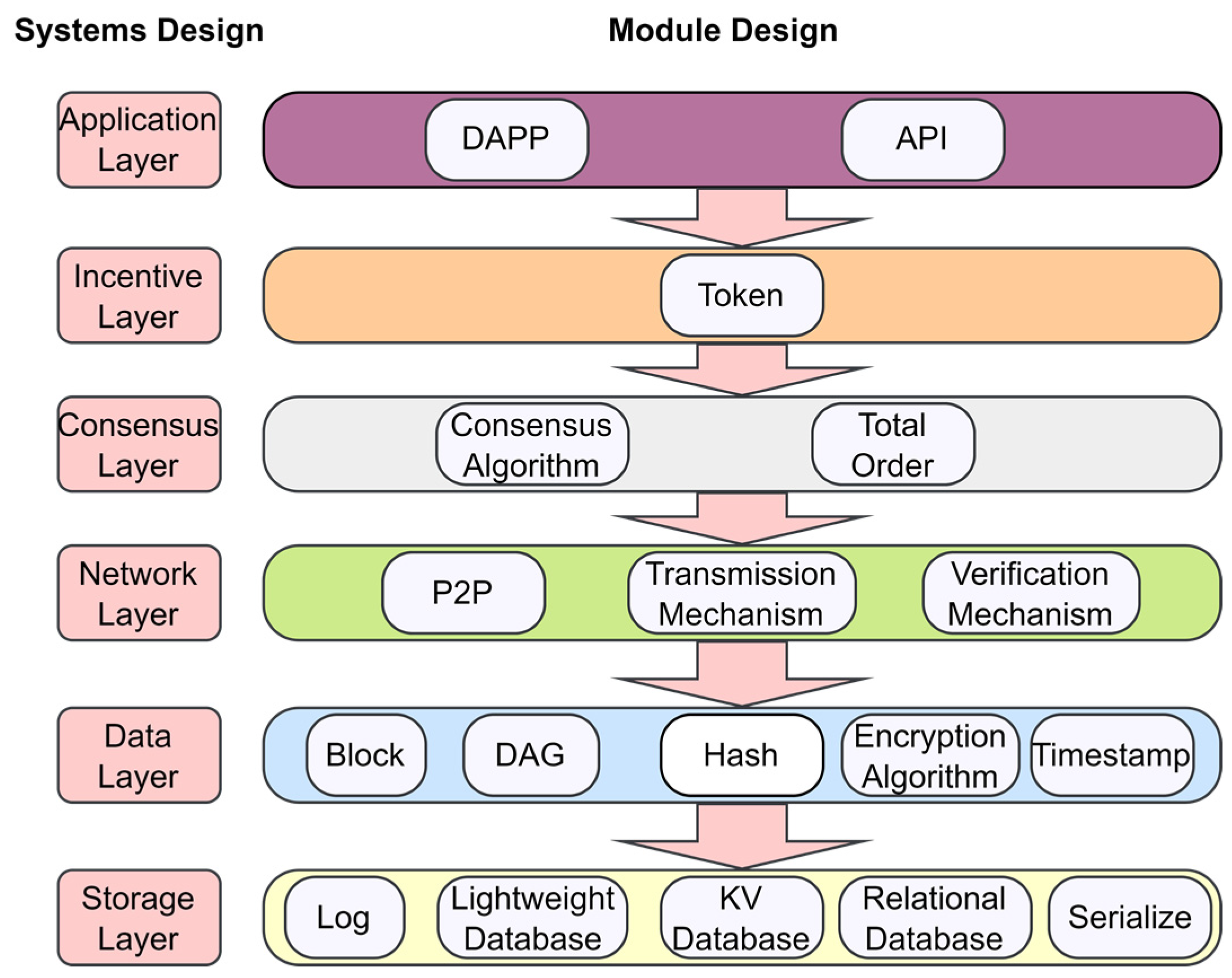
3.1. System Architecture
3.2. System Model
4. Design of Distributed Ledger Based on DAG
4.1. Parallel Chain Based on Self-Referencing
4.2. DAG Blocks Based on Multiple Hash References
4.3. DAG Consensus Algorithm Based on Voting
| Algorithm 1 The DAG consensus algorithm based on voting |
| Begin |
| //Build the block messages to send to the other nodes |
| members, permissions, organizations, nodeCount = Manager.getInfomations() |
| blocks = Server.build(transactions) |
| block = TEE.build(blocks) |
| signature = TEE.sign(block) |
| if block is null |
| throw exception |
| else |
| Node.sendBlockMessage(members, block) |
| //Receive the block messages from the other nodes |
| blockMessage = Net.getBlockMessage () |
| if blockMessage is null |
| throw exception |
| else |
| blockHash,permission,version,selfHash,proofHash,signature = Server.get(blockMessage) |
| check1 = TEE.verfy(signature) |
| check2 = Manager.checkBlockMessage (blockMessage) |
| if check1 is false or check2 is false |
| throw exception |
| else |
| Node.sendVoteMessage(members, true) |
| //Receive the vote messages from the other nodes |
| vote = Net.getVote() |
| Manager.checkVote(vote) |
| if vote is true |
| voteCount = voteCount + 1 |
| if voteCount > nodeCount/2 |
| Node.sendStateMessage(members,true) |
| //Receive the state message from the other nodes |
| stateMessage= Net.getStateMessage() |
| Manager.checkStateMessage (stateMessage) |
| if stateMessage is true |
| stateCount = stateCount + 1 |
| if stateCount > nodeCount/2 |
| localBlock = Node.build(block) |
| //the block in local DAG is built |
| End |
5. Trusted Computing Based on TEE
5.1. Trusted Signature Technology Based on TEE
| Algorithm 2 The algorithm of trusted signature technology based on TEE |
| Begin |
| //Receive a block from the node |
| block.timeStamp = TEE.getTimeStamp() |
| block.selfParentHash = TEE.getSelfParentHash(nodeId) |
