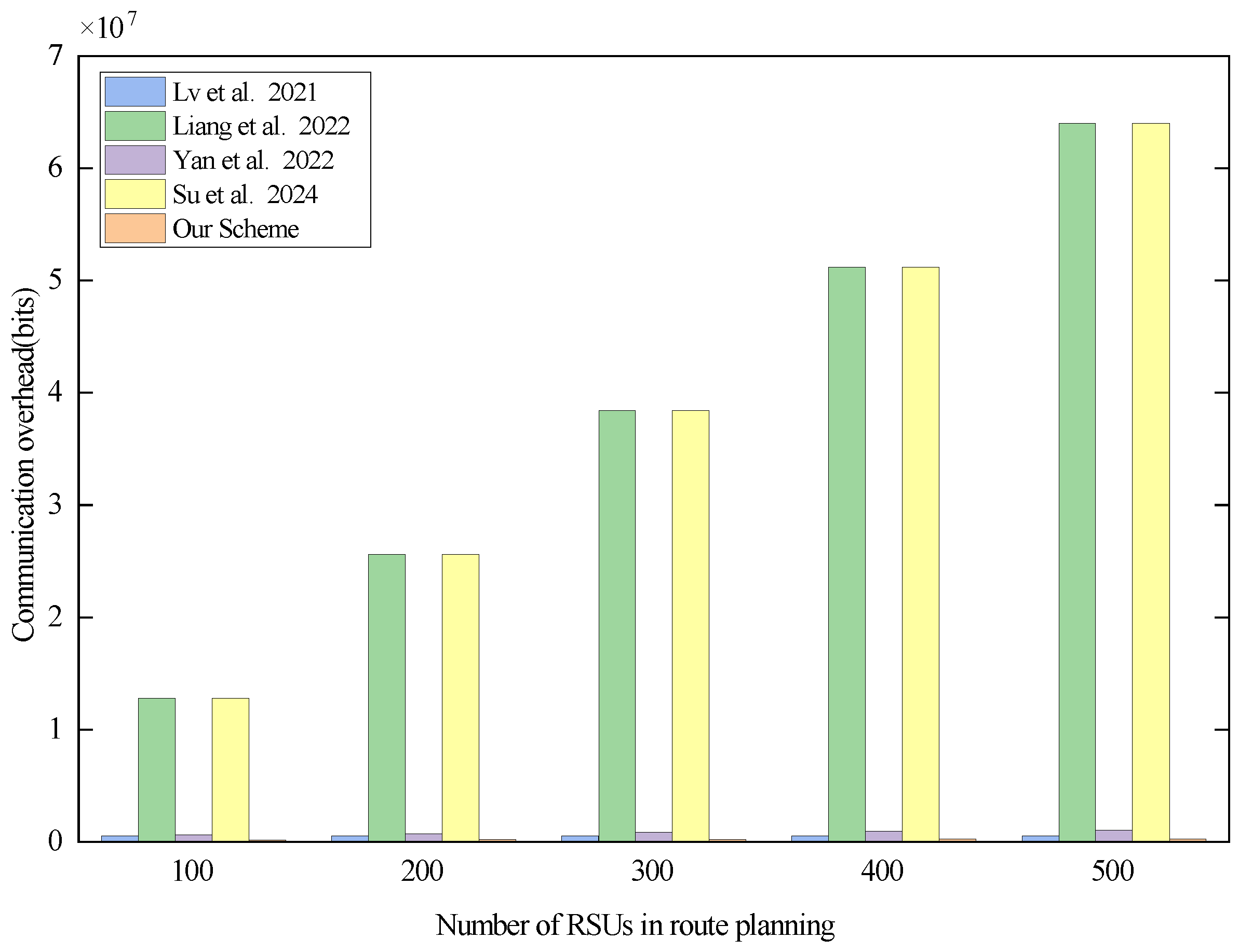Abstract
Due to the characteristics of high-speed movement of vehicles, authentication between vehicles and roadside units (RSUs) needs to be performed quickly. Vehicles can obtain the authentication information of the relevant RSUs from the certification authority (CA) in advance through route planning. Fast authentication can be performed when the vehicle enters the RSU range. However, in most of the current vehicle-to-infrastructure (V2I) fast authentication schemes, when the vehicle requests the authentication information of an RSU from the CA, the vehicle often needs to provide the CA with the travel path information, which leads to the CA easily obtaining the travel path of the vehicle. In addition, the CA encrypts the private keys of RSUs and sends them to vehicles as authentication keys, and the vehicles can obtain the private key information of RSUs directly after decryption. Once the private keys of RSUs are leaked, vehicular ad hoc networks (VANETs) can be attacked by malicious access. In order to protect the confidentiality of RSU private keys and the route privacy of vehicles, we propose a privacy-preserving V2I fast authentication scheme in VANETs. The scheme realizes the confidentiality of RSU private keys and the route privacy protection of vehicles by improving the oblivious transfer (OT) algorithm. Security analysis proves that our scheme has good privacy and attack resistance. Finally, performance evaluation shows that the proposed scheme performs better in terms of computational overhead and communication overhead compared to related schemes.
1. Introduction
With the rapid development of the Internet of Things (IoT), Big Data, Artificial Intelligence (AI), and other technologies, the intelligence and automation of vehicular networking systems have become a trend. VANETs are an important part of Intelligent Transportation Systems (ITSs) [1]. They can provide real-time road conditions, traffic information, safety warnings, and other services that are important for improving driving safety and reducing traffic accidents [2,3]. Therefore, information security and data exchange in VANETs become particularly important. In general, VANETs consist of the following three main entities: a certification authority (CA), roadside units (RSUs), and on-board units (OBUs) [4]. Their communication method is divided into two main parts, namely vehicle-to-infrastructure communication (V2I) and vehicle-to-vehicle communication (V2V) [5]. Both V2V and V2I communications follow the Dedicated Short-Range Communications (DSRC) protocol and use the IEEE 802.11p standard for wireless communication [6,7]. In V2I communication, information about road safety and traffic conditions is mainly provided to vehicles by RSUs to promote driving safety. In V2V communication, each vehicle utilizes a wireless transceiver to communicate in real time with other vehicles around it, exchanging information such as auxiliary information about the road, real-time traffic conditions, and emergency situations [8,9]. In order to secure communication in VANETs, mutual authentication between communicating entities is required before communication can be realized. Therefore, authentication protocols in VANETs are crucial.
In 2019, Ahmad et al. [10] introduced a scheme related to route planning in VANETs through which fast authentication for V2I is achieved. In the V2I fast authentication process, the vehicle usually plans the travel path in advance before traveling and calculates the RSUs that the path needs to pass through, then requests the authentication keys of the RSUs on the path from the CA; finally, the CA sends the authentication keys of these RSUs to the vehicle. When the vehicle enters the coverage area of the relevant RSU, it then utilizes the corresponding RSU authentication key to authenticate with the RSU. However, in many current V2I fast authentication schemes, when the vehicle requests authentication information from the CA for an RSU, the vehicle needs to provide the CA with the path information of the trip, which results in the CA easily obtaining the travel path of the vehicle. In fact, the vehicle’s sensitive information, such as the traveling path, departure time, and parking time, is private to other entities (including the CA). In addition, the CA encrypts the private key of the RSU as the authentication key and sends it to the vehicle, which is able to obtain the private key of that RSU directly after decryption. Since the CA does not further encrypt the private keys of these RSUs, once the private keys of these RSUs are maliciously leaked by vehicles, the RSUs may be subject to attacks such as malicious access and information tampering by attackers. This can cause serious consequences for the whole VANET. Therefore, how to ensure the confidentiality of RSU private keys and the route privacy of vehicles has become an urgent problem. To solve this problem, this paper proposes a privacy-preserving V2I fast authentication scheme in VANETs. The contributions of this scheme are described as follows:
- In the route-planning phase, the RSU authentication key sent by the CA to the vehicle is based on the RSU private key with the vehicle’s public identity key added. In this way, the confidentiality of the RSU private key is guaranteed, in addition to ensuring that this authentication key can only be used by the vehicle that applies for it.
- When the vehicle requests the authentication key of an RSU from the CA, the improved OT algorithm is utilized to encrypt the driving path information of the vehicle so that the CA cannot infer the driving path of the vehicle from the request information of the vehicle. In this way, the route privacy of the vehicle is protected.
The rest of this paper is organized as follows. Section 2 describes work related to privacy preservation in VANETs. Section 3 describes the preparatory work involved in this paper. Section 4 describes the models and design goals. Section 5 describes the privacy protection scheme proposed in this paper. A security analysis is presented in Section 6. Section 7 presents a comparison of performance overhead. In Section 8, we provide our conclusions and a discussion.
2. Related Works
In this section, privacy protection schemes in VANETs are introduced, and the advantages and disadvantages of these schemes are discussed.
In order to ensure the data privacy of each entity in VANETs, it is crucial to establish a system that can effectively protect the applications in VANETs. The protection of privacy information mainly relies on the communication authentication protocols in VANETs. Therefore, a secure and reliable authentication protocol needs to be constructed to ensure the confidentiality of private keys and route privacy in VANETs [11,12,13,14,15]. In terms of key management, to address the problems of complex and variable topologies that cause keys to be constantly updated every moment, as well as interference with regular V2I data exchanges, Tan et al. [16] proposed a secure authentication and key management scheme to solve the above problems. The scheme issues an independent session key for each legitimate vehicle, vehicle data are shared between neighboring vehicles, and all authenticated vehicles maintain group management records. As a result, the scheme has a large storage burden on the vehicle side. Ma et al. [17] proposed an efficient, decentralized, blockchain-based key management mechanism (DB-KMM) for in-vehicle self-organizing networks that automatically realizes the registration, updating, and revocation of users’ public keys. However, the connection, node deployment, and maintenance of the whole network require high operation costs. Xu et al. [18] proposed a BAGKD protocol to realize powerful and efficient group networking and ensure the security and efficiency of VANETs. The group key can be dynamically updated through the group key distribution mechanism, which effectively reduces the risk of group key breakage and leakage. Mansour et al. [19] introduced a new group key management protocol, ALMS, which solves the privacy problem of group members and the collusion problem among receivers. However, when a vehicle applies to join a group, the TA needs to broadcast the encrypted group key to all vehicles in the receiving group, which tends to lead to problems such as channel congestion. Li et al. [20] proposed an unlinkable authentication key protocol that prevents the problem of entity collusion in VANETs. The protocol relies heavily on the AAC stored in the blockchain and needs to focus on managing and controlling the data on the chain. As a result, the efficiency of authentication decreases. Li et al. [21] proposed an identity-based dynamic data integrity auditing scheme for CMTS. The scheme’s batch auditing approach can reduce the key management burden in VANETs and improve the auditing efficiency. Wei et al. [22] proposed a verified secure AKA scheme. The scheme is a tree-based key negotiation algorithm that focuses on assigning a public session key to vehicles and RSUs after they have been authenticated. This session key can protect V2V and V2I communications, along with the authentication algorithm and encryption algorithm for messages. Since frequent communication between the TAand RSUs is required, the scheme requires a large communication overhead. Yang et al. [23] proposed a two-way anonymous authentication and key negotiation scheme based on identity authentication. The scheme claims to fulfill the real-time communication requirements of VANETs with good security. However, due to the resource cost, the RSU nodes in VANET quickly reach their peak processing capacity under large-scale traffic due to the excessive number of messages that need to be authenticated and, thus, cannot quickly authenticate a large number of messages.
