SmartContent—Self-Protected Context-Aware Active Documents for Mobile Environments
Abstract
:1. Introduction
2. Related Works
2.1. Traditional Techniques
2.2. Context-Aware Solutions
2.3. Analysis and Comparison
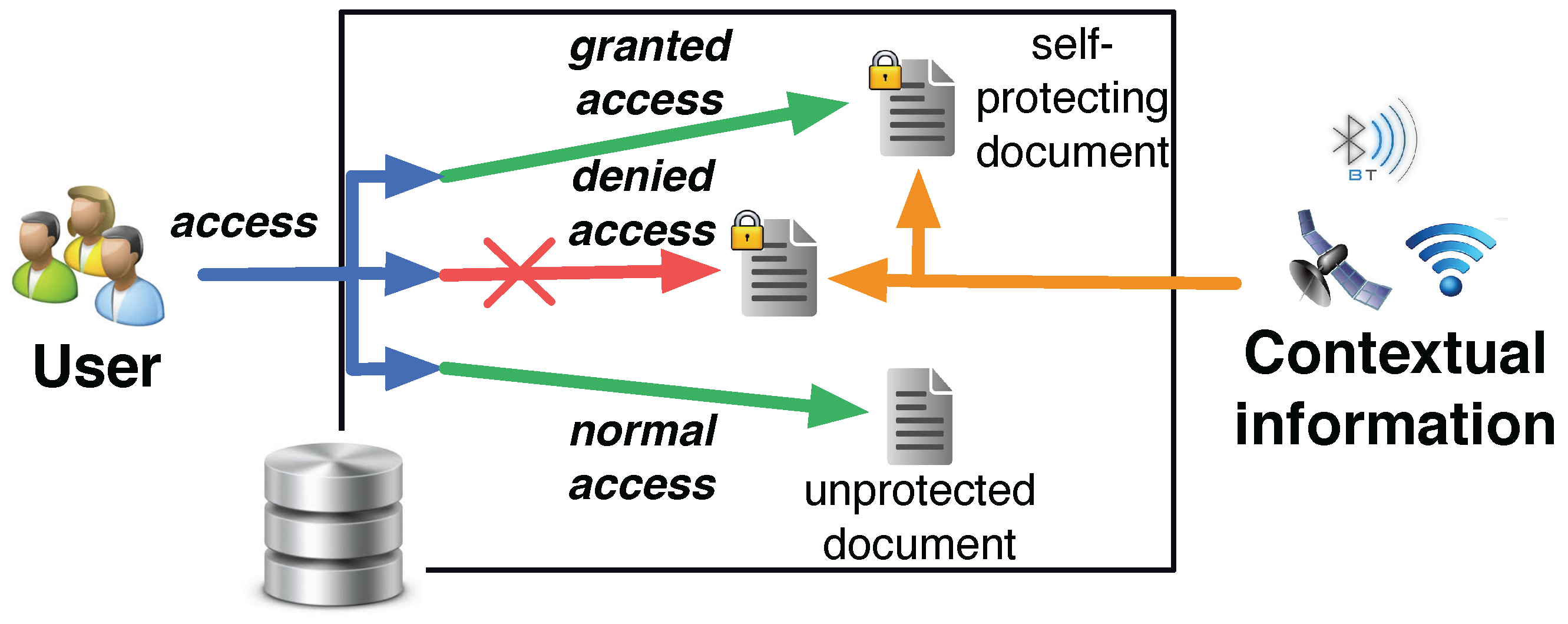
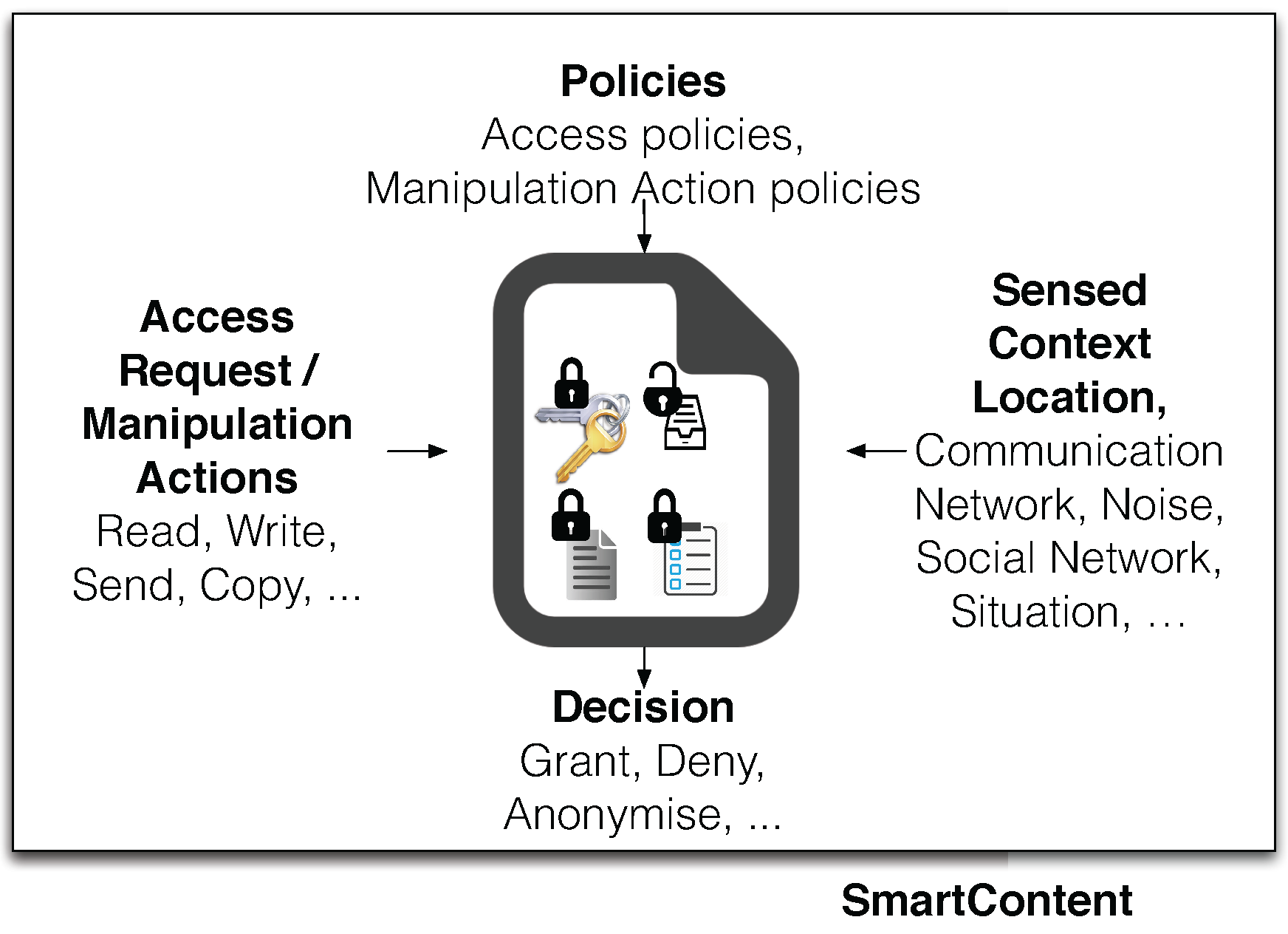
3. Generic Model and Approach
3.1. Contextual Information
- Contextual-based information: generated from distinct contextual data sources and based on physical or virtual sensor data such as biometric information, current location, current viewer, near Bluetooth/Wi-Fi devices, third-party applications data, etc. Each contextual data source is represented as a set of contextual data values . The whole set of contextual data values forms a multidimensional space called contextual space, composed of as many dimensions as the total number of sources.
