Lightweight IoT Authentication Protocol Using PUFs in Smart Manufacturing Industry
Abstract
:1. Introduction
1.1. Related Work
1.2. Motivations and Contributions
- We present a secure and efficient mutual authentication protocol based on PUFs, specifically developed for IoT environments. This protocol guarantees essential security attributes such as confidentiality, integrity, anonymity, unlinkability, and untraceability.
- To resolve clock synchronization challenges, our protocol replaces traditional nonces with timestamps, ensuring accuracy and reliability.
- The security of the proposed protocol is rigorously verified using the established Burrows–Abadi–Needham (BAN) logic framework and assessed using the SPAN/AVISPA tool. Additionally, an informal security analysis is provided to further validate the protocol.
- A comparison of our protocol with existing solutions highlights its superior performance in terms of both security robustness and efficiency.
2. Network and Adversary Model
2.1. IoT Network Model
2.2. Adversary Model
- The server node (S) is considered trustworthy in terms of its legitimate operation and authentication capabilities, but it may be vulnerable to an adversary gaining unauthorized access to its database. This could allow the adversary to steal or manipulate stored information. However, the server’s master secret key (KS) remains secure.
- The adversary has the ability to eavesdrop on all links within the network and may replace or replay previously transmitted messages.
- An adversary can capture any sensor node (SN), granting them access to all confidential information stored in the node’s memory. A full security breach occurs for the captured node. However, this should not compromise the confidentiality of other uncaptured nodes in the network.
- Our security framework is based on the well-established Dolev–Yao threat model [17], which considers communication between two entities over an untrusted channel. The evaluation of our protocol’s security, including analysis and simulation, is performed within this model.
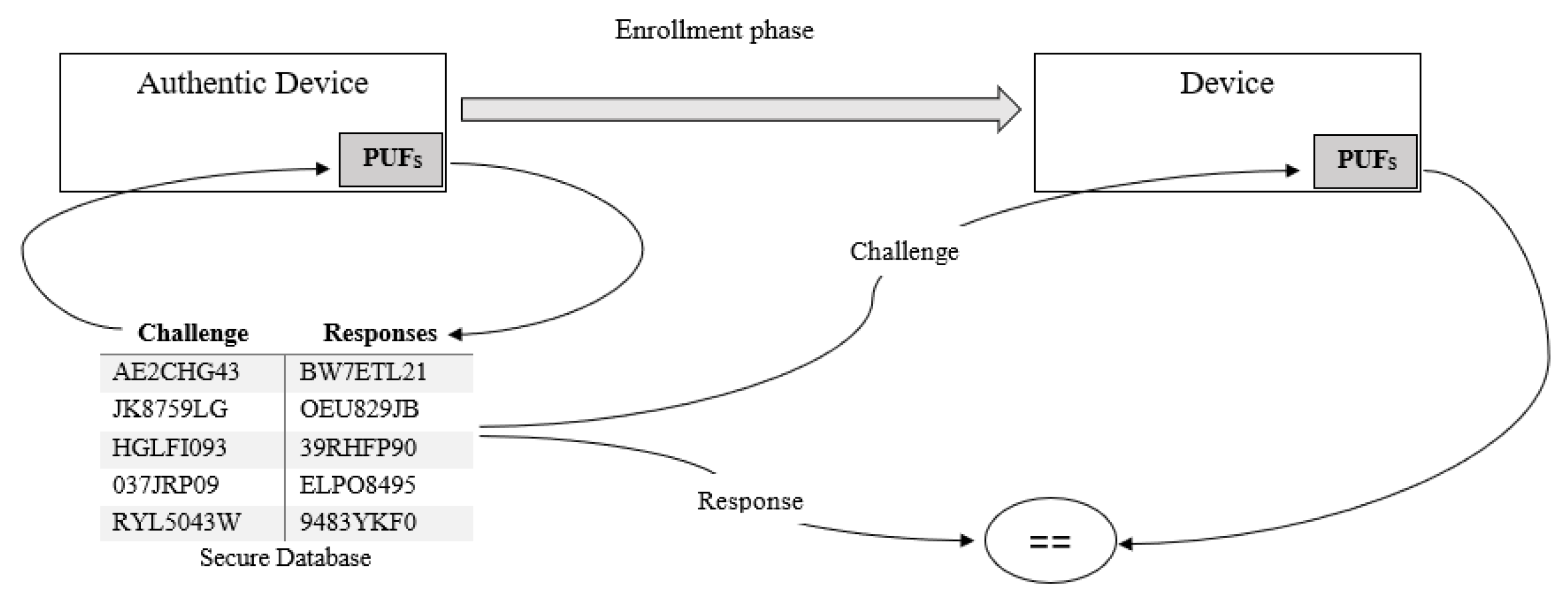
2.3. Challenge–Response Mechanism Based on PUF Model
3. Proposed Protocol
3.1. Initialization Phase
- The SA selects a master secret key for the server (S).