In terms of route privacy, the transmission of messages in open-access environments such as VANETs is faced with the most critical and challenging privacy issues [24]. To protect vehicle route privacy in VANETs, Sampigethaya et al. [25] proposed a location privacy scheme called CARAVAN. This scheme addresses the location privacy threat in VANETs based on broadcast tracking of vehicles. However, the scheme is still able to analyze the location privacy of vehicles by combining the analysis of map data and communication traffic. In order to further protect the user’s route privacy information, Zhu et al. [26] proposed bilinear pairing-based local authentication and roaming authentication for VANETs, which is able to provide secure communication and anonymous authentication between RSUs and vehicles. However, since the authentication process of this scheme includes both local and roaming authentication, the vehicle needs to spend a long time waiting for a response from the RSU during the authentication process between the vehicle and the RSU, resulting in inefficient communication. In order to efficiently and securely realize authentication in VANETs, Cui et al. [27] proposed a novel authentication scheme. The scheme uses a dual pseudonym approach to hide the true identity of the vehicle and a dynamic update technique to periodically update the information stored in the vehicle. By not using bilinear pairing, they claim that the scheme performs better in terms of computational overhead and communication overhead and is suitable for widespread application in VANETs. Wahid et al. [28] proposed a holistic safety-aware location-preserving scheme called Coupling Privacy with Safety (CPS). They claim that this scheme can ensure the provision of driver privacy and security. However, in this scheme, an RSU can use the information contained in the BSM to obtain the point in time when the vehicle enters its range and the driving time within its range. Therefore, the privacy information of the vehicle is not fully protected. Subsequently, Lv et al. [29] proposed a lightweight V2I fast authentication scheme that combines Moore’s curve and BGN homomorphic encryption to protect the vehicle’s travel path, making it impossible for CAs to learn about the vehicle’s travel path as well. Liang et al. [30], Yan et al. [31], and Su et al. [32] all utilized the idea of oblivious transfer to achieve route privacy protection for vehicles, which also makes it impossible for the CA to know a vehicle’s travel path. However, these schemes [29,30,31,32] are all subject to the problem that when the vehicle requests the RSU authentication key from the CA in the route-planning phase, the RSU authentication key returned by the CA to the vehicle is the private key of the RSU. These private keys are unique and can be used by all vehicles in the system to authenticate with the corresponding RSU. Therefore, once these RSU private keys are maliciously leaked or disseminated by vehicles, the RSUs, may be subject to malicious access and information tampering by attackers. This can have disastrous consequences for the entire VANET.
Inspired by the above problem, we propose a privacy-preserving V2I fast authentication scheme. The scheme ensures the confidentiality of RSUs’ private keys and the route privacy of vehicles through an improved oblivious transfer algorithm. In the route-planning phase, when a vehicle requests an RSU authentication key from the CA, the vehicle sends its planned route information to the CA, which is encrypted using the OT algorithm so that the CA cannot know which RSUs the vehicle passes through. In addition, the RSU authentication key returned by the CA to the vehicle is the vehicle’s public identity key added to the RSU private key. This ensures that the RSU’s authentication key can only be used by the requesting vehicle. Even if the authentication key of the RSU obtained by the vehicle is leaked, the security of the RSU private key can still be guaranteed. Therefore, while protecting the RSU private key, the route privacy of the vehicle is also protected.
3. Preliminaries
In this section, we focus on elliptic curve cryptography (ECC) and oblivious transfer (OT) as used in this paper.
3.1. Elliptic Curve Cryptography
Let be a finite field and p be a large prime order. E is an elliptic curve defined by , where is a constant and . Suppose that the infinitely far point is O; then, O and all the points on E form a cyclic additive group G with the order q, and its generator is P. The elliptic curve group (G) has the following properties.
- Point addition: Let be two points on E. If P and Q are not the same, there exists a point, , where R is the intersection of straight lines on E connecting P and Q. If P and Q are the same, then . If , then .
- Scalar point multiplication: Scalar multiplication on E is the repeated addition of a point. Let , ; then, .
- Elliptic curve discrete logarithm problem (ECDLP): Given two random points (), compute , where . It is difficult to compute x from R in probabilistic polynomial time.
- Elliptic curve computational Diffie–Hellman problem (ECCDHP): Given three random points (), compute , where . It is difficult to compute in probabilistic polynomial time.
3.2. Oblivious Transfer
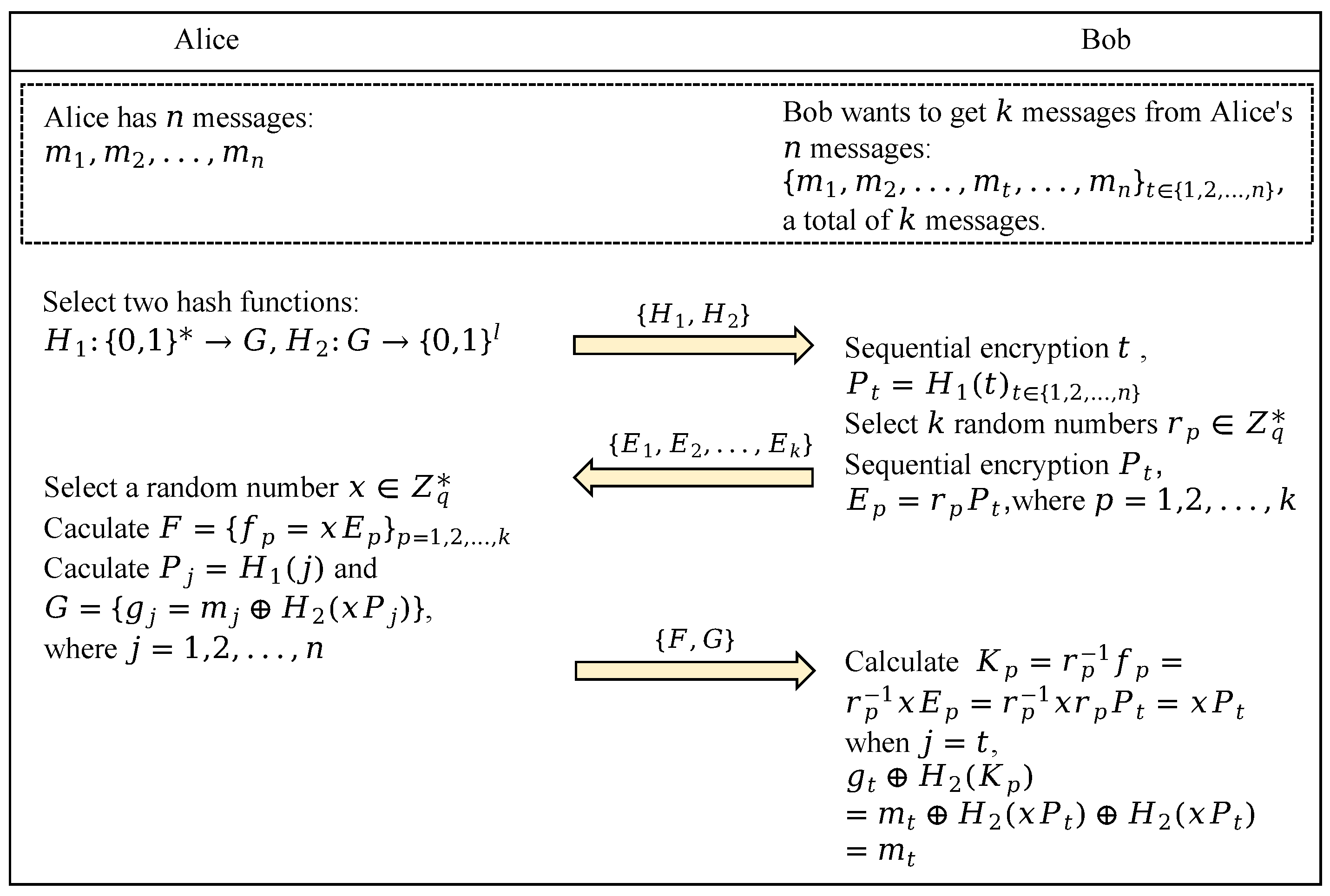
Oblivious transfer (OT) is a basic cryptographic primitive that is widely used in areas such as secure multi-party computation. OT was first proposed by Michael O. Rabin [33] in 1981. In Rabin’s OT protocol, the sender, Alice, sends a message (m) to the receiver, Bob, and the receiver (Bob) accepts the message (m) with a probability. Therefore, at the end of the communication, Alice has no way of knowing which message Bob has accepted. Subsequently, after continuous improvement by researchers, it can be generalized to the k-out-of-n OT scheme. In general, there are two entities in an , namely a sender containing n messages and a receiver who wants to receive k messages from the sender’s n messages. The receiver can select k messages from the n messages, denoted as . In other words, the receiver can only receive the k messages it has selected, and the sender has no way of knowing which specific messages the receiver has received [34]. is defined as follows: Alice holds n messages, and Bob wants k of them. Bob encrypts the desired k messages and sends them to Alice, who encrypts all of them and returns them to Bob. In the end, Bob can only receive the messages he wants. In particular, Alice does not know the details of the information obtained by Bob, while Bob cannot be informed of the other information Alice has. The specific process is shown in Figure 1 below.
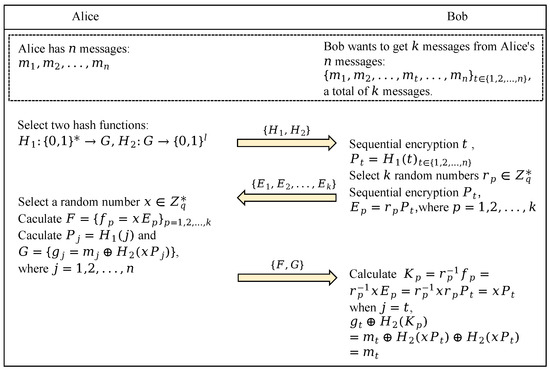
Figure 1.
Oblivious transfer.
4. Models and Design Goals
In this section, the system model, attack model, and design goals of the proposed scheme are presented.
4.1. System Model
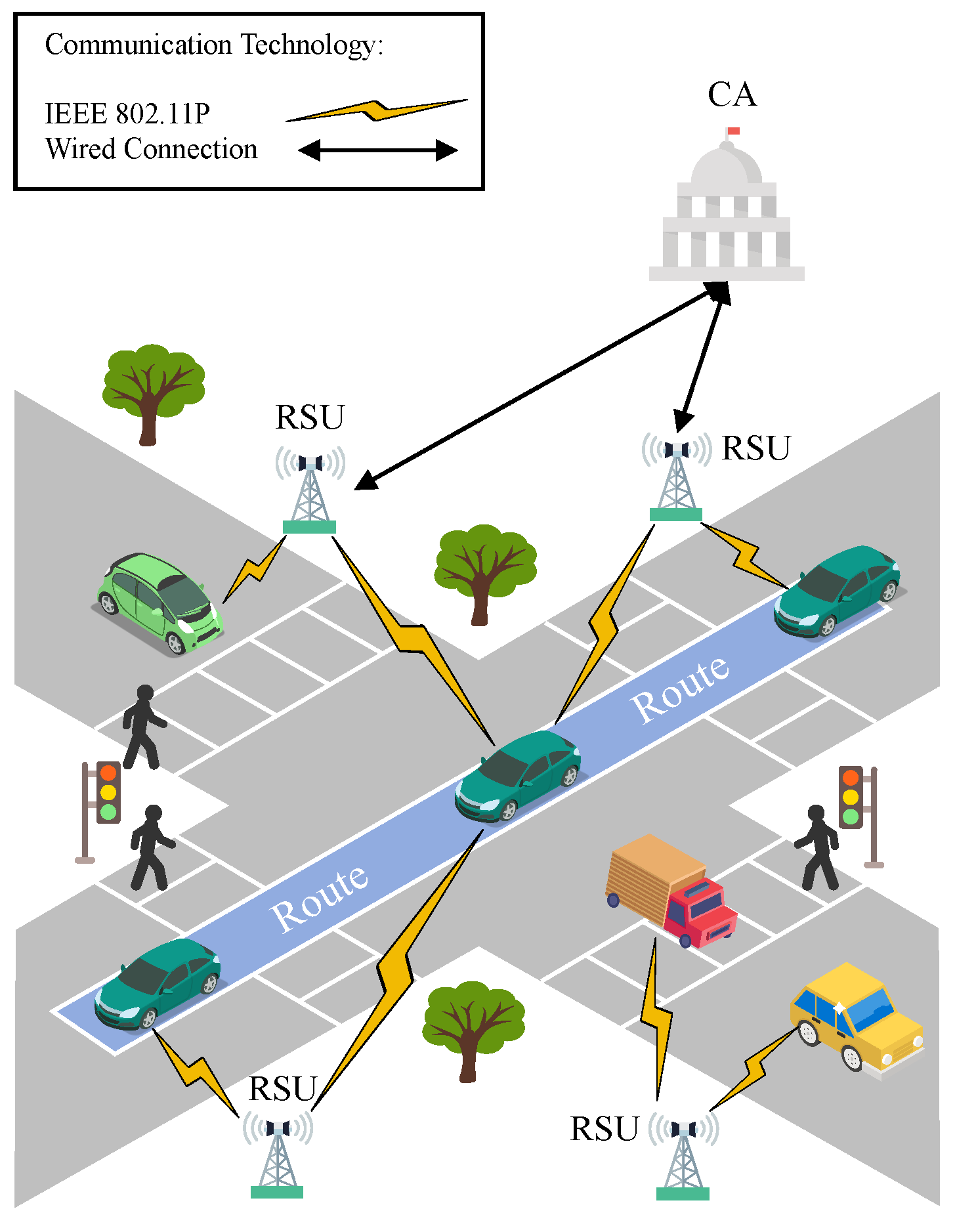
The system model in this scheme consists of three main entities, namely the certification authority (CA), the roadside unit (RSU), and the vehicle with an OBU installed. The responsibilities of each entity are described as shown in Figure 2 below:
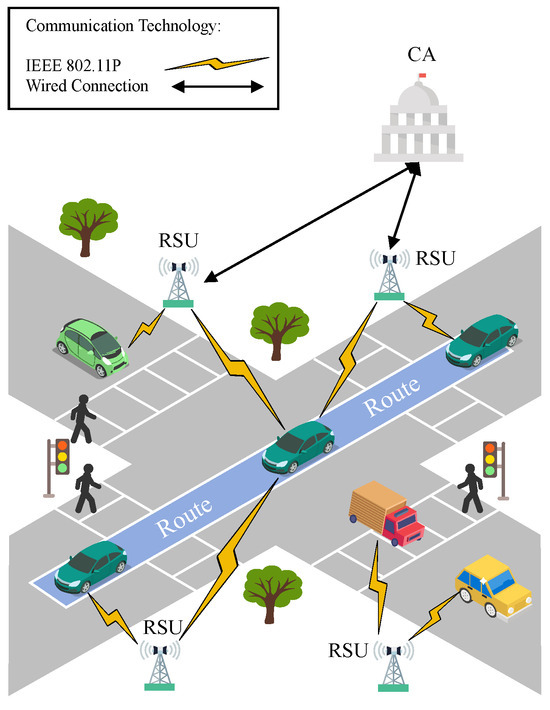
Figure 2.
