An Interference-Aware Resource-Allocation Scheme for Non-Cooperative Multi-Cell Environment
Abstract
:1. Introduction
- Historical information utilization. Different from the conventional interference cancellation-based schemes [7], we propose to collect and store the historical noisy channel states and the acknowledgment/negative acknowledgment (ACK/NACK) feedback from UEs. With this historical information, we can predict the upcoming channel condition and determine the efficient resource allocation strategy accordingly.
- Interference pattern prediction. In addition, we also propose to predict the upcoming interference patterns based on the UEs feedback, where the historical threshold-based interference condition has been utilized. Based on the predicted interference patterns for different UEs, we are able to select the preferred UE-subchannel pairs with less interfering probability.
- Joint sub-channel allocation and rate selection. By utilizing the historical information and the predicted interference patterns, we provide a joint sub-channel allocation and transmission rate selection strategy based on a reinforcement learning framework with deep Q-network (DQN).
- Prototype verification. In the meantime, we implement a prototyping system and sample the interference environment with multiple BSs. By collecting the practical measured channel variations of the entire network, we verify our proposed joint sub-channel allocation and transmission rate selection strategy accordingly. Through both numerical and prototyping examples, we show that it achieves more than 9.7% and 8% average throughput gain for different interference environments, if compared with conventional schemes [14,15,16,17].
2. System Models
2.1. Network Configuration and Transmission Models
2.2. Channel and Interference Models
3. Protocol and Problem Formulation
3.1. Transmission Protocol
- User Information Collection. During the time slot t, the cell edge UE reports the measured channel condition of different sub-channels, , the interference condition from all the neighboring BSs, i.e., , and to the target BS via uplink channels. (In the practical implementation, can be obtained by comparing the measured RSRP from the b-th neighbouring BS with a pre-defined threshold, and can be inferred from the conventional ACK/NACK information as defined in [20]. In addition, we model here to incorporate the potential noises generated from local channel estimation or imperfect feedback transmission.) Here, we assume that the base station can receive the uplink information completely, that is, interference is not considered in the information feedback.
- Channel condition and interference prediction. Once the UE feedback is received, the target BS combines the current and historical feedback reports to predict the upcoming channel fading environment and the interference condition . The corresponding mathematical expressions are thus given bywhere and denote the prediction functions for the channel fading and interference condition, respectively.
- Rate identification and transmission. Based on the predicted results, the target BS performs sub-channel and rate allocation to maximize the achievable average throughput . Denote to be the allocation policy, and the mathematical relation is given asWith the determined sub-channel and rate allocation, the target BS starts the downlink transmission for the t-th time slot, and the above procedures continue to operate until the entire transmission duration ends.
3.2. Problem Formulation
4. Problem Transformation and DQN-Based Solution
4.1. Problem Transformation
4.2. DQN-Based Solution
- (1)
- State: In each time slot t, the target base station makes a decision step according to the channel condition. In order to facilitate the simulation, we calculate the capacity of the channel with the predicted channel and interference condition. Because there is an upper limit on resource allocation for the user, the resource which has been allocated to the user needs to be taken into account. So the prediction capacity and the prior transmission rate are denoted as the state of DQN:
- (2)
- Acton: In each time slot t, the action space is the selected number of the sub-channels and the transmission rate on each sub-channel, which is the same as in Problem 2. It is denoted as
- (3)
- Reward function: In view of the long-term average limitation on the number of sub-channels in Equation (10), we add a penalty item in the reward function to achieve it. Because we want to obtain the maximum throughput, the average number of allocated sub-channels should be as close to as possible. The reward is denoted as
| Algorithm 1 DQN-based joint sub-channel allocation and transmission rate selection |
Data/Model Preparation
DQN policy Training
|
5. Experimental Results
- Baseline 1: Measured channel condition only [14], which utilizes the current measured channel condition from UEs, i.e., .
- Baseline 2: Measured channel and interference condition only [15], which utilizes the current measured channel and interference condition from UEs, i.e., and .
- Baseline 3: Predicted channel and interference condition [16], which utilizes the predicted and to maximize the instantaneous throughput.
- Baseline 4: Measured channel and interference condition with DQN [15], which utilizes the current measured channel and interference condition and the DQN-based reinforcement learning framework.
- Baseline 5: Genie-aided, which utilizes the perfect and and the DQN-based reinforcement learning framework.
