Ensuring Cross-Chain Transmission Technique Utilizing TPM and Establishing Cross-Trusted Root Security via SM Algorithm
Abstract
1. Introduction
2. Related Work
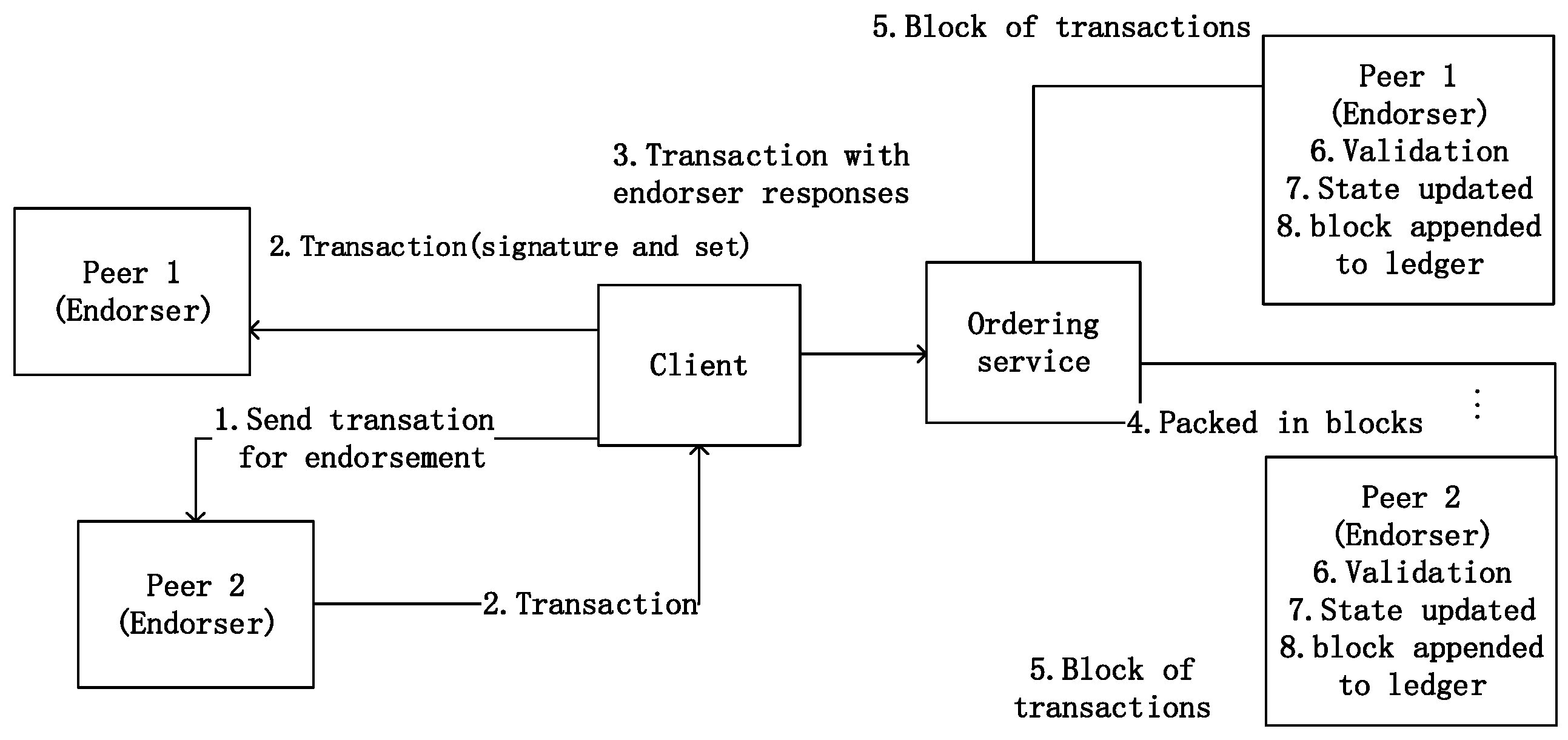
2.1. Hyperledger Fabric
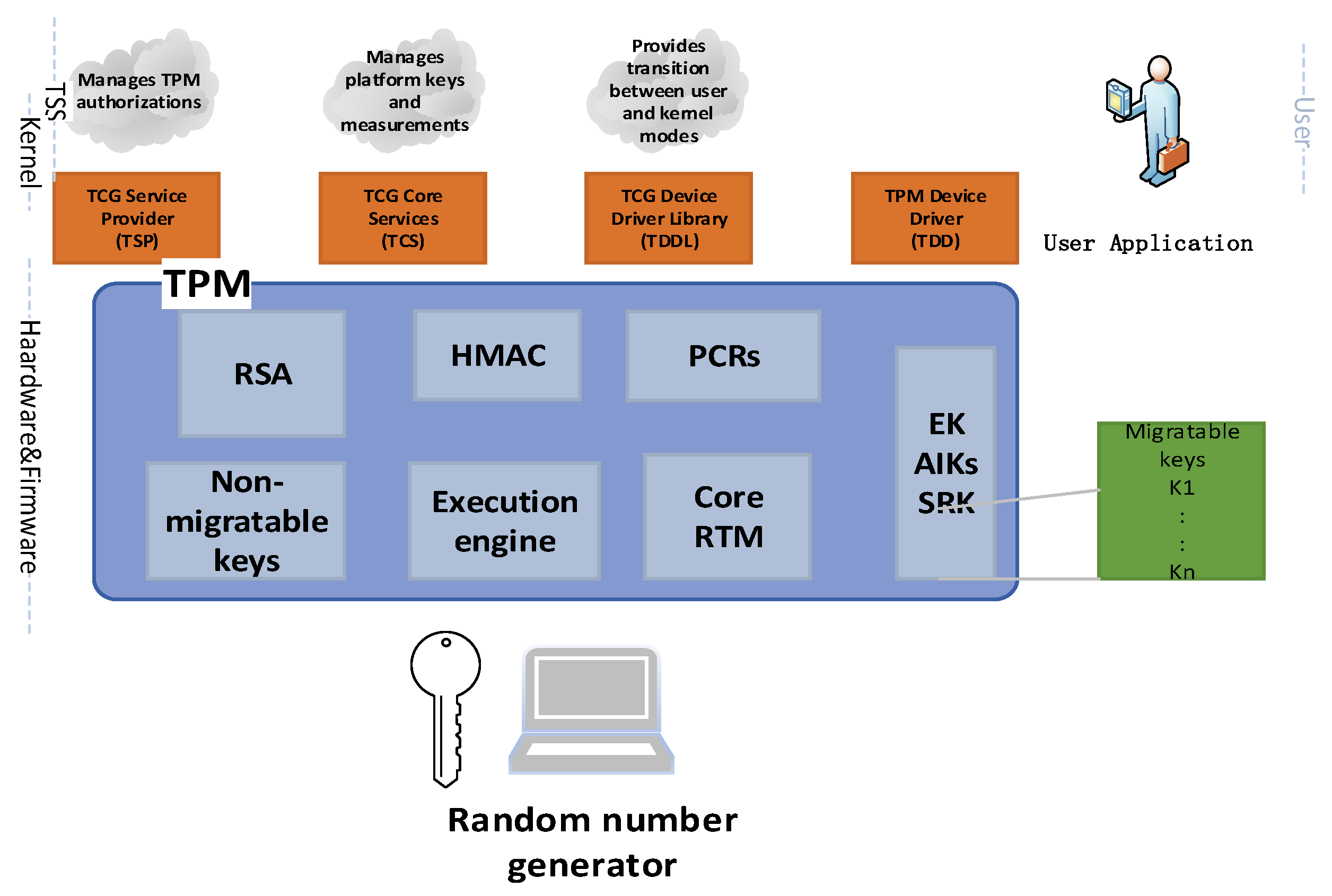
2.2. Trusted Platform Module (TPM)
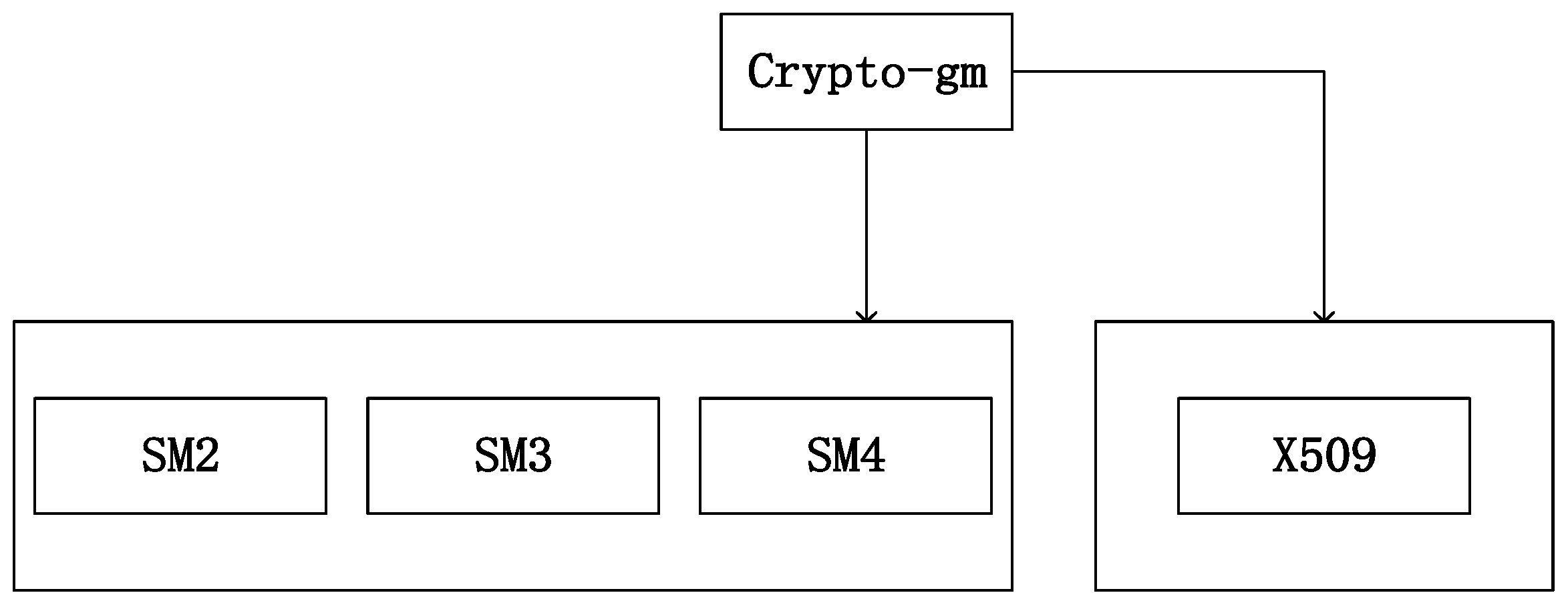
2.3. SM Cryptographic Algorithm
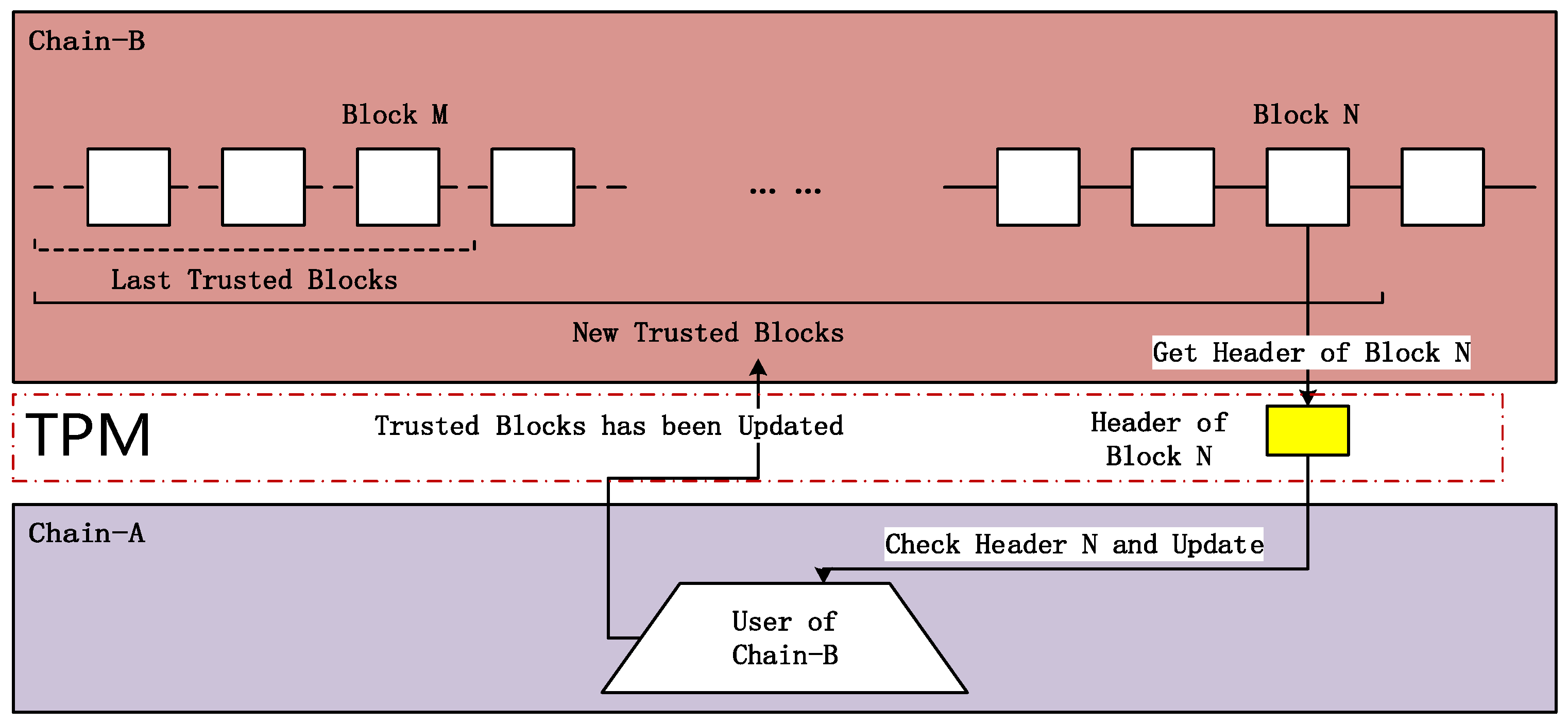
3. The Model
3.1. Model Analysis
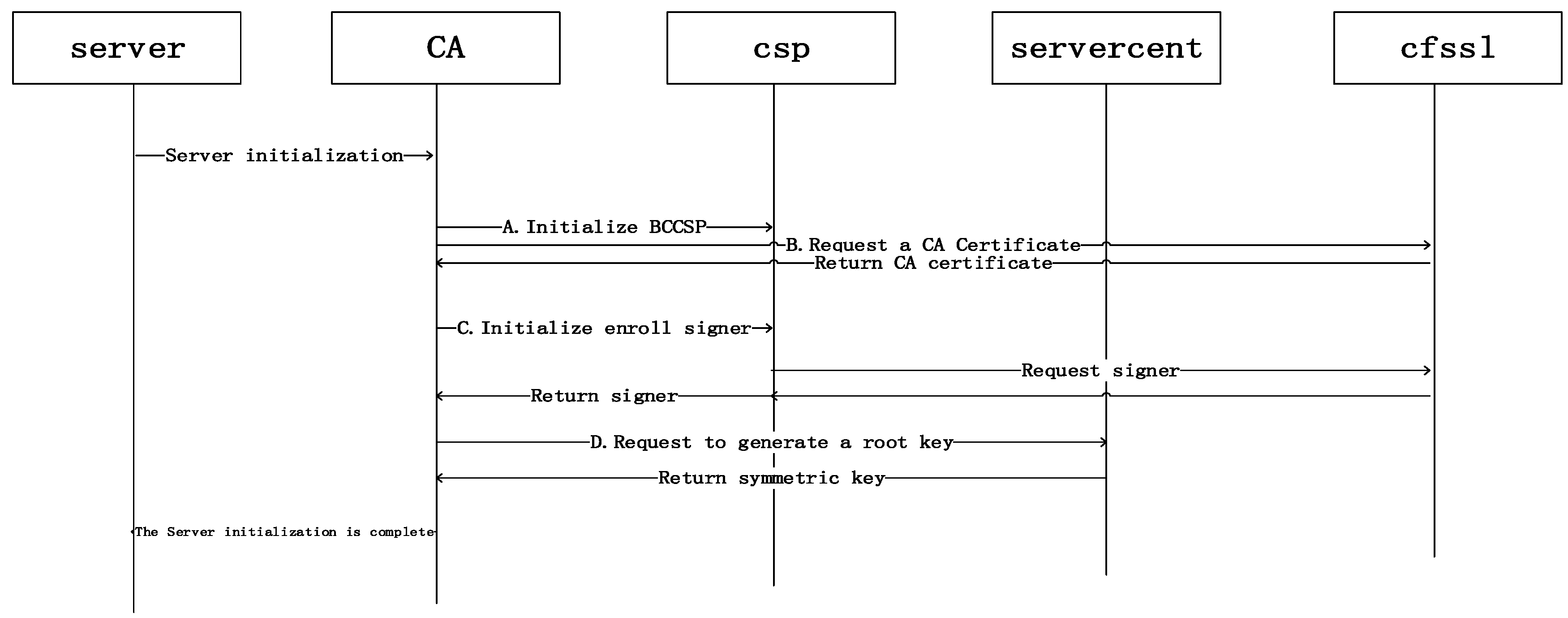
Simulated Use of TPM to Protect Hyperledger Fabric Transmission Model
| Algorithm 1. Initialize transaction parties |
| 1: function Initialized 2: (G1, G2) ← GenerateKeys() 3: (G1, G2) ← GenerateAccount() ∆Generate account and other related information 4: sealedState ← Seal(G1, G2) 5: return (sealedState, G1, G2) 6: end function |
- Sub
