6Trace: An Effective Method for Active IPv6 Topology Discovery
Abstract
1. Introduction
- We propose 6Trace, an innovative tool for large-scale IPv6 network topology discovery. 6Trace leverages a stateless asynchronous scanning mechanism, enabling efficient and scalable probing. A core feature of 6Trace is its feedback-based, bisection-like probing strategy, which dynamically optimizes TTL value adjustments, achieves high-speed probing, minimizes redundancy, and reduces local network load. This design significantly mitigates the impact of large-scale topology discovery on network performance, making it an effective and scalable solution for IPv6 probing.
- Through extensive real-world experiments using diverse seed sets, we demonstrate that 6Trace achieves a 70% improvement in scanning efficiency on average. This enhancement enables faster, more comprehensive, and resource-efficient topology discovery compared to existing state-of-the-art methods for IPv6 network measurement.
- This study is the first to systematically analyze biases in network topology discovery results. Our findings reveal that targeting Network Service Providers (NSPs) and Internet Service Providers (ISPs) uncovers significantly more extensive topology information compared to other network categories. These results provide actionable insights for selecting optimal target sets to meet varying scanning requirements, thereby improving the accuracy and relevance of future IPv6 network measurement research.
2. Related Work
2.1. IPv6 Topology Discovery
2.2. IPv6 Hitlists
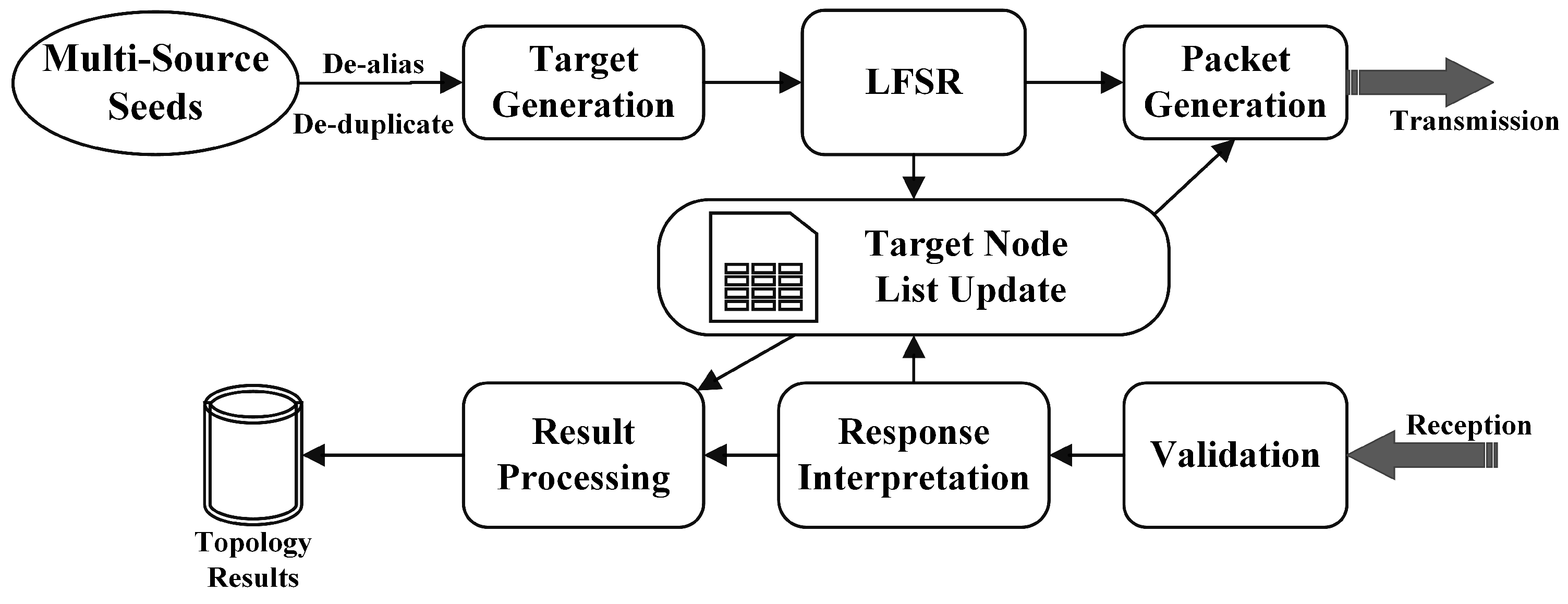
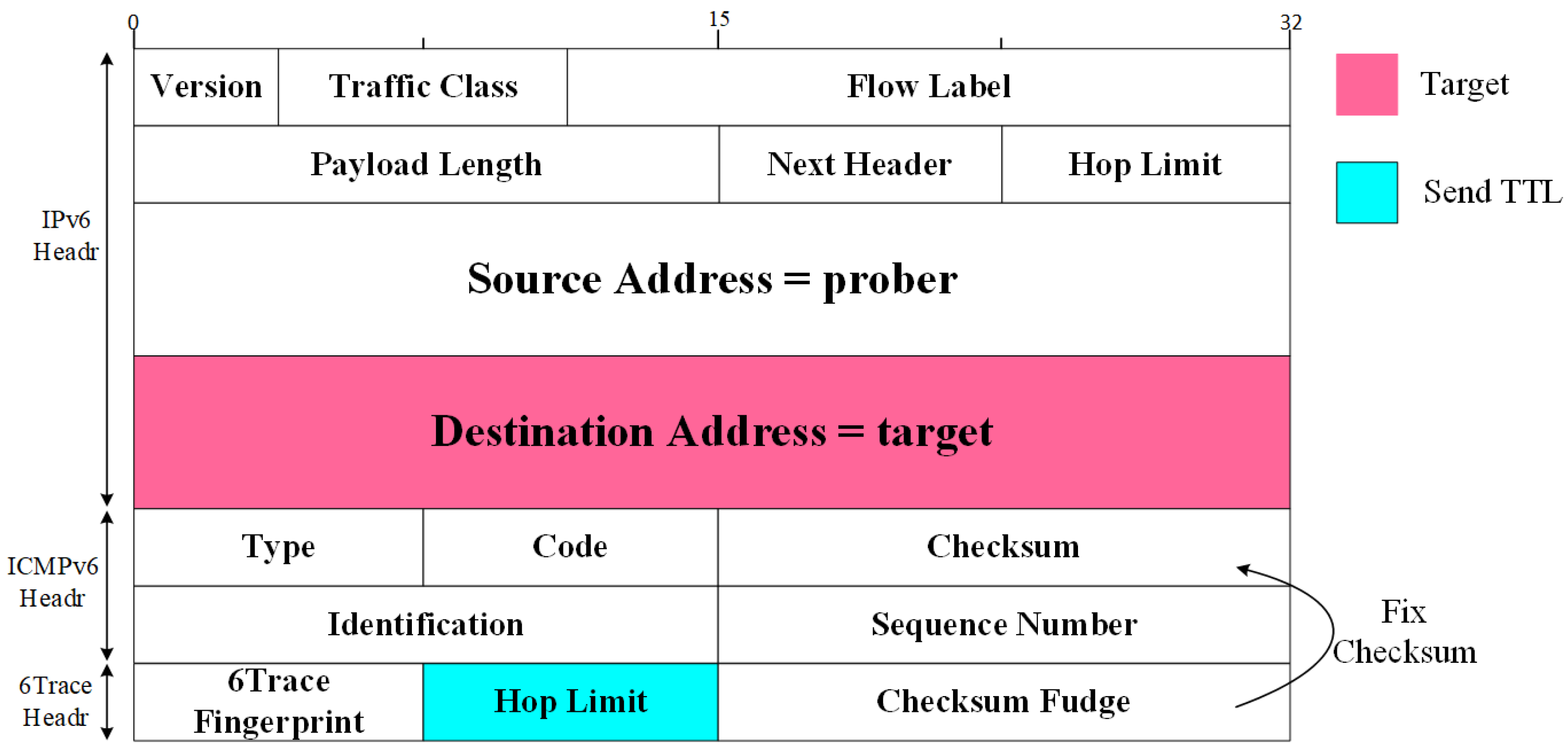
3. Design of 6Trace
3.1. Overview of 6Trace
