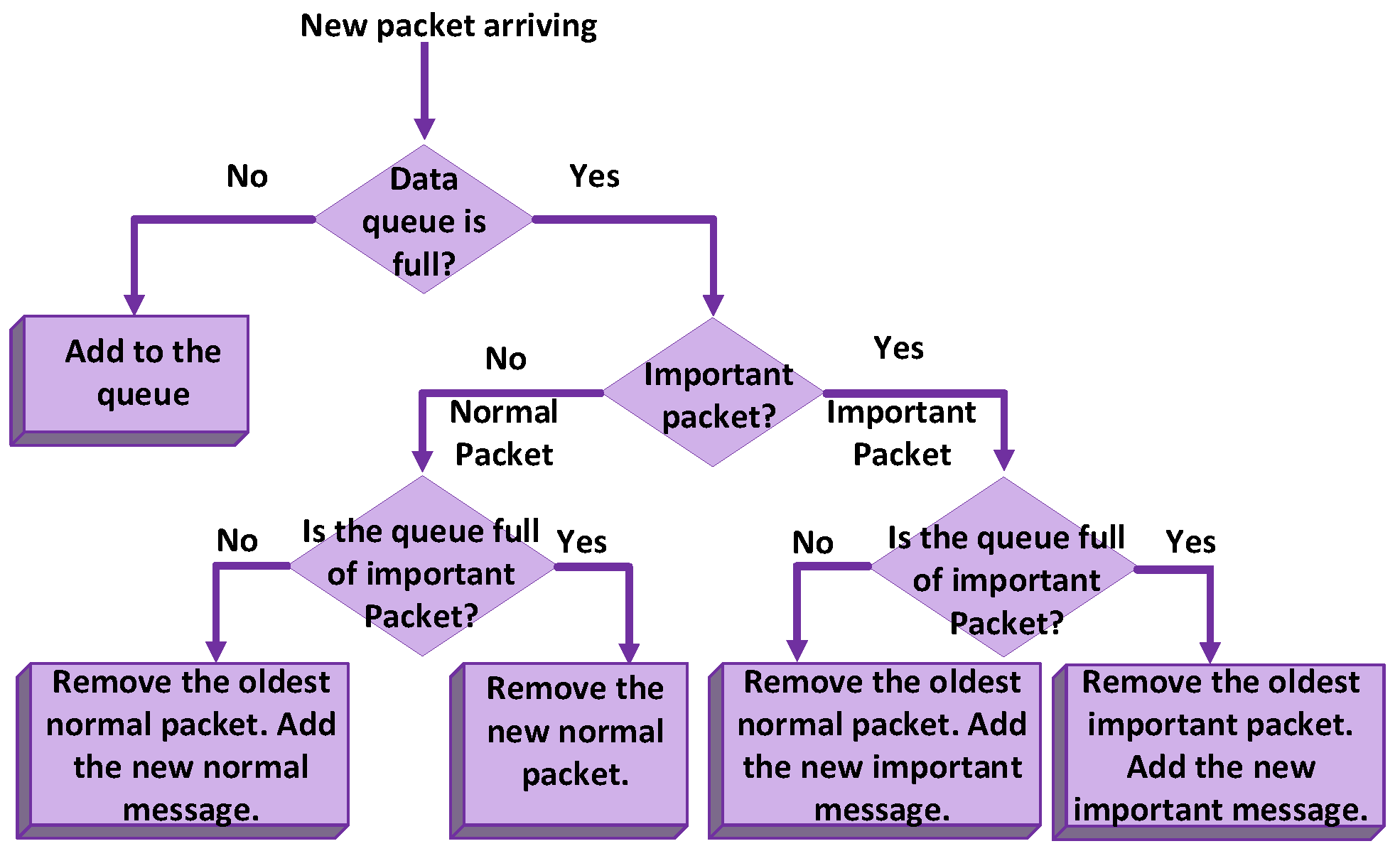
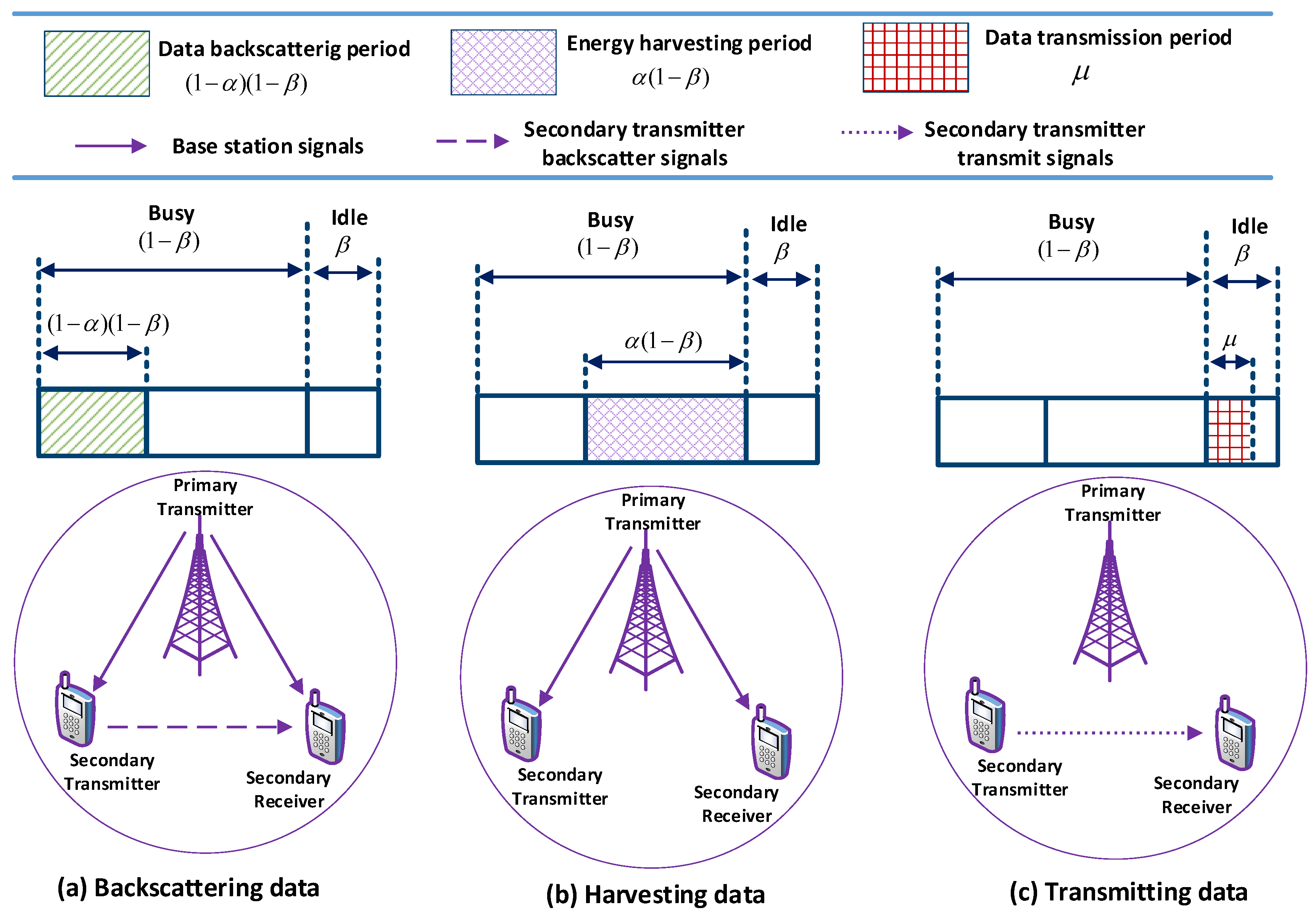
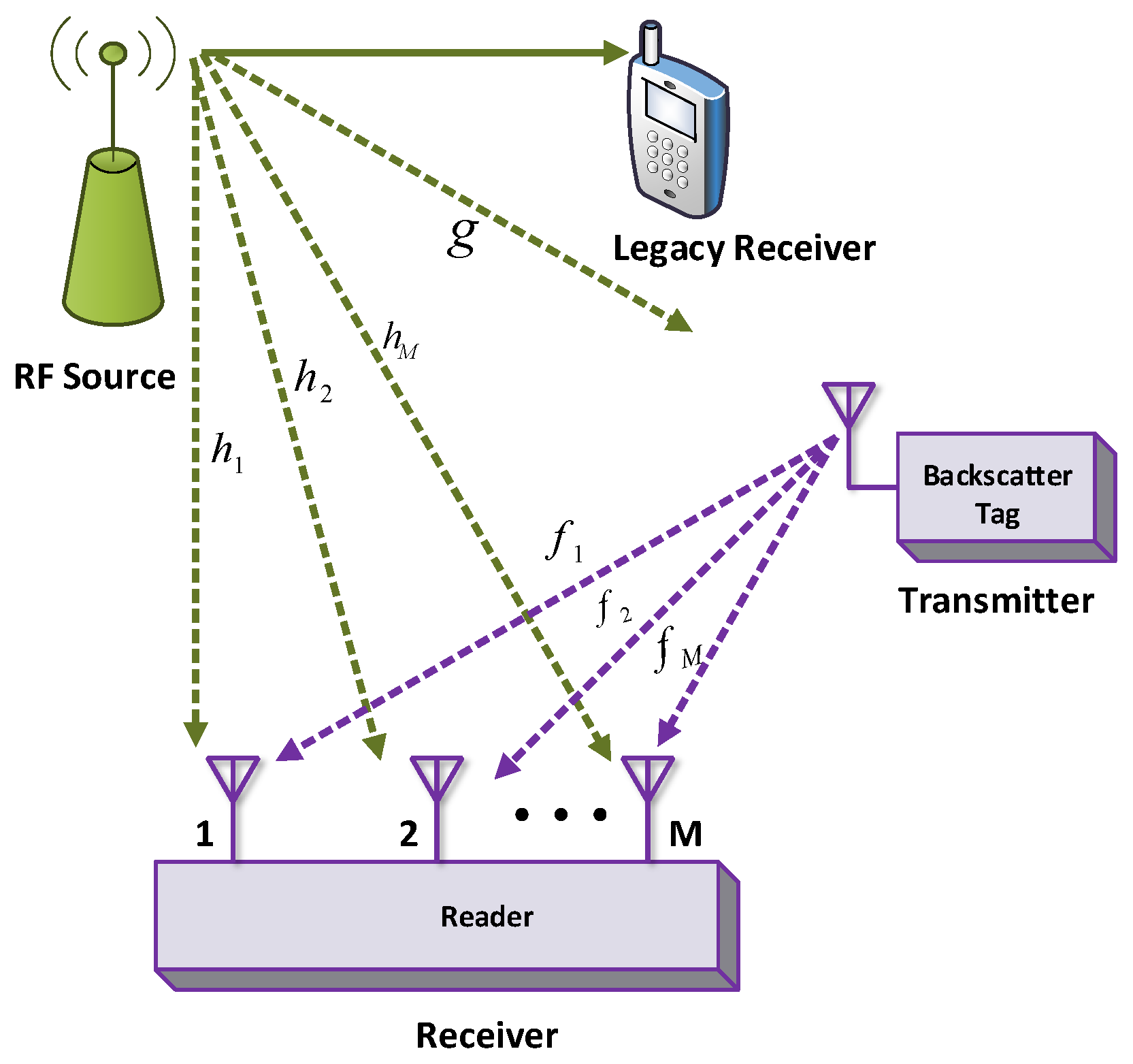
Abstract
The ever increasing proliferation of wireless objects and consistent connectivity demands are creating significant challenges for battery-constrained wireless devices. The vision of massive IoT, involving billions of smart objects to be connected to the cellular network, needs to address the problem of uninterrupted power consumption while taking advantage of emerging high-frequency 5G communications. The problem of limited battery power motivates us to utilize radio frequency (RF) signals as the energy source for battery-free communications in next-generation wireless networks. Backscatter communication (BackCom) makes it possible to harvest energy from incident RF signals and reflect back parts of the same signals while modulating the data. Ambient BackCom (Amb-BackCom) is a type of BackCom that can harvest energy from nearby WiFi, TV, and cellular RF signals to modulate information. The objective of this article is to review BackCom as a solution to the limited battery life problem and enable future battery-free communications for combating the energy issues for devices in emerging wireless networks. We first highlight the energy constraint in existing wireless communications. We then investigate BackCom as a practical solution to the limited battery life problem. Subsequently, in order to take the advantages of omnipresent radio waves, we elaborate BackCom tag architecture and various types of BackCom. To understand encoding and data extraction, we demonstrate signal processing aspects that cover channel coding, interference, decoding, and signal detection schemes. Moreover, we also describe BackCom communication modes, modulation schemes, and multiple access techniques to accommodate maximum users with high throughput. Similarly, to mitigate the increased network energy, adequate data and power transfer schemes for BackCom are elaborated, in addition to reliability, security, and range extension. Finally, we highlight BackCom applications with existing research challenges and future directions for next-generation 5G wireless networks.
1. Introduction
Cisco visual networking index predicts that by 2021 global mobile data traffic will increase seven-fold, with the number of devices connected to IP networks increased to three times more of the global population [1].Similarly, according to the Ericsson mobility report, there were approximately billion IoT devices connected with cellular networks in 2017. Due to overwhelming interest by industries and standardization of cellular IoT technologies by the 3rd Generation Partnership Project (3GPP), connectivity is expected to reach billion IoT cellular devices in 2023 [2]. This huge usage of wireless devices in mobile networks, the ratification of Device to Device (D2D) communications, and IoT allow us to be remotely connected to everyday objects. However, the problem of these wireless devices is the limited battery life. Consequently, most of the efficient protocols for wireless communications will be inoperative if batteries are exhausted.
Over the past few years, wireless communications have made significant advancements in technology—the high bandwidth of millimeter (mm) waves in the 5G network, internet connectivity of smart objects in IoT, and improved energy harvesting techniques. These advancements in technology are gradually leading us towards one of the most distinct phases of wireless communications—the “Backscatter Communications for next-generation 5G wireless,” which aims to render communications battery-free in emerging wireless network devices.
1.1. Limited Battery-Life: A Problem
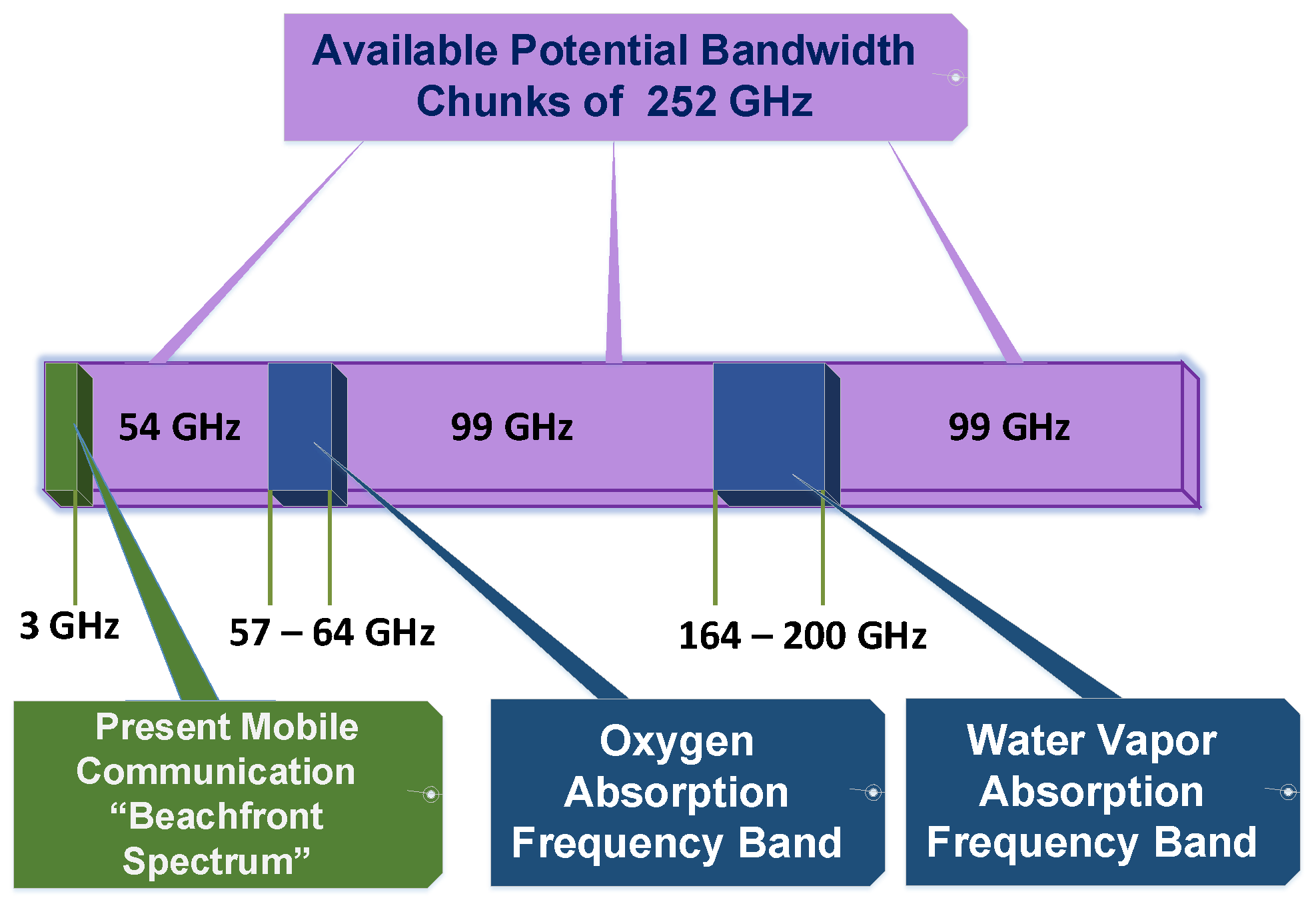
Figure 1 shows emerging 5G communications aiming to resolve the bandwidth constraint by utilizing the mm-wave spectrum [3]. Until recently, only the beachfront spectrum range had been used for wireless communications. Now 5G utilizes wireless bandwidth up to 300 GHz, excepting oxygen and water vapor absorption bands. This high-frequency spectrum supports large-bandwidth directional communications. Besides the attempts for usage of the extended wireless spectrum, there are various proposals to solve the energy constraints in wireless communications. These proposals include
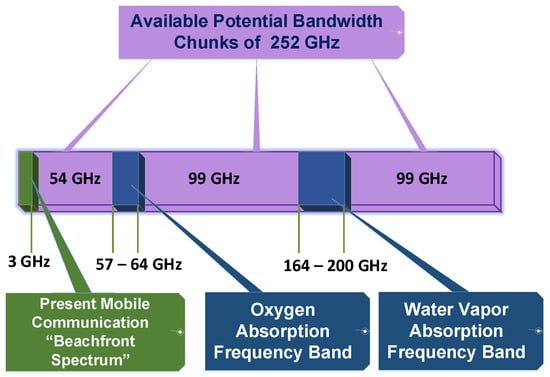
Figure 1.
Frequency band of mm-waves.
- D2D communications for energy efficiency in mission-critical communication while focusing on disaster scenarios [4];
- deployment of IoT in wireless communications to utilize energy more efficiently [5];
- multiple wireless charging techniques proposed to enhance the lifetime of wireless devices [6];
- various RF energy harvesting schemes to solve power issues in wireless communications [7].
These power saving schemes extend the usage time of user equipment (UE) with limited battery power. However, limited battery life is a perennial problem that generally leads to the failure of communication systems. Thus, what could be the solution to this persistent problem? This problem motivates us to think about battery-less communications.
1.2. Towards Battery-Less Communications
What if wireless communications can work without any battery? We would not need any active power source. This proposal will allow us to avoid the trouble of charging, replacement, and recycling. Small devices in cellular communications will have everlasting energy. Battery-less communications also enable devices to be connected round the clock without any battery failure problems. The positive traits of battery-less communications include the following:
- Communication between devices can have a longer life.
- Useful protocols of wireless communications could be long-lasting.
- Devices will operate without power interruption.
These traits would revolutionize the current concept of wireless communications. Moreover, these characteristics would enable battery-less D2D communications in disaster scenarios. Furthermore, we would achieve the goal of IoT to connect everything with emerging wireless networks more practically and without power interruption. Mobile phones would neither require a battery nor long-duration power charging for their operation.
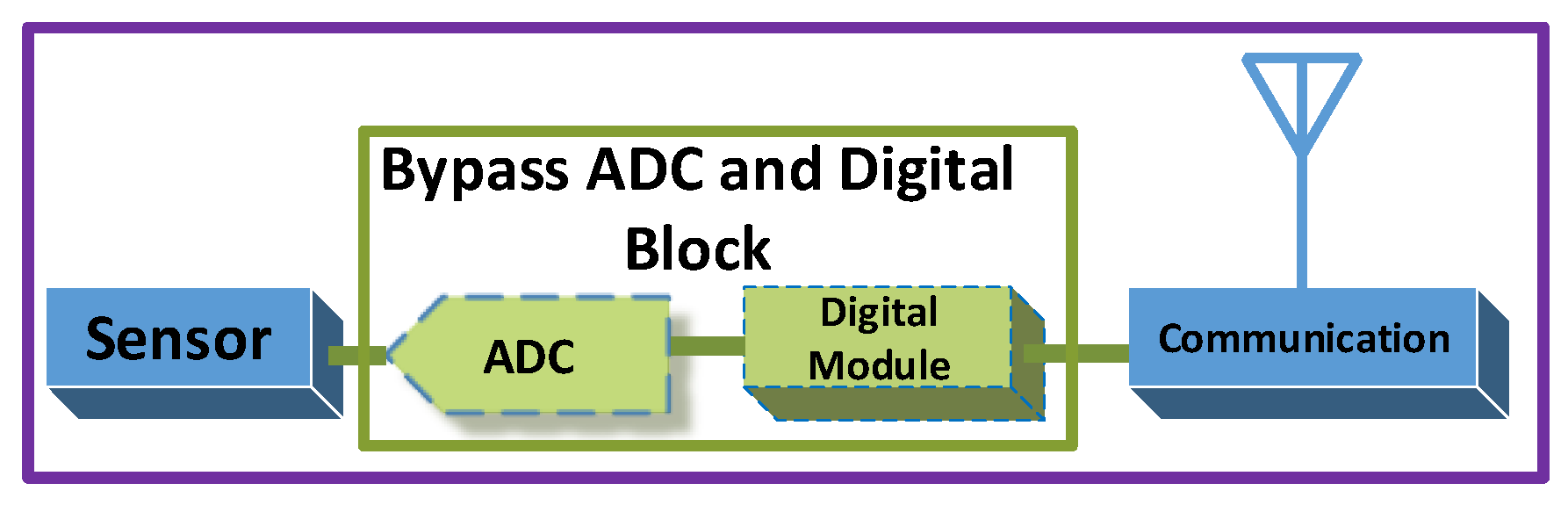
Previously it seemed unrealistic, but a recent research from the University of Washington introduced a prototype of a battery-free cellphone [8] that made battery-free communication more practicable. Figure 2 shows the block diagram of battery-free cellphone, which bypasses the power-thirsty components in battery-free cellphone design. The working principle of this phone depends on the reflection of radio waves, similar to methods used in radio frequency identification (RFID) systems [9]. Usually, RFID is made up of two parts: (i) transponder and (ii) reader. The transponder is placed in the product to be scanned, also known as a “tag”. The reader is used for sending the RF signals and then extracting the data from reflected waves. Traditional RFID readers can work on either active tags, those having their power source, or on passive tags, which do not possess their energy supply. In passive tag communications, neither any oscillator nor any active component is needed to generate the carrier waves for the transmission of data. However, the tag only reflects incident carrier signals by varying the antenna impedance, after modulating its information to those incident signals. This type of communication is referred to as backscatter communications (BackCom) [10], which heralds battery-free communications. Recently, a multi-band development board is designed to support the battery-less autonomous semi-passive RFID transponder [11]. This design allows the devices to harvest energy from various electromagnetic fields (UMTS, LTE, and WiFi). The harvested energy can further be utilized by using an ultra-efficient power conditioner and storage block in a number of battery-free applications.
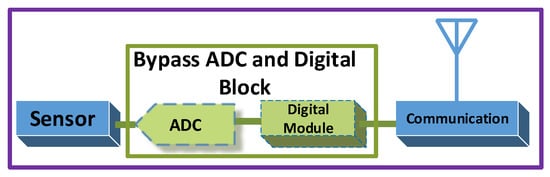
Figure 2.
Block diagram battery-free cellphone.
