SSKM: Scalable and Secure Key Management Scheme for Group Signature Based Authentication and CRL in VANET †
Abstract
:1. Introduction
2. Related Work
3. Proposed Scheme
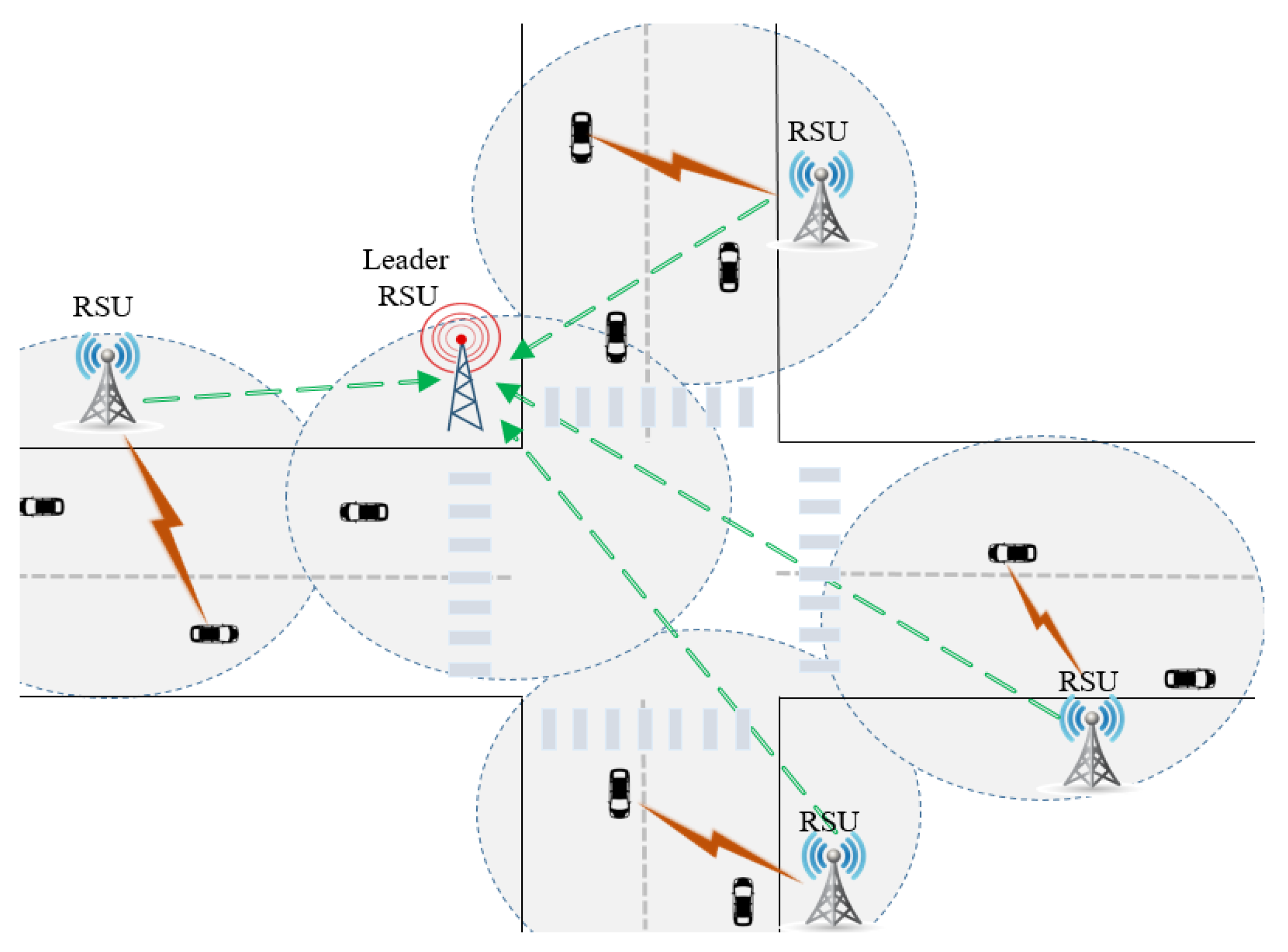
3.1. System Model
- Trusted authority (TA): When vehicles join the network, they are registered, and their certificates are issued by the trusted authority. The TA and RSUs are securely connected via a wired connection network. An RSU can identify the real identity of vehicles with the help of the TA when an investigation is necessary. The TA manages and distributes the regional CRLs for the specific region. The TA also executes the revocation status query requests from any region. With the high-level security protection, we assume that the TA is trusted and cannot be compromised.