System model.
- CA: The CA is the highest administrator within VANETs, with sufficient computing and storage capacity. The CA is mainly responsible for setting system parameters, vehicle registration, storage and distribution of RSU authentication keys, and assisting in vehicle identity authentication. Although the CA will strictly follow the predefined relevant protocols, it is also expected to infer private information such as the vehicle’s departure location, driving status, and trip destination from the vehicle’s request information.
- RSU: RSUs are roadside-installed infrastructure that are primarily responsible for collecting and processing data from vehicles to provide real-time information on traffic conditions and related services. In addition, they work with the CA to ensure the security of vehicle identities and communications. Through the deployment of RSUs, vehicles can effectively communicate and collaborate with road infrastructure and other vehicles.
- Vehicle: As mobile nodes in VANETs, vehicles with OBUs installed have communication and sensing capabilities. They communicate with RSUs, and other vehicles through their OBUs to obtain real-time traffic information and vehicle condition data. In addition, vehicles can share their own information with other vehicles, leading to collaborative operations between vehicles, thereby optimizing the ITS.
4.2. Attack Model
This section demonstrates some of the security threats that can be suffered in this scheme. The registration phase of the scheme occurs on a secure communication channel. Apart from that, the communication between the vehicle and other entities (RSUs, CA and other vehicles) in other phases takes place on an open and unsecured wireless communication channel, which provides breakthrough opportunities for attackers. The identities of RSUs are made public so that vehicles can plan their travel paths. The main elements involved in the attack model of this protocol are shown below.
- An attacker can easily access the public channel and intercept, replay, modify, and forge the messages transmitted on that channel.
- No attacker is able to modify, read, or delete any information stored in the vehicles and RSUs.
- It is assumed that CA and RSUs will honestly implement the designed protocols, but these entities still wish to infer the vehicle’s privacy from the obtained information, such as private information about the vehicle’s travel path and departure time.
- Suppose a vehicle wants to infer the private key of an RSU from the RSU authentication key obtained by the CA to generate an authentication key suitable for use by any vehicle.
4.3. Design Goals
In order to address the issues of confidentiality of RSU private keys and route privacy of vehicles in VANETs, this scheme should achieve the following security and privacy objectives:
- RSU private key confidentiality: RSUs’ private keys should be confidential to other entities (except the CA). Other entities are prevented from misusing an RSU’s private key for attacks such as malicious access to the RSU.
- Route privacy: Protecting vehicle route privacy is critical during the route-planning phase when the CA assists a vehicle in requesting an RSU’s authentication key. If the system fails to meet this requirement, then the CA can easily access the traveling path of any vehicle.
- Traceability: Once the presence of a malicious vehicle is detected as a threat to the security of a VANET, the CA obtains the real identity of the vehicle and revokes its identity information, preventing it from jeopardizing the security of the VANET.
- Unlinkability: An attacker cannot determine whether two or more received messages originate from the same sender. In other words, the attacker cannot trace the real identity of a vehicle by analyzing the messages sent by the vehicle.
- Resistance to common security attacks: Our scheme is resistant to several common security attacks, such as Sybil attacks, modification attacks, replay attacks, and repudiation attacks.
5. Proposed Scheme
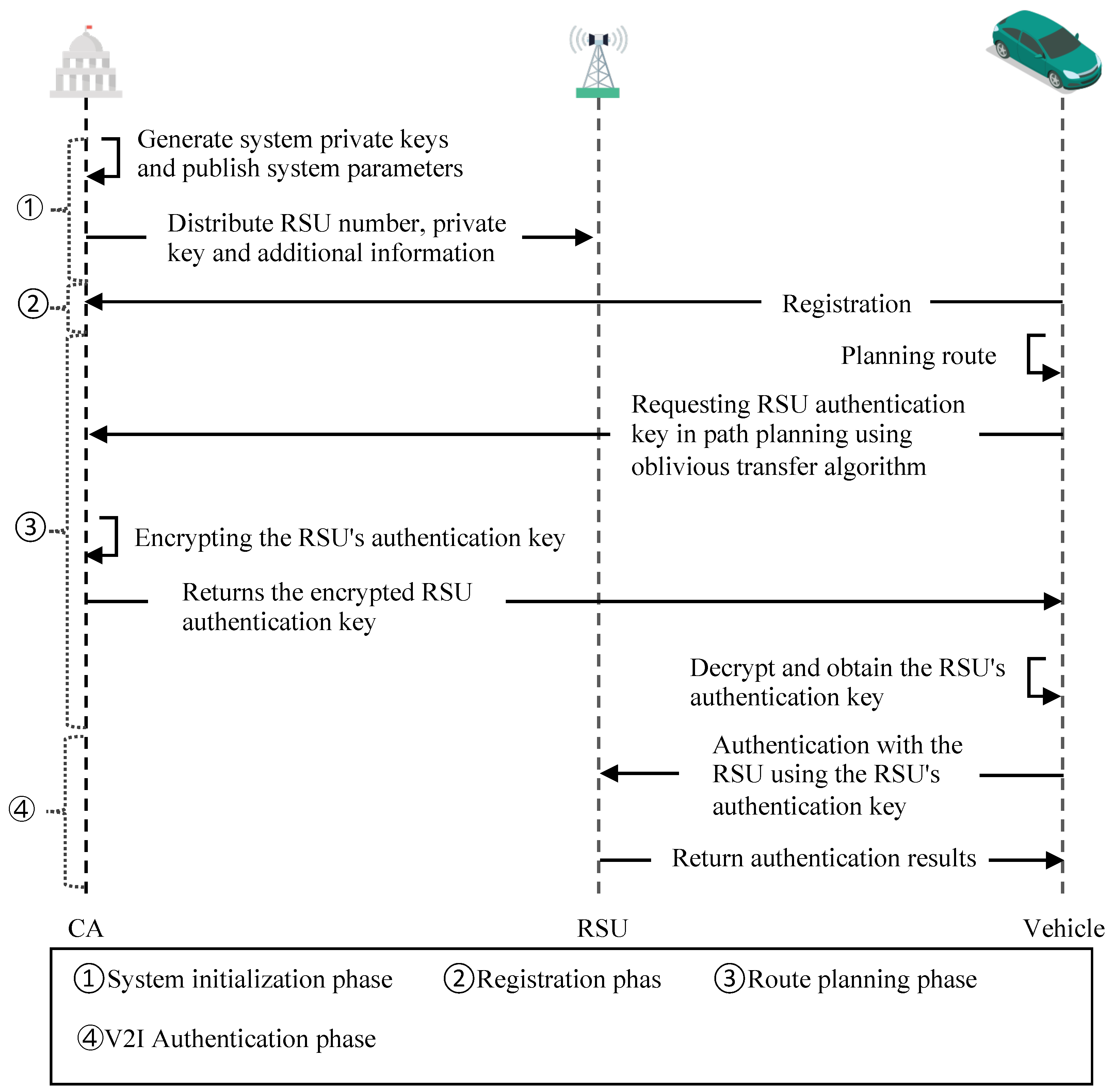
This scheme consists of four phases, namely a system initialization phase, registration phase, route-planning phase, and V2I authentication phase. The notations used in our scheme are shown in Table 1. Meanwhile, in order to describe the work of each entity at each stage more intuitively, Figure 3 shows the workflow of each entity in VANETs.

Table 1.
List of notations.
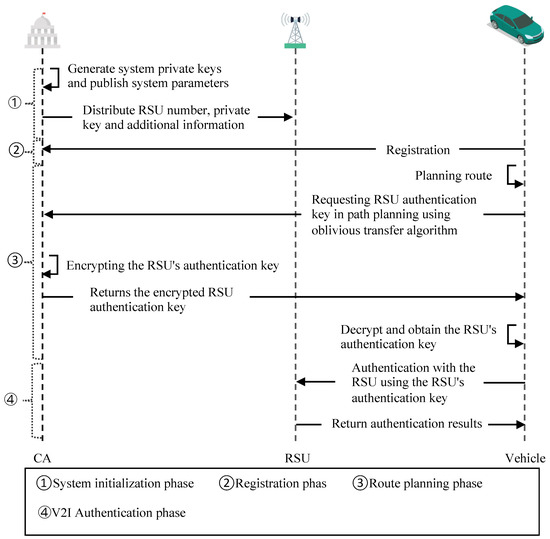
Figure 3.
Workflow of entities in VANETs.
5.1. System Initialization Phase
In this phase, the CA sets up all the necessary system parameters and releases them. To ensure smooth system initialization, the CA needs to perform the following specific steps:
Step 1: The CA selects a security parameter () and a non-singular elliptic curve (, where ) according to the system requirements. Subsequently, an additive cyclic group (G, containing all points on elliptic curve E and one infinity point) of prime order q and generating element P is selected over finite domain .
Step 2: The CA selects a random number () as the system master private key, then computes the corresponding system public key ().
Step 3: The CA selects several secure one-way hash functions (, where l denotes a fixed length bit string).
Step 4: Assume that all RSUs are labeled within the system as . The CA assigns a corresponding private key () to each RSU by secure means. The CA stores the relevant information of all RSUs (, where is the additional information of ). The private key () needs to be updated periodically. The RSU information is stored in the format shown in Table 2 below.

Table 2.
RSU information.
Step 5: The CA chooses the symmetric encryption algorithm (), the symmetric decryption algorithm (), the asymmetric encryption algorithm (), and the asymmetric decryption algorithm (). The algorithms are described as follows:
- Symmetric encryption: , where c is the cipher text, is the private key, and m is the plain text.
- Symmetric decryption: .
- Asymmetric encryption: , where c is the cipher text, is the public key, and m is the plain text.
- Asymmetric decryption: , where is the private key.
Step 6: The CA secretly stores the system master private key (s) and publishes the system parameters () to all entities.
5.2. Registration Phase
Vehicles are required to register with the CA before entering the communication system. Only a successful registration will make a vehicle a legitimate user. The registration phase takes place over a secure communication channel, and the vehicle registration details are described below.
Step 1: Vehicles () with real identities () need to be registered by the CA. selects a random number () and calculates . Finally, sends to the CA over a secure channel.
Step 2: After receiving from , the CA selects a random number () and calculates . The CA then generates a private key () and public identity key () for and calculates the pseudonym (, where is the valid time of the pseudonym). Finally, the CA sends to over a secure channel and stores the corresponding in the local database.
Step 3: stores after receiving .