- The SA securely stores in the memory of the server (S).
- The SA embeds a PUF in the server (S) and applies a set of randomly chosen challenges (C), storing the corresponding responses (R) in the PUF-S database for future authentication.
- Similarly, the SA applies a set of challenges (C) to the PUF embedded in the SN and stores the responses (R) in the PUF-SN database.
- The SA securely stores the PUF-S database in the memory of SN.
- The SA securely stores the PUF-SN database in the memory of server (S).
3.2. Registration Phase
- The SA assigns a unique secret identity for SN.
- The SA selects a temporary secret key for SN.
- The SA computes:
- The SA stores the tuple in the SN’s memory.
- The SA stores in the server (S)’s memory.
3.3. Authentication Phase
3.3.1. A: At the IoT Sensor Node (SN)
- The SN computes a temporary identity:where N is a nonce (randomly generated number), and represents the incremented version of the nonce to ensure uniqueness in each authentication session.
- The SN selects temporary parameters .
- The SN generates a timestamp .
- The SN picks a random challenge from the PUF-S database.
- The SN retrieves the corresponding response .
- The SN computes
- The SN computes a message integrity value:
- The SN sends to the S.
3.3.2. B: At the Server (S)
- The S verifies the timestamp .
- The S checks
- The S computes the message integrity value and verifies it.
- The S applies the challenge to the PUF and retrieves .
- The S computes
3.3.3. Server Prepares Response
- The S selects and generates a timestamp .
- The S picks a challenge from the PUF-SN database and retrieves .
- The S computes
- The S computes the session secret key:
- The S sends to the SN.
3.3.4. C: At the IoT Sensor Node (SN)
- The SN verifies , timestamp , and computes .
- The SN applies the challenge to the PUF and retrieves .
- The SN computes
- The SN computes the session secret key:
4. Security Evaluation
4.1. Informal Security Evaluation
4.1.1. Replay Attack
4.1.2. Eavesdropping Threats
4.1.3. Anonymous and Unlinkable Sessions
4.1.4. Security of Forward and Backward Integrity
4.1.5. Attack on Session Key Prediction
4.1.6. Attack on the Man-in-the-Middle Protocol
4.1.7. Identity Spoofing Attack
4.1.8. Authentication Using Physical Unclonable Functions (PUFs)
4.2. Formal Verification Using BAN Logic
4.2.1. Fundamentals of BAN Logic
- MMR (MMR): If P observes X protected with Y, and P assumes that Y is a secret key shared with S, then P infers that S has previously sent X.
- Nonce Verification Principle: If P is confident that X is new and that X was previously communicated by S, P will infer that S also acknowledges the validity of X.
- Authority Rule: If P believes that S has authority over X and P also believes that S recognizes X, then P accepts X as true.
- Freshness Combination Rule: If a component of a formula is considered fresh, then the whole formula is regarded as fresh. Therefore, if P believes X is fresh, P also believes that both X and Y are fresh.
- Belief Principle: If P believes both X and Y, then P must also believe X.
