Transfer and CNN-Based De-Authentication (Disassociation) DoS Attack Detection in IoT Wi-Fi Networks
Abstract
:1. Introduction
- We propose an end-to-end IDS solution for de-authentication\disassociation DoS attack detection in IoT Wi-Fi networks.
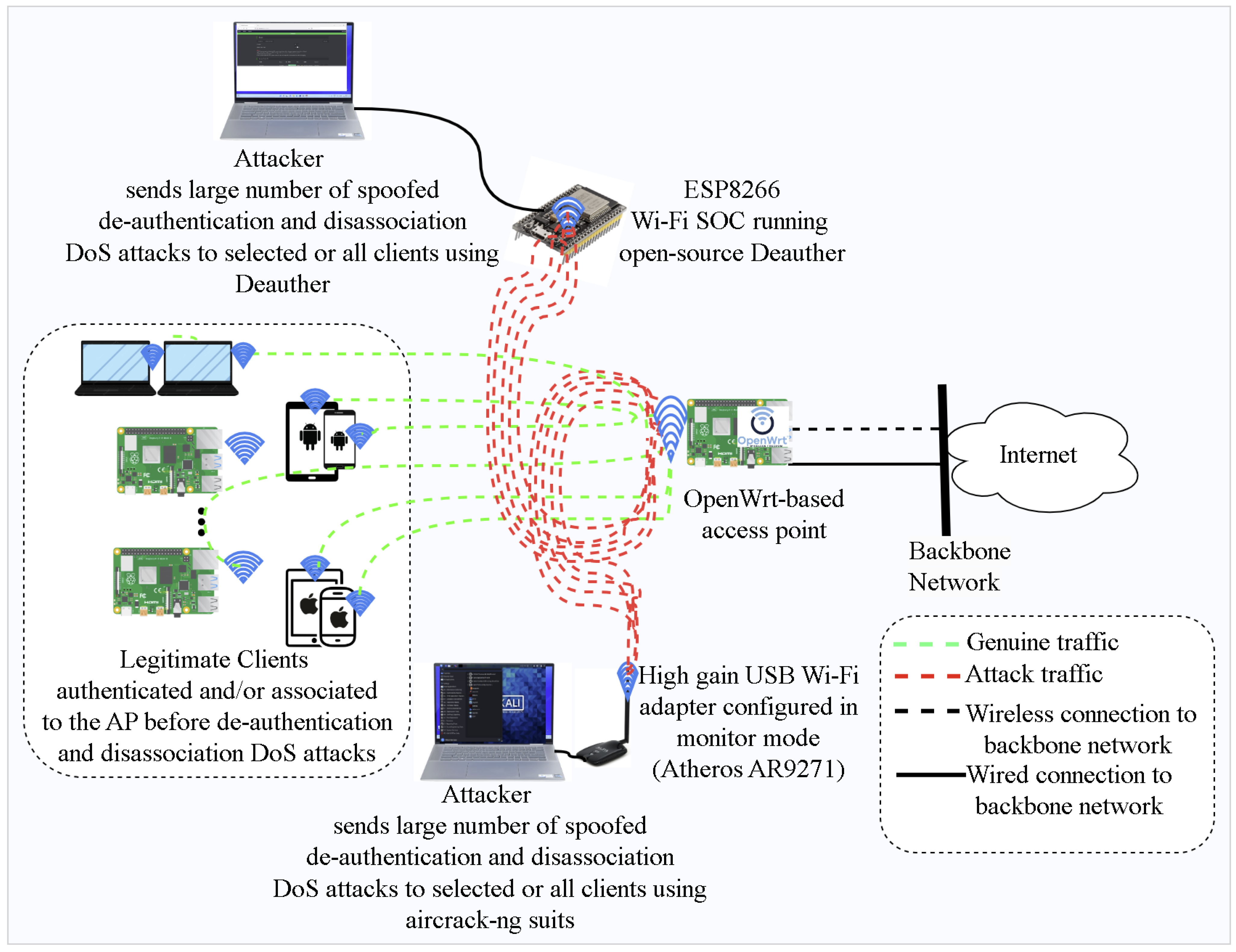
- We design a complete testbed for collecting real-time network traffic and modules for parsing unstructured network traffic, analyzing structured data, and generating datasets for the proposed attack detection solution.