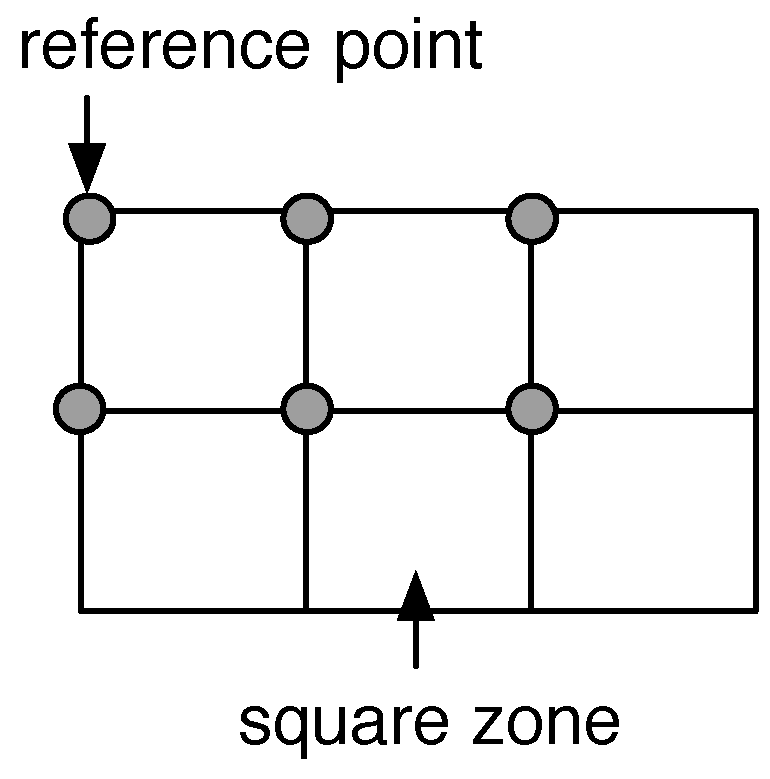
- Situational-based information: generated from the fusion of several contextual-based information gathered over some time periods. We call situational space the extension of the contextual space in which we consider also an additional temporal dimension. Generally speaking, a state of the system is a set of contextual data values belonging to distinct sources, including also a reference to a temporal dimension. A state is then represented by a point in the situational space. By sorting a set of states in ascending order with respect to the temporal dimension we obtain a sequence that represents an evolution of the system. We use the term situation to indicate a transformation of a set of states, i.e., information representative of the evolution of the system. is the set of all values referring to the same typology of situation called . Situational-values may require some manipulations to be representative; for example, when using GPS traces, single high-precision coordinates are difficult to be reproduced. In this case, situational-values belonging to particular ranges (there may be several dimensions) are replaced by reference values representative for such ranges (Figure 3).
3.2. Policies
- Reading policies: define the rules to access to the protected content of a SmartContent document. They identify subspaces of the situational and the contextual space that must be detected to read the internal content. Reading policies form the basic level of protection offered by SmartContent documents and they are intrinsically implemented within the documents.
- Manipulation policies: define the rules to restrict manipulation actions on SmartContent documents, like local or remote copies, renaming, etc. Manipulation policies are optional and resort to a reasoning unit trusted by the owner of the document.
3.3. Internal Structure, Creation and Access to SmartContent Documents
- I
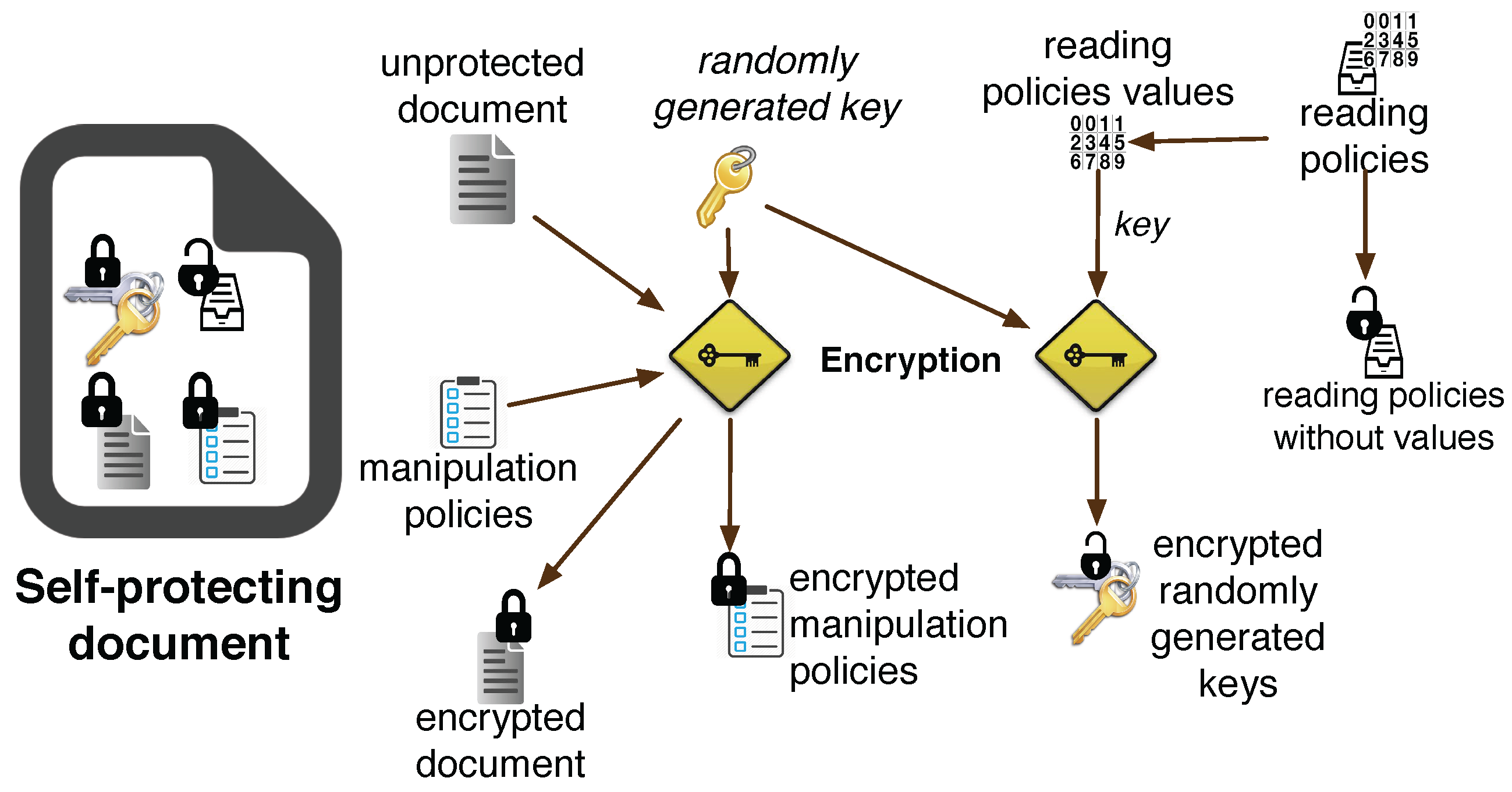
- The creator of the SmartContent document selects an unprotected document and specifies its policies by defining (a) a list of predicates; (b) some logical connectives and (c) some values belonging to the contextual data sources and to the situations .
- II
- A randomly generated symmetric key is used to encrypt the unprotected document and the manipulation policies with a symmetric encryption algorithm (e.g., AES).
- III
- Depending on the logical connectives, values are combined (for example by using a hash function like SHA-3) to create one or more encrypted versions of . These keys are used to recover depending on the contextual and situational values available at a given time. Managing logical connectives efficiently and secret sharing techniques can reduce the number of keys. The contextual and situational spaces represent the key space of the symmetric encryption schema, so should be sets sufficiently large to assure a robust key space.
- IV
- All the encrypted objects are stored in a new file along with the reading policy predicates devoid of contextual and situational information values. According to the structure described so far, reading policy predicates are stored in the document without being encrypted: this fact does not affect the security of the document because the contextual and situational values used to create the encryption keys are unknown. Manipulation policy predicates, instead, are always encrypted within the document because they carry on also the associated values.
- I
- By analysing the unencrypted predicates of reading policies, a set of contextual data sources and situations are selected to obtain the set of values . Such a set identifies the current sensed context, i.e., the subspace of the contextual-situational space describing the environment in which the system is currently operative.
- II
- If satisfies the readable policies then at least one of the encrypted versions of can be decrypted. In this case the environment satisfies the criteria imposed by the policies.