1.3. Ambient BackCom: A Solution to Limited Battery-Life
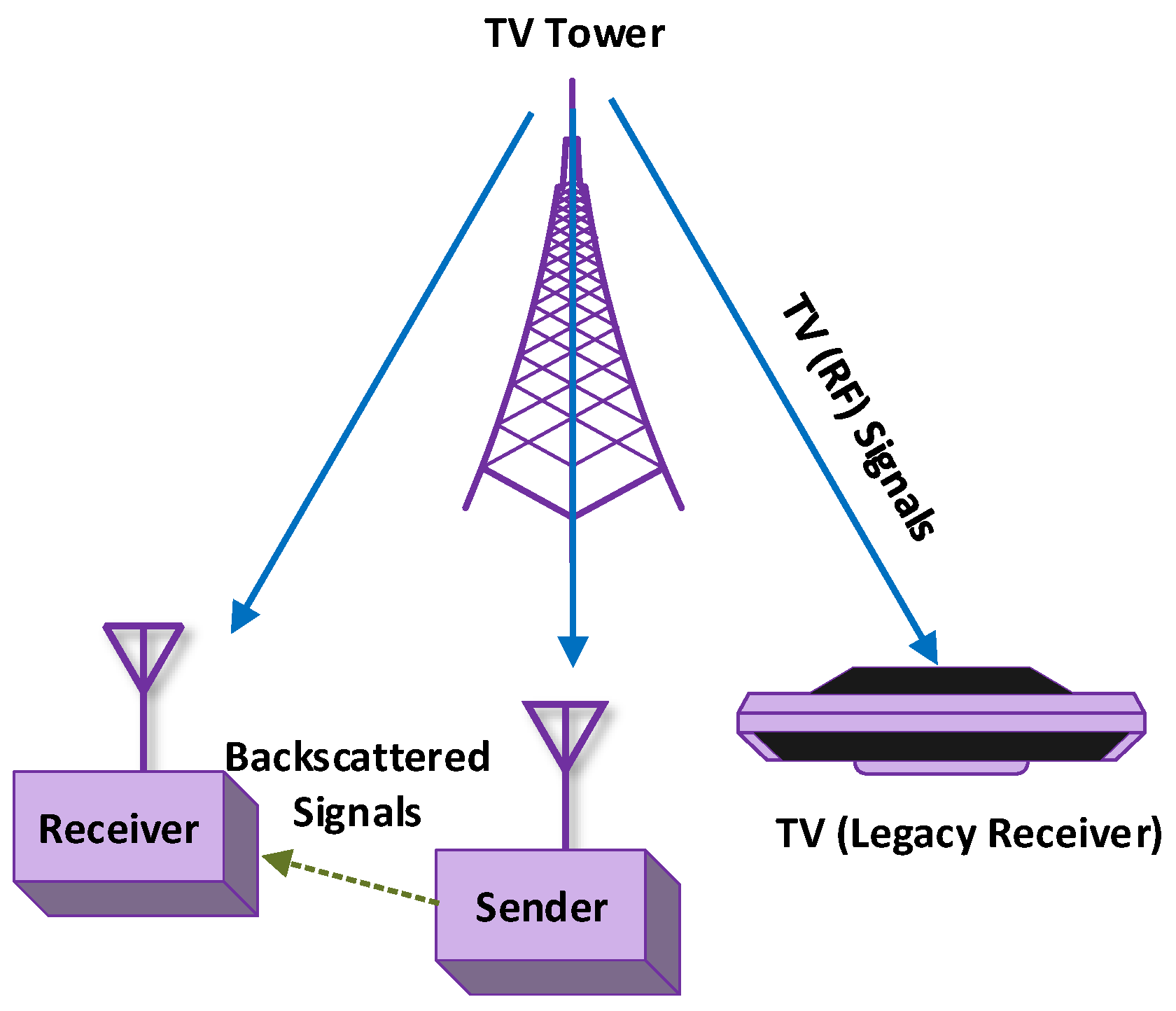
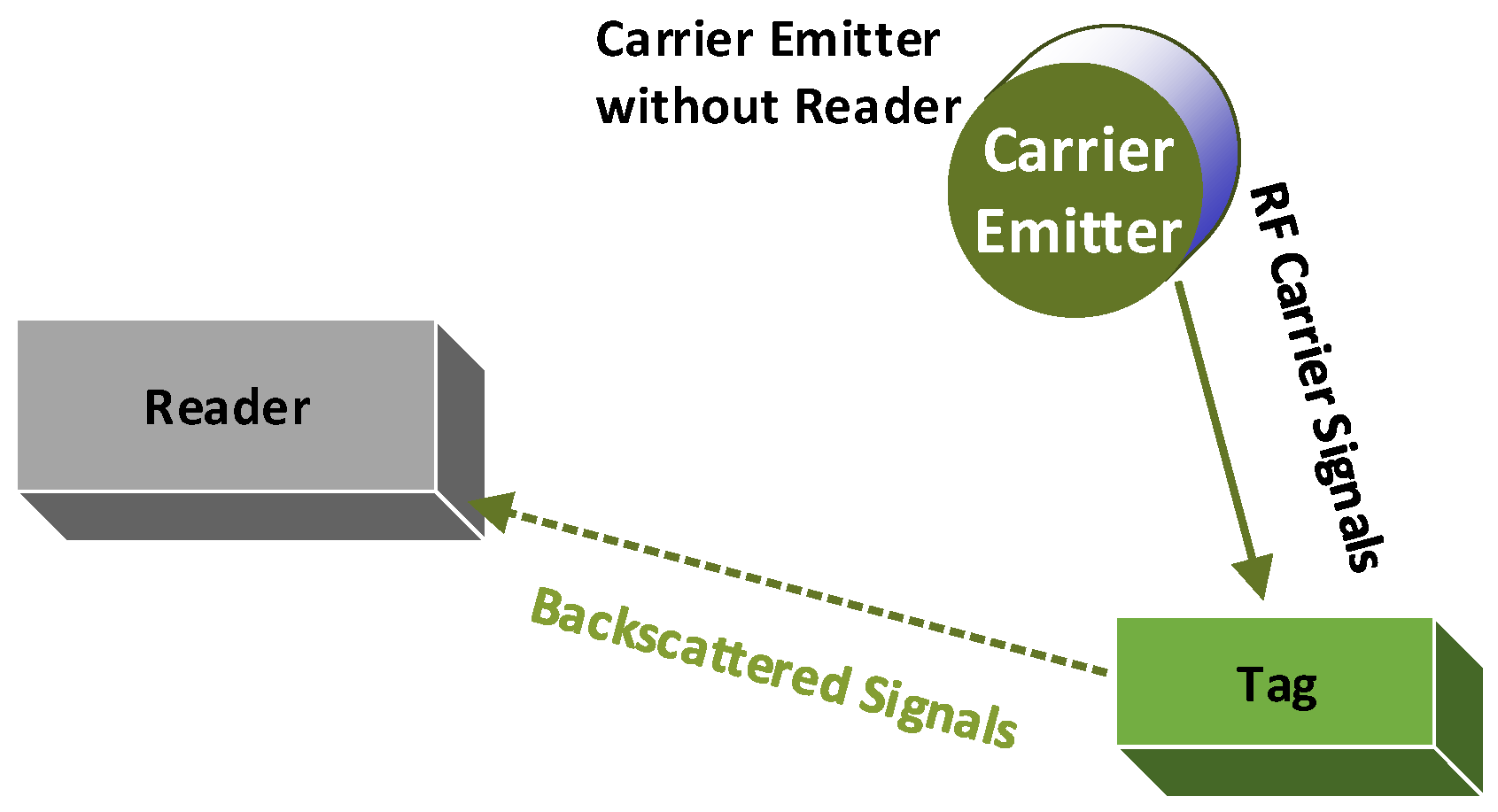
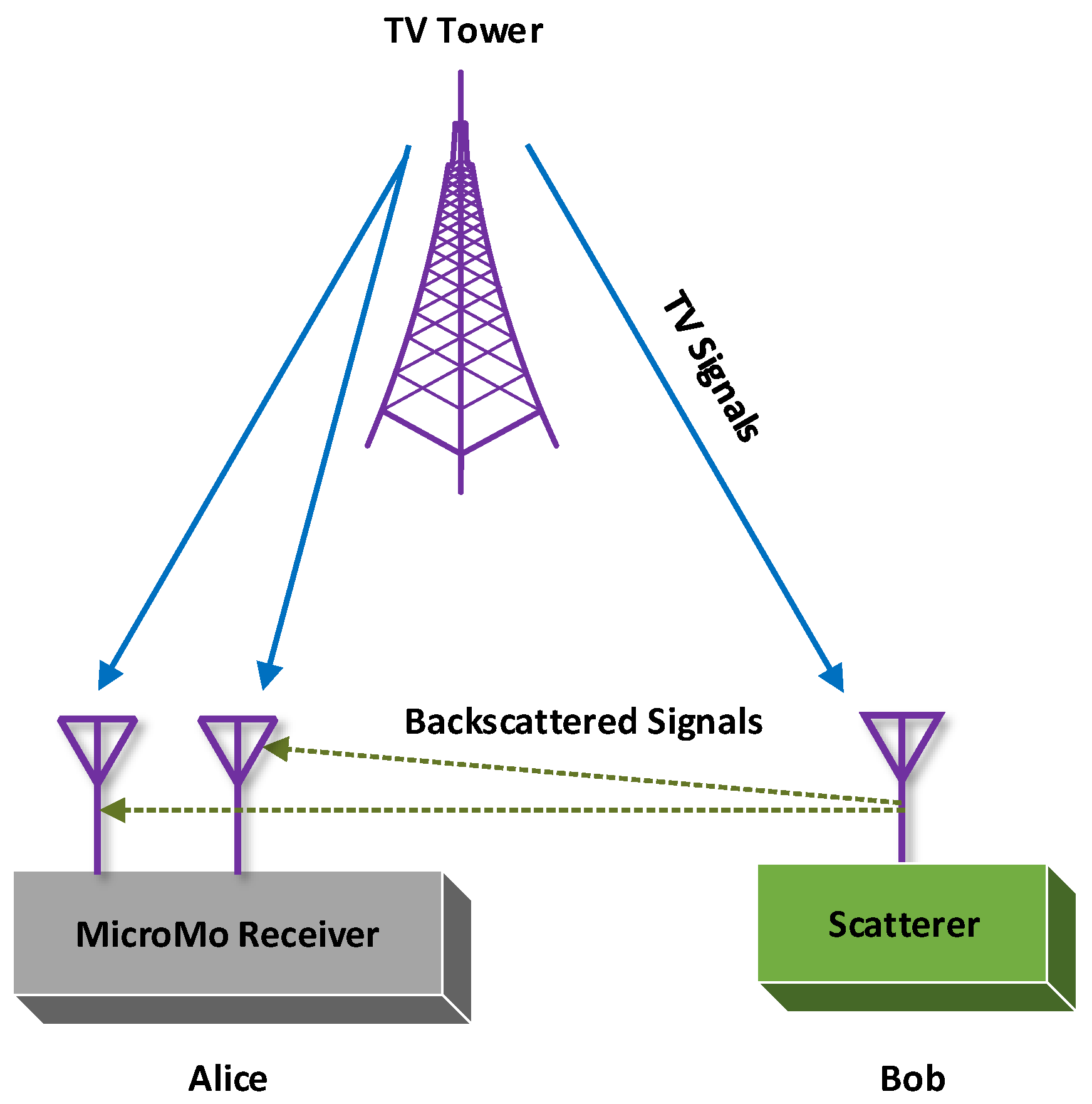
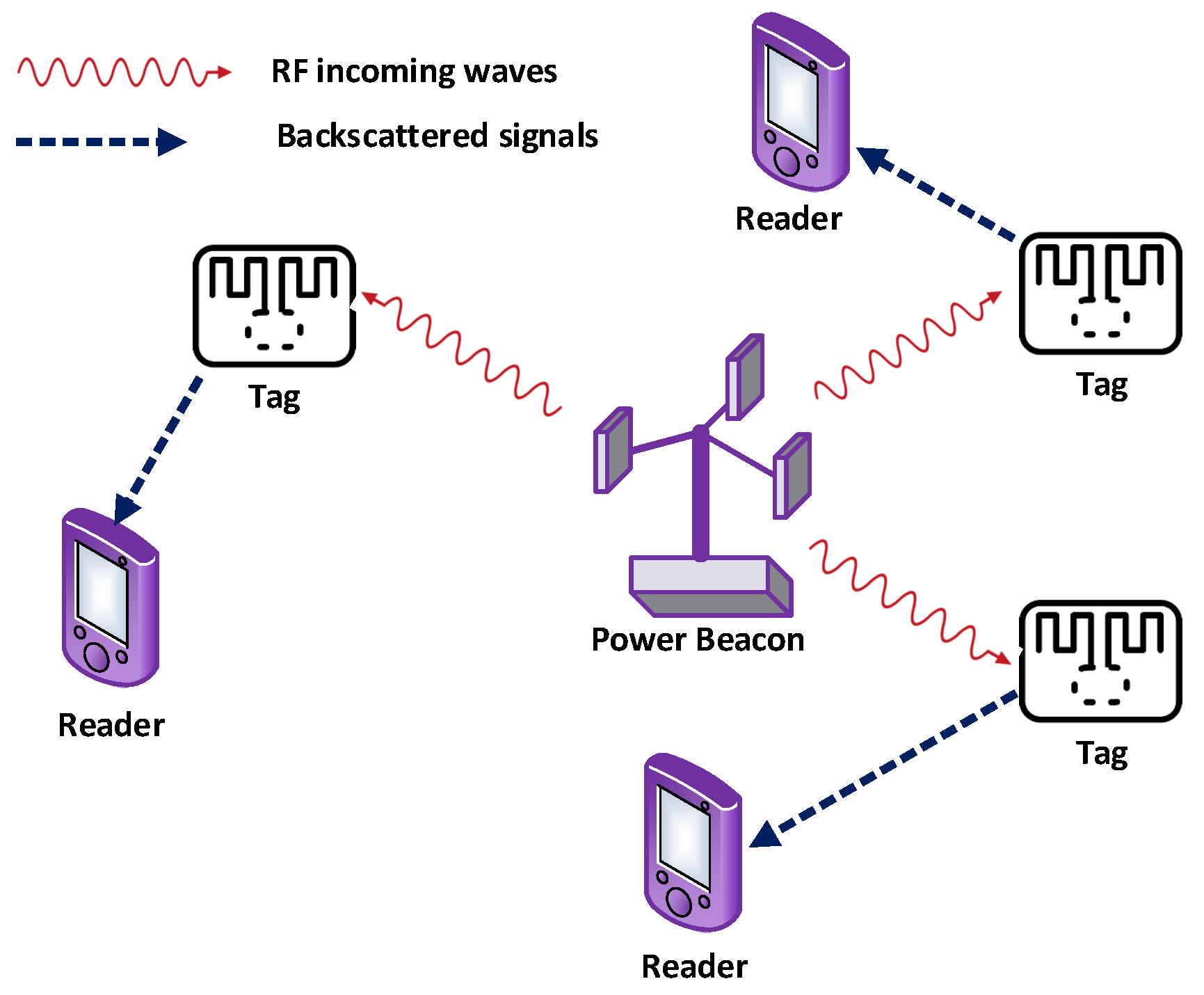
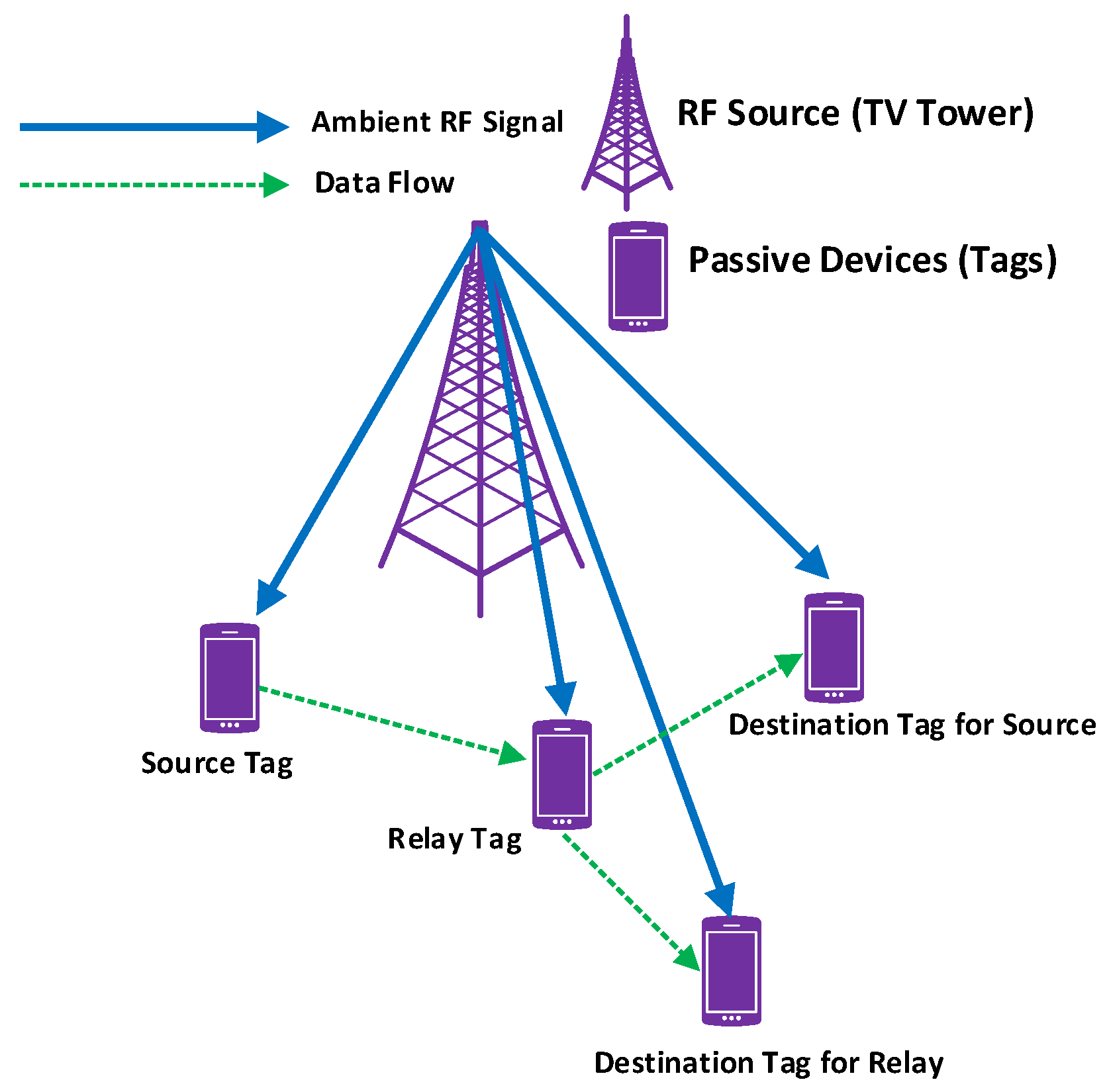
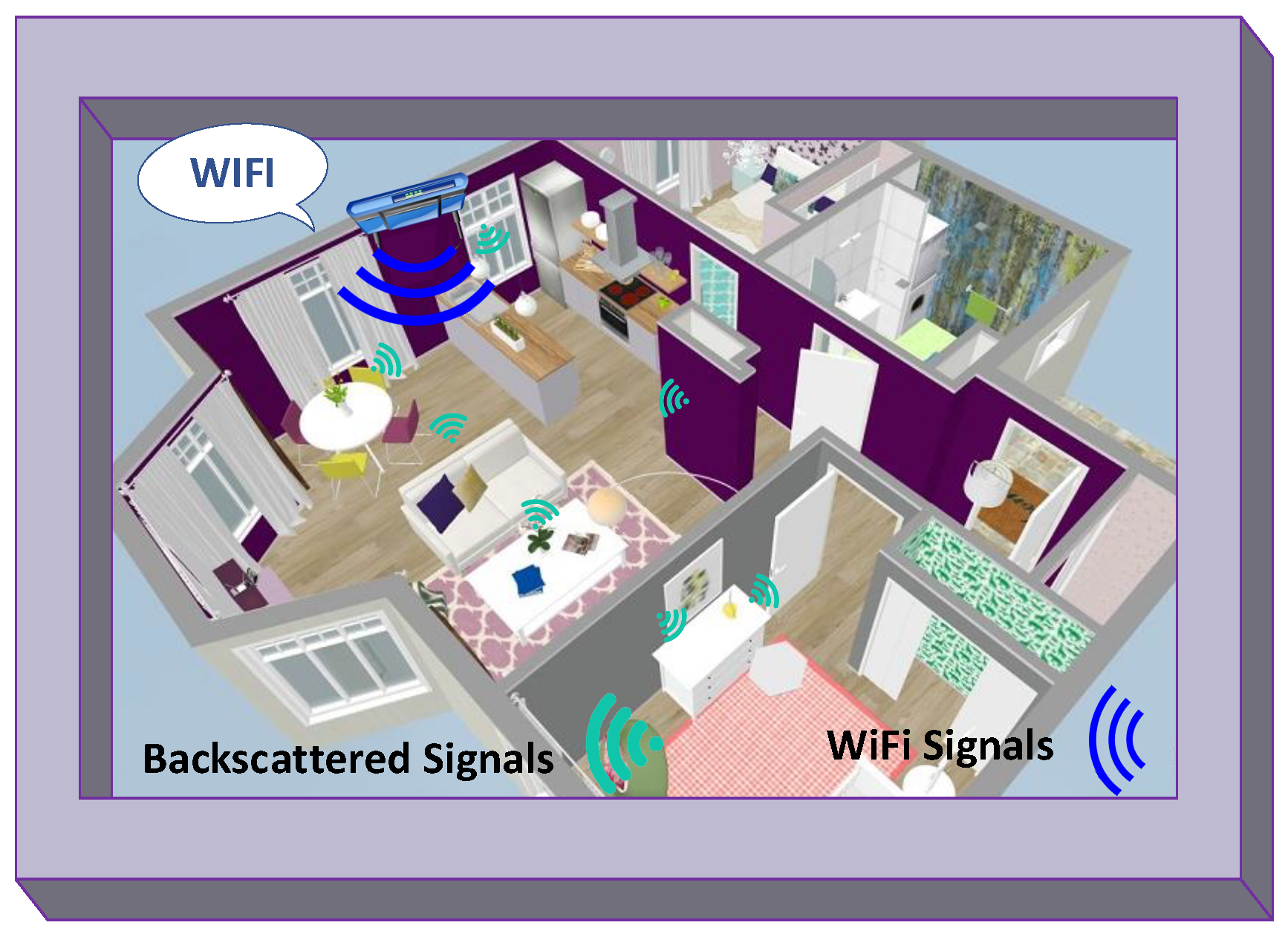
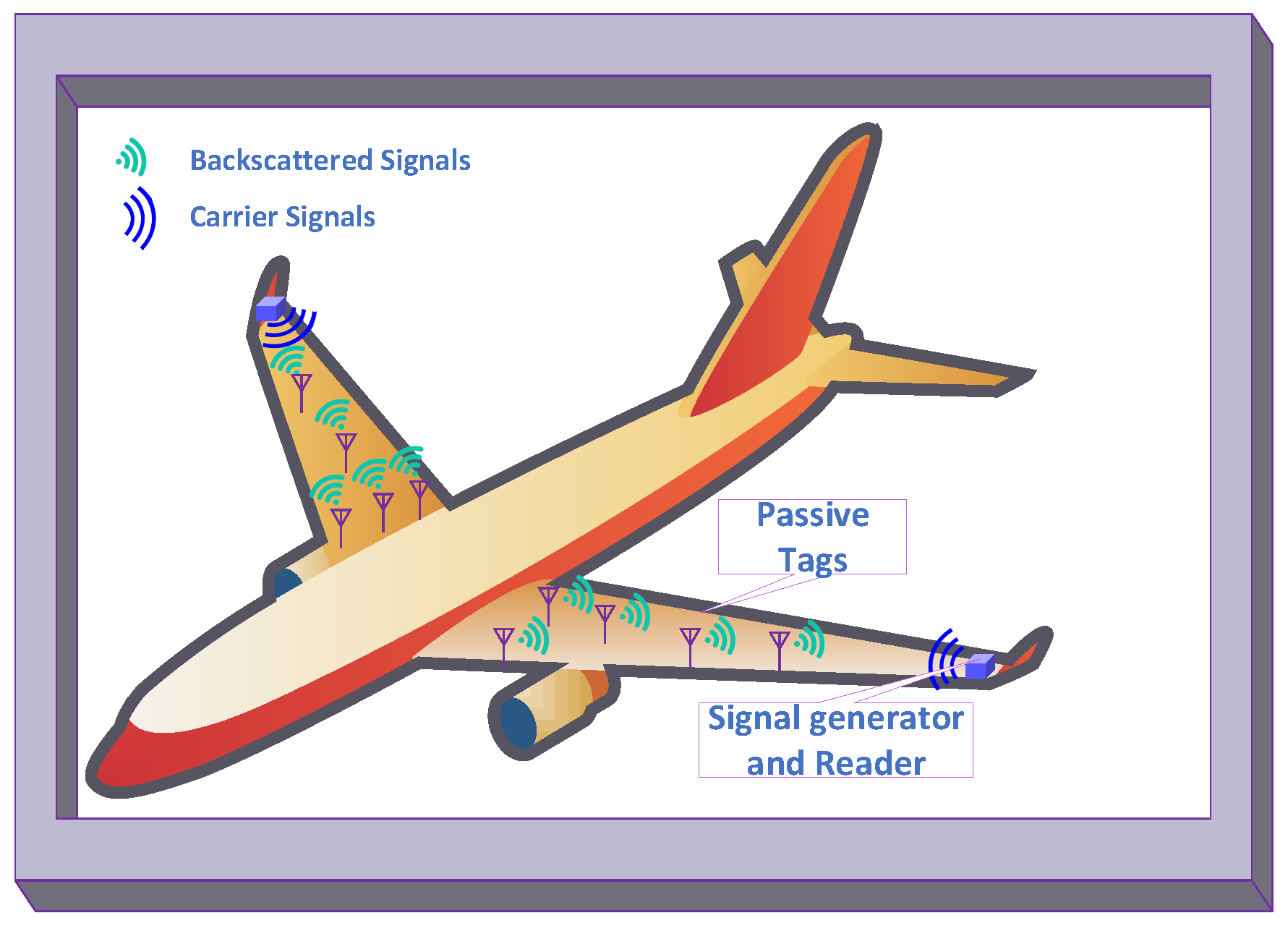
Conventional RFID systems utilize a dedicated radio source and reader. Unlike the traditional RFID system, ambient BackCom (Amb-BackCom) does not need a dedicated RF signal source, such as an oscillator or signal generator with the reader. However, Amb-BackCom explores the advantage of RF signals available in the vicinity (e.g., TV, WiFi, cellular signals, etc.), thus revolutionizing wireless communications [12]. Figure 3 delineates the communication between passive tags by using backscattered TV signals. Currently, researchers are showing great interest in making future communications based on the reflection of ambient RF signals to combat the limited battery life problem in wireless communications [13].
