Decoupling Online Ride-Hailing Services: A Privacy Protection Scheme Based on Decentralized Identity
Abstract
1. Introduction
2. Preliminaries
2.1. Blockchain & Smart Contracts
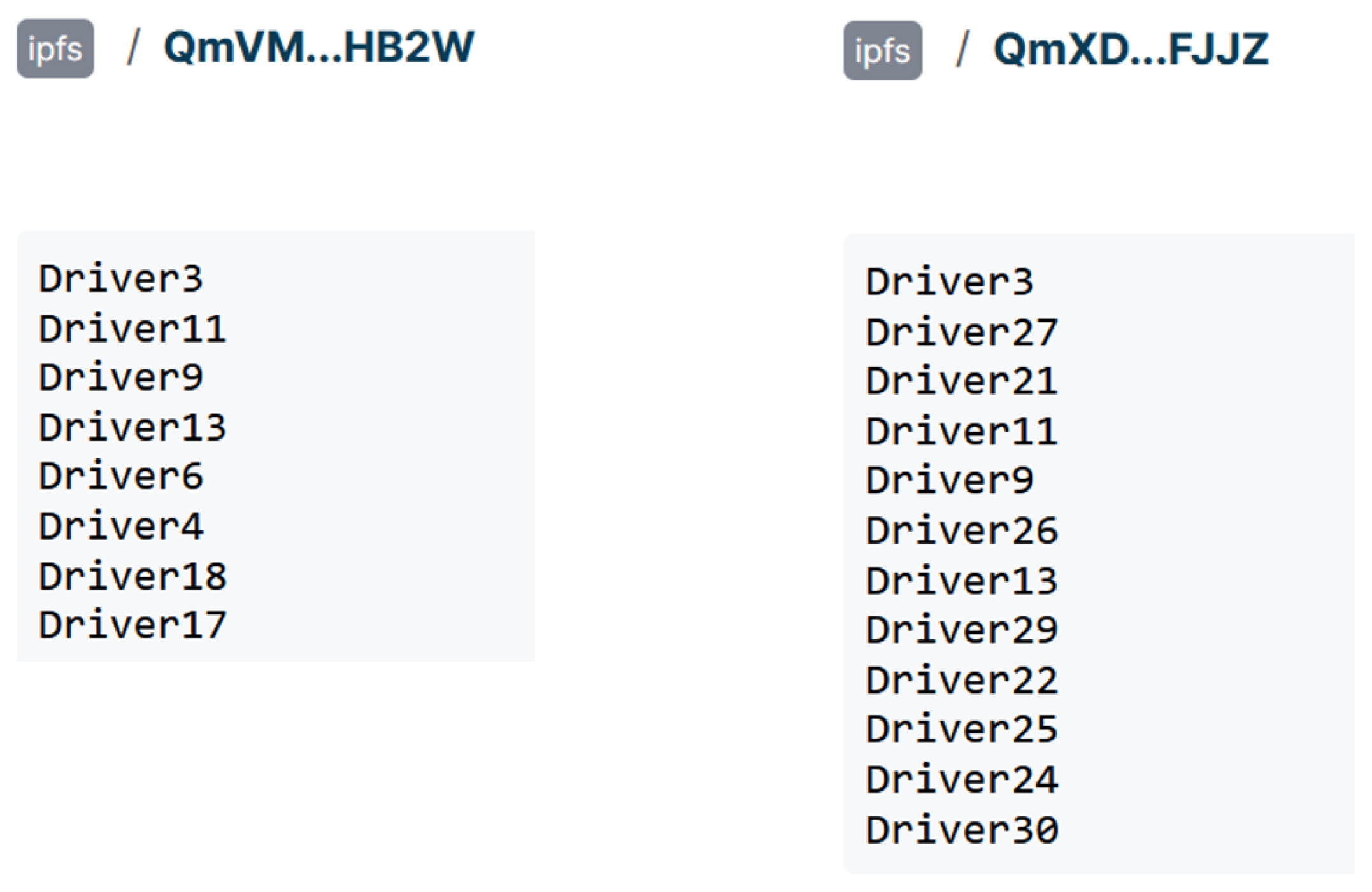
2.2. Decentralized Identity
2.3. MinHash & LSH
2.4. Hybrid Encryption Algorithm
2.5. Spatial Cloaking
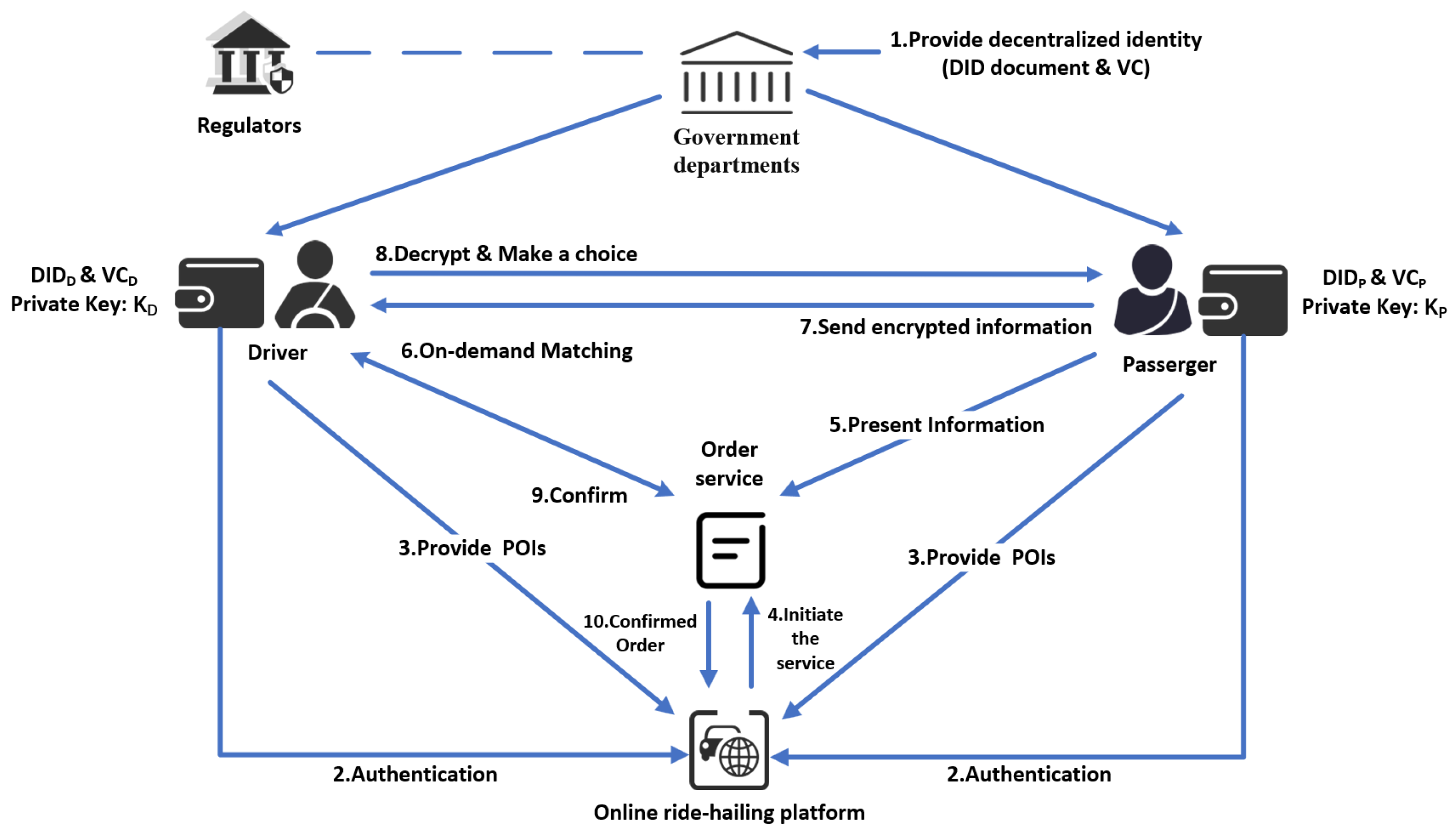
3. Model and Design Goals
3.1. System Model
- Government Departments: Government departments receive and verify users’ identity information, issuing decentralized identities to users. Additionally, they provide digital wallets for managing the aforementioned information.
- Passengers: Passengers submit their current POI and requirement information, offering encrypted location details to drivers who meet their needs.
- Drivers: Drivers submit their current POI information, decrypt passengers’ locations if their attributes match needs, and accept orders.
- Online Ride-hailing Platforms: The ride-hailing platforms aggregate POI information from both passengers and drivers, initiate order matching services to find nearby drivers who meet the requirements, and generate final orders.
- Regulators: As the government entity responsible for criminal investigations, regulators collaborate with government departments and ride-hailing platforms to track drivers and passengers during emergencies by accessing relevant order information. They establish and enforce strict data protection policies to prevent misuse and unauthorized access to sensitive information. Regulators help balance the need for safety and privacy, ensuring that data are accessed only when necessary and for legitimate purposes.
3.2. Design Goals
- Identity Autonomy: Users’ identity information is in their own hands, and they can provide the information required for verification by the online ride-hailing platform based on the principle of data minimization.
- Secure Matching: The platform provides matching services to users without accessing their exact locations, thereby fully protecting their location privacy.
- Uniqueness: Only the driver who meets specific attribute requirements and confirms the order based on the fuzzy location information initially obtained after decryption can obtain the passenger’s accurate location information.
- Service Decoupling: The proposed scheme should separate key services within the online ride-hailing platform that may lead to the association of user data from the platform, protecting user privacy while limiting the power of the online ride-hailing platform.