- III
- With , the internal content of the document and the manipulation policies can be finally decrypted.
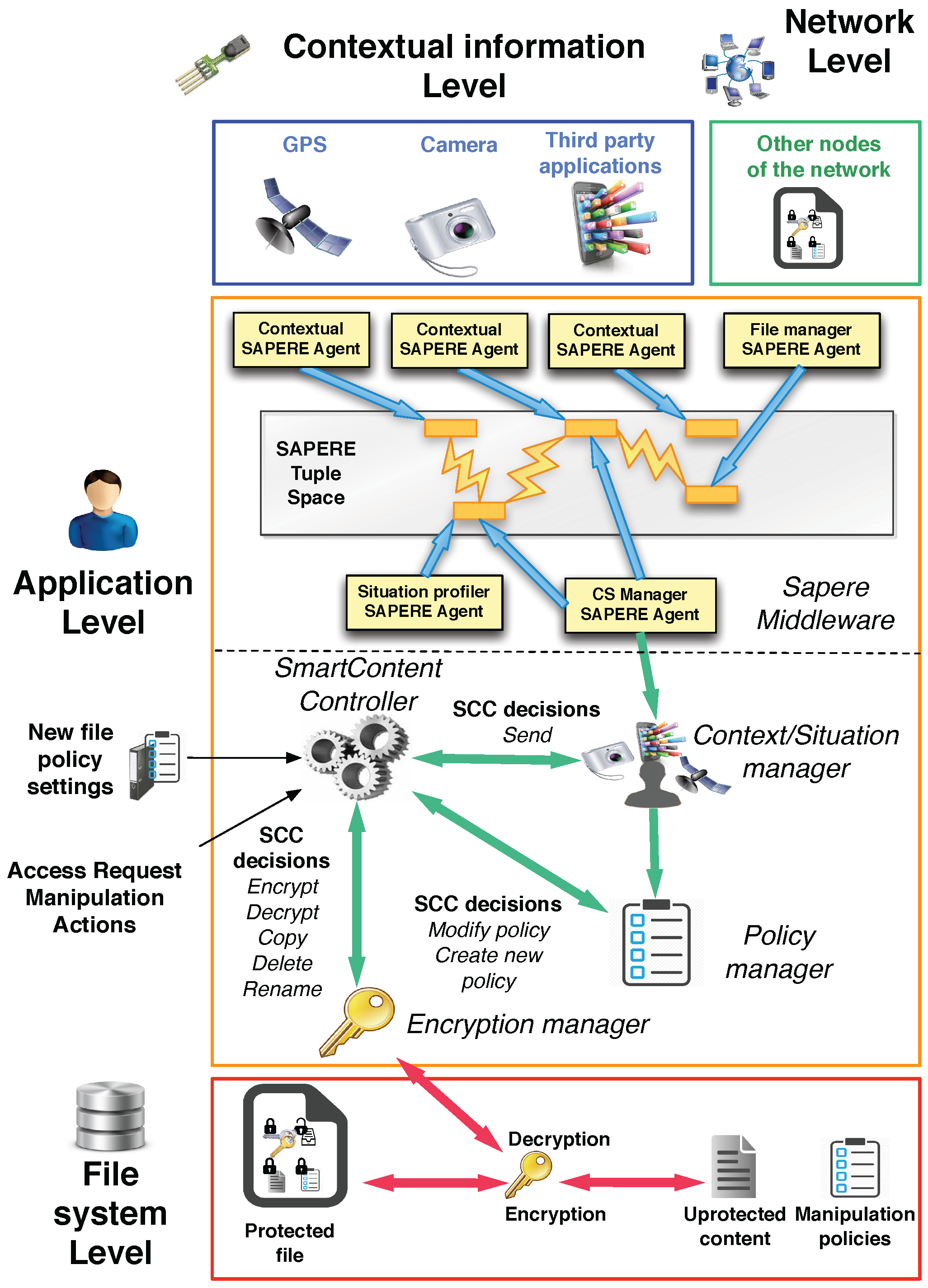
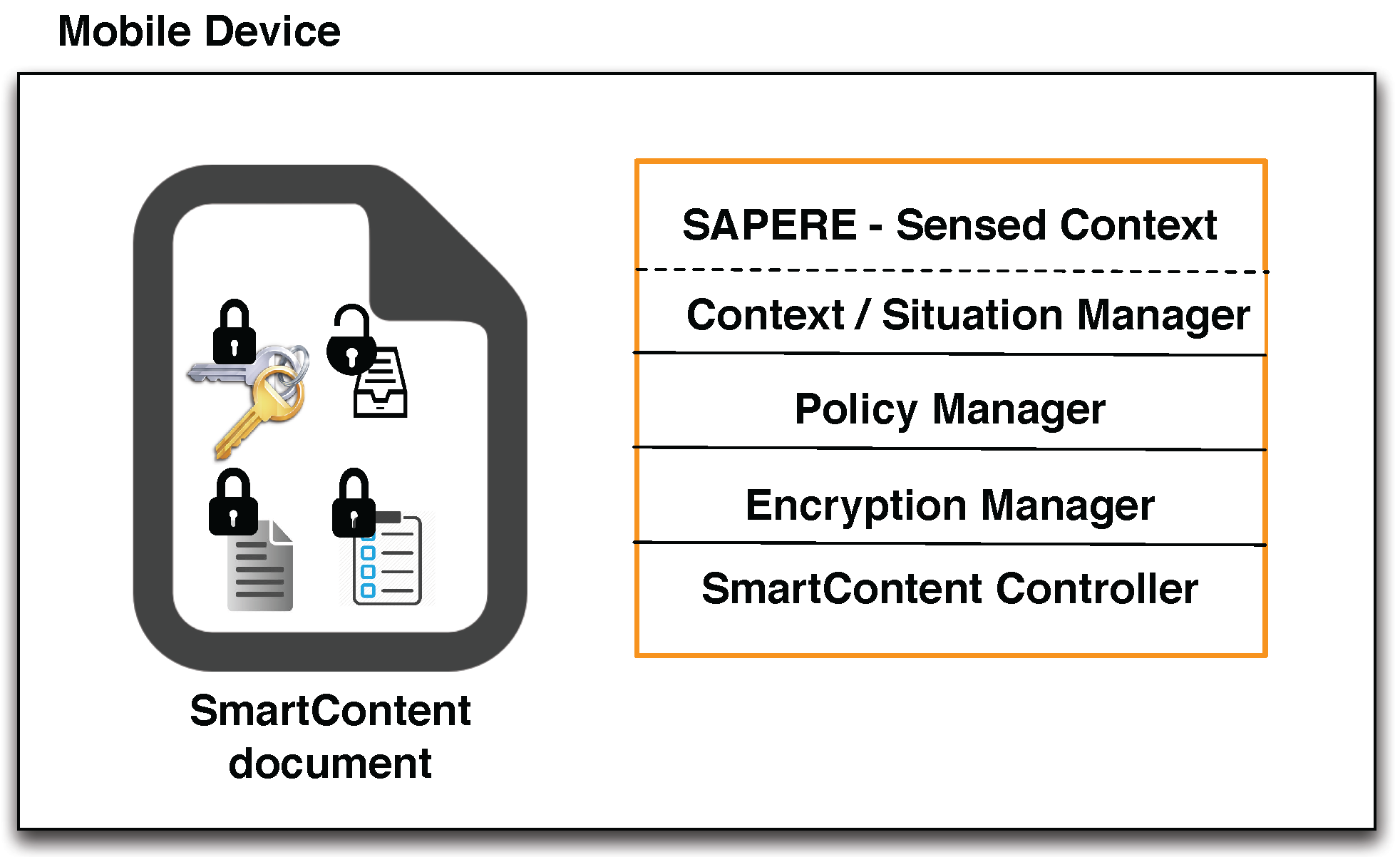
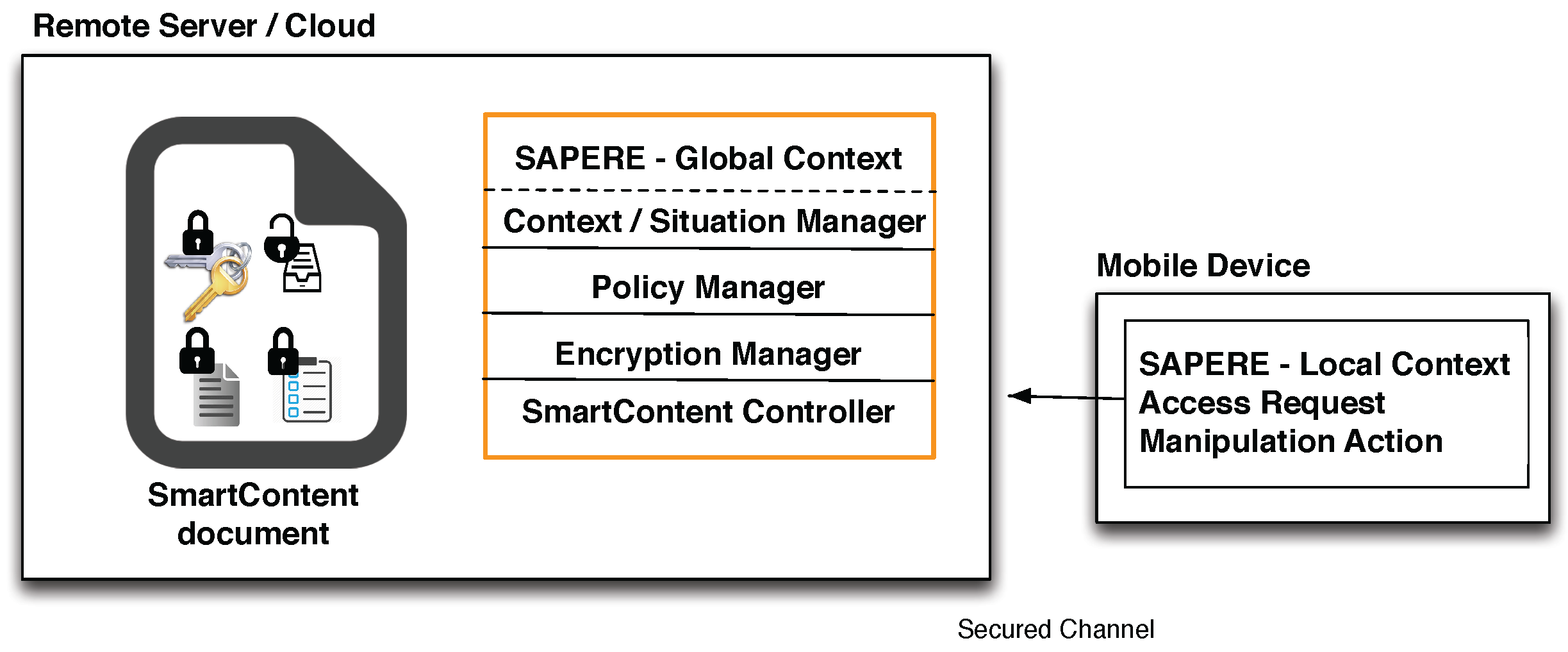
4. Architecture and Implementation
4.1. SAPERE Middleware
4.2. Architecture
- SAPERE middleware: used to have a common model for representing, collecting and spreading contextual and situational information. Every contextual data source (e.g., GPS sensor, accelerometer sensor, third-party application such as calendar, address book, etc.) is managed by a contextual agent, which injects the associated contextual information in the tuple space under the form of LSA. Resorting to the functionalities provided by the Eco-laws, specialized agents named situation profilers produce situational information by aggregating LSAs injected by contextual agents. LSA can also encapsulate SmartContent documents shared with other nodes of the network, handled by specialized agents named file managers. This feature assures that information shared among nodes is managed by resorting to the functionalities provided by middleware. SAPERE is used to handle contextual and situation information and to send and receive SmartContent documents towards and from other nodes of the network. An agent called Context/Situation (CS) Manager Agent, which connects the framework to the Context/Situation manager, represents the interface with the remaining components of the architecture.
- Context/Situation manager: component charged to manage contextual and situational information, acting as an intermediary unit between the SAPERE middleware, the SmartContent Controller and the Policy manager. It also notifies the SmartContent Controller when a document is received from another node, and analogously it is invoked when a document must be sent through the network.