- Observation Principle: If P observes both X and Y, then P will also observe X.
4.2.2. Analysis Goals for Our Authentication Protocol
- Goal 1: S is confident that the SN acknowledges the XSN as a secure shared parameter between the SN and S.
- 2.
- Goal 2: The S is confident that is a secure shared parameter between the SN and S.
- 3.
- Goal 3: The SN is assured that the S considers the SSK as a securely shared parameter between the SN and S.
- 4.
- Goal 4: The SN is confident that the SSK serves as a securely shared parameter between the SN and S.
4.2.3. Messages Exchanged During Authentication
- M1: SN → S:
- M2: S → SN:
4.2.4. Introductory Assumptions
- A1: The S believes is a confidential shared parameter between the SN and S: SN ∣≡ (SN )
- A2: The S believes is fresh: S∣≡#()
- A3: The SN believes the XSN is a confidential shared parameter between the SN and S: SN ∣≡ (SN )
- A4: The S believes is a confidential shared parameter between the SN and S: S ∣≡ (SN )
- A5: The SN believes is fresh: SN |≡ #().
- A6: The SN believes the SSK is a secure shared parameter between the SN and S: SN ∣≡S∣≡ (SN )
- A7: The SN believes the S has jurisdiction over , XSN and MI: SN∣≡S∣⇒{, XSN, MI}
- A8: The S believes the SN has jurisdiction over XSN, SSK, and MI: S∣≡ SN ∣⇒{XSN, SSK, MI}
4.2.5. Analysis of Our Authentication Scheme
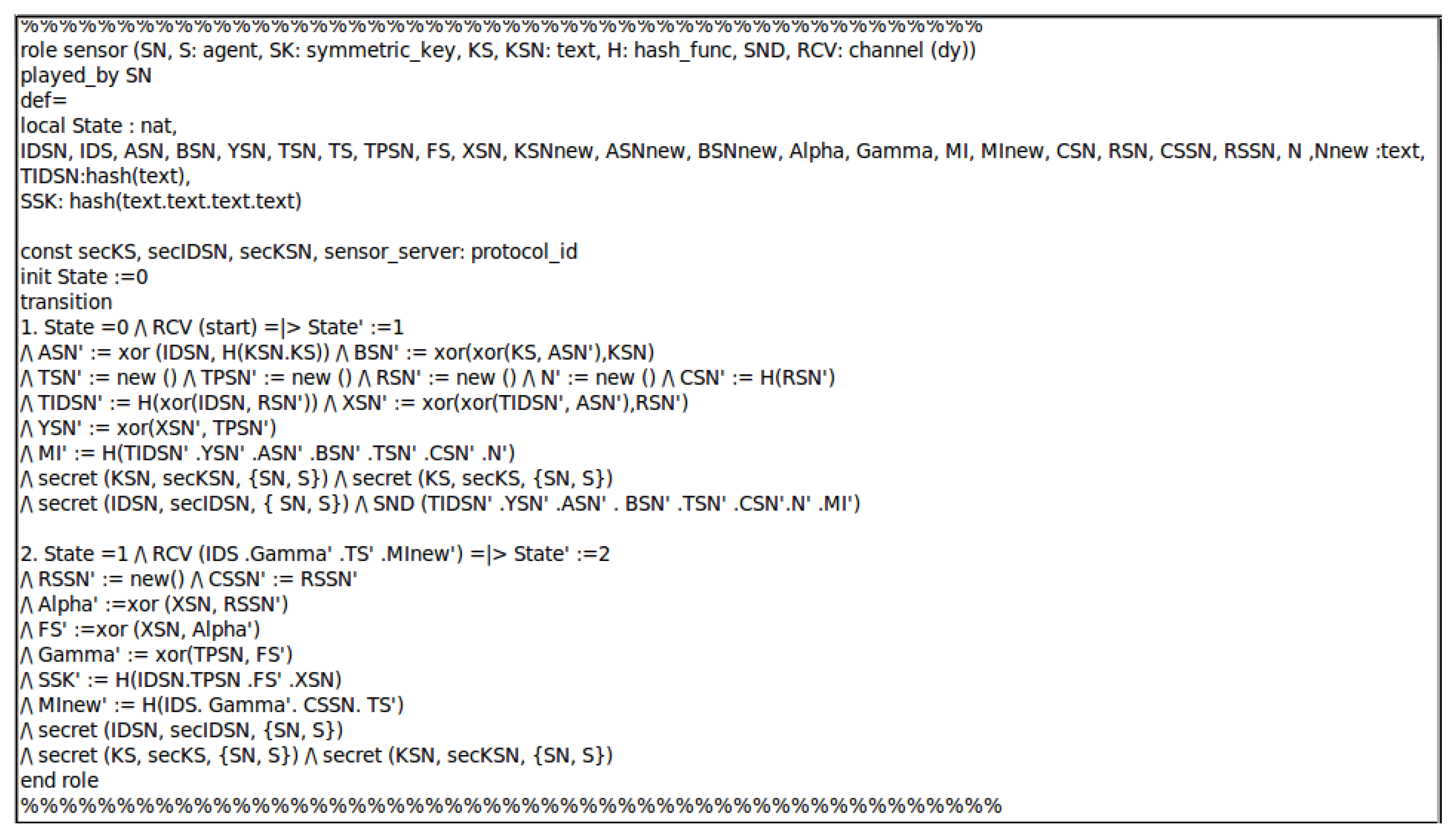
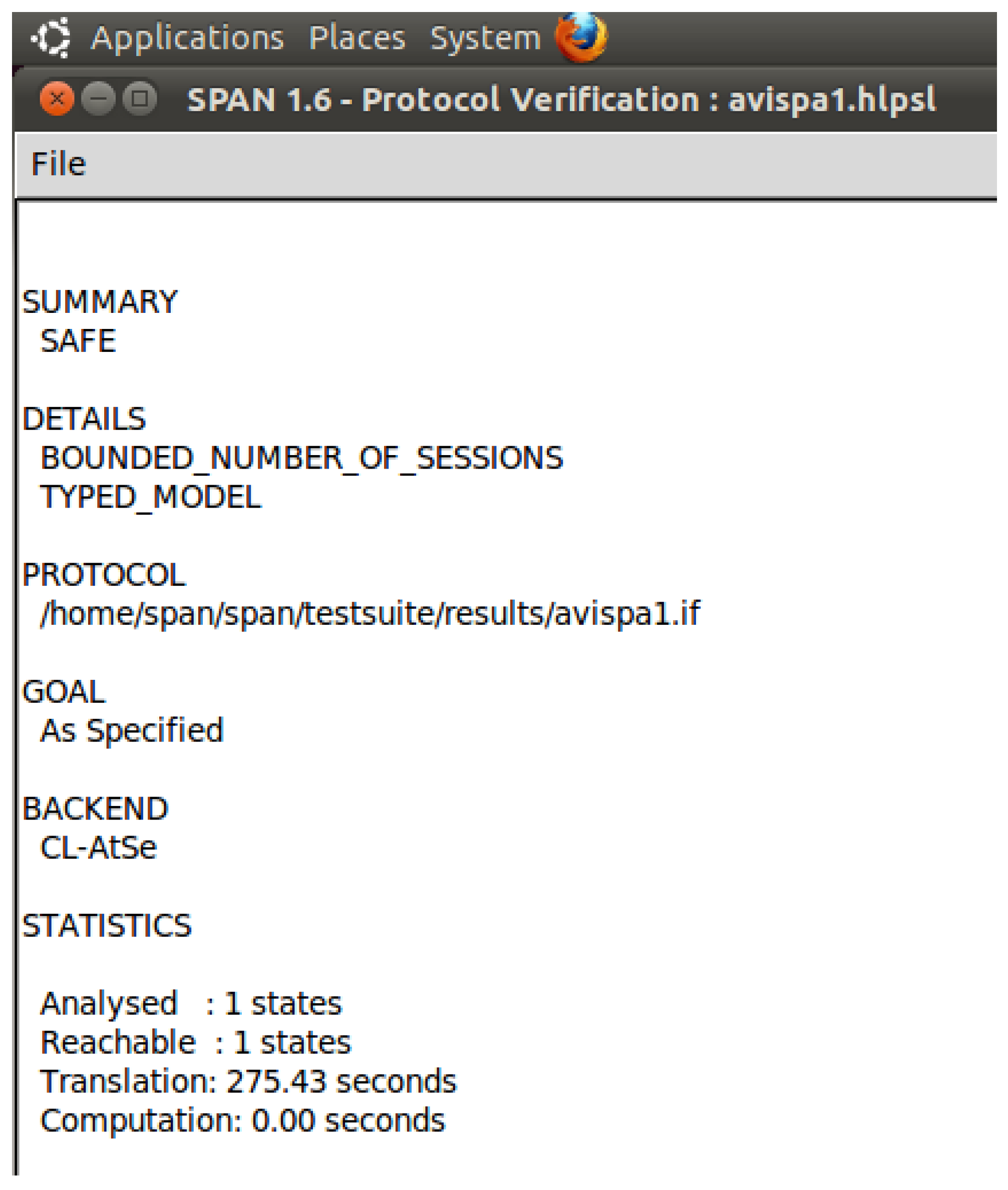
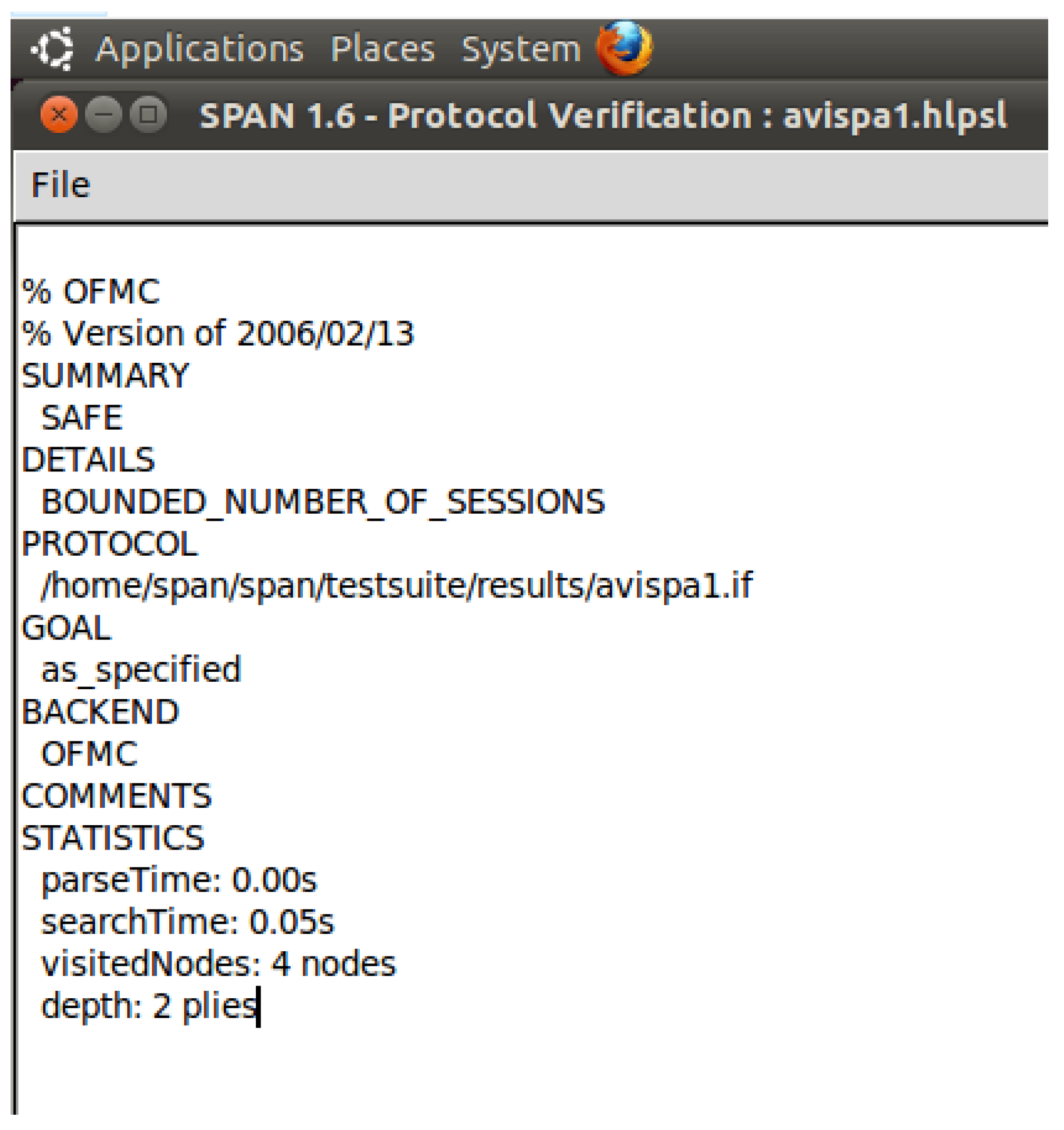
4.3. Formal Proof Using the AVISPA Tool
5. Evaluation of Performance
5.1. Communication Overheads
5.2. Computation Cost
5.3. Computation Time and Energy Consumption
5.4. Storage Requirements
5.5. Comparisons with Other Schemes