5.3. Route-Planning Phase
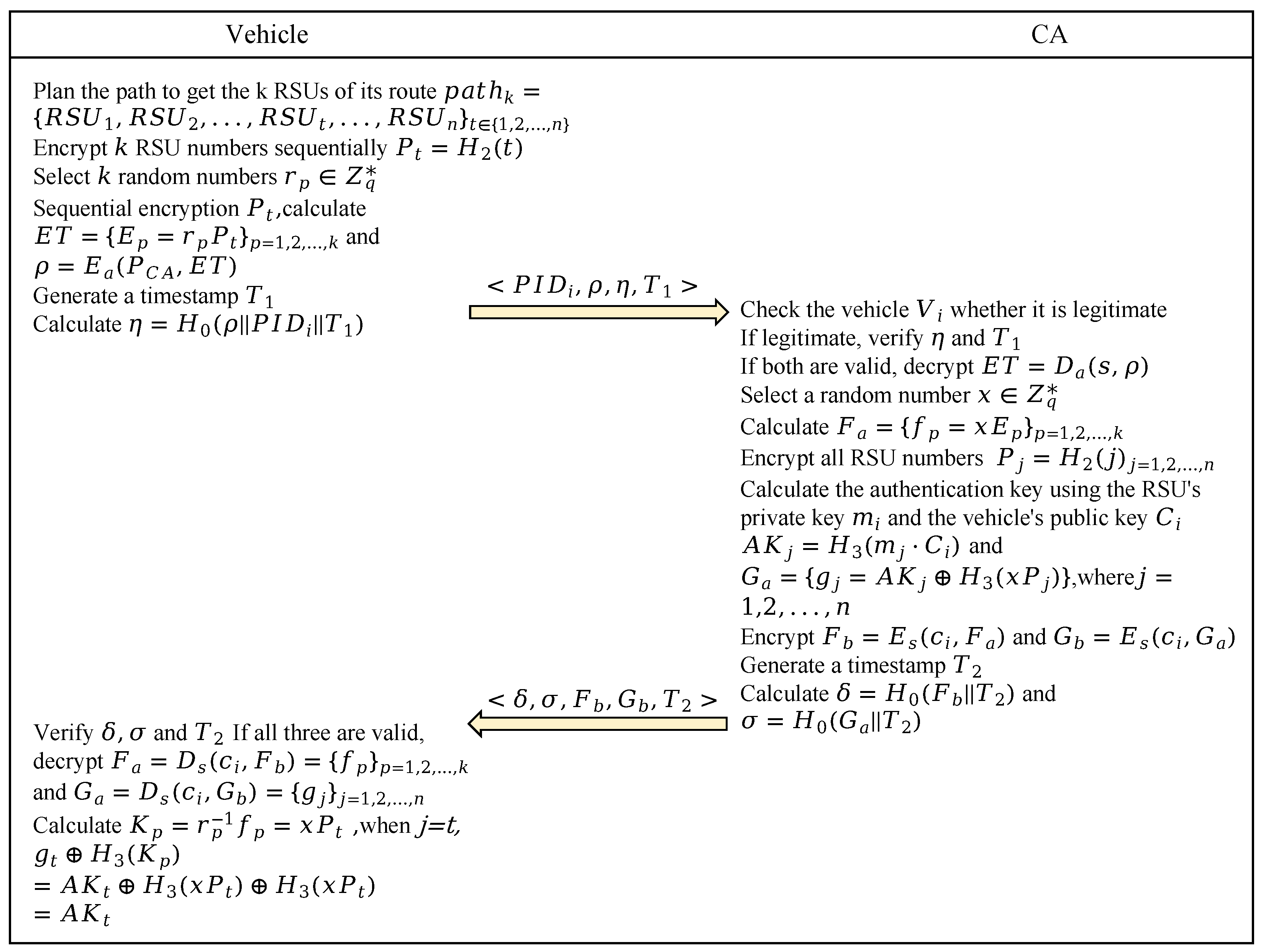
In this phase, the vehicle first plans its travel route to identify the RSUs that it will pass through. Then, the vehicle requests authentication information from the CA for these RSUs. In this way, the vehicle can quickly authenticate with the RSUs on the route while traveling. Finally, Figure 4 illustrates the interaction process of vehicle’s route planning.
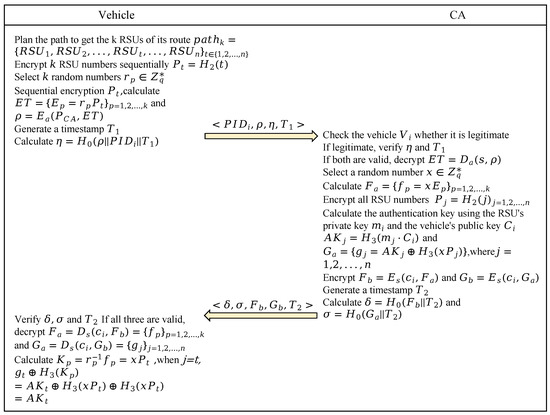
Figure 4.
The process of the route-planning phase.
Step 1: Before the trip starts, the vehicle () plans its path through the Dijkstra algorithm and obtains the RSUs it will pass through (). needs to obtain these k RSU private keys () corresponding to the authentication key ().
Step 2: encrypts the k RSU numbers in sequence to calculate . Then, selects k random numbers () and computes , obtaining , where . is then utilized to encrypt to compute .
Step 3: generates a timestamp and calculates . Finally, sends to the CA.
Step 4: After receiving , the CA first checks the validity of , then queries the pseudonym of to check the legitimacy of the vehicle identity. The message is accepted if both checks pass; otherwise, the message is rejected. Next, the CA verifies and accepts if the content () has not been tampered with; otherwise, it rejects .
Step 5: The CA decrypts to obtain using its own private key (s) to . The CA selects a random number () and calculates for the elements within . Then, it queries the vehicle’s public identity key () based on the of and uses to encrypt the private keys of all to obtain the corresponding authentication key. The specific calculations are , , and , where . Finally, the computed information is encrypted (,).
Step 6: The CA generates a timestamp () and calculates and . Finally, it sends to .
Step 7: After receiving , checks the validity of first, then calculates and . If both are valid, it accepts ; otherwise, it rejects .
Step 8: decrypts and by calculating and using private key . is then obtained by calculating . The specific calculations of and are shown in the following equations:
When :
5.4. V2I Authentication Phase
Since the vehicle has acquired the corresponding RSU authentication key on the path, when the vehicle () enters the communication range of , it and quickly complete the mutual authentication work. The steps for quick authentication of and are as follows:
Step 1: When the vehicle enters the communication range of , the vehicle selects a random number () and a timestamp () and calculates and . Finally, sends to .
Step 2: When receives , it first verifies the validity of the check message time (). If it is valid, then the subsequent validation continues; otherwise, the communication is rejected. Then, it verifies the validity of to . If is legitimate, then the corresponding is returned to ; otherwise, the vehicle pseudonym is broadcast as illegal. Finally, the correctness of is calculated. If the checksum passes, then is received; otherwise, is rejected.
Step 3: obtains by calculating . Then, it uses for decryption calculation () to obtain .
Step 4: calculates . Finally , sends to .
Step 5: receives and calculates . If , the authentication between and is successful; otherwise, the authentication fails.
6. Security Analysis
This section focuses on proving that our scheme is able to achieve the design goals presented in Section 4.3. The security of our scheme is compared with the schemes proposed in [29,30,31,32] in terms of confidentiality of RSU private keys, route privacy, traceability, unlinkability, and resistance to common security attacks. The analysis results show that our scheme provides more advantages. The comparison results are listed in Table 3, where × means that the scheme does not have the corresponding security requirements and √ means that the scheme has the corresponding security requirements.

Table 3.
Comparison results with respect to safety requirements.
- RSU private key confidentiality: In the route-planning phase, the CA combines the private key () and the public identity key () to generate the authentication key (), which is only applicable to the vehicle, then sends it to the vehicle. If the vehicle wants to derive from the known and , it needs to solve the unidirectionality problem of the one-way hash function first. However, the unidirectionality problem of the hash function is very difficult to overcome. Therefore, the confidentiality of can be guaranteed.
- Route privacy: In the route-planning phase, encrypts the information of the k RSU numbers that the planned path needs to pass through to calculate and , then send to the CA. If the CA wants to derive , then it needs to obtain the correspondence between and . If the CA wants to obtain the correspondence between and , it needs to solve the ECDLP problem of ECC to obtain . However, the CA is well within the hard probabilistic polynomial time to solve the ECDLP problem of ECC to obtain . In addition, if the CA wishes to derive the travel path of by calculating , it needs to solve the unidirectionality problem of the one-way hash function first. However, the unidirectionality problem of the one-way hash function is difficult to overcome. In summary, the CA cannot infer from ’s message which RSUs will pass through, and ’s route privacy is protected.
- Traceability: Although the real identity of a vehicle is hidden in a pseudonym, when an anonymous vehicle in the system sends a message that is disputed, the CA can calculate its real identity based on its pseudonym. Since and s are stored in the CA’s database, the CA can obtain the real identity of the vehicle by calculating . Therefore, traceability can be guaranteed.
- Unlinkability: In this scheme, each is created using a different random number (), each pseudonym is updated periodically, and the pseudonyms contained within each message are indistinguishable. Therefore, an attacker cannot link any two or more messages to a particular vehicle.
- Resistance to common security attacks: The scheme proposed in this paper is able to resist several common security attacks, such as Sybil attacks, modification attacks, replay attacks, and repudiation attacks. The proof details are shown below.
- –
- Sybil attacks: Since the pseudonym of the vehicle is generated by the CA through the vehicle’s real identity (), the system private key (s), and vehicle private key (), n attacker cannot obtain this information to generate a valid pseudonym. In addition, the attacker cannot know the rules for generating pseudonyms. Therefore, the attacker cannot utilize a pseudonym to realize a Sybil attack.
- –
- Modification attacks: We resist modification attacks using secondary encryption of the message through a hash function. For example, sends a request message as when it applies for the authentication key of an RSU from the CA. When the CA receives the message, it calculates , and if , it proves that the message has not been modified. Thus, our scheme is resistant to modification attacks.
- –
- Replay attacks: We include a timestamp () in both the message and the content of the communication to resist replay attacks. Each entity generates a timestamp () when it receives a message, and if , the message is fresh. denotes a fixed value set by the system. Therefore, the receiver of a message can detect a replay attack by verifying the timestamp contained in the message.
- –
- Repudiation attacks: When a vehicle wants to deny a message that has been sent, the CA can hold the vehicle responsible by calculating to obtain the real identity of the corresponding vehicle based on the pseudonym information in the message. Therefore, our scheme is capable of low resistance to repudiation attacks.
7. Performance Evaluation
This section focuses on the comparative analysis of the performance overhead of our scheme with the schemes proposed in [29,30,31,32]. The comparative analysis considers computational overhead, communication overhead, and packet loss rate. This is to demonstrate the performance advantages of our proposed scheme. Our comparison experiments were conducted on a laptop computer. The laptop consists of a Quad-Core Intel Core i5 processor with a clock frequency of 1.4 GHz, 16 GB of operating memory, and a macOS Catalina operating system.
7.1. Computational Overhead Comparison
In order to count the computational overhead of each scheme, we experimented with the time overhead of some major cryptographic operations. Each cryptographic operation was run 1000 times, and the average value was taken as the final time overhead. The time overhead statistics of the relevant cryptographic operations are described in Table 4.

Table 4.
Execution time of primary operations.
Since the registration phase is a one-time process, to be fair, only the computational overheads of the route-planning phase and the V2I authentication phase are compared. In the route-planning phase, the vehicle plans its traveling path in advance. Assuming that there are a total of n RSUs in the VANET, the vehicle’s planned path needs to pass through k RSUs. In our scheme, the computational overhead of the vehicle in the route-planning phase is , and the computational overhead required in the V2I authentication phase is . Therefore, the total computational overhead on the vehicle side is . The CA side only participates in computation during the route-planning phase; therefore, the total computational overhead of the CA is . The RSU side only participates in computation during the V2I authentication phase, so the total computational overhead of an RSU is . Ultimately, the total computational overhead of our proposed scheme is . The total computational overhead of several other related protocols for each entity was similarly analyzed and calculated using the same method, and the results are displayed in Table 5.

Table 5.
Computational overhead for each scheme.