3.2. Regional State Encoding Technique
3.3. Probe Order
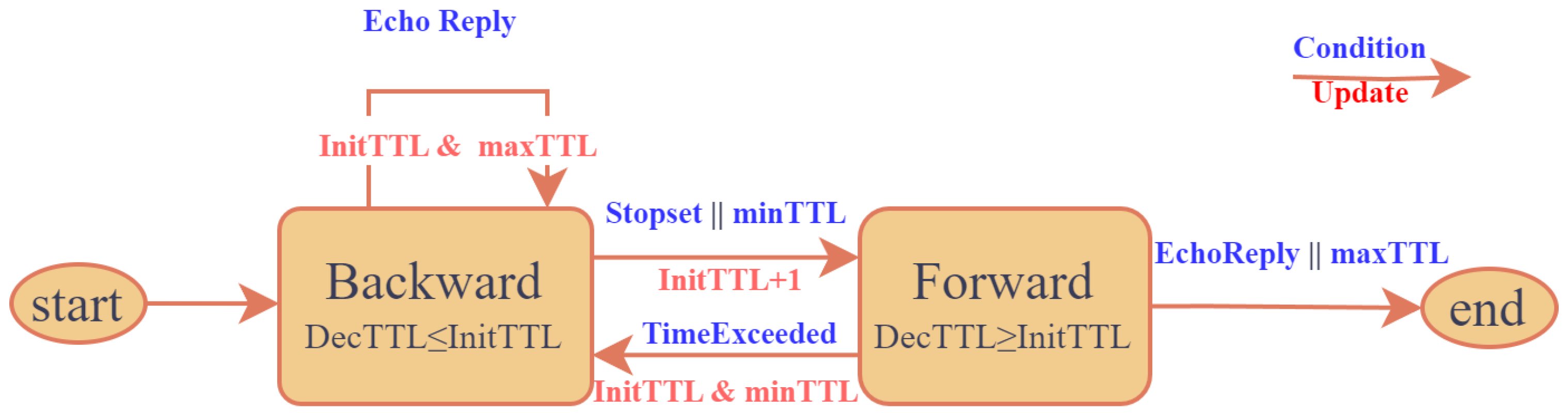
3.4. Probing Strategy
| Algorithm 1 Update strategy for receiving threads |
| Input: ResponsePacket, TN(Target Node) Output: Updated TN
|
3.5. Computational and Memory Requirements
4. Target Select
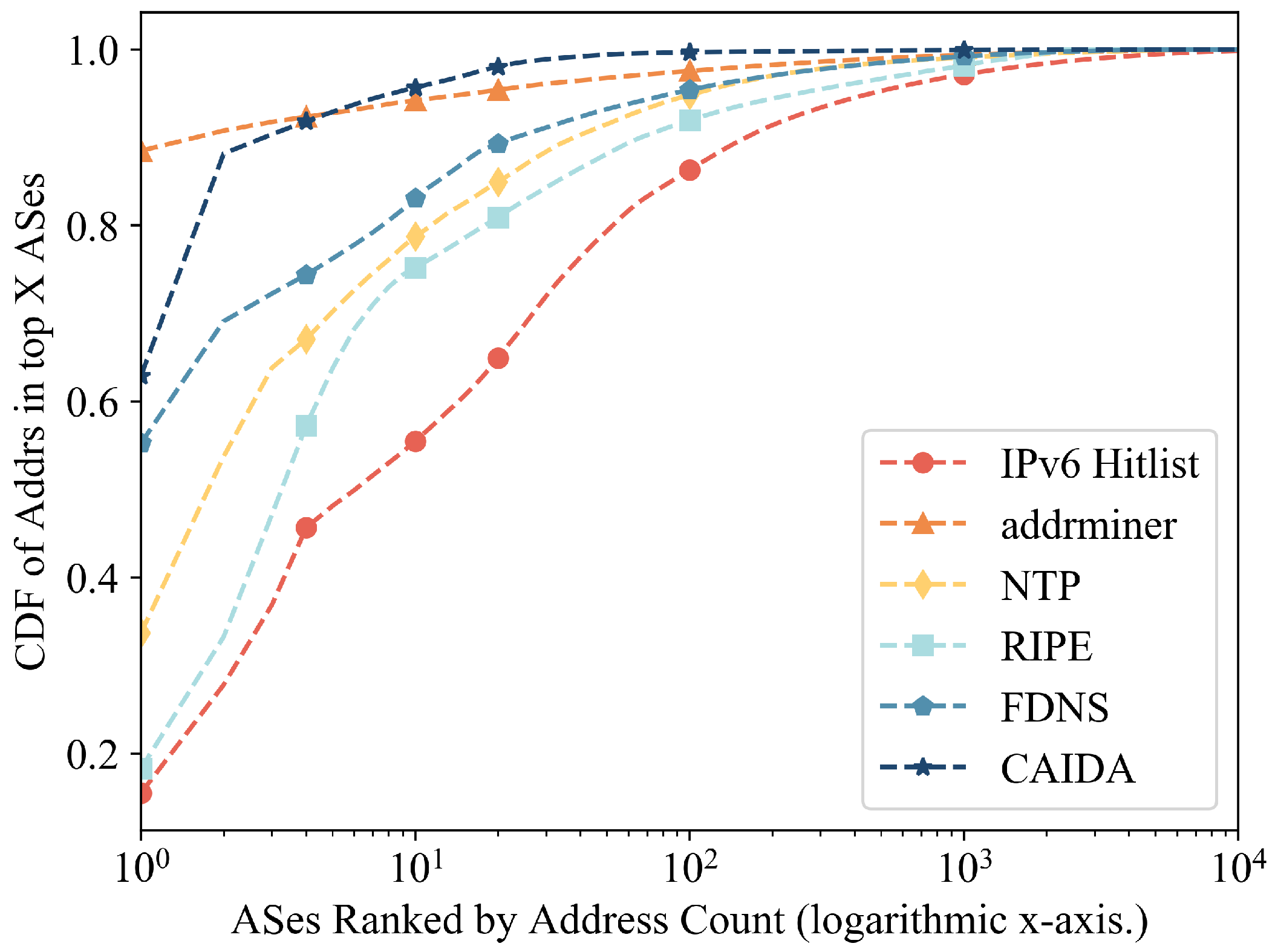
4.1. Multi-Source Seeds Collection
4.2. Characterization
4.2.1. AS Distribution
4.2.2. Network Type Distribution
4.3. Target Generation
5. Performance Evaluation
5.1. Experimental Setup
5.2. Evaluation Metrics
- Number of Discovered Interface Addresses: This metric represents the total number of unique interface addresses discovered during the probing process. To ensure fairness in comparison, ICMP reply addresses were excluded from this count to avoid bias in favor of ICMP-based tools.