| Algorithm 2. Using TPM to protect Hyperledger Fabric transaction transfer protection asset |
| 1: contract Hyperledger Fabric1 extends Hyperledger Fabric hub1, 2 2: Initialized ← false; ctr ← 0 3: function Initialize(G2, Hyperledger Fabric2) 4: if ¬Initialized then 5: crosschain.Initialized(G2) ∆Initialize genesis block 6: Initialized ← true 7: this.Hyperledger Fabric2 ← Hyperledger Fabric2 8: end if 9: end function 10: payable function deposit(target) 11: Emit an event to generate related transactions 12: ctr += 1 13: emit Deposited1(target, msg.value, ctr) 14: emit TPM1(target, msg.value, ctr) ∆Transfer to TPM1 for transmission assurance 15: protected ← TPM1 16: end function 17: end contract |
| Algorithm 3. Protecting transaction security |
| 1: contract Hyperledger Fabric2 extends Hyperledger Fabric hub1, 2; ARC20 2: mapping(address int) balances 3: Initialized ← false; ctr ← 0 4: function Initialize(G1, Hyperledger Fabric1) 5: if ¬Initialize then 6: crosschain.Initialize(G1) 7: Initialized ← true 8: this.Hyperledger Fabric1 ← Hyperledger Fabric1 9: end if 10: end function 11: function deposit(target, amount) 12: if balances[msg.sender] < amount then 13: emit TPM2 (target, msg.value, ctr) ∆Transfer to TPM2 for transmission assurance 14: protected ← TPM2 15: return 16: end if 17: balances[msg.sender] −= amount ∆Charge account of sender 18: ctr += 1 19: emit Deposited2(target, amount, ctr) 20: end function 21: balances[target] += amount ∆Credit target account 22: end contract |
4. Security Proof
- Initialization phase:
- Query phase:
- Forgery phase:
5. Experiment
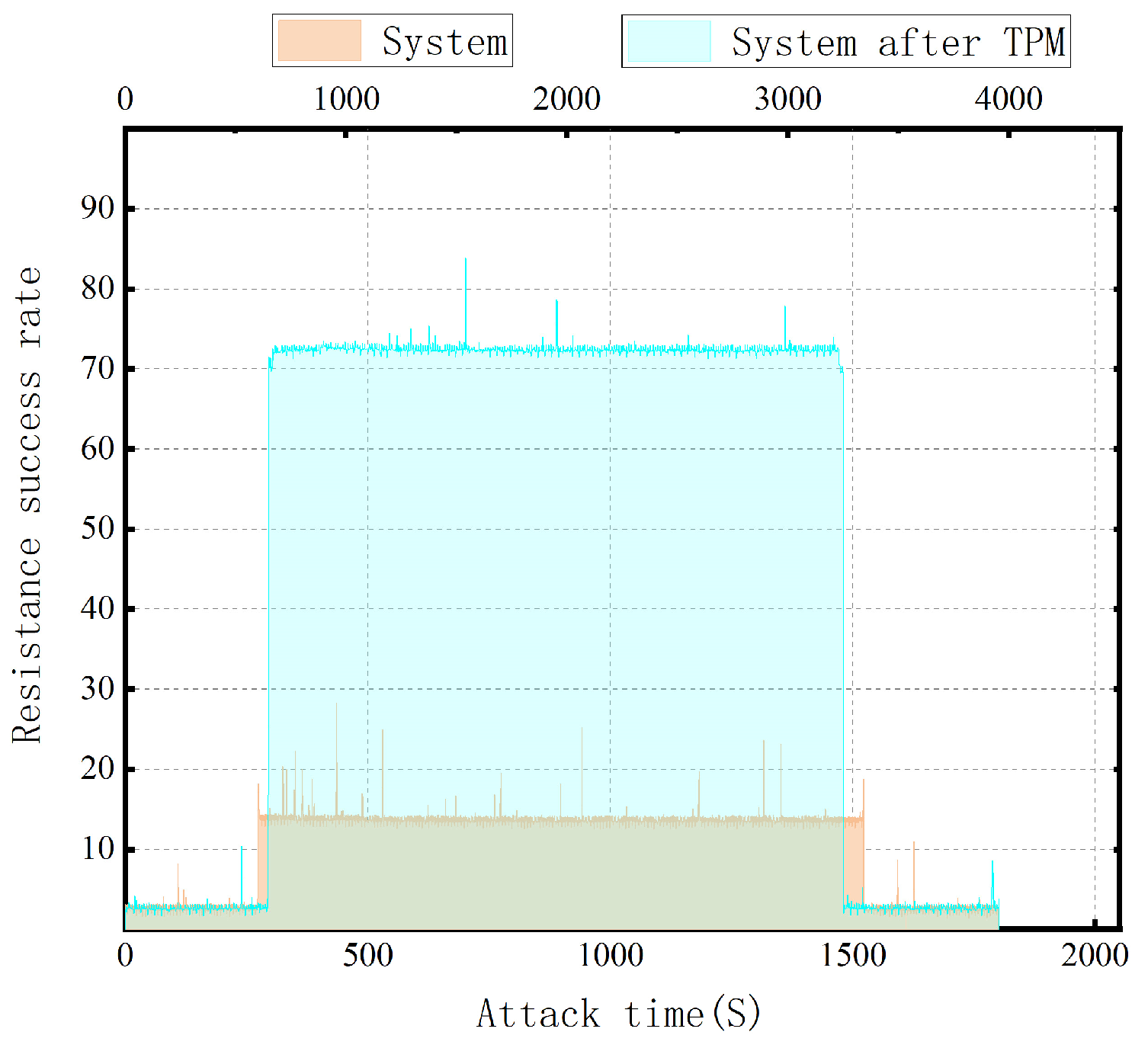
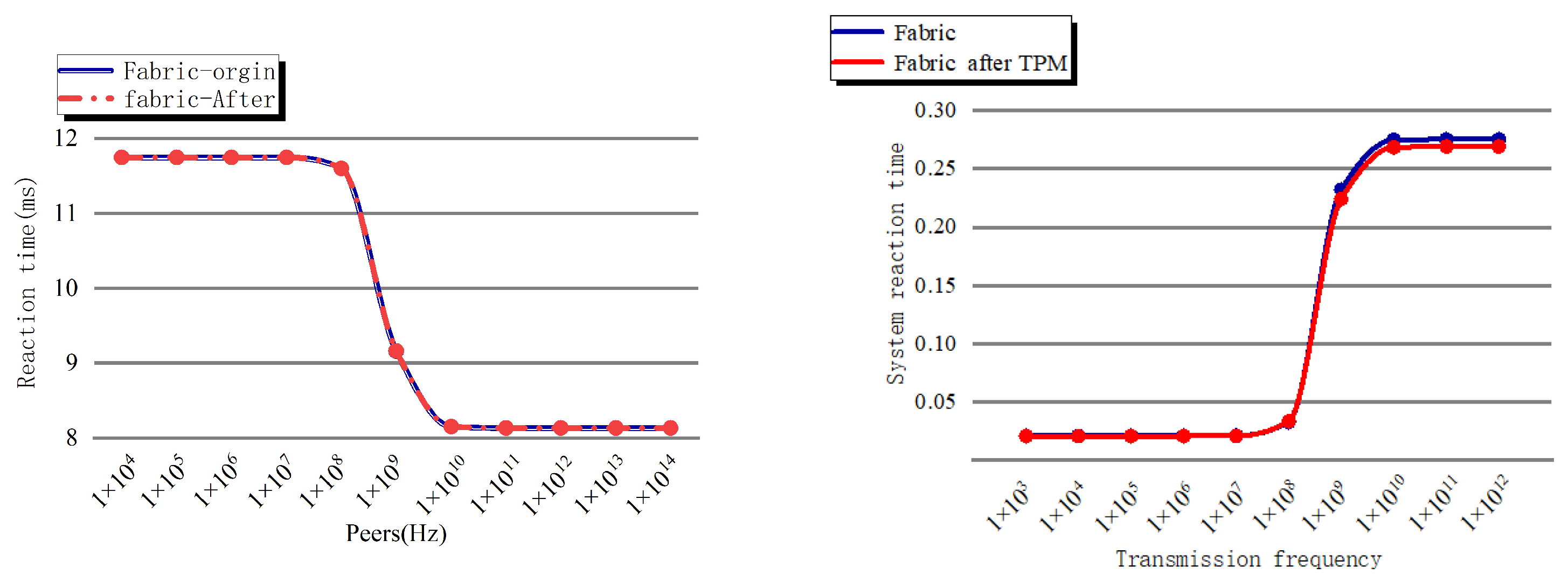
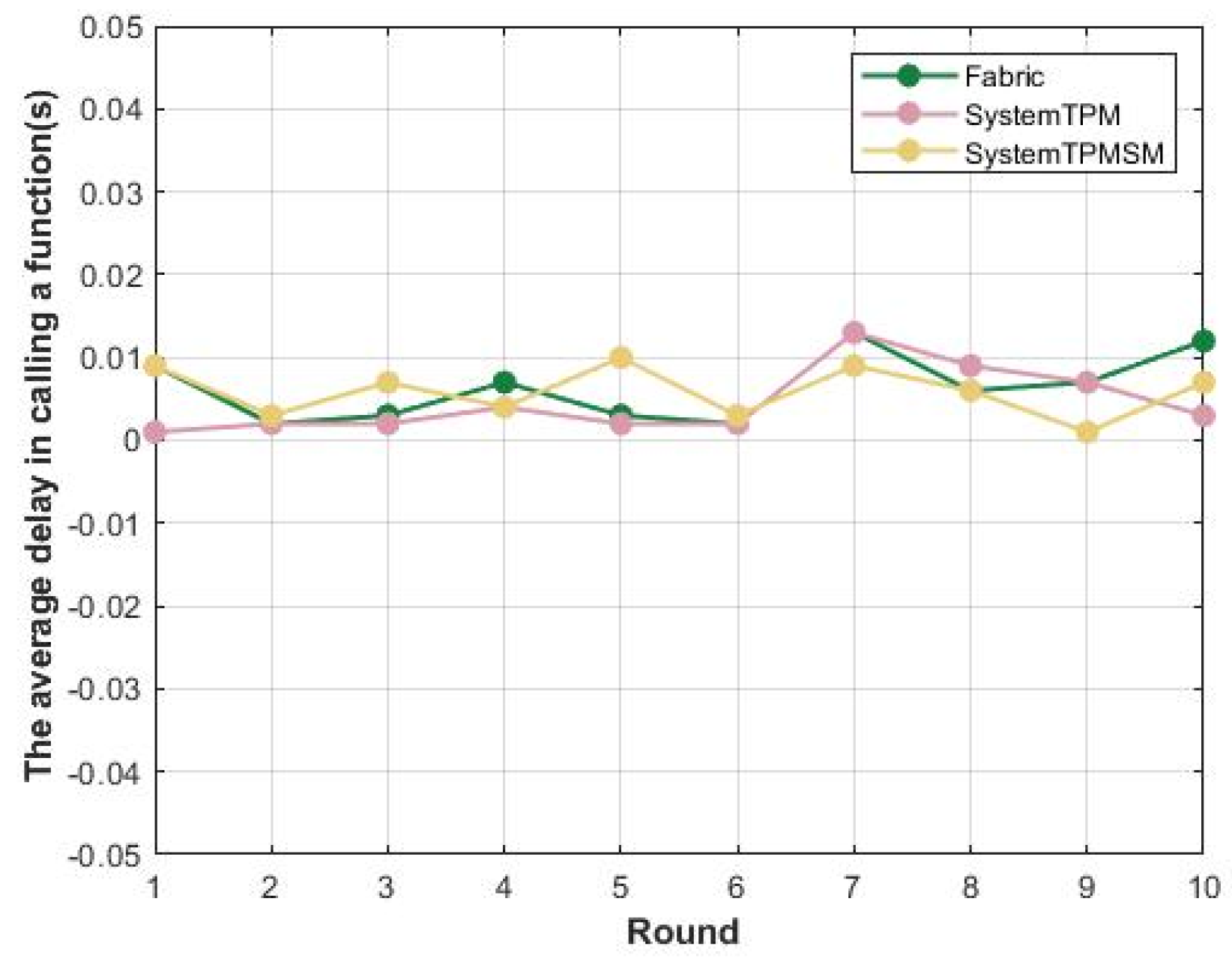
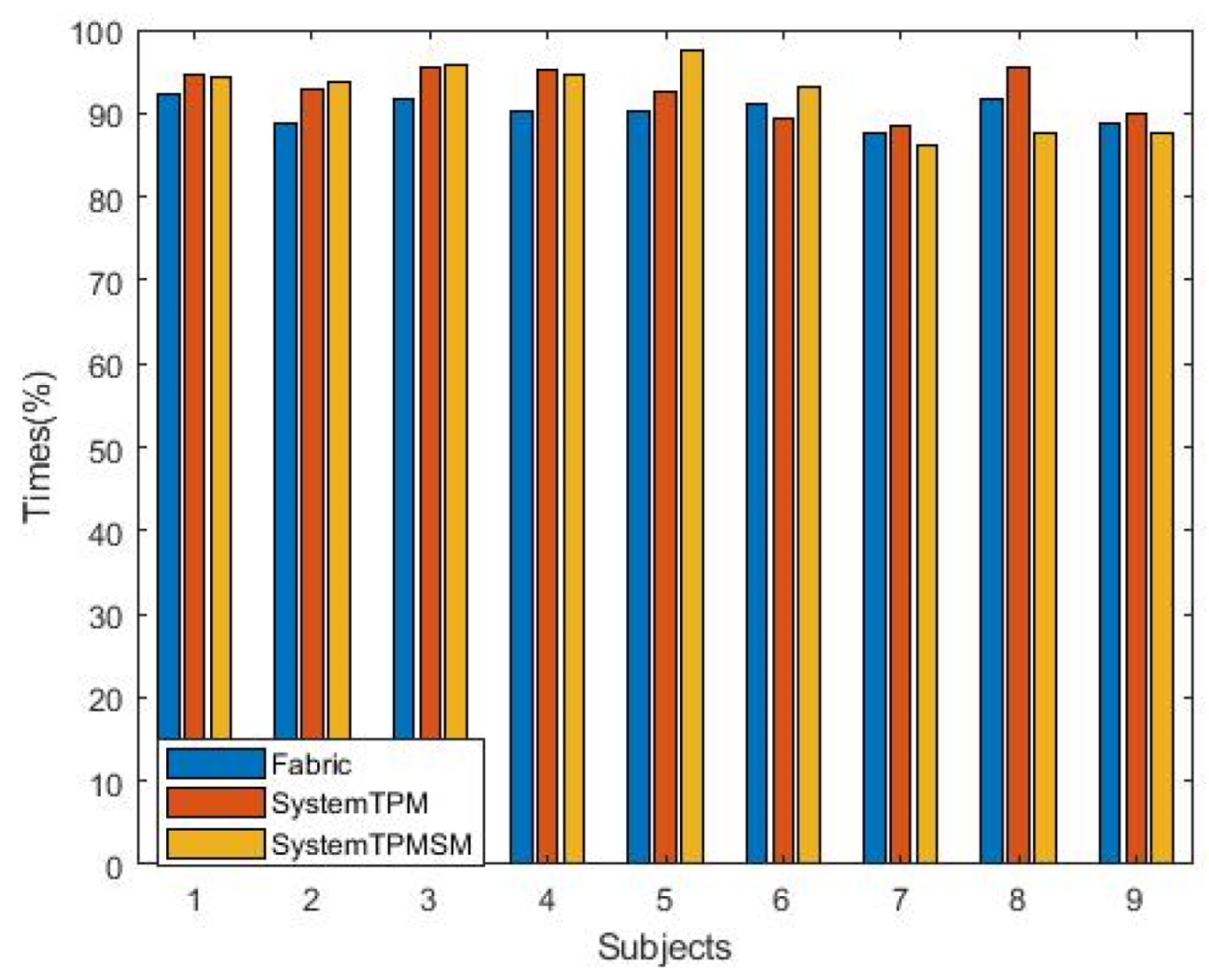
