Research on Multi-Layer Defense against DDoS Attacks in Intelligent Distribution Networks
Abstract
:1. Introduction
- Firstly, this paper conducts a DDoS security analysis on the new power distribution communication network based on SDN architecture.
- Secondly, with the progressive nature of computation in mind, a three-layer defense architecture is designed from shallow to deep, efficiently preventing resource wastage in detecting low-intensity DDoS attacks.
- Thirdly, this paper employs Rényi entropy for DDoS detection. This step is improved for complex DDoS attacks, and when combined with the random forest classifier, it effectively detects potential DDoS behaviors in the traffic passing through switches.
- Finally, this paper uses a dual defense method combining BiCNN and OneDCNN to inspect and filter port traffic, ensuring normal communication of valid traffic while eliminating malicious traffic.
2. System Models
2.1. Network Composition of User-Side Devices in Distribution Networks
2.2. DDoS
- -
- SYN Flood: Attackers send a large number of SYN request packets to the target server but do not complete the TCP three-way handshake, thereby exhausting the server’s connection resources.
- -
- ICMP Flood: Using the ICMP protocol, attackers send numerous ping request packets to the target server, causing the server to become busy responding to these requests and depleting its resources.
- -
- UDP Flood: Attackers send a large number of UDP packets to random ports on the target server, forcing the server to continuously check and respond to these nonexistent requests, thus consuming the server’s computational resources.
3. Methodology
3.1. DDoS Detection Based on Rényi Entropy
3.2. Random Forest Classifier
3.3. Convolutional Neural Network
4. System Design
- Without the first layer, BiCNN would need to run continuously, constantly monitoring each switch. Since BiCNN is based on CNN, its computational load and model size are significantly higher compared to the Rényi entropy and random forest combination, which retrieves fewer features. Under low-saturation DDoS attacks, most of the time, there are no abnormal data in the switch, leading to resource wastage.