| block.proofHash = TEE.getProofHash(blockHash) |
| if timestamp is null or selfParentHash is null or proofHash is null |
| throw exception |
| else |
| TEE.sign(block) |
| return the block back to the node |
| End |
5.2. Trusted Verification Technology Based on TEE
| Algorithm 3 The algorithm of trusted verification technology based on TEE |
| Begin |
| //Receive a block from the other node |
| if blockMessage is null |
| throw exception |
| publicKey, signature = get(blockMessage) |
| if publicKey is null or signature is null |
| throw exception |
| flag = verify(signature) |
| return the flag to the node |
| End |
5.3. Trusted Sorting Technology Based on TEE
| Algorithm 4 The algorithm of trusted sorting technology based on TEE |
| Begin |
| //Get all the identified blocks from DAG |
| block = getEach(blocks) |
| timeStamp, selfParentHash, proofHash, nodeId = get(block) |
| if timeStamp is null or selfParentHash is null or proofHash is null or nodeId is null |
| throw exception |
| else |
| blocks.sort(timeStamp) |
| if block.timeStamp is equal and blockHash is not equal to selfParentHash and blockHash is not equal to proofHash |
| blocks.sort(nodeId) |
| else |
| throw exception |
| End |
6. Experiment and Analysis
6.1. Experimental Environment
6.2. Experiments and Results
6.2.1. Efficiency Testing of Distributed Ledger Databases
6.2.2. Throughput Testing of Distributed Ledger
6.2.3. Throughput Testing of Distributed Ledger
6.3. Comprehensive Evaluation
6.3.1. Scalability
6.3.2. Security
6.3.3. Decentralization
6.3.4. Resource Consumption
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Monrat, A.A.; Schelén, O.; Andersson, K. A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- IoT Roaming Strategies Market Report 2022-27: Statistics, Size, Trends. Available online: https://www.juniperresearch.com/researchstore/operators-providers/iot-roaming-strategies-research-report (accessed on 11 April 2023).