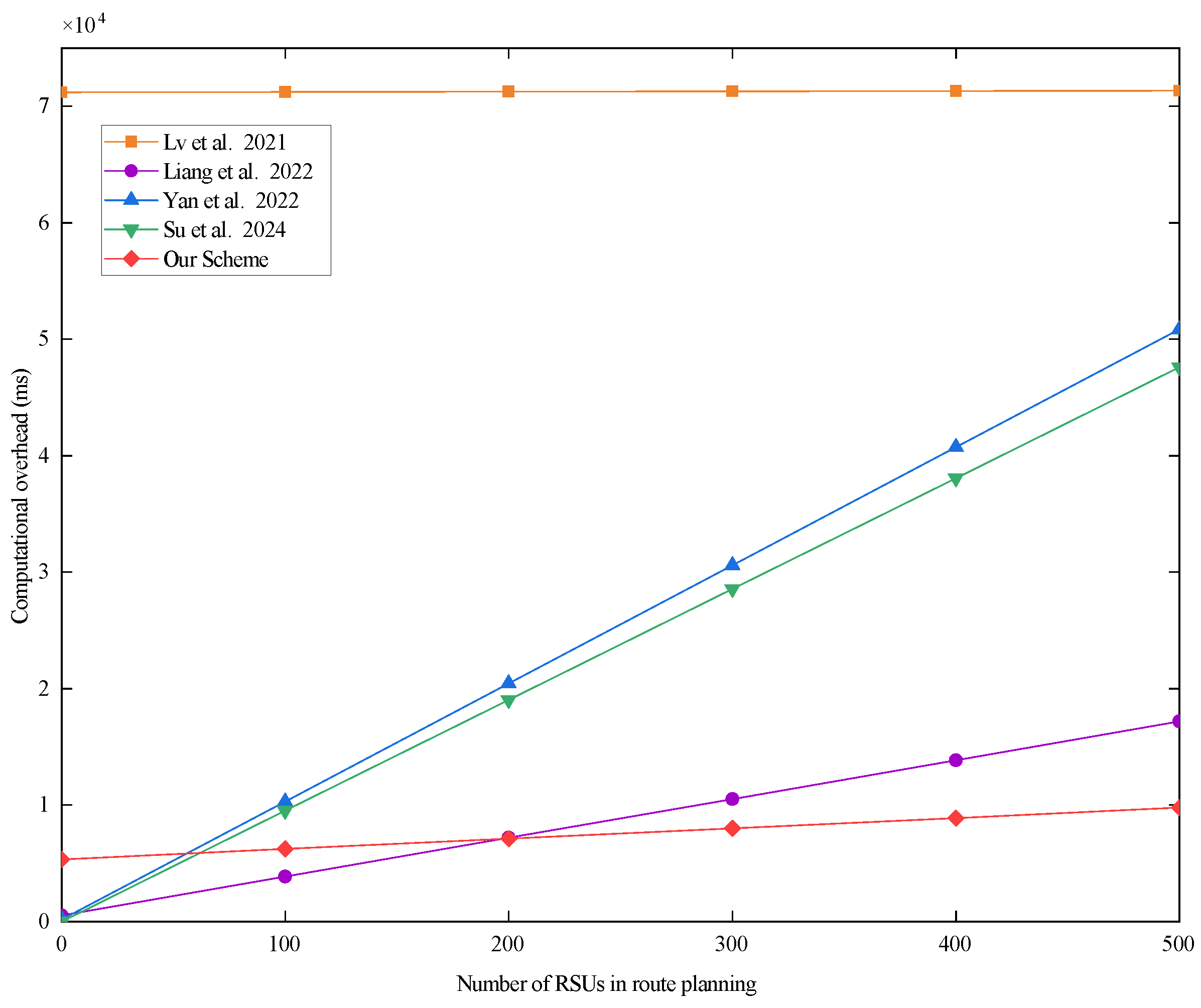
Since the computation time of the route-planning phase is mainly related to the number of RSUs, the number of RSUs in the system needs to be determined by the coverage of the system. We determined the range of our scheme based on the communication coverage method proposed by Gang et al. [35]. Take the city of Houston in the U.S. as an example. The area of Houston is about 1659.4 square kilometers [36]. The maximum communication distance of an RSU is 1 km, and the communication coverage area of an RSU is about 3.14 square kilometers. Approximately 500 RSUs are required to cover the entire city of Houston. Therefore, we take 500 RSUs in the system as an example to analyze the computational overhead corresponding to different protocols. The results of the analysis are shown in Figure 5 below.
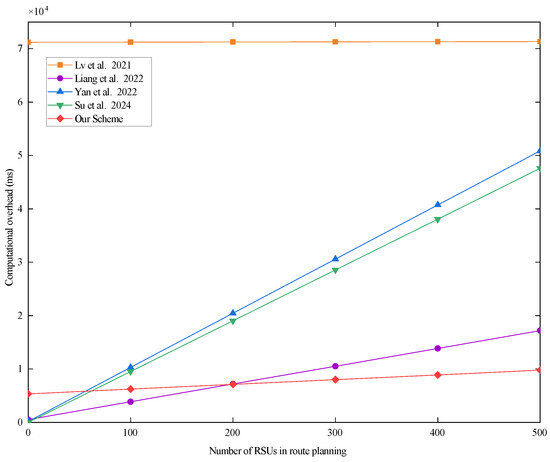
Figure 5.
The total computational overhead of each scheme when there are 500 RSUs in the system. Lv et al. proposed the scheme in [29], Liang et al. proposed the scheme in [30], Yan et al. proposed the scheme in [31], and Su et al. proposed the scheme in [32].
As can be seen in Figure 5, the computational overhead of the scheme proposed in [29] is high and appears to converge at a specific value. This is because the computational overhead of the scheme proposed in [29] is highly correlated with the number of RSUs in the system and less correlated with the number of RSUs for vehicle path planning. In the scheme proposed in [29], the vehicle marks the numbers of n RSUs in the system to determine the travel path and encrypts the marked n numbers and sends them to the CA. The CA performs n BGN homomorphic encryptions on the n RSU private keys in the system to return to the vehicle, and the vehicle obtains the required k RSU authentication key by decryption. Combined with the results in Table 5, it can be known that the computational overhead of the scheme proposed in [29] depends very much on the number of RSUs in the system (n), while the number of RSUs for vehicle path planning has less of an impact. Therefore, the computational overhead of the scheme proposed in [29] is high and appears to converge at a specific value.
The overall overhead of the scheme proposed in [30] is better than that of our proposed scheme when the number of RSUs in the path-planning phase is within 200. This is due to the fact that the CA of the scheme proposed in [30] returns an ciphertext matrix based on the number of RSUs in path planning (k), where n is the number of RSUs in the system. All the ciphertext elements inside the ciphertext matrix are encrypted by a one-way hash function and symmetric encryption algorithm. When n is determined, there is a strong correlation between the computational overhead of the ciphertext matrix and k. In our scheme, the CA returns a list of cipher texts of according to the number of RSUs in vehicle path planning k. When n is determined, the correlation between the computational overhead of the ciphertext list and k is smaller than that for the scheme proposed in [30]. The elements of the ciphertext list are encrypted by the a hash-to-map function and the symmetric encryption algorithm. From Table 4, it can be seen that the computational overhead of the hash-to-map function is higher than the computational overhead of the one-way hash function used in the scheme proposed in [30]. Therefore, when the number of RSUs in the system (n) is set to 500, with a smaller value of k, the computational overhead of the CA in the case reported in [30] is relatively smaller. In the scheme proposed in [31], the CA uses an exponentially correlated encryption algorithm for all RSU authentication keys. The overall computational overhead is highly correlated with both n and k. When n is determined, with a smaller k, the computational overhead is relatively reduced. The computational overhead of the scheme proposed in [32] follows the same principle as that of the scheme proposed in [31]. In short, our scheme uses a relatively time-consuming hash-to-map function to ensure the confidentiality of RSU private keys. However, our overall computational overhead is less correlated with the number of RSUs for path planning. Therefore, when the number of RSUs in the system is determined, with a smaller number of RSUs for path planning, the overall computational overhead of our scheme is relatively increased.
In summary, when the number of RSUs in vehicle path planning is small, our scheme’s computational overhead performs slightly worse than that of the schemes proposed in [30,31,32]. As the number of RSUs in vehicle path planning increases, the total computational overhead of the schemes proposed in [30,31,32] tends to increase linearly. The scheme proposed in [29] is in a relatively smooth state, but its total computational overhead is several times higher than that of the other schemes. Overall, the total computational overhead of our scheme is generally lower and grows most slowly. It also ensures the confidentiality of RSU private keys. Therefore, our scheme performs better than all compared schemes in terms of total computational overhead and security.
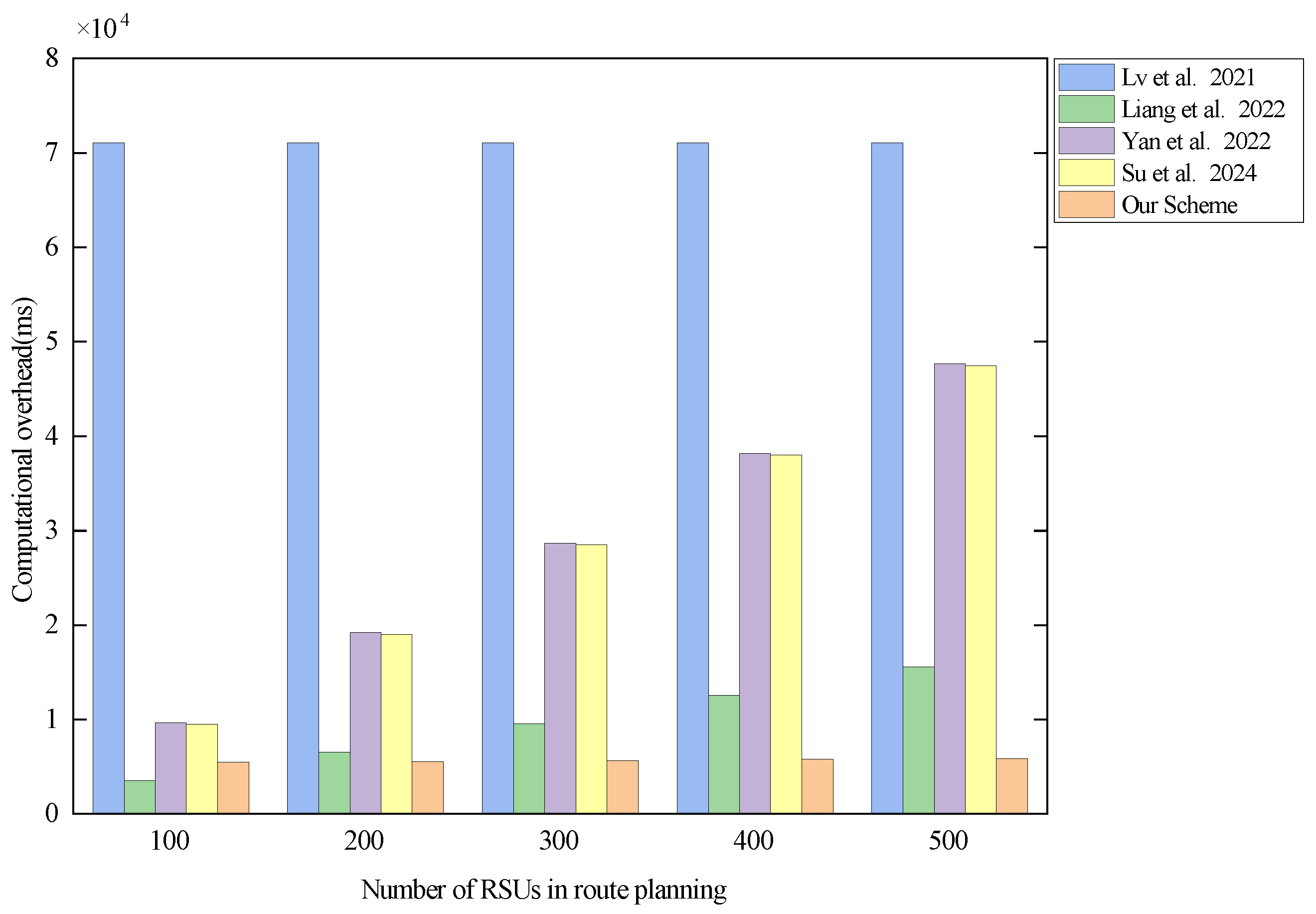
Since most of the computational overheads of the relevant schemes for path planning depend on the CA side, we analyzed the computational overhead relationship between different protocols from the perspective of the CA side. The results of the analysis are shown in Figure 6.