- Without the second layer, OneDCNN would need to filter all packets across the entire network upon receiving the first layer’s alert, resulting in an excessive computational load that could crash the system.
- Without the third layer, the mechanism cannot participate in the controller’s decision-making process, rendering it unable to perform packet filtering.
5. Results and Validation
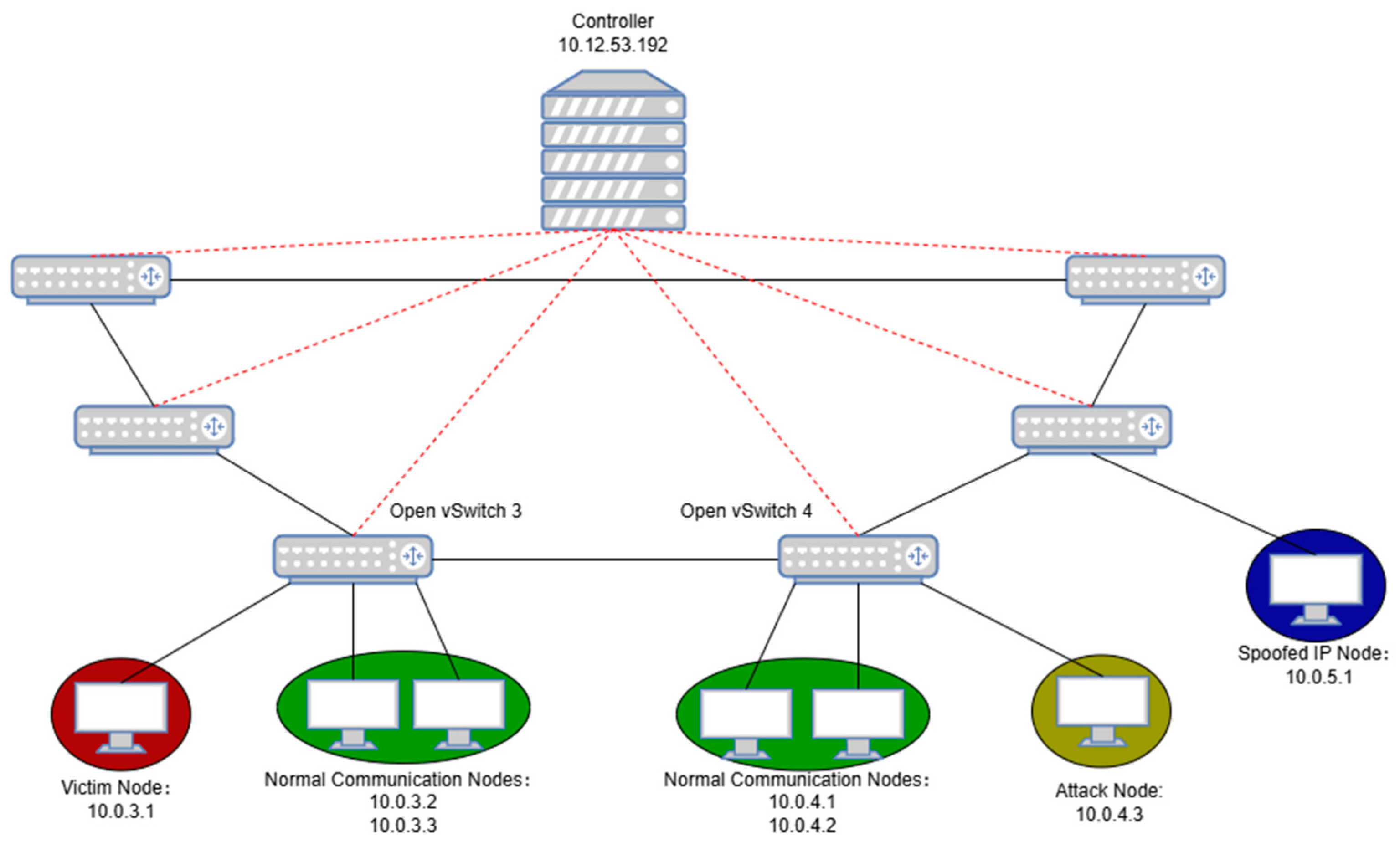
5.1. Experimental Topology
5.2. Baselines
- φ-entropy [10]: This method analyzes traffic characteristics using φ-entropy to achieve early attack detection. φ-entropy amplifies the characteristic differences between different types of data by adjusting parameters. As a non-machine learning method, it performs well in early attack detection, particularly suited for detecting anomalous traffic by emphasizing data differences through parameter adjustments.
- Spark Streaming and Flink [27]: This method proposes an online internet traffic monitoring and DDoS attack detection approach based on big data frameworks (Spark Streaming and Flink). It is suitable for large-scale internet traffic monitoring and achieves high detection rates through machine learning techniques.
- 3Dual-CNN [26]: In the first two layers of the three-layer detection mechanism proposed in this paper, CNN methods are utilized. By leveraging convolutional layers, pooling layers, and fully connected layers, CNNs effectively extract and integrate image features, excelling in tasks such as target classification and attack detection. However, the effectiveness of CNNs requires a significant number of parameters.
- Dual Rényi [11]: In the first two layers of the three-layer detection mechanism proposed in this paper, Rényi entropy methods are used, demonstrating the superiority of introducing the random forest classifier in our work and using the BiCNN method in the second layer.
5.3. Evaluation Criteria
5.4. Attack Modes
- Each batch contains 100 entries to facilitate model training and testing.
- Two types of batches are extracted from the dataset: one type contains entirely benign data, labeled as benign; the other type contains attack data, labeled as attack, with the proportion of attack data allocated according to the aforementioned distribution.