4. Registration
4.1. Identity Acquisition
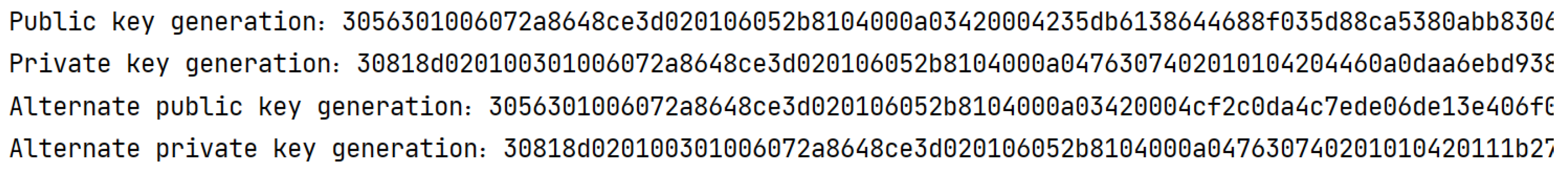
4.1.1. Key Pair Generation
4.1.2. Generation of DID
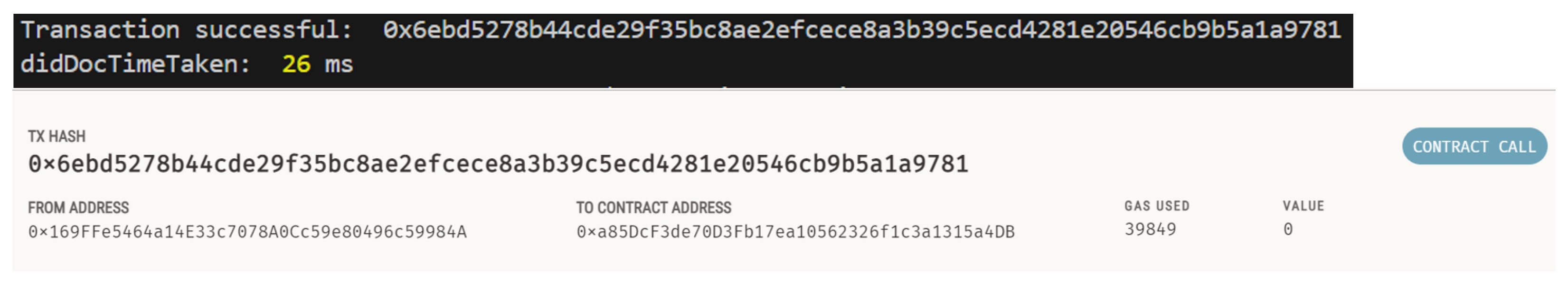
4.1.3. Identity Registration
4.1.4. Generation of DID Document and VC
| Algorithm 1 storeDoc | |
| 1: Input: string ipfsCID, string DID | // User Data |
| 2: struct Document | |
| 3: string ipfsCID; | |
| 4: uint256 timestamp; | // Timestamp of order creation |
| 5: address public owner; | |
| 6: mapping (string => Document)public didDocuments; | //DID -> Document |
| 7: function createDoc(string ipfsCID, string DID) public onlyOwner | |
| 8: add Document(ipfsCID, timestamp) to didDocuments; | |
| 9: function getDetails(string DID) public view returns (Document) | |
| 10: return didDocuments[DID]; | |
4.1.5. Registration Information Return
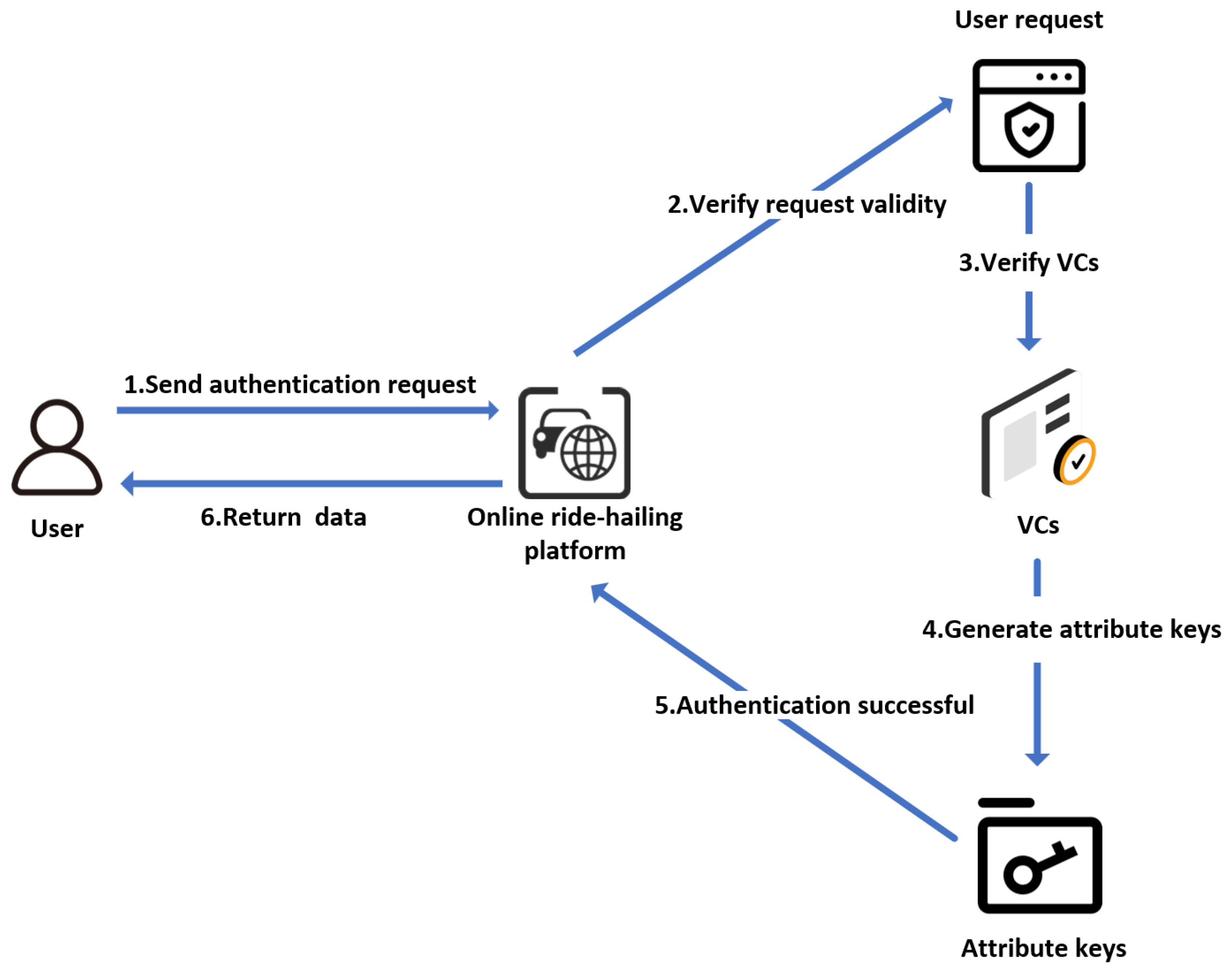
4.2. Authentication
5. Ride-Hailing Platform Services
5.1. Fuzzy Location Information Generation
5.2. Fuzzy Location Matching
| Algorithm 2 fuzzyMatching | |
| 1: Input: Set<User> users | // Users with their current POI |
| 2: Output: drivers nearby | |
| 3: function indexUser(Set<User> users) | |
| 4: for each user in users do | |
| 5: for each band in user’s MinHash signature do | |
| 6: bandHash = Hash(band); | |
| 7: add user to lshBucket according to bandHash; | |
| 8: end for | |
| 9: end for | |
| 10: function findPotentialMatches(User user) | |
| 11: potentialMatches = empty set; | |
| 12: for each band in user’s MinHash signature do | |
| 13: bandHash = Hash(band); | |
| 14: get lshBucket by bandHash; | |
| 15: for each candidate in lshBucket do | |
| 16: if candidate != passenger | // Not a passenger |
| 17: add candidate to potentialMatches; | |
| 18: end if | |
| 19: end for | |
| 20: end for | |
| 21: return potentialMatches; | |
| 22: function findMatchesForPassenger(User passenger) | |
| 23: potentialMatches = findPotentialMatches(passenger); | |
| 24: sort potentialMatches by similarity score; | |
| 25: return nearby results; | |
5.3. Demand Matching and Order Generation
5.3.1. Initialization
5.3.2. Key Generation
5.3.3. Encryption
5.3.4. Decryption
| Algorithm 3 createOrder | |
| 1: Input: string ipfsCID | // Order identifier |
| 2: struct Order | |
| 3: string ipfsCID; | |
| 4: uint256 timestamp; | // Timestamp of order creation |
| 5: mapping(uint => Order)public orders; | // Map of orders |
| 6: function createOrder(string ipfsCID) public onlyOwner | |
| 7: add Order(ipfsCID, currentTime) to orders; | |
| 8: function getOrder(uint orderId) public view returns (Order) | |
| 9: return orders[orderId]; | |
6. Performance Analysis
6.1. Security Analysis