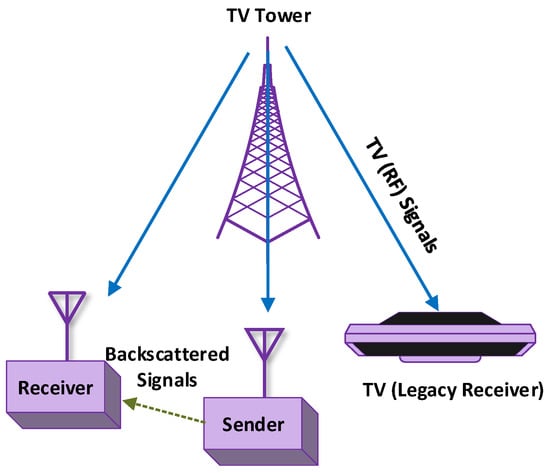
Figure 3.
Passive tags communicating using backscatter communication (BackCom).
5G communication has advantages of high-power mm-waves, in addition to directional beam communication with multi-input multi-output (MIMO) antenna arrays [14], enabling devices to send power beams in a certain direction. Thus, we explore BackCom, which can enable battery-free communications in emerging wireless networks. Existing work has shown a detailed overview of the latest developments in ambient and bistatic scatter types of BackCom [13]. Authors have covered various channel models of BackCom and their theoretical analysis along with experimental measurements. They also discussed the antenna designs in detail. Our survey deliberately avoided content details that is extensively covered in existing work [13], such as antenna design, communication channels, visible light BackCom, and energy harvesting networks. However, our approach suggests the BackCom for emerging battery-free heterogeneous wireless networks. Our work organization explores BackCom with a 5G perspective, which may be suitable for future battery-free communication. Furthermore, our approach bridges the gap between previous works [13] and recent developments, by covering the latest research related to BackCom, battery-free communication, and emerging networks.
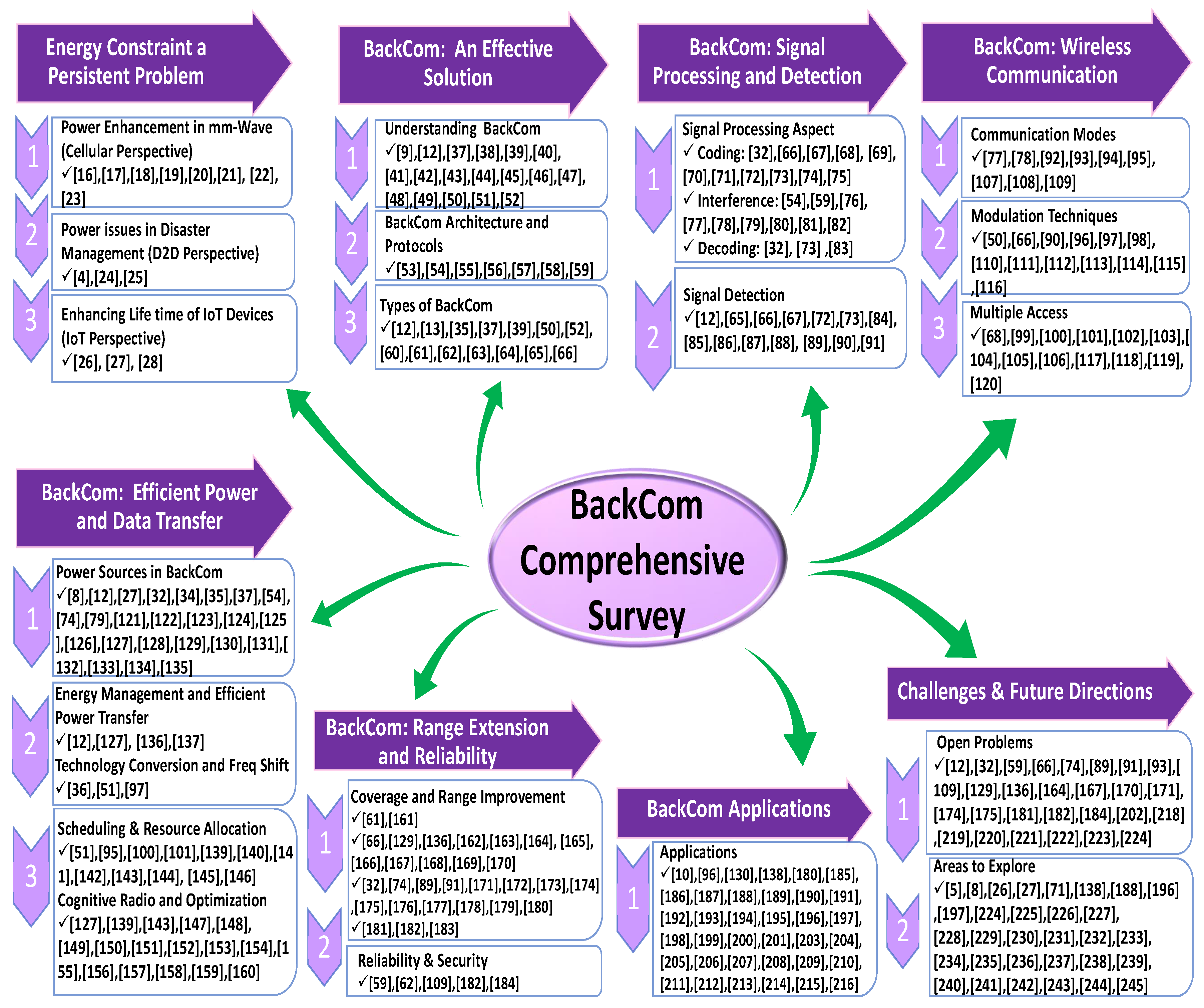
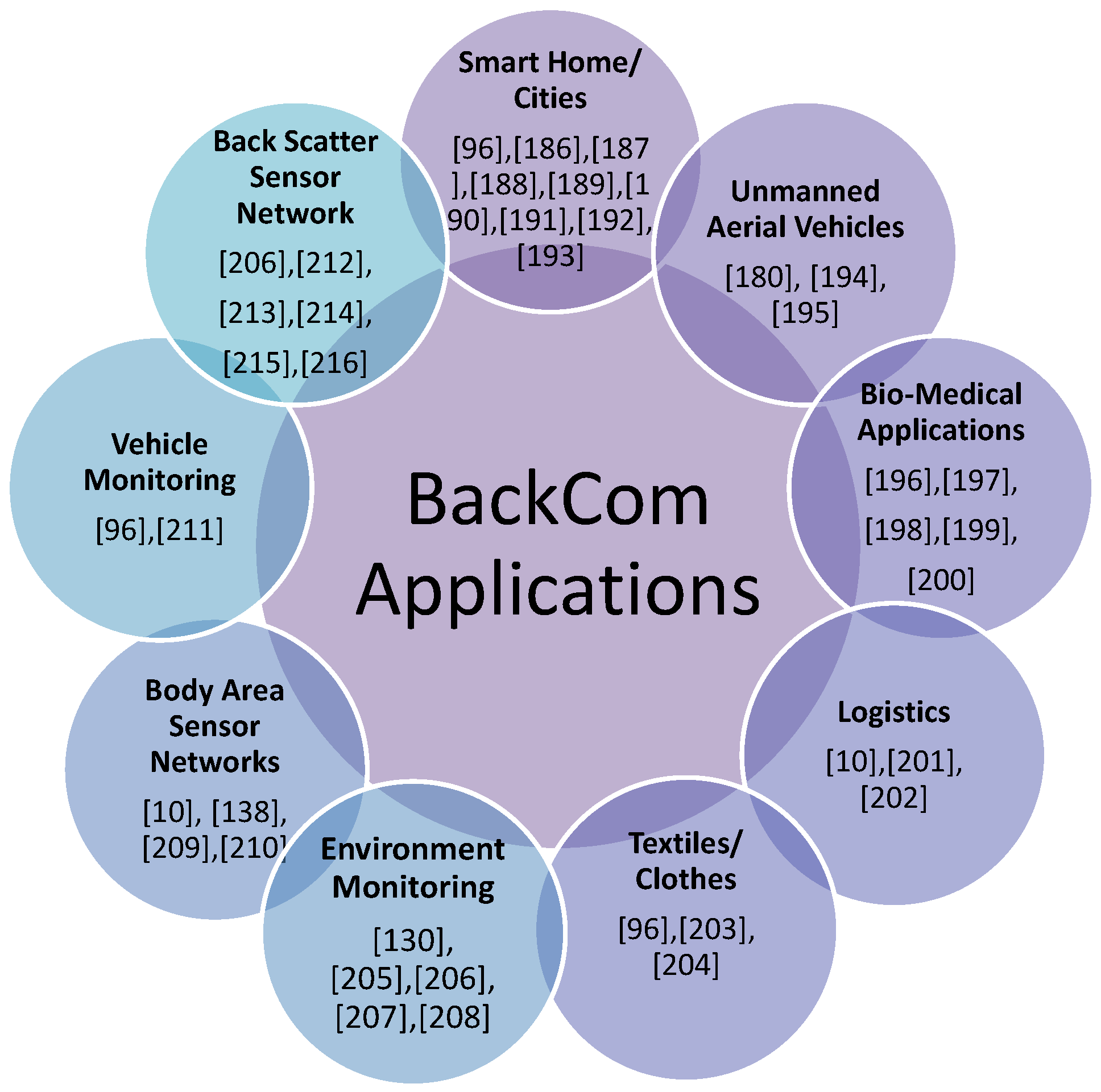
This paper aims to survey BackCom as an emerging technology to solve the limited battery life problem in next-generation wireless heterogeneous networks. Figure 4 presents a taxonomy graph of our survey paper. To be precise, the following aspects are covered in this paper.
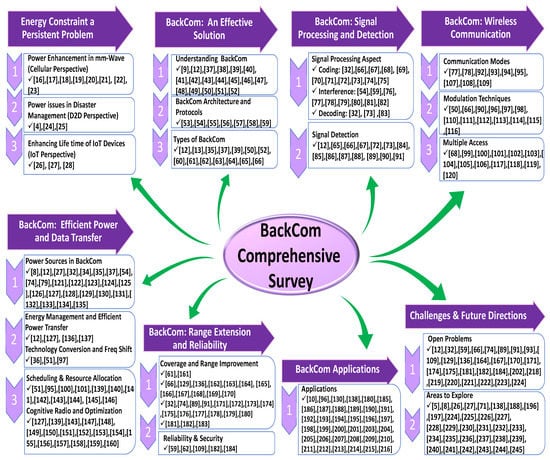
Figure 4.
Overview of our survey paper.
- We discuss the energy constraints in wireless communications and suggest BackCom with emerging 5G wireless as an effective solution to this long-lasting problem.
- We present signal processing and signal detection schemes for BackCom.
- We demonstrate different communication techniques for BackCom including communication modes, modulation techniques, and multiple access schemes.
- We highlight efficient power and data transfer schemes for BackCom, in addition to an increase in the communication range and the reliability of data.
- We show various applications of BackCom, its challenges, and future directions for emerging wireless networks.
The rest of the article is organized as follows. Section 2 focuses on the energy problem in different wireless communications perspectives. The evolution, types, and protocols for BackCom are discussed in Section 3. Section 4 discovers BackCom signal processing aspects, such as coding, interference, decoding, and signal detection schemes. Communication modes, modulation methods, and multiple access techniques for BackCom are explained in Section 5. Section 6 considers different power sources used in BackCom in addition to efficient power and data transfer techniques, such as scheduling, resource allocation, and optimization. The BackCom coverage problem and range extension along with the reliability and security of data are illustrated in Section 7. Different applications of BackCom are shown in Section 8. Section 9 presents the challenges and future directions for BackCom in next-generation 5G wireless networks. Finally, the paper is concluded in Section 10.
2. Energy Constraints—A Persistent Problem
The need for high data rates with high frequency spectrum in 5G cellular networks [14,15] and the objective of uninterrupted internet connectivity in the massive IoT [10] motivate us to explore the feasibility of battery-free devices in emerging wireless communications [8]. Battery-free devices can have the benefit of continuous communications utilizing the same bandwidth. The advantage of using passive devices in wireless communications lies in information exchange without any interruption. Moreover, reliable communication with limited battery life is an important research area. Various steps have been taken to solve the limited battery life problem, and these steps include the designing of energy-efficient network architectures using mm-waves and energy harvesting in mobile networks. We will first discuss the power issues in the cellular, D2D, and IoT perspectives, and we will then review various attempts taken to resolve the energy constraints.
2.1. Power Enhancement in mm-wave—A Cellular Perspective
The utilization of directive antennas enables 5G wireless networks for simultaneous power and data transfer. The higher bandwidth usage allows mobile devices to send and receive a vast amount of data. Ghosh et al. made a case study by utilizing different bands of mm-waves, such as 28 GHz, 38 GHz, 71–26 GHz, and 81–86 GHz for a 5G enhanced local area network [16]. The investigation to collect power from cellular networks has already started [17]. This technique has the potential to supply sufficient energy to devices under the network coverage. Likewise, RF-based energy harvesting in the cognitive cellular networks was proposed in [18]. The work considers that secondary users can harvest energy from the mobile base station (primary transmitter) channel and store it. When the cellular channel becomes idle, the secondary users can use the accumulated energy to fulfill power requirements.
Tu el al. presented numerical results to show that mm-wave frequencies possess the potential to increase the achievable rates and harvested power, compared to conventional cellular networks [19]. A fully functional mm-wave identification system at frequencies above 70 GHz is introduced for the RFID system [20]. This work discusses the size of the transponder in the receiver, while considering backscattering operation, to enable BackCom in low power devices. The concept of BackCom beamforming is introduced through continuously variable antenna loads [21]. Wang et al. introduced wireless power transfer for mm-wave cellular networks and found users with high energy storage [22]. The energy storage power was examined and recharged with mm-wave base stations. Subsequently, energy harvesting performance for low power devices, energized by the mm-wave cellular networks, was analyzed to show improvement in energy coverage with narrower beams, during beam alignment between transmitter and receiver [23]. Moreover, this work also indicates that wider beams provide more energy if receivers are not aligned with any specific transmitter.
2.2. Power Management in Disasters—A D2D Perspective
Efficient reliable and agile communications during disaster can be achieved if we address the hindrance of limited battery life. Different techniques are proposed using D2D communications to optimize the battery life in critical communications. Survival in sharing mechanism uses D2D-based communications features to overcome battery power limitations during disasters [4]. A D2D discovery mechanism was considered by exploring the proximity area concept, for energy-efficient D2D communications [24]. A D2D-based messaging solution was also proposed to overcome battery power limitation issues in disaster situations [25]. Unfortunately, battery has finite energy, and the stored energy drains as all electrical charges flow out. Hence, state-of-the-art network architecture for critical communications is of no use if devices suffer from power constraints.
2.3. Enhancing the Lifetime of Devices—An IoT Perspective
The concept of IoT encompasses resource-constrained devices (such as tiny, battery-powered wireless temperature sensors, humidity sensors, movement detectors, etc.). To address the energy needs in IoT, an energy-efficient network architecture was proposed. This architecture avoids the energy hole problem (uneven energy drainage) using sensor and relay nodes [26]. The Quark operating system (OS) was introduced for low power IoT devices, with very small energy buffers [27]. The Quark OS saves power by scaling down every task of communication, sensing, and computation into small quanta (e.g., one pixel, half a bit) by fragmentation. The Quark OS has better performance than other traditional OSs for IoT. Magno et al. suggested an energy-efficient multi-sensing platform WuLoRa (wake-up long range) for IoT by combining wake up radio and LoRa (long range) [28]. The wake-up radio technique, made for self-sustaining sensing application, enhances the operative lifetime of outdoor and indoor devices by utilizing low power hardware construction in IoT networks. The power consumption and latency is reduced by using ultra-low power wake up radio, supporting long-range communications.
Discussion:Table 1 summarizes Section 2 and covers limited battery life as a long-lasting problem in cellular networks, D2D communications in disaster management, and IoT devices. Various steps have been taken to address the energy problems mentioned above, some of which are discussed below.

Table 1.
Summary of energy constraints in wireless communications.
- Energy harvesting from the base station can be used for energy-efficient communications in cognitive cellular networks [18]. This technique is useful to address energy problems while considering busy channels.
- mm-waves enable devices to harvest more power compared to conventional mobile networks [19]. mm-waves can also address energy crises in dense network areas to fulfill power demands.
- D2D-based survival in sharing techniques [4], D2D discovery mechanisms [24], and D2D-based messaging [25], perform well in disaster scenarios to combat power issues.
- An energy-efficient network architecture [26], a small power OS (Quark OS) [27], and low energy sensing platforms [28] are preferred in IoT to fulfill energy needs.
3. BackCom: An Effective Solution
The high expectations of emerging 5G technology to connect massive IoT devices to the Internet [14,26] and to enhance the bandwidth of cellular network [19,22,23,29,30] made users expect a solution to the limited battery life problem in cellular networks, since the major constraint with wireless communications is the limited battery life. The problem of limited battery life can be effectively addressed if there are battery-free communications. The popular technique in recent ultra-low power communications is BackCom, which is based on RFID technology and receives power from nearby sources [12,31,32,33,34,35,36,37]. BackCom enabled the first battery-free cell phone with all passive components [8]. The battery-free cell phone is an ultra-low power device that consumes very little power and does not require a battery. Moreover, it does not possess any digital signal processing component in the handset. The analog voice signals are modulated directly on the carrier waves by utilizing BackCom and amplitude modulation. Subsequently, the nearest base station is responsible for receiving analog signals from the cellphone for all digital processing of the signals. The special microphone in the cellphone works as a capacitor that generates sufficient power to energize the earphones, in conjunction with other energy harvesting components. In summary, BackCom devices do not require any battery but harvest power from incident RF signals. Hence, BackCom is the desired solution to combat the energy crisis in emerging wireless networks. BackCom can also lead us to new communications protocols suitable for future battery-less devices.
3.1. Understanding BackCom
Table 2 demonstrates the complete evolution of BackCom since its roots in 1945, with the concept of a spying device used by the Soviet Union to listen to conversations had at the US embassy [38]. Similarly, in the Second World War, BackCom was used to reflect back RADAR signals to identify “foes” or “friends” [39]. The idea of backscattering was officially published in 1948 by Harry Stockman [40]. Afterwards, Norman proposed a radio-communication-based Aloha system in 1970 for linking interactive computers and devices [41]. Later, electronic toll collection (ETC) based on RFID was introduced to collect tolls from vehicles [42,43]. The hardware implementation was proposed for bridging physical things and the virtual world using electronic tags [44].

Table 2.
Evolution of BackCom.
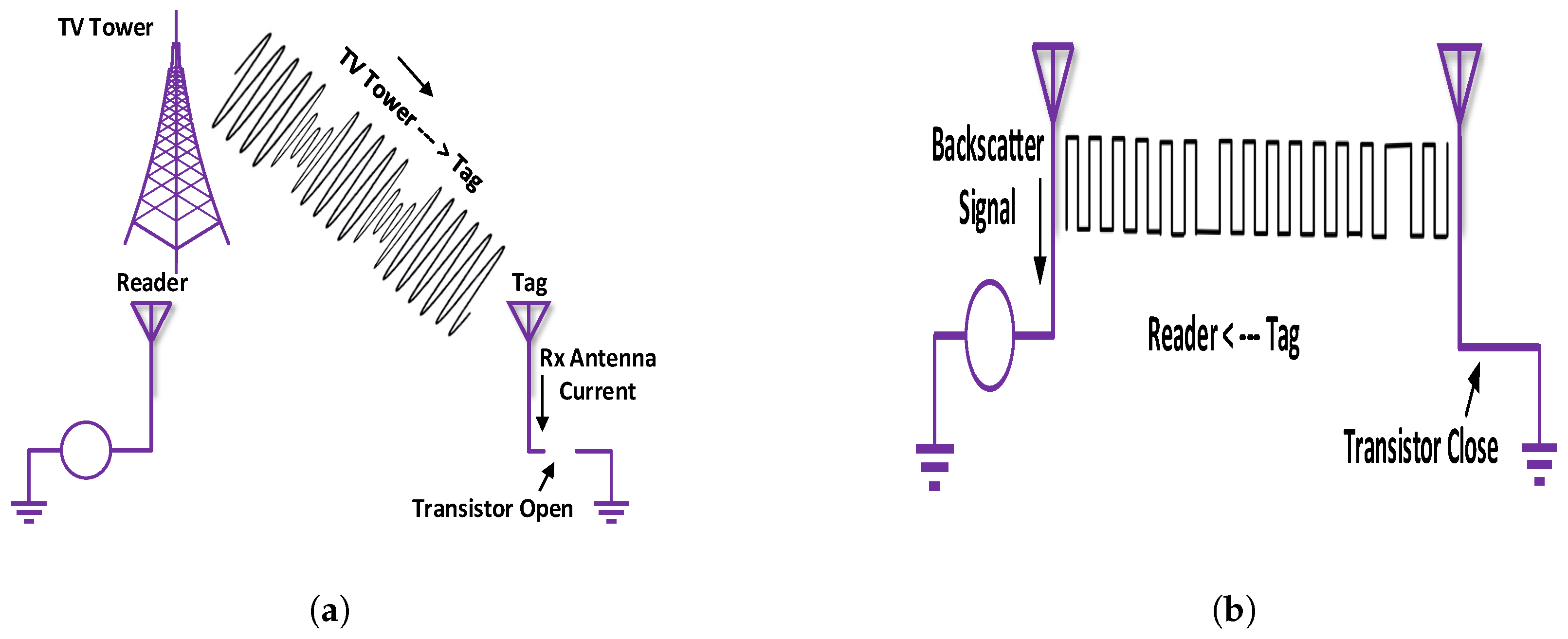
The signal flow diagram for BackCom shown in Figure 5a illustrates the carrier signals moving from a TV tower to a passive tag. The information-carrying backscattered modulated signals, moving from tag to reader, are demonstrated in Figure 5b. The backscatter radio system allows passive tags to consume sufficient energy from incident RF carrier signals, generated by different sources, while reflecting back part of the carrier signals to transmit the tag’s data [45]. The working principle of BackCom [46], compared to traditional RFID, is as follows:
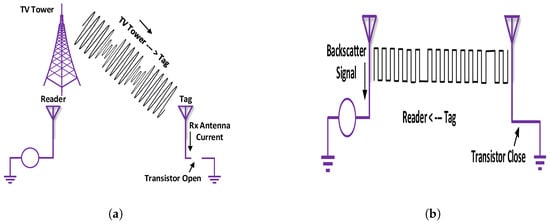
Figure 5.
Basics of BackCom. (a) Signal from reader to tag; (b) signal from tag to reader.
- Conventional RFID reader generates and transmits carrier waves to the RF-tags. In BackCom, the reader does not require carrier wave production. Instead, the tags receive the signals from nearby TV, cellular, or WiFi waves.
- BackCom considers passive tags, similar to the RFID system. These passive tags capture electromagnetic (EM) waves to extract power.
- Similar to RFID, the BackCom tag possesses a small dipole antenna that collects the energy as the varying potential difference, appearing across the arms of the dipole antenna.
- A diode rectifies the potential in the arms of the dipole antenna, and the rectified voltages are then stored in the capacitor to supply continuous energy to the electronic circuit [47].
