A Privacy-Preserving Ride Matching Scheme for Ride Sharing Services in a Hot Spot Area
Abstract
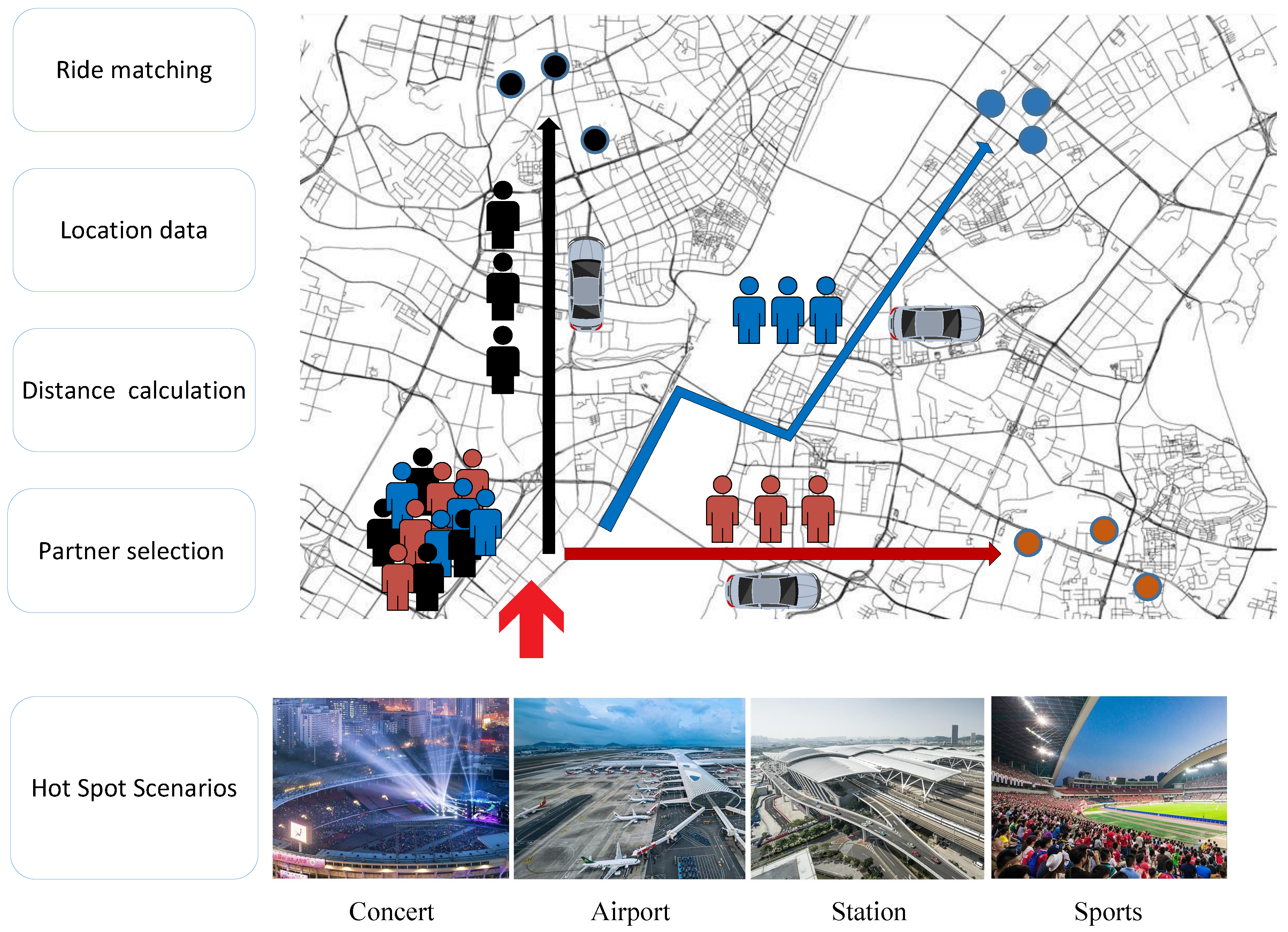
:1. Introduction
- We formulate the problem to maximize the vehicle’s carrying capacity and propose a privacy-preserving ride matching scheme. Our scheme can calculate the road network distance between users to provide ride matching services without knowing the users’ location.
- We propose an efficient scheme that can quickly provide ride matching results to deal with a large number of ride sharing services in hot spot area. The users are pre-selected according to their trip and schedules before matching. We use ciphertexts packing to reduce communication overhead.
- We evaluate the scheme and the experimental results demonstrate that our scheme provides accurate matching service within acceptable time. Our scheme can provide travel time saving and reduce the overall energy consumption.