- Domain and roadside units (RSUs): RSUs are the infrastructure located along the roadside that plays an important role in message authentication/verification, key management, and message dissemination in the networks. A group of RSUs forms a domain. The number of RSUs within a domain can be determined based on the infrastructure capacity, geographical location, vehicle demography, and deployment plan. The size of the domain is defined as the desired number of vehicles that can be accommodated by the RSUs within a geographic region, called the domain.
- Leader roadside units (L-RSU): RSUs are classified into leader RSU (L-RSU) and member RSU (M-RSU). An L-RSU coordinates with the TA and generates the group private keys and group public keys for the vehicles within its domain. The L-RSU also manages and maintains the database of the group keys and the regional CRL for its domain. When detecting suspicious behavior, the L-RSU communicates with the TA to reveal the identity of the malicious vehicle or it can also send the query to TA to authenticate the certificate of the vehicle. Since the L-RSUs are the primary component in the key generation and management process, we assume that the L-RSUs are equipped with trusted platform modules and high level security protection, hence it cannot be compromised.
- Member roadside units (M-RSU): M-RSUs are not involved in the key generation and management process nor in the CRL management. Instead, M-RSUs help vehicles obtain the group keys and an up-to-date regional CRL produced by the L-RSU. Therefore, the M-RSUs are semi-trusted with medium level security protection.
- Vehicle nodes: Vehicle nodes are cars with an on-board unit (OBU) installed for communication and computation, a GPS (global positioning system) for location services, and an interface for interacting with drivers/passengers. Vehicles can communicate with each other or with RSUs through the radio defined under the IEEE Standard 1609.2 [27], which is a standard for wireless access in the vehicular environment (WAVE). The group keys and public/private key pairs are used for vehicular communications to provide authentication and encryption/decryption features. All secret keys are stored in a tamper-proof device [28] for protection. A vehicle node validates received messages by evaluating the sender’s certificate with the CRL. We assume that every vehicle obtained the public keys of the RSUs in the networks when registered by the TA, and they are regularly updated.
3.2. Basic Idea behind Our Scheme
3.3. Short Group Signature
3.3.1. Key Setup
3.3.2. Membership Registration
3.3.3. Signing
3.3.4. Verification
3.3.5. Key Retrieval
3.3.6. Membership Revocation
3.4. Scalable and Secure Key Management Scheme
4. CRL Management
| Algorithm 1: Verifying the certificate in the TBFV scheme. |
 |
5. Evaluation and Analysis
5.1. Security Analysis
5.1.1. Source Authentication and Privacy
5.1.2. Anonymity
5.1.3. Non-Repudiation
5.1.4. Man-in-the-Middle Attack
5.1.5. Other Attacks
Sybil Attack
Replay Attack
Message Alteration Attack
Collusion Attack
Revoking Malicious/Misbehaving Node
5.2. Performance Evaluation
5.2.1. Key Establishment
5.2.2. Group Key Utilization
5.2.3. Communication Overhead
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Papadimitratos, P.; De La Fortelle, A.; Evenssen, K.; Brignolo, R.; Cosenza, S. Vehicular communication systems: Enabling technologies, applications, and future outlook on intelligent transportation. IEEE Commun. Mag. 2009, 47, 84–95. [Google Scholar] [CrossRef]