- Threat: Potential attackers can trace all transaction information of a specific user stored on the blockchain to analyze the user’s location information, and then infer the user’s personal privacy.Resist Threat: To better protect the privacy of users, both drivers and passengers provide a collection of POI representing their current locations to the platform. The passenger’s encrypted location information will be sent to each eligible driver through end-to-end encryption technology. Only the driver who accepts the order can access the precise location of the passenger. The online ride-hailing platform can only obtain fuzzy information about the starting point for ride matching but cannot obtain any data related to the destination. This design ensures that transactions stored on the blockchain by the platform are not linked to the user’s complete travel information, thereby effectively preventing potential attackers from analyzing user privacy through on-chain transaction orders.
- Threat: Drivers might use multiple platform accounts to await incoming orders, then select the most advantageous ride request for themselves.Resist Threat: By using DIDs for authentication, the uniqueness and immutability of a DID ensure that each driver can only have one DID associated with their identity. In order to address the problem of drivers authenticating on multiple online ride-hailing platforms to increase the chance of receiving orders, this scheme defines the driver’s current status within the “service” field in the DID document. Once the driver starts accepting orders on any platform, the status in serviceEndpoint will change from ‘available’ to ‘busy’. All platforms verify the driver’s current status before accepting orders, and only drivers marked as “available” can accept orders. This effectively prevents drivers from using multiple accounts to accept more orders, thus enhancing service quality.
- Threat: If the passenger’s encrypted location only includes precise coordinates, it would enable all drivers who meet the specified attributes to access the exact location, potentially increasing the security risks for the passenger during the pick-up and drop-off processes.Resist Threat: Considering user experience for both parties, this scheme matches drivers near passengers based on fuzzy location information. Subsequently, it identifies a suitable group of drivers according to the requirements provided by the passengers and provides the passengers’ encrypted location data. Drivers decide whether or not to accept the order based on the preliminary decrypted POI of the passenger’s destination. Critically, this process ensures that both parties have autonomy in their choices, while guaranteeing that only the driver who ultimately accepts the order receives the passenger’s precise location information.