- We propose a novel data pre-processing technique to prepare our Wi-Fi Association_Disassociation dataset to make it suitable for TL- and CNN-based attack detection.
- We evaluate our solution’s performance using different metrics, including confusion matrix, accuracy, precession, recall, F1-score, and ROC/AUC. Then, we compare it with state-of-the-art solutions that involve both TML and DL models. We show that our solution can effectively detect de-authentication/disassociation attacks with high accuracy.
2. Background
2.1. Intrusion Detection System (IDS)
2.2. Machine and Deep Learning for IDS
2.2.1. Convolutional Neural Networks
2.2.2. Transfer Learning
2.3. IoT and the Wi-Fi Protocol
De-Authentication and Disassociation Attacks
2.4. De-Authentication DoS Attack
2.5. Disassociation DoS Attack
2.6. Log Collection and Parsing
2.7. Elastic Stack
3. Related Work
4. Proposed Intrusion Detection Method
4.1. Attack and Normal Traffic Generator Module
4.2. Log Collection, Parsing, Storing, Analysis, and Generating Dataset
| Algorithm 1: Simplified high-level parsing algorithm for association and disassociation network traffic | |
| Input: Raw logs | |
| Output: Structured logs | |
| begin: | |
| 1: input-plugin | |
| 2: | inputType ← stdin |
| 3: | protocol ← TCP/UDP |
| 4: | port ← portNumber |
| 5: end input-plugin | |
| 6: filter | |
| 7: | inputMessage ← incomingRawLogMessage |
| 8: | getMatchingPatterns ← [timestamp, macAddress, host, logMessage] |
| 9: | fieldNames ← [macAddress, timestamp, association, dataType] |
| 10: | if (matching macAddress exists in inputMessage) then |
| 11: | inputMessage ← [macAddress, logmessage] |
| 12: | else if (matching macAddress does not exists in inputMessage) then |
| 13: | inputMessage ← logmessage |
| 14: | else if (logmessage contains associated) then |
| 15: | association ← associated |
| 16: | else(logmessage contains disassociated) |
| 17: | association ← disassociated |
| 18: | end if |
| 19: end filter | |
| 20: output-plugin | |
| 21: | elasticsearch |
| 22: | hosts ← logServerIP |
| 23: | index ← indexName |
| 24: | end elasticsearch |
| 25: | stdout |
| 26: | set output to be displayed in console |
| 27: | end stdout |
| 28: end output-plugin | |
| 29: return structuredLogs | |
| end | |
4.3. Visualization and Dataset Generation Module
4.4. Data Pre-Processing Module
| Algorithm 2: Algorithm for pre-processing part dataset to be suitable for the proposed IDS model | |
| Input: CSV dataset | |
| Output: images | |
| begin: | |
| 1: winSizeInMin ← minutes (10 or 5) | |
| 2: function GETDAY(timestamp) | |
| 3: | split timestamp |
| 4: | return day |
| 5: end function | |
| 6: function ASSOCIATIONTODIGITAL(action) | |
| 7: | if (action==’associated’) then |
| 8: | return 1 |
| 9: | else (logmessage contains disassociated) |
| 10: | return 0 |
| 11: | end if |
| 12: end function | |
| 13: function CHANGETOMINUTES(referenceTime, currentTime) | |
| 14: | timeSince ← currentTime—referenceTime |
| 15: | minutesSince ← × 60 |
| 16: | return minutesSince |
| 17: end function | |
| 18: function PLOTSIGNAL(sigData, height, width, fig, fileName, winSizeInMin) | |
| 19: | set dpi size |
| 20: | sigData ← first index of dataset |
| 21: | if len(sigData == 1) ∨ max(sigData[winSizeInMin]) < winSizeInMin then |
| 22: | repeat first index |
| 23: | sigData ← winSizeInMin |
| 24: | end if |
| 25: | scale sigData |
| 26: | sigData[′winSizeInMin′] ← sigData[′winSizeInMinutes′] × |
| 27: | // Set figure size in inches to fit the image |
| 28: | figSize ← |
| 29: | create a figure to fit between 0(lower limit) and 1(upper limit) |
| 30: | show image per device per day |
| 31: | save the image |
| 32: end function | |
| 33: function EXTRACTIMAGESFROMLOGS(f ilePath, outputImagesDir, outputCSVPath) | |
| 34: | create folders for both attack and normal data |
| 35: | // create a dataframe which holds the final file (cleaned and transformed) |
| 36: | read CSV file from filePath |
| 37: | get all rows consisting of associated and disassociated |
| 38: | get all columns of [association, timestamp, MACAddress, dataType] |