2. Related Work
| Reference | Technique | Characteristic |
|---|---|---|
| [5,10,14,15,16] | obfuscation method such as k-anonymity | Fast and easy to implement |
| [1,9] | Homomorphic encryption | Euclidean Distance calculation and reputation assessment |
| [17,18,19] | Spatial mapping | Flexible matching and personal preference |
| [2,4] | Road network distance | Accurate location; one-to-one matching |
| [7,21] | Blockchain | Smart contract and reputation assessment system |
3. Models and Problem Definition
3.1. System Model
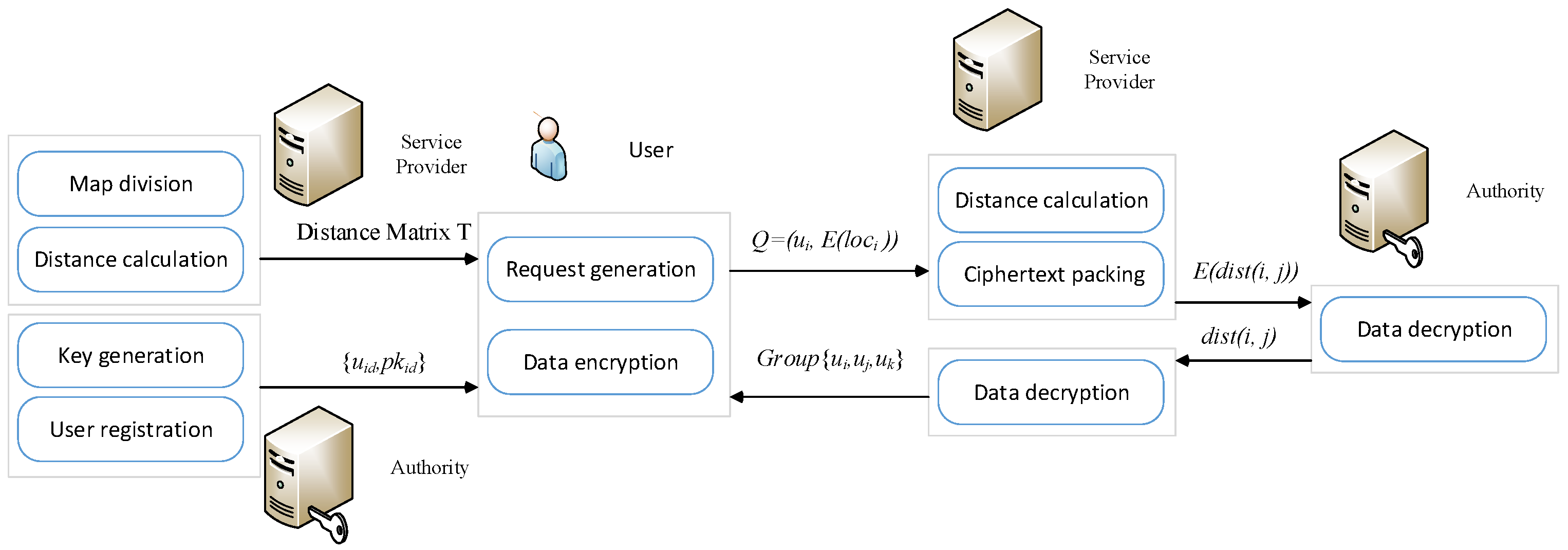
- Users: Each user has a smart phone with a built-in positioning system, where he can get their location anytime and anywhere. At the same time, the user has installed the ride sharing application and completed the registration. A ride sharing query message includes their identity and location information. represents a user’s identity and denotes the user’s location information, including pick-up and drop off locations. A user submits their encrypted query to the service provider to request nearby users who can ride together.
- Service Provider: The ride matching service provider (SP) is responsible for calculating the distance and providing ride matching service. It divides the road network into small areas and calculates the distance matrix of the road network. After receiving the user’s request, the SP calculates the distance between different users with the encrypted location data. For example, represents the encrypted distance between user i and user j. The SP sends the encrypted distance to the authority to get data decrypted. Based on the decrypted distance, the SP gives the matching result , which means user i, j and k share the same ride.
- Authority: The authority is responsible for the registration of users. It provides efficient key management for a wide range of password operations. It decrypts the distance data and sends the result back to the SP. The authority is an independent third party and will not conspire with the SP, thus ensuring the privacy of the service.
3.2. Threat Model
- The SP may try to accurately track users in their daily activities, such as the boarding and alighting locations recorded by the system. According to the travel information collected, it may perform large-scale inference attacks to learn additional user privacy information, such as the user’s home and work address, behavior and interests.