- Hartenstein, H.; Laberteaux, K. VANET Vehicular Applications and Inter-Networking Technologies; John Wiley & Sons: Hoboken, NJ, USA, 2009; Volume 1. [Google Scholar]
- Raya, M.; Hubaux, J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Chaum, D.; Van Heyst, E. Group signatures. In Advances in Cryptology—EUROCRYPT’91; Springer: Berlin, Germany, 1991; pp. 257–265. [Google Scholar]
- Boneh, D.; Boyen, X.; Shacham, H. Short group signatures. In Crypto; Springer: Berlin, Germany, 2004; Volume 3152, pp. 41–55. [Google Scholar]
- Hao, Y.; Cheng, Y.; Zhou, C.; Song, W. A distributed key management framework with cooperative message authentication in VANETs. IEEE J. Sel. Areas Commun. 2011, 29, 616–629. [Google Scholar] [CrossRef]
- Chim, T.W.; Yiu, S.M.; Hui, L.C.; Li, V.O. VSPN: VANET-based secure and privacy-preserving navigation. IEEE Trans. Comput. 2014, 63, 510–524. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.H.; Shen, X. ECPP: Efficient conditional privacy preservation protocol for secure vehicular communications. In Proceedings of the IEEE INFOCOM 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1229–1237. [Google Scholar]
- Buttyán, L.; Holczer, T.; Vajda, I. On the effectiveness of changing pseudonyms to provide location privacy in VANETs. In European Workshop on Security in Ad-hoc and Sensor Networks; Springer: Berlin, Germany, 2007; pp. 129–141. [Google Scholar]
- U.S. Department of Justice. Federal Bureau of Investigation. 2018. Available online: https://www.iii.org/fact-statistic/facts-statistics-auto-theft (accessed on 23 July 2017).
- Lim, K.; Tuladhar, K.M.; Wang, X.; Liu, W. A scalable and secure key distribution scheme for group signature based authentication in VANET. In Proceedings of the 8th IEEE Ubiquitous Computing, Electronics and Mobile Communication Conference, New York, NY, USA, 19–21 October 2017; pp. 478–483. [Google Scholar]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Gerlach, M. Assessing and improving privacy in VANETs. In Proceedings of the Fourth Workshop on Embedded Security in Cars (ESCAR), Berlin, Germany, 14–15 November 2006; pp. 19–28. [Google Scholar]
- Huang, L.; Matsuura, K.; Yamane, H.; Sezaki, K. Enhancing wireless location privacy using silent period. In Proceedings of the 2005 IEEE Wireless Communications and Networking Conference, New Orleans, LA, USA, 13–17 March 2005; pp. 1187–1192. [Google Scholar]
- Freudiger, J.; Raya, M.; Félegyházi, M.; Papadimitratos, P.; Hubaux, J.P. Mix-zones for location privacy in vehicular networks. In Proceedings of the 2007 ACM Workshop on Wireless Networking for Intelligent Transportation Systems (WiN-ITS), Vancouver, BC, Canada, 14 August 2007. number LCA-CONF-2007-016. [Google Scholar]
- Sampigethaya, K.; Li, M.; Huang, L.; Poovendran, R. AMOEBA: Robust location privacy scheme for VANET. IEEE J. Sel. Areas Commun. 2007, 25, 1569–1589. [Google Scholar] [CrossRef]
- Sun, X.; Lin, X.; Ho, P.H. Secure vehicular communications based on group signature and ID-based signature scheme. In Proceedings of the 2007 IEEE ICC International Conference, Glasgow, UK, 24–28 June 2007; pp. 1539–1545. [Google Scholar]
- Zhang, C.; Lu, R.; Lin, X.; Ho, P.H.; Shen, X. An efficient identity-based batch verification scheme for vehicular sensor networks. In Proceedings of the IEEE INFOCOM 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 246–250. [Google Scholar]