- Scanning efficiency: Scanning efficiency was defined as the ratio of discovered interface addresses to the total number of probes sent. A higher scanning efficiency indicates that the tool achieved better performance with fewer probes, reflecting the effectiveness of mechanisms like dynamic probing strategies and redundancy reduction.
- Probing Time: This metric measures the total time required to complete the probing process at a specified probing rate. It provides insight into the overall speed of the topology discovery method and highlights its scalability for large-scale network environments.
5.3. Impact of Configuration Parameters
5.3.1. InitTTL Range
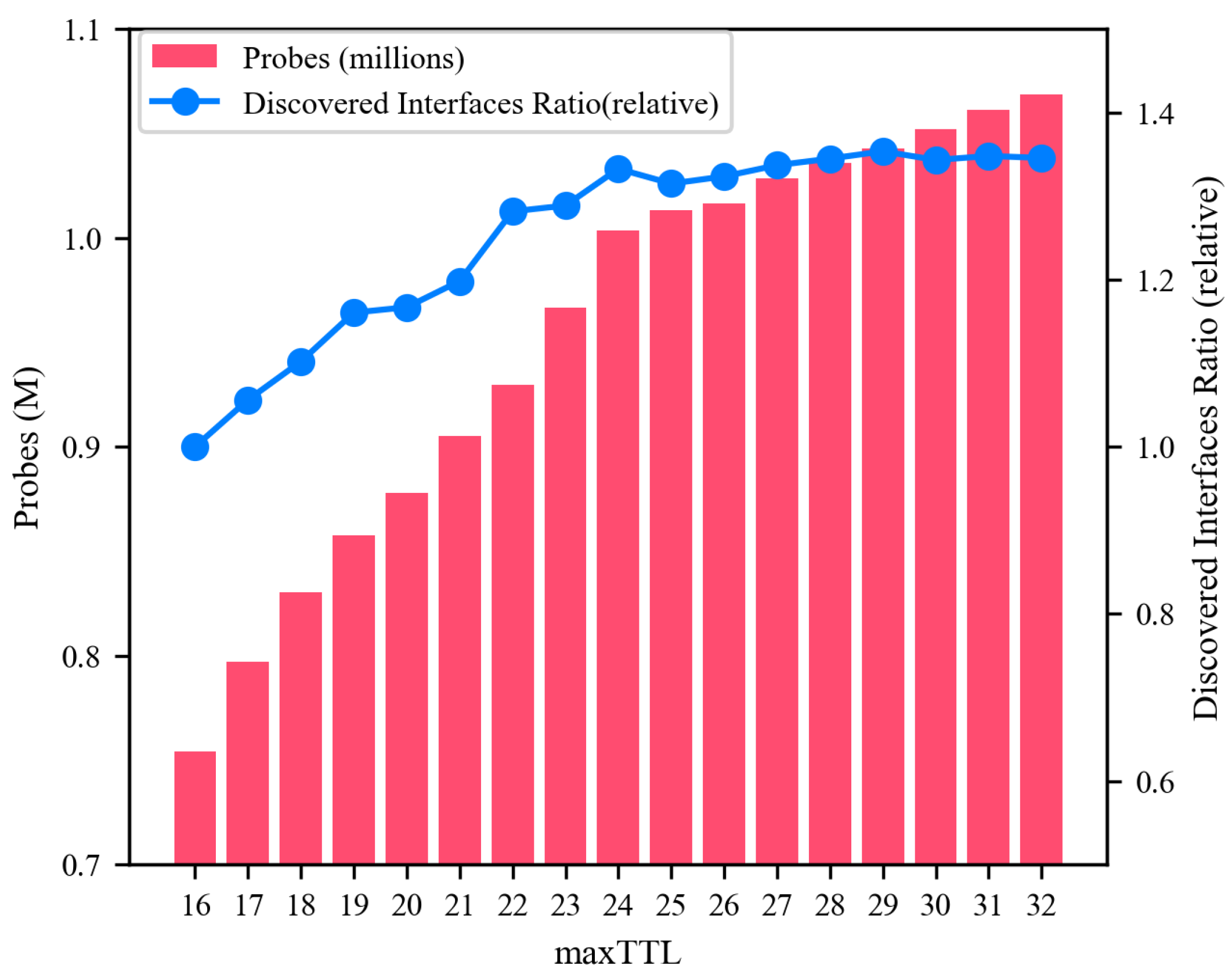
- Maximizing discovery accuracy by focusing on the most active TTL values, as indicated by response distributions.
- Avoiding redundant probes near the source by setting a sufficiently large lower bound, especially in densely connected regions.
- Preventing unnecessary probing beyond intended targets by limiting the upper bound, which minimizes resource overhead and scan duration.