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Majumdar, S.; Awasthi, A. From Vulnerability to Resilience: Securing Public Safety GPS and Location Services with Smart Radio, Blockchain, and AI-Driven Adaptability. Electronics 2025, 14, 1207. [Google Scholar] [CrossRef]
- Abd Elaziz, M.; Dahou, A.; Aseeri, A.O.; Ewees, A.A.; Al-Qaness, M.A.; Ibrahim, R.A. Cross vision transformer with enhanced Growth Optimizer for breast cancer detection in IoMT environment. Comput. Biol. Chem. 2024, 111, 108110. [Google Scholar] [CrossRef] [PubMed]
- Sabit, H. Artifical Intelligence-Based Smart Security System Using Internet of Things for Smart Home Applications. Electronics 2025, 14, 608. [Google Scholar] [CrossRef]
- Al-Qaness, M.A.; Ewees, A.A.; Abd Elaziz, M.; Dahou, A.; Al-Betar, M.A.; Aseeri, A.O.; Yousri, D.; Ibrahim, R.A. Boosted barnacles algorithm optimizer: Comprehensive analysis for social IoT applications. IEEE Access 2023, 11, 73062–73079. [Google Scholar] [CrossRef]
- Thoben, K.D.; Wiesner, S.; Wuest, T. Industrie 4.0 and smart manufacturing–A review of research issues and application examples. Int. J. Autom. Technol. 2017, 11, 4–16. [Google Scholar] [CrossRef]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Kalra, S.; Sood, S.K. Secure authentication scheme for IoT and cloud servers. Pervasive Mob. Comput. 2015, 24, 210–223. [Google Scholar] [CrossRef]
- Patil, S.S.; Biradar, A. Novel authentication framework for securing communication in internet-of-things. Int. J. Electr. Comput. Eng. 2020, 10, 1092. [Google Scholar] [CrossRef]
- Liu, J.; Li, Q.; Yan, R.; Sun, R. Efficient authenticated key exchange protocols for wireless body area networks. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 188. [Google Scholar] [CrossRef]