| 39: | make sure timestamp is in datetime format |
| 40: | get day from datetime formatted of timestamp |
| 41: | GETDAY() |
| 42: | // convert association to digital (association –> 1, and disassociation–> 0) |
| 43: | ASSOCIATIONTODIGITAL() |
| 44: | Devices ← unique MAC address of each device |
| 45: | // for each device, each day get the association and dissociation |
| 46: | for each device in devices do |
| 47: | sort data by time |
| 48: | // change time to minutes for each device |
| 49: | for each day in days do |
| 50: | sort data by time |
| 51: | // change time to minutes for each device |
| 52: | save each image with unique file name |
| 53: | for each row of data in length of data per device per day do |
| 54: | change time to minutes for each device |
| 55: | put each value of minutes of each device in winSizeInMinutes column |
| 56: | save this data |
| 57: | // now iterate through data per defined minutes |
| 58: | plot a figure |
| 59: | maxTimeInMinutes ← max value fromwinSizeInMinutes |
| 60: | for currentTime in range(0, maxTimeInMinutes, winSizeInMin) do |
| 61: | check if windowData is between current value in winSizeInMinutes and currentTime |
| 62: | lable the current windowData as attack or normal |
| 63: | save each image with unique file name |
| 64: | end for |
| 65: | end for |
| 66: | end for |
| 67: | end for |
| 68: | save each image with unique file name |
| 69: end function | |
| end | |
4.5. Attack Detection Module
5. Results and Analysis
5.1. Experimental Setup
5.2. Training the Proposed Model
5.3. Hyperparameter Tuning
5.4. Performance Evaluation
5.5. Comparison with State-of-the-Art Models
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- IEEE 802.11-1997; IEEE Standard for Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- IEEE 802.11a-1999; IEEE Standard for Telecommunications and Information Exchange between Systems—LAN/MAN Specific Requirements—Part 11: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications: High Speed Physical Layer in the 5 GHz Band. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11g-2003; IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Further Higher Data Rate Extension in the 2.4 GHz Band. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11n-2009; IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC)and Physical Layer (PHY) Specifications Amendment 5: Enhancements for Higher Throughput. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11ac-2013; IEEE Standard for Information Technology—Telecommunications and Information Exchange between Systems–Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications—Amendment 4: Enhancements for Very High Throughput for Operation in Bands below 6 GHz. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11ai-2016; IEEE Standard for Information Technology—Telecommunications and Information Exchange between Systems—Local and Metropolitan Area Networks—Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 1: Fast Initial Link Setup. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- Gu, J.; Zhao, J.; Li, W. Research on WLAN Security Technology Based on IEEE 802.11. In Proceedings of the 2011 3rd International Conference on Advanced Computer Control, ICACC, Harbin, China, 18–20 January 2011; pp. 234–237. [Google Scholar] [CrossRef]
- Juhász, K.; Póser, V.; Kozlovszky, M.; Bánáti, A. WiFi Vulnerability Caused by SSID Forgery in the IEEE 802.11 Protocol. In Proceedings of the SAMI 2019—IEEE 17th World Symposium on Applied Machine Intelligence and Informatics, Herlany, Slovakia, 24–26 January 2019; pp. 333–338. [Google Scholar] [CrossRef]
- Yao, X.; Farha, F.; Li, R.; Psychoula, I.; Chen, L.; Ning, H. Security and Privacy Issues of Physical Objects in the IoT: Challenges and Opportunities. Digit. Commun. Netw. 2021, 7, 373–384. [Google Scholar] [CrossRef]
- CVE Records for Deatuthentication and Disassociation Attacks. Available online: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=deauthentication+attack (accessed on 28 June 2023).