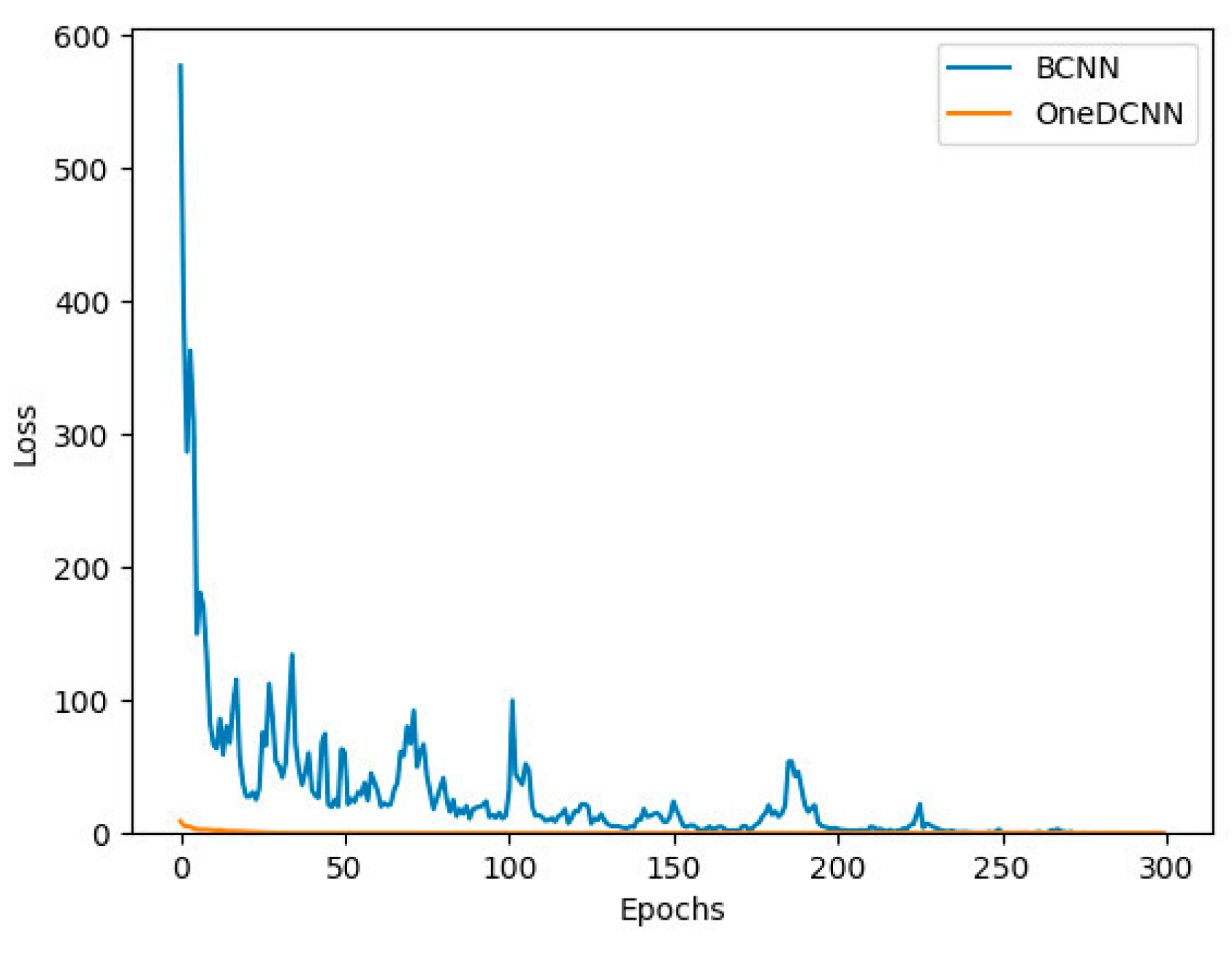
5.5. Results Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Fotopoulou, M.; Petridis, S.; Karachalios, I.; Rakopoulos, D. A Review on Distribution System State Estimation Algorithms. Appl. Sci. 2022, 12, 11073. [Google Scholar] [CrossRef]
- Yang, H.; He, X.; Wang, Z.; Qiu, R.C.; Ai, Q. Blind False Data Injection Attacks Against State Estimation Based on Matrix Reconstruction. IEEE Trans. Smart Grid 2022, 7, 3174–3187. [Google Scholar] [CrossRef]
- Vinicius, D.; Pedro, R.; Damien, M.; Mario, M. Detection and Mitigation of Low-Rate Denial-of-Service Attacks: A Survey. IEEE Access 2022, 10, 76648–76668. [Google Scholar]
- Zhao, J.; Jing, X.; Yan, Z.; Pedrycz, W. Network traffic classification for data fusion: A survey. Inf. Fusion 2021, 72, 22–47. [Google Scholar] [CrossRef]
- Kaur, S.; Kumar, K.; Aggarwal, N.; Singh, G. A comprehensive survey of DDoS defense solutions in SDN: Taxonomy, research challenges, and future directions. Comput. Secur. 2021, 110, 102423. [Google Scholar] [CrossRef]
- Deb, R.; Roy, S. A comprehensive survey of vulnerability and information security in SDN. Comput. Netw. 2022, 206, 108802. [Google Scholar] [CrossRef]
- Yuan, J.; Mills, K. Monitoring the macroscopic effect of DDoS flooding attacks. IEEE Trans. Dependable Secur. Comput. 2005, 2, 324–335. [Google Scholar] [CrossRef]
- Galeano-Brajones, J.; Carmona-Murillo, J.; Valenzuela-Valdés, J.F.; Luna-Valero, F. Detection and Mitigation of DoS and DDoS Attacks in IoT-Based Stateful SDN: An Experimental Approach. Sensors 2020, 20, 816. [Google Scholar] [CrossRef]
- Biswas, R.; Kim, S.; Wu, J. Sampling Rate Distribution for Flow Monitoring and DDoS Detection in Datacenter. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2524–2534. [Google Scholar] [CrossRef]
- Tsobdjou, L.D.; Pierre, S.; Quintero, A. An Online Entropy-Based DDoS Flooding Attack Detection System With Dynamic Threshold. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1679–1689. [Google Scholar] [CrossRef]
- Liu, Z.; Hu, C.; Shan, C. Riemannian manifold on stream data: Fourier transform and entropy-based DDoS attacks detection method. Comput. Secur. 2021, 109, 102392. [Google Scholar] [CrossRef]
- Li, R.; Wu, B. Early detection of DDoS based on φ-entropy in SDN networks. In Proceedings of the 2020 IEEE 4th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Darmstadt, Germany, 12–14 June 2020; pp. 731–735. [Google Scholar]
- Ahalawat, A.; Babu, K.S.; Turuk, A.K.; Patel, S. A low-rate DDoS detection and mitigation for SDN using Renyi Entropy with Packet Drop. J. Inf. Secur. Appl. 2022, 68, 103212. [Google Scholar] [CrossRef]
- Wang, X.; Zhong, X.; Li, L.; Zhang, S.; Lu, R.; Yang, T. TOT: Trust aware opportunistic transmission in cognitive radio Social Internet of Things. Comput. Commun. 2020, 162, 1–11. [Google Scholar] [CrossRef]
