Abstract
It is always challenging to tackle timeliness and privacy security problems in sensing data in mobile crowdsensing (MCS) systems, and the key is in how to realize data freshness optimization in privacy-preserving scenarios. In view of the fact that existing studies on timeliness optimization of sensing data and those on privacy security enhancement are independent of each other, this paper systematically investigates data freshness optimization techniques for privacy-preserving MCS systems. Firstly, the preliminaries about MCS, privacy preservation, and sensing data quality are introduced. Then, a coupling mechanism, which intricately links the dynamics of privacy preservation and data freshness, is unveiled. This intertwining relationship introduces complexities that make the problem particularly challenging to address. Next, effective measures are summarized to realize data freshness performance enhancement in MCS. Finally, implementation, potential applications, and future directions on timely and secure MCS are discussed.
1. Introduction
In recent years, significant attention has been placed on digital twin (DT), artificial intelligence (AI), and metaverse technologies, which are resulting in a new round of the technological revolution [1,2]. These emerging technologies are driven by massive sensing data that make it difficult for traditional sensing data collection schemes to fulfill their requirements [3]. Traditional sensing is based on the wireless sensor network (WSN), which can only execute the sensing task in limited and specific areas by deploying dedicated sensing equipment. Different from WSNs, mobile crowdsensing (MCS) can realize timely and effective data collection from a group of entities (e.g., online people) [4]. Specifically, MCS integrates the attributes of crowdsourcing and -sensing, which can utilize the sensing abilities of all potential intelligent terminals with sensing modules to collect data. Therefore, MCS has the advantages of a flexible implementation manner, robust system performance, and low deployment cost, and an MCS-enabled sensing data collection method can provide rich data sources and a solid data guarantee for the development of current emerging technologies.
Although MCS can bring plenty of benefits, there are many challenges, mainly due to heterogeneous requirements (e.g., task scale and wide range of data sources). Typically, MCS systems are characterized by the following challenges:
- 1.
- Sensing network scale diversity. In an MCS system, the sensing tasks are flexible, and the sensing data amount and type requirements are different, which results in various sensing network scales. Specifically, the system network size is proportional to the number of intelligent terminals and the execution complexity of the sensing task. Hence, under various types of sensing networks, if we aim to improve the system timeliness and security performance, the question of how to model the relationships among task requester, service provider, and intelligent terminals could be the primary challenge.
- 2.
- Sensing task requirement heterogeneity. The differences in sensing abilities among intelligent terminals are huge, as the demands and constraints of intelligent sensing terminals are heterogeneous during the sensing and transmission processes. In detail, the wireless resources of intelligent terminals, including spectrum, energy, space, and power aspects, cannot meet the needs of the sensing task requirements. Given the heterogeneity between the sensing task’s demand and intelligent terminals’ constraints, the question of how to realize timely and secure wireless resource optimization could be another challenge.
- 3.
- Sensing environment openness. Due to the wide range of sources of MCS, the sensing environment is open to all potential intelligent sensing terminals, which increases the security risks [5]. For example, some malicious users may launch attacks on an MCS system, bringing threats in terms of sensing data content, sensing terminal identity and location information, and sensing task content or even causing the service provider cloud node to be paralyzed and disabled, unable to recruit terminals and assign sensing tasks. Therefore, the question of how to design privacy preservation schemes for different potential threats can also be challenging.
The aforementioned challenges significantly affect the data freshness quality and privacy preservation of MCS, which may result in the performance degradation of MCS tasks. For instance, if the sensing data are out of date, it will minimize the accuracy and reliability of system decisions and cause performance degradation for real-time applications. On the other hand, if the sensing data content is not protected, the sensing data will be hijacked, monitored, or tampered with by a data poisoning attack or a Sybil attack [6], where the identity of the intelligent terminals can be forged and thus can submit false or useless data to the service requester. However, maintaining data freshness and protecting privacy simultaneously is non-trivial. Therefore, this paper considers data freshness quality and privacy preserving for MCS. The main contributions are as follows:
- 1.
- We systematically study the components, architecture, interactions, and privacy preservation issues for MCS. In addition, performance indicators and mathematical models for the AoI are also illustrated for the data freshness quality aspect of MCS.
- 2.
- We reveal the relationship between data freshness optimization and privacy preservation issues in MCS, where privacy preservation’s impact on data freshness optimization is investigated to cover the current research gap.
- 3.
- We give potential privacy preservation and data freshness optimization schemes for building secure and timely MCS, which can be implemented in different system layers.
- 4.
- We discuss the possible implementation and application for secure and timely MCS and list future directions in open issues.
The rest of this paper is organized as follows. Section 2 introduces related works. Section 3 introduces some fundamentals and design aspects of MCS. Then, Section 4 presents privacy preservation research for MCS, and Section 5 investigates the data freshness optimization issues for privacy-preserving MCS. Next, Section 6 gives a case study, and Section 7 discusses the open issues of secure and timely MCS. Finally, Section 8 concludes this paper. In addition, Table 1 and Table 2 showing symbol and acronym lists are presented below.

Table 1.
Symbol list.

Table 2.
Acronym list.
2. Related Works on AoI and Privacy Efforts for MCS
Regarding robust MCS, the main concerns concentrate on timeliness and security issues, where the data freshness and privacy of the sensing data should be paid much more attention. Currently, the AoI metric can accurately measure the sensing data freshness trait, including the transmission time over the air and the waiting and queuing times at the source and destination ends, respectively. AoI is defined as the time elapsed since the generation of the most recently received information, providing a real-time measure of data staleness. Up to now, some practical efforts have been made to improve the freshness quality of sensing data in MCS, which can help build timely MCS. For example, under a scenario of short packet communication, implementing packet length design can significantly improve the AoI of the sensing data [7], where the communication effect can be significantly ensured. Furthermore, from the viewpoint of wireless spectrum access, channel allocation [8] can be used to enhance the freshness of sensing data as well, where intelligent terminals can choose channel selection strategies in an AoI-oriented manner. Moreover, position deployment can influence the freshness of the collected sensing data [8]. After being appropriately deployed, AI bots can handle bio-sensing data in a timely and effective manner. Finally, power control [9] can also decrease the AoI value and increase the freshness of sensing data simultaneously, which can help UAVs monitor real-time traffic flows in the sky. As for the privacy issues of MCS, the contents regarding the sensing data, sensing task, intelligent terminals’ position and identification, and the cloud server’s storage are all facing some potential threats, such as the single-point attack, data poisoning attack, witch attack, etc. [10]. Up to now, some emerging technologies have been used as an alternative approach for addressing privacy security concerns. For example, to defend against single-point attacks, the edge computing [11] approach can provide a non-centralized architecture, where sensing data can be processed or computed in a distributed way. To protect the privacy of intelligent terminals, the federated learning [12] method can be adopted, where sensing data can be protected among different intelligent terminals. Moreover, blockchain technology can be used in a decentralized manner to ensure the security of central storage to act as a reliable SP [13]. Finally, the data encryption [14] method can ensure the security of the terminals’ position and location, where the data source can be collected anonymously.
A detailed comparison of our paper with surveys/tutorials on the state of the art of MCS is shown in Table 3. In current MCS survey and tutorial papers [4,15,16,17,18,19], research studies on privacy preservation and research studies on data freshness optimization are independent, while our work first reveals the relationship between privacy preservation and data freshness optimization issues, which can close the current independent research gap. In addition, specific approaches for privacy protection and data freshness optimization schemes are also summarized in this paper. For example, Ref. [20] utilizes multiple unmanned aerial vehicles (UAVs) as sensing terminals for three-dimensional data collection, proposing a multi-UAV target iterative matching algorithm and a UAV three-dimensional navigation algorithm. This approach addresses the data collection energy efficiency and latency challenges in mobile crowdsensing assisted by multiple UAVs. Regarding data quality, Ref. [21] leverages MCS to infer the spatial–temporal correlations of sparse samples, enabling the prediction of missing temporal data and reconstructing the entire sensing map. To address the issue of low data accuracy during this inference process, a dynamic signal map reconstruction model based on a spatial–temporal graph attention mechanism is proposed. This model reduces inference errors and improves inference accuracy. Furthermore, Ref. [22] addresses the problem of low-quality sensor data leading to data collection task failures by proposing a scheme for reliable data mining at the sensing terminal, thereby improving data quality. In a mobile edge computing scenario, Ref. [23] utilizes mobile crowdsensing for environmental data collection, simultaneously optimizing data collection time, energy consumption, and budget for multi-objective data collection tasks. In terms of data privacy and security, Ref. [24] leverages mobile crowdsensing to collect location data, providing recommendations for users’ travel route planning while protecting trajectory information during continuous changes in the sensing terminal’s location based on differential privacy protection techniques. Ref. [25] both enhances the privacy security of the terminal itself and further improves data utility by designing a data perturbation scheme based on local differential privacy. Ref. [26] proposes a hybrid scheduling genetic algorithm aimed at enhancing the security level and providing data freshness. Ref. [27] formulates a joint age-of-information optimization and privacy preservation problem, where game theory and homomorphic encryption approaches are used to solve the above problem. Ref. [28] proves the cloud possesses the latest version of shared data while still preserving identity privacy in the cloud storage situation. To ensure both privacy and data freshness in cloud-based data sharing, Ref. [29] introduces a novel approach. The method utilizes a homomorphic authenticable ring signature scheme to protect user identities and an Overlay Tree algorithm to deliver data with the required level of freshness. Ref. [30] integrates a proof-of-storage technique with data dynamics support into cryptographic storage, which is designed to provide full integrity for outsourced data. Based on artificial-noise-based privacy preservation technology, Ref. [31] aims at jointly minimizing the age-of-information metric and weighted privacy preservation budget in data submission scenarios.

Table 3.
Comparison of related works.