- Li, M.; Xiong, M.; Hamada Ibrahim, M.; Kumari, S.; Sangaiah, A.K.; Gupta, V.; Choo, K.K.R. Anonymous mutual authentication and key agreement scheme for wearable sensors in wireless body area networks. Comput. Netw. 2017, 129, 429–443. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF based authentication and key exchange protocol for IoT without explicit CRPs in verifier database. IEEE Trans. Dependable Secur. Comput. 2018, 16, 424–437. [Google Scholar] [CrossRef]
- Rullo, A.; Felicetti, C.; Vatalaro, M.; De Rose, R.; Lanuzza, M.; Crupi, F.; Sacca, D. Puf-based authentication-oriented architecture for identification tags. IEEE Trans. Dependable Secur. Comput. 2024, 22, 66–83. [Google Scholar] [CrossRef]
- Alsheavi, A.; Hawbani, A.; Othman, W.; Wang, X.; Qaid, G.; Zhao, L.; Al-Dubai, A.; Zhi, L.; Samy, A.; Jhaveri, R.H.; et al. IoT Authentication Protocols: Challenges, and Comparative Analysis. ACM Comput. Surv. 2024, 57, 1–43. [Google Scholar] [CrossRef]
- Kamarudin, N.H.; Suhaimi, N.H.S.; Nor Rashid, F.A.; Khalid, M.N.A.; Mohd Ali, F. Exploring Authentication Paradigms in the Internet of Things: A Comprehensive Scoping Review. Symmetry 2024, 16, 171. [Google Scholar] [CrossRef]
- Laghari, A.A.; Li, H.; Khan, A.A.; Shoulin, Y.; Karim, S.; Khani, M.A.K. Internet of Things (IoT) applications security trends and challenges. Discov. Internet Things 2024, 4, 36. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. London. Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In Proceedings of the International Conference on Computer Aided Verification, Scotland, UK, 6–10 July 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- STMicroelectronics. STM32F103VE: Mainstream Performance Line, Arm Cortex-M3 MCU with 512 Kbytes of Flash Memory, 72 MHz CPU, Motor Control, USB and CAN. 2025. Available online: https://www.st.com/en/microcontrollers-microprocessors/stm32f103ve.html (accessed on 19 January 2025).