- Policy manager: component charged to manage the reading and manipulation policies of the SmartContent documents existing in the system. It is connected to the Context/Situation manager to access the information about the context and to the Controller to inform it about changes in the manipulation policies. The Policy manager is charged to manage both the policies of an existing SmartContent document as well as the new policies introduced by a user during the creation of a new document. When the policies of a document become unsatisfied, the component notifies the controller, which requests the Encryption manager to re-encrypt the document.
- SmartContent Controller: main unit orchestrating all other components of the application. Through an interface it also receives the external commands issued by users (e.g., creation of a new SmartContent document).
- Encryption manager: component managing the authorized manipulation actions on a SmartContent document. Given that it implements the encryption/decryption algorithms and the routines to access the internal content and policies, it acts as the interface between the file system and the SmartContent Controller, implementing the security functionalities to encrypt, decrypt, copy, delete, rename a SmartContent document when a notification is generated by the SmartContent Controller. Moreover, it is also charged to recover the (internal) Manipulation Policies of the document once accessible, passing them to the SmartContent Controller.
4.3. Security Analysis
4.4. Implementation
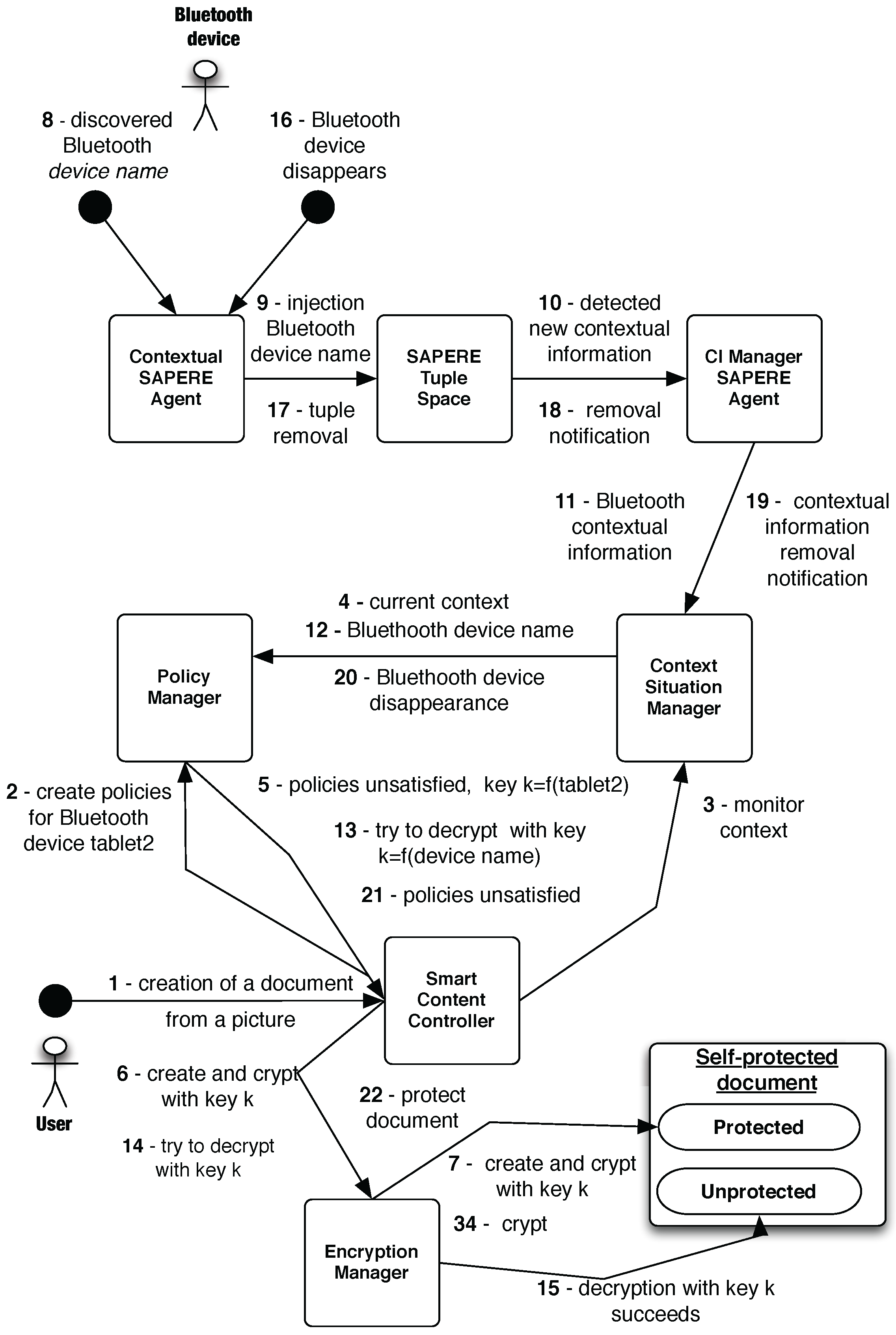
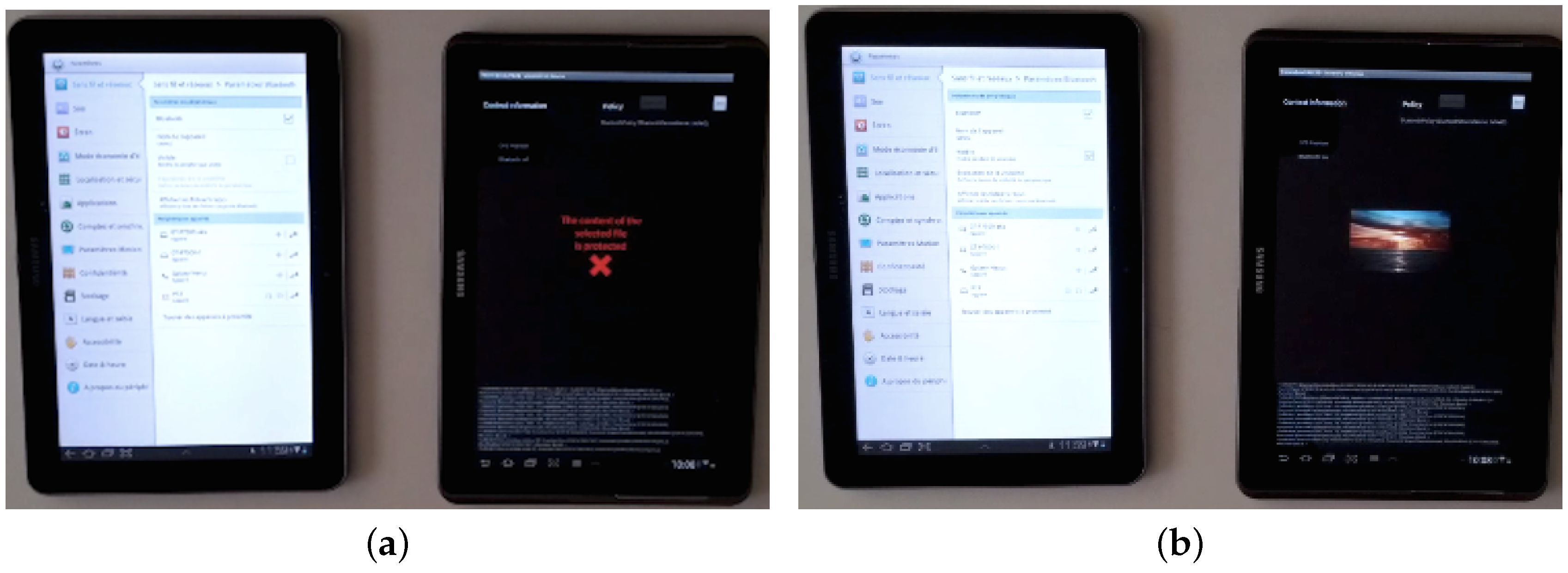
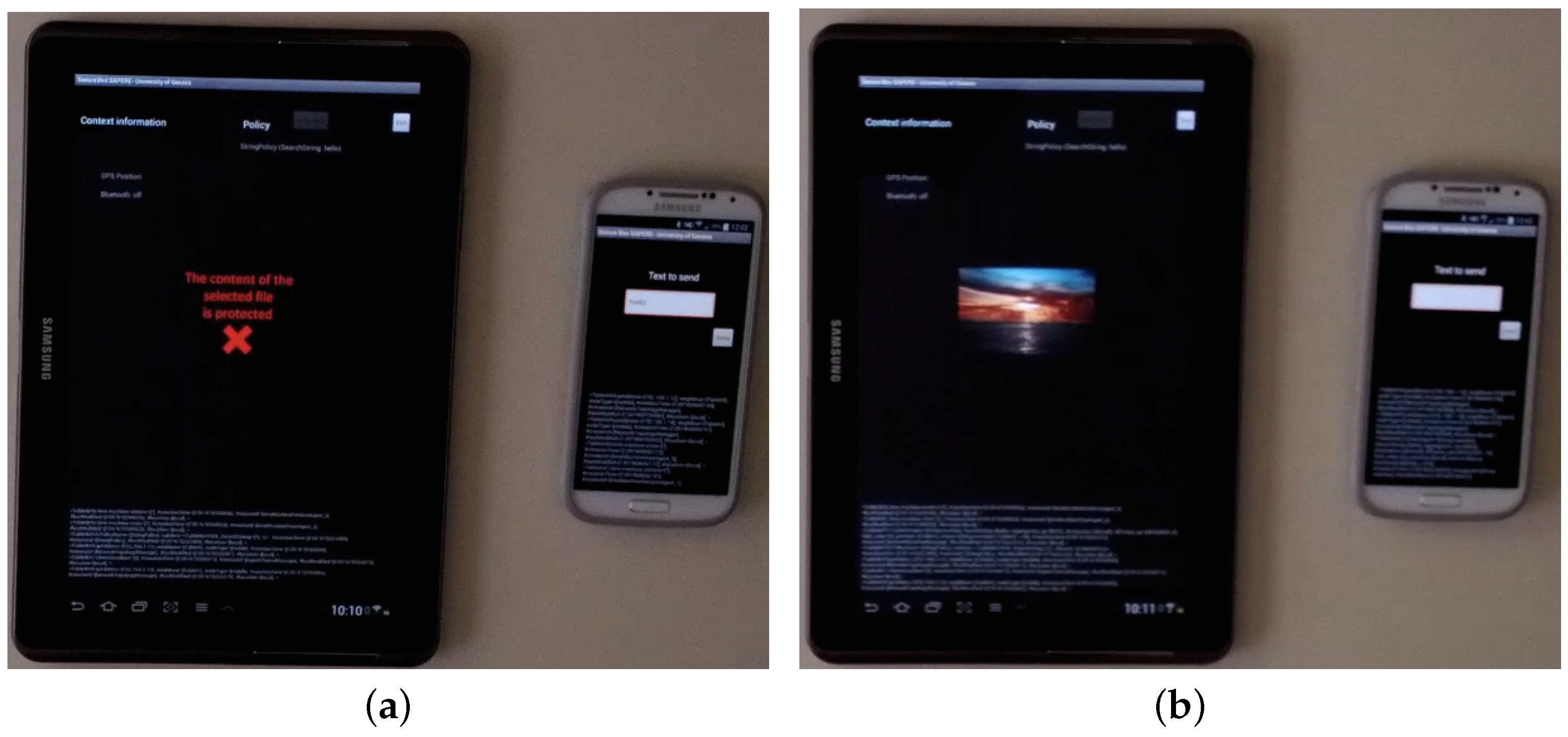
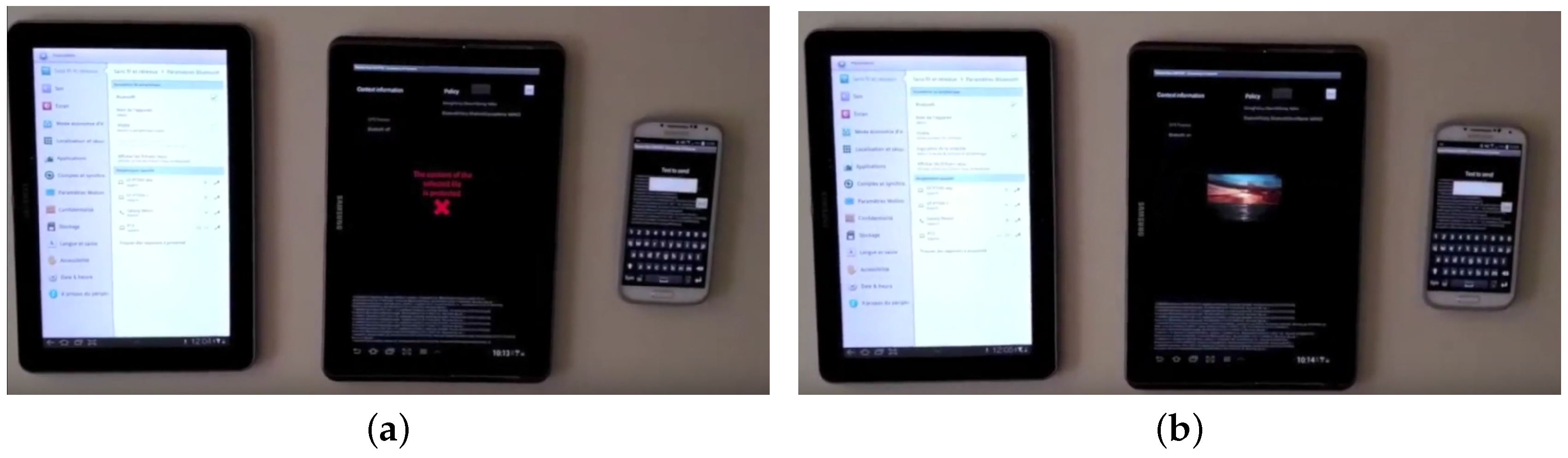
5. Proof-of-Concept and Demonstration
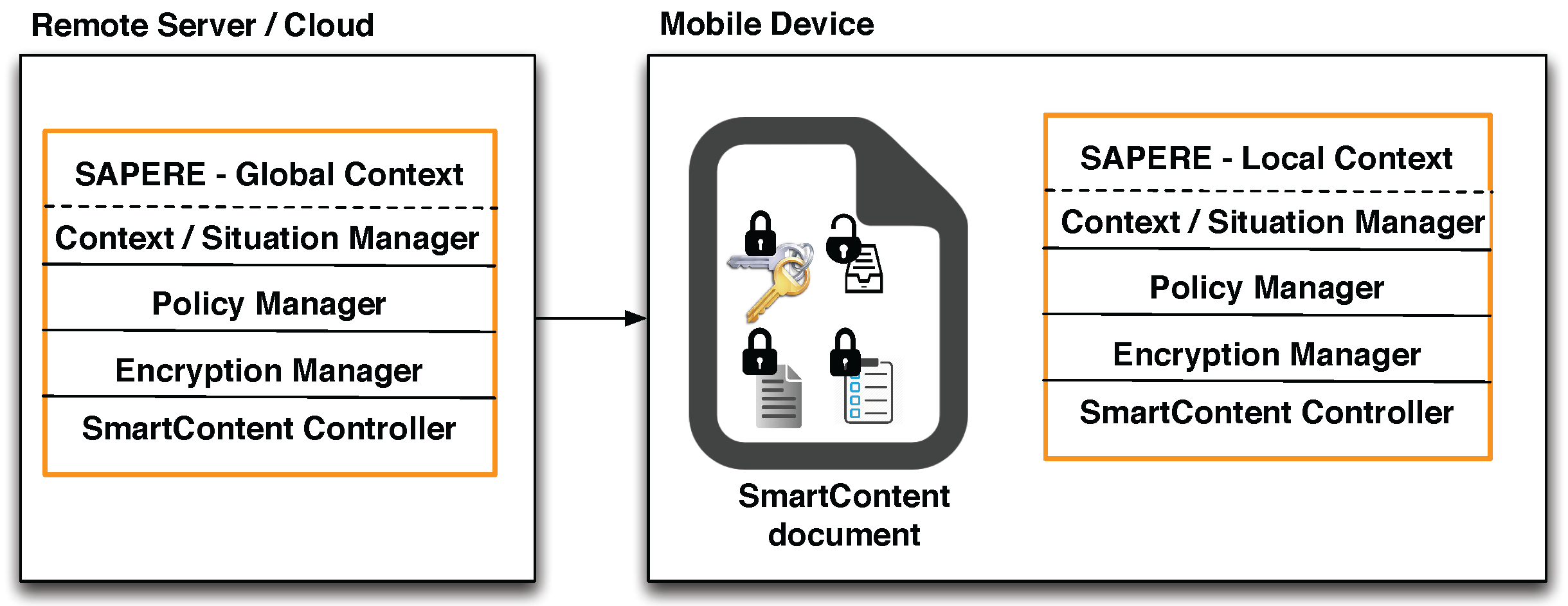
6. Variants on Cloud and Remote Servers
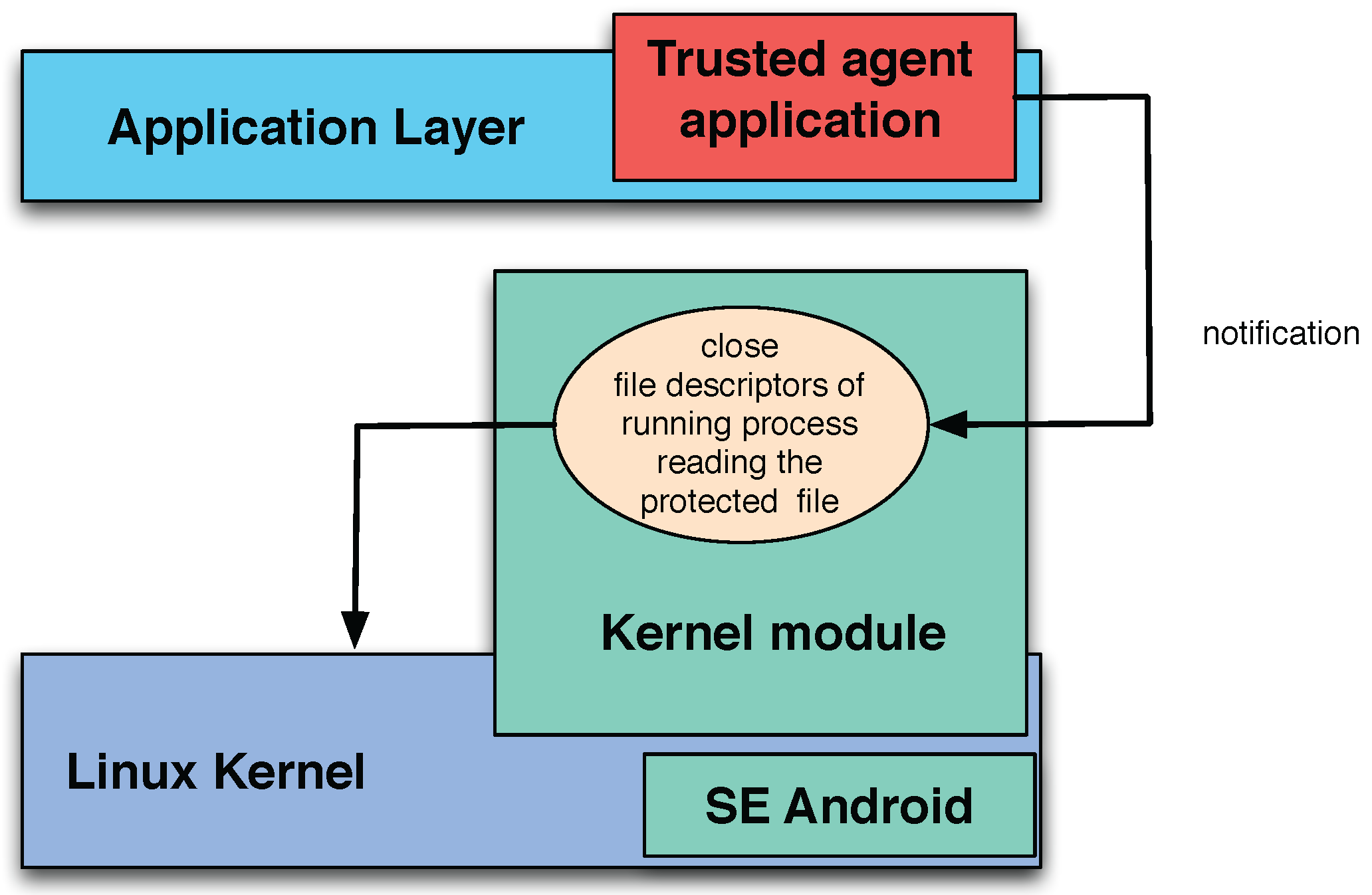
7. Further Security Improvements
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Johnson, N.F.; Jajodia, S. Exploring Steganography: Seeing the Unseen. Computer 1998, 31, 26–34. [Google Scholar] [CrossRef]
- Anderson, R.J.; Petitcolas, F.A. On the Limits of Steganography. IEEE J. Sel. A Commun. 2006, 16, 474–481. [Google Scholar] [CrossRef]
- Irwin, J. Digital Rights Management: The Open Mobile Alliance DRM Specifications. Inf. Secur. Tech. Rep. 2004, 9, 22–31. [Google Scholar] [CrossRef]
- Liu, Q.; Safavi-Naini, R.; Sheppard, N.P. Digital Rights Management for Content Distribution. In Proceedings of the Australasian Information Security Workshop Conference on ACSW Frontiers 2003; Australian Computer Society, Inc.: Darlinghurst, Australia, 2003; Volume 21, pp. 49–58. [Google Scholar]
- Tchao, A.; Di Marzo, G.; Morin, J.H. Personal DRM (PDRM)—A Self-Protecting Content Approach. In Digital Rights Management: Technology, Standards and Applications; Hartung, F., Kalker, T., Shiguo, L., Eds.; CRC Press: London, UK, 2012. [Google Scholar]
- Tchao, A.E.; Di Marzo Serugendo, G. SmartContent: A self-protecting and context-aware active content. In Proceedings of the 2nd Workshop on Challenges for Achieving Self-Awareness in Autonomic Systems (AWARE) at Sixth IEEE International Conference on Self-Adaptive and Self-Organizing Systems (SASO12), Lyon, France, 10–14 September 2012; pp. 151–156.