3. Fundamentals and Design Aspects
3.1. Fundamentals
Mobile Crowdsensing
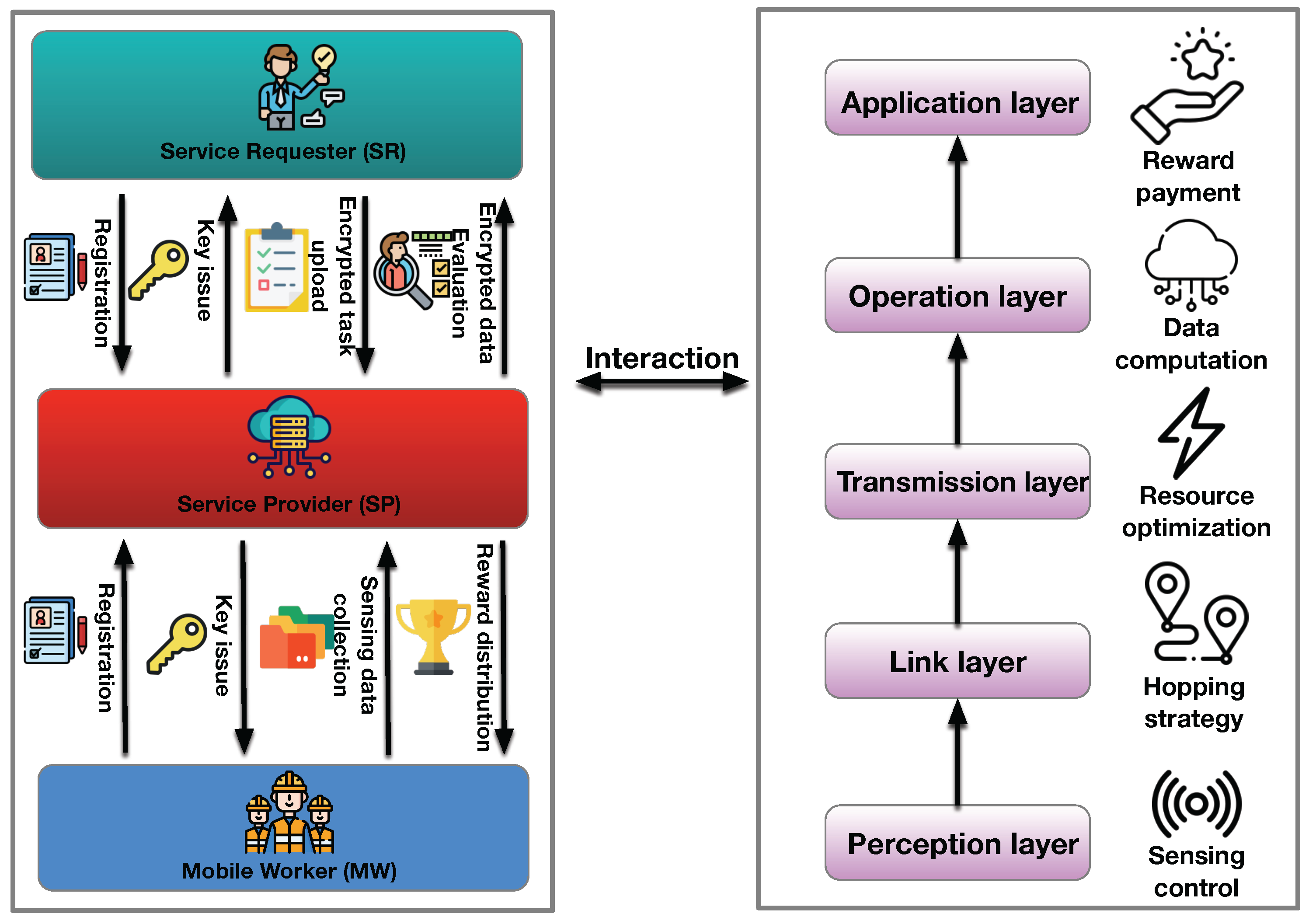
Typically, a mobile crowdsensing system comprises three basic entities, the service requester (SR), service provider (SP), and mobile worker (MW) [13], as shown in Figure 1. An SR is the sensing task initiator, which stipulates the type, quality, and amount of the needed sensing data. The SP can act as a middleman between the SR and MWs, which can conduct task assignments, data processes, and reward payment operations in a central or distributed manner. Regarding MWs, they are the executors of the specific sensing data collection tasks. Note that due to different sensing abilities, MWs may need to cooperate to complete the sensing data collection tasks. On the other hand, in a layered architecture, from bottom to top, an MCS system is made up of a perception layer, link layer, transmission layer, operation layer, and application layer. To be specific, the perception layer is in charge of sensing rate control, sensing task scheduling, and sensing terminal coordination among MWs. In the link layer, MWs can determine their routing and forwarding strategies. As for the transmission layer, it is devoted to optimizing power and frequency resources for MWs. Furthermore, the operation layer and application can provide data computation, quality evaluation, and reward payment services for MWs. Other than the components and layered architecture, to complete an MCS task, the SR, SP, and MWs need to participate in data interactions. At first, the SP and MWs should register their identity with the SP. Then, the SR uploads the detailed sensing tasks to the SP. Next, the SP recruits the registered MWs to perform the sensing task and sends keys and system parameters to the MWs and SR. After finishing the sensing data collection, the MWs hand the sensing data to the SP to be further processed. Finally, when the SP relays the computed sensing data to the SR to make the quality evaluation, the MWs obtain the corresponding rewards based on the results report from the SR [32].
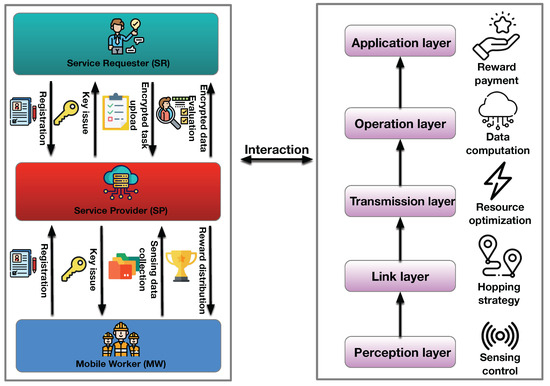
Figure 1.
MCS overview: The SR initiates tasks and specifies data needs, while the SP coordinates and processes data, and MWs execute the sensing tasks. This layered system streamlines task distribution, data collection, and reward allocation. The large right rectangle represents different layers of MCS, and the large left rectangle represents the service provider of MCS.
3.2. Design Aspects
There are many design aspects for mobile crowdsensing, such as task scheduling, mobile terminal recruitment, payment incentive design, privacy preservation, and data freshness. Our work focuses on privacy preservation and data freshness quality.
3.2.1. Privacy Preservation for Mobile Crowdsensing
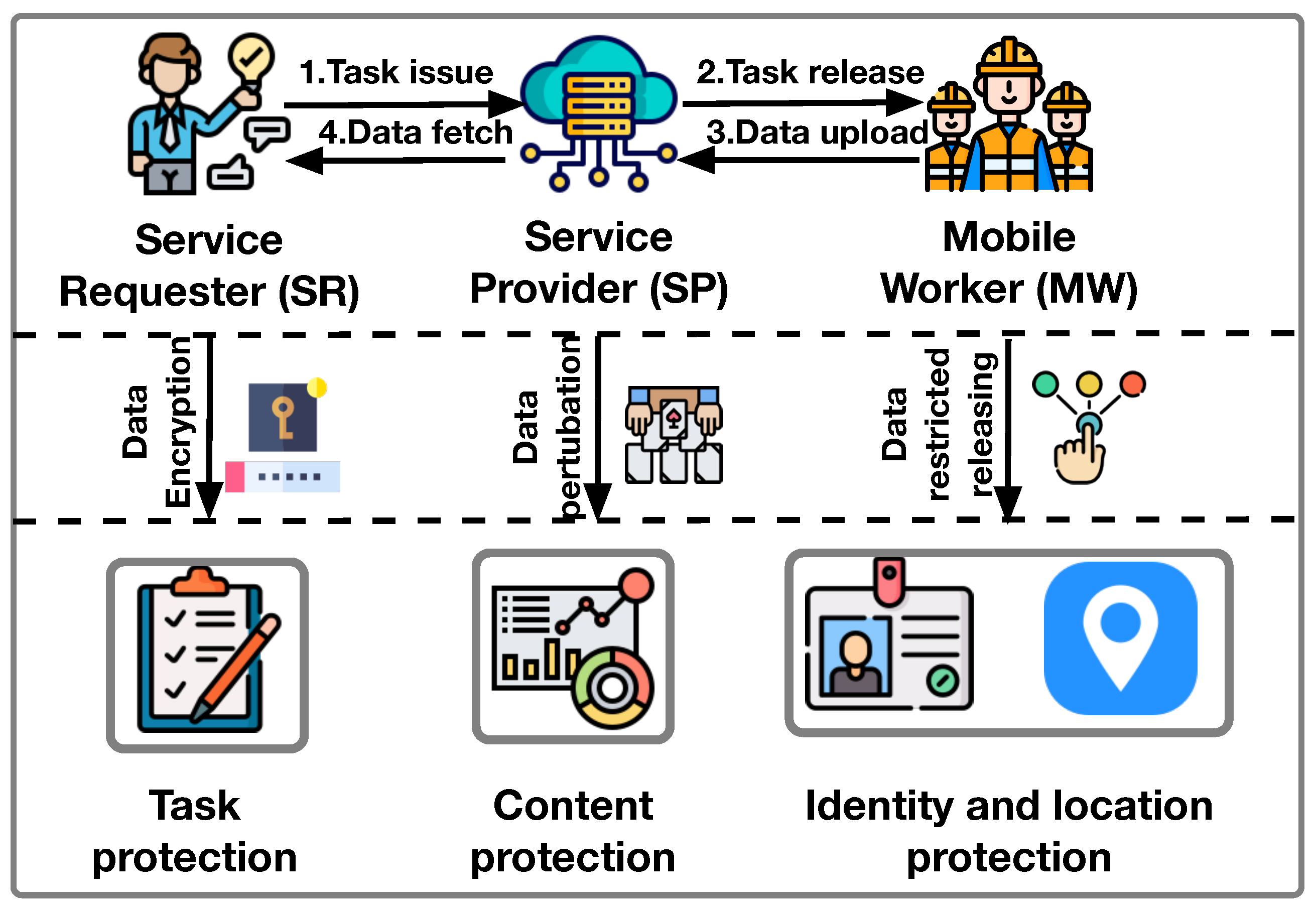
Privacy preservation in mobile crowdsensing refers to sensing data content protection, sensing task content protection, and MWs’ location and identity information protection [33], as shown in Figure 2, whose details are listed below:
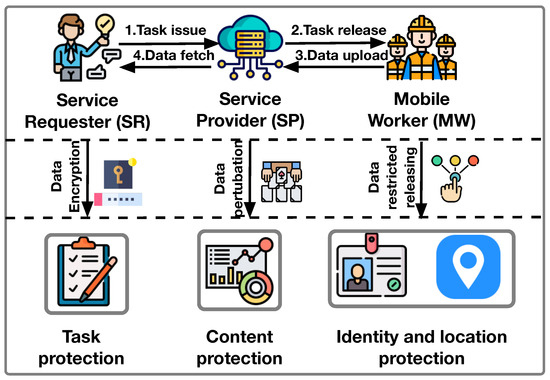
Figure 2.
Comprehensive protection for MCS interaction.
- 1.
- Sensing data content protection: Protecting the sensing data is significantly important. To save the implementation cost and sensing time during the data collection process, one might suffer from various issues (e.g., tempering). Without taking sensing data content protection measures, the sensing data can be easily forged, stolen, or tampered with, which will lead to unqualified and useless sensing data collection. Hence, it is of significance to realize and enable sensing data content protection [34].
- 2.
- Sensing task content protection: Protecting the sensing data is significantly important. To save the implementation cost and sensing time during the data collection process, one might suffer from various issues. For example, fewer sensors or less frequent sampling can lead to data incompleteness, and the usage of lower-cost sensors or less robust data collection methods can result in reduced accuracy. Therefore, without taking sensing data content protection measures, the sensing data can be easily forged, stolen, or tampered with, which will lead to unqualified and useless sensing data collection. Hence, it is of significance to realize and enable sensing data content protection [35].
- 3.
- Location and identity information protection: In some navigation or positioning-oriented scenarios, the MWs need to provide their own location and identification information to assist the object detection or location [36]. However, if the MWs’ location and identity information is not well protected, it will face the risk of being leaked or tampered with. On the one hand, modified location and identity information can lead to inaccurate or wrong navigation or positioning results. On the other hand, the MWs’ position and identity can be exposed to the public, which increases security risks. To provide better service and enhance individual service, the location and identity information of MWs should be protected.
3.2.2. Sensing Data Freshness Quality
Queuing theory has been utilized in MCS to model and analyze the flow of data from sensor nodes to the data collection server. By representing sensing data generated by sensor nodes as queues and the communication channels as servers, queuing models can help to analyze and optimize the age of information (AoI), further ensuring data freshness performance [9]. For example, wireless resource allocation techniques can be applied to prioritize data transmission based on freshness requirements, giving higher priority to data with a higher time sensitivity to guarantee its timely delivery. In addition, data freshness quality focuses on the timeliness of the sensing data. Freshness is very important in MCS systems since time-sensitive data can more accurately reflect the real-time status of the target. To assess the freshness quality of perceptual data, we can consider the following two aspects:
- 1.
- Performance indicators: To accurately describe the data freshness performance of sensing data, an AoI indicator is proposed, which refers to the elapsed time for the latest successfully received packet from its generating time slot to its being-received time slot. Different from a latency performance metric, the AoI comprehensively takes the waiting time at the source node and queuing time at the destination node into consideration [37]. The basic performance indicators for AoI can be divided into three types: instant AoI (IAoI), average AoI (AAoI), and peak AoI (PAoI). Specifically, during the data packet transmission process, instant AoI focuses on the data freshness value at a random time slot, the average AoI value concentrates on the overall data freshness performance for all time slots, and peak average AoI pays attention to the worst data freshness performance (i.e., maximum AoI value) at each time slot.
- 2.