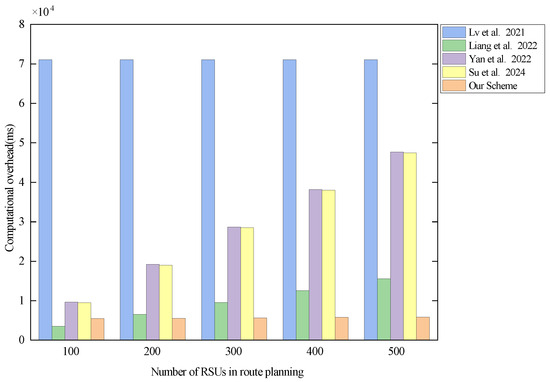
Figure 6.
Computational overhead of the CA in each scheme when there are 500 RSUs in the system. Lv et al. proposed the scheme in [29], Liang et al. proposed the scheme in [30], Yan et al. proposed the scheme in [31], and Su et al. proposed the scheme in [32].
In Figure 6, it can be seen that the CA’s computational overheads in the scheme proposed in [29] and our scheme do not float much. From Table 5, we can learn that the computational overhead on the CA side of our scheme is , n is the number of RSUs present in the system, and k is the number of RSUs in vehicle path planning. When there are 500 RSUs in the system, the number of RSUs in path planning is in the range of 100 to 500, corresponding to the computational overhead of the CA side in the range of ms to ms, which is a difference of ms. The performance of ms is not significant within the Y-axis range of 0 ms–80,000 ms in the statistical chart. Therefore, this is why Figure 6 appears to show the same value for all RSU numbers. The principle is similar in scheme [29]. The difference is that the scheme proposed in [29], uses BGN homomorphic encryption in encrypting the authentication keys of RSUs and encrypts the private keys of n RSUs n times. This leads to a large computational overhead required by the CA. The CA side of both the scheme proposed in [31] and the scheme proposed in [32] uses similar encryption operations and performs encryption operations on the authentication key of the RSU. Therefore, the CA’s computational overhead in the scheme proposed in [31] and the scheme proposed in [32] increases with the number of RSUs for path planning. Overall, the computational overhead on the CA side of the scheme proposed in [29] is much higher than that of other schemes, and the computational overhead on the CA side of the schemes proposed in [30,31,32] tends to increase. In our scheme, on the other hand, the computational overhead of the CA is the lowest and slowest-growing overall. Therefore, the CA’s computation overhead in our scheme performs better than that in all compared schemes.
7.2. Communication Overhead Comparison
In this section, we focus on analyzing the communication overhead in the route-planning phase and the V2I authentication phase. For security purposes, we constructed the bilinear pair cryptography algorithm and elliptic curve cryptography algorithm with a security level of 128 bits. First, a bilinear pair cryptography algorithm was constructed, and a group of order was set up (, which denotes the additive group generating elements of on the hyper-singular elliptic curve ()). Secondly, we constructed an elliptic curve cryptography algorithm, where the q order group (G) denotes the additive group that generates the element as P on a non-singular elliptic curve (). Then, the sizes of groups and G were bits and bits, respectively. For fairness, it is assumed that the length of the identity in all schemes is bits, the length of the random number is bits, the length of the hash value is bits, the length of the timestamp is bits, the length of the cipher text for AES encryption is bits, the ciphertext length of RSA encryption is bits, and the ciphertext length of ElGamal encryption is bits.
In the route-planning phase, it is assumed that there are a total of n RSUs in the VANET and that the route planned by the vehicle needs to pass through k RSUs. In this paper’s scheme, the message sent by the vehicle to the CA is , and the spent communication overhead is bits. The message sent by the CA to the vehicle is , and the spent communication overhead is bits. Therefore, the total communication overhead is bits. The total communication overheads of several other related protocols in the route-planning phase can be similarly analyzed. The specific results are displayed in Table 6.

Table 6.
Communication overhead in the route-planning phase.
In order to more intuitively observe the communication overhead of all protocols in the route-planning phase, according to the inference of 7.1, we also take the existence of 500 RSUs in the system as an example to analyze the relationship between the number of RSUs in path planning and the corresponding communication overhead of different protocols. The analysis results are shown in Figure 7.
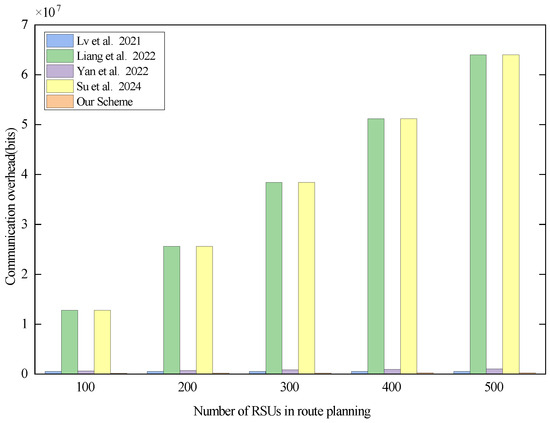
Figure 7.
Communication overhead of each scheme in the route-planning phase when there are 500 RSUs in the system. Lv et al. proposed the scheme in [29], Liang et al. proposed the scheme in [30], Yan et al. proposed the scheme in [31], and Su et al. proposed the scheme in [32].
From Figure 7, it can be seen that the total communication overhead of all the schemes increases linearly with the increase in the number of RSUs on the vehicle path. From Table 6, we can learn that in the route-planning phase, the communication overhead of the scheme proposed in [29] is (bits), where n is the number of RSUs in the system and k is the number of RSUs in vehicle path planning. The communication overhead of the scheme proposed in [30] is (bits), that of scheme [31] is (bits), and that of scheme [32] is (bits). It can be seen that the communication overhead of the scheme proposed in [29] is dependent on the number of RSUs present in the system but is not affected by the number of RSUs in path planning, whereas the communication overhead of the schemes proposed in [30,31,32] is not only affected by the number of RSUs in the system but also by the number of RSUs in path planning. The communication overhead of the schemes proposed in [30,32] is significantly higher than that in the other schemes due to the fact that the CA side of the schemes proposed in [30,32] returns the authentication key of the RSU to the vehicle in the form of an ciphertext matrix. Our scheme is also affected by the number of RSUs in the system and the number of RSUs in path planning. However, in our scheme, the CA utilizes AES symmetric encryption of the RSU’s authentication key. According to the definition of ciphertext size in this section, the ciphertext size after AES symmetric encryption is 256 bits, and the CA returns the authentication key of the RSU to the vehicle in the form of , which greatly reduces the communication burden of the CA. Although the CA side of the scheme proposed in [31] also returns the authentication key of the RSU to the vehicle in the form of , they use the ELG encryption algorithm with a ciphertext size of 1024 bits. Therefore, the communication overhead of scheme [31] is higher than that of our scheme. In summary, our scheme has a significant advantage in terms of communication overhead in the route-planning phase.
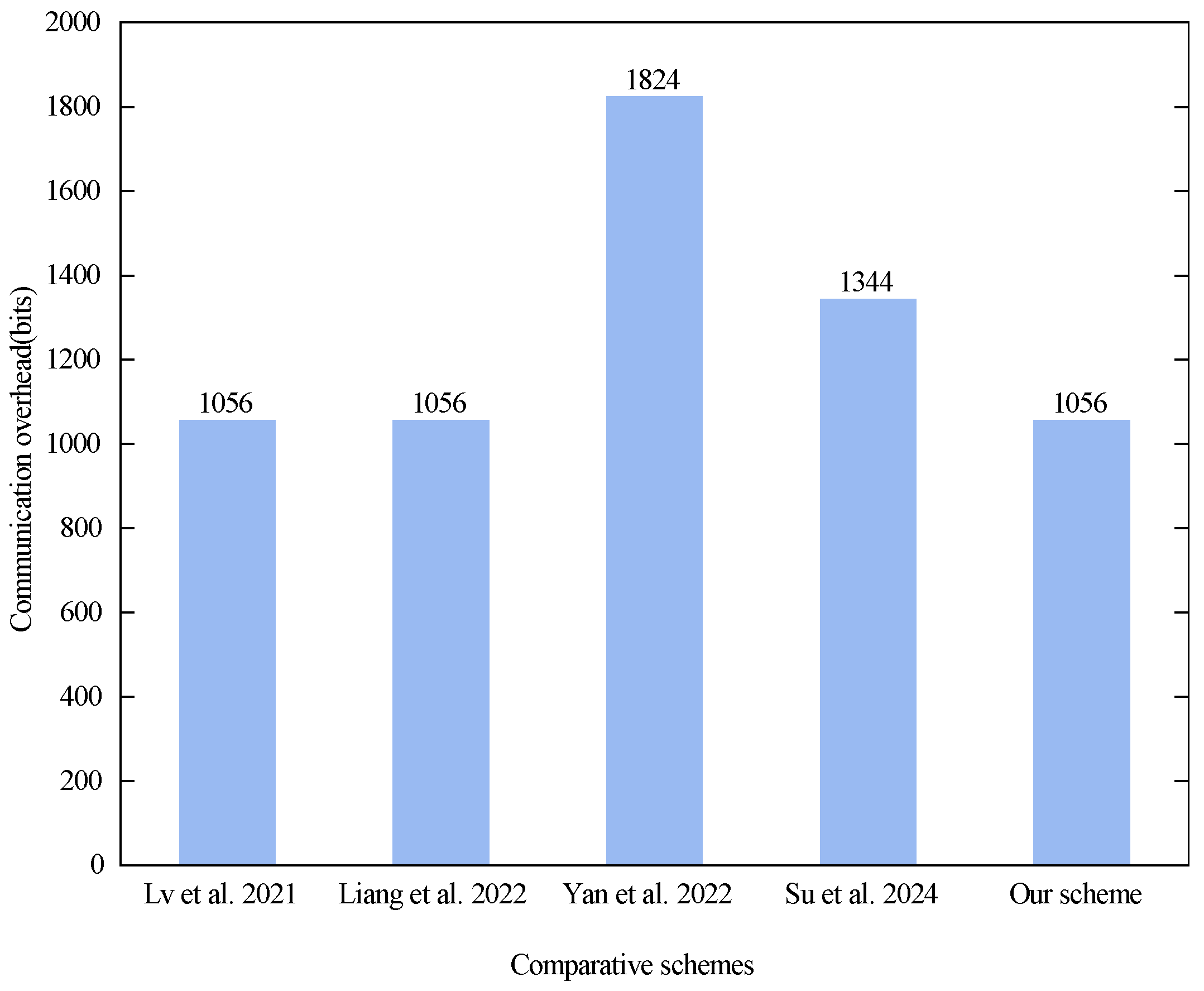
In the V2I authentication phase, the messages to be communicated by the scheme proposed in [29] are , H(E), , and , and the expended communication overhead is bits. The messages to be communicated in scheme [30] are and , and the spent communication overhead is bits. The messages to be communicated in the scheme proposed in [31] are and , and the expended communication overhead is bits. The messages that need to be communicated in scheme [32] are , , and , and the spent communication overhead is bits. The messages to be communicated in our scheme are and , and the spent communication overhead is bits. Finally Figure 8 shows a comparison of the communication overhead of the V2I authentication phase between the different schemes.
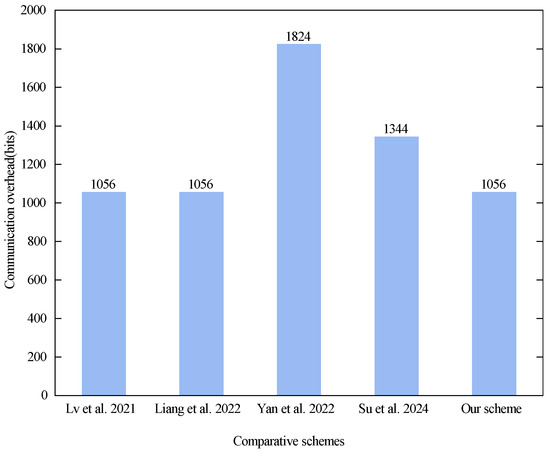
Figure 8.
Communication overhead in the V2I authentication phase. Lv et al. proposed the scheme in [29], Liang et al. proposed the scheme in [30], Yan et al. proposed the scheme in [31], and Su et al. proposed the scheme in [32].