- Zambonelli, F.; Castelli, G.; Ferrari, L.; Mamei, M.; Rosi, A.; Di Marzo Serugendo, G.; Risoldi, M.; Tchao, A.E.; Dobson, S.; Stevenson, G.; et al. Self-Aware Pervasive Service Ecosystems. Procedia CS 2011, 7, 197–199. [Google Scholar] [CrossRef]
- Broder, A. On the Resemblance and Containment of Documents. In Proceedings of the International Conference on Compression and Complexity of Sequences 1997, Positano, Salerno, Italy, 11–13 June 1997; pp. 21–29.
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and Secure Sharing of Personal Health Records in Cloud Computing Using Attribute-Based Encryption. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 131–143. [Google Scholar] [CrossRef]
- Hayashi, E.; Das, S.; Amini, S.; Hong, J.; Oakley, I. CASA: Context-aware Scalable Authentication. In Proceedings of the Ninth Symposium on Usable Privacy and Security, Newcastle, UK, 24–26 July 2013; pp. 3:1–3:10.
- Goel, D.; Kher, E.; Joag, S.; Mujumdar, V.; Griss, M.; Dey, A.K. Context-Aware Authentication Framework. In Mobile Computing, Applications, and Services; Springer: Berlin/Heidelberg, Germany, 2010; Volume 35, pp. 26–41. [Google Scholar]
- Karapanos, N.; Marforio, C.; Soriente, C.; Capkun, S. Sound-Proof: Usable Two-Factor Authentication Based on Ambient Sound. In Proceedings of the 24rd USENIX Security Symposium (USENIX Security 15), USENIX Association, Washington, DC, USA, 12–14 August 2015; pp. 483–498.
- Bai, G.; Gu, L.; Feng, T.; Guo, Y.; Chen, X. Context-Aware Usage Control for Android. In Proceedings of the 6th Iternational Conference on Security and Privacy in Communication Networks (SecureComm 2010), Singapore, 7–9 September 2010; pp. 326–343.