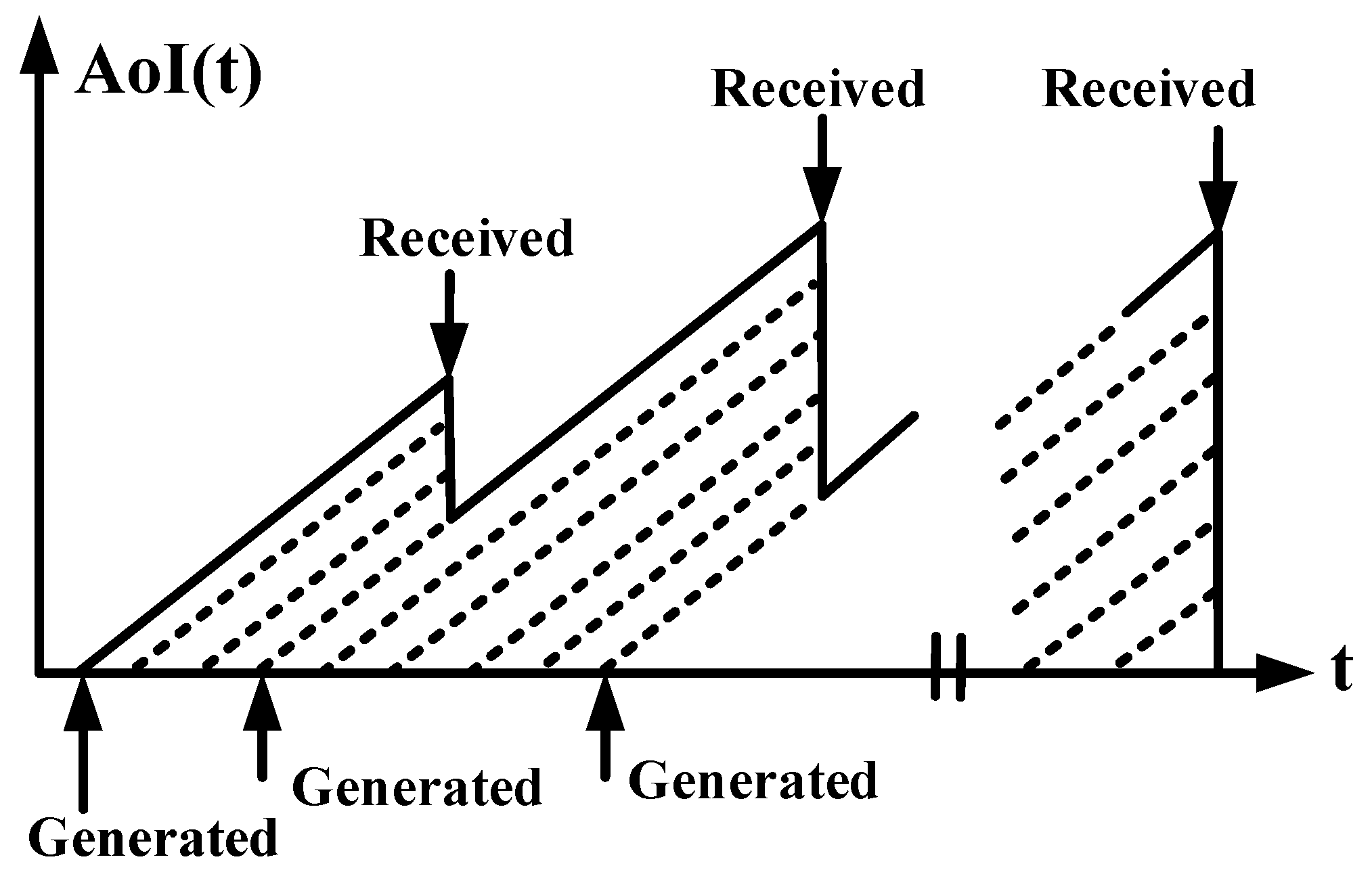
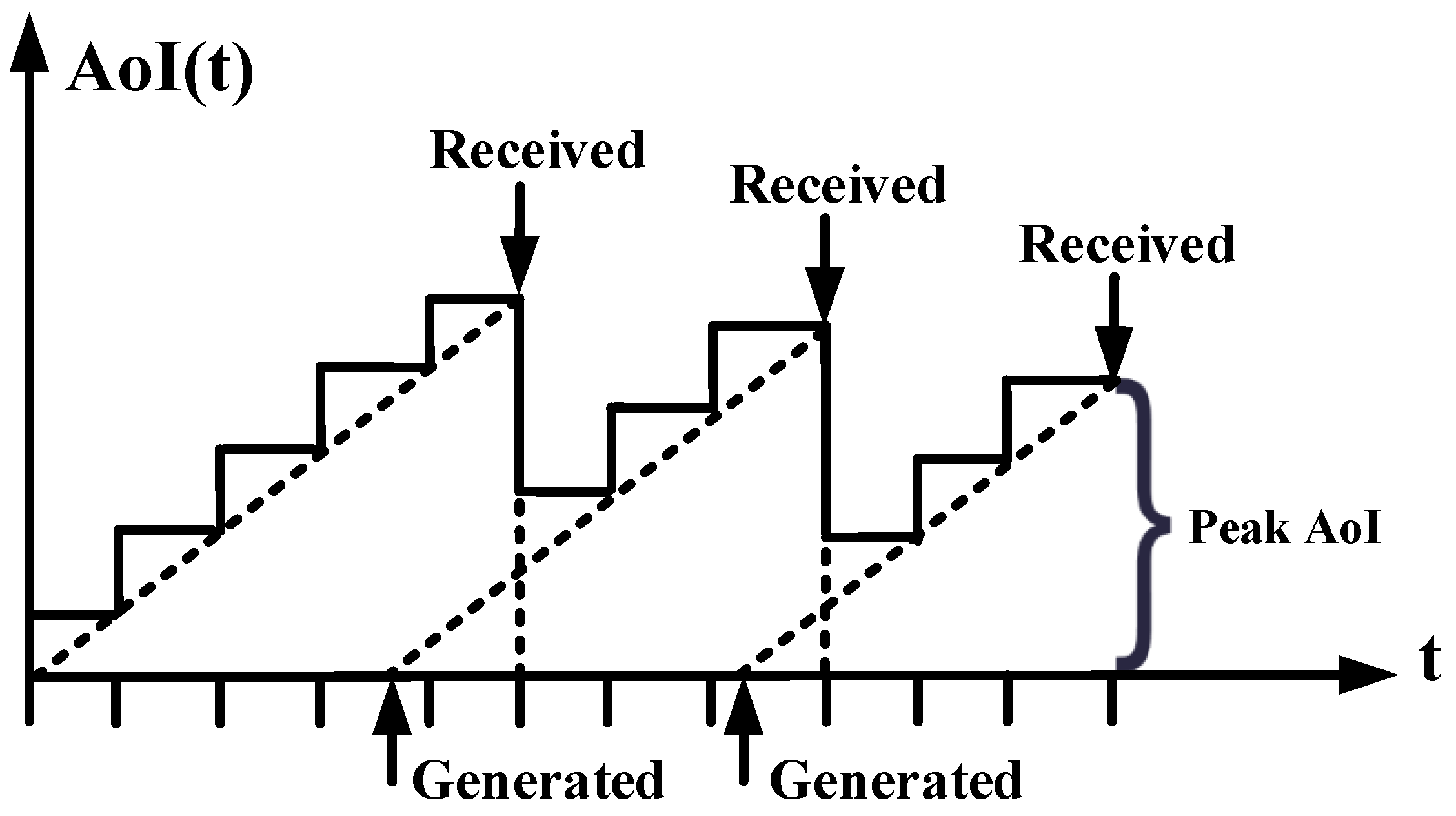
- Mathematical models: Using the queue theory and Markov process, the mathematical expression (i.e., as shown in Figure 3 and Figure 4) for the AoI metric can be derived in the closed form [8]. In detail, the instant AoI can be directly obtained by calculating the current time value minus the packet generation timestamp. As for the average AoI, when the AoI is modeled as a sawtooth function, it can be calculated as the area (i.e., enclosed by the function and the axis) divided by the time period. From the perspective of queue theory, the sensing data are the guest, and the wireless channel represents the server. At this time, the sum area can be divided into the sum system time and the waiting time, where queue theory can help calculate their values under different serving rules and queue models. Moreover, as far as the peak AoI is concerned, the Markov process can help describe the stochastic data packet arrivals, thus determining the maximum AoI value at each time slot.
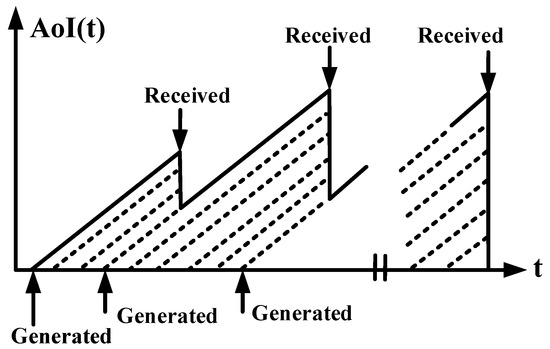 Figure 3. Queue-theory-based average AoI model. The dashed lines are used to represent the area surrounded by time axis and AoI function, whose average value indicates the average AoI performance.
Figure 3. Queue-theory-based average AoI model. The dashed lines are used to represent the area surrounded by time axis and AoI function, whose average value indicates the average AoI performance.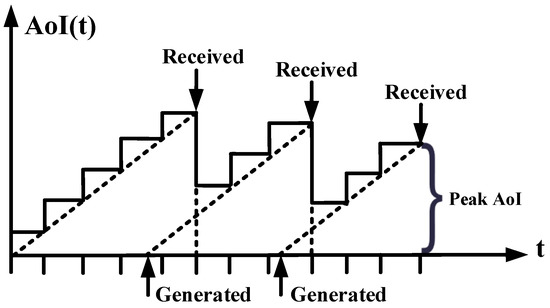 Figure 4. Markov-process-based peak AoI model. The chosen height is assumed to correspond to the timestamp when the sensing data are successfully received.
Figure 4. Markov-process-based peak AoI model. The chosen height is assumed to correspond to the timestamp when the sensing data are successfully received.
Based on the above analysis, we give the closed-form expressions for the sensing data’s freshness with the AoI indicator. Specifically, as shown in Figure 3 and Figure 4, for the sensing data packet, we denote the AoI function as and let t and be the generated and successfully accepted timestamps, so the instant AoI can be calculated as
Moreover, within the time interval , the average AoI of the sensing data can be denoted as [37]
Furthermore, during the transmission of sensing data over a wireless channel, a significant portion of the wireless signal energy is concentrated along the line-of-sight propagation path. Therefore, when sensing data are first generated, they receive preferential transmission service over the wireless channel. This phenomenon can be described using the first come first served (FCFS) serving rule [14]. In addition, due to the time-varying and selective fading characteristics of the wireless channel, some sensing data generated earlier may experience delayed service (i.e., transmission) and thus be received later by the service provider. To quantitatively analyze this phenomenon, this section employs the last come first served (LCFS) serving rule [14].
In addition, the M/M/1, M/D/1, and D/M/1 queuing models are fundamental tools for analyzing systems with waiting lines. The M/M/1 model assumes random, exponentially distributed arrivals and service times with a single server, providing simple formulas for performance metrics but exhibiting high variability. The M/D/1 model retains random arrivals but has a fixed, deterministic service time, resulting in more efficiency and lower average wait times. Conversely, the D/M/1 model has fixed, deterministic arrivals with exponentially distributed service times, requiring more complex analysis [37]. In this regard, different queue models and serving rules should be taken into consideration to further calculate the average AoI expression of the sensing data. Specifically, we denote the wireless channel transmission rate as and let and represent the sensing data generation rate and wireless channel utilization ratio, so we have
Further, from the perspective of queue theory, the wireless channel is the server, and indicates its serving rate, while the sensing data are the customer, and means their arriving rate. Based on [14], under the FCFS serving rule, we have the following expressions for M/M/1, M/D/1, and D/M/1 queue models, respectively.