- A. Reyes, A.; D. Vaca, F.; Castro Aguayo, G.A.; Niyaz, Q.; Devabhaktuni, V. A Machine Learning Based Two-Stage Wi-Fi Network Intrusion Detection System. Electronics 2020, 9, 1689. [Google Scholar] [CrossRef]
- WPA3 Specification. Available online: https://www.wi-fi.org/downloads-public/WPA3%2BSpecification%2Bv3.1.pdf/35332 (accessed on 12 May 2023).
- IEEE Std 802.11ax-2021 (Amendment to IEEE Std 802.11-2020); IEEE Standard for Information Technology–Telecommunications and Information Exchange between Systems Local and Metropolitan Area Networks–Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 1: Enhancements for High-Efficiency WLAN. IEEE: Toulouse, France, 2021; pp. 1–767. [CrossRef]
- Dalal, N.; Akhtar, N.; Gupta, A.; Karamchandani, N.; Kasbekar, G.S.; Parekh, J. A Wireless Intrusion Detection System for 802.11 WPA3 Networks. In Proceedings of the 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 4–8 January 2022; Volume 3. [Google Scholar]
- Baras, K.; Moreira, A. Anomaly Detection in University Campus WiFi Zones. In Proceedings of the 2010 8th IEEE International Conference on Pervasive Computing and Communications Workshops, PERCOM Workshops 2010, Mannheim, Germany, 29 March–2 April 2010; pp. 202–207. [Google Scholar] [CrossRef]
- Simbana, S.; Lopez, G.; Tipantuna, C.; Sanchez, F. Vulnerability Analysis Toolkit for IEEE 802.11 Wireless Networks: A Practical Approach. In Proceedings of the 3rd International Conference on Information Systems and Computer Science, INCISCOS, Quito, Ecuador, 13–15 November 2018; pp. 227–232. [Google Scholar] [CrossRef]
- Seraphim, B.I.; Palit, S.; Srivastava, K.; Poovammal, E. A Survey on Machine Learning Techniques in Network Intrusion Detection System. In Proceedings of the 2018 4th International Conference on Computing Communication and Automation, ICCCA, Greater Noida, India, 14–15 December 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Satam, P.; Hariri, S. WIDS: An Anomaly Based Intrusion Detection System for Wi-Fi (IEEE 802.11) Protocol. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1077–1091. [Google Scholar] [CrossRef]
- Yousefnezhad, N.; Malhi, A.; Främling, K. Security in Product Lifecycle of IoT Devices: A Survey. J. Netw. Comput. Appl. 2020, 171, 102779. [Google Scholar] [CrossRef]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A Survey of Intrusion Detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Danziger, M.; De Lima Neto, F.B. A Hybrid Approach for IEEE 802.11 Intrusion Detection Based on AIS, MAS and Naïve Bayes. In Proceedings of the 2010 10th International Conference on Hybrid Intelligent Systems, Atlanta, GA, USA, 23–25 August 2010; pp. 201–204. [Google Scholar]
- Thing, V.L.L. IEEE 802.11 Network Anomaly Detection and Attack Classification: A Deep Learning Approach. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Riyaz, B.; Ganapathy, S. A Deep Learning Approach for Effective Intrusion Detection in Wireless Networks Using CNN. Soft Comput. 2020, 24, 17265–17278. [Google Scholar] [CrossRef]
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. Security Analysis of Network Anomalies Mitigation Schemes in IoT Networks. IEEE Access 2020, 8, 43355–43374. [Google Scholar] [CrossRef]