5.1. Simulate Attacks and Measure and Compare Related Performance
- (1)
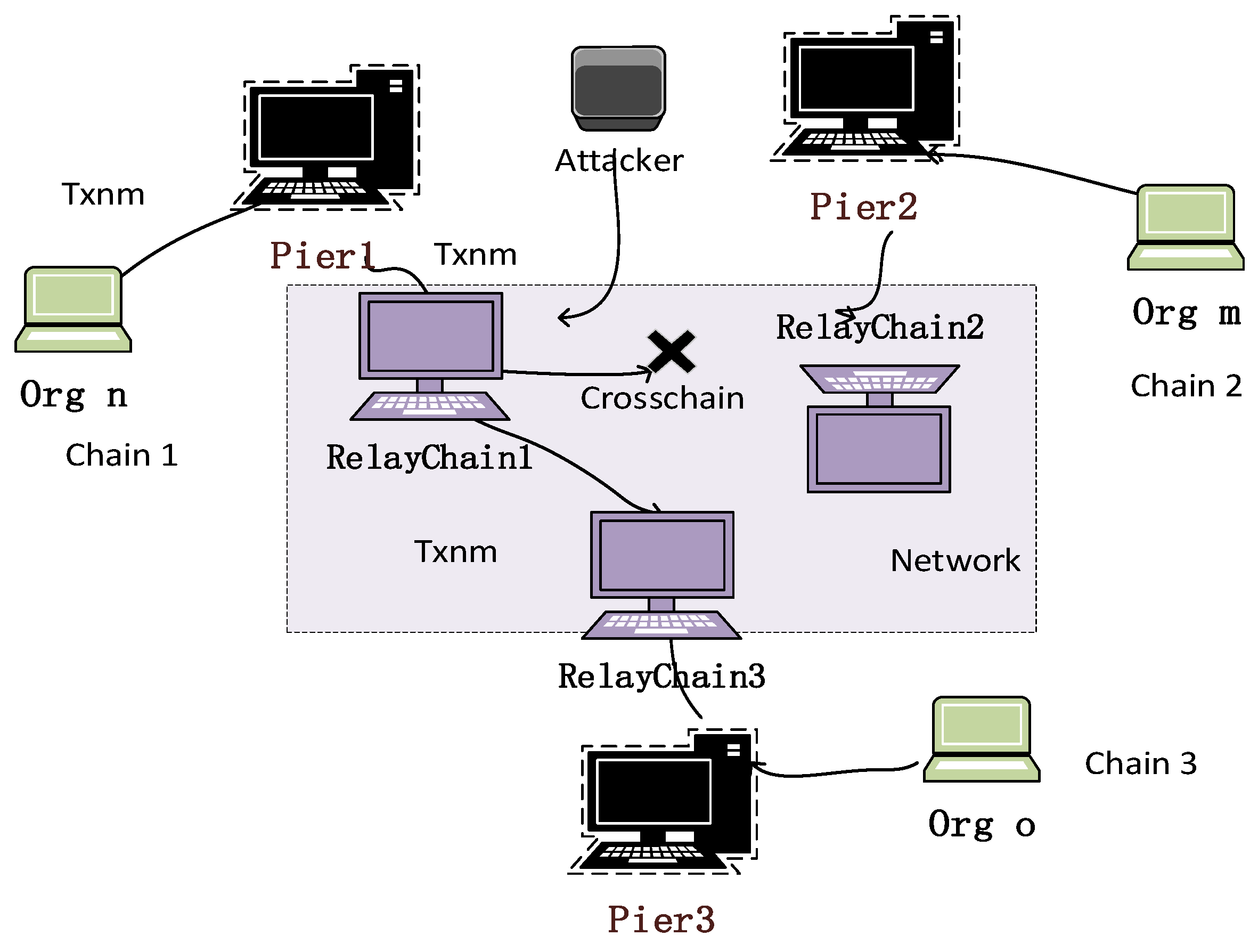
- Attacks on the relay chain routing [20]: Once the attacker has taken over the router, they can use various tools to mess with the router’s domain name resolution system server, insert ads or viruses, or steal user information. The primary purposes of cross-chain routing in cross-chain systems are to authenticate some cross-chain transactions and send cross-chain communications depending on addresses [21]. A cross-chain transaction (TXnm) is sent from the sender in the organization Orgn on Chain1 to a user in the organization Orgm on Chain2. The standard procedure is for TXnm to travel via gateway Pier1, relay chain RelayChain1, which is a cross-chain network, and then be routed to the appropriate users of the organization Orgm through gateway