- The electronic component contains a micro-controller that can save the tag’s information.
- The tag’s data is then modulated by reflecting incident RF signals. An on–off keying (OOK) scheme of amplitude modulation is usually considered.
- Intentional impedance mismatching between the tag’s load and the antenna causes the reflection of incident signals to modulate the tag’s information. The increase or decrease in impedance causes the circuit to work as a transistor in an open switch state or a closed switch condition.
- The RF reader in RFID and the corresponding BackCom reader in the tag decode the information of the received signals reflected by the tags.
The above-mentioned eight points explain the BackCom working principle. The internal architecture of BackCom tag is elaborated below, in addition to the communication protocols for passive tags.
3.2. BackCom Architecture and Protocols
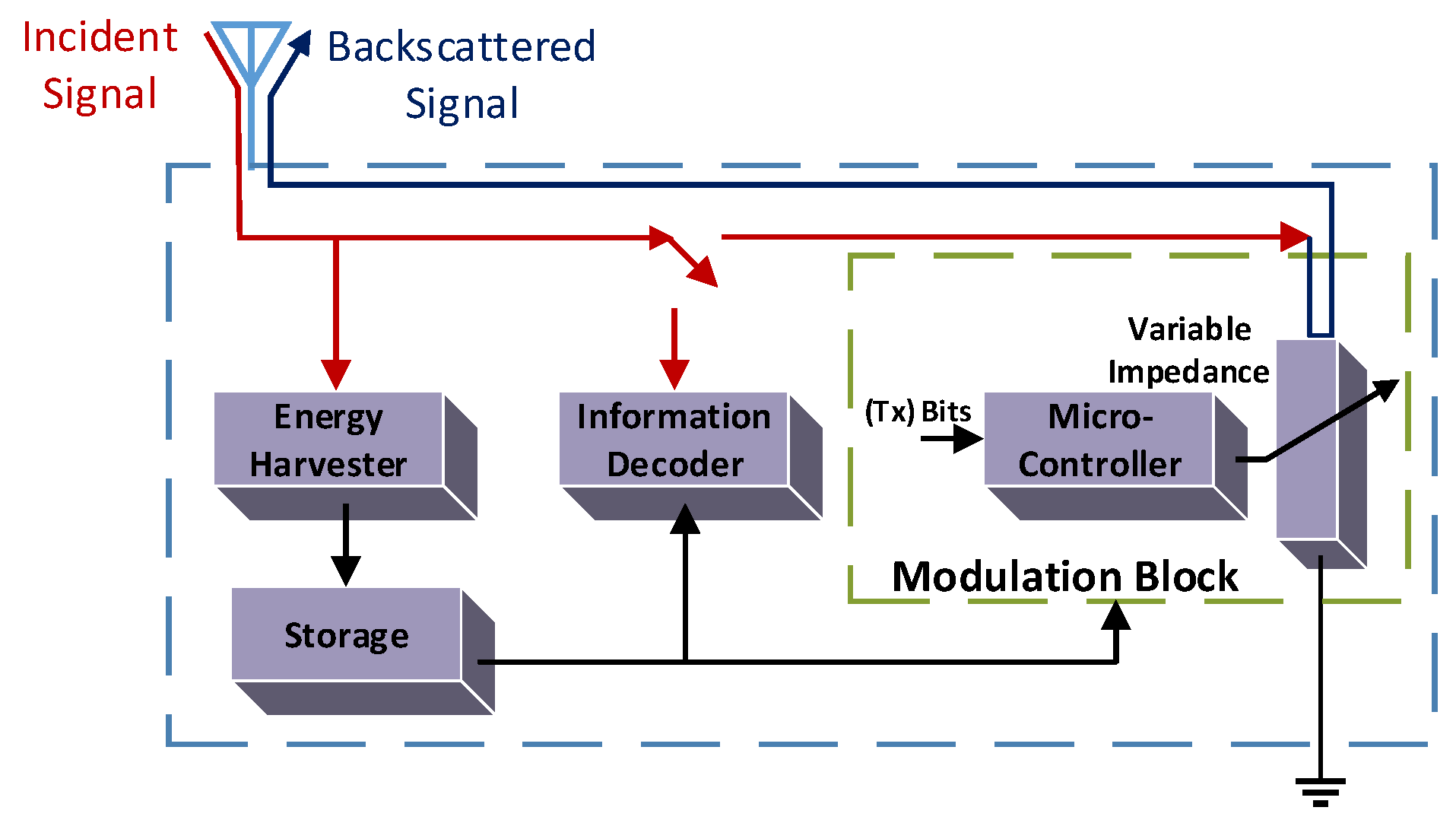
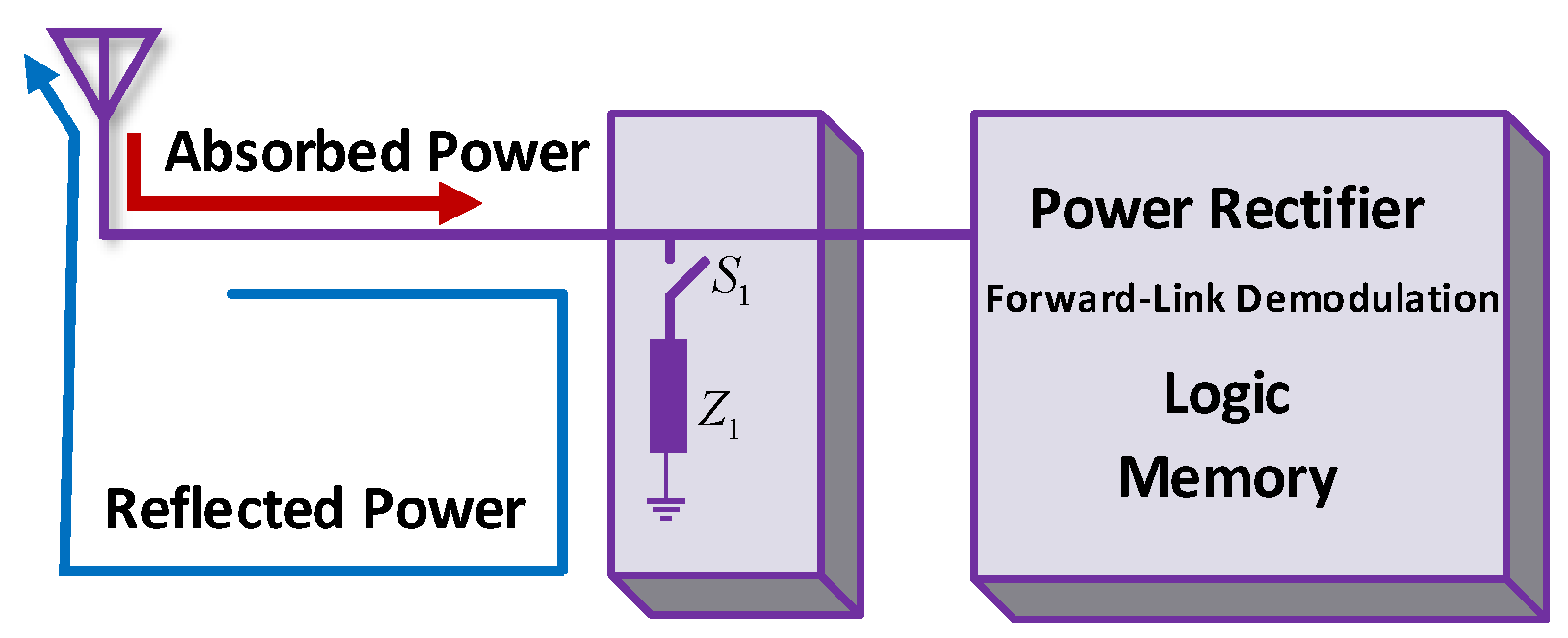
Figure 6 delineates the architecture of the BackCom tag and shows a passive tag receiving carrier signals, transmitted by the RF source. The energy harvester block of the tag can harvest energy from carrier signals. The accumulated energy can be collected in the capacitors or energy storing components in the storage block. The stored energy can supply consistent power to send information to the decoder unit and the modulation box. Subsequently, the micro-controller in the modulation box can modulate the unique information of the tag on the carrier signals via the backscattering operation [9]. The signal backscattering is caused by changing the impedance intentionally, as shown by the variable impedance block in Figure 6. Similarly, an architecture of the receiver is presented in [53]. It consumes 361 W and is compatible with battery-free applications. We have considered the physical architecture of the tag and its different blocks. Various protocols will now be discussed. Efficient BackCom protocols can maintain consistency between the harvested power and the data transmission via the same antenna in the tag.
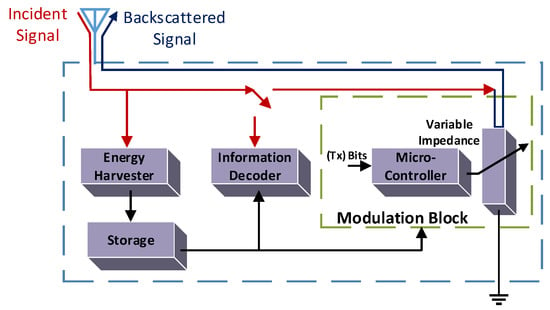
Figure 6.
Architecture of the BackCom tag.
The passive tags always rely on external power sources to harvest sufficient energy for their operation. However, maintaining uniformity in the power harvesting rate and the information transfer in passive tags is a challenging task. Efficient protocols can address this challenge by maintaining the energy harvesting rate and data reception. The scenario that uses RF tags to harvest energy first and to then utilize the stored power to transmit information from tags to readers is referred to as the harvest-then-transmit (HTT) protocol. The HTT protocol is used to maximize the expected throughput of wireless communications (using direct and relay transmission) with non-dedicated sources [54]. Similarly, a hybrid access point (Hybrid-AP) employs the HTT protocol and initially broadcasts wireless energy to various distributed users in the downlink while allowing the device to transmit data to the Hybrid-AP while working in uplink mode [55]. Similarly, the Flit protocol was also designed to increase channel utilization while reducing energy loss [56]. Flit improves the data rate by exploring idle listening and reduction in collisions between multiple tags. Moreover, Flit offers practical and straightforward coordination mechanism for tags. Zang et al. proposed the QuarkNet stack [57], which divides the BackCom network stack into random smaller units called micro-frames. The micro-frames depend on the remaining energy of the tag. The frame size in QuarkNet could be at least 1 bit in limited energy scenarios and as large as a complete frame in the case of sufficient available energy [57].
Usually, a tag has to wait for carrier signals to be transmitted completely by the RF source. Afterwards, the tag can transmit its complete signal. This symmetry between the transmitter and tag is exploited by Hu et al. [33]. The authors propose a fully asymmetric protocol for BackCom, namely the Laissez-Faire protocol, which allow nodes to transmit data as soon as they sense carrier signals. This technique takes advantage of the ability of the reader to sample data at a rate higher than the tag. Moreover, this method suggests concurrent transfers in asymmetric BackCom. For concurrent transmissions from various devices, the NetScatter protocol is suggested [58]. NetScatter uses a distributed coding mechanism and can decode all concurrent transmissions using only a single FFT operation. Likewise, Wang et al. presented the automatic rate adaption protocol, which adapts the aggregate bit rate of multiple transmitters [59]. However, this protocol could not change the transmission bit rate individually. We have discussed protocols and taking advantage of RF signals in different scenarios. We will now outline multiple configurations of the source, reader, and tag. These configurations further lead to different types of BackCom, having their own advantages as well as shortcomings.
3.3. Different Types of BackCom
Conventional BackCom systems send the carrier signals generated from the RF reader to the passive tag. Some parts of the carrier signals reflect back to modulate the information from tag to reader. This to and fro process involves round trip path loss [60], and limits the range of reflected signals. This limitation in range problem draws more attention towards the coverage problem in BackCom [12]. Moreover, the coverage problem finds different configuration setups among source, tag, and reader to minimize the associated path loss. These set of configurations can further improve the range of BackCom, while reducing the path loss [61,62,63,64].
The category of BackCom systems depending on devoted carrier generator is known as “dedicated BackCom (Ded-BackCom).” BackCom with multiple carrier sources for different tags is called “ambient BackCom (Amb-BackCom).” The classification based on an arrangement of source and reader is “hybrid BackCom,” a combination of Ded-BackCom and Amb-BackCom. The arrangement involving the dislocation of the reader from the signal generator source is referred to as “bistatic scatter (BiS).” The BackCom type that uses the same antenna for transmitter and receiver is known as the “monostatic BackCom (Mon-BackCom).” These types of BackCom are discussed in detail below.
3.3.1. Dedicated BackCom
Figure 7 delineates the concept of Ded-BackCom, which considers a dedicated power source for a tag. This type is used to obtain the high throughput and the least interference compared to other BackCom configurations. Ded-BackCom is widely used in a variety of applications. Kellogg et al. consider a passive WiFi system with a dedicated WiFi source in order to transmit RF carrier signals [35]. Moreover, the paper also discusses the frequency range outside the desired WiFi channel band for BackCom, which allows a WiFi receiver to suppress the resulting direct link (out-of-band) carrier interference.
Figure 7.
Dedicated BackCom.
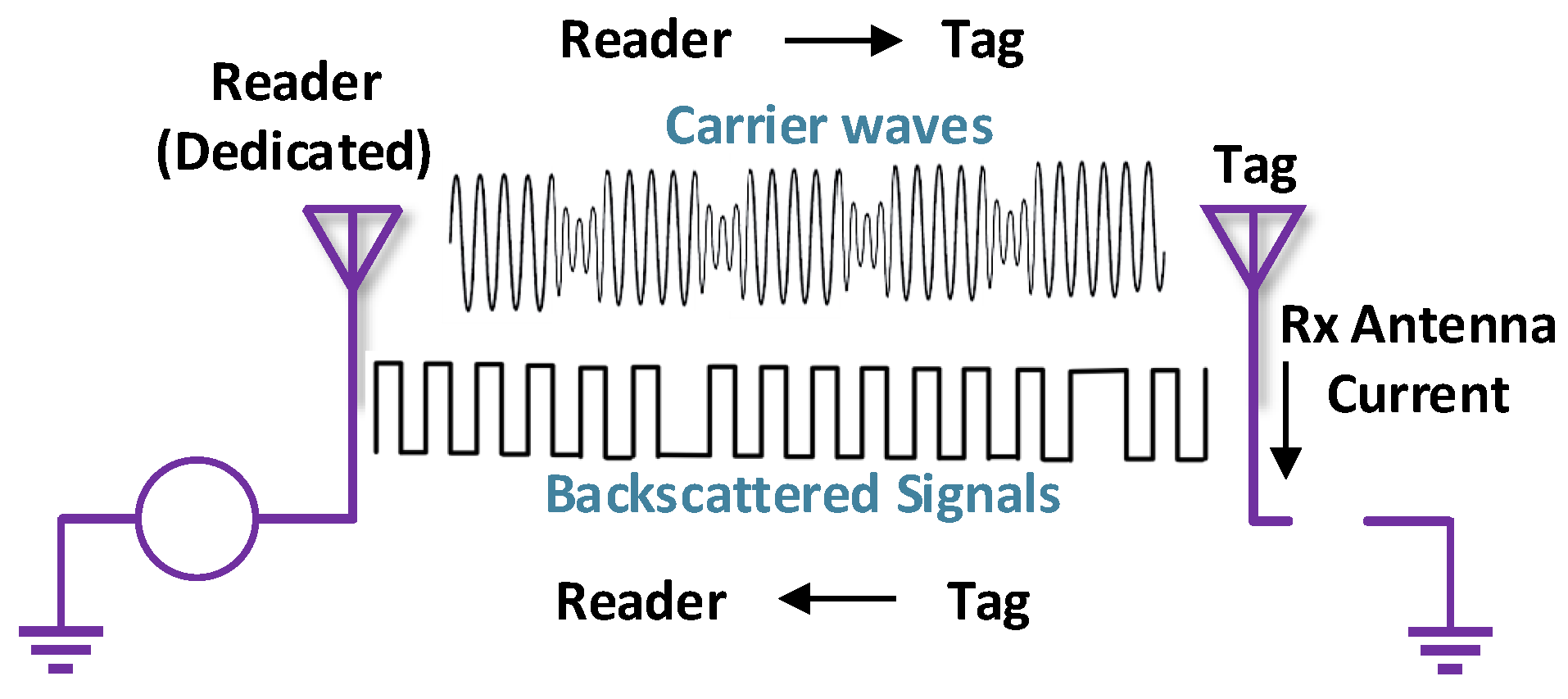
3.3.2. Ambient BackCom
This type of BackCom uses ambient (surrounding) RF signals, such as television (TV), cell phone, and WiFi signals as the carrier, to power up the passive tags, respectively [37]. A passive tag can communicate with another passive tag by reflecting incident ambient signals after modulating its information [12].
Figure 8 depicts ambient configurations. The working principle of Amb-BackCom is described below:
Figure 8.
Ambient BackCom.
- Passive tags receive RF signals from the surrounding RF sources.
- Tags harvest power from ambient signals to modulate their information, using the OOK scheme.
- Tags transmit binary bits due to change in the impedance. The “0” bit is transmitted when the antenna has high impedance and when major parts of the signals are reflected. On the other hand, for binary “1” the antenna impedance would be low, and the signals are considered least reflected.
- Since the TV or other nearby signals already have information on them, to avoid data overlapping between original and modulated signals, the passive tags transmit their data by reflecting the signals at a smaller bit rate than the surrounding radio waves rate. Afterwards, the receiver can differentiate among both signals by taking their mean value.
This type of BackCom revived the use of RFID technology by utilizing nearby signals of different technologies [13]. Different types of communication channels such as the basic backscatter channel and the dyadic backscatter channel for Amb-BackCom have been explored with multiple antenna designs [13]. Furthermore, the idea of Amb-BackCom was utilized for the communication between two passive tags to calculate the associated bit error rate (BER) [65]. Unfortunately, the ambient signals have low signal power compared to dedicated source, and backscattering operation weakens these signals even more. In order to provide sufficient power to tags, another approach is suggested below.
3.3.3. Bistatic Scatter
Kimionis et al. present the bistatic scatter (BiS) configuration for BackCom [50]. Figure 9 illustrates BiS BackCom, showing an RF receiver that is separated from the carrier emitter. BiS configuration increases the communication range by bringing the carrier emitter closer to the tag. The carrier emitter has an oscillator and power amplifier to generate and transmit the carrier signals. It is different from the traditional reader, such that it does not possess its own receiver. The signals generated from the adjacent carrier emitter in the BiS scenario reduce the round trip path loss by decreasing the distance between the tag and the power source (carrier emitter) [60]. In this way, the reflected signals have a higher signal-to-noise ratio (SNR) at the receiver end when compared to Amb-BackCom. Furthermore, this type of bistatic setup for communications shows better BER performance in the receiver than its counterpart [66]. Similarly, for an extended range, a full signal model for BiS radio is derived to demonstrate the experimental ranges of order 100 m [50]. However, it is not possible to consider a nearby signal generator in every scenario. Considering the size limitations of passive devices, another type is discussed below.
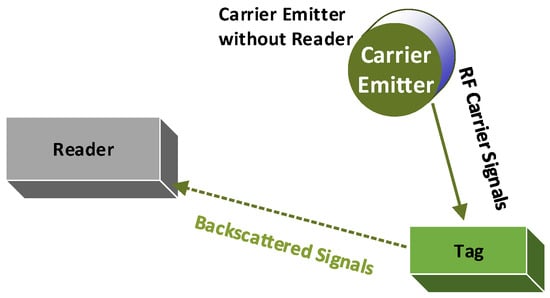
Figure 9.
Bistatic Scatter Communication.
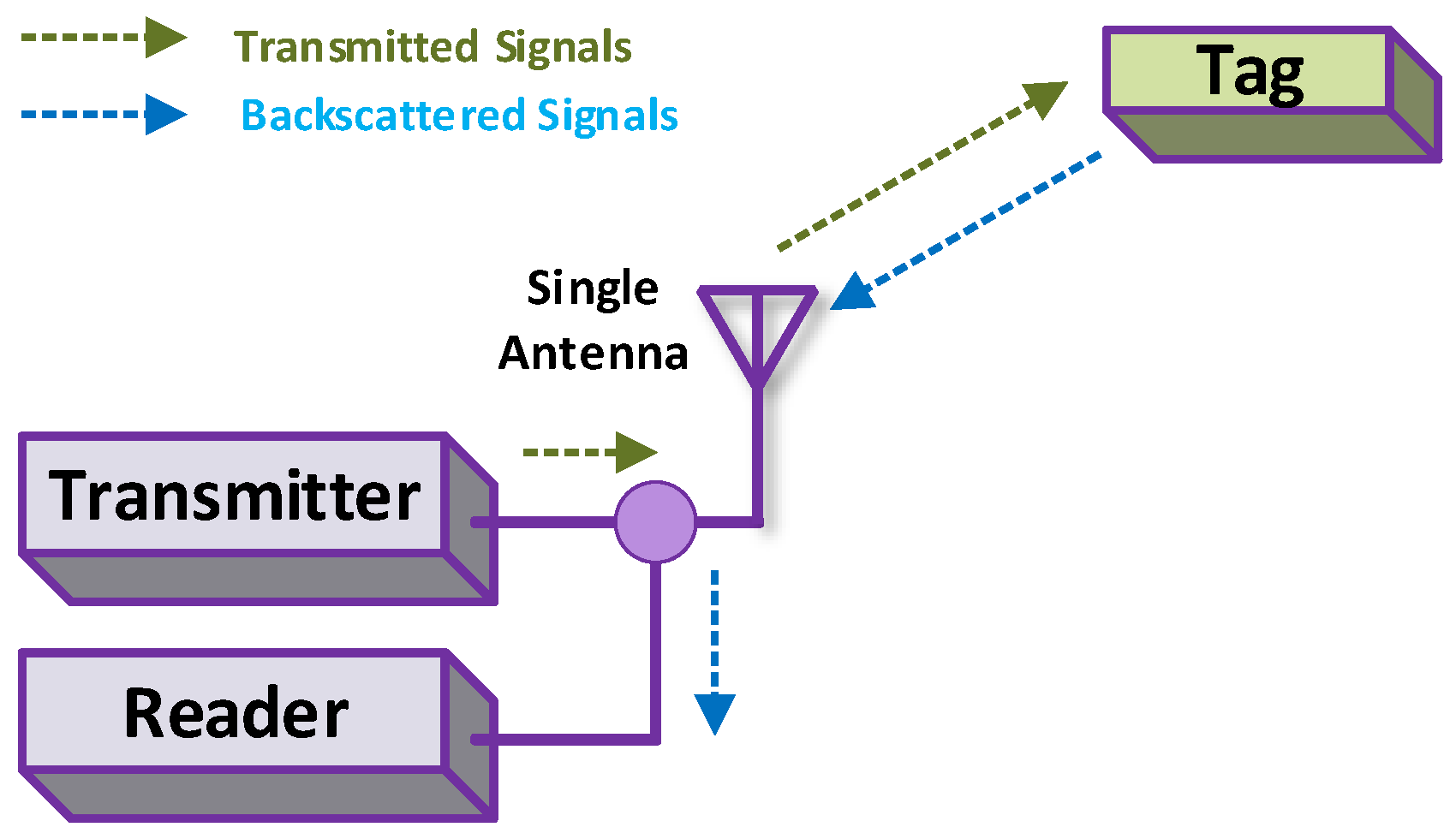
3.3.4. Monostatic BackCom
The preceding configuration of BackCom needs two separate antennas, one each for transmitter and receiver. On the other hand, some applications such as hand-held readers cannot afford two antennas, due to the additional size, complexity, and expense. Alternatively, a single antenna can be used for both transmission and reception. Such configuration is referred to as Monostatic BackCom (Mon-BackCom) [39]. Figure 10 shows the transmission and reception process using the single common antenna in the reader. However, the data rate of this type of BackCom is low due to the one-way information transfer. Exploiting two different types of BackCom, a hybrid combination is elaborated below.
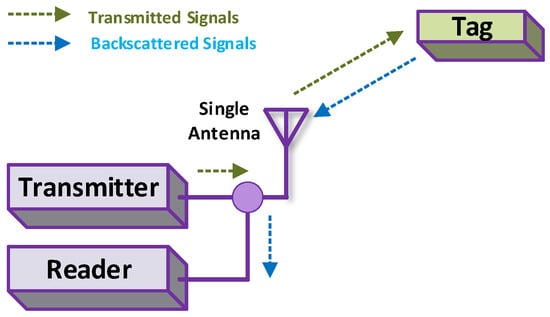
Figure 10.
Monostatic BackCom.