- Ram, P.; Ta, T.; Wang, X. Self-Protecting Documents. EP Patent 0999488, 2005. [Google Scholar]
- Sibert, O.; Bernstein, D.; Van Wie, D. Digibox: A self-protecting container for information commerce. In Proceedings of the First USENIX Workshop on Electronic Commerce, New York, NY, USA, 11–12 July 1995; pp. 1–13.
- Munier, M.; Lalanne, V.; Ricarde, M. Self-Protecting Documents for Cloud Storage Security. In Proceedings of the TrustCom–11th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; pp. 1231–1238.
- Chen, S.; Thilakanathan, D.; Xu, D.; Nepal, S.; Calvo, R. Self Protecting Data Sharing Using Generic Policies. In Proceedings of the 15th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGrid), Shenzhen, Guangdong, China, 4–7 May 2015; pp. 1197–1200.
- Thilakanathan, D.; Chen, S.; Nepal, S.; Calvo, R. SafeProtect: Controlled Data Sharing with User-Defined Policies in Cloud-based Collaborative Environment. IEEE Trans. Emerg. Top. Comput. 2016, 4, 301–315. [Google Scholar] [CrossRef]
- Studer, A.; Perrig, A. Mobile User Location-specific Encryption (MULE): Using Your Office As Your Password. In Proceedings of the Third ACM Conference on Wireless Network Security, Hoboken, NJ, USA, 22–24 March 2010; pp. 151–162.
- May, M.J.; Bhargavan, K. Towards Unified Authorization for Android. In Engineering Secure Softwware and Systems; Lecture Notes in Computer Science Series 7781; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Boukayoua, F.; Lapon, J.; Decker, B.D.; Naessens, V. Secure Storage on Android with Context-Aware Access Control. In Proceedings of the 15th IFIP TC 6/TC 11 International Conference Communications and Multimedia Security, CMS 2014, Aveiro, Portugal, 25–26 September 2014; pp. 46–59.