Pier2. However, attackers take the use of a port vulnerability on the relay chain RelayChain1 server, resulting in the failure of the relay chain RelayChain1, which prevents the relay chain from continuing to send TXnm. The interplay of relay chain routing attacks is seen in Figure 5.
- (2)
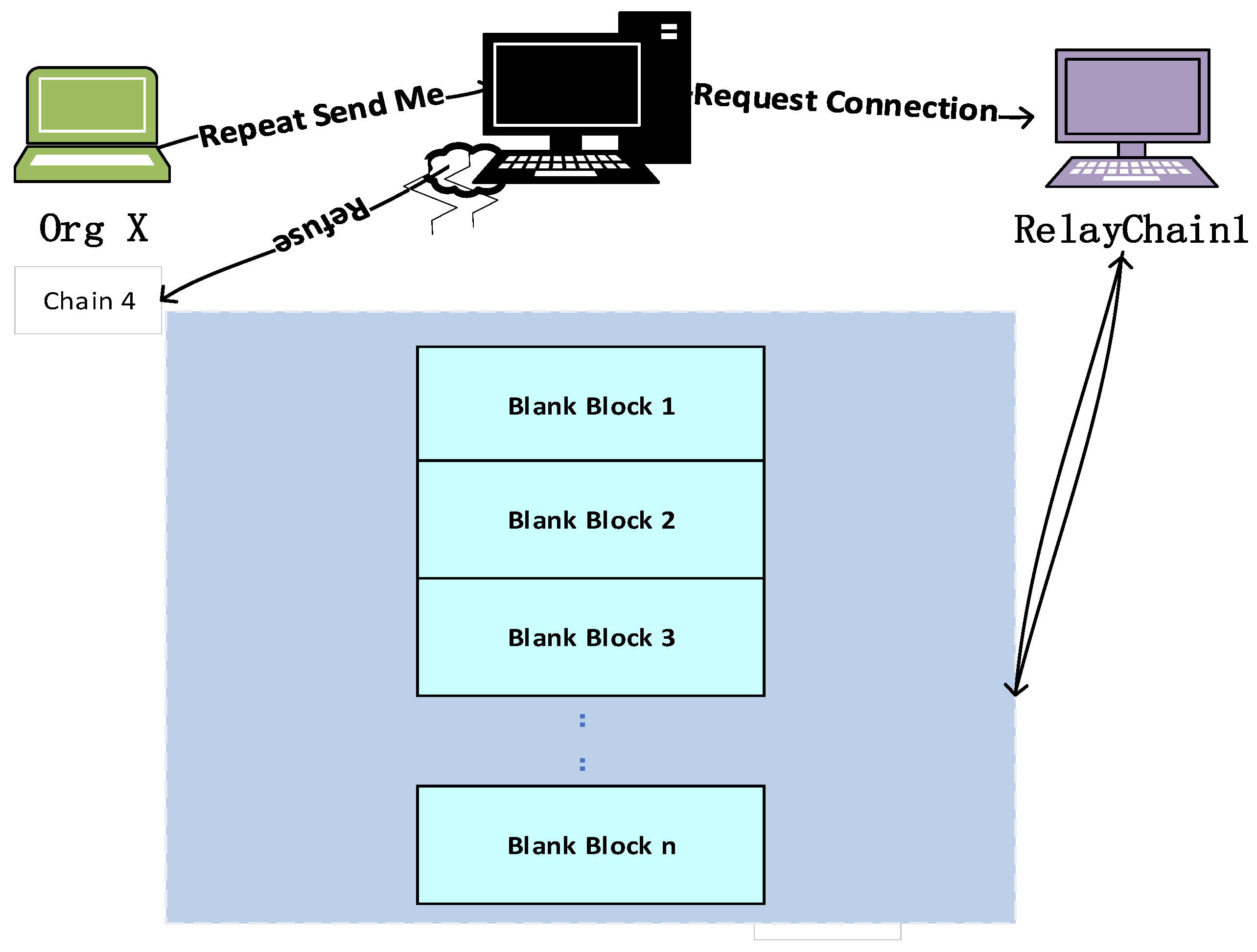
- Blocking relay chain attacks [22]: On RelayChainA, a hostile attacker from org X must make a request for cross-chain information Me, which contains the information of the transaction initiator and recipient on the application chain address, before they may attempt to conduct cross-chain transactions [23]. The Pier gateway will submit a connection setup request to the RelayChainA it belongs to after successfully receiving and verifying it. Attackers can, however, purposefully break the connection and then request a connection to the Pier gateway once more, continuing this procedure. The message requesting a connection will still be packaged into the relay chain to form two empty blocks that only contain the information of the requesting connection gateway, even though the gateway will prevent the attacker’s application RelayChainA from accessing the Pier gateway after a certain number of repetitions (i.e., revoking its connection permission to the relay chain).These blocks do not contain any valid transaction information and can be considered invalid blocks. As attackers continue to repeatedly connect and cancel the connection to the Pier gateway, a large number of blank invalid blocks will be generated in the relay chain in a short period of time, bringing enormous pressure to the entire cross-chain network. Figure 6 shows the interaction process of blocking attacks in the relay chain.