3.3.5. Hybrid BackCom
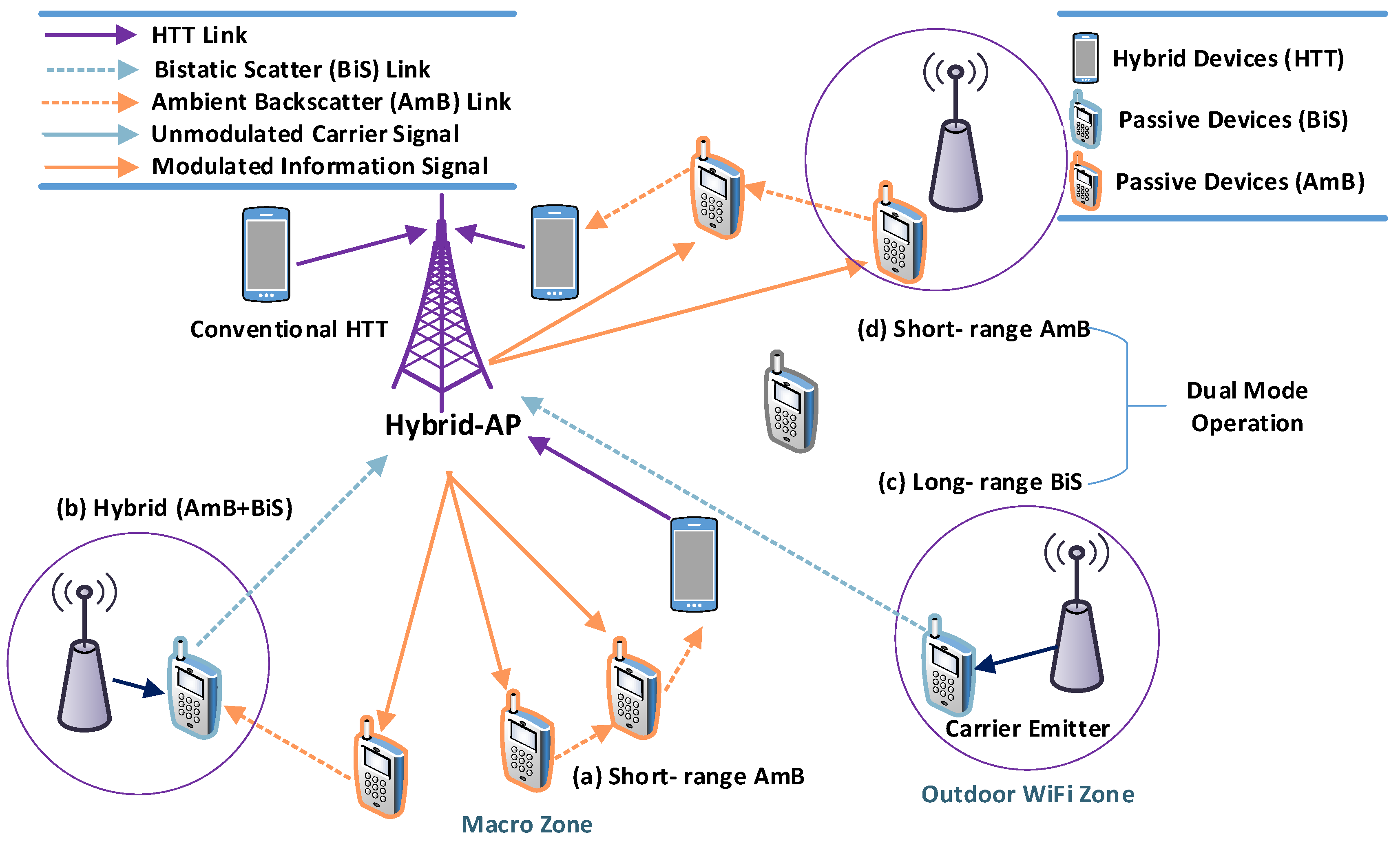
In traditional BackCom, the tags first harvest energy and then transmit data. This process creates some delay in communications. To overcome the delay, ambient and dedicated sources can be used together. This combination is known as “Hybrid BackCom.” Figure 11 depicts a hybrid BackCom scenario, which includes various types of links and devices. Figure 11a demonstrates short-range ambient communications in the macro zone between ambient devices and hybrid devices connected via Hybrid-AP. Figure 11b exhibits a scenario for hybrid communications employing ambient as well as bistatic types of BackCom. Long-range BiS is shown in Figure 11c,d, showing short range Amb-BackCom with its dual mode of operations. In dual mode, tags can operate in the individual mode of Amb-BackCom, dedicated BiS, or hybrid (both together) mode [52].
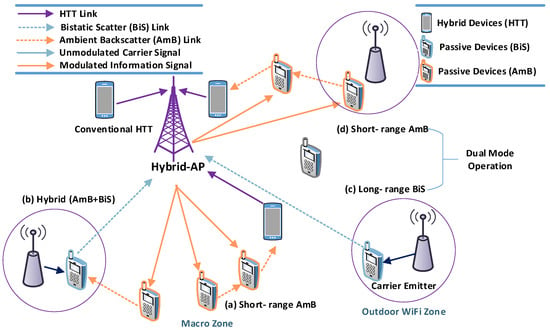
Figure 11.
Hybrid BackCom.
Discussion: We can summarize the above section by emphasizing various types of BackCom, based on different categorization as shown in Table 3. This table is divided into two categories, based on the dedication/non-dedication of the carrier signal source and based on the arrangement of the source and the reader. The main points are as follows.

Table 3.
Summary for Types of BackCom.
- The first category based on the usage of the dedicated source and reader, is known as “dedicated BackCom (Ded-BackCom)” [35]. This type is better suited for applications that need a dedicated power source for tags.
- Another type in the first category is “ambient BackCom (Amb-BackCom)” [12]. It does not require any dedicated source but utilizes radio signals available in the vicinity. Since ambient radio waves (such as TV signals, WiFi signals, cellular signals, etc.) are present everywhere, Amb-BackCom can revolutionize wireless communications by promoting battery-free communications.
- The second categorization of BackCom is based on the arrangement of source and reader. In BiS, the signal generator is dislocated from the reader to reduce the path loss [50]. This type of BackCom sends backscattered signals to a wide range compared to Ded-BackCom. This is because the carrier emitter approaches the tag. Moreover, signals received by the tag face less round trip path loss, and the backscattered signals travel far in comparison to dedicated or Amb-BackCom.
- Another type in the second category is based on the antenna arrangement of the source and the reader and is referred to as “monostatic BackCom (Mon-BackCom)” [39]. This is useful for tiny devices that cannot afford space for separate antennas in the transmitter or the receiver. However, Mon-BackCom can share the single antenna for both transmission and reception operations.
- The last type in the second category highlights “hybrid BackCom,” which was introduced to take advantage of both Amb-BackCom and Ded-BackCom [52].
4. BackCom: Signal Processing and Detection
This section covers signal processing aspects such as channel coding techniques, interference problems, and decoding schemes in BackCom. BackCom channel coding schemes are used to efficiently transmit data over wireless channels. The decoding techniques for backscattered signals and signal detection schemes including coherent and non-coherent detection are described in the following subsections, respectively.
4.1. BackCom Signal Processing Aspect
The signal processing component in BackCom considers carrier signals and backscattered signals. Carrier signals with a higher frequency are emitted from the transmitter and propagate towards passive tags. The passive tags reflect back the incoming signals with a lower frequency as compared to the carrier waves. Lu et al. discussed signal processing and BER performance analysis for Amb-BackCom [67]. Usually, in multi-tag communications, a large number of the passive nodes are unable to observe each other’s transmissions. Thus, enabling concurrent transmissions is one of the primary challenges in BackCom. Backscatter spike train (BST) addresses the concurrent transmissions problem [68]. BST allows the BackCom physical layer for concurrent transmissions from multiple tags with the help of intra-bit multiplexing of OOK signals. Similarly, the MOXcatter system is suggested for multiplexing using a spatial stream BackCom with off-the-shelf WiFi devices [69]. The coding techniques for accommodating a large amount of data on backscattered signals are elaborated below.
4.1.1. BackCom Coding
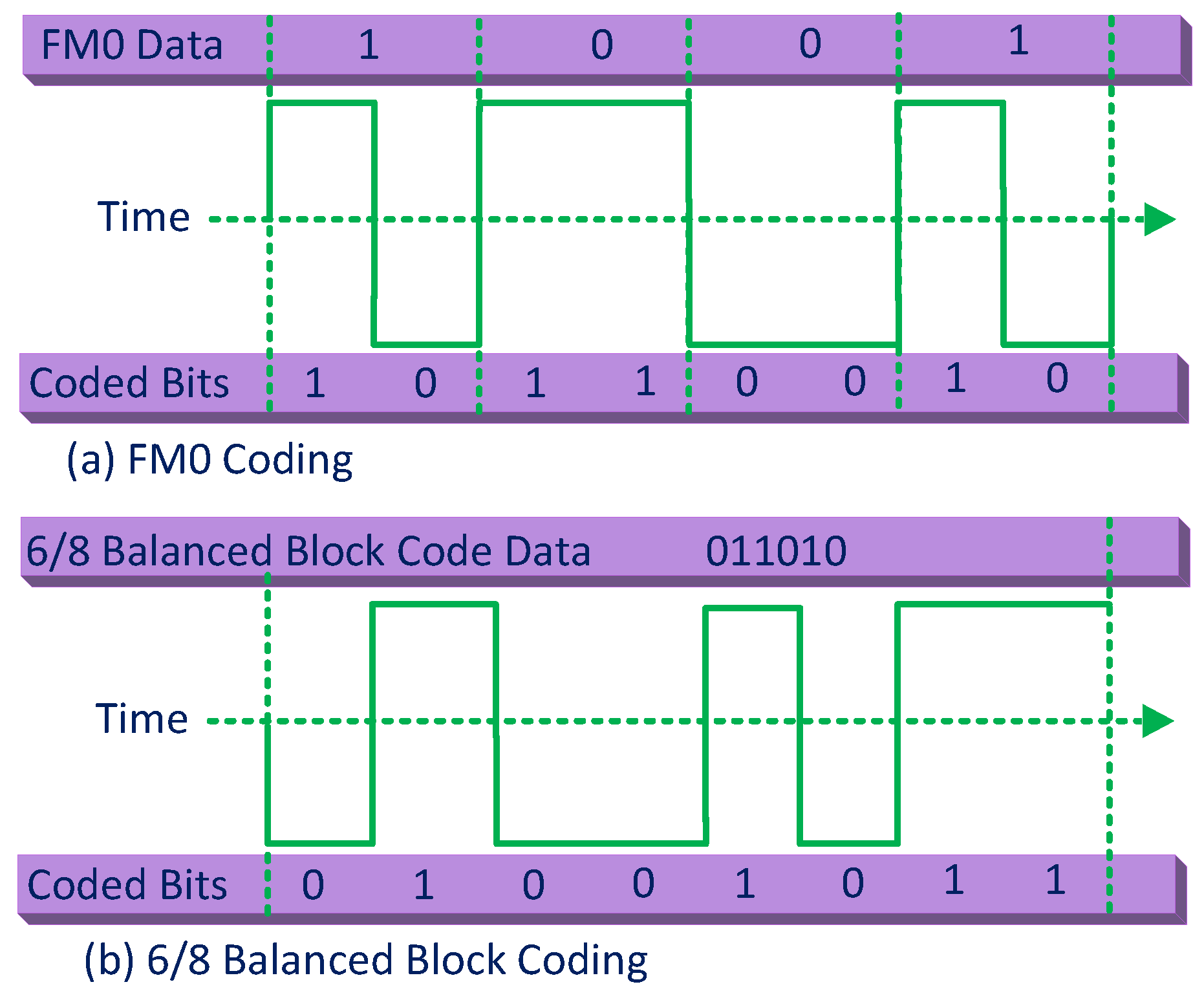
Similar to wirelessly powered communication, the data in BackCom is encoded with certain coding techniques before the start of transmission over RF channels. The purpose is to support the recovery of (lost) data across noisy channels. Channel coding is also performed for efficient transmission over wireless communication channels. Coding schemes proposed for a conventional wireless system not only consume a high amount of power but involve high computational complexity. Hence, these techniques are not suitable for low power passive devices. To standardize RFID BackCom encoding schemes, EPC Global provided the EPC Gen-2 communication protocol. This standard suggests two encoding schemes for backscatter base-band signals: (i) the Miller code and (ii) the bi-phase space (FM0) code.
Both of these channel codes have the highest transmission rate of one half [70]. However, to address the need for high data rates in BackCom, the improved rate channel codes employ a rate balanced block code for higher throughput [71]. Figure 12a shows the Gen-2 FM0 encoding and its corresponding code bits, whereas Figure 12b delineates a rate balanced block code and its relevant wave forms.
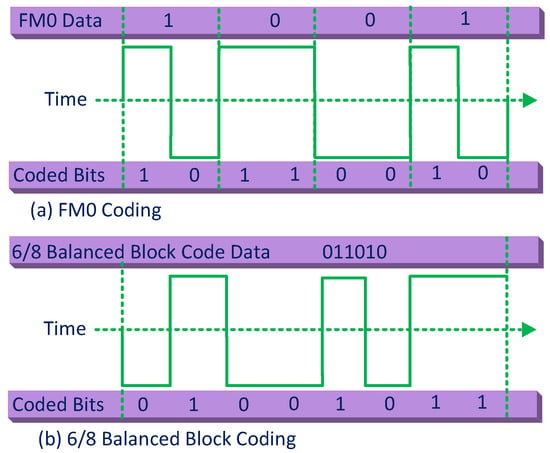
Figure 12.
Coding in BackCom.
Park et al. proposed a “microcode”-based mechanism for Amb-BackCom [32]. Microcode supports concurrent transmissions and has a longer transmission range compared to traditional Amb-BackCom. The authors suggest a coding technique by considering three states of tags response: (i) backscattered signals with the same phase; (ii) backscattered signals with an inverted phase; and (iii) no backscattered signals [72]. Likewise, short length cyclic error-correcting codes for the BiS network are employed to improve transmission rates [66]. Subsequently, short block length channel codes, with very low encoding complexity, are considered for BiS radio [73]. These channel codes can adopt bistatic scattering on large-scale, ultra-low price wireless sensor networks (WSNs). Meanwhile, the coupled usage of coding and the modulation of energy shows better results for energy harvesting in BackCom [74]. Cnaan et al. proposed run-length limited codes for the backscatter system, which were used for a reduction in self-interference and an improvement in data rates [75]. After coding, the backscattered signals were sent to the reader via transmission channels. These channels added noise and interference due to the presence of similar signals. The next section focuses on the interference component of BackCom.
4.1.2. Interference in BackCom
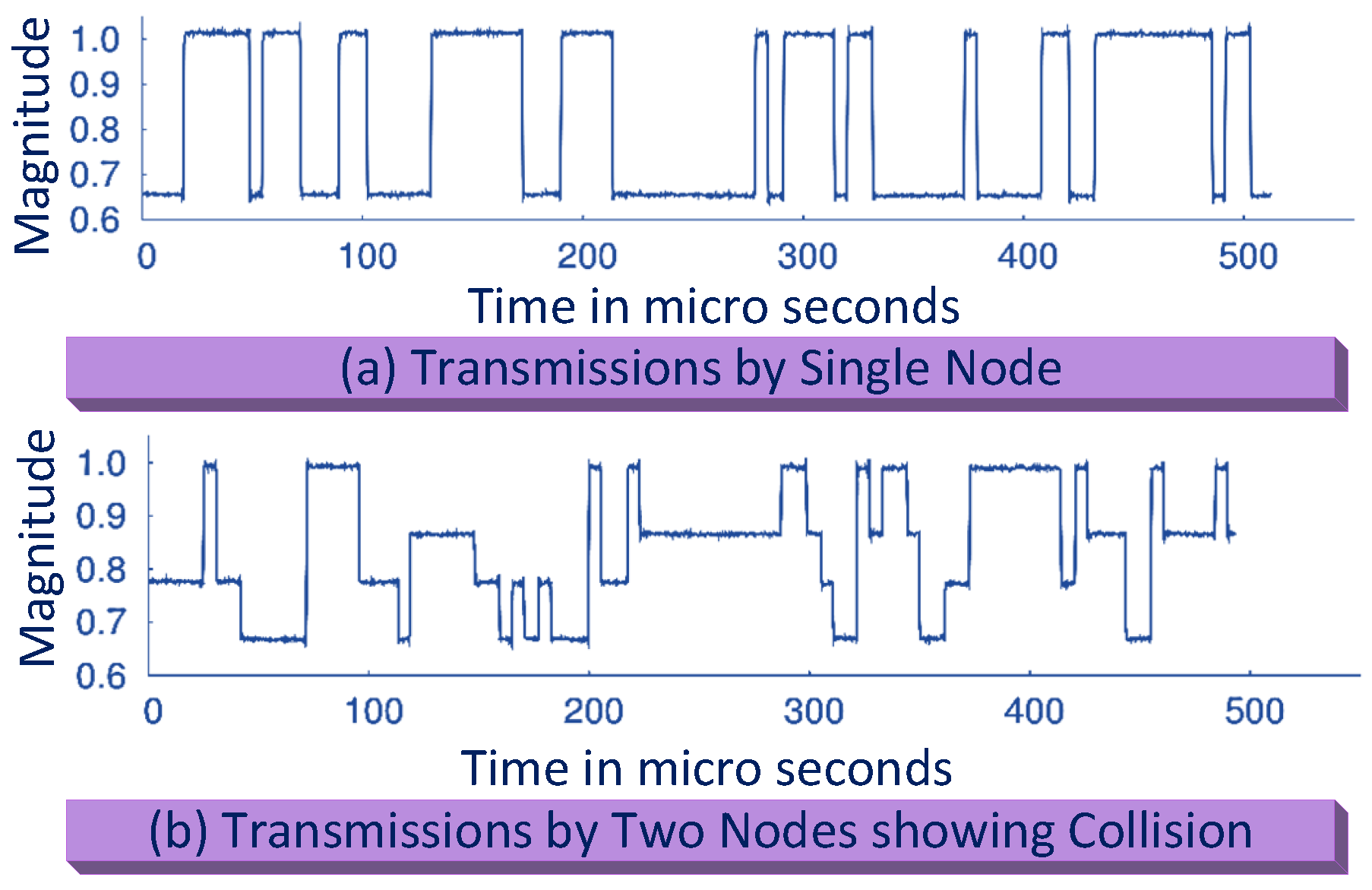
BackCom tags could be embedded into everyday objects of IoT with next-generation 5G networks, thus raising the connectivity of smart objects with ubiquitous networks based on ultra-low power consumption. The primary challenge associated in accomplishing ultra-low power communication is the high reliability and efficiency of communication between BackCom tags. However, nodes in BackCom systems are not able to sense each other’s transmissions, thus suffering from collisions and interference. Figure 13 shows signal levels with and without collisions. In Figure 13a, the transmission is shown by a single node. Signals have two levels of magnitude and could be distinguished as “0” and “1.” Figure 13b delineates the collision between the signals of two nodes. The received signal has four levels of magnitude corresponding to “00,” “01,” “10,” and “11.” To address the collision problem, a communication system named “Buzz” was proposed by Wang et al. [59]. Buzz handles all the BackCom tags as one virtual sender. Buzz also treats collisions as code across all the bits, transmitted by nodes. In this way, Buzz allows only a small number of nodes to have collisions at a time. Moreover, the authors made collisions to act like a sparse code that could be decoded by a customized sensing algorithm.
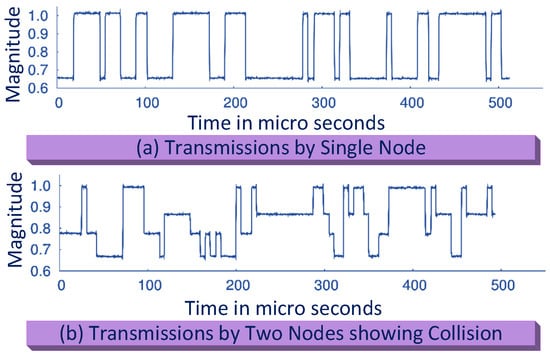
Figure 13.
Interference in BackCom.
Kim et al. suggest anti-collision algorithms for BackCom based on bit collision detection for the FM0 code and miller sub-carrier sequence [76]. Throughput of the suggested algorithms is greater than the conventional binary tree algorithm.
The work in [77] addresses the interference issue in BackCom by proposing a full-duplex BackCom network design. To reduce in-band full-duplex (IBFD) self-interference, a remote device was proposed, and this device could communicate over the same frequency band as in IBFD communication [78]. “Near-far” is a problem in wireless communications in which a receiver catches high power signals, making it difficult for the receiver to detect low power signals [79]. Similarly, “doubly near-far” is a condition observed in energy harvesting networks [54], where the devices closer to the access point harvest more energy in the downlink and require less power to achieve the given SNR. Therefore, this condition allow devices far from the access point to harvest less energy, but the devices require high power to obtain the targeted SNR [80].
To compensate the path loss in mm-wave BackCom, a power efficient solution was proposed [81]. This solution allows one to equip tags with retro-directive arrays that have a maximum reflection gain direction of incidence. Bletsas et al. discussed sensor collisions (interference) in the backscattered network and elaborated on the feasibility of anti-collision performance in high-density backscatter sensor networks [82]. Moreover, the results show that the performance of backscatter sensor networks depends on the modulation scheme used at each sensor node. In addition, the interference and noise generated from surrounding nodes and wireless communication channels, respectively, render the backscattered signals weaker at the receiver end. Therefore, the task of the BackCom decoder is to decode the information from the low power backscatter signals.
4.1.3. BackCom Decoding
It is a challenging task to obtain transmitted data from small power signals. However, there are various proposed decoding techniques for BackCom to extract information from weaker reflected signals. Alevizos et al. designed a composite hypothesis testing decoding rule for non-coherent channel-coded BiS radio tags [73]. A multi-antenna decoding scheme that does not require channel estimation was proposed [32], and it could be implemented using standard analog components. This decoding type is referred to as “mo” (MicroMo) decoding, as shown in Figure 14. The dual-antenna MicroMo receiver (Alice) could decode Bob’s backscattered information. Moreover, backscattered signals can be separated from direct TV transmissions. The best part of this decoding scheme is that it accomplishes all tasks without any channel estimation or digital computation. Furthermore, the BiGroup decoding technique allows parallel decoding of commodity off-the-shelf (COTS) RFID tags. It can also address high tag collisions in BackCom networks [83]. Usually, the decoding of information depends on the detection of signals. Once signals are detected, they can be compared to a certain threshold level to decide the desired bit. Let us now discuss the signal detection schemes for BackCom.
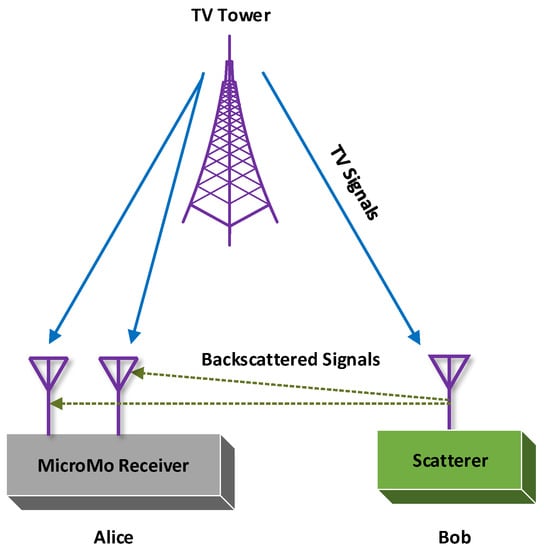
Figure 14.
mo decoding in BackCom.