- Mezquita, Y.; Casado, R.; Gonzalez-Briones, A.; Prieto, J.; Corchado, J.M. Blockchain technology in IoT systems: Review of the challenges. Ann. Emerg. Technol. Comput. (AETiC) 2019, 3, 17–24. [Google Scholar] [CrossRef]
- Qifeng, S.; Cheqing, J.; Zhao, Z.; Qian, W.; Zhou, A. Blockchain technology: Architecture and progress. Chin. J. Comput. 2018, 41, 3–22. [Google Scholar]
- Xuan, H.; Yong, Y.; Feiyue, W. Blockchain security issues: Research status and prospect. Acta Autom. Sin. 2019, 45, 206–225. [Google Scholar]
- Wang, Q.; Yu, J.; Chen, S.; Xiang, Y. Sok: Dag-based blockchain systems. ACM Comput. Surv. 2023, 55, 1–38. [Google Scholar] [CrossRef]
- Gao, Z.; Zheng, J.; Tang, S.; Long, Y.; Liu, Z.; Gu, D. State-of-the-art survey of consensus mechanisms on dag-based distributed ledger. J. Softw. 2019, 31, 1124–1142. [Google Scholar]
- Sompolinsky, Y.; Zohar, A. Secure high-rate transaction processing in bitcoin. In Financial Cryptography and Data Security: 19th International Conference, FC 2015, San Juan, Puerto Rico, 26–30 January 2015; Revised Selected Papers 19; Springer: Berlin/Heidelberg, Germany, 2015; pp. 507–527. [Google Scholar]
- Lewenberg, Y.; Sompolinsky, Y.; Zohar, A. Inclusive block chain protocols. In Financial Cryptography and Data Security: 19th International Conference, FC 2015, San Juan, Puerto Rico, 26–30 January 2015; Revised Selected Papers 19; Springer: Berlin/Heidelberg, Germany, 2015; pp. 528–547. [Google Scholar]
- Churyumov, A. Byteball: A Decentralized System for Storage and Transfer of Value. 2016. Available online: https://byteball.org/Byteball.pdf (accessed on 20 May 2023).
- Li, C.; Li, P.; Zhou, D.; Xu, W.; Long, F.; Yao, A. Scaling nakamoto consensus to thousands of transactions per second. arXiv 2018, arXiv:1805.03870. [Google Scholar]
- Couto, A.C. A Blockchain-Based Consensus Algorithm for DAG DLTs. 2020. Available online: https://bibliotecadigital.fgv.br/dspace/handle/10438/30041 (accessed on 20 May 2023).
- Xu, J.; Cheng, Y.; Wang, C.; Jia, X. Occam: A secure and adaptive scaling scheme for permissionless blockchain. In Proceedings of the 2021 IEEE 41st International Conference on Distributed Computing Systems (ICDCS), Washington, DC, USA, 7–10 July 2021; pp. 618–628. [Google Scholar]
- Xiong, T.; Xie, T.; Xie, J.; Luo, X. ORIC: A Self-Adjusting Blockchain Protocol with High Throughput. In Proceedings of the 2021 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), New York, NY, USA, 30 September–3 October 2021; pp. 1422–1434. [Google Scholar]
- Baird, L. The swirlds hashgraph consensus algorithm: Fair, fast, byzantine fault tolerance. Swirlds Tech. Rep. SWIRLDS-TR-2016-01 Tech. Rep. 2016, 34, 9–11. [Google Scholar]
- Chen, T.Y.; Huang, W.N.; Kuo, P.C.; Chung, H.; Chao, T.W. A Highly Scalable, Decentralized DAG-Based Consensus Algorithm. DEXON Foundation, Taiwan. Available online: https://eprint.iacr.org/2018/1112.pdf (accessed on 20 May 2023).
- LeMahieu, C. Nano: A Feeless Distributed Cryptocurrency Network. Nano. 2018. Available online: https://nano.org/en/whitepaper (accessed on 24 March 2018).