5.3.2. maxTTL
5.4. Comparison with Existing Solutions
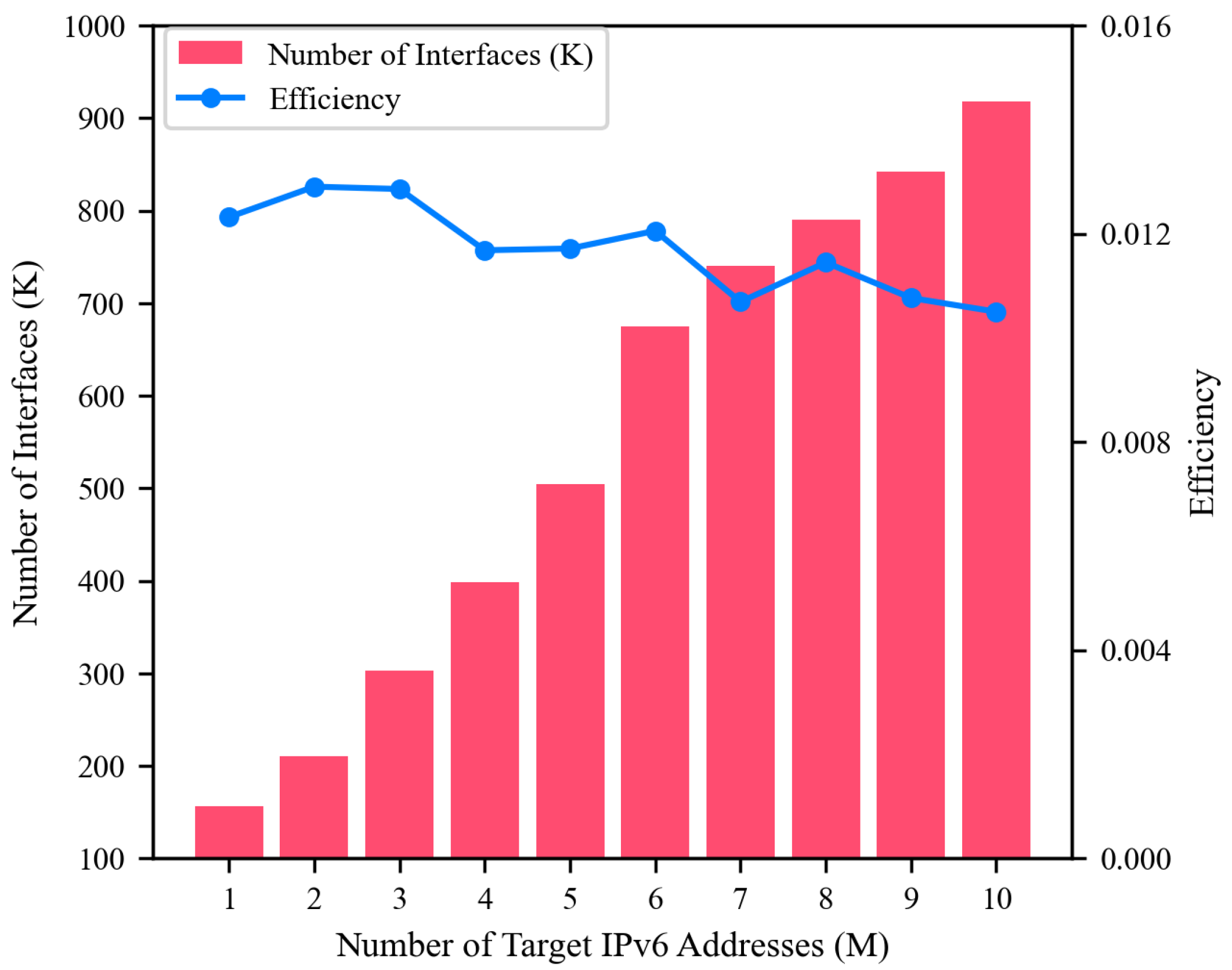
5.5. Scalability Evaluation for Larger IPv6 Target Sets
5.6. Impact of Different Network Categories on Seed Sets
6. Discussion
6.1. Insights from Experimental Results
6.2. Limitations and Challenges
6.3. Future Work
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Google. IPv6 Adoption Statistics. 2024. Available online: https://www.google.com/intl/en/ipv6/statistics.html (accessed on 15 July 2024).