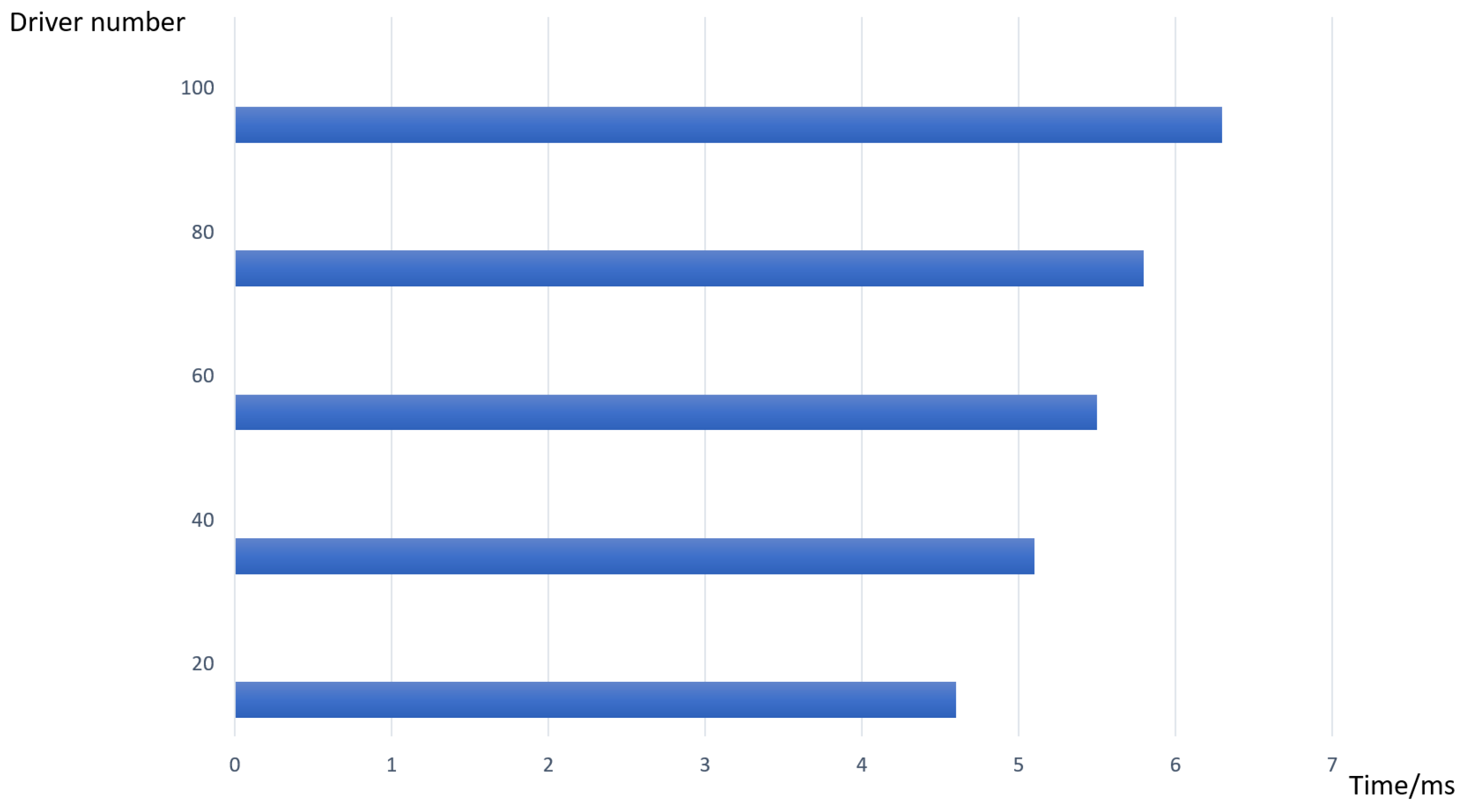
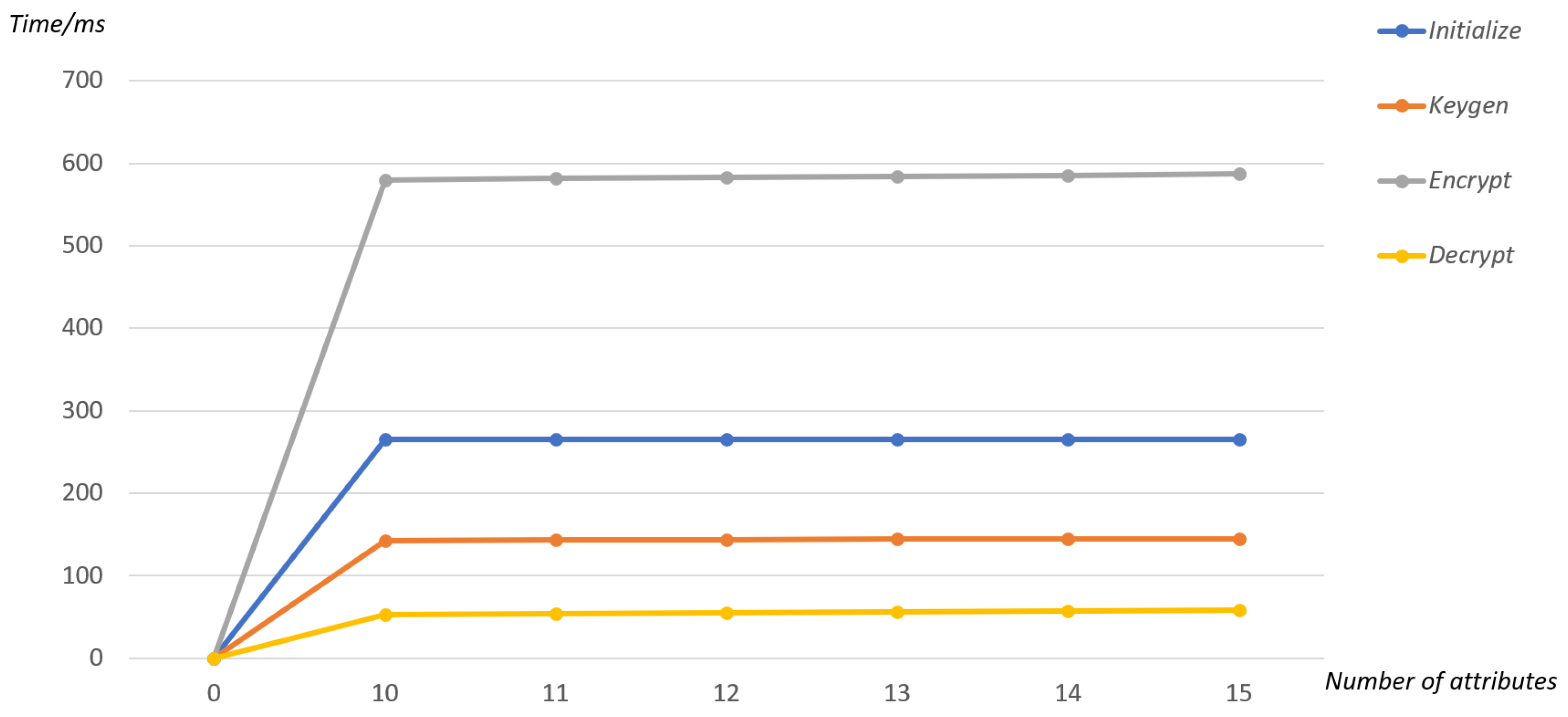
6.2. Experimental Analysis
6.3. Performance Comparison
7. Analysis and Discussion
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ma, N.F.; Hanrahan, B.V. Unpacking sharing in the peer-to-peer economy: The impact of shared needs and backgrounds on ride-sharing. Proc. ACM Hum.-Comput. Interact. 2020, 4, 1–19. [Google Scholar] [CrossRef]
- Zhang, W.; Zhong, S. Data Legal Supervision of Online Car-Hailing Platform Based on Big Data Technology and Edge Computing. Wirel. Commun. Mob. Comput. 2022, 2022, 5298152. [Google Scholar] [CrossRef]
- Tibken, S. Uber Accused of Tracking Celebs, Politicians. Available online: https://www.cnet.com/news/privacy/uber-lawsuit-alleges-startup-tracked-celebs-politicians/ (accessed on 18 September 2024).
- Canivel, R.S.C. Uber PH Confirms Data of Filipino Users among Those Hacked— NPC. Available online: https://technology.inquirer.net/69763/breaking-internet-hacking-uber-national-privacy-commission-breach-personal-information/ (accessed on 18 September 2024).
- Chow, C.Y.; Mokbel, M.F. Enabling private continuous queries for revealed user locations. In International Symposium on Spatial and Temporal Databases; Springer: Berlin/Heidelberg, Germany, 2007; pp. 258–275. [Google Scholar]
- Hengartner, U. Hiding location information from location-based services. In Proceedings of the 2007 International Conference on Mobile Data Management, Mannheim, Germany, 1 May 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 268–272. [Google Scholar]
- Houerbi, K.R.; Machfar, D.; Ayed, H.K.B. Blockchain for Ridesharing: A Systematic Literature Review. In Proceedings of the 2023 International Conference on Smart Applications, Communications and Networking (SmartNets), Istanbul, Turkiye, 25–27 July 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Renu, S.A.; Banik, B.G. Implementation of a secure ridesharing DApp using smart contracts on Ethereum blockchain. Int. J. Saf. Secur. Eng. 2021, 11, 167–173. [Google Scholar]
- Fadhil, M.; Sukarno, P.; Wardana, A.A. Decentralized Privacy-Preserving Solution Through Blockchain Smart Contracts and Spatial Cloaking for Ride Sharing Application. In Science and Information Conference; Springer: Cham, Switzerland, 2024; pp. 377–395. [Google Scholar]
- Shawon, S.K.; Ahammad, H.; Shetu, S.Z.; Rahman, M.; Hossain, S.A. DIUcerts DApp: A blockchain-based solution for verification of educational certificates. In Proceedings of the 2021 12th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kharagpur, India, 6–8 July 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–10. [Google Scholar]