- The malicious users may attempt to capture some sensitive information, including personal information and travel data. They may perform replay attacks. They will apply for ride services. After obtaining the matching results, they cancel the ride request. By repeating this, they may collet many travel information of different users.
3.3. Design Goal
3.3.1. Function
3.3.2. Privacy Preservation
3.3.3. Efficient
4. Problem Formulation and Proposed Scheme
4.1. Problem Formulation
4.2. Proposed Scheme
- (1)
- System initialization: The authorized authority generates a public key and a private key according to the encryption algorithm. The generated keys will be assigned to the designated user. The SP divides the road network into small areas and calculates the distance matrix of the road network.
- (2)
- User Registration: The users use phone number or other personal information to register their personal identity. The service provider will encrypt the registration information.
- (3)
- Request Generation: Users generate and submit the requests to the SP in encrypted form.
- (4)
- Ride Matching: The SP computes the distances between different users based on encrypted location data, and then transmit the encrypted distance to the authority. After the distance is decrypted, the result is sent back to the SP. The SP selects a set of users with the maximum TTS.
5. Performance Evaluation
5.1. Security Analysis
5.2. Simulation Result
- (1)
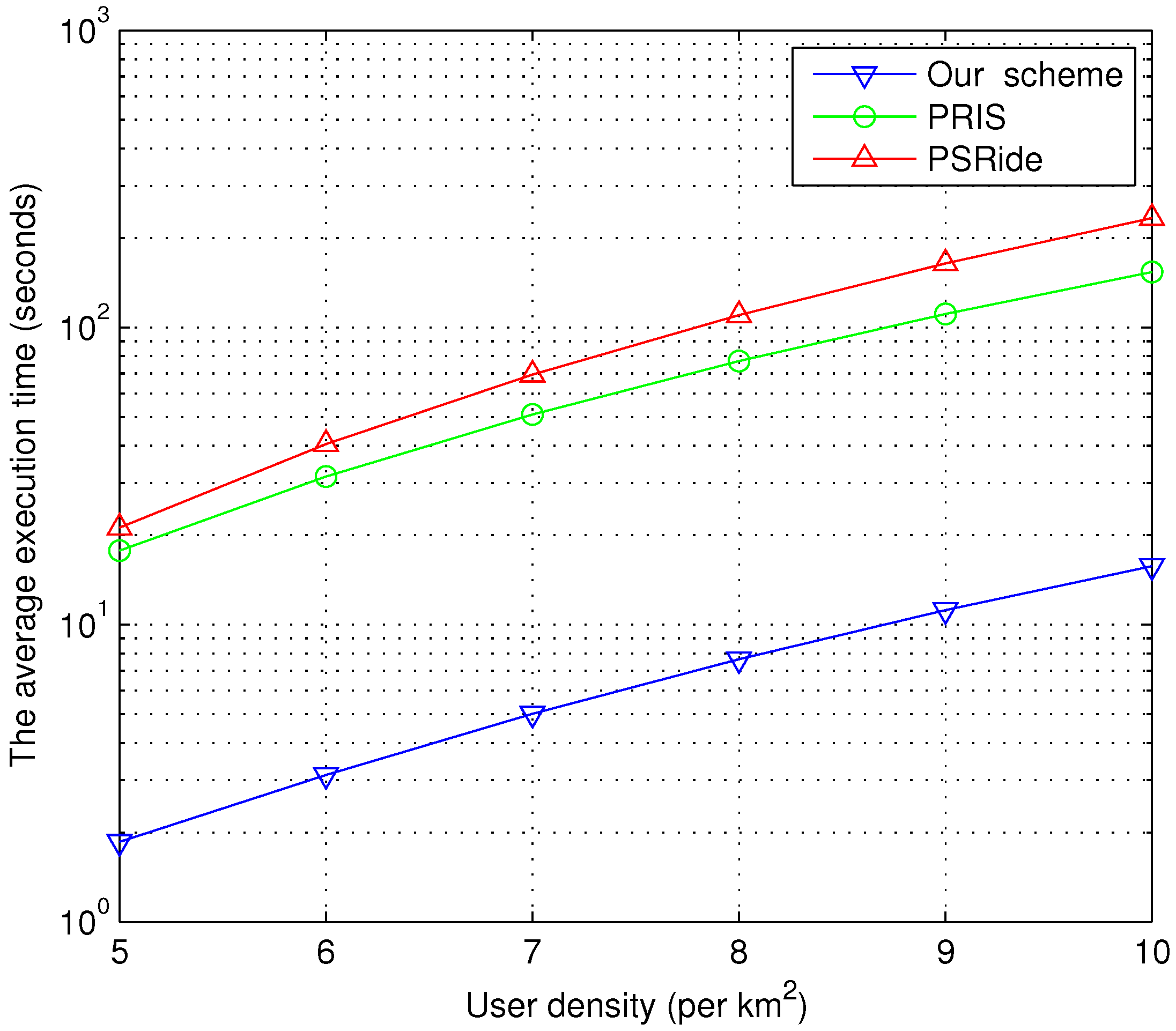
- Complexity Analysis
- (2)
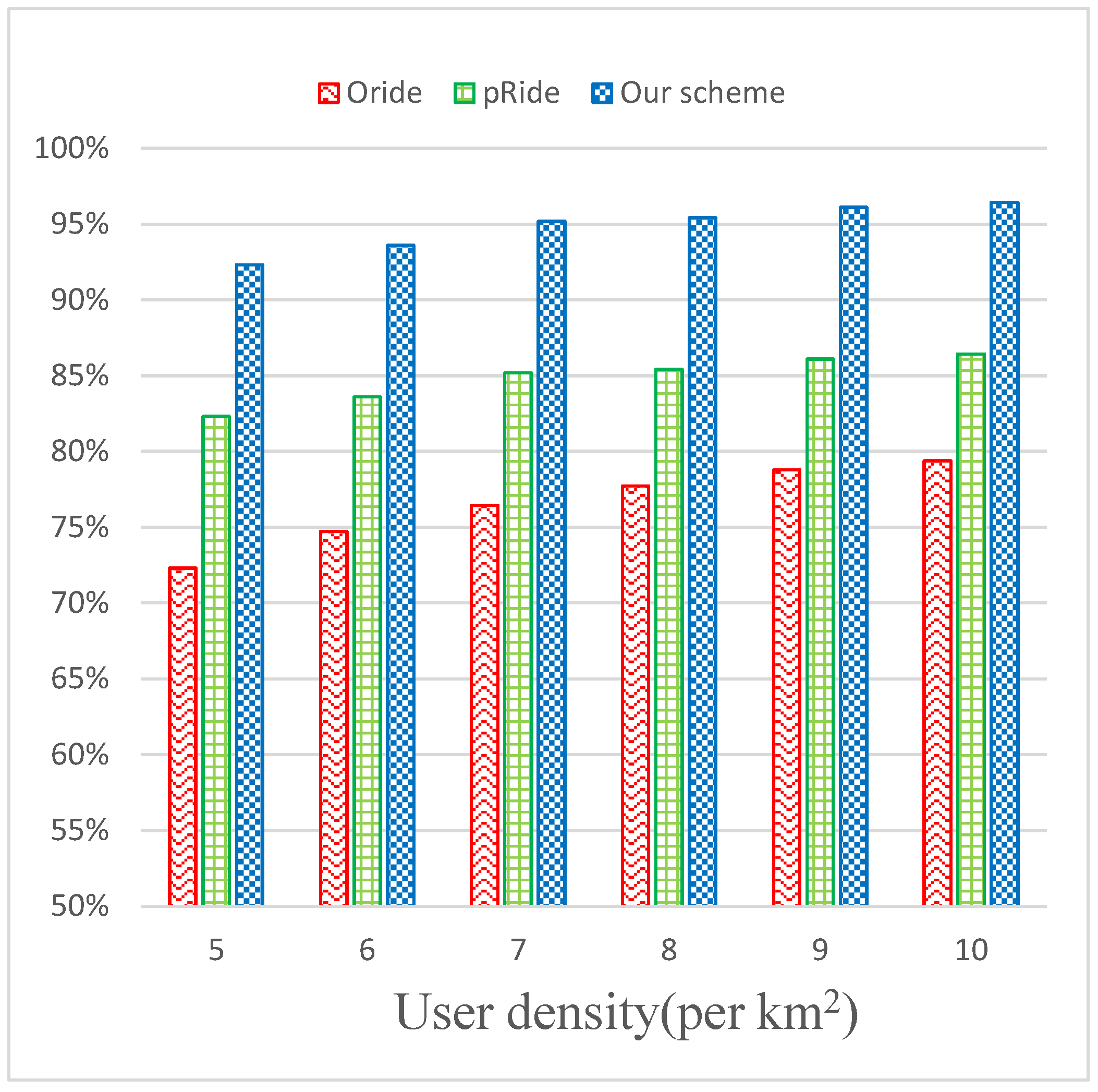
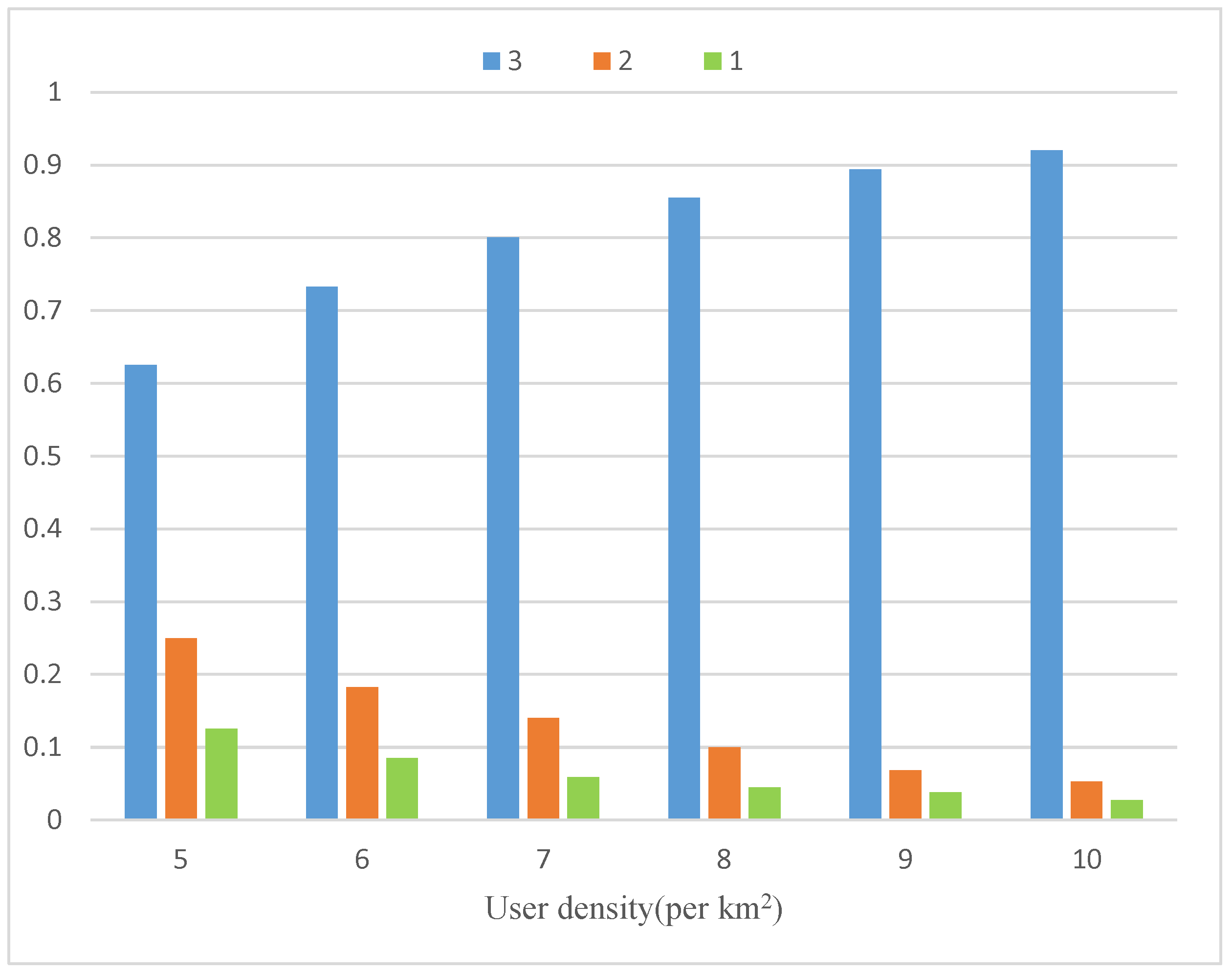
- Accuracy Analysis
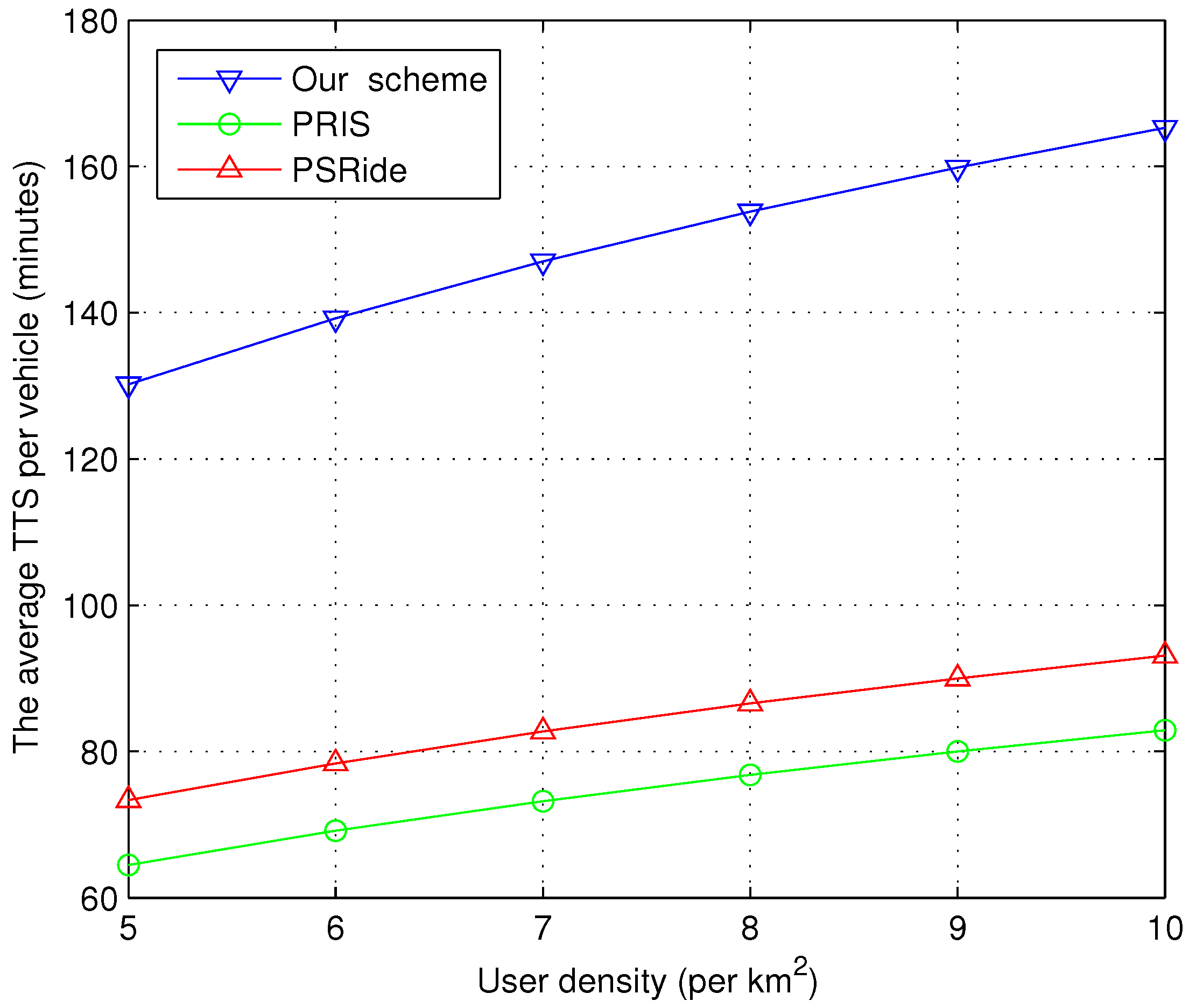
- (3)
- Benefit Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| RSS | Ride Sharing Service |
