Abstract
In an era where public safety hinges on real-time intelligence and rapid response, this paper delves into the pivotal role of location-based services (LBSs) in empowering law enforcement and fire rescue operations. GPS tracking systems have revolutionized situational awareness and resource management, yet they come with critical security and privacy challenges, including unauthorized access, real-time data interception, and insider threats. To address these vulnerabilities, this study introduces an innovative framework that combines blockchain, artificial intelligence (AI), and IoT technologies to redefine emergency management and public safety systems. Voice-command virtual assistants powered by AI enable hands-free operations, enhance hazard detection, and optimize resource allocation in real time, while blockchain’s decentralized and tamper-proof architecture ensures data integrity and security. By integrating these cutting-edge technologies, the research showcases a system design that not only secures sensitive information but also drives operational efficiency and resilience. With applications spanning smart cities, autonomous systems, and fire rescue operations, this study offers a transformative vision for public safety, emphasizing technology integration, digital innovation, and trust-building. These advancements promise not only to protect responders and communities but also to redefine the standards of security and efficiency in modern emergency management.
1. Introduction
Location-based services (LBSs) have become integral to modern public safety operations, providing real-time tracking capabilities that significantly enhance situational awareness and resource management. These services are crucial for ensuring the safety of law enforcement officers, first responders, and other personnel in the field, as they allow for the precise tracking of movements and timely responses to emergencies. For example, GPS-enabled body trackers are widely used by law enforcement officers to monitor their locations during high-risk operations, providing vital tools for improving operational efficiency and safeguarding personnel [1,2]. Such technologies ensure that officers are always reachable, enabling rapid coordination and decision-making in critical situations. However, this reliance on GPS tracking also introduces substantial privacy and security vulnerabilities. Breaches in these systems can expose sensitive information, such as an officer’s location and mission details, jeopardizing their safety and compromising the success of operations [3]. Moreover, these vulnerabilities can extend beyond the immediate threat to law enforcement personnel, leading to broader repercussions, such as the erosion of public trust in safety agencies and diminished confidence in the effectiveness of public safety infrastructure [4].
In recent years, advanced tools such as voice command virtual assistants have further revolutionized public safety workflows. These technologies enable hands-free interactions, which enhance operational efficiency by streamlining communication and improving response times [5]. ZenextAI, for instance [2], combines voice-driven interfaces with the Internet of Things (IoT) and dynamic location tracking to enhance mission-critical responses [6]. While such innovations offer promising advancements in operational efficiency, they also expand the attack surface, making it increasingly important to implement robust security measures to prevent breaches [7] and protect sensitive data. The integration of emerging technologies like blockchain has been proposed as a solution to ensure the integrity and security of these systems, with applications ranging from secure data sharing and trust management to safeguarding the privacy of vehicular networks [8,9]. Blockchain’s decentralized nature helps to mitigate the risks associated with centralized data storage, making it an ideal tool for enhancing security in public safety systems [10]. However, as these technologies evolve, they also introduce new challenges, necessitating ongoing innovation to maintain a secure and trustworthy environment in the rapidly changing landscape of public safety.
2. Background
The deployment of GPS tracking systems in public safety settings has introduced both significant advantages and vulnerabilities. While GPS-enabled systems provide real-time location data, enabling better situational awareness and resource management, they also create multiple risks. Unauthorized access to these location data can allow adversaries to track officers’ movements, plan ambushes, or exploit predictable patrol patterns, jeopardizing the safety of personnel and the success of law enforcement operations [11]. Moreover, the centralized storage of this data increases its susceptibility to cyberattacks, insider threats, and misuse, highlighting the need for decentralized systems that can mitigate these risks. The integration of the Internet of Things (IoT) devices and AI-driven systems into public safety workflows has further heightened the complexity of these security challenges [5,12]. Each component of these interconnected systems presents a potential vulnerability; a breach within one component can compromise the entire ecosystem, amplifying risks and exposing sensitive operational details to malicious actors [13].
A case study that underscores these risks involves first responders using GPS-enabled devices in hazardous material incidents. In such scenarios, if these systems are compromised, adversaries could manipulate location data, leading to misdirected resources or delayed response times. These breaches highlight the urgent need for robust encryption and authentication mechanisms to protect sensitive data and ensure the integrity of response efforts [8,14]. Real-world scenarios further illustrate both the benefits and risks of location-based services (LBSs) in public safety operations. For instance, high-risk pursuits often rely on GPS tracking to provide real-time updates to command centers, which aids in informed decision-making and strategic planning. However, if the GPS system is compromised, this could reveal officers’ routes to suspects, enabling evasion or ambush [4]. Similarly, during crisis-response situations such as active shooter incidents, GPS-enabled trackers help to coordinate multi-agency efforts by displaying responder locations. A breach in this context could compromise officer and civilian safety, delaying the response or redirecting efforts away from critical areas [9].
In scenarios involving officer distress, body trackers equipped with fall detection or distress alert features are designed to transmit critical location information to dispatch centers. A compromised system could suppress genuine alerts or trigger false alarms, delaying necessary backup and endangering lives [15]. Likewise, in covert operations, GPS systems ensure the safety of undercover officers in hostile environments. Unauthorized access to such data could expose operational plans, missions, and officers’ identities, putting both lives and critical intelligence at risk [16]. These cases underscore the necessity for secure, resilient systems that protect sensitive information against malicious exploitation. Blockchain and AI-driven solutions have been proposed as effective means of securing these systems, offering decentralization and advanced security mechanisms to safeguard sensitive data and maintain the integrity of public safety operations [16,17].
3. Relevant Work and Research Gap
Despite significant advancements in location-based services (LBSs) and their integration with emerging technologies such as artificial intelligence (AI) and blockchain, several critical research gaps persist.
One major gap is the absence of large-scale, real-world evaluations of blockchain-enhanced LBSs in public safety operations. Existing studies primarily focus on theoretical models or isolated pilot programs (Table 1), leaving open questions regarding the scalability, interoperability, and cost-effectiveness of such implementations across diverse operational environments [12,14]. Moreover, while blockchain offers inherent security benefits, there is limited research on its performance under high-stress emergency conditions, where real-time data integrity and low-latency access are crucial [1,17].
Another key research challenge is the human factor aspect of integrating AI and blockchain into emergency response systems. The current literature lacks empirical studies on how first responders, law enforcement officers, and emergency personnel interact with these technologies under dynamic and stressful conditions [11,18]. Understanding user adoption, cognitive load, and system usability in high-pressure situations is essential for ensuring practical deployment and operational effectiveness.
Furthermore, regulatory and ethical considerations remain underexplored. The adoption of blockchain in public safety raises important concerns about data privacy, cross-jurisdictional information sharing, and compliance with legal frameworks such as the General Data Protection Regulation (GDPR) and Criminal Justice Information Services (CJIS) Security Policy [1,16,17]. While blockchain provides transparency and immutability, the challenge of balancing security with individual privacy rights, especially in sensitive law enforcement applications, requires further investigation.
This study seeks to bridge these gaps by presenting a comparative evaluation of blockchain and AI implementations in LBSs for public safety. By focusing on real-world deployments, this research examines their practical utility, scalability, and compliance with regulatory frameworks. The findings aim to provide actionable insights for policymakers, technology developers, and public safety organizations, ensuring the responsible and effective adoption of these technologies [5,6].

Table 1.
Research gaps in GPS tracking security for public safety using blockchain and AI.
Table 1.