- Abidi, R.; Azzouna, N.B. Self-adaptive trust management model for social IoT services. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC), Nicosia, Cyprus, 31 October 31–2 November 2021; pp. 1–7. [Google Scholar]
- Magdich, R.; Jemal, H.; Nakti, C.; Ben Ayed, M. An efficient Trust Related Attack Detection Model based on Machine Learning for Social Internet of Things. In Proceedings of the 2021 International Wireless Communications and Mobile Computing (IWCMC), Nicosia, Cyprus, 28 June–2 July 2021; pp. 1465–1470. [Google Scholar]
- Abdelghani, W.; Amous, I.; Zayani, C.A. Dynamic and scalable multi-level trust management model for Social Internet of Things. J. Supercomput. 2022, 78, 8137–8193. [Google Scholar] [CrossRef]
- Balarezo, J.F.; Wang, S.; Chavez, K.G.; Al-Hourani, A.; Kandeepan, S. A survey on DoS/DDoS attacks mathematical modelling for traditional, SDN and virtual networks. Eng. Sci. Tech. Int. J. 2022, 31, 101065. [Google Scholar] [CrossRef]
- Baskar, M.; Ramkumar, J.; Karthikeyan, C. Low rate DDoS mitigation using real-time multi threshold traffic monitoring system. J. Ambient Intell. Humaniz. Comput. 2021, 1–9. [Google Scholar] [CrossRef]
- Engström, V.; Lagerström, R. Two decades of cyberattack simulations: A systematic literature review. Comput. Secur. 2022, 116, 102681. [Google Scholar] [CrossRef]
- Cil, A.E.; Yildiz, K.; Buldu, A. Detection of DDoS attacks with feed forward based deep neural network model. Expert Sys. Appl. 2021, 169, 114520. [Google Scholar] [CrossRef]
- Doriguzzi-Corin, R.; Millar, S.; Scott-Hayward, S.; Martínez-del-Rincón, J.; Siracusa, D. Lucid: A Practical, Lightweight Deep Learning Solution for DDoS Attack Detection. IEEE Trans. Netw. Serv. Manag. 2020, 17, 876–889. [Google Scholar] [CrossRef]
- Wei, G.; Wang, Z. Adoption and realization of deep learning in network traffic anomaly detection device design. Soft Comput. 2021, 25, 1147–1158. [Google Scholar] [CrossRef]
- Fouladi, R.F.; Ermiş, O.; Anarim, E. A DDoS attack detection and countermeasure scheme based on DWT and auto-encoder neural network for SDN. Comput. Netw. 2022, 214, 109140. [Google Scholar] [CrossRef]
- Asad, M.; Asim, M.; Javed, T.; Beg, M.O.; Mujtaba, H.; Abbas, S. DeepDetect: Detection of Distributed Denial of Service Attacks Using Deep Learning. Comput. J. 2020, 63, 983–994. [Google Scholar] [CrossRef]
- Zaib, M.H.; Bashir, F.; Qureshi, K.N. Deep learning based cyber bullying early detection using distributed denial of service flow. Multimed. Syst. 2022, 28, 1905–1924. [Google Scholar] [CrossRef]
- Rehman, S.U.; Khaliq, M.; Imtiaz, S.I.; Rasool, A.; Javed, A.R.; Jalil, Z.; Bashir, A.K. DIDDOS: An approach for detection and identification of Distributed Denial of Service (DDoS) cyberattacks using Gated Recurrent Units (GRU). Future Gen. Comput. Sys. 2021, 118, 453–466. [Google Scholar] [CrossRef]