For ease of presentation, we take a proof example of the M/M/1 model under the FCFS serving rule, and other expressions can be derived in a similar way. To be specific, based on [14], for the FCFS serving rule, the AoI can be generally calculated as
where means the expectation operation, Q is the elapsed time for updating two adjacent sensing data, and K is the difference of the current sensing data’s received time slot and generated time slot. For the M/M/1 model, according to [14], we have
By combining Equations (4)–(6), we can obtain
Following similar approaches, we can obtain the average AoI expressions for the M/D/1 and D/M/1 queue models under FCFS serving rules:
where denotes the Lambert-W function. Similarly, under the LCFS serving rule, we have the following expressions for the M/M/1, M/D/1, and D/M/1 queue models [14], respectively:
4. Privacy Preservation for Mobile Crowdsensing
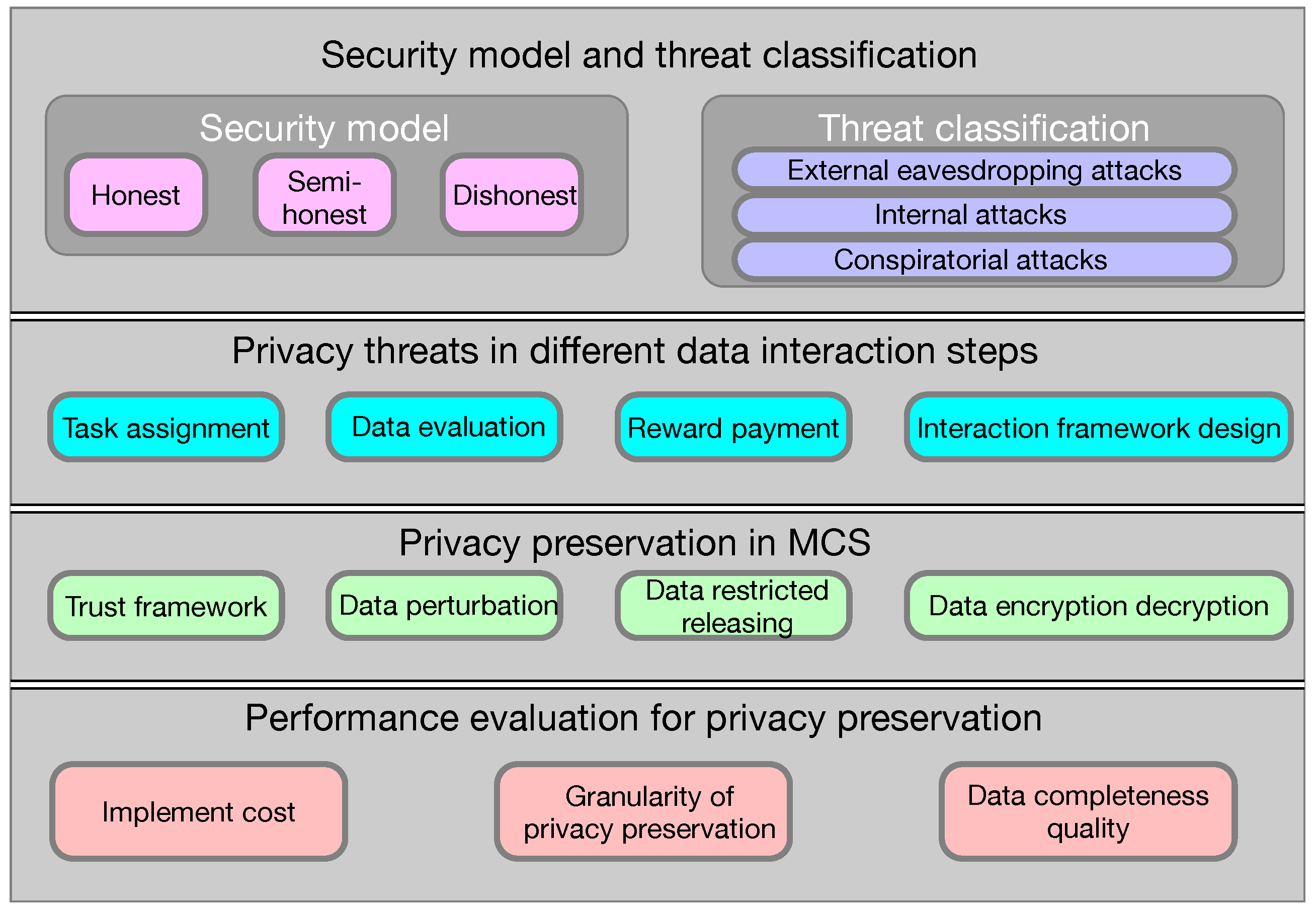
In this section, we focus on the privacy preservation issue for MCS, where threat and attack models, including credibility level and attack origin, are presented. Then, we illustrate the privacy threats in different interaction steps. Next, some detailed effective measures for privacy guarantees are summarized. Finally, the indicators for privacy preservation performance evaluation are listed. Note that Figure 5 gives a comprehensive overview of all the mentioned points.
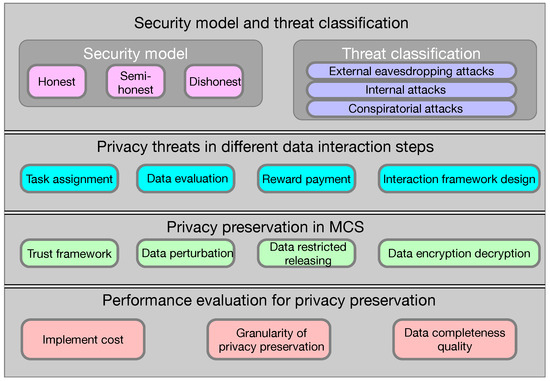
Figure 5.
An overview of privacy preservation in MCS.
4.1. Security Model and Threat Classification
To realize privacy preservation for MCS, the premise is to establish a comprehensive security model and threat classification, where the credibility level of MCS elements and attack origins should be fully considered [13].
4.1.1. Security Model
There are three types of security levels in MCS, honest, semi-honest, and dishonest [38]. Specifically, the honest level means the participant in MCS obeys the rules of protocol and is not curious about private data; thus, it is assumed to be fully reliable and trustworthy. As for the semi-honest level, it means the participant follows the agreements as well, but it is curious about the privacy data, such as deducing the content of the sensing data. For the dishonest level, the participant breaks the protocol rule, and the privacy data may be stolen, tampered with, or even leaked. Hence, the participant is regarded as unreliable and untrustworthy under such a circumstance. In summary, due to the different reliability assumptions about the participant, from low to high order, the security level can be ranked as honest, semi-honest, or dishonest.
4.1.2. Threat Classification
From the viewpoint of attack origins, attacks in MCS can be divided into three categories, external eavesdropping attacks, internal attacks, and conspiratorial attacks [15]. Further, external eavesdropping attacks make use of the inherent openness of wireless channels; thus, the malicious attacker can launch data-stealing attacks to deteriorate data confidentiality. Internal attacks mainly refer to attacks launched by individual participants in MCS. For example, the SR would leak or deduce the privacy data of MWs to obtain payment. In addition, conspiratorial attacks are generated by internal participants in MCS together. For example, a semi-honest MW can cooperate with a dishonest SP to obtain the private information of other honest MWs [16].
4.2. Privacy Threats in Data Interaction Steps
4.2.1. Privacy Threats in Task Assignment Stage
In the task assignment step, the SP needs to assign sensing tasks to MWs based on their sensing abilities and service reputations, which can ensure the data freshness quality and low implementation cost. At this time, MWs need to interact with the SP to obtain the task content; thus, security risks about their location and identity breaches are increased, as the SP may leak their private information. Moreover, without appropriate privacy-preserving measures, the sensing task content is also vulnerable. For example, once the sensing task content is stolen and tampered with, MWs collect useless data, which seriously threatens the security of the MCS system [39].
4.2.2. Privacy Threats in Data Evaluation Stage
The data quality is essential for MCS efficiency, as only high-quality sensing data can stimulate more MWs to participate in MCS. However, there could be some privacy threats that can deteriorate the efficiency of the data evaluation stage. For example, a semi-honest SR can deduce the location and identify information of MWs from the submitted sensing data. In addition, without sensing data content protection, a dishonest SR can also maliciously tamper with the data, then give falsified data evaluation results, where the MWs can only obtain small payment even though they are providing high-quality data [40].
4.2.3. Privacy Threats in Reward Payment Stage
Due to the task execution cost for sensing data collection, the corresponding rewards should be paid to MWs. Meanwhile, facing the risk of privacy disclosure and without the proper benefits from task execution, MWs may be unwilling to spend time and limited resources on the MCS task. For example, by sharing an incorrect or inaccurate data quality report, a dishonest SR and semi-honest SP can conspire to defraud the sensing data from MWs, even stealing, leaking, or selling their position and identity information [41].
4.2.4. Privacy Threats of Interaction Framework Design
To successfully complete the MCS tasks, the MWs, SP, and SR all need to conduct data interactions with each other. When the reliability and credibility of the participants cannot be ensured, the privacy of task content, data content, and MWs’ location and identity information are greatly threatened. Therefore, under various sensing task requirements, the interaction framework also suffers from serious privacy threats [42].
4.3. Privacy Preservation in MCS
4.3.1. Data Encryption/Decryption
By protecting sensitive data, the data encryption method can realize privacy preservation. Specifically, the sending and receiving ends have a set of agreed-upon rules to change and restore the data presentation form, which is stimulated by secret keys. Hence, after being encrypted, the content of the sensing data cannot be accessed by unauthorized parties during the transmission process [43]. One typical and promising applicable technique in MCS is secure multi-party computation (SMC), where one constrained function can be securely calculated without the help of the trusted third party.
4.3.2. Data Perturbation
Through adding noise to the original sensing data, data privacy can be protected in a distorted form. Specifically, data perturbation can distort sensitive data while keeping their properties of some statistical characteristic aspects [44]. There are, mainly, three kinds of measures to realize data perturbation, including randomization, blocking and condensation, and differential privacy. Randomization means adding random noise to original data, then releasing the disturbed data. Blocking refers to the method where some specific data are not released, and condensation refers to storing statistics in groups of raw data records. In addition, differential privacy protection aims at maximizing the accuracy of data queries when queried from a statistical database while minimizing the chance of identifying their records.
4.3.3. Data Restricted Releasing
To realize data privacy preservation, data restricted releasing technology can publish partial data selectively, publish low-accuracy data, or even not publish data [45]. Currently, the research about data restricted releasing mainly concentrates on data anonymization, which is widely used for data mining processes. To be specific, as far as data privacy is concerned, through performing data anonymization, the risks of being exposed can be decreased to a tolerable range. For instance, k-anonymity technology can publish low-accuracy data through generalization and suppression approaches, which can make an identifier have at least k records so that the observer cannot link the records to the identifier.
4.3.4. Trust Framework
From the perspective of system design, it is indispensable to construct a trust framework for data interaction [46]. To be specific, the trust framework can integrate the above detailed privacy preservation technologies into some specific data interaction step, where the corresponding data privacy can be well protected [47]. For example, under the Stackelberg game framework, the data quality and data restricted releasing level can be traded off between the SP and MWs. Through determining an equilibrium solution, data accuracy can be ensured and data privacy can simultaneously be protected.
4.3.5. Blockchain Technology
Blockchain technology offers an alternative approach to enhancing privacy and security in MCS. It provides a secure and decentralized platform for managing data and access control. In the context of MCS, blockchain can be utilized for decentralized data management, providing a secure and tamper-proof ledger for recording and verifying sensing data. It can also be used for secure access control, enforcing fine-grained control over who can access and use the data through smart contracts [13]. Furthermore, blockchain, with proper implementation, can be used to anonymize the source of data contributions, decoupling data from identifying information. Finally, blockchain provides transparent and auditable data provenance, useful for establishing trust and identifying data manipulation. In conclusion, while blockchain does not directly address data content privacy like encryption or perturbation do, it provides a unique suite of features—decentralized management, secure access control, and transparent audit trails—that can significantly enhance the security and privacy of MCS systems, especially in areas where security against manipulation and accountability are of paramount concern.
4.4. Performance Evaluation for Privacy Preservation
4.4.1. Implementation Cost
For protecting data privacy, detailed technologies are adopted. In this regard, to measure the implementation cost for privacy preservation, communication cost and computation cost can be used for evaluation. Specifically, communication cost indicates the bit overhead in the privacy process, and computation cost refers to the time overhead for the summed operations of encryption, decryption, and key generation [48]. Moreover, when performing the computation process for the data, the energy consumption of the participants should also be considered. Therefore, it is clear that a suitable encryption scheme should meet the needs of light implementation costs.