- Sharma, N.; Jain, V.; Mishra, A. An Analysis of Convolutional Neural Networks for Image Classification. Procedia Comput. Sci. 2018, 132, 377–384. [Google Scholar] [CrossRef]
- Narayana Rao, K.; Venkata Rao, K.; Pvgd, P.R. A Hybrid Intrusion Detection System Based on Sparse Autoencoder and Deep Neural Network. Comput. Commun. 2021, 180, 77–88. [Google Scholar] [CrossRef]
- Lawrence, S.; Giles, C.L.; Tsoi, A.C.; Back, A.D. Face Recognition: A Convolutional Neural-Network Approach. IEEE Trans. Neural. Netw. 1997, 8, 98–113. [Google Scholar] [CrossRef]
- Zhiqiang, W.; Jun, L. A Review of Object Detection Based on Convolutional Neural Network. In Proceedings of the 2017 36th Chinese Control Conference (CCC), Dalian, China, 26–28 July 2017; pp. 11104–11109. [Google Scholar]
- Chang, Y.; Yan, L.; Fang, H.; Zhong, S.; Liao, W. HSI-DeNet: Hyperspectral Image Restoration via Convolutional Neural Network. IEEE Trans. Geosci. Remote Sens. 2019, 57, 667–682. [Google Scholar] [CrossRef]
- Devlin, J.; Cheng, H.; Fang, H.; Gupta, S.; Deng, L.; He, X.; Zweig, G.; Mitchell, M. Language Models for Image Captioning: The Quirks and What Works 2015. arXiv 2015, arXiv:1505.01809. [Google Scholar]
- Yang, J.; Li, J. Application of Deep Convolution Neural Network. In Proceedings of the 2017 14th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Chengdu, China, 15–17 December 2017; IEEE: Chengdu, China, 2017; pp. 229–232. [Google Scholar]
- Torfi, A.; Iranmanesh, S.M.; Nasrabadi, N.; Dawson, J. 3D Convolutional Neural Networks for Cross Audio-Visual Matching Recognition. IEEE Access 2017, 5, 22081–22091. [Google Scholar] [CrossRef]
- Idrissi, I.; Azizi, M.; Moussaoui, O. Accelerating the Update of a DL-Based IDS for IoT Using Deep Transfer Learning. IJEECS 2021, 23, 1059. [Google Scholar] [CrossRef]
- Pan, S.J.; Yang, Q. A Survey on Transfer Learning. IEEE Trans. Knowl. Data Eng. 2010, 22, 1345–1359. [Google Scholar] [CrossRef]
- Global Economic Value of Wi-Fi_2021-2025—Wi-Fi Alliance. Available online: https://www.wi-fi.org/downloads-public/Global_Economic_Value_of_Wi-Fi_2021-2025_202109.pdf/37347 (accessed on 12 May 2023).
- Waliullah, M.; Moniruzzaman, A.B.M.; Rahman, M.S. An Experimental Study Analysis of Security Attacks at IEEE 802.11 Wireless Local Area Network. Int. J. Future Gener. Commun. Netw. 2015, 8, 9–18. [Google Scholar] [CrossRef]
- Mahini, H.; Mousavirad, S.M. WiFi Intrusion Detection and Prevention Systems Analyzing: A Game Theoretical Perspective. Int. J. Wirel. Inf. Netw. 2020, 27, 77–88. [Google Scholar] [CrossRef]
- Milliken, J.; Selis, V.; Yap, K.M.; Marshall, A. Impact of Metric Selection on Wireless Deauthentication Dos Attack Performance. IEEE Wirel. Commun. Lett. 2013, 2, 571–574. [Google Scholar] [CrossRef]
- Tyagi, M.; Narvare, S.; Agrawal, C. A Survey of Different Dos Attacks on Wireless Network. Comput. Eng. Intell. Syst. 2018, 9, 23–32. [Google Scholar]
- Agrawal, A.; Dixit, A.; Shettar, N.; Kapadia, D.; Karlupia, R.; Agrawal, V.; Gupta, R. Delog: A Privacy Preserving Log Filtering Framework for Online Compute Platforms. arXiv 2019, arXiv:1902.04843v3. [Google Scholar]
- Tsung, C.K.; Yang, C.T.; Yang, S.W. Visualizing Potential Transportation Demand from ETC Log Analysis Using ELK Stack. IEEE Internet Things J. 2020, 7, 6623–6633. [Google Scholar] [CrossRef]