- Jia, X.; Yuan, X.; Meng, L.; Wang, L.M. EPAS: Efficient Privacy-preserving Authentication Scheme for VANETs-based Emergency Communication. JSW 2013, 8, 1914–1922. [Google Scholar] [CrossRef]
- Ravi, K.; Kulkarni, S. A secure message authentication scheme for VANET using ECDSA. In Proceedings of the 2013 Fourth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Tiruchengode, India, 4–6 July 2013; pp. 1–6. [Google Scholar]
- Huang, J.L.; Yeh, L.Y.; Chien, H.Y. ABAKA: An anonymous batch authenticated and key agreement scheme for value-added services in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2010, 60, 248–262. [Google Scholar] [CrossRef]
- Calandriello, G.; Papadimitratos, P.; Hubaux, J.P.; Lioy, A. Efficient and robust pseudonymous authentication in VANET. In Proceedings of the Fourth ACM International Workshop on Vehicular Ad Hoc Networks, Montreal, QC, Canada, 10 September 2007; pp. 19–28. [Google Scholar]
- Sun, Y.; Lu, R.; Lin, X.; Shen, X.; Su, J. An efficient pseudonymous authentication scheme with strong privacy preservation for vehicular communications. IEEE Trans. Veh. Technol. 2010, 59, 3589–3603. [Google Scholar] [CrossRef]
- Rigazzi, G.; Tassi, A.; Piechocki, R.J.; Tryfonas, T.; Nix, A. Optimized Certificate Revocation List Distribution for Secure V2X Communications. arXiv 2017, arXiv:1705.06903. [Google Scholar]
- Haas, J.J.; Hu, Y.C.; Laberteaux, K.P. Efficient certificate revocation list organization and distribution. IEEE J. Sel. Areas Commun. 2011, 29, 595–604. [Google Scholar] [CrossRef]
- Rabieh, K.; Mahmoud, M.M.; Akkaya, K.; Tonyali, S. Scalable certificate revocation schemes for smart grid ami networks using Bloom filters. IEEE Trans. Dependable Secur. Comput. 2017, 14, 420–432. [Google Scholar] [CrossRef]
- 1609.2-2016—IEEE Standard for Wireless Access in Vehicular Environments–Security Services for Applications and Management Messages; IEEE: New York, NY, USA, 2016; pp. 1–240.
- Rosen, S.S. Tamper-Proof Electronic Processing Device. U.S. Patent 6,088,797, 11 July 2000. [Google Scholar]
- Lim, K.; Manivannan, D. An efficient protocol for authenticated and secure message delivery in vehicular ad hoc networks. Veh. Commun. 2016, 4, 30–37. [Google Scholar] [CrossRef]
- Raya, M.; Papadimitratos, P.; Gligor, V.D.; Hubaux, J.P. On data-centric trust establishment in ephemeral ad hoc networks. In Proceedings of the IEEE INFOCOM 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1238–1246. [Google Scholar]
- Raya, M.; Jungels, D.; Papadimitratos, P.; Aad, I.; Hubaux, J.P. Certificate Revocation in Vehicular Networks; Laboratory for computer Communications and Applications (LCA) School of Computer and Communication Sciences, EPFL: Lausanne, Switzerland, 2006. [Google Scholar]
- Song, H.; Dharmapurikar, S.; Turner, J.; Lockwood, J. Fast hash table lookup using extended Bloom filter: An aid to network processing. ACM SIGCOMM Comput. Commun. Rev. 2005, 35, 181–192. [Google Scholar] [CrossRef]
- Tuladhar, K.M.; Lim, K. Efficient and scalable certificate revocation list distribution in hierarchical VANETs. In Proceedings of the 2018 IEEE International Conference on Electro/Information Technology (EIT), Rochester, MI, USA, 3–5 May 2018; pp. 620–625. [Google Scholar]
- Rivest, R.L.; Shamir, A. How to expose an eavesdropper. Commun. ACM 1984, 27, 393–394. [Google Scholar] [CrossRef]
- Simulation of Urban Mobility. Available online: http://sumo.dlr.de/index.html (accessed on 22 June 2017).