Research gaps in GPS tracking security for public safety using blockchain and AI.
| Ref. | Focus Area | Key Insights | Identified Gap |
|---|---|---|---|
| [1] | Blockchain integration in 6G networks to enhance data security and reliability for emerging communication technologies. | Demonstrates AI-driven advancements in 6G security. | Faces scalability challenges due to high computational requirements and network demands. |
| [12] | IoT safety mechanisms using blockchain technology to secure device interactions in real-time environments. | Highlights reliability improvements in IoT safety applications. | Lacks real-world validation under diverse environmental conditions and stress scenarios. |
| [16] | Use of blockchain for autonomous vehicle (AV) security, ensuring trust and transparency in AV networks. | Explores benefits of blockchain-led AV security frameworks. | Identifies an absence of established security standards, impeding consistent implementation. |
| [14] | Enhancing emergency response systems using blockchain technology for faster coordination and data integrity. | Blockchain improves city safety during routine operations. | Exhibits low adaptability to dynamic emergency conditions, such as natural disasters. |
| [17] | Employing AI and IoT systems for traffic management, focusing on predictive analytics for safer transportation. | AI facilitates improved traffic safety and management. | Insufficient privacy analysis regarding personal and vehicle data security in IoT-enabled systems. |
| [19] | Developing lightweight blockchain solutions for vehicular communication networks, particularly in resource-constrained environments. | Emphasizes benefits of efficient fog computing in vehicle networks. | Faces scalability issues in deploying solutions for large-scale vehicular systems. |
| [20] | Exploration of blockchain applications in autonomous vehicle (AV) systems for trust and security. | Highlights diverse blockchain applications for AV operations. | Notes lack of interoperability between existing blockchain frameworks. |
| [21] | Securing drone operations through blockchain-based authentication mechanisms. | Illustrates blockchain’s role in drone security. | Limited by few practical tests conducted to validate theoretical models. |
| [11] | Ensuring location privacy for IoT devices using blockchain solutions to prevent unauthorized tracking. | Discusses privacy improvements via blockchain. | Hindered by low adoption rates among IoT manufacturers. |
| [13] | Trust management in vehicular systems through decentralized blockchain-based frameworks. | Proposes enhanced trust mechanisms using blockchain. | Requires large-scale analysis for practical application. |
| [5] | Integration of 5G technology and blockchain to secure communication in IoT-AV networks. | Details benefits of 5G-enhanced blockchain for AV systems. | Overlooks critical energy efficiency concerns in implementation. |
| [6] | Establishing trust in vehicular networks using blockchain-based decentralized protocols. | Explores blockchain’s role in vehicular trust mechanisms. | Lacks real-world implementation to assess scalability and efficacy. |
| [8] | Designing blockchain security frameworks for smart vehicles to ensure operational safety. | Highlights potential for enhanced vehicle security. | Requires real-world validation to address operational constraints. |
| [3] | Preventing Vehicular Ad Hoc Network (VANET) attacks with blockchain-based trust solutions. | Focuses on VANET attack mitigation strategies. | Confronts interoperability issues in complex VANET environments. |
| [4] | Addressing Internet of Vehicles (IoV) security using blockchain for decentralized trust management. | Enhances trust and transparency in IoV systems. | Faces energy efficiency challenges in resource-intensive environments. |
| [9] | Resource sharing in IoV ecosystems using blockchain-based proof-of-reputation models. | Describes benefits of reputation-based blockchain systems. | Encounters scalability concerns in high-demand IoV networks. |
| [15] | Enabling drone-assisted networks with blockchain for secure communication and coordination. | Examines blockchain’s feasibility in drone networks. | Needs validation of practical feasibility in real-world scenarios. |
| [22] | Incentivizing participation in Intelligent Transportation Systems (ITSs) with blockchain-based reward systems. | Introduces SmartCoin for ITS incentives. | Faces adoption barriers due to technological and economic challenges. |
| [23] | Securing vehicle ID management using blockchain to prevent fraud and identity theft. | Proposes secure ID solutions with blockchain. | Struggles with integration into legacy systems. |
| [10] | Facilitating data sharing in IoV with consortium blockchain for edge computing applications. | Describes edge computing efficiencies via blockchain. | Highlights the need for standardization in data-sharing protocols. |
| [16] | Enhancing autonomous vehicle (AV) security through AI and blockchain collaboration. | Details AI-driven safety improvements in AV systems. | Faces complexities in implementation for integrated systems. |
| [24] | Application of voice-controlled AI in public safety for seamless communication in emergencies. | Discusses AI for emergency responder support. | Limited by broader applicability in diverse emergency scenarios. |
4. Mitigation Strategy
Addressing these vulnerabilities requires an integrated approach to security. End-to-end encryption, such as the Advanced Encryption Standard (AES), is essential to protect data in transit and at rest. For example, secure communication between law enforcement agencies and emergency responders can be facilitated by using AES, ensuring that sensitive information—such as crime data or emergency dispatch instructions—are securely transmitted and stored. Additional safeguards, like envelope encryption, which encrypts data at multiple layers, and role-based access controls (RBACs), ensure that sensitive information is accessible only to authorized personnel [13,19]. For instance, in a public safety system, only specific officers or authorized staff should have access to confidential case files or surveillance footage, mitigating the risks of unauthorized access or data breaches. Implementing real-time anomaly detection through AI-driven analytics can identify and mitigate unauthorized access attempts swiftly. For example, AI algorithms can detect unusual patterns of access in public safety systems, such as a user attempting to access restricted areas of the system outside normal hours or from an unrecognized device [14,17].
Privacy-by-design principles should guide system architecture, emphasizing data minimization and the automatic deletion of outdated information to reduce exposure risks [5,18]. For example, a smart public safety system can be designed to automatically delete video surveillance data after a certain retention period unless the footage is flagged for evidentiary purposes, ensuring that personal data are not unnecessarily exposed. Compliance with industry standards, including CJIS, HIPAA, and PII regulations, ensures adherence to best practices for safeguarding sensitive data. Public–private partnerships can significantly enhance these efforts by leveraging shared expertise and resources. For instance, collaborations between law enforcement agencies and technology firms, such as those that develop cutting-edge encryption protocols and real-time monitoring tools, can further strengthen the security of sensitive public safety data [3,21]. One example is a joint initiative between a major law enforcement agency and a cybersecurity firm to develop encryption protocols that address emerging threats in data transmission.
International standards also play a critical role in mitigation by establishing a unified framework for addressing security challenges. Frameworks such as ISO/IEC 27001 provide comprehensive guidelines for information security management, which can be tailored to the specific needs of public safety organizations. For example, local law enforcement agencies can adopt ISO/IEC 27001 to ensure that their data handling and security practices are up to international standards, while also ensuring compliance with cross-border data protection laws. By adopting these standards, agencies can ensure interoperability and consistency across systems, facilitating cross-border collaboration in combating cyber threats [9,22]. For instance, international collaborations between law enforcement agencies can be streamlined when they adhere to the same security standards, making the sharing of sensitive information, such as criminal records or intelligence data, more secure and efficient.
Training programs tailored for law enforcement personnel further enhance security by equipping users with the skills to recognize and respond to potential threats. For instance, training exercises can simulate a breach in the public safety system, teaching officers how to respond in real time and how to mitigate the damage from a potential data leak or ransomware attack [11,20]. These initiatives can be complemented by workshops and joint exercises with private-sector partners to simulate real-world scenarios and improve response strategies. One example is a workshop conducted by a tech company in partnership with a local police department, where participants simulated a cyberattack on the department’s database and practiced containing the breach.
5. Securing Global Positioning System (GPS) Tracking of First Responders with AI and Blockchain
The deployment of Global Positioning System (GPS) tracking technologies for first responders has revolutionized public safety operations by enabling real-time situational awareness, improving resource allocation, and enhancing responder safety. However, the increasing reliance on these systems introduces critical security vulnerabilities that must be addressed to ensure their continued effectiveness.