5.1. Numerical Results
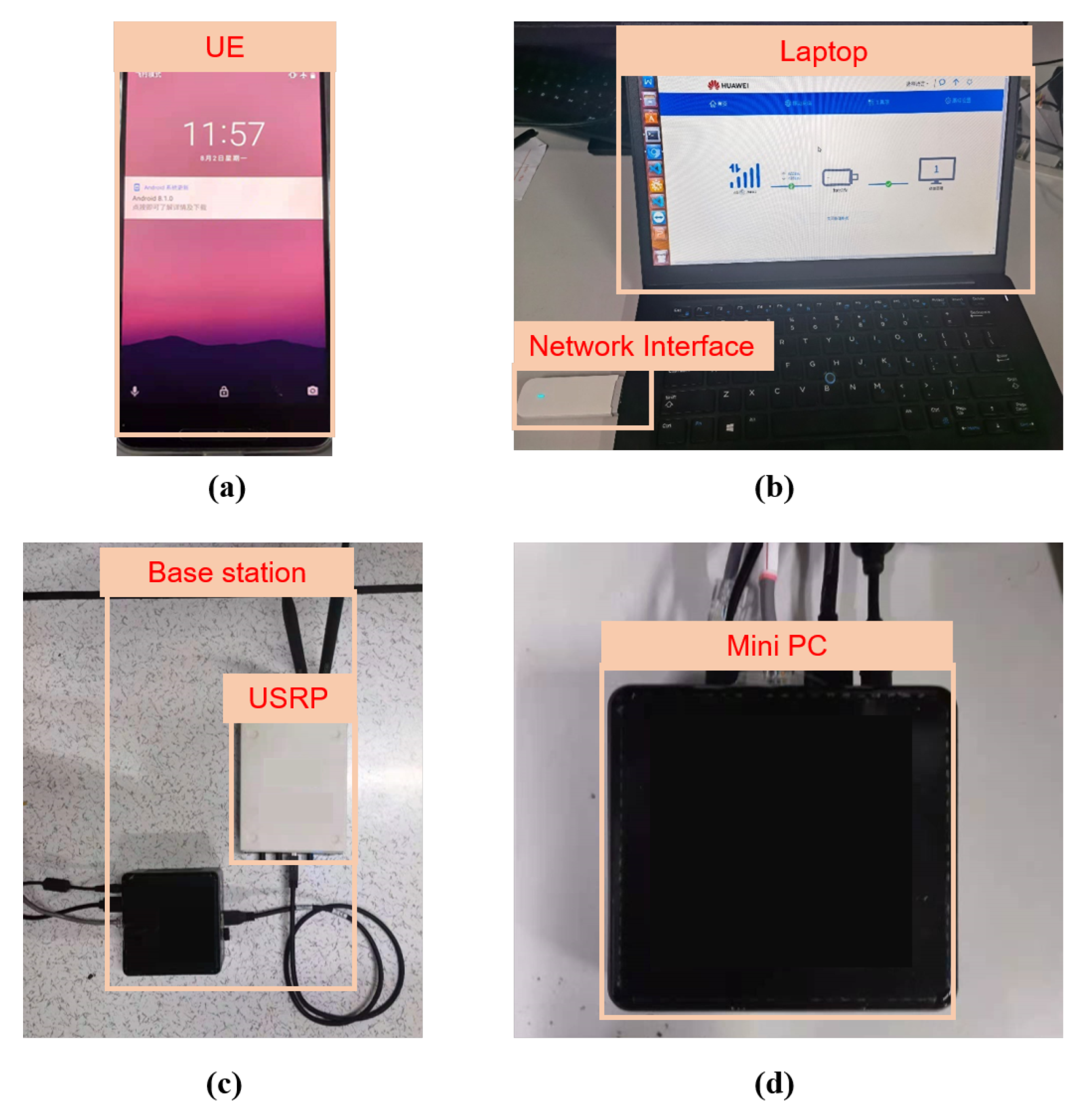
5.2. Prototyping Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Hamza, A.S.; Khalifa, S.S.; Hamza, H.S.; Elsayed, K. A Survey on Inter-Cell Interference Coordination Techniques in OFDMA-Based Cellular Networks. IEEE Commun. Surv. Tutor. 2013, 15, 1642–1670. [Google Scholar] [CrossRef]
- Suo, L.; Li, H.; Zhang, S.; Li, J. Successive Interference Cancellation and Alignment in K-user MIMO Interference Channels with Partial Unidirectional Strong Interference. China Commun. 2022, 19, 118–130. [Google Scholar] [CrossRef]
- Kim, H.; Kim, J.; Hong, D. Dynamic TDD Systems for 5G and Beyond: A Survey of Cross-Link Interference Mitigation. IEEE Commun. Surv. Tutor. 2020, 22, 2315–2348. [Google Scholar] [CrossRef]
- Elhattab, M.; Arfaoui, M.A.; Assi, C. A Joint CoMP C-NOMA for Enhanced Cellular System Performance. IEEE Commun. Lett. 2020, 24, 1919–1923. [Google Scholar] [CrossRef]
- Seifi, N.; Zhang, J.; Heath, R.W.; Svensson, T.; Coldrey, M. Coordinated 3D Beamforming for Interference Management in Cellular Networks. IEEE Trans. Wirel. Commun. 2014, 13, 5396–5410. [Google Scholar] [CrossRef]
- Qamar, F.; Hindia, M.H.D.N.; Dimyati, K.; Noordin, K.A.; Amiri, I.S. Interference Management Issues for the Future 5G Network: A Review. Telecommun. Syst. 2019, 71, 627–643. [Google Scholar] [CrossRef]
- Han, S.; Yang, C.; Chen, P. Full Duplex-Assisted Intercell Interference Cancellation in Heterogeneous Networks. IEEE Trans. Commun. 2015, 63, 5218–5234. [Google Scholar] [CrossRef]
- Yu, Z.; Hou, J. Research on Interference Coordination Optimization Strategy for User Fairness in NOMA Heterogeneous Networks. Electronics 2022, 11, 1700. [Google Scholar] [CrossRef]
- Evolved Universal Terrestrial Radio Access (E-UTRA) and Evolved Universal Terrestrial Radio Access Network (E-UTRAN); Overall description; Stage 2. TS 36.300, 3GPP. R17. 2022. Available online: https://www.etsi.org/deliver/etsi_ts/136300_136399/136300/17.01.00_60/ts_136300v170100p.pdf (accessed on 12 December 2022).