- Xiang, F.; Huaimin, W.; Peichang, S.; Xue, O.; Xunhui, Z. Jointgraph: A DAG-based efficient consensus algorithm for consortium blockchains. Softw. Pract. Exp. 2021, 51, 1987–1999. [Google Scholar] [CrossRef]
- Yu, H.; Nikolić, I.; Hou, R.; Saxena, P. OHIE: Blockchain scaling made simple. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 90–105. [Google Scholar]
- Fu, X.; Wang, H.; Shi, P.; Zhang, X. Teegraph: A Blockchain consensus algorithm based on TEE and DAG for data sharing in IoT. J. Syst. Archit. 2022, 122, 102344. [Google Scholar] [CrossRef]
- Keidar, I.; Kokoris-Kogias, E.; Naor, O.; Spiegelman, A. All you need is dag. In Proceedings of the 2021 ACM Symposium on Principles of Distributed Computing, Virtual, 26–30 July 2021; pp. 165–175. [Google Scholar]
- DagCoin: A Cryptocurrency without Blocks|Bitslog. Available online: https://bitslog.com/2015/09/11/dagcoin/ (accessed on 4 March 2023).
- Sompolinsky, Y.; Lewenberg, Y.; Zohar, A. Spectre: A fast and scalable cryptocurrency protocol. Cryptology ePrint Archive 2016. Available online: https://eprint.iacr.org/2016/1159 (accessed on 20 May 2023).
- Popov, S. The tangle. White Pap. 2018, 1, 30. [Google Scholar]
- Bentov, I.; Hubáček, P.; Moran, T.; Nadler, A. Tortoise and hares consensus: The meshcash framework for incentive-compatible, scalable cryptocurrencies. In Cyber Security Cryptography and Machine Learning: 5th International Symposium, CSCML 2021, Be’er Sheva, Israel, 8–9 July 2021; Proceedings 5; Springer International Publishing: Berlin/Heidelberg, Germany, 2021; pp. 114–127. [Google Scholar]
- Rocket, T. Snowflake to Avalanche: A Novel Metastable Consensus Protocol Family for Cryptocurrencies. 2018. Available online: https://www.semanticscholar.org/paper/Snowflake-to-Avalanche-%3A-A-Novel-Metastable-Family/85ec19594046bbcfe12137c7c2e3744677129820 (accessed on 4 December 2018).
- Bu, G.; Gürcan, Ö.; Potop-Butucaru, M. G-IOTA: Fair and confidence aware tangle. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 644–649. [Google Scholar]
- Bu, G.; Hana, W.; Potop-Butucaru, M. Metamorphic iota. arXiv 2019, arXiv:1907.03628. [Google Scholar]
- Sompolinsky, Y.; Zohar, A. Phantom. IACR Cryptology ePrint Archive, Report 2018/104, 2018. Available online: https://eprint.iacr.org/2018/104 (accessed on 20 May 2023).
- Cordova, D.; Laube, A.; Pujolle, G. Blockgraph: A blockchain for mobile ad hoc networks. In Proceedings of the 2020 4th Cyber Security in Networking Conference (CSNet), Lausanne, Switzerland, 21–23 October 2020; pp. 1–8. [Google Scholar]
- Reddy, S.; Sharma, G.V.V. UL-blockDAG: Unsupervised learning based consensus protocol for blockchain. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 8–10 July 2020; pp. 1243–1248. [Google Scholar]
- Cui, L.; Yang, S.; Chen, Z.; Pan, Y.; Xu, M.; Xu, K. An efficient and compacted DAG-based blockchain protocol for industrial Internet of Things. IEEE Trans. Ind. Inform. 2019, 16, 4134–4145. [Google Scholar] [CrossRef]
- Song, A.; Dai, Y.; Ji, R.; Song, Z. Extend PBFT Protocol with L-DAG. In Proceedings of the 2021 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), New York, NY, USA, 30 September–3 October 2021; pp. 963–970. [Google Scholar]
- Pinto, S.; Santos, N. Demystifying arm trustzone: A comprehensive survey. ACM Comput. Surv. (CSUR) 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.H.; Mohaisen, D. Exploring the attack surface of blockchain: A comprehensive survey. IEEE Commun. Surv. Tutor. 2020, 22, 1977–2008. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, N.; Lou, W.; Hou, Y.T. A survey of distributed consensus protocols for blockchain networks. IEEE Commun. Surv. Tutor. 2020, 22, 1432–1465. [Google Scholar] [CrossRef]