- Dahlmanns, M.; Heidenreich, F.; Lohmöller, J.; Pennekamp, J.; Wehrle, K.; Henze, M. Unconsidered Installations: Discovering IoT Deployments in the IPv6 Internet. In Proceedings of the NOMS 2024–2024 IEEE Network Operations and Management Symposium, Seoul, Republic of Korea, 6–10 May 2024; pp. 1–8. [Google Scholar]
- Sanchez-Navarro, I.; Mamolar, A.S.; Wang, Q.; Calero, J.M.A. 5GTopoNet: Real-time topology discovery and management on 5G multi-tenant networks. Future Gener. Comput. Syst. 2021, 114, 435–447. [Google Scholar] [CrossRef]
- Wang, B.; Zhao, F. Computer networking trends: From generalizing to scenario-specific customizing. Inf. Countermeas. Technol. 2023, 2, 113–122. (In Chinese) [Google Scholar]
- Soltani, S.; Amanlou, A.; Shojafar, M.; Tafazolli, R. Security of Topology Discovery Service in SDN: Vulnerabilities and Countermeasures. IEEE Open J. Commun. Soc. 2024, 5, 3410–3450. [Google Scholar] [CrossRef]
- Wu, J.; Dong, F.; Leung, H.; Zhu, Z.; Zhou, J.; Drew, S. Topology-aware federated learning in edge computing: A comprehensive survey. ACM Comput. Surv. 2024, 56, 1–41. [Google Scholar] [CrossRef]
- Canbaz, M.A. Internet Topology Mining: From Big Data to Network Science. Ph.D. Thesis, University of Nevada, Reno, NV, USA, 2018. [Google Scholar]
- Wang, Z.; Li, Z.; Liu, G.; Chen, Y.; Wu, Q.; Cheng, G. Examination of WAN traffic characteristics in a large-scale data center network. In Proceedings of the 21st ACM Internet Measurement Conference, Online, 2–4 November 2021; pp. 1–14. [Google Scholar]
- Basat, R.B.; Einziger, G.; Gong, J.; Moraney, J.; Raz, D. q-MAX: A unified scheme for improving network measurement throughput. In Proceedings of the Internet Measurement Conference, Amsterdam, The Netherlands, 21–23 October 2019; pp. 322–336. [Google Scholar]
- Li, R.; Makhijani, K.; Dong, L. New IP: A data packet framework to evolve the Internet. In Proceedings of the 2020 IEEE 21st International Conference on High Performance Switching and Routing (HPSR), Newark, NJ, USA, 11–14 May 2020; pp. 1–8. [Google Scholar]
- Beverly, R. Yarrp’ing the Internet: Randomized high-speed active topology discovery. In Proceedings of the 2016 Internet Measurement Conference, Santa Monica, CA, USA, 14–16 November 2016; pp. 413–420. [Google Scholar]
- Huang, Y.; Rabinovich, M.; Al-Dalky, R. Flashroute: Efficient traceroute on a massive scale. In Proceedings of the ACM Internet Measurement Conference, Pittsburgh, PA, USA, 27–29 October 2020; pp. 443–455. [Google Scholar]
- Conta, A.; Deering, S.; Gupta, M. Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification; Technical Report RFC 4443; Internet Engineering Task Force: Fremont, CA, USA, 2006. [Google Scholar]
- Pan, L.; Yang, J.; He, L.; Wang, Z.; Nie, L.; Song, G.; Liu, Y. Your router is my prober: Measuring ipv6 networks via icmp rate limiting side channels. arXiv 2022, arXiv:2210.13088. [Google Scholar]
- Beverly, R.; Durairajan, R.; Plonka, D.; Rohrer, J.P. In the IP of the beholder: Strategies for active IPv6 topology discovery. In Proceedings of the Internet Measurement Conference 2018, Boston, MA, USA, 31 October–2 November 2018; pp. 308–321. [Google Scholar]
- Liu, N.; Jia, C.; Hou, B.; Hou, C.; Chen, Y.; Cai, Z. 6Search: A reinforcement learning-based traceroute approach for efficient IPv6 topology discovery. Comput. Netw. 2023, 235, 109987. [Google Scholar] [CrossRef]
- Luo, Z.; Liu, J.; Yang, G.; Zhang, Y.; Hang, Z. High-Speed Path Probing Method for Large-Scale Network. Sensors 2022, 22, 5650. [Google Scholar] [CrossRef]
- Yang, T.; Cai, Z. Efficient IPv6 router interface discovery. In Proceedings of the IEEE INFOCOM 2024—IEEE Conference on Computer Communications, Vancouver, BC, Canada, 20–23 May 2024; pp. 1641–1650. [Google Scholar]
- Augustin, B.; Cuvellier, X.; Orgogozo, B.; Viger, F.; Friedman, T.; Latapy, M.; Magnien, C.; Teixeira, R. Avoiding traceroute anomalies with Paris traceroute. In Proceedings of the 6th ACM SIGCOMM Conference on Internet Measurement, Rio de Janeriro, Brazil, 25–27 October 2006; pp. 153–158. [Google Scholar]
- Jin, Y.; Renganathan, S.; Ananthanarayanan, G.; Jiang, J.; Padmanabhan, V.N.; Schroder, M.; Calder, M.; Krishnamurthy, A. Zooming in on wide-area latencies to a global cloud provider. In Proceedings of the ACM Special Interest Group on Data Communication, Beijing, China, 19–23August 2019; pp. 104–116. [Google Scholar]