- Chan, C.Y.; Chang, G.Y. A Beam-Based eICIC Algorithm. In Proceedings of the 2020 21st Asia-Pacific Network Operations and Management Symposium (APNOMS), Daegu, Republic of Korea, 22–25 September 2020; pp. 421–427. [Google Scholar] [CrossRef]
- Maruta, K. Imperfect CSI Muting With Time-Domain Thresholding for Cooperative Intercell Interference Cancellation. IEEE Syst. J. 2022, 16, 1147–1157. [Google Scholar] [CrossRef]
- Jiang, S.; Chang, Y.; Fukawa, K. Distributed Inter-cell Interference Coordination for Small Cell Wireless Communications: A Multi-Agent Deep Q-Learning Approach. In Proceedings of the 2020 International Conference on Computer, Information and Telecommunication Systems (CITS), Hangzhou, China, 5–7 October 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Zheng, J.; Gao, L.; Zhang, H.; Niyato, D.; Ren, J.; Wang, H.; Guo, H.; Wang, Z. eICIC Configuration of Downlink and Uplink Decoupling With SWIPT in 5G Dense IoT HetNets. IEEE Trans. Wirel. Commun. 2021, 20, 8274–8287. [Google Scholar] [CrossRef]
- Ye, Y.; Shi, L.; Chu, X.; Hu, R.Q.; Lu, G. Resource Allocation in Backscatter-Assisted Wireless Powered MEC Networks with Limited MEC Computation Capacity. IEEE Trans. Wirel. Commun. 2022, 21, 10678–10694. [Google Scholar] [CrossRef]
- Moosavi, N.; Sinaie, M.; Azmi, P.; Lin, P.H.; Jorswieck, E. Cross Layer Resource Allocation in H-CRAN with Spectrum and Energy Cooperation. IEEE Trans. Mob. Comput. 2021, 22, 145–158. [Google Scholar] [CrossRef]
- Jarinová, D. Fading Channel Prediction by Higher-Order Markov Model. In Proceedings of the 2020 New Trends in Signal Processing (NTSP), Demanovska Dolina, Slovakia, 14–16 October 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Zhao, G.; Li, Y.; Xu, C.; Han, Z.; Xing, Y.; Yu, S. Joint Power Control and Channel Allocation for Interference Mitigation Based on Reinforcement Learning. IEEE Access 2019, 7, 177254–177265. [Google Scholar] [CrossRef]
- Sheng, M.; Wen, J.; Li, J.; Liang, B.; Wang, X. Performance Analysis of Heterogeneous Cellular Networks With HARQ Under Correlated Interference. IEEE Trans. Wirel. Commun. 2017, 16, 8377–8389. [Google Scholar] [CrossRef]
- He, Y.; Zhang, Z.; Yu, F.R.; Zhao, N.; Yin, H.; Leung, V.C.M.; Zhang, Y. Deep-Reinforcement-Learning-Based Optimization for Cache-Enabled Opportunistic Interference Alignment Wireless Networks. IEEE Trans. Veh. Technol. 2017, 66, 10433–10445. [Google Scholar] [CrossRef]
- Evolved Universal Terrestrial Radio Access (E-UTRA); Physical Layer Procedures. TS 36.213, 3GPP. R17. 2022. Available online: https://www.etsi.org/deliver/etsi_ts/136200_136299/136213/17.01.00_60/ts_136213v170100p.pdf (accessed on 12 December 2022).