- Gulati, H.; Huang, C.T. Self-sovereign dynamic digital identities based on blockchain technology. In Proceedings of the 2019 SoutheastCon, Huntsville, AL, USA, 11–14 April 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Salem, S.H.G.; Hassan, A.Y.; Moustafa, M.S.; Hassan, M.N. Blockchain-based biometric identity management. Clust. Comput. 2024, 27, 3741–3752. [Google Scholar] [CrossRef]
- Feher, K. Digital identity and the online self: Footprint strategies–An exploratory and comparative research study. J. Inf. Sci. 2021, 47, 192–205. [Google Scholar] [CrossRef]
- Haque, A.B.; Bhushan, B.; Dhiman, G. Conceptualizing smart city applications: Requirements, architecture, security issues, and emerging trends. Expert Syst. 2022, 39, e12753. [Google Scholar] [CrossRef]
- Wang, F.; De Filippi, P. Self-sovereign identity in a globalized world: Credentials-based identity systems as a driver for economic inclusion. Front. Blockchain 2020, 2, 28. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Ni, J.; Zhang, N.; Shen, X. Blockchain-empowered space-air-ground integrated networks: Opportunities, challenges, and solutions. IEEE Commun. Surv. Tutorials 2021, 24, 160–209. [Google Scholar] [CrossRef]
- Sánchez, D.; Martínez, S.; Domingo-Ferrer, J. Co-utile P2P ridesharing via decentralization and reputation management. Transp. Res. Part Emerg. Technol. 2016, 73, 147–166. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Zhang, Y. Privacy-preserved pseudonym scheme for fog computing supported internet of vehicles. IEEE Trans. Intell. Transp. Syst. 2017, 19, 2627–2637. [Google Scholar] [CrossRef]
- Pham, A.; Dacosta, I.; Jacot-Guillarmod, B.; Huguenin, K.; Hajar, T.; Tramèr, F.; Gligor, V.; Hubaux, J.P. Privateride: A privacy-enhanced ride-hailing service. Proc. Priv. Enhancing Technol. 2017, 2017, 38–56. [Google Scholar] [CrossRef]
- Hong, Y.; Yang, L.; Xiong, Z.; Kanhere, S.S.; Jiang, H. OCHJRNCHAIN: A blockchain-based security data sharing framework for online car-hailing journey. IEEE Trans. Intell. Transp. Syst. 2024, 25, 5299–5311. [Google Scholar] [CrossRef]
- Shen, X.; Wang, Z.; Wang, B.; Wang, L.; Pei, Q. A Privacy-Preserving Ride-Matching Scheme Without a Trusted Third-Party Server. IEEE Syst. J. 2023, 17, 6413–6424. [Google Scholar] [CrossRef]
- Pham, A.; Dacosta, I.; Endignoux, G.; Pastoriza, J.R.T.; Huguenin, K.; Hubaux, J.P. ORide: A Privacy-Preserving yet Accountable Ride-Hailing Service. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1235–1252. [Google Scholar]