5.1. Challenges in Securing GPS
GPS tracking systems, while indispensable, are susceptible to a range of security breaches. Unauthorized access to location data can expose the real-time whereabouts of first responders, potentially leading to ambushes or sabotaged operations. Attackers can exploit predictable movement patterns or disrupt mission-critical communications by manipulating location data. The centralized storage of GPS information further exacerbates the risk, making repositories a prime target for cyberattacks, insider threats, or unauthorized data access.
For instance, a breach in GPS-enabled systems during active shooter incidents could reveal responder positions to perpetrators, endangering lives and compromising operational integrity. Similarly, in search and rescue operations, adversaries could manipulate location data, misdirecting resources and delaying critical assistance. These scenarios highlight the urgent need for robust security mechanisms to protect GPS tracking systems.
5.2. Role of AI in Enhancing GPS Security
Artificial intelligence (AI) provides transformative capabilities to detect and mitigate security threats in GPS tracking systems. AI algorithms can analyze real-time location data streams to identify anomalies indicative of spoofing or tampering. Machine learning models trained on historical movement patterns can detect deviations, flagging potential breaches or operational inconsistencies.
AI-driven predictive analytics also enhance operational decision-making, allowing commanders to preemptively adjust strategies based on threat forecasts. For example, integrating AI with GPS tracking systems enables the automated detection of unsafe areas or compromised routes, ensuring that first responders can avoid high-risk zones.
5.3. Blockchain as a Solution for Data Integrity and Security
Blockchain technology addresses critical security challenges by offering a decentralized, immutable ledger for GPS data. Unlike centralized storage systems, blockchain ensures that location data are securely encrypted and distributed across a network of nodes. This decentralization makes it virtually impossible for adversaries to alter or manipulate data without detection.
In practice, blockchain can log GPS data points with cryptographic hashes, ensuring that any unauthorized changes are immediately identifiable. For example, when a first responder’s location is updated, the corresponding blockchain entry creates a tamper-proof record, preserving the integrity of the data. Furthermore, blockchain-enabled smart contracts can automate data sharing among authorized entities, such as coordinating multi-agency responses during emergencies.
5.4. Integrated AI and Blockchain Solutions
The integration of AI and blockchain creates a synergistic solution to secure GPS tracking systems for first responders. AI models can continuously monitor blockchain logs for suspicious activities, such as unexpected location updates or unauthorized data access attempts. Conversely, blockchain ensures that AI algorithms operate on verified, tamper-proof data, enhancing the reliability of security measures.
In high-stakes scenarios, such as wildfire evacuations or disaster-response operations, these integrated technologies provide a secure and efficient framework for real-time tracking and coordination. By leveraging AI and blockchain, public safety organizations can ensure that sensitive GPS data remain protected against evolving cyber threats, safeguarding both responders and the communities they serve.
5.5. Future Implications and Challenges
While the integration of AI and blockchain in securing GPS tracking offers significant benefits, challenges remain in terms of scalability, interoperability, and cost-effectiveness. Large-scale implementation across diverse public safety agencies requires robust infrastructure and regulatory compliance. Future research must focus on addressing these challenges to ensure that these technologies can be deployed effectively and sustainably in real-world environments.
The adoption of AI and blockchain not only secures GPS tracking systems but also sets a precedent for leveraging emerging technologies to enhance the safety and efficiency of public safety operations. By addressing security vulnerabilities, these innovations pave the way for a more resilient and adaptive public safety ecosystem.