| RHS | Ride Hailing Service |
| PoI | Point of Interest |
| SP | Service Provider |
| TSS | Travel Time Saving |
| RNE | Road Network Embedding |
| HE | Homomorphic Encryption |
| PHE | Partially Homomorphic Encryption |
| SHE | Somewhat Homomorphic Encryption |
| FHE | Fully Homomorphic Encryption |
References
- Pham, A.; Dacosta, I.; Endignoux, G.; Pastoriza, J.R.T.; Huguenin, K.; Hubaux, J.P. ORide: A Privacy-Preserving yet Accountable Ride-Hailing Service. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17); USENIX Association: Vancouver, BC, Canada, 2017; pp. 1235–1252. [Google Scholar]
- Luo, Y.; Jia, X.; Fu, S.; Xu, M. pRide: Privacy-Preserving Ride Matching Over Road Networks for Online Ride-Hailing Service. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1791–1802. [Google Scholar] [CrossRef]
- Clewlow, R.R.; Mishra, G.S. Disruptive Transportation: The Adoption, Utilization, and Impacts of Ride-Hailing in the United States; Working Paper Series; Institute of Transportation Studies, University of California: Davis, CA, USA, 2017. [Google Scholar]
- Yu, H.; Jia, X.; Zhang, H.; Yu, X.; Shu, J. PSRide: Privacy-Preserving Shared Ride Matching for Online Ride Hailing Systems. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1425–1440. [Google Scholar] [CrossRef]
- Goel, P.; Kulik, L.; Ramamohanarao, K. Optimal Pick up Point Selection for Effective Ride Sharing. IEEE Trans. Big Data 2017, 3, 154–168. [Google Scholar] [CrossRef]
- Yu, H.; Zhang, H.; Yu, X.; Du, X.; Guizani, M. PGRide: Privacy-Preserving Group Ridesharing Matching in Online Ride Hailing Services. IEEE Internet Things J. 2021, 8, 5722–5735. [Google Scholar] [CrossRef]