- Maram, D.; Malvai, H.; Zhang, F.; Jean-Louis, N.; Frolov, A.; Kell, T.; Lobban, T.; Moy, C.; Juels, A.; Miller, A. Candid: Can-do decentralized identity with legacy compatibility, sybil-resistance, and accountability. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1348–1366. [Google Scholar]
- Kang, M.; Lemieux, V. A decentralized identity-based blockchain solution for privacy-preserving licensing of individual-controlled data to prevent unauthorized secondary data usage. Ledger 2021, 6, 126–151. [Google Scholar] [CrossRef]
- Javed, I.T.; Alharbi, F.; Bellaj, B.; Margaria, T.; Crespi, N.; Qureshi, K.N. Health-ID: A blockchain-based decentralized identity management for remote healthcare. Healthcare 2021, 9, 712. [Google Scholar] [CrossRef]
- Stockburger, L.; Kokosioulis, G.; Mukkamala, A.; Mukkamala, R.R.; Avital, M. Blockchain-enabled decentralized identity management: The case of self-sovereign identity in public transportation. Blockchain Res. Appl. 2021, 2, 100014. [Google Scholar] [CrossRef]
- Nakamoto, S.; Bitcoin, A. A Peer-To-Peer Electronic Cash System. Bitcoin 2008, 4, 15. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 18 September 2024).
- Ali, V.; Norman, A.A.; Azzuhri, S.R.B. Characteristics of blockchain and its relationship with trust. IEEE Access 2023, 11, 15364–15374. [Google Scholar] [CrossRef]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Paper 2014, 3, 2-1. [Google Scholar]
- Dutta, P.; Choi, T.M.; Somani, S.; Butala, R. Blockchain technology in supply chain operations: Applications, challenges and research opportunities. Transp. Res. Part Logist. Transp. Rev. 2020, 142, 102067. [Google Scholar] [CrossRef]
- Raja Santhi, A.; Muthuswamy, P. Influence of blockchain technology in manufacturing supply chain and logistics. Logistics 2022, 6, 15. [Google Scholar] [CrossRef]
- Brunner, C.; Gallersdörfer, U.; Knirsch, F.; Engel, D.; Matthes, F. Did and vc: Untangling decentralized identifiers and verifiable credentials for the web of trust. In Proceedings of the 2020 3rd International Conference on Blockchain Technology and Applications, Xi’an China, 14–16 December 2020; pp. 61–66. [Google Scholar]
- W3C. DID Specification Registries. Available online: https://www.w3.org/TR/did-spec-registries/ (accessed on 18 September 2024).
- W3C. Decentralized Identifiers (DIDs) v1.0. Available online: https://www.w3.org/TR/did-core/ (accessed on 18 September 2024).