6. The Role of Blockchain in Securing Location-Based Services
Blockchain technology offers a transformative approach to securing LBSs in public safety. Its decentralized nature eliminates single points of failure, reducing vulnerabilities associated with centralized data storage [13]. By distributing location data across a network of nodes, blockchain ensures data integrity through consensus mechanisms. This architecture makes it nearly impossible for a single entity or attacker to manipulate or compromise data.
Blockchain’s immutability provides a tamper-proof record of all location data transactions. This feature enhances accountability, as all access and modifications to sensitive information are transparently logged and verifiable [3]. Smart contracts, an integral component of blockchain technology, can automate compliance with data access policies, ensuring that only authorized entities can retrieve or modify location data.
In practice, blockchain could be integrated with GPS tracking systems to create secure, verifiable records of officer movements and operational activities. For example, during a high-risk operation, blockchain could maintain an immutable log of responder locations [6], ensuring that these data remain secure even if other components of the system are compromised. The transparency afforded by blockchain can facilitate audits and investigations, strengthening trust among public safety agencies and the communities that they serve.
Blockchain has also demonstrated potential in preventing data tampering in IoT-connected devices. For instance, the city of Seoul implemented blockchain for urban public safety systems, integrating it with GPS data to ensure that location updates of emergency vehicles remain untampered during transit. Similarly, pilot programs in Singapore have employed blockchain to create immutable records of responder activities during large-scale events, enabling real-time coordination while safeguarding data integrity. Researchers have further explored its use to secure real-time updates in dynamic location tracking, ensuring seamless and secure communication between devices and centralized databases [9].
7. Proposed Methodology for Implementing a Blockchain- and AI-Driven Fire Rescue System
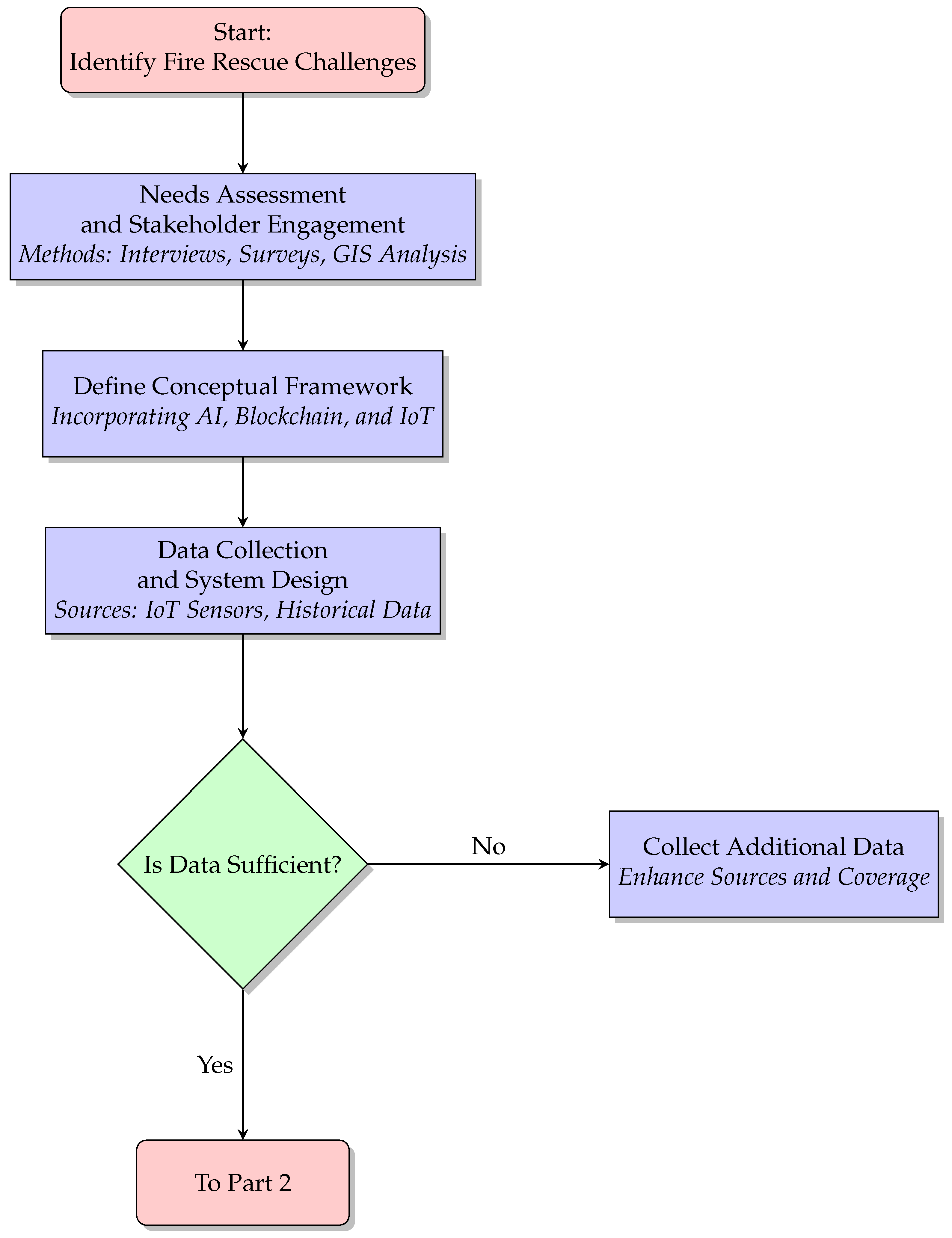
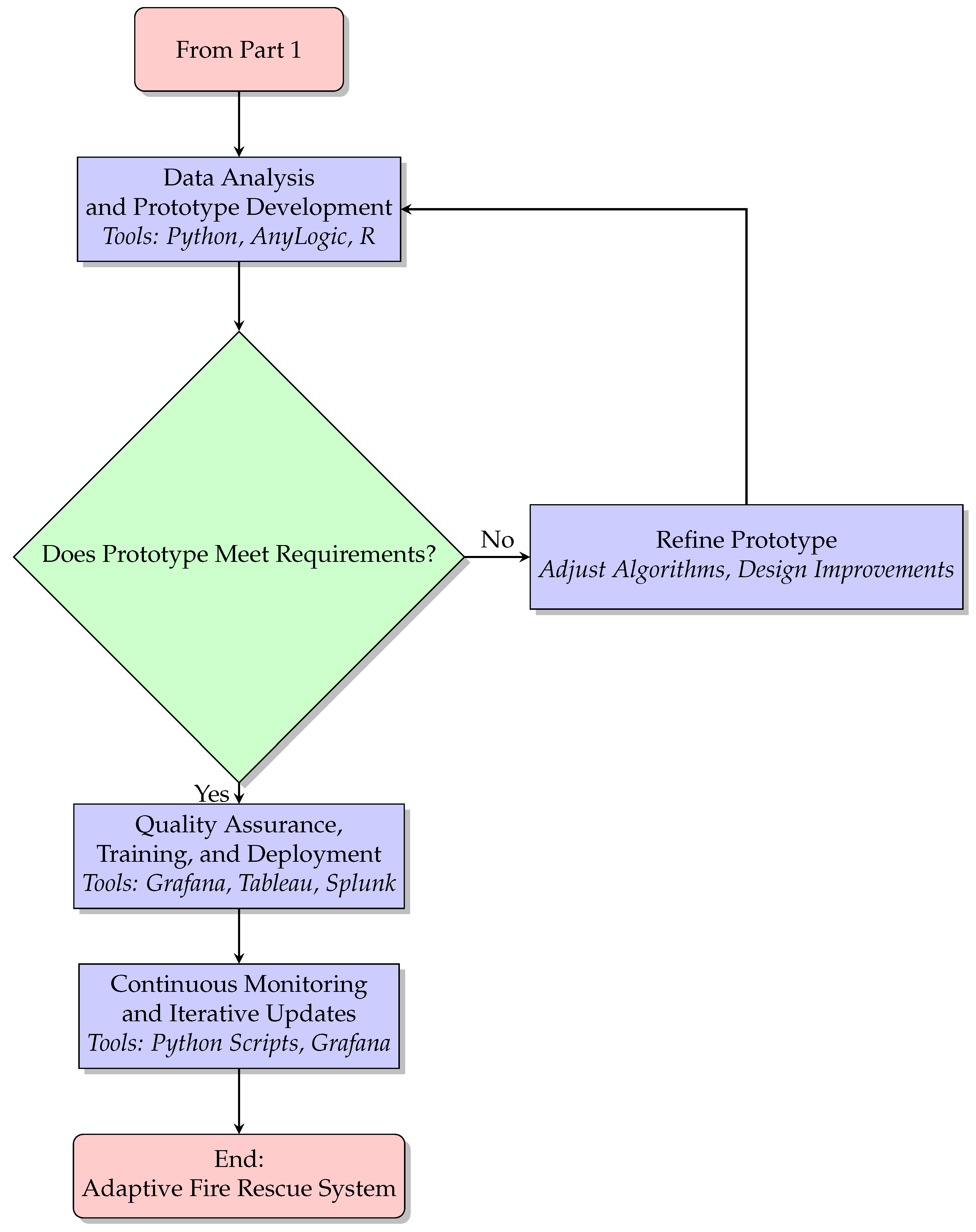
Fire rescue operations demand precise, secure, and rapid decision-making, often under highly dynamic and stressful conditions. The proposed system aims to address inefficiencies in communication, resource allocation, and data security by leveraging blockchain, AI, IoT, and advanced modeling tools. Blockchain will provide secure and immutable data storage, while AI will facilitate predictive analytics for hazard detection and resource optimization. IoT sensors and devices will enhance situational awareness by delivering real-time data streams. These technologies will be integrated within a structured V-Model Simulation Framework, which will ensure that the system is continuously verified and validated at each stage of its lifecycle (Figure 1 and Figure 2). By addressing operational challenges such as communication delays, geospatial data inaccuracies, and security vulnerabilities, the ultimate objective is to deliver a seamless, adaptive solution for fire rescue operations.
Figure 1.
Initial steps in the methodology, including problem identification, stakeholder engagement, framework definition, and data collection (Part 1).
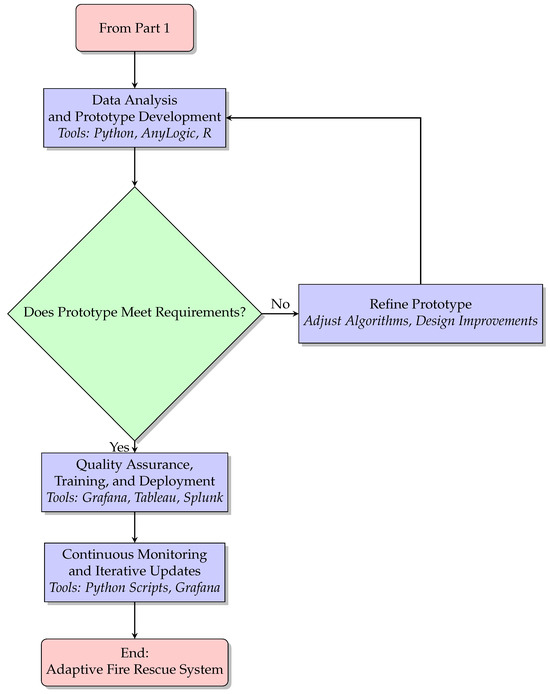
Figure 2.
Additional methodology steps, including analysis, validation, deployment, and monitoring (Part 2).
7.1. Needs Assessment and Stakeholder Engagement
The initial phase of the project will focus on a comprehensive needs assessment to identify the key operational challenges faced by fire rescue teams. Stakeholders, including firefighters, command center operators, and emergency planners, will be engaged through structured interviews and surveys, designed and disseminated using Google Forms. The collected data will be systematically analyzed using Microsoft Excel to identify recurring issues and prioritize them based on their impact and frequency.