4.2. Signal Detection in BackCom
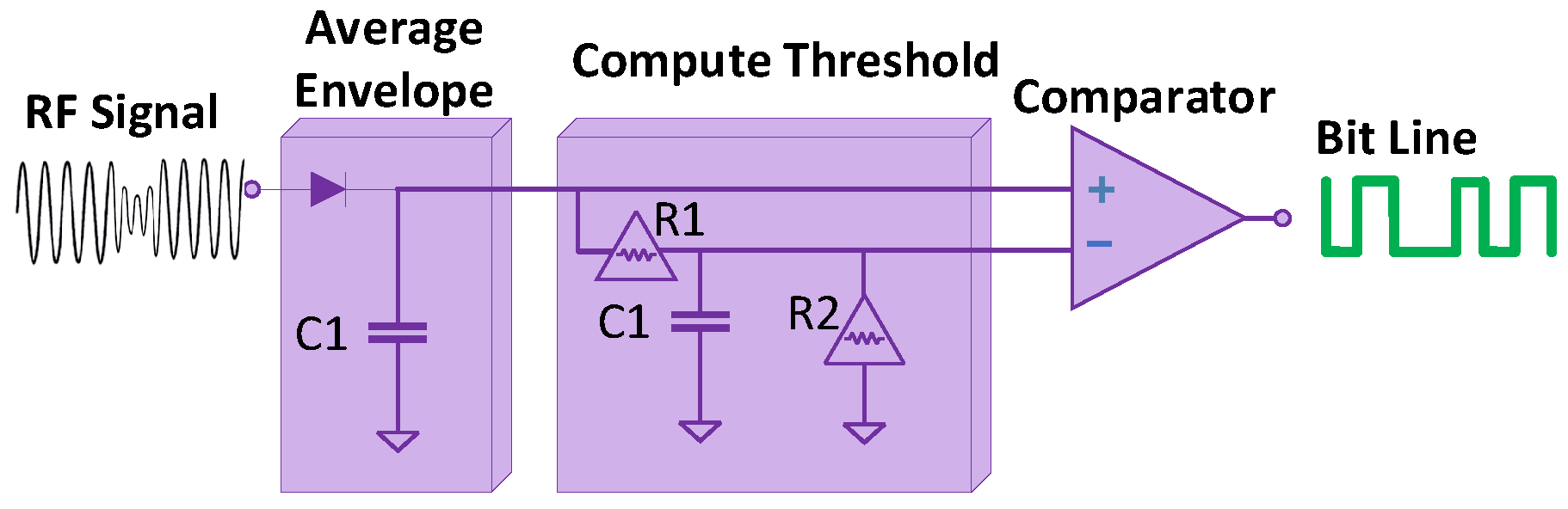
Signal detection has a vital role in BackCom receivers. The received signals by BackCom readers are degraded mainly due to noise, interference, attenuation, and very low frequency, as compared to carrier signals. Considering the degraded signals, some threshold levels need to be fixed for understanding the desired variations of signals. These thresholds are decided by averaging two voltage levels and can be done by a comparator [12]. However, if the resultant of the input signals is higher than the threshold level, (first voltage) can be decided. Moreover, if the result of averaging is less than the threshold level, (second voltage) is considered [12]. Authors further proposed a resistive/capacitive (RC) circuit to average the variation in TV signals, as shown in Figure 15. The circuit diagram has two stages: (i) an envelope detection and averaging stage and (ii) a compute threshold stage. The envelope detection and averaging stage generates an average envelope of the signal, whereas the compute threshold stage compares the averaged signal with the certain threshold level. BackCom receivers’ detection sensitivity is also one of the main challenges in passive device communications. Parks et al. increased the detection sensitivity of a receiver by increasing the transmit signal time duration [32]. Let us now discuss methods of detection of signals. One way includes the phase information, while the other does not need any. These are discussed below:
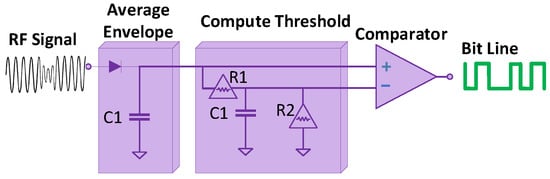
Figure 15.
Signal detection in BackCom.
4.2.1. Coherent Detection
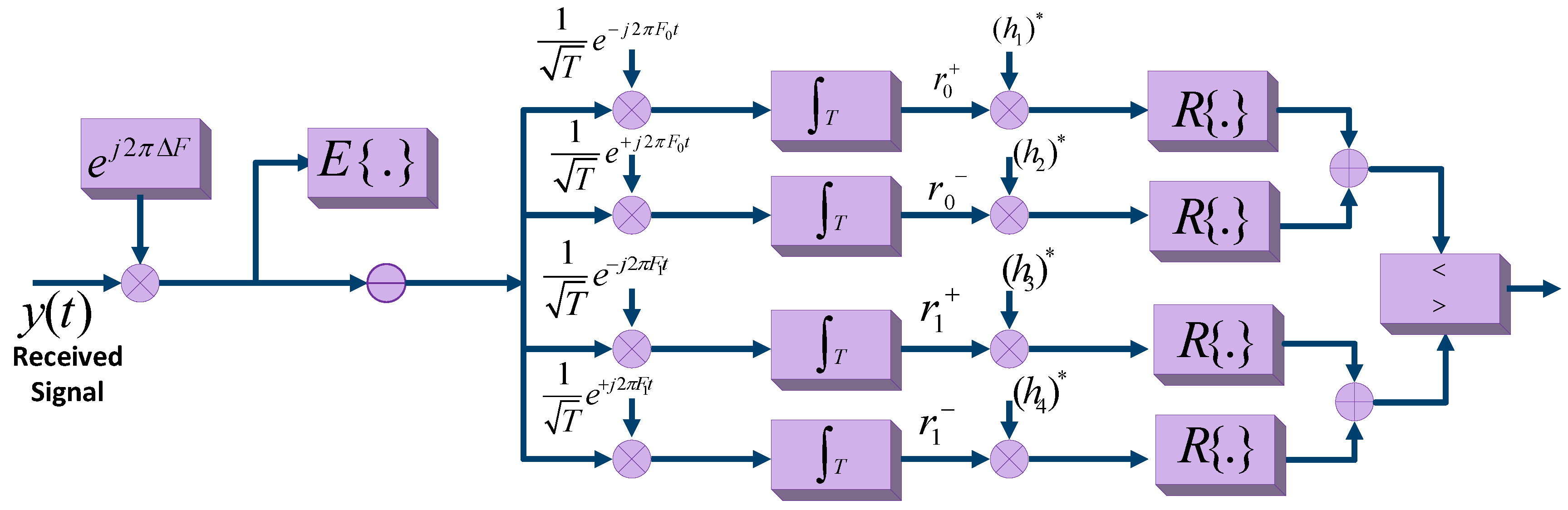
This detection technique considers the phase information of the signals while detecting signals. The phase information can be extracted from the nearby source of carrier waves, due to less attenuation and other signal degradation parameters. Hence, coherent detection can effectively be employed in the BiS setup of BackCom. A coherent receiver for BiS radio was proposed to employ a bistatic coherent uncoded reception scheme [66]. This type of detection works by separating a carrier emitter from the receiver. However, in a bistatic setup, the coherent reception is difficult for three unknown channel links. These links are between carrier-emitter and reader, carrier-emitter and tag, and tag and reader. The reception also depends on many new parameters related to scattering radio. Figure 16 exhibits the design of the coherent correlation receiver with four correlators. This work assumes that channel state information is available with equiprobable transmitted bits [66]. h denotes the maximum likelihood estimate of the channel, shows the received signals at the backscatter receiver, and and represent two orthogonal frequencies exponential of the received signal. The complex vector is base band equivalent of the received signal for duration T of a single bit. However, obtaining the phase information is very difficult in some cases. The detection of signals without considering phase information is discussed next.
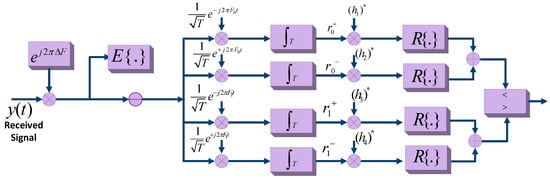
Figure 16.
The Structure of Coherent Correlation Receiver with Four Correlators and Two Pairs of Complex Channel Gains.
4.2.2. Non-Coherent Detection
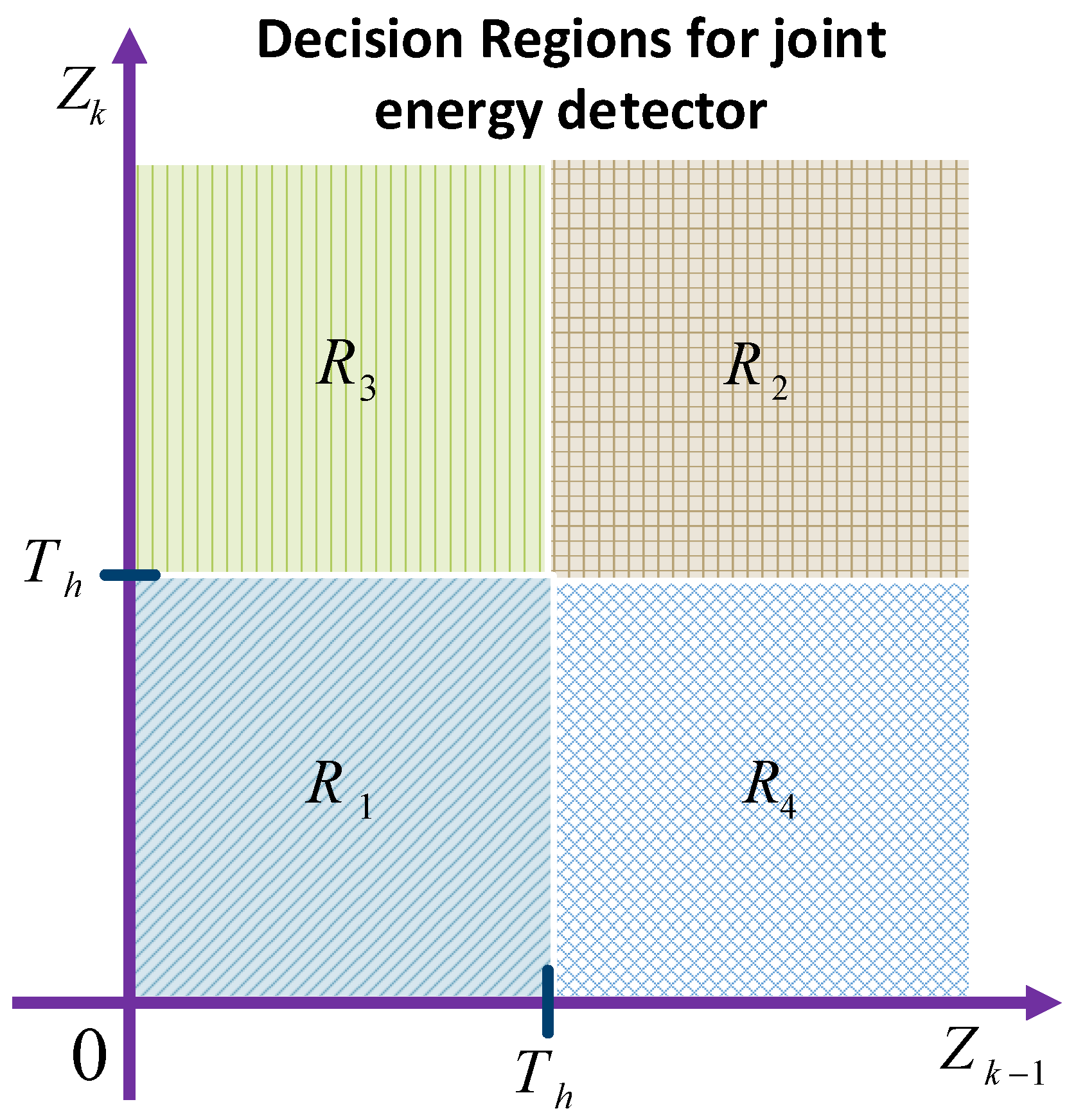
Non-coherent detection in BackCom does not need phase information for the detection of signals. Therefore, this detection technique can be used in different scenarios in which phase information cannot be extracted easily. Quan et al. studied the fundamentals of various aspects of non-coherent Amb-BackCom systems [84]. They utilized the joint probability distribution function (PDF) of the received signals for the computation of the maximum likelihood detector. Figure 17 shows the decision regions for the non-coherent joint energy detector, which has four decision regions: –. The notation and are notations referred to below as signal energies, and is considered the detection threshold.
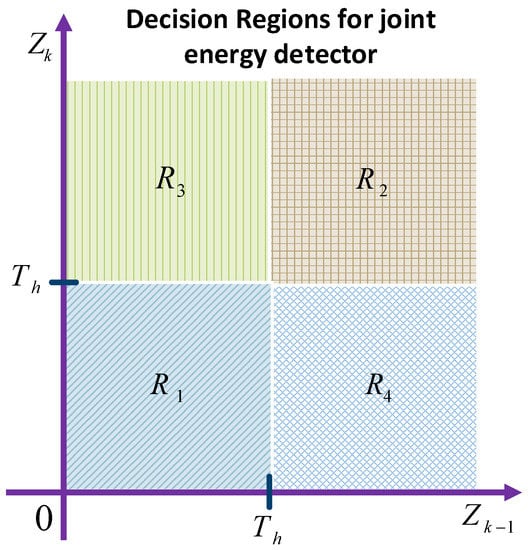
Figure 17.
Non-Coherent Detection for BackCom.
- Decision Region would be selected if and , and the symbol sent by the tag would be decided as .
- Decision Region would be selected if and , and the symbol sent by the tag would be decided as .
- Decision Region would be selected if and , and the symbol sent by the tag would be decided as .
- Decision Region would be selected if and , and the symbol sent by the tag would be decided as .
The detection schemes for Amb-BackCom are highlighted next. Wang et al. considered a transmission model for signal detection in Amb-BackCom [65]. The authors designed an algorithm to derive two closed-form detection thresholds. Similarly, another algorithm based on the detection of three states of backscattered signals considered a positive phase backscatter, a negative phase backscatter, and non-backscattered signals for Amb-BackCom [72]. Later, a joint-energy detector was designed to derive detection thresholds for Amb-BackCom signals [84]. This work also suggested a simple blind method for the practical implementation of detectors to obtain necessary parameters. Guo et al. solved the issue of the error floor in conventional energy detection created by the direct link interference in BackCom [85]. Moreover, they proposed a likelihood ratio dependent detector and a beamforming assisted energy detector for BackCom symbol detection, in the presence of channel state information. Likewise, the problem of uplink detection for the Amb-BackCom system was considered in a one-reader–one-tag scenario [67]. Theoretical models for two detectors were designed to address the problem of uplink detection. One detector obtains a minimum BER, while the other attains equal BER in detecting “0” and “1.” Meanwhile, the thresholds are derived for both detectors in addition to similar BER expressions.
Signal detection for Amb-BackCom is focused on examining the corresponding BER performance [86]. Authors formulated a theoretical system model to design a data detection approach with channel state information (CSI). Similarly, a flicker detector uses per symbol in-band BackCom while using a residual channel of WiFi packets [87]. Tao et al. suggested a semi-coherent manchester detector and a non-coherent manchester detector [88]. These detectors could decode the manchester-coded and differential manchester-coded information, respectively. Later, the signal detection problem in the cooperative receiver was addressed for Amb-BackCom. The recovery of signals from ambient devices in addition to RF sources is shown in [89].
Qian et al. solved the signal detection problem with differential modulation for the Amb-BackCom system [90]. They designed a suboptimal detector by integrating an approximate threshold for detection and derived relative BER expressions. Similarly, the detection of BiS was proposed to improve the BER performance in comparison to earlier BiS radio receivers [66]. The non-coherent channel coding was incorporated within a BiS radio framework [73]. The receivers in this framework have less computational complexity as compared to maximum likelihood (ML) coherent receivers, and the corresponding BER results were obtained and compared to their coherent counterparts. Subsequently, a transmission model was formulated while considering multiple antennas in the reader [91]. They also proposed a different method of signal detection in the absence of CSI.
Discussion:Table 4 summarizes Section 4, which covers coding, interference, decoding, and signal detection schemes in BackCom. Moreover, various techniques for channel coding are discussed. The primary purpose of these coding schemes is to enhance the reliability, throughput, and range of backscattered signals. The key points are discussed below:

Table 4.
Summary of signal processing and signal detection.
- The standard coding scheme in BackCom employs FM0 and the Miller code, which has a maximum rate of one half [70]. In other words, each information bit adds one additional bit for redundancy, before transmitting data to the wireless channel. This technique provides redundancy to the data, at the cost of a significant bandwidth. Hence, these types of codes are beneficial in large bandwidth scenarios.
- An improved-rate channel block codes for Amb-BackCom are suggested to address the need for high data rates in limited bandwidth scenarios [71].
- The renowned cyclic error correcting codes, with short length, are preferred to improve throughput when the carrier emitter is far from the reader [66].
- Another way to improve the communication range in BackCom is to enable concurrent transmissions instead of serial transmissions. This type of scenario is suitable for tags and readers with multiple antennas. Moreover, Microcode and BST focus on simultaneous transmissions of data for BackCom [32,68], whereas concurrent transmissions require multiple antennas, which consequently require more space.
- The BackCom data rate can be enhanced by utilizing the phase information of backscattered signals: negative phase, positive phase, or no backscattering [72]. This technique is preferred when there is no available phase information.
- Coding and modulation can be used together, for acquiring a high data rate and an extended range, at the cost of higher complexity [74].
- The detection techniques were analyzed to observe variations with particular receivers. A distinct detector is suggested if received signals are obtained from multiple antenna tag receivers [91].
- Coherent detection is preferable in a bistatic setup due to the availability of phase information by the near carrier emitter [66].
- Non-coherent detectors are preferred for scenarios such as Amb-BackCom, as the phase information of backscattered signals is hard to identify [84].
- For optimal detection, an ML detector is chosen and can be utilized as the reference to establish other optimal detectors [65].
Let us now consider communication modes, modulation schemes, and multiple access techniques in the upcoming section to accommodate more tags.
5. BackCom: Wireless Communications
Table 5 highlights three significant parts of this section. First, we focus on communication modes for BackCom signals. Next, we explore various modulation techniques for backscattered signals. Finally, multiple access techniques for BackCom are explained.

Table 5.
BackCom: wireless communications.
5.1. BackCom Communication Modes
Like traditional wireless communications, BackCom also has two communication modes: (i) a full-duplex mode used in two-way communications between tag and reader and (ii) a half-duplex mode that allows only one-way communication. Both modes are discussed below:
5.1.1. Full-Duplex BackCom
Full-duplex communication mode is widely used in BackCom and Wireless Powered Communication Networks (WPCNs). The WPCN with a full-duplex hybrid (energy and information) access point is considered to enable energy harvesting capabilities for wireless users [92]. Moreover, dual antennas are used in H-AP for operation in full-duplex mode. While the first antenna broadcasts wireless energy to users in the downlink, the other antenna receives data using time division multiple access in the uplink. Ensworth et al. presented the first demonstration of a monostatic full-duplex BackCom system that considers the carrier source co-located with a commercial Bluetooth chipset [97]. This system allows for the transmission of information from specially designed Bluetooth low energy (BLE) backscatter tags to a commercial Bluetooth chipset, without any software modifications.
A full-duplex scheme for Amb-BackCom devices is considered to relay the information [93]. The relay node can send its information, while receiving signals from the source node. Jain et al. designed a full-duplex radio that uses balun cancellation, a signal inversion, and an adaptive cancellation technique [107]. The circuits of balun cancellation can tune their cancellation circuits in variable environments. A full-duplex BackCom network to address the interference problem was suggested in [77]. This network considers a multi-access design for time hopping spread spectrum. It allows a coexisting reader-tag link to set up a one-way wireless energy transfer and dual-way wireless information exchange.
A full-duplex BackCom system for wireless communication systems, namely “ReflectFX,” was proposed by Smida et al. [108]. ReflectFX prevents self-interference in half and full-duplex modes. Moreover, it allows backscatter nodes to reuse interfering received carrier signals for the transmission of data. Likewise, IBFD wireless communications utilize a full-duplex mode on the same frequency band for wireless terminals to transmit and receive information [78]. Previously, network designers were unable to attain a full-duplex feedback channel on battery-less devices. However, the usefulness of the full-duplex feedback channel is demonstrated in [94]. This channel can facilitate a network layer and link layer mechanisms to improve BackCom performance. Optimal policies for time allocation in full-duplex, backscattered assisted wirelessly powered communications networks (BAWPCNs) were achieved to maximize the throughput of the BackCom system [95].
5.1.2. Half-Duplex BackCom
Half-duplex mode in BackCom considers data to be transmitted one way at a time. This mode requires less energy than the counterpart, due to the single way transmission at an instant. Lyu et al. suggested the optimal policies for time allocation in the half-duplex BAWPCN to maximize the system throughput [95]. The half-duplex mode of communication was also used in BackCom for relaying and for extension of the communication range [109]. The data rate of the half-duplex BackCom is lower than the full-duplex mode due to one-way communication on the same frequency spectrum. This is the reason that the half-duplex mode was used only in bandwidth constraint applications, with a low data rate requirement.
Discussion:Table 6 summarizes the communication modes. Both communication modes of BackCom have importance in different applications. However, the full-duplex mode is widely used, due to the advantage of dual way communications. The usage of both methods in various scenarios is enumerated below:

Table 6.
Summary of communication modes in BackCom.
- Full-duplex mode of BackCom is used in multiple access [77], in-band communication [78], H-AP [92], relaying [93], and feedback channels [94].
- The simultaneous transmission and reception are supported in full-duplex mode. This enables the concurrent reception of energy while transmitting data [93]. Moreover, this feature of simultaneous transmissions and reception enhances the data rate compared to the half-duplex mode.
- The half-duplex mode of transmission has the benefits of lower energy consumption and low bandwidth utilization [109].
5.2. BackCom Modulation Techniques
Different amplitude modulation (AM) and frequency modulation (FM) techniques for backscattered signals have been proposed for efficient data transmission. AM techniques include OOK, differential modulation, and quadrature amplitude modulation (QAM). Frequency shift keying (FSK), Gaussian frequency shift keying (GFSK), and frequency shifting techniques are among FM techniques.
5.2.1. Amplitude Modulation in BackCom
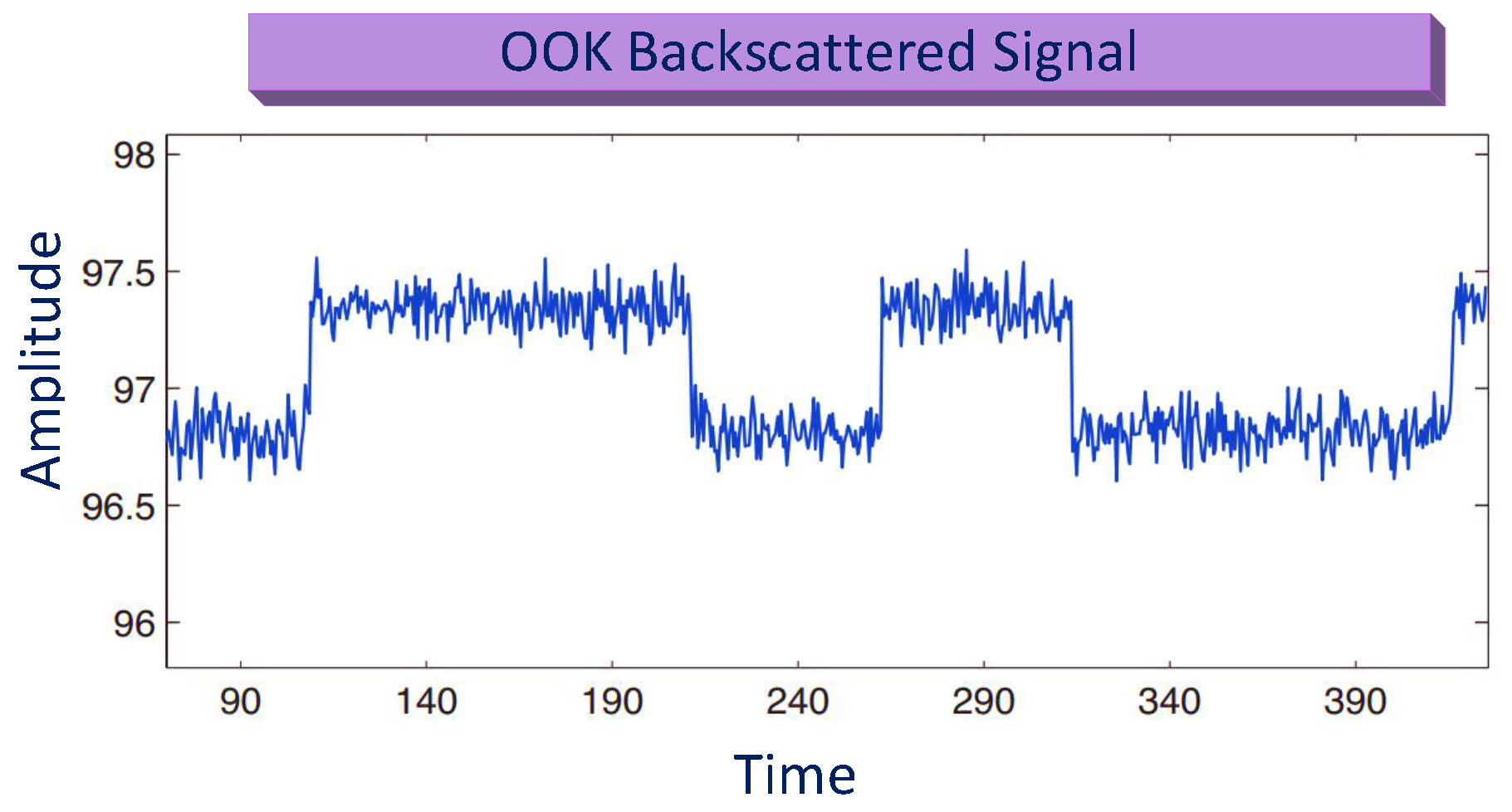
The simple type of AM that is based on amplitude shift keying (ASK) is OOK. It shows binary data in the absence or presence of carrier signals. The waveform of the OOK backscattered signals is delineated in Figure 18, showing the fluctuation in magnitude, corresponding to 0 and 1. Similarly, OOK in AM is used with BiS to increase the range in BackCom [50]. Thomas et al. showed that the phase could be modulated in addition to AM [98].