- Baza, M.; Lasla, N.; Mahmoud, M.M.E.A.; Srivastava, G.; Abdallah, M. B-Ride: Ride Sharing with Privacy-Preservation, Trust and Fair Payment Atop Public Blockchain. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1214–1229. [Google Scholar] [CrossRef]
- Hua, J.; Tong, W.; Xu, F.; Zhong, S. A Geo-Indistinguishable Location Perturbation Mechanism for Location-Based Services Supporting Frequent Queries. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1155–1168. [Google Scholar] [CrossRef]
- Pham, A.; Dacosta, I.; Jacot-Guillarmod, B.; Huguenin, K.; Hajar, T.; Tramer, F.; Gligor, V.; Hubaux, J.P. PrivateRide: A Privacy-Enhanced Ride-Hailing Service. Proc. Priv. Enhancing Technol. 2017, 2017, 38–56. [Google Scholar] [CrossRef]
- He, Y.; Ni, J.; Yang, L.T.; Wei, W.; Deng, X.; Zou, D.; Ahmed, S.H. Differentially Private Tripartite Intelligent Matching Against Inference Attacks in Ride-Sharing Services. IEEE Trans. Intell. Transp. Syst. 2022, 23, 22583–22595. [Google Scholar] [CrossRef]
- Niu, B.; Li, Q.; Zhu, X.; Cao, G.; Li, H. Achieving k-anonymity in privacy-aware location-based services. In Proceedings of the IEEE INFOCOM 2014–IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 754–762. [Google Scholar]
- Fu, Z.; Wu, X.; Guan, C.; Sun, X.; Ren, K. Toward Efficient Multi-Keyword Fuzzy Search Over Encrypted Outsourced Data With Accuracy Improvement. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2706–2716. [Google Scholar] [CrossRef]
- Dong, C.; Chen, L.; Wen, Z. When Private Set Intersection Meets Big Data: An Efficient and Scalable Protocol. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, CCS ’13, Berlin, Germany, 4–8 November 2013; Association for Computing Machinery: New York, NY, USA, 2013; pp. 789–800. [Google Scholar]