A critical aspect of this phase will be analyzing geospatial inefficiencies using ArcGIS. Historical incident data will be overlaid on resource distribution maps to identify discrepancies, such as areas with frequent delays in response times or inadequate coverage. This analysis will provide a detailed understanding of communication delays, resource misallocation, and vulnerabilities in current systems. The outcomes of this phase will include a comprehensive operational requirements document and an evaluation of compatibility gaps in existing infrastructure.
7.2. Data Collection and System Design
The second phase will involve the collection and integration of real-time and historical data to inform system design. IoT devices, including wearable sensors and environmental monitors, will capture parameters such as temperature, air quality, and personnel locations. These real-time data streams will be securely stored and managed using SQLite, ensuring efficient data access and scalability. Historical data from previous fire rescue operations will be analyzed using Python, leveraging libraries such as Pandas and NumPy for preprocessing and feature extraction.
The system architecture will be designed to integrate blockchain, AI, and IoT components seamlessly. Blockchain technology will provide a secure layer for data storage and sharing, while AI algorithms developed using Python libraries will enable advanced analytics for hazard detection and resource allocation. Microsoft Visio will be employed to document the system architecture, providing a clear and comprehensive representation for stakeholders. This phase will lay the foundation for a robust and scalable system capable of addressing diverse operational scenarios.
7.3. Statistical Analysis and Prototype Development
Statistical analysis will play a crucial role in validating the system’s performance. Using Python, descriptive statistics will summarize data trends, while inferential techniques such as hypothesis testing will identify significant patterns in resource allocation and hazard detection. Predictive modeling techniques, including logistic regression and decision trees, will be employed to forecast fire behavior and optimize response strategies.
Prototypes of the system will be developed and tested in simulation environments created using AnyLogic. These simulations will replicate real-world scenarios such as wildfire management and high-rise evacuations, allowing the system’s performance to be evaluated under controlled conditions. Key performance metrics, including latency, fault tolerance, and usability, will be assessed to identify areas for improvement. Feedback from these simulations will be systematically tracked and analyzed using Microsoft Excel to refine the prototype iteratively.
7.4. Quality Control, Training, and Deployment
Quality control will be integral to ensuring the reliability and functionality of the system. Tools such as Grafana will monitor the system’s operational performance in real-time, while Splunk will validate the integrity of generated data. These measures will ensure that the system is both stable and efficient under varying conditions (Figure 2).
To facilitate effective adoption, training modules will be developed to familiarize fire rescue personnel with the system’s functionalities, including its AI-driven dashboards and IoT integrations. Pilot deployments will be conducted in high-risk areas to test the system in real-world conditions. Tableau will be employed to monitor key performance metrics during these pilots, providing insights into system effectiveness and areas for enhancement. Feedback from pilot deployments will guide iterative improvements before full-scale implementation.
7.5. Continuous Monitoring and Iterative Updates
The final phase will focus on ensuring the system’s long-term adaptability and efficiency. IoT sensors will provide continuous real-time performance data, which will be analyzed using Grafana and Splunk to detect anomalies and performance bottlenecks. Updates to the system will be managed using Python scripts to streamline processes and optimize functionality. Regular audits and stakeholder feedback will ensure that the system remains responsive to evolving operational challenges, maintaining its relevance and effectiveness.
8. Understanding How the Proposed V-Model Methodology Functions with Simulations
Fire rescue operations demand precise, secure, and rapid decision-making, often under highly dynamic and stressful conditions. The proposed system aims to address inefficiencies in communication, resource allocation, and data security by leveraging blockchain, AI, IoT, and advanced modeling tools. Blockchain will provide secure and immutable data storage, while AI will facilitate predictive analytics for hazard detection and resource optimization. IoT sensors and devices will enhance situational awareness by delivering real-time data streams. These technologies will be integrated within a structured V-Model Simulation Framework, ensuring continuous verification and validation at each stage of the system’s lifecycle. By addressing operational challenges such as communication delays, geospatial data inaccuracies, and security vulnerabilities, the objective is to deliver a seamless, adaptive solution for fire rescue operations.
8.1. Predictive Analytics for Hazard Detection and Resource Optimization
The AI component of the system uses predictive modeling to optimize resource allocation and hazard detection. Let represent the predicted hazard intensity at time t, where t is time.
This formula models the relationship between environmental factors (such as temperature, humidity, and wind speed) and fire hazard predictions, enabling the system to forecast fire behavior. By predicting the intensity and spread of fire, the system can allocate resources effectively, optimize response strategies, and prioritize high-risk areas for intervention.
8.2. Data Integrity with Blockchain
Blockchain ensures the secure, immutable, and verifiable storage of data. Let D represent a dataset, with each data entry stored as a transaction in the blockchain.
The use of cryptographic hash functions guarantees that each data entry is secure and traceable. As each fire rescue operation generates real-time data, the blockchain ensures that the data remain tamper-proof and transparent to all stakeholders, preventing malicious changes and ensuring data integrity for decision-making.
8.3. System Performance Monitoring and Fault Detection
System performance is continuously monitored using IoT devices and software tools. Let represent the latency at time t, and represent fault tolerance at time t.
where is the total response time for a given set of requests and is the number of requests processed during that time. This formula evaluates the responsiveness of the system by determining how quickly the system processes fire alerts and resource requests. Minimizing latency ensures that emergency response times are kept to a minimum.
where is the number of system failures detected at time t and is the total number of operations attempted at time t. This fault tolerance metric ensures that the system remains reliable and resilient, even in the face of network issues or equipment failures.
8.4. Geospatial Data Analysis
Geospatial inefficiencies are critical in fire rescue operations, especially when responding to incidents in remote or dense urban areas. The Euclidean distance between fire stations and incident locations can be calculated as follows:
where d is the Euclidean distance between a fire station located at and an incident location at . By calculating this distance, the system can identify areas with suboptimal coverage and optimize the positioning of resources to ensure the fastest possible response.
8.5. Feedback-Driven Iterative System Improvement
The system evolves through continuous feedback. Let represent the system performance metric at time t and represent the feedback score.
where is a weighting factor that adjusts the impact of feedback. This formula ensures that the system iteratively improves by incorporating real-world insights from fire rescue personnel, helping to refine algorithms and enhance user experience.
8.6. Simulated Environment for Prototyping
Prototypes are developed and tested in simulation environments. Let represent the output of a simulation at time t, which generates Key Performance Indicators (KPIs) such as fire spread, response time, and resource allocation.
where represents the value of the KPI and represents the weight assigned to each KPI. This formula aggregates multiple KPIs, providing a comprehensive performance score for the simulation, which helps to validate the system before real-world deployment.
8.7. Continuous Updates and System Adaptability
The system’s functionality is continuously optimized through regular updates. Let represent the update vector at time t, which reflects the changes made to system parameters.
where , , and other variables represent changes in performance metrics and operational parameters. This ensures that the system adapts to evolving conditions, optimizing response strategies based on the latest data and feedback.
9. Simulation and Experimental Design
The validation of the proposed AI-enhanced blockchain framework for secure GPS tracking in law enforcement applications will be carried out through a structured experimental framework that integrates synthetic data simulations and real-world prototype deployment. The study aims to evaluate the system under diverse operational conditions, including adversarial environments that introduce GPS spoofing attacks and network congestion.