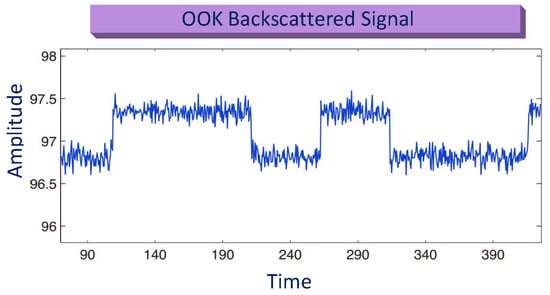
Figure 18.
Amplitude modulation for BackCom.
Figure 19 depicts a block diagram of an ASK and phase shift keying (PSK) modulator, consisting of two blocks. Load impedance , in the first block, causes the reflection of signals after the modulation of data with the help of an switch. A power rectifier in the second block supply constant power to the tag. Similarly, forward link demodulation in the second block detects incoming signals to extract the information with the help of logic and memory of the tag. Furthermore, a simple linear model for simulation of the complex reflection coefficient for RFID tags is considered based on an equivalent circuit diagram [110]. This model can further be utilized in derivations, to elaborate modulation by tags. Qian et al. utilized M-PSK modulation with Amb-BackCom and derived equations for an optimal multi-level energy detector [111]. Likewise, a 4-PAM modulation scheme for Amb-BackCom was suggested for ultra-low power devices [112]. The quantization index modulation technique was presented for Amb-BackCom [113]. This technique embeds messages into wireless signals.
Figure 19.
An amplitude shift keying (ASK) or phase shift keying (PSK) modulator for BackCom.
5.2.2. Frequency Modulation in BackCom
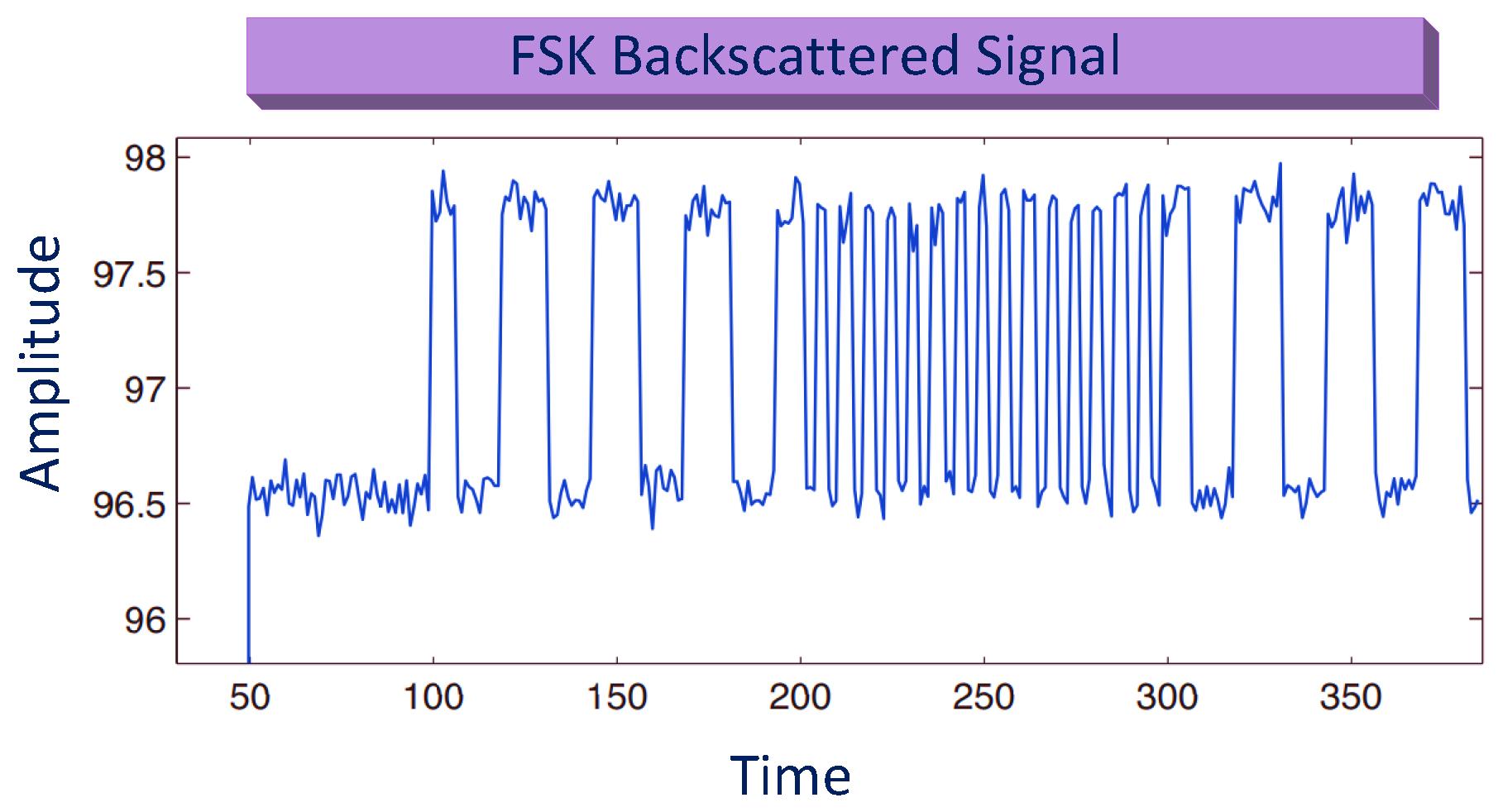
FM is used to modify the frequency of carrier signals according to the data present in information signals. This technique helps to carry information to remote receivers by extending the communication range of BackCom having the least interference. Similarly, FSK modulation was proposed to extend the communication range of the coherent receiver in the BiS radio channel [66]. The signal representation of FSK backscattered signals is shown in Figure 20. Kimionis et al. demonstrated experimentally that FSK could increase coverage in BiS configuration [50].
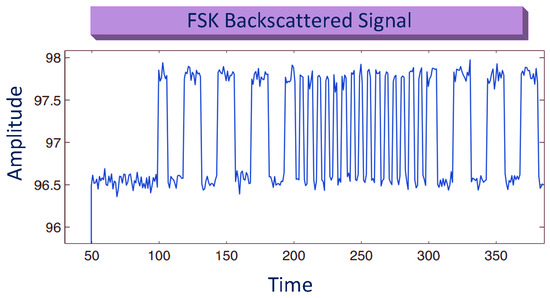
Figure 20.
Frequency shift keying (FSK) for BackCom.
Similarly, ambient FM radio waves could be utilized as the signal source for BackCom [96]. This scheme enables BackCom transmissions to be decoded by any FM receiver available in smartphones or cars. The key innovation of this idea is the modulation technique. This technique can transform RF signals to backscattered signals, with simple multiplication operation on RF signals and an additional operation on audio signals output by the FM receiver. Yang et al. discussed the BackCom design for ambient OFDM carrier signals available in the environment [114]. They further developed a system model for spread spectrum modulation. Darsena et al. proved through analysis that the BackCom system can transmit a single symbol per OFDM symbol of the traditional wireless system, and this system can attain better data rates over small distances [115]. However, the desired recipient of backscatter signals is considered to be co-located with the traditional transmitter (lying on the same device).
5.2.3. Gaussian Frequency Shift Keying in BackCom
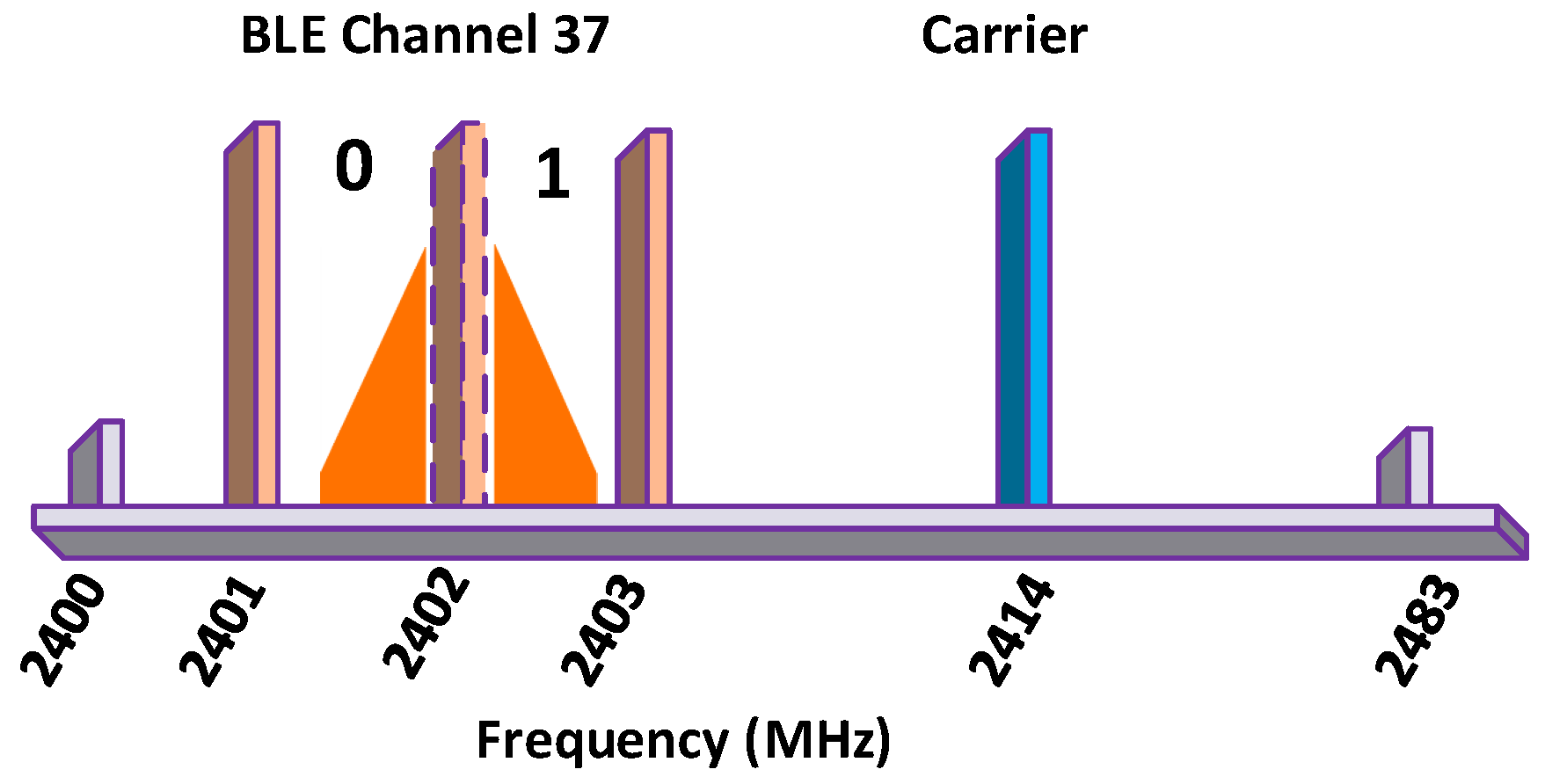
GFSK uses the Gaussian-shaped frequency shifting technique to modulate information in BackCom. GFSK is considered for modulation, in a monostatic full-duplex Bluetooth Low Energy (BLE) compatible BackCom system, for mobile devices [97]. BLE utilizes a 1 Mbps Gaussian-shaped binary shift keying modulation technique. The positive frequency deviation of more than 185 kHz above the channel’s center frequency represents “1” bit, while a negative frequency deviation of more than 185 kHz shows a “0” bit in each of the 40 BLE channels. Figure 21 delineates the frequency plan for creating BLE-compatible backscatter messages. Usually, BLE backscatter tags are made to reflect carrier signals in a manner whereby the resulting sub-carriers contain frequency components within a particular choice of BLE channel.
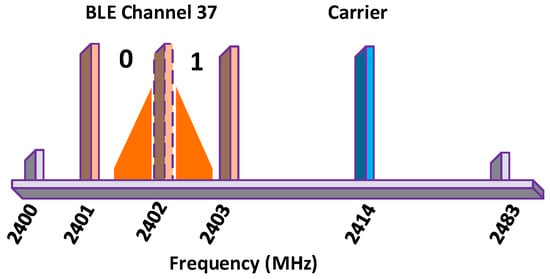
Figure 21.
GFSK: frequency plan for creating BLE-compatible backscatter messages.
5.2.4. Differential Modulation in BackCom
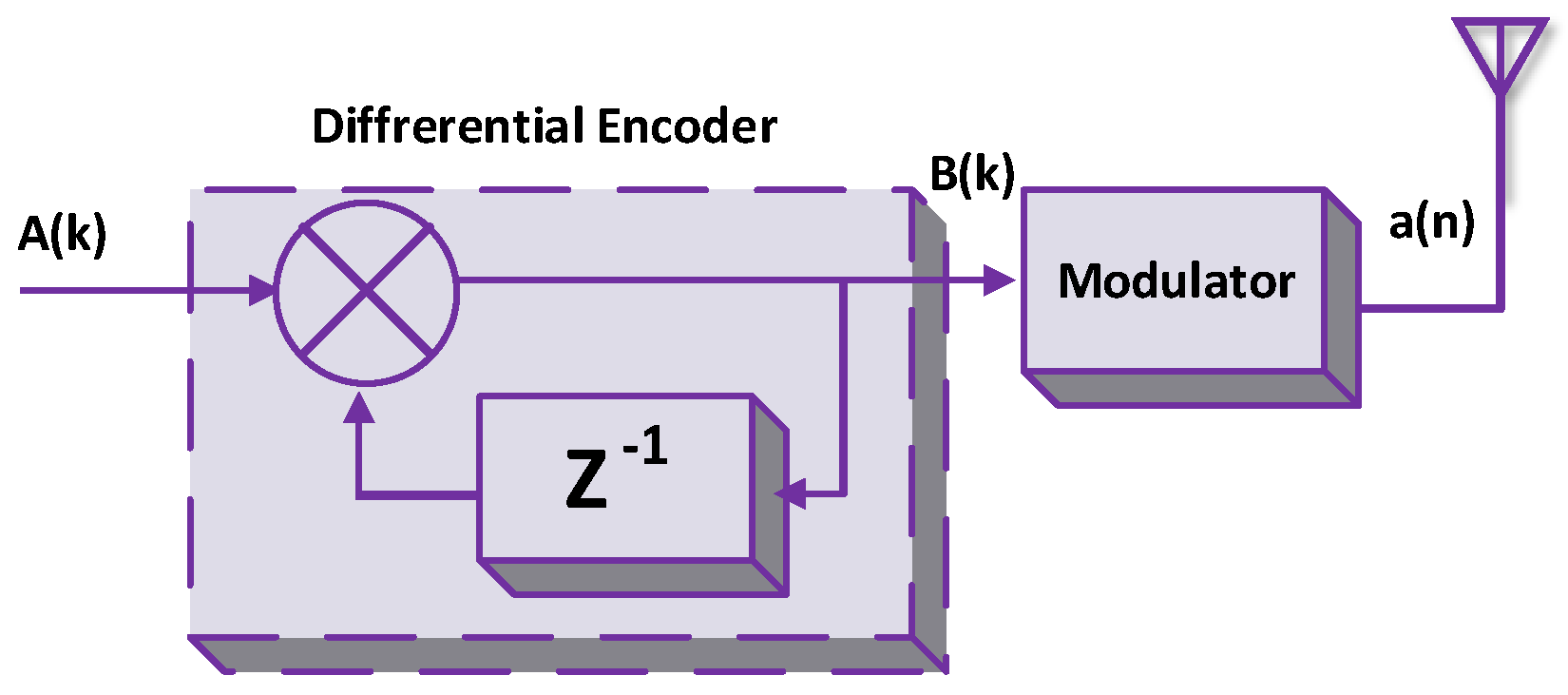
This modulation technique considers the difference between current and previous signal elements (such as amplitude) to generate modulated signals. Differential modulation has two parts: (i) a differential encoder and (ii) a modulator. The differential encoder can be referred to as the feedback system. Figure 22 depicts the differential encoder for the backscatter tag. Multiple signals are inserted into the differential encoder to output signals. signals have the effects of current and previous signals at different instants of time. signals are further sent to the modulator to obtain modulated signals . Moreover, Qian et al. used differential modulation to address the signal detection problem of Amb-BackCom [90].
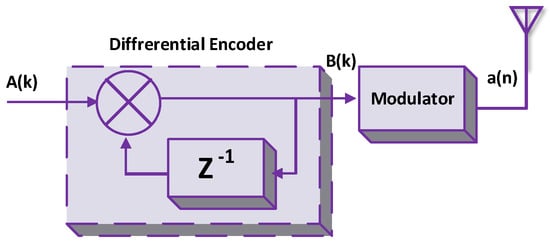
Figure 22.
Differential encoder for a passive tag.
5.2.5. Quadrature Amplitude Modulation in BackCom
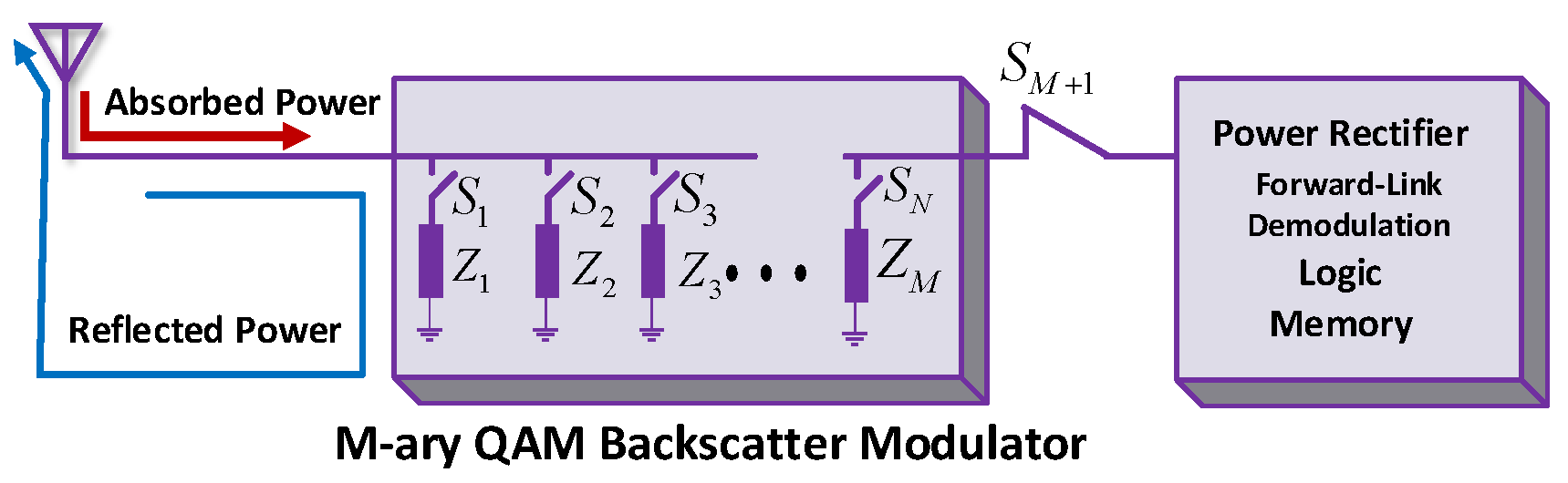
QAM is a technique that combines two amplitude-modulated signals to double the effective bandwidth. Figure 23 illustrates the block diagram of QAM in BackCom. The notations show the M number of load impedance to backscatter signals, and represent the number of switches. The QAM modulation has the advantage of considering no on-chip inductors [98]. Tags in QAM can send higher than one data bit in each symbol period, permitting tag makers to use low power on-chip oscillators. QAM maintains data throughput equal to ASK or PSK by using a frequency equal to the symbol rate. Correia et al. suggested a dual band 4-QAM Amb-BackCom circuit for modulation that utilizes a dual-band Wilkinson power divider in addition to a modulator made up of two transistors [116]. This circuit consumes 27 nW of power for a 500 kbps data rate.
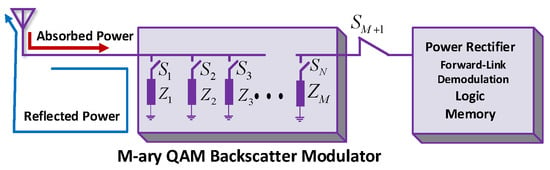
Figure 23.
Quadrature amplitude modulation (QAM) in BackCom.
Discussion:Table 7 gives a summary of modulation techniques used in BackCom. The key conclusions are as follows:

Table 7.
Summary of modulation techniques for BackCom.
- The AM technique, based on OOK, improves the communication range in BiS [50].
- Differential modulation can be used in Amb-BackCom systems for signal detection [90].
- QAM is used to double the effective bandwidth [95].
- Frequency modulation utilizes FSK and GFSK to extend the communication range by changing the frequency to the Bluetooth spectrum [97].
5.3. Multiple Access Techniques for BackCom
Various multiple access techniques are used to adjust for a greater number of users at the same time. The method includes multiple access based on time division, code division, and frequency division [68,99,100,101,105]. Figure 24 depicts the basic concept of multiple access schemes, demonstrating multiple-tag backscattering carrier signals to a single reader.
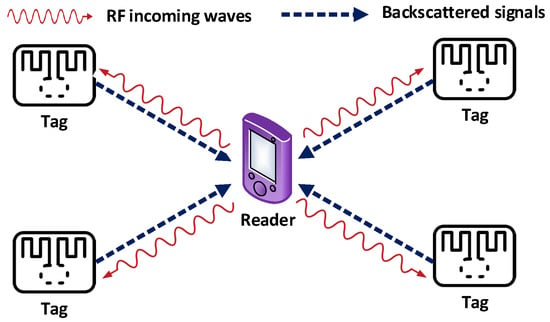
Figure 24.
Multiple access in BackCom.
5.3.1. Time Division Multiple Access
TDMA-based multiple access scenario for BackCom considers the transmission of signals to many users via wireless access point (AP) [100]. This scenario enables tags to harvest energy first, and harvested energy is then used to backscatter signals received from wireless AP. Ju et al. used TDMA to uplink data from two users [99]. These two distributed users harvested energy in the downlink broadcasted by the H-AP, while TDMA was used in the data uplink to transmit users’ data individually. A multiple access technique was used in BST to show a sequence of edges in time [68]. BST is a physical layer scheme for BackCom networks, which enables concurrent transmissions from multiple devices by leveraging temporary interleaved signal edges. Furthermore, BST works on OOK signals received from various tags.
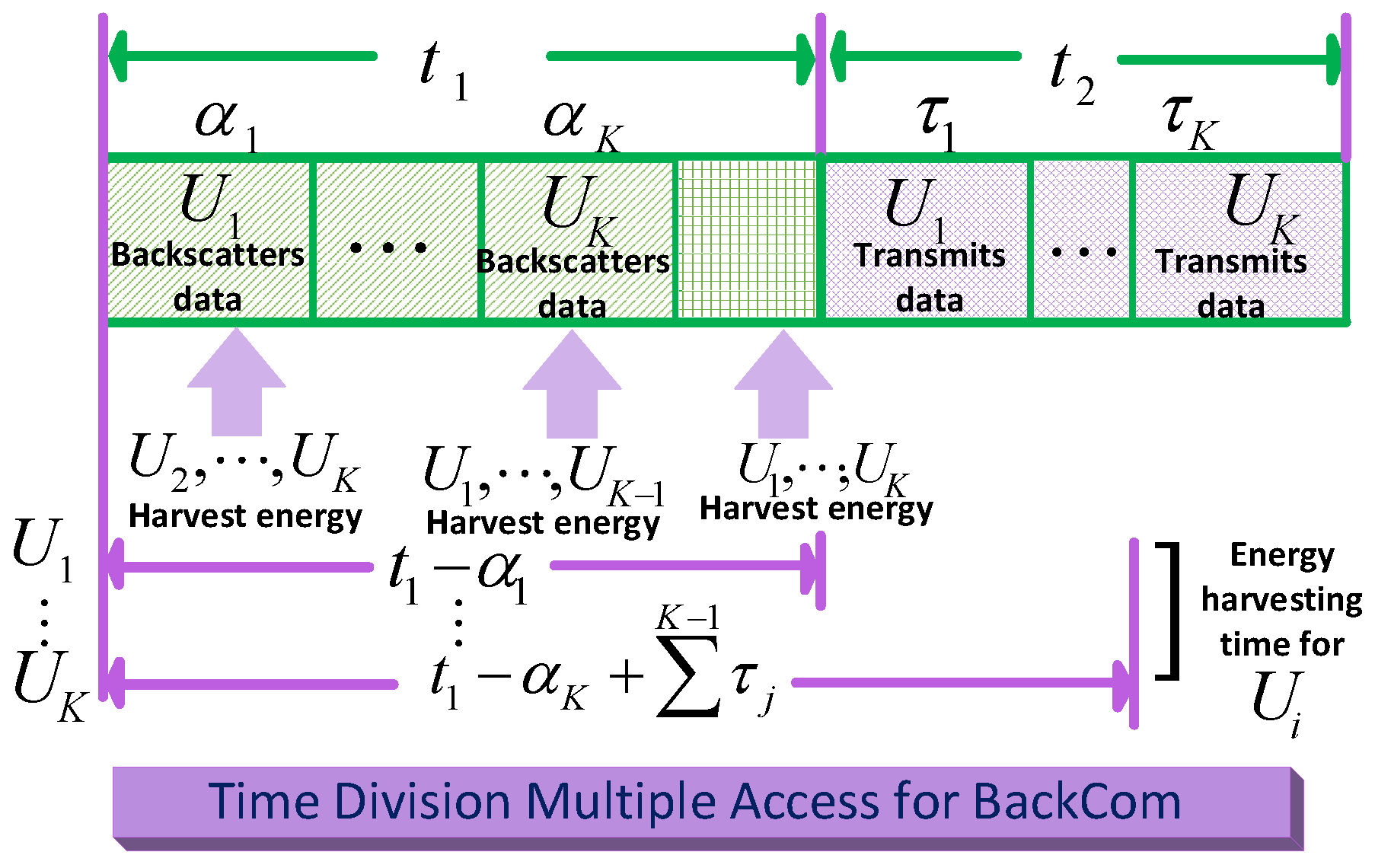
As shown in Figure 25, a model based on the bifurcation of the time block was proposed to have two segments: (i) the data backscattering segment and (ii) the transmission period [101]. The first time segment is used for data backscattering in BackCom mode, while the other segment considers energy harvesting. TDMA is employed in data transmission and data backscattering periods. Subsequently, to improve system throughput, some users harvest energy from the power station, while others reflect/backscatter data. The notation in Figure 25 denotes the number of users, where . The duration of the two periods is denoted by and . The overall time for energy harvesting of during the data backscattering period is denoted by . The multiple access system for Amb-BackCom was proposed by Liu et al. [117]. This system detects information from the source and the tag simultaneously. Moreover, they also introduced a new channel model named as the multiple-access channel.