- Shi, L.; Wu, L.; Guan, Z. Three-Layer Hybrid Intrusion Detection Model for Smart Home Malicious Attacks. Comput. Electr. Eng. 2021, 96, 107536. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J. An Intrusion Detection System Against DDoS Attacks in IoT Networks. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 562–567. [Google Scholar]
- Mehedi, S.T.; Anwar, A.; Rahman, Z.; Ahmed, K.; Islam, R. Dependable Intrusion Detection System for IoT: A Deep Transfer Learning Based Approach. IEEE Trans. Ind. Inf. 2023, 19, 1006–1017. [Google Scholar] [CrossRef]
- Masum, M.; Shahriar, H. TL-NID: Deep Neural Network with Transfer Learning for Network Intrusion Detection. In Proceedings of the 2020 15th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 8–10 December 2020; pp. 1–7. [Google Scholar]
- Fan, Y.; Li, Y.; Zhan, M.; Cui, H.; Zhang, Y. IoTDefender: A Federated Transfer Learning Intrusion Detection Framework for 5G IoT. In Proceedings of the 2020 IEEE 14th International Conference on Big Data Science and Engineering (BigDataSE), Guangzhou, China, 31 December 2020—1 January 2021; pp. 88–95. [Google Scholar]
- Elsayed, N.; Zaghloul, Z.S.; Azumah, S.W.; Li, C. Intrusion Detection System in Smart Home Network Using Bidirectional LSTM and Convolutional Neural Networks Hybrid Model. In Proceedings of the 2021 IEEE International Midwest Symposium on Circuits and Systems (MWSCAS), Lansing, MI, USA, 9–11 August 2021. [Google Scholar]
- Huong, P.V.; Thuan, L.D.; Hong Van, L.T.; Hung, D.V. Intrusion Detection in IoT Systems Based on Deep Learning Using Convolutional Neural Network. In Proceedings of the 2019 6th NAFOSTED Conference on Information and Computer Science (NICS), Hanoi, Vietnam, 12–13 December 2019; pp. 448–453. [Google Scholar]
- Xu, Y.; Liu, Z.; Li, Y.; Zheng, Y.; Hou, H.; Gao, M.; Song, Y.; Xin, Y. Intrusion Detection Based on Fusing Deep Neural Networks and Transfer Learning. In Digital TV and Wireless Multimedia Communication; Zhai, G., Zhou, J., Yang, H., An, P., Yang, X., Eds.; Communications in Computer and Information Science; Springer: Singapore, 2020; Volume 1181, pp. 212–223. ISBN 9789811533402. [Google Scholar]
- Hsu, C.-M.; Hsieh, H.-Y.; Prakosa, S.W.; Azhari, M.Z.; Leu, J.-S. Using Long-Short-Term Memory Based Convolutional Neural Networks for Network Intrusion Detection. In Wireless Internet; Chen, J.-L., Pang, A.-C., Deng, D.-J., Lin, C.-C., Eds.; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer International Publishing: Cham, Switzerland, 2019; Volume 264, pp. 86–94. ISBN 978-3-030-06157-9. [Google Scholar]
- Wi-Fi-Association_Disassociation-Dataset. Available online: https://github.com/samsonkg/Wi-Fi-Association_Disassociation-Dataset (accessed on 26 August 2023).
- ESP8266 Deauther 2021. Available online: https://github.com/SpacehuhnTech/esp8266_deauther (accessed on 5 May 2023).
- Brandao, A.; Georgieva, P. Log Files Analysis for Network Intrusion Detection. In Proceedings of the 2020 IEEE 10th International Conference on Intelligent Systems, IS, Varna, Bulgaria, 28–30 August 2020; pp. 328–333. [Google Scholar] [CrossRef]
- Brown, R. OpenWrt Project. Available online: https://openwrt.org/start (accessed on 22 February 2023).