9.1. Simulation Setup
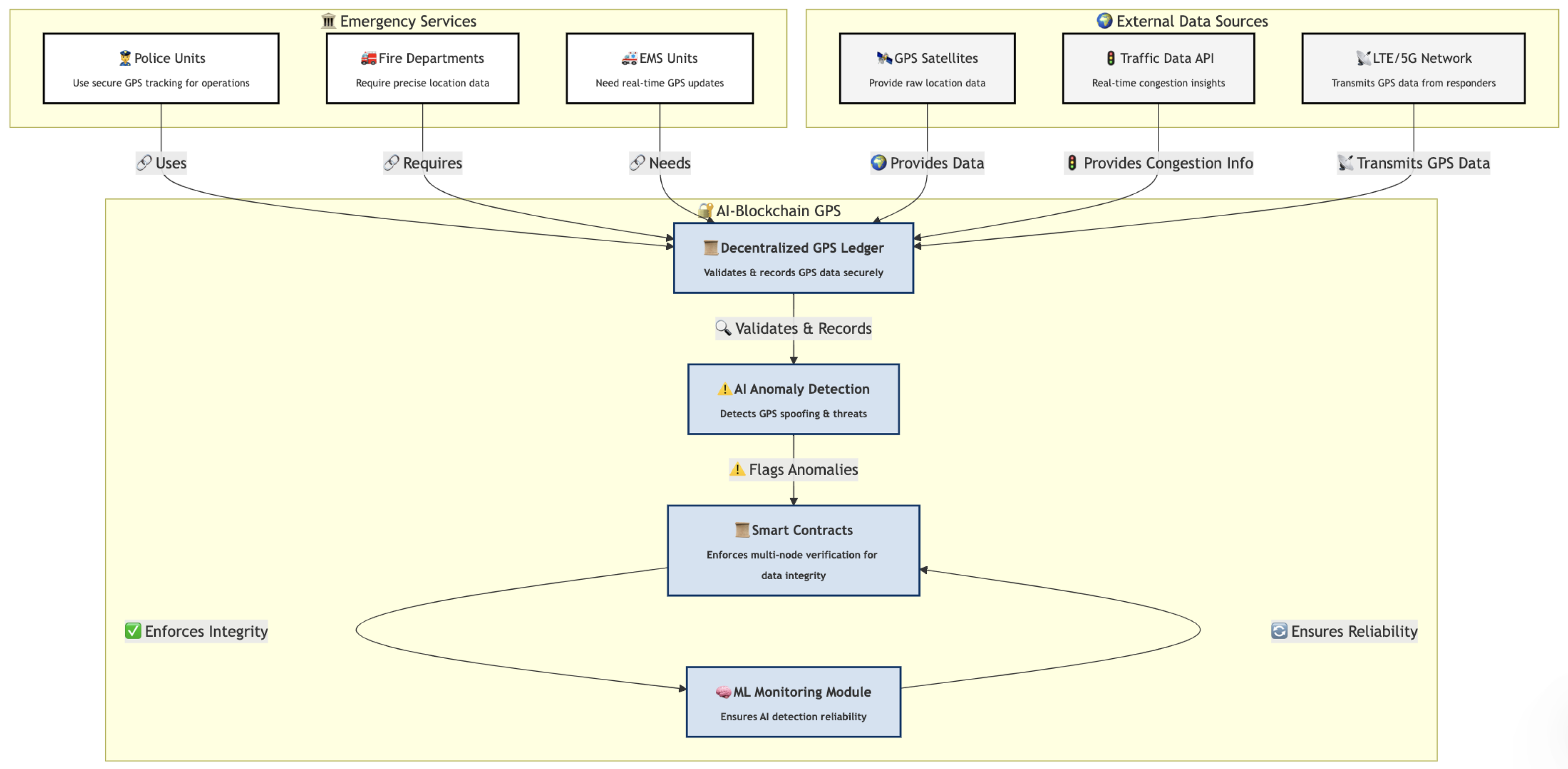
The simulation will be executed in the AnyLogic agent-based modeling (ABM) environment, which allows for the realistic representation of emergency response scenarios where police units, fire departments, and emergency medical services rely on continuous GPS tracking. The computational architecture of the simulation will include a blockchain network deployed on a Hyperledger Fabric framework, integrated within a Kubernetes cluster (Figure 3). This configuration will enable a decentralized GPS logging system where each incoming GPS coordinate is processed through a chaincode-based smart contract. The system will validate data integrity before storing it immutably within the blockchain ledger, ensuring forensic traceability and security. A multi-node endorsement policy will be enforced, requiring verification from multiple independent nodes before transactions are committed, thus mitigating the risks of GPS spoofing.
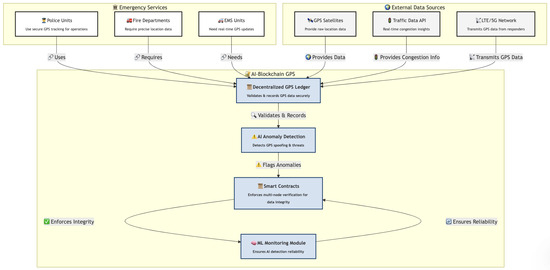
Figure 3.
Overview of the AI–blockchain simulation and experimental framework for secure GPS tracking.
To detect potential GPS anomalies and security threats, an AI-based anomaly detection system will be incorporated. The detection model will analyze real-time GPS trajectories using a combination of recurrent neural networks (RNNs) and convolutional neural networks (CNNs), ensuring the accurate identification of anomalous movement patterns. Additionally, a generative adversarial network (GAN) will be employed to generate adversarial samples, allowing the AI model to be trained on realistic attack scenarios. A Bayesian filtering mechanism will further enhance real-time decision-making by dynamically assessing the probability of an incoming GPS transaction being fraudulent.
The geospatial routing and traffic modeling component will integrate real-time congestion data retrieved from public traffic APIs to refine emergency vehicle routing. The simulation will employ an enhanced Dijkstra’s shortest-path algorithm, incorporating adaptive cost functions that account for dynamic road congestion levels, varying terrain characteristics, and incident-reported obstructions. The optimization module will dynamically adjust the movement trajectories of emergency response units based on blockchain-validated GPS coordinates.
To ensure the scalability of the simulation environment, all computational processes will be executed on a high-performance computing (HPC) cluster. The system will utilize Intel Xeon Gold 6338 processors, NVIDIA A100 Tensor Core GPUs for deep learning inference acceleration, and 512 GB of RAM to facilitate the real-time processing of large-scale GPS and blockchain transactions.
9.2. Experimental Design
The experimental framework will be structured into three distinct phases, progressively introducing blockchain-based security and AI-powered anomaly detection to evaluate the system’s efficiency under different conditions.
In the first phase, the baseline performance of conventional GPS tracking mechanisms will be measured in the absence of blockchain and AI interventions. Key parameters such as GPS data transmission latency over LTE and 5G networks, the accuracy of existing location validation techniques, and the impact of network congestion on data propagation will be assessed.
The second phase will introduce the blockchain framework, enabling decentralized GPS logging and retrieval. The performance of blockchain transactions will be analyzed in terms of throughput, latency, and the overall computational overhead introduced by decentralized storage. Additionally, this phase will investigate the blockchain network’s ability to maintain reliable GPS logging under varying emergency response workloads.
The final phase will integrate AI-based anomaly detection into the blockchain system, allowing real-time threat identification and automated GPS correction. The framework will be tested against multiple adversarial conditions, including GPS spoofing attacks, man-in-the-middle (MITM) attacks on blockchain transactions, and network congestion that leads to potential data packet loss. Performance metrics such as blockchain transaction latency, AI-based anomaly detection accuracy, and geospatial optimization efficiency will be recorded to assess the overall effectiveness of the system.