- Friginal, J.; Gambs, S.; Guiochet, J.; Killijian, M.O. Towards privacy-driven design of a dynamic carpooling system. Pervasive Mob. Comput. 2014, 14, 71–82. [Google Scholar] [CrossRef]
- Chow, C.Y.; Mokbel, M.F.; Liu, X. A peer-to-peer spatial cloaking algorithm for anonymous location-based service. In Proceedings of the 14th Annual ACM International Symposium on Advances in Geographic Information Systems, Arlington, VA, USA, 10–11 November 2006; p. 171. [Google Scholar]
- Martelli, F.; Renda, M. Enhancing Privacy in Ride-Sharing Applications Through POIs Selection. In Proceedings of the 2022 IEEE 23rd International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), Belfast, UK, 14–17 June 2022; pp. 444–449. [Google Scholar]
- Nabil, M.; Mahmoud, M.; Sherif, A.; Alsharif, A.; Abdallah, M.M. Efficient and Privacy-Preserving Ride Sharing Organization for Transferable and Non-Transferable Services. IEEE Trans. Dependable Secur. Comput. 2018, 18, 1291–1306. [Google Scholar] [CrossRef]
- Vignesh, R.; Samhitha, B.K.; Suja, C.M.; Divya, S. Privacy-preserving Ride Sharing Scheme with Global Social Network for vehicles using Big Data. Indian J. Sci. Technol. 2018, 11, 21. [Google Scholar] [CrossRef]
- Xie, H.; Guo, Y.; Jia, X. A Privacy-preserving Online Ride-hailing System without Involving a Third Trusted Server. IEEE Trans. Inf. Forensics Secur. 2021, 16, 3068–3081. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual IEEE Symposium on Foundations of Computer Science, Chicago, IL, USA, 3–5 November 1982. [Google Scholar]
- Baza, M.; Mahmoud, M.; Srivastava, G.; Alasmary, W.; Younis, M. A Light Blockchain-Powered Privacy-Preserving Organization Scheme for Ride Sharing Services. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 25–28 May 2020. [Google Scholar]