- Huang, J.J.; Juang, W.S.; Fan, C.I.; Liaw, H.T. Robust and privacy protection authentication in cloud computing. Int. J. Innov. Comput. Inf. Control 2013, 9, 4247–4261. [Google Scholar]
- Cao, X.; Kou, W.; Du, X. A pairing-free identity-based authenticated key agreement protocol with minimal message exchanges. Inf. Sci. 2010, 180, 2895–2903. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S. Authentication protocol for an ambient assisted living system. IEEE Commun. Mag. 2015, 53, 71–77. [Google Scholar] [CrossRef]
- Zhao, Z. An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 2014, 38, 13. [Google Scholar] [CrossRef] [PubMed]
- Liu, J.; Zhang, Z.; Chen, X.; Kwak, K.S. Certificateless remote anonymous authentication schemes for wireless body area networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 332–342. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J.H. Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 2016, 11, 2590–2601. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, L.; Sun, R. 1-Raap: An efficient 1-round anonymous authentication protocol for wireless body area networks. Sensors 2016, 16, 728. [Google Scholar] [CrossRef]


| Notation | Description |
|---|---|
| S | Server (S). |
| SA | System administrator (SA). |
| SN | IoT sensor node (SN). |
| Temporary confidential parameters selected by the S. | |
| Temporary confidential parameters selected by the SN. | |
| Timestamp generated by the S. | |
| Timestamp generated by the SN. | |
| N | Nonce (random number) used for freshness in communication. |
| Temporary identity of the SN. | |
| Permanent identity of the SN. | |
| Challenge value stored in the SN table for communication with the S. | |
| Response value stored in the SN table for communication with the S. | |