5.1.1. Experimental Group
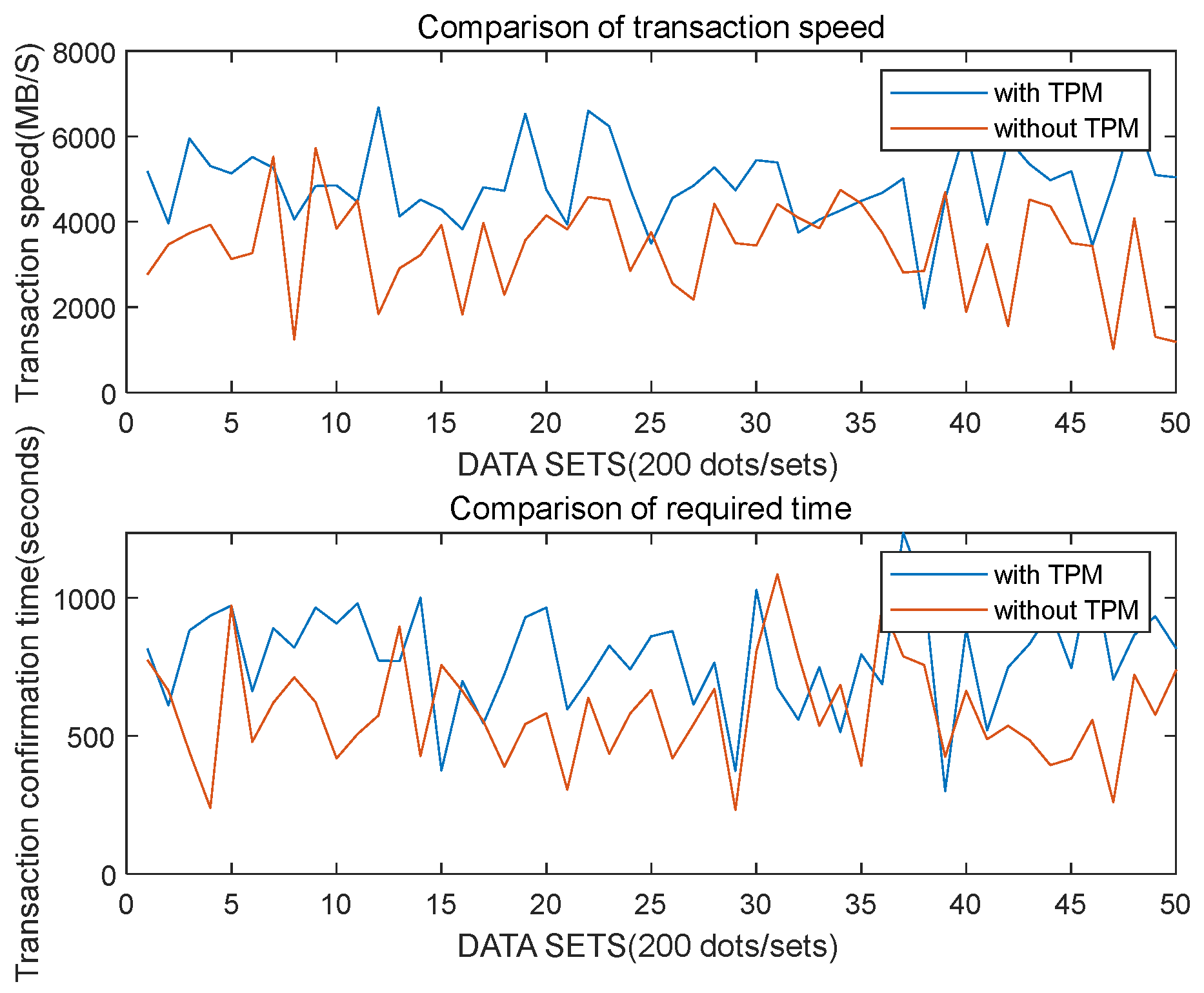
5.1.2. Recording of Attack Results
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Nie, X.-W.; Fang, D.-G.; Che, J.-J.; Wang, X.-P. Design and implementation of security operating system based on trusted computing. In Proceedings of the 2006 International Conference on Machine Learning and Cybernetics, Dalian, China, 13–16 August 2006. [Google Scholar]
- Allan, T. Introduction to the TPM. In Smart Cards, Tokens, Security and Applications; Springer: Berlin/Heidelberg, Germany, 2017; pp. 173–191. [Google Scholar]
- Sailer, R.; Zhang, X.; Jaeger, T.; van Doorn, L. Design and implementation of a TCG-based integrity measurement architecture. In Proceedings of the USENIX Security Symposium, San Diego, CA, USA, 9–13 August 2004; Volume 13, pp. 223–238. [Google Scholar]
- Lioy, A.; Ramunno, G. Trusted computing. In Handbook of Information and Communication Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 697–717. [Google Scholar]
- Meng, B.; Wang, Y.; Zhao, C.; Wang, D.; Ma, B. Survey on Cross-Chain Protocols of Blockchain. J. Front. Comput. Sci. Technol. 2022, 16, 2177–2192. [Google Scholar]
- Ou, W.; Huang, S.; Zheng, J.; Zhang, Q.; Zeng, G.; Han, W. An overview on cross-chain: Mechanism, platforms, challenges. Comput. Netw. 2022, 218, 109378. [Google Scholar] [CrossRef]
- Zhang, L.; Liu, B.; Zhang, R.; Jiang, B.; Liu, Y. Overview of Blockchain Technology. Comput. Eng. 2019, 45, 1–12. [Google Scholar] [CrossRef]
- Liu, S.; Lei, M.; Wang, L.; Sun, C.; Xu, L.; Cao, L.; Feng, D.; Zheng, J.; Li, J. Survey of Blockchain Key Technologies and Existing Problems. Comput. Eng. Appl. 2022, 58, 66–82. [Google Scholar]
- Nakamoto, S. Bitcoin Whitepaper. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 17 July 2019).
- Wood, G. Polkadot: Vision for a heterogeneous multi-chain framework. Comput. Sci. 2016, 21, 2327–4662. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25 July 2016; Volume 310, pp. 1–4. [Google Scholar]
- Li, F.; Li, Z.-R.; Zhao, H. Research on the Progress in Cross-chain Technology of Blockchains. J. Softw. 2019, 30, 1649–1660. [Google Scholar]
- Xue, Y.; Herlihy, M. Hedging against sore loser attacks in cross-chain transactions. In Proceedings of the 2021 ACM Symposium on Principles of Distributed Computing, Salerno, Italy, 26–30 July 2021; pp. 155–164. [Google Scholar]
- Yu, B.; Ren, S.; Liu, J. Overview of blockchain assets theft attacks and defense technology. Chin. J. Netw. Inf. Secur. 2023, 9, 1–17. [Google Scholar]
- Osborn, J.D.; Challener, D.C. Trusted Platform Module Evolution. Johns Hopkins Apl Tech. Dig. 2013, 32, 536–543. [Google Scholar]
- Buterin, V. Chain Interoperability. Available online: https://allquantor.at/blockchainbib/pdf/vitalik2016chain.pdf (accessed on 9 September 2016).