- Yungaicela-Naula, N.M.; Vargas-Rosales, C.; Perez-Diaz, J.A. SDN-Based Architecture for Transport and Application Layer DDoS Attack Detection by Using Machine and Deep Learning. IEEE Access 2021, 9, 108495–108512. [Google Scholar] [CrossRef]
- Zhou, B.; Li, J.; Ji, Y.; Guizani, M. Online Internet Traffic Monitoring and DDoS Attack Detection Using Big Data Frameworks. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 1507–1512. [Google Scholar]
- Tayfour, O.E.; Marsono, M.N. Collaborative detection and mitigation of DDoS in software-defined networks. J. Supercomput. 2021, 77, 13166–13190. [Google Scholar] [CrossRef]
- Haider, S.; Akhunzada, A.; Mustafa, I.; Patel, T.B.; Fernandez, A.; Choo, K.K.R.; Iqbal, J. A Deep CNN Ensemble Framework for Efficient DDoS Attack Detection in Software Defined Networks. IEEE Access 2020, 8, 53972–53983. [Google Scholar] [CrossRef]
- Hwang, R.H.; Peng, M.C.; Huang, C.W.; Lin, P.C.; Nguyen, V.L. An Unsupervised Deep Learning Model for Early Network Traffic Anomaly Detection. IEEE Access 2020, 8, 30387–30399. [Google Scholar] [CrossRef]
- Cheng, J.; Liu, Y.; Tang, X.Y.; Sheng, V.S.; Li, M.Y.; Li, J.Q. DDoS Attack Detection via Multi-scale Convolutional Neural Network. Comput. Mater. Contin. 2020, 62, 1317–1333. [Google Scholar] [CrossRef]
- Kumar, H.; Aoudni, Y.; Ortiz, G.G.R.; Jindal, L.; Miah, S.; Tripathi, R.; Damaševičius, R. Light Weighted CNN Model to Detect DDoS Attack over Distributed Scenario. Secur. Commun. Netw. 2022, 2022, 7585457. [Google Scholar] [CrossRef]
- Abrahamsen, F.E.; Ai, Y.; Cheffena, M. Communication Technologies for Smart Grid: A Comprehensive Survey. Sensors 2021, 21, 8087. [Google Scholar] [CrossRef] [PubMed]
- Tightiz, L.; Yang, H. A Comprehensive Review on IoT Protocols’ Features in Smart Grid Communication. Energies 2020, 13, 2762. [Google Scholar] [CrossRef]
- Jiménez, M.B.; Fernández, D.; Rivadeneira, J.E.; Bellido, L.; Cárdenas, A. A Survey of the Main Security Issues and Solutions for the SDN Architecture. IEEE Access 2021, 9, 122016–122038. [Google Scholar] [CrossRef]
- Correa, C.J.C.; Imbachi, J.C.; Vega, J.F.B. Security in SDN: A comprehensive survey. J. Net. Comp. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Maleh, Y.; Qasmaoui, Y.; El Gholami, K. A comprehensive survey on SDN security: Threats, mitigations, and future directions. J. Reliable Intell. Environ. 2023, 9, 201–239. [Google Scholar] [CrossRef]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Dorsch, N.; Kurtz, F.; Georg, H.; Hägerling, C.; Wietfeld, C. Software-defined networking for Smart Grid communications: Applications, challenges and advantages. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 422–427. [Google Scholar]
- Zhang, J.; Seet, B.C.; Lie, T.T.; Foh, C.H. Opportunities for Software-Defined Networking in Smart Grid. In Proceedings of the 2013 9th International Conference on Information, Communications & Signal Processing, Tainan, Taiwan, 10–13 December 2013; pp. 1–5. [Google Scholar]