| Master secret key of the S or the PC. | |
| , | Temporary confidential parameters selected by the S for the SN. |
| SSK | Session secret key to be agreed upon for secure communication. |
| , | Authentication-related parameters securely stored within the SN’s memory. |
| h(..) | Collision-resistant one-way cryptographic hash function. |
| , , y, , | Authentication parameters used by the S for authentication with the SN. |
| , | Auxiliary parameters used for authentication. |
| XY:Z | Entity X transmits message Z to entity Y over a publicly accessible communication channel. |
| ⊕ | Bitwise XOR operation. |
| t | Timestamp or time value used to ensure the freshness of the communication. |
| C | Cryptographic challenge or commitment value. |
| MI | Message Integrity value to ensure message authenticity and integrity. |
| XSN | Shared secret key between the SN and the S for secure communication. |
| MMR | Message meaning rule |
| Notation | Description |
|---|---|
| P|≡ X | (P believes X) P is authorized to act as though X is true. |
| P ⊲ X | (P sees X) a message sent to X. |
| P |∼ X | At a certain point in time P sent X. Furthermore, at the time of sending, P believed X. |
| P |→ X | (P has authority over X) P is a trusted source for X. |
| #(X) | (X is fresh) meaning that X has not been sent before in any run of the protocol. |
| (X, Y) | X or Y is a part of (X, Y). |
| X combined with Y. | |
| P↔S | K is a confidential parameter shared between P and S. |
| P | (P and S share secret X) X is a confidential known only to P, S and possibly some trusted associates. |
| Between Nodes | Cost |
|---|---|
| SN → S | 992 bits |
| S → SN | 528 bits |
| Node | Storage Cost (in Bits) | Computation Cost |
|---|---|---|
| SN | 960 | 4 + 5 ≈ 4 |
| S | 16m + 160 | 4thash+ 5 ≈ 4 |