- Shavitt, Y.; Shir, E. DIMES: Let the Internet measure itself. ACM Sigcomm Comput. Commun. Rev. 2005, 35, 71–74. [Google Scholar] [CrossRef]
- Donnet, B.; Raoult, P.; Friedman, T.; Crovella, M. Efficient algorithms for large-scale topology discovery. In Proceedings of the 2005 ACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems, Orlando, FL, USA, 19–23 June 2005; pp. 327–338. [Google Scholar]
- Augustin, B.; Friedman, T.; Teixeira, R. Multipath tracing with Paris traceroute. In Proceedings of the 2007 Workshop on End-to-End Monitoring Techniques and Services, Munch, Germany, 21 May 2007; pp. 1–8. [Google Scholar]
- Durumeric, Z.; Wustrow, E.; Halderman, J.A. {ZMap}: Fast internet-wide scanning and its security applications. In Proceedings of the 22nd USENIX Security Symposium (USENIX Security 13), Washington, DC, USA, 14–16 August 2013; pp. 605–620. [Google Scholar]
- Gasser, O.; Scheitle, Q.; Foremski, P.; Lone, Q.; Korczynski, M.; Strowes, S.D.; Hendriks, L.; Carle, G. Clusters in the Expanse: Understanding and Unbiasing IPv6 Hitlists. In Proceedings of the 2018 Internet Measurement Conference, New York, NY, USA, 31 October–2 November 2018. [Google Scholar] [CrossRef]
- Song, G.; Yang, J.; Wang, Z.; He, L.; Lin, J.; Pan, L.; Duan, C.; Quan, X. Det: Enabling efficient probing of ipv6 active addresses. IEEE/ACM Trans. Netw. 2022, 30, 1629–1643. [Google Scholar] [CrossRef]
- Liu, C.; Li, R.; Ding, S.; Liu, Y.; Luo, X. 6Subpattern: Target Generation Based on Subpattern Analysis for Internet-Wide IPv6 Scanning. IEEE Trans. Netw. Serv. Manag. 2024, 21, 3692–3710. [Google Scholar] [CrossRef]
- Cui, T.; Gou, G.; Xiong, G.; Liu, C.; Fu, P.; Li, Z. 6GAN: Ipv6 multi-pattern target generation via generative adversarial nets with reinforcement learning. In Proceedings of the IEEE INFOCOM 2021-IEEE Conference on Computer Communications, Vancouver, BC, Canada, 10–13 May 2021; pp. 1–10. [Google Scholar]
- Williams, G.; Pearce, P. Seeds of Scanning: Exploring the Effects of Datasets, Methods, and Metrics on IPv6 Internet Scanning. In Proceedings of the 2024 ACM on Internet Measurement Conference, Madrid, Spain, 4–6 November 2024; pp. 295–313. [Google Scholar]
- Jiao, L.; Zhu, Y.; Zhang, W.; Zhao, L.; Zhou, Y.; Liu, Q. 6GAI: Active IPv6 Address Generation via Adversarial Training with Leaked Information. In Proceedings of the 2024 27th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Tianjin, China, 8–10 May 2024; pp. 1079–1085. [Google Scholar]
- Li, X.; Liu, B.; Zheng, X.; Duan, H.; Li, Q.; Huang, Y. Fast IPv6 network periphery discovery and security implications. In Proceedings of the 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Taipei, Taiwan, 21–24 June 2021; pp. 88–100. [Google Scholar]
- PeeringDB. PeeringDB Dataset. Available online: https://catalog.caida.org/dataset/peeringdb (accessed on 4 May 2024).
- Steger, L.; Kuang, L.; Zirngibl, J.; Carle, G.; Gasser, O. Target acquired? Evaluating target generation algorithms for IPv6. In Proceedings of the 2023 7th Network Traffic Measurement and Analysis Conference (TMA), Naples, Italy, 26–29 June 2023; pp. 1–10. [Google Scholar]
- Gasser, O.; Scheitle, Q.; Foremski, P.; Lone, Q.; Korczyński, M.; Strowes, S.; Hendriks, L.; Carle, G. IPv6 Hitlist Service. 2024. Available online: https://ipv6hitlist.github.io/ (accessed on 17 June 2024).
- Song, G.; Yang, J.; He, L.; Wang, Z.; Li, G.; Duan, C.; Liu, Y.; Sun, Z. AddrMiner: A Comprehensive Global Active IPv6 Address Discovery System. In Proceedings of the 2022 USENIX Annual Technical Conference (USENIX ATC 22), Carlsbad, CA, USA, 11–13 July 2022; pp. 309–326. [Google Scholar]
- Rye, E.; Levin, D. Ipv6 hitlists at scale: Be careful what you wish for. In Proceedings of the ACM SIGCOMM 2023 Conference, New York, NY, USA, 10–14 September 2023; pp. 904–916. [Google Scholar]
- RIPE NCC. RIPE Atlas. 2014–2024. Available online: https://atlas.ripe.net/ (accessed on 17 April 2024).
- Rapid7. Forward DNS Datasets. 2017–2021. Available online: https://scans.io/study/sonar.fdns_v2 (accessed on 17 April 2024).