- Ruch, C.; Lu, C.; Sieber, L.; Frazzoli, E. Quantifying the Efficiency of Ride Sharing. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5811–5816. [Google Scholar] [CrossRef]
- He, Y.; Ni, J.; Wang, X.; Niu, B.; Li, F.; Shen, X. Privacy-Preserving Partner Selection for Ride-Sharing Services. IEEE Trans. Veh. Technol. 2018, 67, 5994–6005. [Google Scholar] [CrossRef]
- Shahabi, C.; Kolahdouzan, M.R.; Sharifzadeh, M. A Road Network Embedding Technique for K-Nearest Neighbor Search in Moving Object Databases. GeoInformatica 2003, 7, 255–273. [Google Scholar] [CrossRef]
- Acar, A.; Aksu, H.; Uluagac, A.S.; Conti, M. A Survey on Homomorphic Encryption Schemes: Theory and Implementation. ACM Comput. Surv. 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF Formulas on Ciphertexts. In Proceedings of the Theory of Cryptography; Kilian, J., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 325–341. [Google Scholar]
- Gentry, C. A fully homomorphic encryption scheme. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 2009. [Google Scholar]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Proceedings of the Advances in Cryptology—EUROCRYPT ’99; Stern, J., Ed.; Springer: Berlin/Heidelberg, Germany, 1999; pp. 223–238. [Google Scholar]



| Description | Value |
|---|---|
| Road network size | km |
| Matching threshold | 2 km |
| User scale | 2000–4000 |
| User density | 5–10 per km |
| Maximum riders of a taxi | 3 |
| Parameters of Paillier cryptosystem | N = 1024 bits, g = 160 bits |
| Dimension | 4, 8, …, 32 |
| Bit-length of a sketch | 32 bits |
| Dimension | Original Scheme | Our Scheme | ||||
|---|---|---|---|---|---|---|
| Rider (KBs) | Driver (KBs) | Server (MBs) | Rider (KBs) | Driver (KBs) | Server (MBs) | |