| Node | Computation Time (ms) | Energy Consumption (mJ) |
|---|---|---|
| SN | 0.24 | 0.0285 |
| S | 0.24 | 0.0285 |
| Symbol | Description | Cost |
|---|---|---|
| One SHA-1 hash invocation | ||
| ECC scalar multiplication | 72.5 | |
| Symmetric enc. | Th | |
| Modular addition | 0.3 | |
| ECC point addition | 13 | |
| Modular multiplication | 2.5 | |
| ECC map-to-point | 450 | |
| Modular exponentiation | 600 |
| Protocol | Computation Cost | Computation Time | Energy |
|---|---|---|---|
| Liu et al. [25] | 6 + 2 + 4 + 1 + 1 = 2534 | 152.040 ms | 18.060 mJ |
| He-Zeadally [26] | + 1 + 1 + 4 = 757 | 45.420 ms | 5.40 mJ |
| Zhao [24] | 5 + 1 + 6 = 441 | 26.460 ms | 3.140 mJ |
| Liu et al. [27] | 2 + 2 + 1 + 2 + 3 + 1 = 180.80 | 10.8480 ms | 1.290 mJ |
| He-Zeadally [23] | 1 + 2 + 2 = 148 | 8.88 ms | 1.06 mJ |
| Li et al. [10] | 5 + 11 = 5 | 0.3 ms | 0.035 mJ |
| Proposed scheme | 4 + 5 = 4 | 0.24 ms | 0.28 mJ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alharthi, A.M.; Altuwaijri, F.S. Lightweight IoT Authentication Protocol Using PUFs in Smart Manufacturing Industry. Electronics 2025, 14, 1788. https://doi.org/10.3390/electronics14091788
Alharthi AM, Altuwaijri FS. Lightweight IoT Authentication Protocol Using PUFs in Smart Manufacturing Industry. Electronics. 2025; 14(9):1788. https://doi.org/10.3390/electronics14091788
Chicago/Turabian StyleAlharthi, Abdullah M., and Fahad S. Altuwaijri. 2025. "Lightweight IoT Authentication Protocol Using PUFs in Smart Manufacturing Industry" Electronics 14, no. 9: 1788. https://doi.org/10.3390/electronics14091788
APA StyleAlharthi, A. M., & Altuwaijri, F. S. (2025). Lightweight IoT Authentication Protocol Using PUFs in Smart Manufacturing Industry. Electronics, 14(9), 1788. https://doi.org/10.3390/electronics14091788