- Kim, H.; Kim, S.; Lee, H.; Jang, C.; Choi, Y.; Choi, J. Massive MIMO Channel Prediction: Kalman Filtering vs. Machine Learning. IEEE Trans. Commun. 2021, 69, 518–528. [Google Scholar] [CrossRef]
- Li, Q.; Li, R.; Ji, K.; Dai, W. Kalman Filter and Its Application. In Proceedings of the 2015 8th International Conference on Intelligent Networks and Intelligent Systems (ICINIS), Tianjin, China, 1–3 November 2015; pp. 74–77. [Google Scholar] [CrossRef]
- Liu, L.; Cai, L.; Ma, L.; Qiao, G. Channel State Information Prediction for Adaptive Underwater Acoustic Downlink OFDMA System: Deep Neural Networks Based Approach. IEEE Trans. Veh. Technol. 2021, 70, 9063–9076. [Google Scholar] [CrossRef]
- Yu, Y.; Liew, S.C.; Wang, T. Non-Uniform Time-Step Deep Q-Network for Carrier-Sense Multiple Access in Heterogeneous Wireless Networks. IEEE Trans. Mob. Comput. 2021, 20, 2848–2861. [Google Scholar] [CrossRef]
- Oai /openairinterface5G · GitLab. Available online: https://gitlab.eurecom.fr/oai/openairinterface5g (accessed on 12 December 2022).
- Foukas, X.; Nikaein, N.; Kassem, M.M.; Marina, M.K.; Kontovasilis, K. FlexRAN: A Flexible and Programmable Platform for Software-Defined Radio Access Networks. In Proceedings of the 12th International on Conference on Emerging Networking EXperiments and Technologies, Irvine, CA, USA, 12–15 December 2016; ACM: New York, NY, USA, 2016; pp. 427–441. [Google Scholar] [CrossRef]
- Brand, a National Instruments, E.R. USRP B210 USB Software Defined Radio (SDR). Available online: https://www.ettus.com/all-products/ub210-kit/ (accessed on 12 December 2022).









| Parameters | Value | Parameters | Value |
|---|---|---|---|
| Number of base staions | TX antennas Num | 1 | |
| Distance of base stations | 500 m | RX antennas Num | 1 |
| UE relative distance | 150–250 m | TX power | 1W |
| Number of subcarriers | Fading environment | Rayleigh | |
| Number of channel states | Slot per episode | 100 | |
| Interference normalization coefficients | , | Total training episode | |
| Slide window | Learning rate | 0.01 |
| Single Interference Source | Double Interference Source | |||
|---|---|---|---|---|
| Throughput | Performance Loss | Throughput | Performance Loss | |
| Baseline 1 | 59.5 | 0.691 | 19.6 | 0.891 |
| Baseline 2 | 40.0 | 0.792 | 9.96 | 0.944 |
| Baseline 3 | 129.7 | 0.327 | 62.8 | 0.52 |
| Baseline 4 | 57.0 | 0.704 | 48.7 | 0.730 |
| Ours | 142.3 | 0.262 | 100.3 | 0.444 |
| Genie-aided | 192.7 | 0 | 180.5 | 0 |
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| Frame Type | FDD | TX Antennas Num | 1 |
| Downlink Frequency | 26.75 MHz | RX Antennas Num | 1 |
| Bandwidth | 10 MHz | TX Gain | −90 dB |
| Prefix Type | Normal | RX Gain | 125 dB |
| Single Interference Source | Double Interference Source | |||
|---|---|---|---|---|
| Throughput | Performance Loss | Throughput | Performance Loss | |
| Baseline 1 | 61.1 | 0.668 | 29.9 | 0.808 |
| Baseline 2 | 41.1 | 0.777 | 19.6 | 0.874 |
| Baseline 3 | 133.7 | 0.273 | 63.7 | 0.592 |
| Baseline 4 | 149.6 | 0.188 | 133.5 | 0.273 |
| Ours | 161.6 | 0.123 | 135.8 | 0.130 |
| Genie-aided | 184.1 | 0 | 156.0 | 0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Z.; Pan, G.; Sun, Y.; Zhang, S. An Interference-Aware Resource-Allocation Scheme for Non-Cooperative Multi-Cell Environment. Electronics 2023, 12, 868. https://doi.org/10.3390/electronics12040868
Wang Z, Pan G, Sun Y, Zhang S. An Interference-Aware Resource-Allocation Scheme for Non-Cooperative Multi-Cell Environment. Electronics. 2023; 12(4):868. https://doi.org/10.3390/electronics12040868
Chicago/Turabian StyleWang, Zhe, Guangjin Pan, Yanzan Sun, and Shunqing Zhang. 2023. "An Interference-Aware Resource-Allocation Scheme for Non-Cooperative Multi-Cell Environment" Electronics 12, no. 4: 868. https://doi.org/10.3390/electronics12040868