- W3C. Verifiable Credentials Data Model v1.1. Available online: https://www.w3.org/TR/vc-data-model/ (accessed on 18 September 2024).
- Broder, A.Z.; Charikar, M.; Frieze, A.M.; Mitzenmacher, M. Min-wise independent permutations. J. Comput. Syst. Sci. 1998, 60, 327–336. [Google Scholar] [CrossRef]
- Indyk, P.; Motwani, R. Approximate nearest neighbors: Towards removing the curse of dimensionality. In Proceedings of the Thirtieth Annual ACM Symposium on Theory of Computing, Dallas, TX, USA, 24–26 May 1998; pp. 604–613. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 321–334. [Google Scholar]
- Abdullah, A.M. Advanced encryption standard (AES) algorithm to encrypt and decrypt data. Cryptogr. Netw. Secur. 2017, 16, 11. [Google Scholar]
- Gruteser, M.; Grunwald, D. Anonymous usage of location-based services through spatial and temporal cloaking. In Proceedings of the 1st International Conference on Mobile Systems, Applications and Services, San Francisco, CA, USA, 5–8 May 2003; pp. 31–42. [Google Scholar]
- Gedik, B.; Liu, L. Protecting location privacy with personalized k-anonymity: Architecture and algorithms. IEEE Trans. Mob. Comput. 2007, 7, 1–18. [Google Scholar] [CrossRef]
- Fang, X.; Wu, Y. Investigation into the elliptic curve cryptography. In Proceedings of the 2017 3rd International Conference on Information Management (ICIM), Chengdu, China, 21–23 April 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 412–415. [Google Scholar]
- Koblitz, N. An elliptic curve implementation of the finite field digital signature algorithm. In Proceedings of the Advances in Cryptology—CRYPTO’98: 18th Annual International Cryptology Conference, Santa Barbara, CA, USA, 23–27 August 1998; Proceedings 18. Springer: Berlin, Germany, 1998; pp. 327–337. [Google Scholar]
- Niwattanakul, S.; Singthongchai, J.; Naenudorn, E.; Wanapu, S. Using of Jaccard coefficient for keywords similarity. In Proceedings of the International Multiconference of Engineers and Computer Scientists, Hongkong, China, 13–15 March 2013; Volume 1, pp. 380–384. [Google Scholar]


| Parameter | Definition |
|---|---|
| context | W3C organization requirements |
| id | User’s DID |
| controller | Entity with the right to modify |
| verificationMethod | Structured data objects required for verification |
| authentication | Authorization signature |
| assertionMethod | Issue VC |
| capabilityDelegation | Authority delegation |
| keyAgreement | End-to-end communication key |
| service | Related services |
| Parameter | Definition |
|---|---|
| Random integers | |
| The public parameters | |
| Random group element | |
| Set of integers | |
| System’s public key | |
| M | Plaintext message |
| System’s master key | |
| Attribute private key | |
| S | Source parameter on the group |
| Symmetric key | |
| Attribute value hash mapping to group element | |
| U | Secret key attribute collection |
| T | Access tree |
| n | Leaf node attributes |
| Ciphertext | |
| Secret shard during Encryption and Decryption |
| Executor | Pattern | Operations | Time (ms) |
|---|---|---|---|
| Government department | off-chain | DID document generation | 2 |
| off-chain | Store to IPFS | 70 | |
| on-chain | Store CID | 26 | |
| Online ride-hailing platform | off-chain | Authentication | 5 |
| User | off-chain | Key generation | 140 |
| off-chain | DID generation | 12 | |
| off-chain | Sign | 3 |
| Scheme | Protect User (Driver & Passenger) Privacy | User Anonymity | User Autonomy | Emergency Response | Complete Decoupling of Key Services |
|---|---|---|---|---|---|
| Fadhil et al. [9] | yes | no | no | yes | no |
| Sánchez et al. [17] | yes | no | no | yes | no |
| Pham et al. [19] | no | yes | no | no | no |
| Shen et al. [21] | yes | yes | no | no | no |
| Pham et al. [22] | yes | no | no | yes | no |
| Our scheme | yes | yes | yes | yes | yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, N.; Liu, Y.; Zhang, Y.; Liu, Y. Decoupling Online Ride-Hailing Services: A Privacy Protection Scheme Based on Decentralized Identity. Electronics 2024, 13, 4060. https://doi.org/10.3390/electronics13204060
Sun N, Liu Y, Zhang Y, Liu Y. Decoupling Online Ride-Hailing Services: A Privacy Protection Scheme Based on Decentralized Identity. Electronics. 2024; 13(20):4060. https://doi.org/10.3390/electronics13204060
Chicago/Turabian StyleSun, Nigang, Yuxuan Liu, Yuanyi Zhang, and Yining Liu. 2024. "Decoupling Online Ride-Hailing Services: A Privacy Protection Scheme Based on Decentralized Identity" Electronics 13, no. 20: 4060. https://doi.org/10.3390/electronics13204060
APA StyleSun, N., Liu, Y., Zhang, Y., & Liu, Y. (2024). Decoupling Online Ride-Hailing Services: A Privacy Protection Scheme Based on Decentralized Identity. Electronics, 13(20), 4060. https://doi.org/10.3390/electronics13204060