- Bera, S.; Misra, S.; Vasilakos, A.V. Software-Defined Networking for Internet of Things: A Survey. IEEE Internet Things J. 2017, 4, 1994–2008. [Google Scholar] [CrossRef]
- Zargar, S.T.; Joshi, J.; Tipper, D. A Survey of Defense Mechanisms Against Distributed Denial of Service (DDoS) Flooding Attacks. IEEE Commun. Surv. Tut. 2013, 15, 2046–2069. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommun. Syst. 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Huseinović, A.; Mrdović, S.; Bicakci, K.; Uludag, S. A Survey of Denial-of-Service Attacks and Solutions in the Smart Grid. IEEE Access 2020, 8, 177447–177470. [Google Scholar] [CrossRef]
- Shah, Z.; Ullah, I.; Li, H.; Levula, A.; Khurshid, K. Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey. Sensors 2022, 22, 1094. [Google Scholar] [CrossRef] [PubMed]
- Eliyan, L.F.; Di, P.R. DoS and DDoS attacks in Software Defined Networks: A survey of existing solutions and research challenges. Future Gen. Comp. Sys. 2021, 122, 149–171. [Google Scholar] [CrossRef]
- Song, W.; Beshley, M.; Przystupa, K.; Beshley, H.; Kochan, O.; Pryslupskyi, A.; Pieniak, D.; Su, J. A Software Deep Packet Inspection System for Network Traffic Analysis and Anomaly Detection. Sensors 2020, 20, 1637. [Google Scholar] [CrossRef] [PubMed]
- Yang, L.; Fu, S.; Zhang, X.; Guo, S.; Wang, Y.; Yang, C. FlowSpectrum: A concrete characterization scheme of network traffic behavior for anomaly detection. World Wide Web 2022, 25, 2139–2161. [Google Scholar] [CrossRef]
- Breiman, L. Random Forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Kingma, D.P.; Ba, J. Adam: A Method for Stochastic Optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]


| Layername | Layerdesign (Kernel Size, (Padding), Stride) | Output |
|---|---|---|
| Input | 100 × 18, 1 channel | |
| Conv2d_1 | 7 × 7, 3, 1 | 100 × 18, 4 channels |
| Binary_conv2d_1 | 5 × 5, 2, 1 | 100 × 18, 8 channels |
| Conv2d_2 | 5 × 5, 2, 1 | 100 × 18, 16 channels |
| Pooling | 2 × 2, (1,2) | 50 × 9, 16 channels |
| Binary_conv2d_2 | 3 × 3, 1, 1 | 50 × 9, 16 channels |
| GAP | 1 × 1, 16 channels | |
| Dense | 2 |
| Featurename | Role |
|---|---|
| Flow Duration | Helps to identify the abnormal duration of potential DDoS attacks. |
| Total Fwd Packets | Checks for the abnormal increase in total packets sent forward. |
| Total Backward Packets | Checks for the abnormal increase in total packets sent backward. |
| Fwd Packets Length Total | Identifies the large data transfer of potential DDoS attacks. |
| Bwd Packets Length Total | Identifies the large data transfer of potential DDoS attacks. |
| Flow Bytes/s | Monitors the high data rate of potential DDoS attacks. |
| Flow Packets/s | Monitors the high packet rate of potential DDoS attacks. |
| Fwd Packets/s | Checks for the abnormal increase in packet rate sent forward. |
| Bwd Packets/s | Checks for the abnormal increase in packet rate sent backward. |