4.4.2. Granularity of Privacy Preservation
The effectiveness of a privacy preservation scheme can be evaluated by considering two key aspects: the strength of the privacy protection it offers and the range of data it covers. Privacy preservation strength relates to the resilience of the scheme against information leakage. It quantifies an adversary’s difficulty in inferring sensitive information from the protected data. We can assess this strength using various metrics [49], such as the degree of information leakage (measured by metrics such as mutual information or conditional entropy between the sensitive data and the released data), the differential privacy parameters in cases where differential privacy is used, or the success rate of privacy attacks (such as re-identification or attribute inference) when measured via experimental attacks. On the other hand, the privacy preservation range refers to the breadth of protection offered by the privacy scheme. It defines what specific data elements and aspects are secured and at what stage they are protected [50]. This can be categorized as the types of data protected (such as data content, task content, and mobile workers’ (MWs’) location and identity information), the entities whose privacy is preserved (such as data contributors, task requesters, or service providers), and/or the different phases of a data life cycle where the protection is applied (including data acquisition, data transmission, data storage, and data processing stages).
4.4.3. Data Completeness Quality
Privacy preservation techniques often distort sensing data, creating a trade-off between data privacy and data integrity. Therefore, data completeness can be assessed through the following aspects [51]: (1) Data utility measures the practical usefulness of processed data via metrics like accuracy, recall, statistical similarity, and specific business metrics relevant to the application. (2) Data consistency evaluates the preservation of logical relationships, business rules, and temporal order. (3) Data retention assesses data completeness, structural preservation, and semantic preservation. By evaluating these metrics, we can assess the effectiveness of a privacy-preserving mechanism in a nuanced way. Such a holistic approach allows for a more thorough evaluation and comparison of various privacy-preserving techniques, leading to better-informed choices about the trade-offs between data privacy and data quality.
5. Data Freshness Optimization for Privacy-Preserving Mobile Crowdsensing
In this section, to realize data freshness optimization for privacy-preserving MCS, we first investigate the impact on data freshness optimization of privacy preservation. Then, we illustrate the issues about data freshness optimization in different layers. Finally, detailed measures to realize data freshness are presented.
5.1. Privacy Preservation Impact on Data Freshness Optimization
5.1.1. Communication Overhead Constraints
Due to the limited resources of the SR, SP, and MWs, there is an important resource consumption constraint in the privacy-preserving data freshness optimization process. For example, implementing a data encryption scheme can consume some communication costs, which are measured in bits [52]. Hence, when focusing on minimizing the AoI value under a secure privacy premise, the communication overhead should be less than a certain partial sensing data size.
5.1.2. Freshness Optimization Constraints
Freshness-oriented sensing data are time-sensitive, and performing data encryption or decryption operations can cost some time. Therefore, realizing data privacy preservation results in additional computation overhead during the data freshness optimization process [47]. To be specific, when formulating the data freshness optimization problem, the goal is to minimize the AoI value, and the computation overhead for data encryption operation can be one of the most important time constraints, e.g., the computation overhead should be less than a certain partial AoI value for unencrypted data.
5.1.3. Communication Covertness Constraint
For some confidential data collection scenarios, the communication behavior needs to be hidden. At this time, the communication covertness and data freshness should be traded off [31]. To be specific, the signal-to-interference plus noise ratio (SINR) can directly decide the communication covertness, where the smaller the SINR value is, the better the covertness performance may be. Furthermore, the SINR can also influence the data transmission rate (i.e., wireless channel service rate) performance, where a larger or smaller SINR may result in queue emptiness or congestion, bringing about bad AoI performance. Therefore, communication covertness can also be one of constraints in the privacy-preserving AoI optimization problem.
5.1.4. Task-Participation-Level Constraint
In some location- or identity-driven MCS applications, the MWs need to provide their position information to achieve the goal of navigation or location [52]. In this regard, the higher the participation level is, the higher the privacy leaking risk is, while a high participation level can also enhance the sensing data generation rate (also known as the data arrival rate), which may improve the data freshness performance for the empty service queue. Hence, to simultaneously ensure data privacy and data freshness, the task participation level should be taken into consideration when minimizing the privacy-preservation-oriented AoI value.
5.1.5. Data Interaction Architecture Constraint
Since data privacy preservation can be the premise on which we can build timely MCS, it is necessary and significant to design privacy preservation-oriented data interaction architecture among the SR, SP, and MWS [53]. For example, to ensure the identity legitimacy of the SR and MWs, before handling or receiving the tasks, they both need to register with a third party. In this manner, anonymous attacks for data stealing can be effectively defended. Therefore, when designing a data freshness-oriented MCS framework, the data interaction architecture can also be an important constraint.
5.2. Data Freshness Optimization at Various Layers
5.2.1. Data Freshness Optimization at Perception Layer
In the perception layer, due to the heterogeneity between MWs’ sensing abilities and sensing task requirements, MWs need to first determine their sensing strategies, including the sensing area, sensing data amount, and types [54]. At this time, the question of how to construct AoI-oriented task scheduling can be the key point for data freshness optimization. In addition, since the energy of the MWs is also limited and high updating rates cause huge energy consumption, low updating rates may empty the transmission queue. Hence, status-updating strategies should also be optimized to satisfy the needs of data freshness and energy consumption.
5.2.2. Data Freshness Optimization at Link Layer
In some cases, due to the transmission power or communication range being constrained, the sensing data need to be relayed by MWs. At this time, from the viewpoint of the link layer, the question of how to route and forward the collected sensing data among MWs can have a straight impact on data freshness quality [55]. For example, different MWs have ranged transmission powers, and the distances between them from the SR are also varied. In this regard, the designed data relay links can influence the data transmission rate (i.e., wireless channel service rate), which ultimately results in changes in the AoI value. Therefore, in the link layer, data freshness could be improved via optimizing the data relay schedule.
5.2.3. Data Freshness Optimization at Transmission Layer
Owing to scarce transmission resources in the frequency and power domains, for realizing data freshness optimization in the transmission layer, AoI-oriented channel access and power control problems should be formulated and optimized. Through deriving solutions to the above problems, not only can the data freshness be ensured, but also the performance of spectrum utilization and energy efficiency can be improved [56]. For example, channel access and power control issues could focus on interference management during the transmission process, realizing data freshness optimization through improving the transmission rate (i.e., wireless channel service rate) performance.
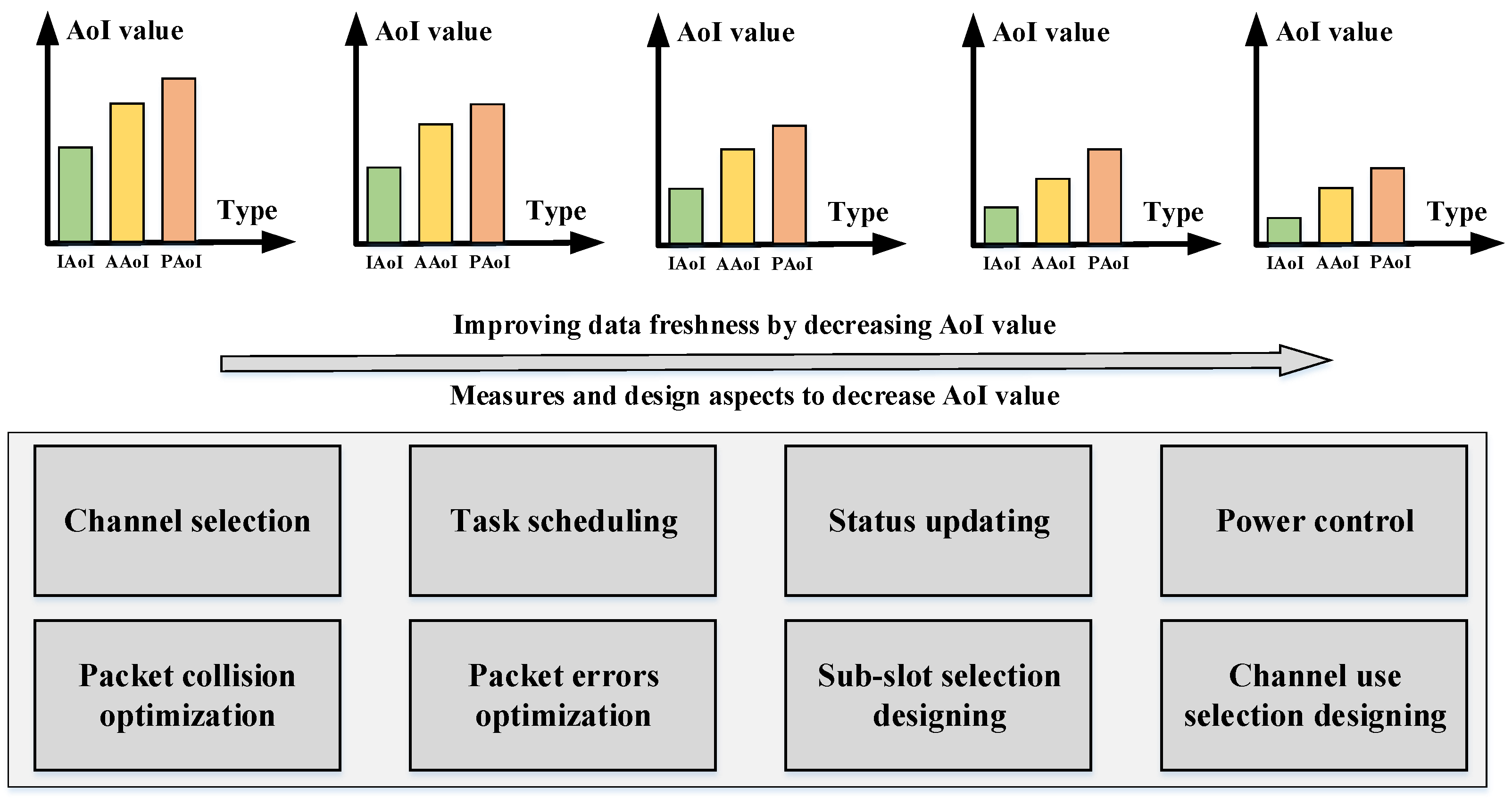
5.3. Measures to Optimize Data Freshness
Figure 6 presents the measures to optimize data freshness. Generally, data freshness can be directly reflected by the AoI value: a smaller AoI value leads to fresher sensing data, and vice versa. As shown in Figure 6, on the one hand, data freshness performances can be improved by decreasing AoI values (IAoI, AAoI, and PAoI). On the other hand, effective measures for realizing data freshness optimization in privacy-preserving MCS include resource allocation [57], coding design, and access control aspects. The details are listed below.
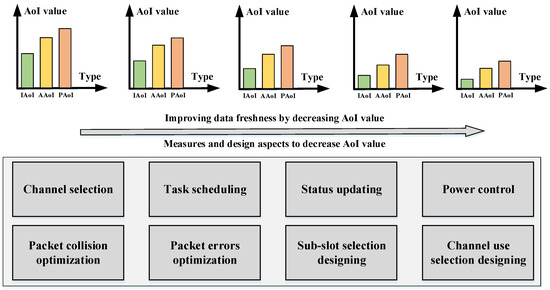
Figure 6.
Measures to optimize data freshness.
5.3.1. Resource Allocation
It is clear that sensing data freshness can be directly reflected by AoI performance, where a small AoI value represents fresh sensing data quality. Moreover, from the perspective of queue theory, the AoI can be decided by data and service generation rates simultaneously, which correspond to an MW’s status-updating and a wireless channel’s transmission rates [58]. Therefore, since resource allocation-based optimization methods can improve the system throughput performance, they are still effective for AoI optimization via tuning the MWs’ status updating rate and wireless channel’s transmission rate. For instance, the energy-efficient approach can be applied to status-updating strategy design, and channel selection can optimize a wireless channel’s service rate in the frequency domain [33].
5.3.2. Coding Design
AoI refers to the elapsed time for the latest successfully received packet, i.e., time difference from its source to its destination. It is worth noting that data packet errors can have an impact on the data freshness quality as well, where a dropped or wrong data packet should be re-transmitted, leading to bad AoI performance. Therefore, through handling the problems of data collisions or data errors, coding theory can help improve data freshness performance as well [59]. For example, after adopting a suitable coding scheme, the successful status-updating probability for a data packet can be improved, thus enhancing the data freshness performance at last.