| 4 | 2.0 | 2.0 | 8.7 | 0.256 | 0.256 | 4.5 |
| 8 | 4.1 | 4.1 | 17.2 | 0.256 | 0.256 | 7.3 |
| 12 | 6.1 | 6.1 | 25.8 | 0.256 | 0.256 | 10.2 |
| 16 | 8.2 | 8.2 | 34.3 | 0.256 | 0.256 | 13.1 |
| 20 | 10.3 | 10.3 | 42.9 | 0.256 | 0.256 | 16.0 |
| 24 | 12.3 | 12.3 | 51.4 | 0.256 | 0.256 | 18.9 |
| 28 | 14.4 | 14.4 | 59.9 | 0.256 | 0.256 | 21.8 |
| 32 | 16.5 | 16.5 | 68.5 | 0.256 | 0.256 | 24.6 |
| Dimension | Original Scheme | Our Scheme | ||||
|---|---|---|---|---|---|---|
| Rider (s) | Driver (s) | Server (s) | Rider (ms) | Driver (ms) | Server (s) | |
| 4 | 3.4 | 3.4 | 130.9 | 5.0 | 4.9 | 2.9 |
| 8 | 6.9 | 6.9 | 297.3 | 5.1 | 4.9 | 4.2 |
| 12 | 10.3 | 10.3 | 380.3 | 4.9 | 5.0 | 5.4 |
| 16 | 13.8 | 13.8 | 549.4 | 5.1 | 4.9 | 6.7 |
| 20 | 17.0 | 17.0 | 729.1 | 4.9 | 5.0 | 7.7 |
| 24 | 20.6 | 20.6 | 801.4 | 5.0 | 4.9 | 9.1 |
| 28 | 24.0 | 24.0 | 1048.9 | 5.1 | 5.0 | 10.1 |
| 32 | 27.5 | 27.5 | 1187.5 | 4.9 | 5.0 | 11.2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Q.; Wu, H.; Dong, C. A Privacy-Preserving Ride Matching Scheme for Ride Sharing Services in a Hot Spot Area. Electronics 2023, 12, 915. https://doi.org/10.3390/electronics12040915
Li Q, Wu H, Dong C. A Privacy-Preserving Ride Matching Scheme for Ride Sharing Services in a Hot Spot Area. Electronics. 2023; 12(4):915. https://doi.org/10.3390/electronics12040915
Chicago/Turabian StyleLi, Qingyuan, Hao Wu, and Chen Dong. 2023. "A Privacy-Preserving Ride Matching Scheme for Ride Sharing Services in a Hot Spot Area" Electronics 12, no. 4: 915. https://doi.org/10.3390/electronics12040915
APA StyleLi, Q., Wu, H., & Dong, C. (2023). A Privacy-Preserving Ride Matching Scheme for Ride Sharing Services in a Hot Spot Area. Electronics, 12(4), 915. https://doi.org/10.3390/electronics12040915