| Flow IAT Mean | Identifies the abnormal inter-arrival time of potential DDoS attacks. |
| Flow IAT Std | Measures the variation in inter-arrival time, detecting anomalies. |
| Flow IAT Max | Helps to measure the long delay in data packets during potential DDoS attacks. |
| Flow IAT Min | Identifies the short delay of data packets in potential DDoS attacks. |
| SYN Flag Count | Helps to identify the abnormal duration of potential DDoS attacks. |
| FIN Flag Count | Checks for the abnormal increase in total packets sent forward. |
| PSH Flag Count | Checks for the abnormal increase in total packets sent backward. |
| ACK Flag Count | Identifies the large data transfer of potential DDoS attacks. |
| Layername | Layerdesign (Kernel Size, (Padding), Stride) | Output |
|---|---|---|
| Input | 1 × 8, 1 channel | |
| Conv1d_1 | 3, 1, 1 | 1 × 8, 8 channels |
| Conv1d_2 | 3, 1, 1 | 1 × 8, 16 channels |
| Conv1d_3 | 3, 1, 1 | 1 × 8, 32 channels |
| Pooling | 2, 2 | 1 × 4, 32 channels |
| GAP | 1 × 1, 32 channels | |
| Dense | 2 |
| Featurename | Role |
|---|---|
| proto | Protocol Type: Used to identify the protocol type used by the data packet; different protocol types may behave differently in DDoS attacks. |
| total_length | Total Length: The total length of the data packet; unusually large or small packet lengths may be a characteristic of DDoS attacks. |
| ttl | Time to Live: The lifetime of the data packet in the network; abnormal TTL values may indicate abnormal behavior in the network. |
| src_port | Source Port: The port number of the source device; random source port numbers are often used in DDoS attacks. |
| dst_port | Destination Port: The port number of the target device; DDoS attacks typically focus on certain commonly used service ports. |
| seq | Sequence Number: The sequence number in a TCP connection; abnormal sequence numbers may indicate forged data packets. |
| ack | Acknowledgment Number: The acknowledgment number in a TCP connection; abnormal acknowledgment numbers may indicate forged acknowledgment packets. |
| flags | Flags: TCP flag bits; abnormal combinations of flag bits may be a sign of DDoS attacks. |
| window_size | Window Size: The receiving window size; abnormal window sizes may indicate network congestion or attack behavior. |
| udp_total_length | UDP Total Length: The total length of the UDP data packet; abnormal lengths may be a characteristic of DDoS attacks. |
| icmp_type | ICMP Type: The type of ICMP message; certain types of ICMP messages sent in large quantities may be part of a DDoS attack. |
| icmp_code | ICMP Code: The code of the ICMP message; specific ICMP codes may be used to identify attack types. |
| icmp_data_length | ICMP Data Length: The length of the data portion of the ICMP message; abnormal data lengths may indicate the presence of attack behavior. |
| Devices | Parameter |