5.3.3. Access Control
Similar to coding theory, access control technology can also play an important role in improving successful data packet updating performance. To be specific, an access control scheme mainly includes two aspects, sub-slot and channel use selection designs [60]. In this regard, data collision performance can be improved and status data can be updated successfully with better probability; thus, the transmission time and even the AoI value of a data packet can be optimized. Furthermore, when considering the random access strategy as an example, it can also provide an AoI performance reference under different access control protocols.
6. Case Study: Traffic Management in Smart City
For most metropolitan cities, traffic congestion stands out as an obstinate challenge, often intensified by the presence of outdated data and ever-present privacy concerns that act as significant barriers to the adoption of MCS. In our endeavor to revolutionize this paradigm, we employ our newly proposed framework to establish a city-endorsed MCS application. From its inception, MWs (drivers) place the utmost emphasis on minimal personal data collection. Inspired by the framework in [61], the Third-Party Secure Verification System (TPSVS) is adopted here, which is designed to provide an additional layer of security and trust, especially in environments where data integrity is of critical importance. In contrast to traditional systems, which may rely on potentially compromised central authorities, the TPSVS is designed as a separate component to perform verification without having access to the raw data themselves. It serves as a trusted, unbiased third party that securely verifies the correctness of computations without compromising the privacy of the sensitive data. In this regard, the TPSVS works in tandem with the MCS application and seamlessly authenticates the MWs, thereby solidifying the foundations of a privacy-centric environment. Once onboard, as these MWs traverse the intricate web of city streets and alleys, their state-of-the-art devices, stratified into distinct tiers factoring in patterns and the quality of data collection, serve as the city’s sensory organs. These devices, constantly feeding data, are governed by meticulously crafted algorithms. These algorithms strike a delicate yet optimal balance between reporting rates and the device’s energy consumption, thus ensuring that the data remain fresh and relevant while simultaneously preventing rapid battery drain. Furthermore, the intelligent bandwidth allocation system dynamically prioritizes pressing updates. Leveraging a suite of tailored algorithms, finally, the service provider (data center) compiles all the traffic data, dynamically formulates optimal routes for each MW, and advises the SRs on intelligent traffic signal control based on traffic flow insights.
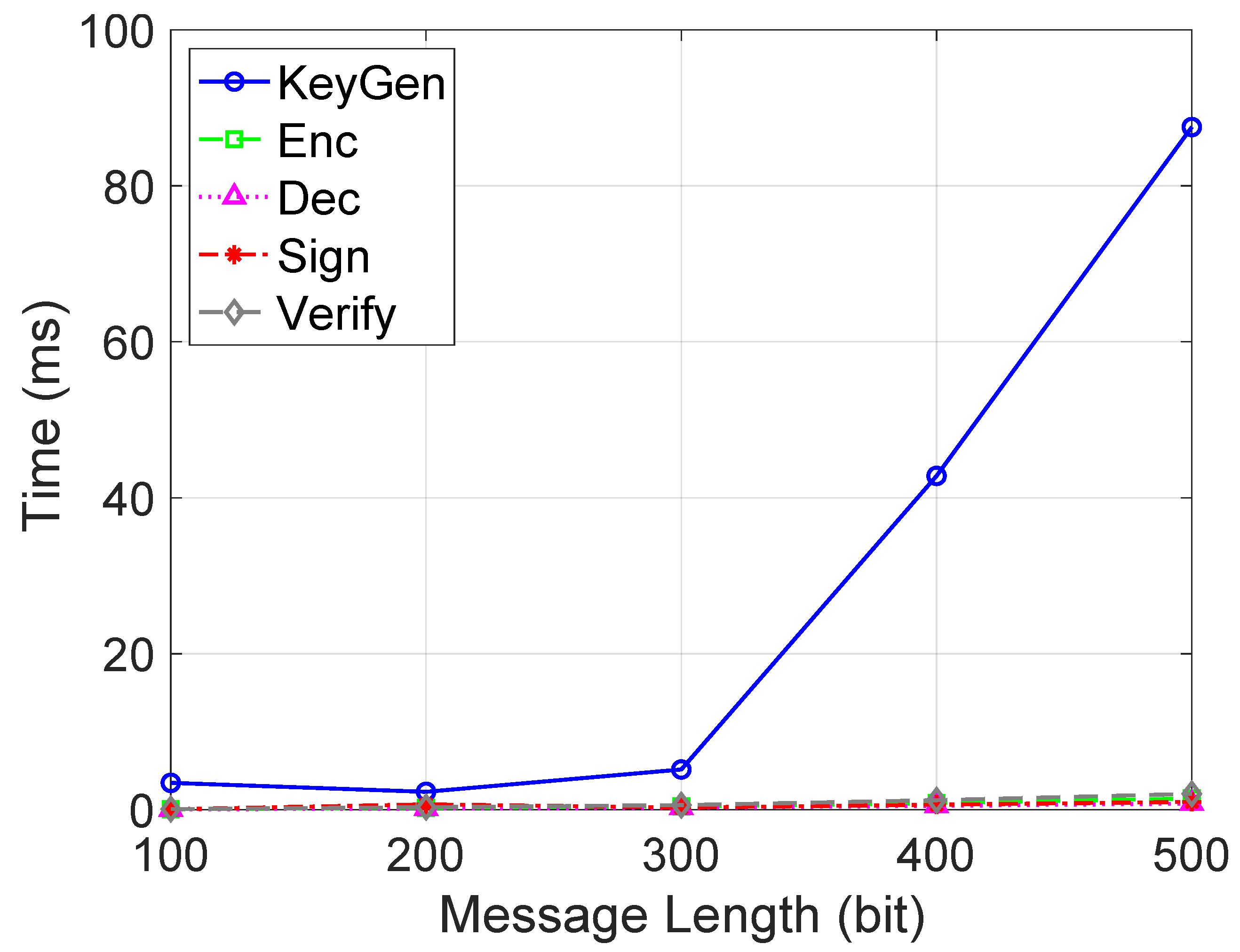
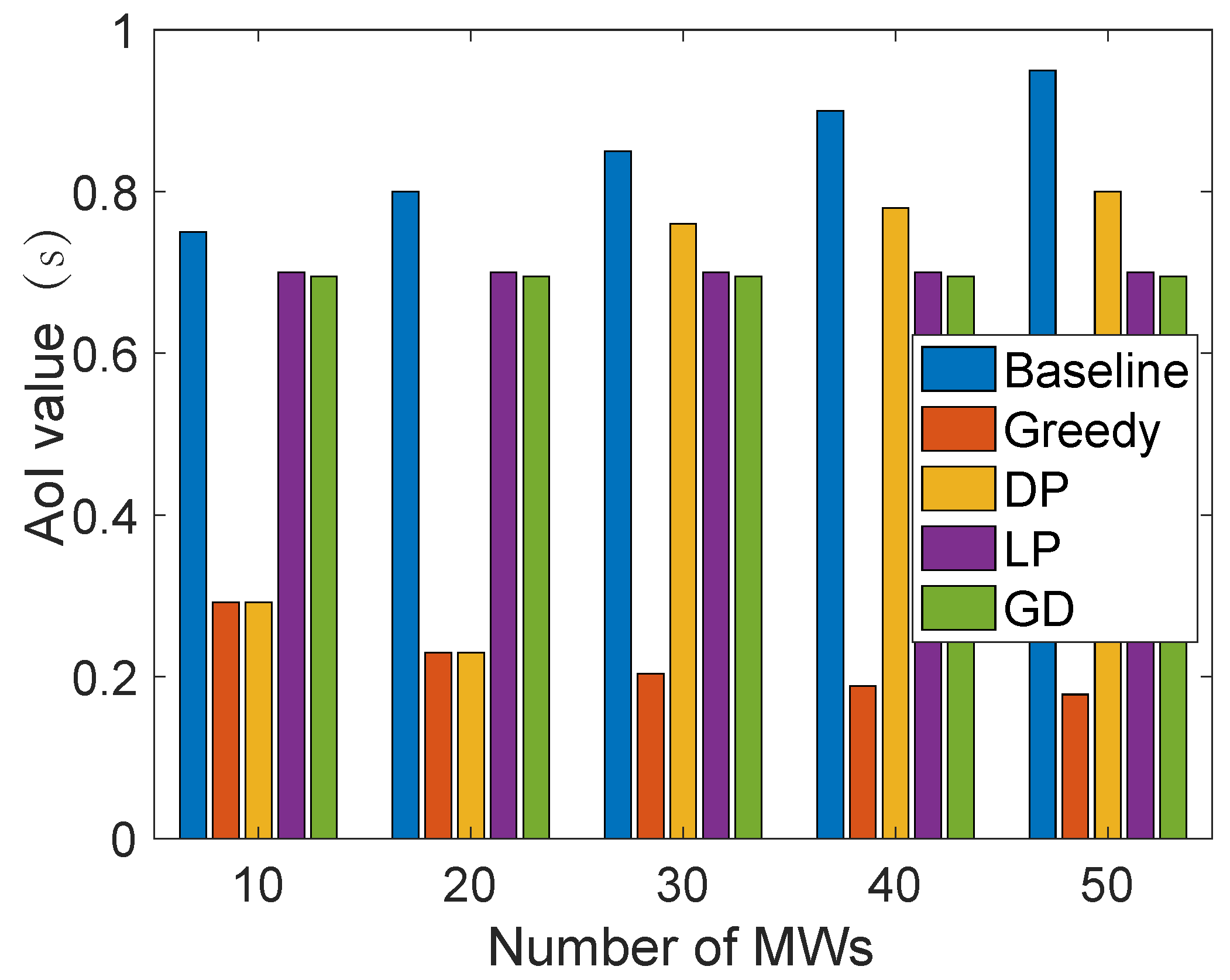
In addition, we conduct two individual experiments to evaluate the data freshness quality in privacy-enabled traffic management in MCS in a smart city. First, an “ElGamal-based TPSVS” refers to our implementation of the Third-Party Secure Verification System (TPSVS) that utilizes the ElGamal cryptosystem for secure verification [61]. Specifically, the ElGamal encryption scheme allows for verifiable computation on encrypted data [62]. This means that the TPSVS can perform verification operations on encrypted data transmitted by sensing devices without ever having to decrypt and reveal sensitive information. This enhances the privacy and security of the verification process. We chose to use the ElGamal cryptosystem due to its suitability for homomorphic encryption and its well-documented secure foundations. Our implementation builds upon this known cryptosystem, and the cited reference is helpful for the reader to understand the foundations of our implementation. In detail, Figure 7 shows the time cost for different operations in the ElGamal-based TPSVS. Based on the ElGamal-based TPSVS, we can effectively verify the correctness of our results without requiring the data themselves to be revealed. Therefore, our experiments focus on measuring the computational overhead of this process to highlight its practicability. Specifically, the ElGamal-based TPSVS experiment outcomes in Figure 7 show that key generation times are notably larger than other operations. However, it is worth noting that key generation is a one-time cost, making its longer duration less impactful in ongoing operations. Meanwhile, other cryptographic operations, like encryption, decryption, and verification, scale predictably with message length, underscoring the system’s overall efficiency for real-time applications. This suggests that the TPSVS, despite the initial key generation time, remains a viable solution for metropolitan traffic management systems. The second experiment, shown in Figure 8, evaluates AoI optimization methods across different traffic flows, represented by worker counts ranging from 10 to 50. The greedy method excels in AoI optimization by making locally optimal decisions, consistently outperforming other methods across traffic flows. Dynamic programming (DP) is effective at lower traffic levels but struggles as complexity increases. Linear programming (LP) and gradient descent (GD) offer steady but middling results, suggesting potential misalignment with the AoI’s inherent nature. In contrast, the baseline method, relying on a simplistic first come first served (FCFS) approach, demonstrates the drawbacks of a non-optimized strategy, particularly as traffic intensifies.