- Vujičić, D.; Jagodić, D.; Ranđić, S. Blockchain technology, bitcoin, and Ethereum: A brief overview. In Proceedings of the 2018 17th International Symposium INFOTEH-JAHORINA (INFOTEH), East Sarajevo, Bosnia and Herzegovina, 21–23 March 2018. [Google Scholar]
- Bhatia, R. Interoperability Solutions for Blockchain. In Proceedings of the 2020 International Conference on Smart Technologies in Computing, Electrical and Electronics (ICSTCEE), Bengaluru, India, 9–10 October 2020; pp. 381–385. [Google Scholar]
- Kwon, J.; Buchman, E.J.A.N.D.L. Hyperledger Fabric Whitepaper. 2019. [Google Scholar]
- Gao, W.; Hei, X.; Wang, Y. The Data Privacy Protection Method for Hyperledger Fabric Based on Trustzone. Mathematics 2023, 11, 1357. [Google Scholar] [CrossRef]
- Buchman, E. Tendermint: Byzantine Fault Tolerance in the Age of Blockchains. Ph.D. Thesis, University of Guelph, Guelph, ON, Canada, 2016. [Google Scholar]
- Li, W.; Feng, C.; Zhang, L.; Xu, H.; Cao, B.; Imran, M.A. A scalable multi-layer PBFT consensus for blockchain. IEEE Trans. Parallel Distrib. Syst. 2020, 32, 1146–1160. [Google Scholar] [CrossRef]
- Belchior, R.; Vasconcelos, A.; Correia, M.; Hardjono, T. Hermes: Fault-tolerant middleware for blockchain interoperability. Future Gener. Comput. Syst. 2022, 129, 236–251. [Google Scholar] [CrossRef]
- Cao, L.; Song, B. Blockchain cross-chain protocol and platform research and development. In Proceedings of the 2021 International Conference on Electronics, Circuits and Information Engineering (ECIE), Zhengzhou, China, 22–24 January 2021; pp. 264–269. [Google Scholar]
- Lu, A.; Zhao, K.; Yang, J.; Wang, F. Research on Cross-chain Technology of Blockchain. Netinfo Secur. 2019, 19, 83–90. [Google Scholar]
- Howell, A.; Saber, T.; Bendechache, M. Measuring node decentralisation in blockchain peer to peer networks. Blockchain Res. Appl. 2023, 4, 10–20. [Google Scholar] [CrossRef]
- Lin, J.-y.; Zhang, Z.-l.; Yuan, Z.-w. Research on Authentication Encryption Mechanism based on IBC in Internet of Thing. Inf. Secur. Commun. Priv. 2020, 8, 95–101. [Google Scholar]
- Butterworth, J.; Kallenberg, C.; Kovah, X.; Herzog, A. Problems with the static root of trust for measurement. In Proceedings of the Black Hat USA, Las Vegas, NV, USA, 27 July–1 August 2013. [Google Scholar]
- Teo, J. Features and benefits of trusted computing. In Proceedings of the 2009 Information Security Curriculum Development Conference, Kennesaw, GA, USA, 25–26 September 2009; pp. 67–71. [Google Scholar]
- Song, C.; Liu, B.; Hu, Z.-m.; Xin, Y.; Yang, Y.-x.; Yin, H. Efficient ID-based TPM key loading scheme for trusted platform. J. China Univ. Posts Telecommun. 2010, 17, 74–79. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Zhang, M.; Choo, K.-K.R. A provable-secure and practical two-party distributed signing protocol for SM2 signature algorithm. Front. Comput. Sci. 2020, 14, 143803. [Google Scholar] [CrossRef]
- Zheng, X.; Xu, C.; Hu, X.; Zhang, Y.; Xiong, X. The software/hardware co-design and implementation of SM2/3/4 encryption/decryption and digital signature system. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2019, 39, 2055–2066. [Google Scholar] [CrossRef]
- Zhou, Y.; Wu, N.; Hu, B.; Zhang, Y.; Qiu, J.; Cai, W. Implementation and performance of face recognition payment system securely encrypted by sm4 algorithm. Information 2022, 13, 316. [Google Scholar] [CrossRef]
- Chen, L.; Qian, S.; Lim, M.; Wang, S. An Enhanced Direct Anonymous Attestation Scheme with Mutual Authentication for Network-Connected UAV Communication Systems. China Commun. 2018, 15, 61–76. [Google Scholar] [CrossRef]
- Shand, M.; Vuillemin, J. Fast implementations of RSA cryptography. In Proceedings of the IEEE 11th Symposium on Computer Arithmetic, Windsor, ON, Canada, 29 June–2 July 1993; IEEE: Piscataway, NJ, USA, 1993; pp. 252–259. [Google Scholar]
- Wang, X.; Yu, H. How to break MD5 and other hash functions. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 19–35. [Google Scholar]


| Number of Validators | 1st | 2nd | 3rd | 4th | 5th | 6th | 7th | 8th | 9th | 10th |
|---|---|---|---|---|---|---|---|---|---|---|
| × | √ | × | × | √ | √ | × | × | √ | × | |
| √ | √ | × | √ | × | √ | √ | √ | √ | × | |
| √ | √ | √ | × | √ | √ | √ | × | √ | × | |
| √ | √ | × | × | √ | × | × | √ | × | √ | |
| √ | √ | √ | √ | × | √ | √ | √ | √ | √ |
| Number of Validators | Tt/ms | Tut/ms | Total Time/ms |
|---|---|---|---|
| 24.46 | 45.49 | 70.57 | |
| 117.51 | 285.40 | 402.31 | |
| 275.63 | 571.39 | 847.02 | |
| 1643.49 | 2775.79 | 4419.28 | |
| 4111.85 | 5375.10 | 9489.95 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Yan, Y.; Zhang, Y.; Tian, M.; Liu, X. Ensuring Cross-Chain Transmission Technique Utilizing TPM and Establishing Cross-Trusted Root Security via SM Algorithm. Electronics 2024, 13, 2978. https://doi.org/10.3390/electronics13152978
Wang Y, Yan Y, Zhang Y, Tian M, Liu X. Ensuring Cross-Chain Transmission Technique Utilizing TPM and Establishing Cross-Trusted Root Security via SM Algorithm. Electronics. 2024; 13(15):2978. https://doi.org/10.3390/electronics13152978
Chicago/Turabian StyleWang, Yichuan, Yiliang Yan, Yaling Zhang, Mengjie Tian, and Xiaoxue Liu. 2024. "Ensuring Cross-Chain Transmission Technique Utilizing TPM and Establishing Cross-Trusted Root Security via SM Algorithm" Electronics 13, no. 15: 2978. https://doi.org/10.3390/electronics13152978
APA StyleWang, Y., Yan, Y., Zhang, Y., Tian, M., & Liu, X. (2024). Ensuring Cross-Chain Transmission Technique Utilizing TPM and Establishing Cross-Trusted Root Security via SM Algorithm. Electronics, 13(15), 2978. https://doi.org/10.3390/electronics13152978