| Ref. | ML/DL Algorithm | Preprocessing/Feature Selection Algorithm | Dataset | Accuracy | Detected Attacks |
|---|---|---|---|---|---|
| [18] | Isolation Forest, C4.5, Random Forest, Adaboost, Decision Tree | n-grams + Bayes Theorem | Generated from local setup (2016, 2017, 2018) | 99% | Attacks on availability and encryptions |
| [22] | SAE | NA | AWID-CLS-R | 98.67% | Injection, flooding, impersonation |
| [23] | CNN | CRFLCFS | KDD 99 Cup | 98.88% | DoS, U2R, R2L, Probe |
| [41] | DT, NB, SVM, KNN | Random Forest and PCA | Generated from local real-time setup (2020) | 95.90% | DoS/DDoS, probing/theft |
| [42] | CNN, LSTM | NSGA-II | CISIDS2017 | 99.03% | DDoS |
| [43] | DTL | Numconv, correlation, min–max | Generated from local real-time setup | 87% | DoS, DDoS, data injection, MITM, backdoor, PCA, scanning, XSS, ransomware |
| [33] | CNN, TL | Argus tool | Bot-IoT | NA | Reconnaissance, DDoS, DoS, theft |
| [44] | DNN, VGG-16 | One-hot encoding, min–max | NSL-KDD | 70.97% | DoS, Probe, U2R, R2L |
| [45] | AB, RF, CNN, KNN | NA | CICIDS2017, NSL-KDD, 3 other IoT private datasets | 91.93% | DoS, Probe, U2R, R2L, Mirai, MitM, Bot, etc. |
| [46] | BiLSTM, CNN | NA | NSL-KDD | 98.93% | DoS, Probe, U2R, R2L |
| [47] | CNN | NA | IoT intrusion | 98.9% | DoS, scan, MaliciousControl, MaliciousOperation, spying, prob |
| [48] | CNN, TL | One-hot encoding, min–max | KDD Cup 99 | 97.9% | DoS, U2R, R2L, Probe |
| [49] | LSTM, CNN | One-hot encoding | NSL-KDD | 94.12% | DoS, Probe, U2R, R2L |
| THIS WORK | CNN, TL | Novel (developed) | Generated from local real-time setup (2022) | 99.36% | De-authentication and disassociation DoS |
| Data Type | Number of Samples | Description |
|---|---|---|
| Attack | 376,430 |
|
| Normal | 233,130 |
|
| Total Samples | 609,560 |
| SN. | Features | Description |
|---|---|---|
| 1 | MAC address | MAC address of the targeted client |
| 2 | Timestamp | The date and time at which the traffic data is logged by the AP |
| 3 | Association | “Associated” when the client device is associated |
| “disassociated” when the client device is disassociated | ||
| 4 | datatype | “normal” when network traffic flow is benign/legitimate |
| “attack” when network traffic flow is illegitimate/malicious |
| SN. | Features | Description |
|---|---|---|
| 1 | MAC address | MAC address of the targeted client |
| 2 | Timestamp | The date and time at which the traffic data is logged by the AP |
| 3 | Association | “Associated” when the client device is associated |
| “disassociated” when the client device is disassociated | ||
| 4 | dateTime | Obtained from timestamp for the purpose of extracting day |
| 5 | Day | Extracted from dateTime to calculate client de vice association disassociation time duration per day |
| 6 | Signal | Is 1 when the client device is associated and 0 when disassociated |
| 7 | PerDevicePerDayTimeMinutes | Time duration in minutes for each device per day during association and disassociation |
| 8 | datatype | “normal” when network traffic flow is benign/legitimate |
| “attack” when network traffic flow is illegitimate/malicious |
| Data Type | No. Images/Window Size | Description | |
|---|---|---|---|
| 5 min | 10 min | ||