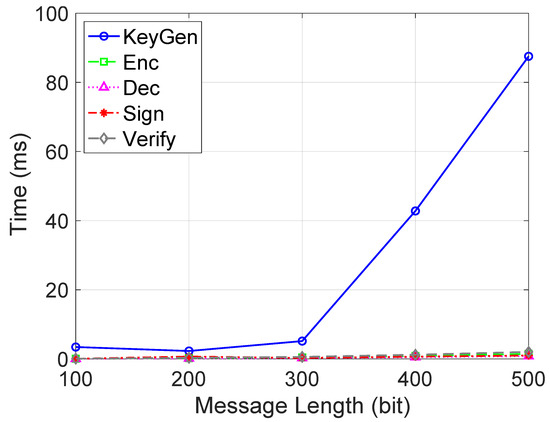
Figure 7.
Time cost for different operations in ElGamal-based TPSVS.
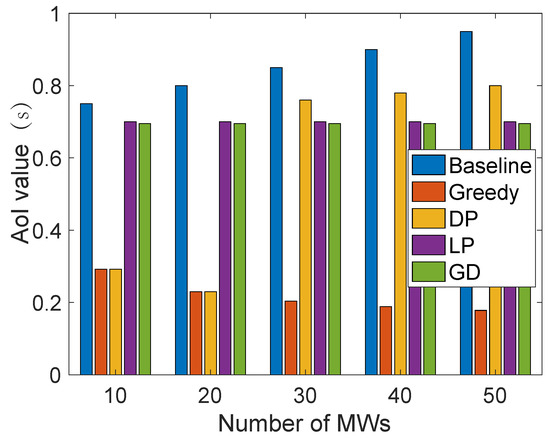
Figure 8.
AoI value for each optimization method under different worker counts.
7. Future Works and Open Issues
7.1. Data Freshness Optimization in Mobile Crowdsensing Powered by Wireless Power Transfer
To enhance the operational longevity of sensing devices and minimize the costs associated with data collection, we explore an MCS system empowered by wireless power transfer (WPT). In this model, sensing devices collect data for service providers, receiving wireless charging as compensation. A device’s sensing rate directly influences both data freshness and its energy reserves, while the service provider’s charging frequency impacts the device’s energy levels. Thus, under WPT, an important avenue for future research lies in jointly optimizing device sensing rates and provider charging frequencies to achieve optimal data timeliness, device energy management, and provider charging costs, ultimately contributing to secure and real-time MCS.
7.2. Data Freshness Optimization Based on Attention Mechanism in Large-Scale Mobile Crowdsensing
The increasing complexity of data collection tasks in MCS necessitates the recruitment of a larger pool of sensing devices. This expansion poses significant challenges to data freshness optimization, especially under privacy constraints. Specifically, the growing number of variables hinders both the efficiency and performance of traditional optimization algorithms. Attention mechanisms provide a viable solution to these challenges by focusing on the most relevant parts of the input data. These mechanisms dynamically assign weights to input variables based on their influence on the optimization outcome, allowing for a more targeted and efficient exploration of the solution space. Consequently, research into attention-based data freshness optimization for large-scale MCS is vital for enabling secure and real-time MCS.
7.3. Generative Artificial Intelligence-Based Privacy Preservation in Mobile Crowdsensing
In this work, privacy protection in MCS relies primarily on non-artificial intelligence (non-AI) algorithms, such as data encryption, differential privacy, and covert communication, to protect sensitive details like sensing tasks, device identification and location, and the data themselves. However, these conventional methods suffer from certain limitations in terms of their broad applicability and scalability. To overcome this, we explore the potential of generative AI, which, after being trained on real datasets, possesses a remarkable ability to generate high-quality synthetic data [63,64,65]. Specifically, in sensing data protection, AI-generated synthetic data, mimicking the original data distributions, can act as substitutes during processing and analysis, effectively safeguarding the real data. Therefore, devising generative AI-based privacy protection methods is an essential step to strengthen both the privacy and data freshness dimensions of secure MCS.
7.4. Blockchain-Based Solutions for Data Freshness Quality in Privacy-Enabled Mobile Crowdsensing
In typical MCS systems, centralized service providers manage task assignment, data collection, and computation, creating a single point of failure vulnerable to attacks. Such attacks can compromise data integrity, availability, and especially freshness [66]. To mitigate these issues, blockchain technology offers a decentralized and secure platform for managing and verifying data. By distributing control and storage, a blockchain network reduces the risk of manipulation and system failures. Blockchain enhances data freshness primarily through decentralized timestamping, verifiable provenance, and smart-contract-based data management [66]. Further, to bridge the gap between the blockchain and real-world data in MCS applications, reliable oracle mechanisms are essential. Oracles act as trusted data gateways, authenticating external sources before feeding them to blockchain smart contracts [67]. For instance, an oracle can verify a third-party weather API for MCS tasks. Oracles themselves need to be trustworthy; therefore, a system of multiple, auditable oracles can increase the overall reliability. Therefore, blockchain’s security and transparency, coupled with reliable oracles, can ensure data integrity, verifiability, and timeliness, which recommends blockchain-based solutions for data freshness quality in privacy-enabled mobile crowdsensing.
8. Conclusions
In this paper, we provide a comprehensive overview of the challenges and solutions for a timely and secure MCS system, where data freshness optimization issues under the premise of privacy preservation are investigated. Compared with other surveys on the state of the art, we shed light on the impact of privacy preservation on data freshness optimization, which can close the gap for independent research between data freshness optimization and privacy preservation research. To evaluate the correctness and effectiveness of our researched topic, we conducted an experiment on traffic management in a smart city as a case study. In the future, we will implement the proposed schemes on real-world MCS to improve the system’s timeliness and security performance.
Author Contributions
Conceptualization, S.C. and Y.C. (Yong Chen); methodology, S.C. and Y.C. (Yong Chen); software, Y.S. and G.L.; validation, S.C., Y.C. (Yong Chen) and Y.S.; formal analysis, Y.C. (Yanru Chen) and Z.C.; investigation, Y.C. (Yanru Chen) and Z.C.; resources, Y.C. (Yanru Chen) and Z.C.; data curation, Y.C. (Yanru Chen), and Z.C.; writing—original draft preparation, S.C. and Y.C. (Yong Chen); writing—review and editing, S.C. and Y.C. (Yong Chen); visualization, S.C. and Y.C. (Yong Chen); supervision, Y.S., G.L., Y.C. (Yanru Chen) and Z.C. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by Zhiqiang Fund Project Funding.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Khan, L.U.; Guizani, M.; Niyato, D.; Al-Fuqaha, A.; Debbah, M. Metaverse for Wireless Systems: Architecture, Advances, Standardization, and Open Challenges. arXiv 2023, arXiv:2301.11441. [Google Scholar]
- Liu, H.; Xu, Z.; Wei, Y.; Han, K.; Peng, X. Multispectral non-line-of-sight imaging via deep fusion photography. Sci. China Inf. Sci. 2025, 68, 140407. [Google Scholar] [CrossRef]
- Zhang, T.; Kong, F.; Deng, D.; Tang, X.; Wu, X.; Xu, C.; Zhu, L.; Liu, J.; Ai, B.; Han, Z.; et al. Moving Target Defense Meets Artificial Intelligence-Driven Network: A Comprehensive Survey. IEEE Internet Things J. 2025. [Google Scholar] [CrossRef]
- Capponi, A.; Fiandrino, C.; Kantarci, B.; Foschini, L.; Kliazovich, D.; Bouvry, P. A survey on mobile crowdsensing systems: Challenges, solutions, and opportunities. IEEE Commun. Surv. Tutor. 2019, 21, 2419–2465. [Google Scholar]
- Jiang, J.; Liu, F.; Liu, Y.; Tang, Q.; Wang, B.; Zhong, G.; Wang, W. A dynamic ensemble algorithm for anomaly detection in IoT imbalanced data streams. Comput. Commun. 2022, 194, 250–257. [Google Scholar]
- Tahmasebian, F.; Xiong, L.; Sotoodeh, M.; Sunderam, V. Crowdsourcing under data poisoning attacks: A comparative study. In Data and Applications Security and Privacy XXXIV; Springer: Regensburg, Germany, 2020; pp. 310–332. [Google Scholar]
- Yu, B.; Cai, Y.; Diao, X.; Cheng, K. Adaptive Packet Length Adjustment for Minimizing Age of Information Over Fading Channels. IEEE Trans. Wirel. Commun. 2023, 22, 6641–6653. [Google Scholar]
- Yang, Y.; Wang, W.; Yin, Z.; Xu, R.; Zhou, X.; Kumar, N.; Alazab, M.; Gadekallu, T.R. Mixed game-based AoI optimization for combating COVID-19 with AI bots. IEEE J. Sel. Areas Commun. 2022, 40, 3122–3138. [Google Scholar]
- Yang, Y.; Wang, W.; Liu, L.; Dev, K.; Qureshi, N.M.F. AoI optimization in the UAV-aided traffic monitoring network under attack: A Stackelberg game viewpoint. IEEE Trans. Intell. Transp. Syst. 2022, 24, 932–941. [Google Scholar]
- Jiang, J.; Liu, F.; Ng, W.W.Y.; Tang, Q.; Zhong, G.; Tang, X.; Wang, B. AERF: Adaptive ensemble random fuzzy algorithm for anomaly detection in cloud computing. Comput. Commun. 2023, 200, 86–94. [Google Scholar]
- Qin, Z.; Ye, J.; Meng, J.; Lu, B.; Wang, L. Privacy-preserving blockchain-based federated learning for marine Internet of Things. IEEE Trans. Comput. Soc. Syst. 2021, 9, 159–173. [Google Scholar]
- Lim, W.Y.B.; Xiong, Z.; Kang, J.; Niyato, D.; Leung, C.; Miao, C.; Shen, X. When information freshness meets service latency in federated learning: A task-aware incentive scheme for smart industries. IEEE Trans. Ind. Inform. 2020, 18, 457–466. [Google Scholar] [CrossRef]
- Wang, W.; Yang, Y.; Yin, Z.; Dev, K.; Zhou, X.; Li, X.; Qureshi, N.M.F.; Su, C. BSIF: Blockchain-based secure, interactive, and fair mobile crowdsensing. IEEE J. Sel. Areas Commun. 2022, 40, 3452–3469. [Google Scholar]
- Yang, Y.; Zhang, B.; Guo, D.; Xu, R.; Kumar, N.; Wang, W. Mean Field Game and Broadcast Encryption-based Joint Data Freshness Optimization and Privacy Preservation for Mobile Crowdsensing. IEEE Trans. Veh. Technol. 2023, 72, 14860–14874. [Google Scholar]
- Wang, Y.; Yan, Z.; Feng, W.; Liu, S. Privacy protection in mobile crowd sensing: A survey. World Wide Web 2020, 23, 421–452. [Google Scholar] [CrossRef]
- Boubiche, D.E.; Imran, M.; Maqsood, A.; Shoaib, M. Mobile crowd sensing—Taxonomy, applications, challenges, and solutions. Comput. Hum. Behav. 2019, 101, 352–370. [Google Scholar] [CrossRef]
- Ray, A.; Chowdhury, C.; Bhattacharya, S.; Roy, S. A survey of mobile crowdsensing and crowdsourcing strategies for smart mobile device users. CCF Trans. Pervasive Comput. Interact. 2023, 5, 98–123. [Google Scholar]
- Liu, Y.; Kong, L.; Chen, G. Data-oriented mobile crowdsensing: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 2849–2885. [Google Scholar]
- Khan, F.; Rehman, A.U.; Zheng, J.; Jan, M.A.; Alam, M. Mobile crowdsensing: A survey on privacy-preservation, task management, assignment models, and incentives mechanisms. Future Gener. Comput. Syst. 2019, 100, 456–472. [Google Scholar]