As can be seen in Figure 8, the communication overhead in the V2I authentication phase is the same for the schemes proposed in [29,30] and our scheme. This is due to the fact that the communication messages between the vehicle and the RSUs all use similar encryption methods, and the communication content is of the same size. For example, the schemes proposed in [29,30] and our scheme all utilize the RSUs’ authentication keys to symmetrically encrypt the authentication content, then utilize a hash function for secondary encryption to ensure the reliability of the message. According to the definition of ciphertext size in this section, the size of the ciphertext of the request authentication content sent by the vehicle to the RSU is 256 bits, the size of the secondary encryption of the requested authentication ciphertextis 256 bits, the size of the pseudonym is 256 bits, and the size of the timestamp is 32 bits. The size of the ciphertext authentication content returned by the RSU to the vehicle is 256 bits. The communication overheads of the scheme proposed in [29], the scheme proposed in [29], and our scheme are all bits. Therefore, we have the same communication overhead in the V2I authentication phase. But scheme [31] adds a public key with a length of 512 bits on the basis of the above to ensure the legitimacy of the message. At the same time, the RSU returns a message to the vehicle with 256 bits of additional RSU information. Therefore, the communication overhead of the scheme proposed in [31] is bits. This shows that the evaluation performance of the scheme proposed in [31] lags behind the other schemes. In this regard, our scheme also maintains good performance in terms of communication overhead in the V2I authentication phase.
7.3. Packet Loss Rate Evaluation
In order to analyze the network availability of each scheme in the V2I authentication phase, we conducted simulation experiments on the data packet loss rate (PLR). Our simulation environment was configured according to the real test scheme for the data packet loss rate proposed by Fan et al. [37]. The simulation experiment environment consists of OMNET++ 5.6.2, SUMO 1.8.0, and Veins 5.2. The main parameters of the simulation environment are shown in Table 7 below. The map and all roads in the simulation experiment use the default settings of SUMO.

Table 7.
Parameter configuration of the simulation.
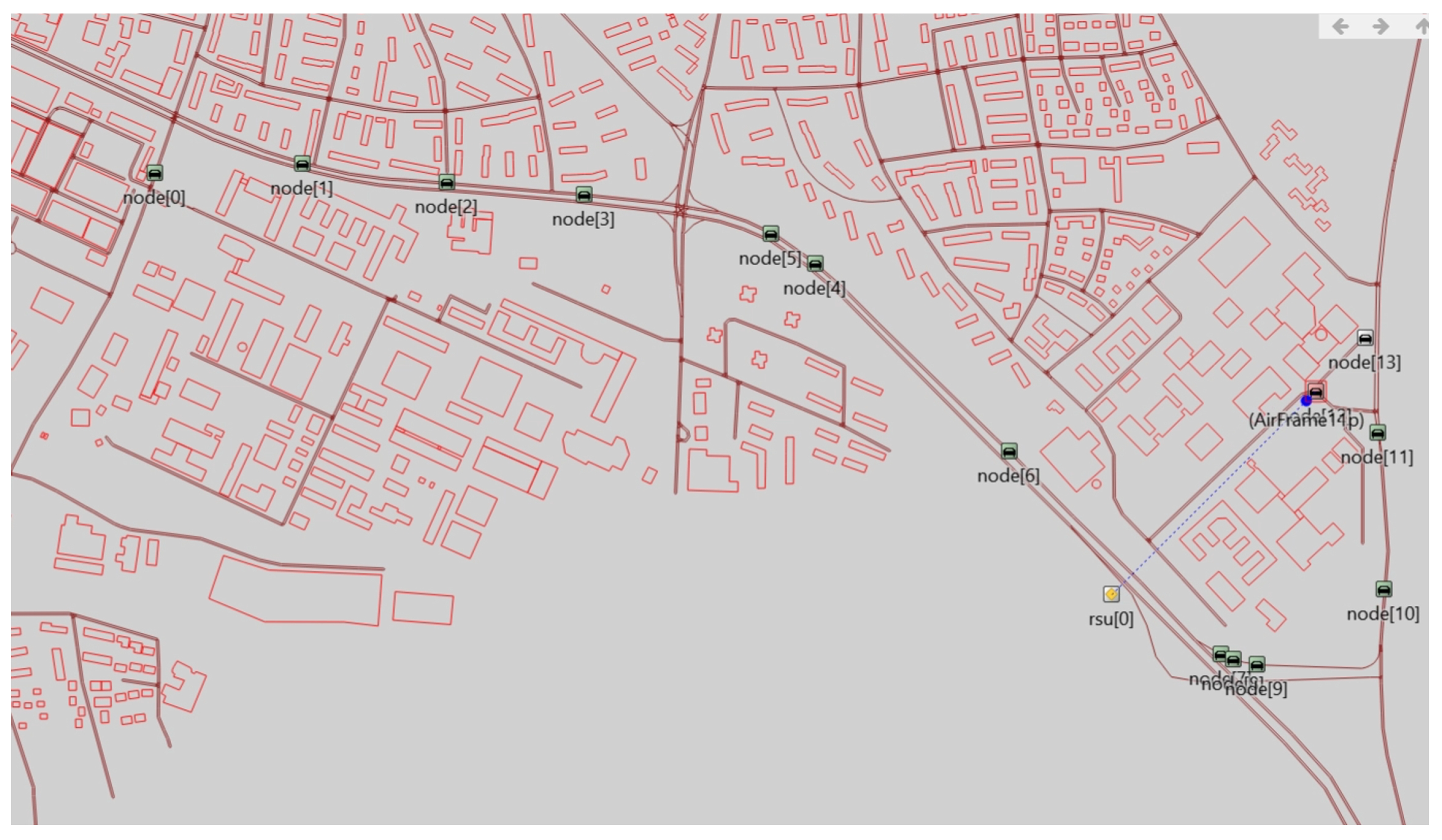
Figure 9 shows the simulation process of our scheme. From Figure 9, we can visualize the interaction process between the vehicle and RSU for authentication in the V2I authentication phase. The nodes in the figure represent traveling vehicles, and rsu[0] represents the RSU. In addition, green nodes represent vehicle that have completed mutual authentication with the RSU, the white node represents a vehicle that has not yet completed mutual authentication with the RSU, and the red node represents that a vehicle in the process of mutual authentication with the RSU. The blue dotted line indicates that the vehicle and RSU are interacting with each other.
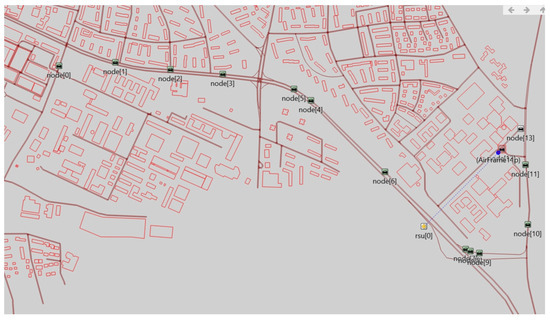
Figure 9.
Simulation process of the V2I authentication phase.
We define the formula for calculating the average packet loss rate according to the calculation of the average packet loss rate of the scheme proposed in [32]. The formula for calculating the packet loss rate is shown in Equation (3) below.
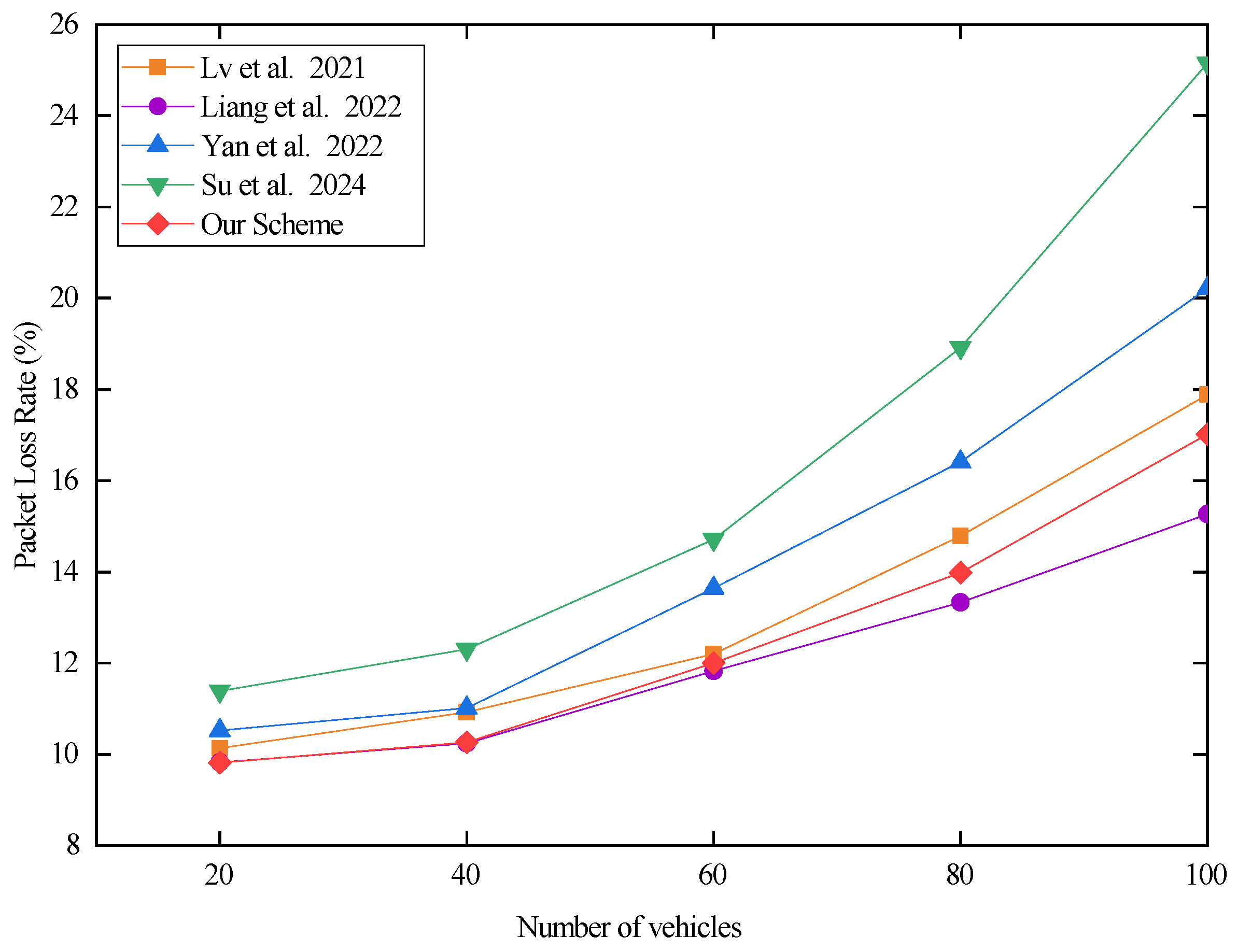
In Equation (3), denotes the packet loss rate, denotes the total number of lost packets, and denotes the total number of accepted packets. According to the formula for the packet loss rate, we obtain the experimental results as shown in Figure 10 below.
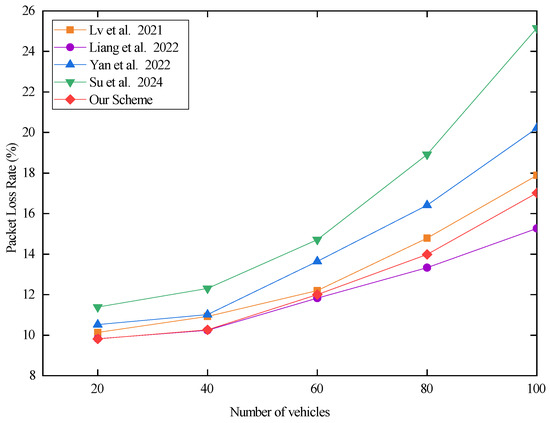
Figure 10.
The packet loss rate for different traffic volumes in the V2I authentication phase. Lv et al. proposed the scheme in [29], Liang et al. proposed the scheme in [30], Yan et al. proposed the scheme in [31], and Su et al. proposed the scheme in [32].