| Attack | 1112 | 615 | As the number of attack sample data is very large compared to normal samples in a given window, it becomes very small after they are transformed |
| Normal | 46,644 | 23,296 | |
| Total Samples | 47,756 | 23,911 | |
| Hardware | CPU | Intel Core i7 2.30 GHz processor |
| RAM | 32 GB | |
| HDD | 1TB | |
| Software | Operating system | Windows 11 |
| Anaconda | 3 | |
| Python | 3.9 |
| Window Size | Data Type | Dataset Partitioning | ||
|---|---|---|---|---|
| Training | Validation Set | Test Set | ||
| 5 min | Attack | 772 | 180 | 160 |
| Normal | 32,789 | 6892 | 6963 | |
| 10 min | Attack | 455 | 79 | 81 |
| Normal | 16,340 | 3447 | 3509 | |
| Hyperparameter | Value/Function |
|---|---|
| Batch size | 32 |
| Number of epochs | 150 |
| Hidden layer activation function | ReLu |
| Output layer activation function | Softmax |
| Dropout rate | 0.5 |
| Learning rate | 0.0001 |
| Optimizer | Adam |
| Loss function | Categorical Cross-entropy |
| Model | Batch Size | Overall Accuracy for 5 min Windows Size | Overall Accuracy for 10 min Windows Size |
|---|---|---|---|
| Inception | 16 | 98.217 | 99.3036 |
| 32 | 98.217 | 99.275 | |
| 48 | 98.217 | 99.220 | |
| Resnet | 16 | 98.315 | 99.275 |
| 32 | 98.371 | 99.275 | |
| 48 | 98.399 | 99.275 | |
| Vgg | 16 | 98.273 | 99.331 |
| 32 | 98.343 | 99.220 | |
| 48 | 98.371 | 99.331 | |
| Xception | 16 | 98.371 | 99.275 |
| 32 | 98.385 | 99.360 | |
| 48 | 98.378 | 99.303 |
| Model | Precision | Recall | F-1 score | ROC Area |
|---|---|---|---|---|
| Inception | 0.89 | 0.78 | 0.83 | 0.93 |
| Resnet | 0.87 | 0.80 | 0.83 | 0.94 |
| Vgg | 0.85 | 0.79 | 0.82 | 0.935 |
| Xception | 0.88 | 0.83 | 0.85 | 0.944 |
| Model | Accuracy (%) | Precision (%) | Recall (%) | F-Measure (%) |
|---|---|---|---|---|
| We citeDT | 97.82 | 97.80 | 97.82 | 97.78 |
| RF | 98.64 | 98.50 | 98.64 | 98.49 |
| XGBoost | 98.64 | 98.50 | 98.64 | 98.49 |
| SVM | 99.13 | 98.19 | 98.36 | 98.03 |
| THIS WORK | 99.36 | 98.38 | 98.74 | 98.59 |
| Model | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| LSTM | 99.21 | 98.79 | 98.96 | 98.72 |
| RNN | 99.16 | 98.63 | 98.95 | 98.85 |
| THIS WORK | 99.36 | 98.38 | 98.74 | 98.59 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gebresilassie, S.K.; Rafferty, J.; Chen, L.; Cui, Z.; Abu-Tair, M. Transfer and CNN-Based De-Authentication (Disassociation) DoS Attack Detection in IoT Wi-Fi Networks. Electronics 2023, 12, 3731. https://doi.org/10.3390/electronics12173731
Gebresilassie SK, Rafferty J, Chen L, Cui Z, Abu-Tair M. Transfer and CNN-Based De-Authentication (Disassociation) DoS Attack Detection in IoT Wi-Fi Networks. Electronics. 2023; 12(17):3731. https://doi.org/10.3390/electronics12173731
Chicago/Turabian StyleGebresilassie, Samson Kahsay, Joseph Rafferty, Liming Chen, Zhan Cui, and Mamun Abu-Tair. 2023. "Transfer and CNN-Based De-Authentication (Disassociation) DoS Attack Detection in IoT Wi-Fi Networks" Electronics 12, no. 17: 3731. https://doi.org/10.3390/electronics12173731
APA StyleGebresilassie, S. K., Rafferty, J., Chen, L., Cui, Z., & Abu-Tair, M. (2023). Transfer and CNN-Based De-Authentication (Disassociation) DoS Attack Detection in IoT Wi-Fi Networks. Electronics, 12(17), 3731. https://doi.org/10.3390/electronics12173731