|---|---|
| CPU | Intel(R) Core(TM) i9-13900HX 2.20 GHz |
| GPU | RTX 4070 Laptop |
| Environment | Python 3.7, PyTorch 2.3.1, Cuda 12.5.78 |
| OS | Ubuntu 18.04.1 |
| Types | Intensive of DDoS Attack | |||||
|---|---|---|---|---|---|---|
| Single Value | 15 | 16 | 17 | 18 | 19 | 20 |
| Interval | 1–3% | 4–7% | 8–10% | 11–14% | ||
| Intensive of DDoS | Acc | Pre | Rec | F1 |
|---|---|---|---|---|
| 1–3% | 0.562 | 0.733 | 0.193 | 0.301 |
| 4–7% | 0.705 | 0.901 | 0.452 | 0.599 |
| 8–10% | 0.832 | 0.902 | 0.744 | 0.813 |
| 11–14% | 0.964 | 0.980 | 0.941 | 0.959 |
| 15% | 0.972 | 0.943 | 1 | 0.971 |
| 16% | 0.963 | 0.942 | 0.982 | 0.961 |
| 17% | 0.971 | 0.943 | 1 | 0.971 |
| 18% | 0.965 | 0.935 | 1 | 0.966 |
| 19% | 0.954 | 0.909 | 1 | 0.952 |
| 20% | 0.965 | 0.935 | 1 | 0.966 |
| Intensive of DDoS | Acc | Pre | Rec | F1 |
|---|---|---|---|---|
| 1–3% | 0.670 | 0.793 | 0.462 | 0.582 |
| 4–7% | 0.896 | 0.908 | 0.885 | 0.896 |
| 8–10% | 0.932 | 0.922 | 0.940 | 0.931 |
| 11–14% | 0.935 | 0.922 | 0.952 | 0.936 |
| 15% | 0.943 | 0.893 | 1 | 0.943 |
| 16% | 0.935 | 0.900 | 0.982 | 0.938 |
| 17% | 0.955 | 0.925 | 0.993 | 0.956 |
| 18% | 0.930 | 0.890 | 0.980 | 0.933 |
| 19% | 0.935 | 0.891 | 0.994 | 0.938 |
| 20% | 0.960 | 0.925 | 1 | 0.961 |
| Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|
| 0.972 | 0.993 | 0.975 | 0.984 |
| Methods | Intensive in Article | Acc.% shown in Article | Acc.% by 10% | Acc.% by 6% |
|---|---|---|---|---|
| φ-entropy [10] | 36 | 100 | 58 | 54.8 |
| Spark Streaming and Flink [27] | 33 | 94.1 | 63.4 | 58.02 |
| DualCNN [26] | 95 | 99.13 | 92.3 | 81 |
| DualRenyi [11] | 30 | 98.2 | 70.2 | 50.4 |
| Ours | None | None | 90.8 | 72.3 |
| Parameters Type | DualCNN | Ours |
|---|---|---|
| Learnable Parameter | 227,132 | 17,916 |
| Size of Model | 886 KB | 213 KB |
| Time Cost (ms) | 0.798 | 0.377 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, K.; Li, Z.; Liang, N.; Kong, F.; Lei, S.; Wang, S.; Paul, A.; Wu, Z. Research on Multi-Layer Defense against DDoS Attacks in Intelligent Distribution Networks. Electronics 2024, 13, 3583. https://doi.org/10.3390/electronics13183583
Xu K, Li Z, Liang N, Kong F, Lei S, Wang S, Paul A, Wu Z. Research on Multi-Layer Defense against DDoS Attacks in Intelligent Distribution Networks. Electronics. 2024; 13(18):3583. https://doi.org/10.3390/electronics13183583
Chicago/Turabian StyleXu, Kai, Zemin Li, Nan Liang, Fanchun Kong, Shaobo Lei, Shengjie Wang, Agyemang Paul, and Zhefu Wu. 2024. "Research on Multi-Layer Defense against DDoS Attacks in Intelligent Distribution Networks" Electronics 13, no. 18: 3583. https://doi.org/10.3390/electronics13183583
APA StyleXu, K., Li, Z., Liang, N., Kong, F., Lei, S., Wang, S., Paul, A., & Wu, Z. (2024). Research on Multi-Layer Defense against DDoS Attacks in Intelligent Distribution Networks. Electronics, 13(18), 3583. https://doi.org/10.3390/electronics13183583