- Lind, J.; Eyal, I.; Kelbert, F.; Naor, O.; Pietzuch, P.; Sirer, E.G. Teechain: Scalable blockchain payments using trusted execution environments. arXiv 2017, arXiv:1707.05454. [Google Scholar]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. (CSUR) 2019, 52, 1–34. [Google Scholar] [CrossRef]













| Scheme | Year | Design | Problem |
|---|---|---|---|
| Ghost [8] | 2015 | Main chain | Low scalability, high resource consumption |
| Inclusive [9] | 2015 | Main chain | Low scalability and security |
| DagCoin [22] | 2015 | Natural topology | Low scalability and security |
| Byteball [10] | 2016 | Main chain | Uncertain transaction confirmation |
| Hashgraph [15] | 2016 | Parallel chain | Complex code Not open source |
| Spectre [23] | 2016 | Natural topology | Smart contracts are not supported |
| IOTA [24] | 2016 | Natural topology | Not completely decentralized |
| Meshcash [25] | 2017 | Natural topology | Low security High resource consumption |
| Dexon [16] | 2018 | Parallel chain | Single chain consensus |
| Conflux [11] | 2018 | Main chain | High resource consumption |
| Nano [17] | 2018 | Parallel chain | Insufficient scalability Contract not supported |
| Avalanche [26] | 2018 | Natural topology | High resource consumption Contract not supported |
| Jointgraph [18] | 2019 | Parallel chain | Weak centralization |
| G-IOTA [27] | 2019 | Natural topology | Optimized for IOTA |
| E-IOTA [28] | 2019 | Natural topology | Optimized for IOTA |
| OHIE [19] | 2020 | Parallel chain | High resource consumption for Pow |
| Phantom [29] | 2020 | Natural topology | Based on Spectre |
| Blockgraph [30] | 2020 | Natural topology | System not implemented |
| UL-blockDAG [31] | 2020 | Natural topology | Graph clustering algorithm is slow |
| CoDAG [32] | 2020 | Hierarchical | High resource consumption for Pow |
| DAG DLT [12] | 2021 | Main chain | High resource consumption for Pow |
| Occam [13] | 2021 | Main chain | High resource consumption for Pow |
| ORIC [14] | 2021 | Main chain | High resource consumption for Pow |
| Teegraph [20] | 2021 | Parallel chain | System not implemented |
| DAG-Rider [21] | 2021 | Parallel chain | Long time for consensus |
| L-DAG [33] | 2021 | Hierarchical | Delayed change in layer width |
| Node | Docker Image | Simulate Object |
|---|---|---|
| Peer0.org1.example.com | dag:v1 | Network Node 0 |
| Peer1.org1.example.com | dag:v1 | Network Node 1 |
| Peer2.org1.example.com | dag:v1 | Network Node 2 |
| Peer3.org1.example.com | dag:v1 | Network Node 3 |
| mysql | mysql:8.0.19 | mysql database server |
| dag_manager | manager:v1 | management |
| Name | Related Configurations |
|---|---|
| LAPTOP-48C72J20 | Windows10; CPU i5-9300H; RAM 16.0GB; NVIDIA GeForce GTX 1660 Ti |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, X.; Jiang, C. TEEDAG: A High-Throughput Distributed Ledger Based on TEE and Directed Acyclic Graph. Electronics 2023, 12, 2393. https://doi.org/10.3390/electronics12112393
Lu X, Jiang C. TEEDAG: A High-Throughput Distributed Ledger Based on TEE and Directed Acyclic Graph. Electronics. 2023; 12(11):2393. https://doi.org/10.3390/electronics12112393
Chicago/Turabian StyleLu, Xiaofeng, and Cheng Jiang. 2023. "TEEDAG: A High-Throughput Distributed Ledger Based on TEE and Directed Acyclic Graph" Electronics 12, no. 11: 2393. https://doi.org/10.3390/electronics12112393
APA StyleLu, X., & Jiang, C. (2023). TEEDAG: A High-Throughput Distributed Ledger Based on TEE and Directed Acyclic Graph. Electronics, 12(11), 2393. https://doi.org/10.3390/electronics12112393