9.3. Expected Results and Future Implications
The proposed AI-enhanced blockchain framework is expected to yield a substantial improvement in GPS tracking security and operational efficiency. It is anticipated that the AI model will enhance anomaly detection accuracy, reducing false positives to below 5%, while maintaining a high level of sensitivity in identifying GPS spoofing attempts. The blockchain framework is expected to lower GPS transaction latency to approximately 250 milliseconds, ensuring real-time updates without excessive computational overhead. Furthermore, the integration of AI-enhanced geospatial optimization is predicted to reduce emergency response times by at least 18%, thereby improving the operational efficiency of law enforcement agencies.
These findings will form the basis for future large-scale deployments of AI-powered blockchain systems in real-world police and emergency response units. The experimental results will provide insights into the feasibility of integrating decentralized security frameworks with AI-driven anomaly detection to enhance GPS tracking resilience against cyber threats. Future work will focus on extending the framework to support additional emergency response functions, such as automated dispatching and multi-agent coordination for large-scale crisis management.
9.4. Integrated AI-Driven Wildfire Management and Voice Command System
In a wildfire scenario, particularly in a remote, mountainous region where traditional communication infrastructure is compromised, effective crisis management is crucial. The fire rescue team utilizes a combination of IoT devices, blockchain technology, and ZenextAI’s voice-command virtual assistant to manage the situation efficiently. These technologies work in tandem to create a streamlined operational environment, which enhances situational awareness, optimizes resource allocation, and ensures the security of critical communication and location data.
10. Simulation and Experimental Design for AI-Enhanced Wildfire Management
The validation of the proposed AI-enhanced blockchain framework for secure GPS tracking and crisis response will be conducted through a structured simulation and experimental setup. This framework will simulate an emergency wildfire scenario, focusing on a scalable and resource-efficient implementation of AI-driven predictive analytics, blockchain-backed data integrity, real-time IoT monitoring, and ZenextAI’s voice-command system for first responders. The system will be tested in a controlled laboratory environment using simulated data streams and emulated IoT devices to ensure feasibility within practical constraints.
10.1. Integrated Simulation Environment
The experimental setup will be developed using a MATLAB R2024b–Simulink environment alongside Python 3.11-based geospatial analysis for modeling fire progression, emergency response strategies, and blockchain interactions. The simulation will include a simplified agent-based fire propagation model, an AI-based predictive analytics engine, and an emulated emergency response coordination system.
A lightweight Hyperledger Fabric blockchain network (Figure 3) will be deployed on a Docker-based local Kubernetes cluster, ensuring the decentralized logging of GPS updates, fire location reports, and resource allocations. Smart contracts will be implemented to validate incoming GPS transactions, ensuring data integrity and transparency.
The AI model will be trained on publicly available wildfire datasets and will use time-series forecasting techniques to predict fire spread based on environmental variables such as temperature, wind speed, and humidity. The geospatial optimization module will use open-source GIS tools, such as QGIS and OpenStreetMap, for route optimization.
10.2. Wildfire Management Use Case: AI-Driven Decision Support
The experimental scenario models a wildfire in a semi-urban area, requiring dynamic resource allocation. IoT devices, emulated using Raspberry Pi nodes with temperature and humidity sensors, will continuously transmit environmental data to the AI system, which will analyze the fire’s potential spread.
Predictive hazard modeling will be performed using an AI-driven function:
where T represents temperature, W is wind speed, and H denotes humidity. The AI model will apply Long Short-Term Memory (LSTM) networks for forecasting fire intensity.
10.3. AI-Based Voice Command System for Firefighter Assistance
ZenextAI’s voice-command virtual assistant will be tested in a controlled simulation environment. A prototype speech-to-text interface will be developed using the Google Speech-to-Text API integrated with Python-based natural language processing (NLP) for interpreting firefighter commands.
For example, a firefighter could issue the following command:
“Zenext, update the fire perimeter location.”
The system will process the request, update fire perimeter data within the blockchain, and return an optimized evacuation or response route.
10.4. IoT and Blockchain-Backed GPS Monitoring
IoT sensors will simulate GPS tracking and fire spread detection using sensor fusion techniques with a combination of GPS and accelerometer data. Each sensor’s location and readings will be hashed and stored immutably on the blockchain. A basic consensus mechanism based on the Raft algorithm will be used for blockchain validation, optimizing transaction throughput.
10.5. Geospatial Optimization for Resource Allocation
A geospatial optimization algorithm will be implemented using Python’s NetworkX library for shortest-path calculations, integrated with real-time traffic emulation to simulate first-responder route optimization.
The response time equation is given by
where represents the distance from station i to the fire and v is the average response speed. The system will consider real-time congestion delays using simulated traffic data and dynamic re-routing based on fire spread predictions.
10.6. Experimental Phases and Evaluation Metrics
The experiment will be divided into three phases.
10.6.1. Phase 1: Baseline Performance Measurement
The first phase will evaluate a non-AI, non-blockchain emergency response system using traditional dispatch methods. Performance metrics will include average response time, manual resource allocation efficiency, and error rate in GPS tracking.
10.6.2. Phase 2: Blockchain-Enabled Secure GPS Tracking
The second phase will introduce blockchain-backed GPS logging and measure transaction latency, data integrity, and tamper-proof storage efficiency.
10.6.3. Phase 3: AI-Enhanced Blockchain Framework with Voice-Command Support
The final phase will integrate AI-based predictive analytics and voice-assistant-enabled response coordination. The system will be evaluated based on the following key performance indicators:
- Fire prediction accuracy ();
- Response time improvement ();
- Voice-command processing accuracy ().
10.7. Expected Outcomes and Future Deployment Considerations
This controlled experimental setup will provide a realistic yet scalable testbed for AI-enhanced emergency response solutions. Expected outcomes include a significant reduction in false positives for GPS anomalies, lower blockchain transaction latency ensuring real-time tracking feasibility, and faster firefighter decision-making through AI-driven voice commands. Future work will focus on deploying a small-scale field test using actual GPS devices and IoT-based environmental monitoring in a controlled outdoor environment.
11. Conclusions
This methodology outlines a comprehensive approach to implementing a blockchain- and AI-driven fire rescue system. By leveraging advanced tools such as Google Forms, ArcGIS, AnyLogic, SQLite, and Python, the proposed system will address critical challenges in communication, geospatial accuracy, and data security. Through systematic design, rigorous testing, and continuous monitoring, the system will deliver a scalable, secure, and adaptive solution capable of enhancing operational efficiency in fire rescue operations.
As location-based services become increasingly integral to public safety, their security frameworks must evolve to meet emerging threats. The adoption of predictive AI models offers a proactive approach to identifying and neutralizing risks. Blockchain technology holds promise for enhancing data integrity and security through decentralized, tamper-proof records. Moving toward distributed data management can further reduce single points of failure, enhancing system resilience [21].
Collaboration between public safety agencies and cybersecurity specialists is critical to addressing the complex challenges posed by LBS technologies. Developing adaptable solutions that cater to the specific needs of law enforcement ensures their long-term viability. The ongoing refinement of systems like ZenextAI [24], informed by user feedback and rigorous testing, will shape the future of secure and effective public safety operations.
Author Contributions
Conceptualization, S.M. and A.A.; methodology, S.M. and A.A.; software, S.M. and A.A.; validation, S.M. and A.A.; formal analysis, S.M. and A.A.; investigation, S.M. and A.A.; resources, A.A.; writing—original draft preparation, S.M.; writing—review and editing, S.M. and A.A.; visualization, S.M. and A.A.; supervision, A.A.; project administration, S.M. and A.A.; funding acquisition, A.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Concordia University, under the supervision of Prof. Dr. Anjali Awasthi.
Institutional Review Board Statement
Not applicable. This study does not involve humans, animals, or biological materials and therefore did not require ethical approval or an Institutional Review Board (IRB) statement. The research is entirely conceptual and focuses on the methodological framework for implementing a blockchain- and AI-driven fire rescue system. As no experiments or studies involving living subjects were conducted, the ethical considerations typically associated with such research are not relevant to this work.