- NS-2. Available online: http://nsnam.sourceforge.net/wiki/index.php (accessed on 22 June 2017).
- Insurance Institute of Highway Safety. 2008. Available online: http://www.iihs.org/iihs/sr/statusreport/article/43/1/1 (accessed on 7 July 2017).
- Wagner, I. U.S. Car Sales. 2018. Available online: https://www.statista.com/statistics/199974/us-car-sales-since-1951/ (accessed on 7 July 2017).
- Scott, M. Efficient Implementation of Cryptographic Pairings. 2007. Available online: http://www. pairing-conference. org/2007/invited/Scott slide. pdf (accessed on 23 August 2018).
- Miyaji, A.; Nakabayashi, M.; Takano, S. New explicit conditions of elliptic curve traces for FR-reduction. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2001, 84, 1234–1243. [Google Scholar]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An efficient pseudonymous authentication-based conditional privacy protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]







| Notation | Description |
|---|---|
| a vehicle i | |
| an RSU i | |
| a time-stamp | |
| L- | a leader RSU |
| M- | a member RSU |
| private key of | |
| public key of | |
| a group public key | |
| a group private key of a vehicle | |
| certificate of issued by the TA | |
| digital signature | |
| shared secret key between and M- | |
| false positive rate | |
| Number of valid vehicles and revoked vehicles | |
| bit vector length of valid and revoked vehicles | |
| hash functions of valid and revoked vehicles | |
| leader RSU index |
| Vehicle V | Member RSU (M-) | Leader RSU (L-) | ||
|---|---|---|---|---|
| 1. Sends message to M- | ||||
| , | → | 2. Sends message to | ||
| 3. Sends (Ack. and Request) to M- | ← | |||
| → | 4. Forwards request to L- () | |||
| → | 5. Issues a group key and sends msg | |||
| ← | ||||
| 6. Sends message to | ||||
| ← | , | |||
| 7. receives the group key and can use it |
| Field | Description | Size(bytes) | ||
|---|---|---|---|---|
| Version | Certificate | Unit8 | 2 | |
| carca_id | Unisigned | CA_ID field | SIZE(8) | 8 |
| Issue Date | CRL issued time stamp | Unit32 | 8 | |
| Next CRL | Next Expected CRL | Unit32 | 8 | |
| Priorityinfo | CRL Priority | Unit8 | 2 | |
| LR_Index | L-RSU index ID | 2.5 | ||
| Hash_functions | For revoked and valid certificate | Domain Variable | K_r | |
| K_v | ||||
| Two Bloom Filter | Revoked bit vector | Domain Variable | m_r | |
| Valid bit vector | m_v | |||
| Signature(ECDSA) | r | Data encryption | 32 | |
| s | 32 | |||
| Certificate | Signed | Public Key of TA | Authentication | 32 |
| Scheme | Verification Overhead | Delay |
|---|---|---|
| SSKM: | 24.3 ms | |
| IBV [18]: | 14.7 ms | |
| PACP [41]: | 12 ms | |
| ECDSA [20]: | 2.4 ms | |
| EPAS [19]: | 5 ms | |
| ABAKA [21]: | 4.2 ms |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lim, K.; Liu, W.; Wang, X.; Joung, J. SSKM: Scalable and Secure Key Management Scheme for Group Signature Based Authentication and CRL in VANET. Electronics 2019, 8, 1330. https://doi.org/10.3390/electronics8111330
Lim K, Liu W, Wang X, Joung J. SSKM: Scalable and Secure Key Management Scheme for Group Signature Based Authentication and CRL in VANET. Electronics. 2019; 8(11):1330. https://doi.org/10.3390/electronics8111330
Chicago/Turabian StyleLim, Kiho, Weihua Liu, Xiwei Wang, and Jingon Joung. 2019. "SSKM: Scalable and Secure Key Management Scheme for Group Signature Based Authentication and CRL in VANET" Electronics 8, no. 11: 1330. https://doi.org/10.3390/electronics8111330