From Figure 10, we notice that the scheme proposed in [32] has the highest data packet loss rate. This is due to the fact a vehicle needs to send a security message with a length of 544 bits to the surrounding vehicles when it enters the range of the RSU. Then, the vehicle sends a request authentication message with a length of 544 bits to the RSU. The RSU confirms that the vehicle’s authentication message is correct, then returns 256 bit authentication content to the vehicle. Therefore, the scheme proposed in [32] requires frequent communication interactions, and the communication overhead of interaction is large, which leads to the phenomenon of a high packet loss rate in the scheme proposed in [32]. Compared with the scheme proposed in [32], the amount of communication data of the scheme proposed [31] is higher than that of the scheme proposed in [32]. However, the vehicles of this scheme do not need to send security messages to the surrounding vehicles, and the interaction frequency of information is lower than that of the scheme proposed in [32]. Therefore, the packet loss rate of the scheme proposed in [31] is lower than that of the scheme proposed in [32]. The communication data sizes of the scheme proposed in [29], the scheme proposed in [29], and our scheme are all 1056 bits. The authentication process of the scheme proposed in [30] is performed once for both vehicle and RSU encryption. Therefore, the overall response time is low, and the packet loss rate is small. The RSU side of our scheme needs to additionally calculate to obtain the authentication key, then perform decryption to obtain the vehicle’s authentication message using . Therefore, the overall delay and packet loss rate of our scheme is high compared to that of the scheme proposed in [30]. In the scheme proposed in [29], the vehicle not only needs to additionally compute the temporary pseudonym, but the RSU also needs to additionally compute the RSU beacon provided by the vehicle. Therefore, the delay and packet loss rate of the scheme proposed in [29] is higher than that of our scheme. To summarize, in the V2I authentication process, the scheme proposed in [29] has a higher delay and packet loss rate than the scheme proposed in [30] and our scheme.
8. Conclusions and Discussion
Currently, most of the V2I fast authentication protocols in VANETs suffer from RSU private key leakage and route privacy problems. To solve the above problems, we propose a privacy-preserving V2I fast authentication scheme in VANETs. The scheme achieves the protection of RSU private keys and route privacy through the use of an improved OT algorithm. The CA cannot obtain the vehicle’s travel path by analyzing the vehicle’s request information, and the vehicle’s route privacy is guaranteed. Meanwhile, even if the vehicle leaks the RSU authentication key, we can still guarantee the security of the RSU private key. In addition, security analysis proves that the scheme is able to guarantee the confidentiality of the RSU private key, the route privacy of the vehicle, the traceability of the vehicle, the unlinkability of the message, and resistance to common security attacks. Finally, the scheme outperforms other related schemes in terms of communication overhead and computational overhead.
Our current scheme treats the RSU as a fully trusted entity in the authentication process of V2I, and the RSU is able to retain information such as the current location and time of the vehicle when the vehicle and the RSU are authenticated. In addition, it has not been investigated how dynamic allocation of system resources can be achieved in the presence of large volumes of traffic. In future work, we will focus on how to perform secure authentication when the RSU is regarded as a not fully trusted entity. We will also investigate how artificial intelligence and machine learning can be utilized to dynamically adjust the allocation of system resources in the presence of varying vehicle traffic, in addition to designing more secure and efficient authentication protocols.
Author Contributions
Conceptualization, Y.G. and Y.L.; methodology, Y.G.; software, Y.G.; validation, X.X. and Y.L.; formal analysis, Y.L.; investigation, Y.G.; resources, X.X. and Y.L.; data curation, Y.G.; writing—original draft preparation, Y.G.; writing—review and editing, Y.L.; visualization, Y.G.; supervision, X.X. and Y.L.; project administration, X.X.; funding acquisition, X.X. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Guangxi key research and development program (grant number Guike AB23026004), the Guangxi key research and development program (grant number Guike AA23062001), and the National Natural Science Foundation of China (grant number 62262011).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The anonymized data used in this study are available upon request from the corresponding author.
Acknowledgments
We thank the anonymous reviewers for their comments and suggestions.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Zhang, H.; Lu, X. Vehicle communication network in intelligent transportation system based on Internet of Things. Comput. Commun. 2020, 160, 799–806. [Google Scholar] [CrossRef]
- Al-shareeda, M.A.; Alazzawi, M.A.; Anbar, M.; Manickam, S.; Al-Ani, A.K. A comprehensive survey on vehicular ad hoc networks (vanets). In Proceedings of the 2021 International Conference on Advanced Computer Applications (ACA), Maysan, Iraq, 25–26 July 2021; pp. 156–160. [Google Scholar]
- Chen, J.; Wang, Z.; Srivastava, G.; Alghamdi, T.A.; Khan, F.; Kumari, S.; Xiong, H. Industrial blockchain threshold signatures in federated learning for unified space-air-ground-sea model training. J. Ind. Inf. Integr. 2024, 39, 10593. [Google Scholar] [CrossRef]
- Ahmed, W.; Di, W.; Mukathe, D. Privacy-preserving blockchain-based authentication and trust management in VANETs. IET Netw. 2022, 11, 89–111. [Google Scholar] [CrossRef]
- Khan, A.R.; Jamlos, M.F.; Osman, N.; Ishak, M.I.; Dzaharudin, F.; Yeow, Y.K.; Khairi, K.A. DSRC technology in Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) IoT system for Intelligent Transportation System (ITS): A review. In Recent Trends in Mechatronics Towards Industry 4.0; Selected Articles from iM3F; Springer: Berlin/Heidelberg, Germany, 2020; pp. 97–106. [Google Scholar]
- Kenney, J.B. Dedicated short-range communications (DSRC) standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Abboud, K.; Omar, H.A.; Zhuang, W. Interworking of DSRC and cellular network technologies for V2X communications: A survey. IEEE Trans. Veh. Technol. 2016, 65, 9457–9470. [Google Scholar] [CrossRef]
- Xiong, H.; Chen, J.; Mei, Q.; Zhao, Y. Conditional privacy-preserving authentication protocol with dynamic membership updating for VANETs. IEEE Trans. Dependable Secur. Comput. 2020, 10, 2089–2104. [Google Scholar] [CrossRef]
- Yu, H.; Liu, R.; Li, Z.; Ren, Y.; Jiang, H. An RSU deployment strategy based on traffic demand in vehicular ad hoc networks (VANETs). IEEE Internet Things J. 2021, 9, 6496–6505. [Google Scholar] [CrossRef]
- Ahmad, A.; Din, S.; Paul, A.; Jeon, G.; Aloqaily, M.; Ahmad, M. Real-time route planning and data dissemination for urban scenarios using the Internet of Things. IEEE Wirel. Commun. 2019, 26, 50–55. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Jegatha Deborah, L. Comprehensive survey on security services in vehicular ad-hoc networks. IET Intell. Transp. Syst. 2016, 10, 379–388. [Google Scholar] [CrossRef]
- Mansour, M.B.; Salama, C.; Mohamed, H.K.; Hammad, S.A. VANET security and privacy-an overview. IJNSA 2018, 10, 13–34. [Google Scholar] [CrossRef]
- Malhi, A.K.; Batra, S.; Pannu, H.S. Security of vehicular ad-hoc networks: A comprehensive survey. Comput. Secur. 2020, 89, 101664. [Google Scholar] [CrossRef]
- Rao, B.T.; Patibandla, R.L.; Narayana, V.L. Comparative study on security and privacy issues in VANETs. Cloud IoT-Based Veh. Ad Hoc Netw. 2021, 145–162. [Google Scholar] [CrossRef]
- Rajeswari, R.M.; Rajesh, S. Enhance security and privacy in VANET based sensor monitoring and emergency services. Cybern. Syst. 2024, 55, 872–893. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. Secure authentication and key management with blockchain in VANETs. IEEE Access 2019, 8, 2482–2498. [Google Scholar] [CrossRef]
- Ma, Z.; Zhang, J.; Guo, Y.; Liu, Y.; Liu, X.; He, W. An efficient decentralized key management mechanism for VANET with blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5836–5849. [Google Scholar] [CrossRef]
- Xu, G.; Li, X.; Jiao, L.; Wang, W.; Liu, A.; Su, C.; Zheng, X.; Liu, S.; Cheng, X. BAGKD: A batch authentication and group key distribution protocol for VANETs. IEEE Commun. Mag. 2020, 58, 35–41. [Google Scholar] [CrossRef]
- Mansour, A.; Malik, K.M.; Alkaff, A.; Kanaan, H. ALMS: Asymmetric lightweight centralized group key management protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2020, 22, 1663–1678. [Google Scholar] [CrossRef]
- Li, X.; Liu, J.; Obaidat, M.S.; Vijayakumar, P.; Jiang, Q.; Amin, R. An unlinkable authenticated key agreement with collusion resistant for VANETs. IEEE Trans. Veh. Technol. 2021, 70, 7992–8006. [Google Scholar] [CrossRef]
- Li, X.; Shang, S.; Liu, S.; Gu, K.; Jan, M.A.; Zhang, X.; Khan, F. An identity-based data integrity auditing scheme for cloud-based maritime transportation systems. IEEE Trans. Intell. Transp. Syst. 2022, 24, 2556–2567. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Zhong, H.; Xu, Y.; Liu, L. Proven secure tree-based authenticated key agreement for securing V2V and V2I communications in VANETs. IEEE Trans. Mob. Comput. 2021, 21, 3280–3297. [Google Scholar] [CrossRef]
- Yang, Q.; Zhu, X.; Wang, X.; Fu, J.; Zheng, J.; Liu, Y. A novel authentication and key agreement scheme for Internet of Vehicles. Future Gener. Comput. Syst. 2023, 145, 415–428. [Google Scholar] [CrossRef]
- Manvi, S.S.; Tangade, S. A survey on authentication schemes in VANETs for secured communication. Veh. Commun. 2017, 9, 19–30. [Google Scholar] [CrossRef]
- Sampigethaya, K.; Huang, L.; Li, M.; Poovendran, R.; Matsuura, K.; Sezaki, K. CARAVAN: Providing Location Privacy for VANET; Technical Report; Department of Electrical Engineering, Washington University: Seattle, WA, USA, 2005. [Google Scholar]
- Zhu, H.; Liu, T.; Wei, G.; Li, H. PPAS: Privacy protection authentication scheme for VANET. Clust. Comput. 2013, 16, 873–886. [Google Scholar] [CrossRef]
- Cui, J.; Xu, W.; Sha, K.; Zhong, H. An efficient identity-based privacy-preserving authentication scheme for vanets. In Proceedings of the 13th International Conference, Edinburgh, UK, 11–13 December 2017; pp. 508–518. [Google Scholar]
- Wahid, A.; Yasmeen, H.; Shah, M.A.; Alam, M.; Shah, S.C. Holistic approach for coupling privacy with safety in VANETs. Comput. Netw. 2019, 148, 214–230. [Google Scholar] [CrossRef]
- Lv, S.; Liu, Y. PLVA: Privacy-preserving and lightweight V2I authentication protocol. IEEE Trans. Intell. Transp. Syst. 2021, 23, 6633–6639. [Google Scholar] [CrossRef]
- Liang, Y.; Liu, Y.; Gupta, B.B. PPRP: Preserving-privacy route planning scheme in VANETs. ACM Trans. Internet Technol. 2022, 22, 1–18. [Google Scholar] [CrossRef]
- Yan, Z.; Zhang, J. Path Privacy-Preserving Scheme Based on Oblivious Transfer Protocol. In Proceedings of the 2022 10th International Conference on Intelligent Computing and Wireless Optical Communications (ICWOC), Chongqing, China, 10–12 June 2022; pp. 6–10. [Google Scholar]
- Su, H.; Dong, S.; Wang, N.; Zhang, T. An efficient privacy-preserving authentication scheme that mitigates TA dependency in VANETs. Veh. Commun. 2024, 45, 100727. [Google Scholar] [CrossRef]
- Rabin, M.O. How To Exchange Secrets with Oblivious Transfer. IACR Cryptol. ePrint Arch. 2005, 187. [Google Scholar]
- Chu, C.-K.; Tzeng, W.-G. Efficient k-out-of-n Oblivious Transfer Schemes with Adaptive and Non-adaptive Queries. In Public Key Cryptography—PKC 2005; Springer: Berlin/Heidelberg, Germeny, 2005; Volume 3386. [Google Scholar]
- Sun, G.; Yu, M.; Liao, D.; Chang, V. Analytical exploration of energy savings for parked vehicles to enhance VANET connectivity. IEEE Trans. Intell. Transp. Syst. 2018, 5, 1749–1761. [Google Scholar] [CrossRef]
- Houston City, Texas—Census Bureau Profiles Results. Available online: https://data.census.gov/profile?q=Houston%20city,%20Texas&g=160XX00US4835000 (accessed on 1 April 2024).
- Fan, F.; Liu, L.; Dong, S.; Zhuang, L.; Qiu, J.; Cai, C.; Song, M. Network Performance Test and Analysis of LTE-V2X in Industrial Park Scenario. Wirel. Commun. Mob. Comput. 2020, 2020, 8849610. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).