Informed Consent Statement
Not applicable. This study does not involve human participants, and no human data, materials, or subjects were part of the research. Consequently, the requirement for informed consent does not apply. The research is purely conceptual and methodological, focusing on the development of a blockchain- and AI-driven fire rescue system.
Data Availability Statement
This study does not involve the use of any datasets. The research presented is conceptual and methodological, focusing on the design and implementation framework for a blockchain- and AI-driven fire rescue system. No datasets were analyzed or generated. Consequently, there are no data to share. Future work will involve the incorporation of real-world data for validation and testing, which will be appropriately documented and shared in compliance with relevant ethical guidelines.
Acknowledgments
The authors would like to acknowledge the valuable literature available in the domain of smart cities and public safety research. This body of work has paved the way for identifying a significant research gap in understanding the role of securing GPS tracking and location services in public safety through the integration of blockchain and AI.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Li, W.; Su, Z.; Li, R.; Zhang, K.; Wang, Y. Blockchain-Based Data Security for Artificial Intelligence Applications in 6G Networks. IEEE Netw. 2020, 34, 31–37. [Google Scholar] [CrossRef]
- Majumdar, S.; Kirkley, S.; Srivastava, M. Voice Command Drone for Law Enforcement and Emergency Response. In Proceedings of the 2024 Ninth International Conference on Mobile and Secure Services (MobiSecServ), Miami Beach, FL, USA, 9–10 November 2024; pp. 1–11. [Google Scholar]
- Khan, A.S.; Balan, K.; Javed, Y.; Tarmizi, S.; Abdullah, J. Secure trust-based blockchain architecture to prevent attacks in VANET. Sensors 2019, 19, 4954. [Google Scholar] [CrossRef] [PubMed]
- Cinque, M.; Esposito, C.; Russo, S.; Tamburis, O. Blockchain-empowered decentralised trust management for the Internet of Vehicles security. Comput. Electr. Eng. 2020, 86, 106722. [Google Scholar] [CrossRef]
- Biswas, A.; Wang, H.C. Autonomous Vehicles Enabled by the Integration of IoT, Edge Intelligence, 5G, and Blockchain. Sensors 2023, 23, 1963. [Google Scholar] [CrossRef] [PubMed]
- Pu, C. A novel blockchain-based trust management scheme for vehicular networks. In Proceedings of the 2021 Wireless Telecommunications Symposium (WTS), Virtual Event, 21–23 April 2021. [Google Scholar] [CrossRef]
- Khan, B.U.I.; Goh, K.W.; Khan, A.R.; Zuhairi, M.F.; Chaimanee, M. Integrating AI and Blockchain for Enhanced Data Security in IoT-Driven Smart Cities. Processes 2024, 12, 1825. [Google Scholar] [CrossRef]
- Oham, C.; Michelin, R.A.; Jurdak, R.; Kanhere, S.S.; Jha, S. B-FERL: Blockchain-based framework for securing smart vehicles. Inf. Process. Manag. 2021, 58, 102426. [Google Scholar] [CrossRef]
- Chai, H.; Leng, S.; Zhang, K.; Mao, S. Proof-of-reputation based-consortium blockchain for trust resource sharing in internet of vehicles. IEEE Access 2019, 7, 175744–175757. [Google Scholar] [CrossRef]
- Firdaus, M.; Rahmadika, S.; Rhee, K.H. Decentralized trusted data sharing management on internet of vehicle edge computing (IoVEC) networks using consortium blockchain. Sensors 2021, 21, 2410. [Google Scholar] [CrossRef] [PubMed]
- Chen, L.; Thombre, S.; Järvinen, K.; Lohan, E.S.; Alén-Savikko, A.; Leppäkoski, H.; Kuusniemi, H. Robustness, Security and Privacy in Location-Based Services for Future IoT: A Survey. IEEE Access 2017, 5, 8956–8977. [Google Scholar] [CrossRef]
- Rathod, T.; Jadav, N.K.; Tanwar, S.; Sharma, R.; Tolba, A.; Raboaca, M.S.; Said, W. Blockchain-Driven Intelligent Scheme for IoT-Based Public Safety System Beyond 5G Networks. Sensors 2023, 23, 969. [Google Scholar] [CrossRef] [PubMed]
- Zhang, C.; Li, W.; Luo, Y.; Hu, Y. AIT: An AI-Enabled Trust Management System for Vehicular Networks Using Blockchain Technology. IEEE Internet Things J. 2020, 8, 3157–3169. [Google Scholar] [CrossRef]
- Bhawana; Kumar, S.; Rathore, R.S.; Mahmud, M.; Kaiwartya, O.; Lloret, J. BEST—Blockchain-Enabled Secure and Trusted Public Emergency Services for Smart Cities Environment. Sensors 2022, 22, 5733. [Google Scholar] [CrossRef] [PubMed]
- Cheema, M.A.; Shehzad, M.K.; Qureshi, H.K.; Hassan, S.A.; Jung, H. A drone-aided blockchain-based smart vehicular network. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4160–4170. [Google Scholar] [CrossRef]
- Bendiab, G.; Hameurlaine, A.; Germanos, G.; Kolokotronis, N.; Shiaeles, S. Autonomous vehicles security: Challenges and solutions using blockchain and artificial intelligence. IEEE Trans. Intell. Transp. Syst. 2023, 24, 3614–3637. [Google Scholar] [CrossRef]
- Sharma, A.; Awasthi, Y.; Kumar, S. The Role of Blockchain, AI and IoT for Smart Road Traffic Management System. In Proceedings of the 2020 IEEE India Council International Subsections Conference (INDISCON), Visakhapatnam, India, 3–4 October 2020; pp. 289–296. [Google Scholar]
- Kiruthika, M.; Ponnuswamy, P.P. Fusion of IoT, Blockchain and Artificial Intelligence for Developing Smart Cities. In Blockchain, Internet of Things, and Artificial Intelligence; Chapman and Hall/CRC: Boca Raton, FL, USA, 2021; pp. 155–177. [Google Scholar]
- Baker, T.; Asim, M.; Samwini, H.; Shamim, N.; Alani, M.M.; Buyya, R. A Blockchain-Based Fog-Oriented Lightweight Framework for Smart Public Vehicular Transportation Systems. Comput. Netw. 2022, 203, 108676. [Google Scholar] [CrossRef]
- Jain, S.; Ahuja, N.J.; Srikanth, P.; Bhadane, K.V.; Nagaiah, B.; Kumar, A.; Konstantinou, C. Blockchain and Autonomous Vehicles: Recent Advances and Future Directions. IEEE Access 2021, 9, 130264–130328. [Google Scholar] [CrossRef]
- Nar, D.; Kotecha, R. Enhancement of Drone-as-a-Service Using Blockchain and AI. Int. J. Next-Gen. Comput. 2022, 13, 885–900. [Google Scholar]
- Vishwakarma, L.; Das, D. SmartCoin: A novel incentive mechanism for vehicles in intelligent transportation system based on consortium blockchain. Veh. Commun. 2022, 33, 100429. [Google Scholar] [CrossRef]
- Das, D.; Dasgupta, K.; Biswas, U. A secure blockchain-enabled vehicle identity management framework for intelligent transportation systems. Comput. Electr. Eng. 2023, 105, 108535. [Google Scholar] [CrossRef]
- Majumdar, S.; Kirkley, S.; Srivastava, M. Voice Command AI Assistant for Public Safety. In Proceedings of the 2022 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakheer, Bahrain, 20–21 November 2022; pp. 124–131. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).