- CAIDA. Index of/Datasets/Topology/ark/ipv6/Dns-Names. 2014–2024. Available online: https://publicdata.caida.org/datasets/topology/ark/ipv6/dns-names/ (accessed on 17 June 2024).
- CAIDA. The CAIDA UCSD IPv6 Topology Dataset. 2024. Available online: http://www.caida.org/data/active/ipv6_allpref_topology_dataset.xml (accessed on 17 June 2024).
- Gont, F.; Chown, T. Network Reconnaissance in IPv6 Networks. RFC 7707 (Informational). 2016. Available online: http://www.ietf.org/rfc/rfc7707.txt (accessed on 17 June 2024).
- Rye, E.; Beverly, R.; Claffy, K.C. Follow the scent: Defeating IPv6 prefix rotation privacy. In Proceedings of the 21st ACM Internet Measurement Conference, Online, 2–4 November 2021; pp. 739–752. [Google Scholar]
- Partridge, C.; Allman, M. Ethical considerations in network measurement papers. Commun. ACM 2016, 59, 58–64. [Google Scholar] [CrossRef]


| Name | Date | Num | ASNs | Interface Identifiers (IIDs) | ||||
|---|---|---|---|---|---|---|---|---|
| EUI-64 | Low-Byte | Embed-IPv4 | Byte-Pattern | Randomized | ||||
| IPv6 Hitlists | 17 June 2024 | 23.09 M | 2.01 w | 1.4 M (6.26%) | 8.47 M (36.66%) | 4.05 M (17.54%) | 0.57 M (2.46%) | 8.34 M (36.12%) |
| Addrminer’s Hitlists | April 2024 | 5.90 M | 9.49 k | 17 k (0.30%) | 0.41 M (6.98%) | 109.12 k (1.85%) | 106.99 k (1.81%) | 5.24 M (88.88%) |
| NTP | January 2022– August 2022 | 5.25 M | 7.78 k | 0 (0.00%) | 2.53 M (48.14%) | 0 (0.00%) | 0 (0.00%) | 2.73 M (51.86%) |
| RIPE Atlas | March 2024– April 2024 | 84 k | 2.35 k | 63.98 k (75.72%) | 3.29 k (3.90%) | 0.62 k (0.73%) | 0.12 k (0.15%) | 16.33 k (19.32%) |
| FDNS | November 2017– November 2021 | 6.36 M | 6.07 k | 173.34 k (2.73%) | 716.54 k (11.27%) | 289.61 k (4.55%) | 500.31 k (7.87%) | 4.66 M (73.22%) |
| CAIDA | May 2014– June 2024 | 47.28 M | 6.35 k | 24.39 k (0.05%) | 391.49 k (0.83%) | 42.69 k (0.09%) | 29.41 k (0.06%) | 46.79 M (98.95%) |
| Experimental Setup | Interfaces | Probes | Scan Time | • Scanning Efficiency |
|---|---|---|---|---|
| Flashroute-16 (gaplimit 8) | 106.23 k | 12.14 M | 496 s | 0.0088 |
| Flashroute-32 | 109.18 k | 21.45 M | 895 s | 0.0051 |
| Yarrp-16 (Fill Mode) | 157.81 k | 16.94 M | 684 s | 0.0093 |
| Yarrp-32 | 167.72 k | 32 M | 1278 s | 0.0052 |
| 6Trace-24 | 162.93 k | 9.98 M | 469 s | 0.0163 |
| 6Trace-32 | 164.75 k | 12.48 M | 519 s | 0.0132 |
| Category | Interfaces | Probes | Scanning Efficiency | Median Distance (Target-Origin) |
|---|---|---|---|---|
| CDN | 16.68 k | 1.03 M | 0.0162 | 12 |
| ISP | 209.60 k | 1.18 M | 0.1776 | 15 |
| NSP | 302.40 k | 1.33 M | 0.2274 | 18 |
| ETP | 6.19 k | 1.26 M | 0.0049 | 19 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shen, Z.; Chen, P.; Xie, Y.; Chen, C.; Zhang, Y.; Yang, G. 6Trace: An Effective Method for Active IPv6 Topology Discovery. Electronics 2025, 14, 343. https://doi.org/10.3390/electronics14020343
Shen Z, Chen P, Xie Y, Chen C, Zhang Y, Yang G. 6Trace: An Effective Method for Active IPv6 Topology Discovery. Electronics. 2025; 14(2):343. https://doi.org/10.3390/electronics14020343
Chicago/Turabian StyleShen, Zhaobin, Pan Chen, Yi Xie, Chiyu Chen, Yongheng Zhang, and Guozheng Yang. 2025. "6Trace: An Effective Method for Active IPv6 Topology Discovery" Electronics 14, no. 2: 343. https://doi.org/10.3390/electronics14020343
APA StyleShen, Z., Chen, P., Xie, Y., Chen, C., Zhang, Y., & Yang, G. (2025). 6Trace: An Effective Method for Active IPv6 Topology Discovery. Electronics, 14(2), 343. https://doi.org/10.3390/electronics14020343