- Sujithra, M.; Padmavathi, G. Mobile Device Security: A Survey on Mobile Device Threats, Vulnerabilities and their Defensive Mechanism. Int. J. Comput. Appl. 2012, 56, 24–29. [Google Scholar] [CrossRef]
- Padmavathi, G.; Shanmugapriya, D. A Survey of Attacks, Security Mechanisms and Challenges in Wireless Sensor Networks. Int. J. Comput. Sci. Inf. Secur. 2009, 4. ISSN 1947 5500. [Google Scholar]
- Castelli, G.; Mamei, M.; Rosi, A.; Zambonelli, F. Engineering Pervasive Service Ecosystems: The SAPERE Approach. TAAS 2015, 10, 1:1–1:27. [Google Scholar] [CrossRef]
- Zambonelli, F.; Omicini, A.; Anzengruber, B.; Castelli, G.; DeAngelis, F.L.; di Marzo Serugendo, G.; Dobson, S.; Fernandez-Marquez, J.L.; Ferscha, A.; Mamei, M.; et al. Developing Pervasive Multi-Agent Systems with Nature-Inspired Coordination. Pervasive Mob. Comput. 2015, 17, 236–252. [Google Scholar] [CrossRef] [Green Version]
- Fernández, J.L.; Serugendo, G.D.M.; Montagna, S.; Viroli, M.; Arcos, J.L. Description and composition of bio-inspired design patterns: A complete overview. Nat. Comput. 2013, 12, 43–67. [Google Scholar] [CrossRef]
- Castelli, G.; Mamei, M.; Rosi, A.; Zambonelli, F. How to Develop Pervasive Social Applications with the SAPERE Middleware. Comput. Inform. 2015, 34, 185–209. [Google Scholar]
| Framework | Typology | Context-Aware Solution | Additional Component Units | Architecture | Collaborative Document Access | Traceability/Policy Management | OS/Device Dependent |
|---|---|---|---|---|---|---|---|
| SmartContent | ACM, UCM, ECM | Full | Only for UCM | Stand-Alone | No | Policy Managment | No |
| Sound-proof [12] | AUM | Partial | Yes | Cloud-oriented | / | / | Microphones |
| ConUCON [13] | ACM, UCM | Full | Yes | Stand-alone | No | Policy managment | Android based |
| SPD [14] | ECM | Partial | Yes | Stand-alone | No | None | No |
| SPO [17] | ACM, UCM | Partial | Yes | Stand-alone, Cloud-oriented | Yes | Both | No |
| Digibox [15] | ACM, UCM | Absent | Yes | Stand-alone | No | Both | No |
| MULE [19] | ECM | Partial | No | Stand-alone | No | None | Yes |
| SAINT [20] | ACM, UCM | Full | Yes | Stand-alone | No | Policy managment | Android based |
| Secure Storage [21] | ACM, UCM | Partial | Yes | Stand-alone | No | Policy managment | Android based |
| Framework | Context Monitoring | Context Poisoning | Software Components Tampering | Hardware Components Tampering |
|---|---|---|---|---|
| SmartContent | Critical | Critical | Critical for ACM, UCM Resilient for ECM | Critical |
| Sound-proof [12] | Critical | Critical | Critical | Critical |
| ConUCON [13] | Critical | Critical | Critical | Critical |
| SPD [14] | Critical | Resilient | Resilient | Partially resilient |
| SPO [17] | Resilient | Partially resilient | Critical | Critical |
| Digibox [15] | / | / | Depending on the implementation | Resilient |
| MULE [19] | Critical | Resilient | Resilient | Resilient |
| SAINT [20] | Critical | Critical | Critical | Critical |
| Secure Storage [21] | Partially Resilient | Partially Resilient | Critical | Depending on the implementation |
| Reading Policies |
| readable-when: the content is readable (decrypted) when the conditions expressed by the predicates are satisfied. |
| Manipulation policies |
| readable-until: the content is readable until the conditions expressed by the predicates are satisfied. writable-until: the content is writable until the conditions expressed by the predicates are satisfied. allowed-remote-copies: the set of nodes to which the document can be sent. allowed-local-copies: the set of local folders where the file can be copied. |
| Type | Device | Description |
|---|---|---|
| Contextual SAPERE Agent | Main tablet | Bluetooth manager used to discover bluetooth devices. |
| Contextual SAPERE Agent | Main tablet | Network manager used to receive messages sent over a Wi-Fi network. |
| CI Manager SAPERE Agent | Main tablet | Manages the contextual information generated by the contextual agents. |
| SAPERE Agent | Smartphone | Generates and sends messages over the Wi-Fi network. |
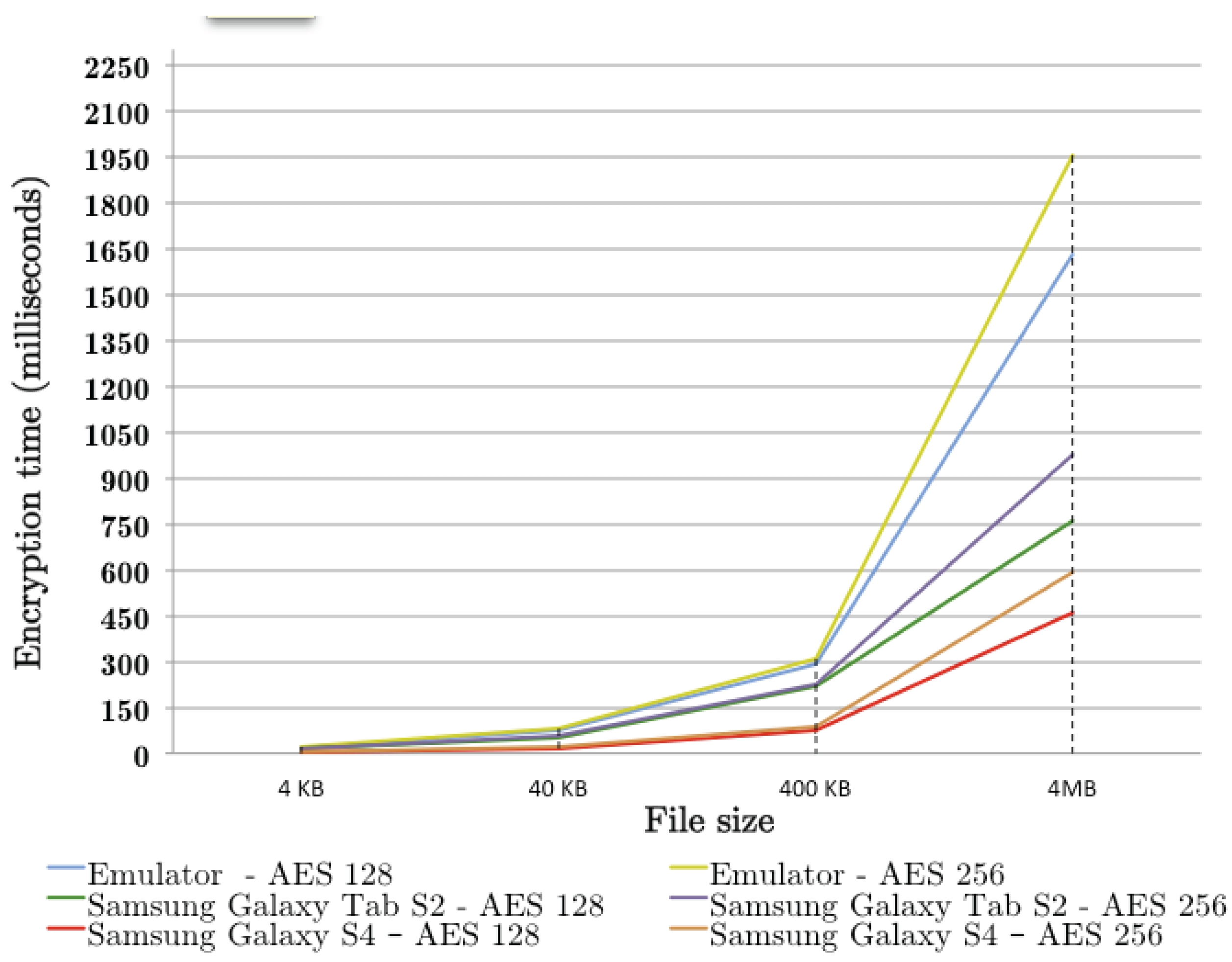
| 4 KB | 40 KB | 400 KB | 4 MB | |
|---|---|---|---|---|
| Emulator AES 128 | 18.92 | 74.54 | 294.77 | 1631.59 |
| Emulator AES 256 | 20.4 | 79.56 | 309.15 | 1952.23 |
| Samsung Galaxy Tab S2 AES 128 | 13.95 | 54.4 | 217.3 | 761.51 |
| Samsung Galaxy Tab S2 AES 256 | 14.98 | 58.4 | 227.94 | 975.89 |
| Samsung Galaxy S4 AES 128 | 4.75 | 18.45 | 75 | 458.8 |
| Samsung Galaxy S4 AES 256 | 5.4 | 21.26 | 87.6 | 590.78 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
De Angelis, F.L.; Di Marzo Serugendo, G. SmartContent—Self-Protected Context-Aware Active Documents for Mobile Environments. Electronics 2017, 6, 17. https://doi.org/10.3390/electronics6010017
De Angelis FL, Di Marzo Serugendo G. SmartContent—Self-Protected Context-Aware Active Documents for Mobile Environments. Electronics. 2017; 6(1):17. https://doi.org/10.3390/electronics6010017
Chicago/Turabian StyleDe Angelis, Francesco Luca, and Giovanna Di Marzo Serugendo. 2017. "SmartContent—Self-Protected Context-Aware Active Documents for Mobile Environments" Electronics 6, no. 1: 17. https://doi.org/10.3390/electronics6010017