- Fu, L.; Zhao, Z.; Min, G.; Miao, W.; Zhao, L.; Huang, W. Energy-Efficient 3D Data Collection for Multi-UAV Assisted Mobile Crowdsensing. IEEE Trans. Comput. 2022, 72, 2025–2038. [Google Scholar]
- Yang, G.; Wen, P.; Liu, Y.; Kong, L.; Liu, Y. Spatial-Temporal Data Inference with Graph Attention Neural Networks in Sparse Mobile Crowdsensing. IEEE Trans. Netw. Sci. Eng. 2024, 11, 4617–4626. [Google Scholar] [CrossRef]
- Wang, P.; Yu, Z.; Lin, C.; Yang, L.; Hou, Y.; Zhang, Q. D2D-enabled Reliable Data Collection for Mobile Crowdsensing. In Proceedings of the 2020 IEEE 26th International Conference on Parallel and Distributed Systems (ICPADS), Hong Kong, China, 2–4 December 2020; pp. 180–187. [Google Scholar]
- Liu, X.; Chen, H.; Liu, Y.; Wei, W.; Xue, H.; Xia, F. Multi-Task Data Collection with Limited Budget in Edge-assisted Mobile Crowdsensing. IEEE Internet Things J. 2024, 11, 16845–16858. [Google Scholar]
- Niu, X.; Huang, H.; Li, Y. A Real-time Data Collection Mechanism with Trajectory Privacy in Mobile Crowdsensing. IEEE Commun. Lett. 2020, 24, 2114–2118. [Google Scholar] [CrossRef]
- Li, F.; Song, H.; Li, J. Personalized Data Collection Based on Local Differential Privacy in the Mobile Crowdsensing. In Proceedings of the 2020 IEEE 6th International Conference on Computer and Communications (ICCC), Chengdu, China, 11–14 December 2020; pp. 2048–2052. [Google Scholar]
- Surendran, D.; Sasikala, K. A Scheduling Genetic Algorithm For Real-Time Data Freshness And Cloud Data Security over Keywords Searching. Int. J. Comput. Inf. Syst. (IJCIS) 2022, 3, 111–120. [Google Scholar]
- Yang, Y.; Zhang, B.; Guo, D.; Xu, R.; Dev, K.; Wang, W. Joint data freshness optimization and privacy preservation in mobile crowdsensing. In Proceedings of the GLOBECOM 2022—2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 510–515. [Google Scholar]
- Maheswari, P.; Sindhumathi, B. AFS: Privacy-preserving public auditing with data freshness in the cloud. IOSR J. Comput. Eng. (IOSRJCE) 2014, 7, 56–63. [Google Scholar]
- Trueman, T.E.; Narayanasamy, P. Ensuring privacy and data freshness for public auditing of shared data in cloud. In Proceedings of the 2015 IEEE International Conference on Cloud Computing in Emerging Markets (CCEM), Bangalore, India, 25–27 November 2015; pp. 22–27. [Google Scholar]
- Jin, H.; Zhou, K.; Jiang, H.; Lei, D.; Wei, R.; Li, C. Full integrity and freshness for cloud data. Future Gener. Comput. Syst. 2018, 80, 640–652. [Google Scholar]
- Yang, Y.; Zhang, B.; Guo, D.; Xiong, Z.; Niyato, D.; Han, Z. Can We Realize Data Freshness Optimization for Privacy Preserving-Mobile Crowdsensing With Artificial Noise? IEEE Trans. Mob. Comput. 2024, 23, 11357–11374. [Google Scholar]
- Wang, W.; Yang, Y.; Xiong, Z.; Niyato, D. Footstone of Metaverse: A Timely and Secure Crowdsensing. IEEE Netw. 2024, 38, 171–178. [Google Scholar]
- Yang, Y.; Zhang, B.; Guo, D.; Xu, R.; Su, C.; Wang, W. Age of Information Optimization for Privacy-preserving Mobile Crowdsensing. IEEE Trans. Emerg. Top. Comput. 2024, 12, 281–292. [Google Scholar]
- Wu, D.; Si, S.; Wu, S.; Wang, R. Dynamic trust relationships aware data privacy protection in mobile crowd-sensing. IEEE Internet Things J. 2017, 5, 2958–2970. [Google Scholar] [CrossRef]
- Gisdakis, S.; Giannetsos, T.; Papadimitratos, P. Security, privacy, and incentive provision for mobile crowd sensing systems. IEEE Internet Things J. 2016, 3, 839–853. [Google Scholar]
- Wang, J.; Du, H.; Niyato, D.; Zhou, M.; Kang, J.; Xiong, Z.; Jamalipour, A. Through the wall detection and localization of autonomous mobile device in indoor scenario. IEEE J. Sel. Areas Commun. 2023, 42, 161–176. [Google Scholar]
- Kaul, S.; Yates, R.; Gruteser, M. Real-time status: How often should one update? In Proceedings of the 2012 Proceedings IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2731–2735. [Google Scholar]
- Zhang, C.; Wu, T.; Zhang, W. Data Privacy and Cybersecurity in Mobile Crowdsensing. Electronics 2025, 14, 1038. [Google Scholar] [CrossRef]
- Wu, D.; Yang, Z.; Yang, B.; Wang, R.; Zhang, P. From centralized management to edge collaboration: A privacy-preserving task assignment framework for mobile crowdsensing. IEEE Internet Things J. 2020, 8, 4579–4589. [Google Scholar]
- He, D.; Chan, S.; Guizani, M. User privacy and data trustworthiness in mobile crowd sensing. IEEE Wirel. Commun. 2015, 22, 28–34. [Google Scholar]
- Liu, Y.; Wang, H.; Peng, M.; Guan, J.; Wang, Y. An incentive mechanism for privacy-preserving crowdsensing via deep reinforcement learning. IEEE Internet Things J. 2020, 8, 8616–8631. [Google Scholar]
- Han, X.; Niu, X.; Chen, L.; Qin, S. Privacy protection strategies in mobile crowdsensing from the framework perspective. In Proceedings of the 2024 29th International Conference on Automation and Computing (ICAC), Sunderland, UK, 28–30 August 2024; pp. 1–6. [Google Scholar]
- Owoh, N.P.; Singh, M.M. Security analysis of mobile crowd sensing applications. Appl. Comput. Inform. 2022, 18, 2–21. [Google Scholar]
- Wang, L.; Zhang, D.; Yang, D.; Lim, B.Y.; Han, X.; Ma, X. Sparse mobile crowdsensing with differential and distortion location privacy. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2735–2749. [Google Scholar]
- Zheng, Y.; Zhou, M.; Wang, S.; Huang, H.; Jia, X.; Yi, X.; Wang, C. SecDR: Enabling secure, efficient, and accurate data recovery for mobile crowdsensing. IEEE Trans. Dependable Secur. Comput. 2023, 21, 789–803. [Google Scholar]
- Li, X.; Zhang, T.; Wang, J.; Han, Z.; Liu, J.; Kang, J.; Niyato, D.; Jamalipour, A. Achieving Network Resilience through Graph Neural Network-enabled Deep Reinforcement Learning. IEEE Netw. 2025. [Google Scholar] [CrossRef]
- Yang, Y.; Zhang, B.; Guo, D.; Wang, W.; Li, X.; Hu, C. PPFO: A privacy preservation-oriented data freshness optimization framework for mobile crowdsensing. IEEE Commun. Stand. Mag. 2023, 7, 34–40. [Google Scholar]
- Zhang, X.; Jiang, L.; Wang, X. Incentive mechanisms for mobile crowdsensing with heterogeneous sensing costs. IEEE Trans. Veh. Technol. 2019, 68, 3992–4002. [Google Scholar]
- Kim, B.D.; Vasudevan, V.A.; Woo, J.; Cohen, A.; D’Oliveira, R.G.L.; Stahlbuhk, T.; Médard, M. CRYPTO-MINE: Cryptanalysis via Mutual Information Neural Estimation. In Proceedings of the ICASSP 2024—2024 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Seoul, Republic of Korea, 14–19 April 2024; pp. 4820–4824. [Google Scholar]
- Kim, J.W.; Edemacu, K.; Jang, B. Privacy-preserving mechanisms for location privacy in mobile crowdsensing: A survey. J. Netw. Comput. Appl. 2022, 200, 103315. [Google Scholar]
- Azhar, S.; Chang, S.; Liu, Y.; Tao, Y.; Liu, G. Privacy-preserving and utility-aware participant selection for mobile crowd sensing. Mob. Netw. Appl. 2022, 27, 290–302. [Google Scholar]
- Wang, J.; Wang, L.; Wang, Y.; Zhang, D.; Kong, L. Task allocation in mobile crowd sensing: State-of-the-art and future opportunities. IEEE Internet Things J. 2018, 5, 3747–3757. [Google Scholar]
- Hu, X.; Li, X.; Ngai, E.C.H.; Leung, V.C.M.; Kruchten, P. Multidimensional context-aware social network architecture for mobile crowdsensing. IEEE Commun. Mag. 2014, 52, 78–87. [Google Scholar]
- Zhu, X.; Liu, J.; Lu, L.; Zhang, T.; Qiu, T.; Wang, C.; Liu, Y. Enabling Intelligent Connectivity: A Survey of Secure ISAC in 6G Networks. IEEE Commun. Surv. Tutor. 2024. [Google Scholar] [CrossRef]
- Dai, Z.; Liu, C.H.; Han, R.; Wang, G.; Leung, K.K.; Tang, J. Delay-sensitive energy-efficient UAV crowdsensing by deep reinforcement learning. IEEE Trans. Mob. Comput. 2021, 22, 2038–2052. [Google Scholar]
- Yang, Y.; Du, H.; Xiong, Z.; Niyato, D.; Jamalipour, A.; Han, Z. Enhancing wireless networks with attention mechanisms: Insights from mobile crowdsensing. arXiv 2024, arXiv:2407.15483. [Google Scholar]
- Zhang, W.; He, Y.; Zhang, T.; Ying, C.; Kang, J. Intelligent Resource Adaptation for Diversified Service Requirements in Industrial IoT. IEEE Trans. Cogn. Commun. Netw. 2024. [Google Scholar] [CrossRef]
- Yang, Y.; Du, H.; Xiong, Z.; Xu, R.; Niyato, D.; Han, Z. Exploring Impacts of Age of Information on Data Accuracy for Wireless Sensing Systems: An Information Entropy Perspective. IEEE Trans. Mob. Comput. 2025. [Google Scholar] [CrossRef]
- Rakhmanov, A.; Wiseman, Y. Compression of GNSS data with the aim of speeding up communication to autonomous vehicles. Remote Sens. 2023, 15, 2165. [Google Scholar] [CrossRef]
- Yang, Y.; Chen, Y.; Wang, J.; Sun, G.; Niyato, D. Embodied AI-empowered Low Altitude Economy: Integrated Sensing, Communications, Computation, and Control (ISC3). arXiv 2024, arXiv:2412.19996. [Google Scholar]
- Maitra, T.; Obaidat, M.S.; Giri, D.; Dutta, S.; Dahal, K. ElGamal cryptosystem-based secure authentication system for cloud-based IoT applications. IET Netw. 2019, 8, 289–298. [Google Scholar] [CrossRef]
- Hussein, H.I.; Abduallah, W.M. An efficient ElGamal cryptosystem scheme. Int. J. Comput. Appl. 2021, 43, 1088–1094. [Google Scholar] [CrossRef]
- Wang, J.; Du, H.; Liu, Y.; Sun, G.; Niyato, D.; Mao, S.; Kim, D.I.; Shen, X. Generative AI based Secure Wireless Sensing for ISAC Networks. arXiv 2024, arXiv:2408.11398. [Google Scholar]
- Wang, J.; Du, H.; Niyato, D.; Kang, J.; Cui, S.; Shen, X.S.; Zhang, P. Generative AI for integrated sensing and communication: Insights from the physical layer perspective. IEEE Wirel. Commun. 2024, 31, 246–255. [Google Scholar] [CrossRef]
- Yang, Y.; Du, H.; Sun, G.; Xiong, Z.; Niyato, D.; Han, Z. Exploring Equilibrium Strategies in Network Games with Generative AI. IEEE Netw. 2024. [Google Scholar] [CrossRef]
- Liu, Y.; Zhao, Y. A blockchain-enabled Framework for Vehicular Data sensing: Enhancing information freshness. IEEE Trans. Veh. Technol. 2024, 73, 17416–17429. [Google Scholar] [CrossRef]
- Ying, C.; Hai, J.; Li, J.; Si, X.; Luo, Y. Incentive mechanism design via smart contract in blockchain-based edge-assisted crowdsensing. Front. Comput. Sci. 2025, 19, 193802. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).