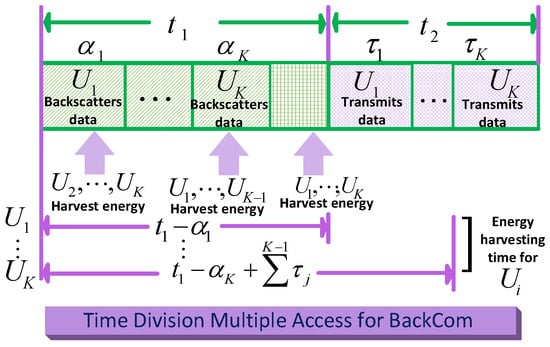
Figure 25.
TDMA in BackCom.
5.3.2. Code Division Multiple Access
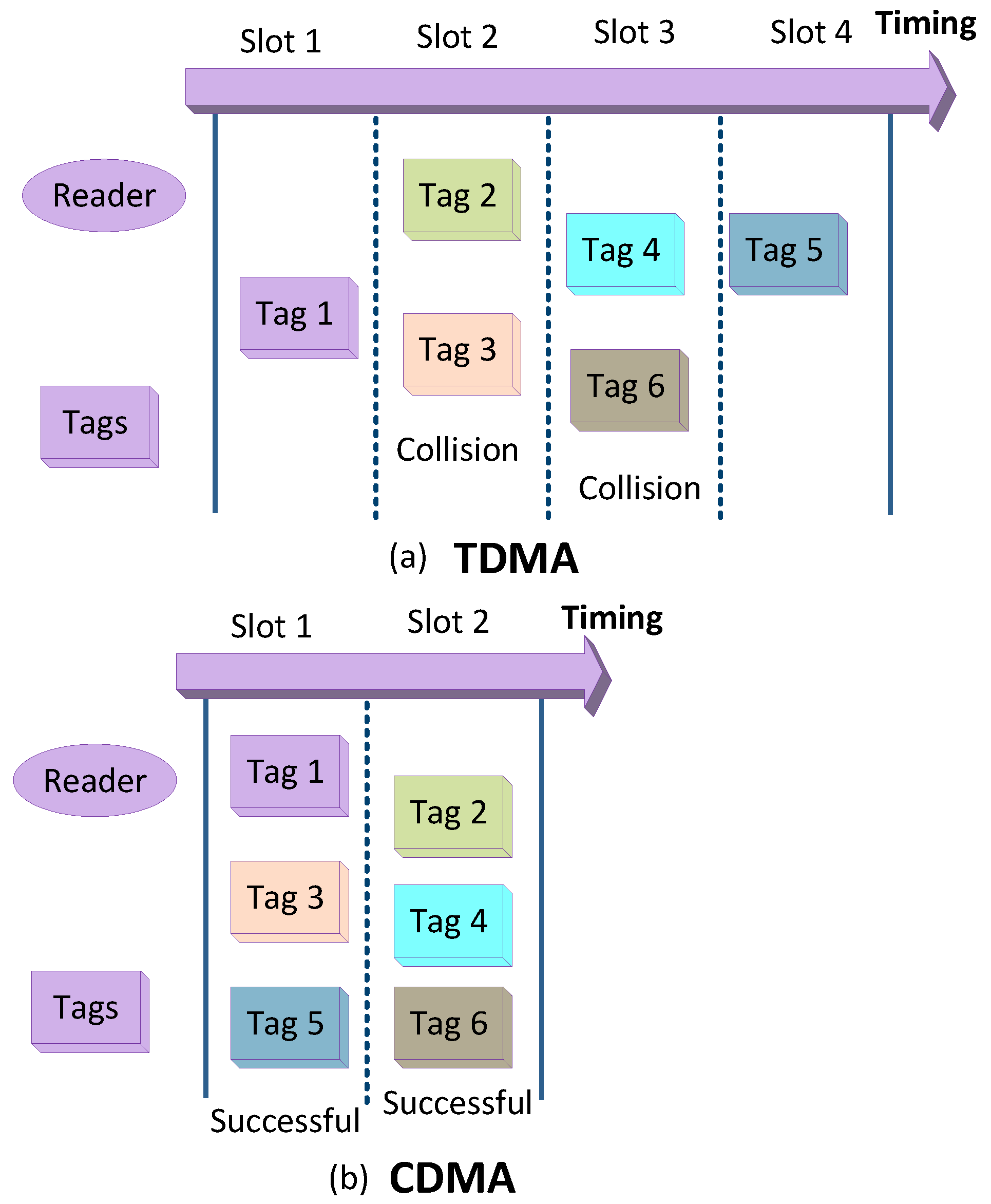
In BackCom, multiple passive tags modulate the same carrier signals that cause overlapping. The overlapped backscattered signals can be separated using code division multiple access (CDMA). CDMA assigns different spreading codes to multiple users by using the characteristic of orthogonality spreading sequence. Different users can communicate with each other without any interference [118]. Figure 26 delineates the comparison of TDMA and CDMA access techniques for BackCom and RFID systems. Figure 26b shows successful transmission by tags using CDMA. Figure 26a shows that tags operating in TDMA mode face collisions. A CDMA-based algorithm for EPC global generation 2 was also proposed to reduce collisions between tags [118]. Moreover, in practical scenarios, dominant signals (carrier component) leak into the receiver. Consequently, received signals lose antipodal modulation properties and corrupt the cross-correlation properties of CDMA codes. To address this issue, code shift modulation was proposed [102]. Mutti et al. suggested CDMA for RFID tags, which proved to be an adequate technique for predicting a large number of tags [103].
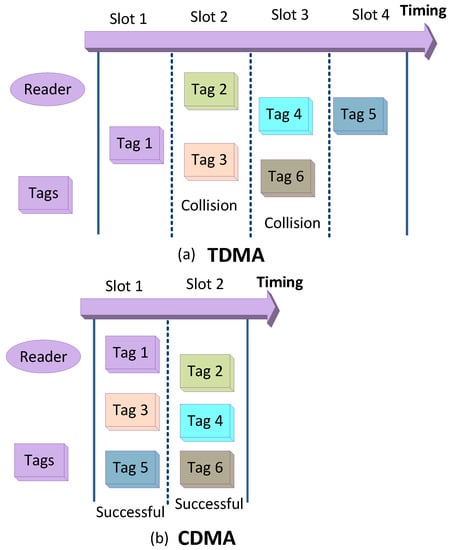
Figure 26.
CDMA compared with TDMA in BackCom.
5.3.3. Orthogonal Frequency Division Multiple Access (OFDMA)
The OFDMA system was found to have synchronous power and information transfer [104]. Moreover, these researchers focused on energy efficiency for the power dividing capabilities of receivers and considered two different scenarios.
- The first arrangement considered the receivers, dividing the received power into a continuous set of power streams while having arbitrary power splitting ratios.
- Another scheme examined receivers that can divide the received power into a discrete set of power streams while having fixed power splitting ratios.
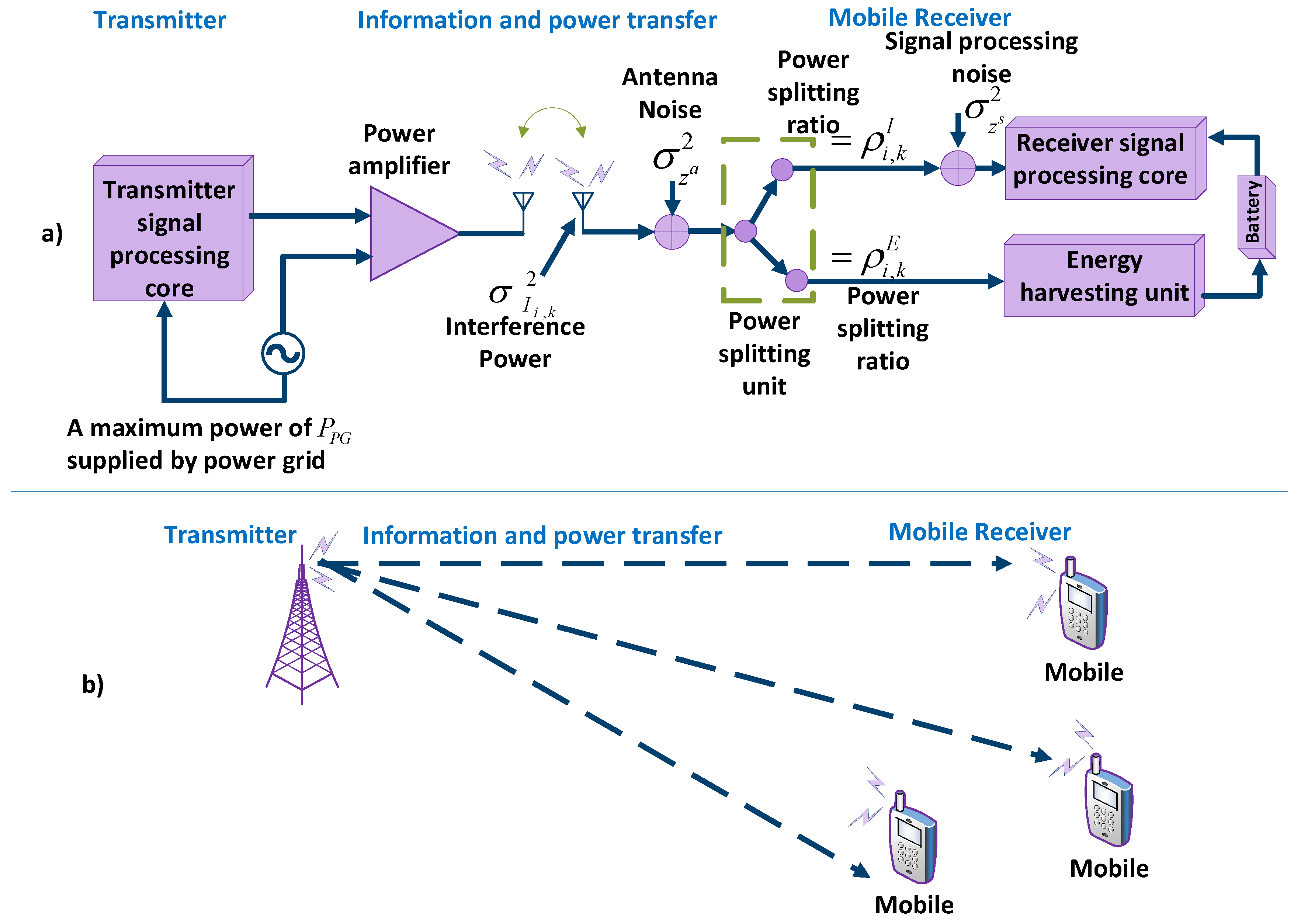
Figure 27a depicts the block diagram of the transceiver model for wireless power and information transfer. Figure 27b shows the OFDMA downlink communication system with K mobile receivers. In the figure, represents the received aggregate co-channel interference on sub-carrier i of receiver k, with zero mean and variance . is emitted by unintended transmitters using the same frequency channel. The power splitting ratios and are used to decode the information in the signal and to harvest the energy, respectively. is the signal processing noise power at the receiver end [104].
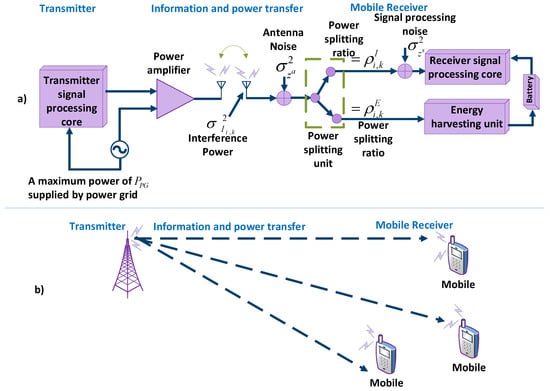
Figure 27.
OFDMA in BackCom. (a) Block diagram of the transceiver model for wireless power and information transfer; (b) OFDMA downlink communication system with various mobile receivers.
5.3.4. Non-Orthogonal Multiple Access (NOMA)
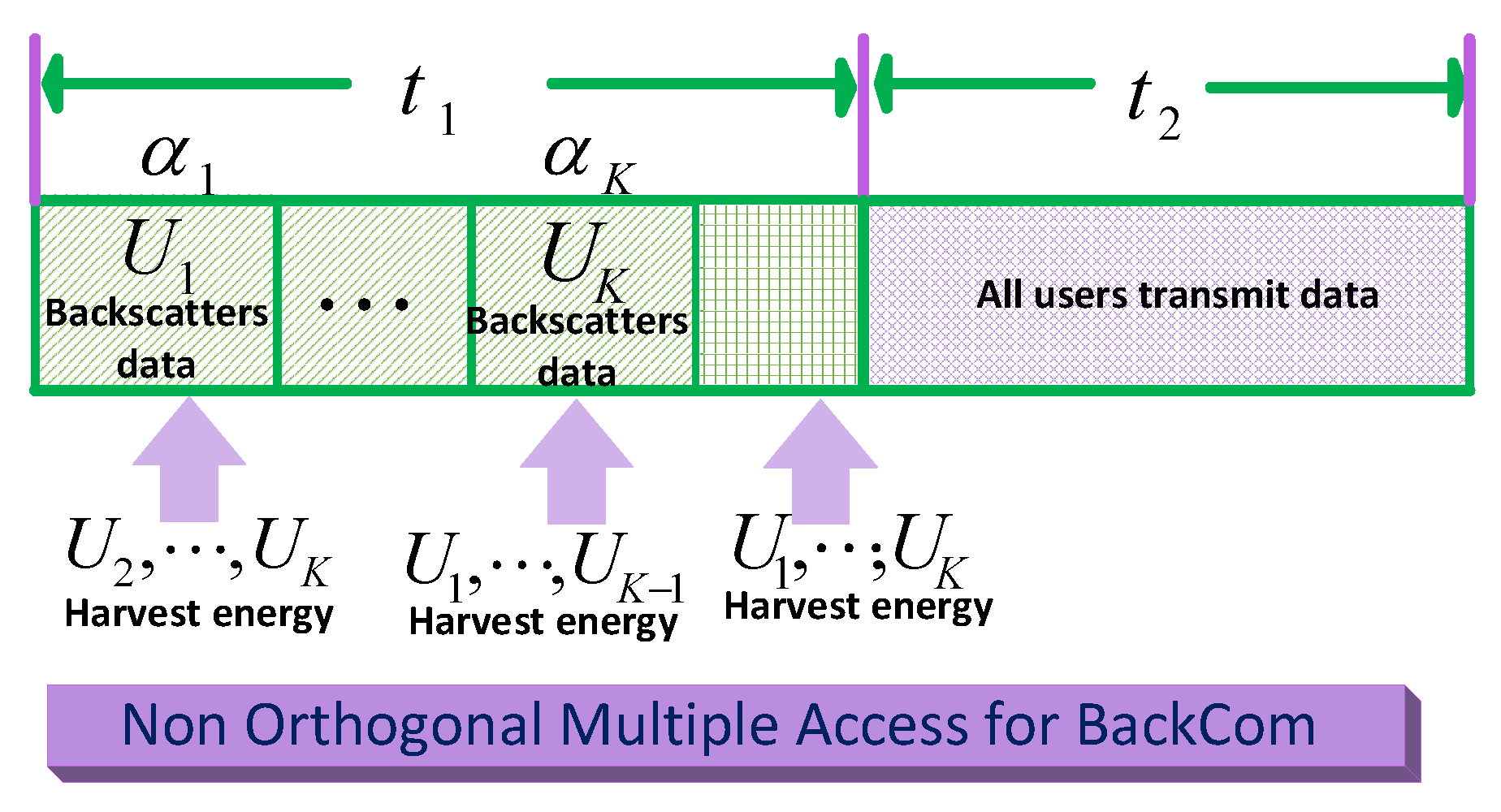
NOMA is treated as the crucial enabling technique with channel gain variations. Various users are multiplexed in the transmission power and could be scheduled non-orthogonally. These multiplexed signals are transmitted on the same spectrum sources. Ali et al. discussed and analyzed the working principles of the uplink and downlink of NOMA [106]. The authors further described distinct working principles for the downlink and uplink using NOMA transmissions in wireless cellular systems. Furthermore, total throughput maximization problem in a cell was formulated, so that user clustering and power allocations conceivably optimize power constraints. NOMA was used for data transfer in BackCom and was shown to have better spectral efficiency and user equity [101].
Figure 28 shows the block structure of WPCN using NOMA. The block is divided into two parts: (i) a data backscattering period and (ii) a transmission period . In the data backscattering period, the user reflects/backscatter data to the information receiver during its designated time slot , whereas all other users harvest energy from the source. Similarly, authors investigated the system level performance of NOMA with successive interference canceller (SIC) on the receiver side [105]. Likewise, the sparse-coded Amb-BackCom modulation algorithm allowed for NOMA in addition to M-ary modulation for concurrent transmissions [119]. NOMA-assisted monostatic BackCom was highlighted by Guo et al. [120]. BackCom nodes, having different power levels, could be paired by the reader to implement the power domain of NOMA. The potential gains of NOMA over OMA (orthogonal multiple access) are discussed to show that NOMA is better than OMA.
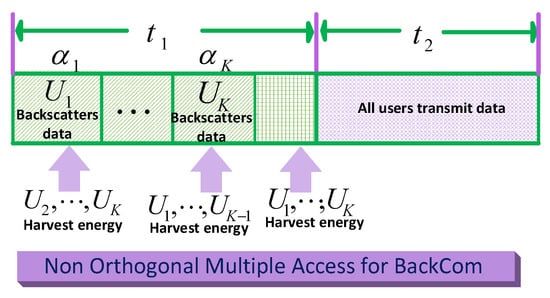
Figure 28.
NOMA in BackCom.
Discussion:Table 8 summarizes the multiple access techniques for BackCom. Moreover, various multiple access techniques for BackCom are suggested to accommodate multiple tags at the same time. These techniques are highlighted below:

Table 8.
Multiple access.
- Multiple access techniques, including TDMA [101], CDMA [103], OFDMA [104], and NOMA [105,106], are proposed for BackCom.
- All schemes accommodate the maximum number of users at the same time.
- We can observe from the above literature that NOMA has a better performance than all others; therefore, NOMA is widely supported by 5G [105].
- NOMA has the potential to meet future demands of connecting a large number of IoT devices.
Let us now consider power sources for BackCom. Adequate data and power transfer methods, in addition to scheduling and resource allocations for BackCom, are also elaborated.
6. Efficient Power and Data Transfer in BackCom
The efficient energy and data transfer in BackCom is receiving attention from the research community to power up passive devices. This section highlights various power sources in different types of BackCom. One of the leading power sources that bring BackCom back to life is Amb-BackCom. In addition to efficient power transfer techniques, energy management is also considered for enhancement of lifetime of passive devices. Recent technology conversion and frequency shifting techniques allowing BackCom to use the frequency spectrum of multiple technologies are also discussed.
6.1. Power Sources in BackCom
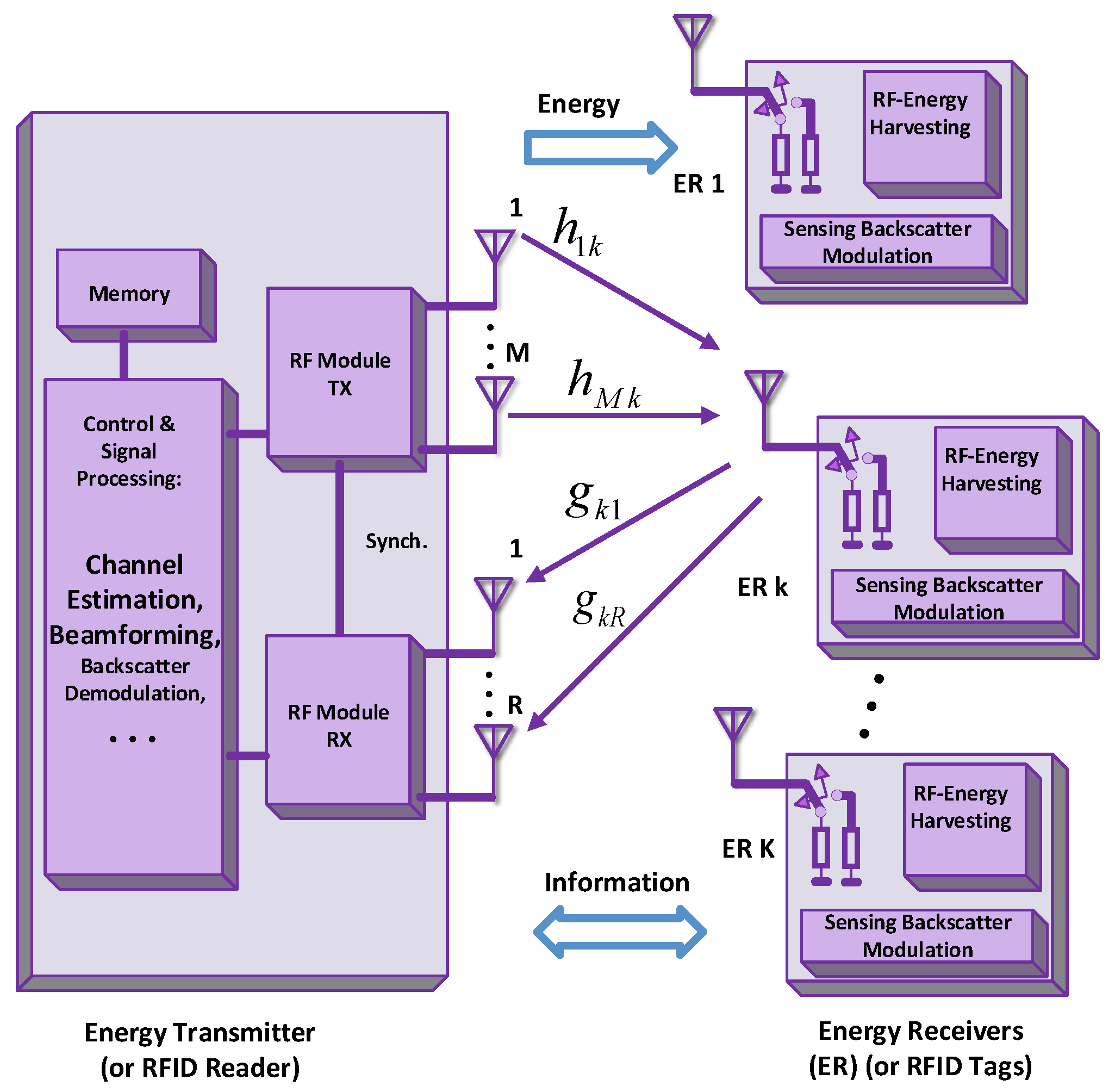
BackCom utilizes multiple power sources for the operation of passive tags, which can be dedicated or non-dedicated. Non-dedicated ambient sources include WiFi transceivers, TV broadcast transmitters, Bluetooth chipset, cellular base stations, AM/FM radio transmitters, or other RF power beacons. Figure 29 shows the connectivity of tags and readers through power beacons.
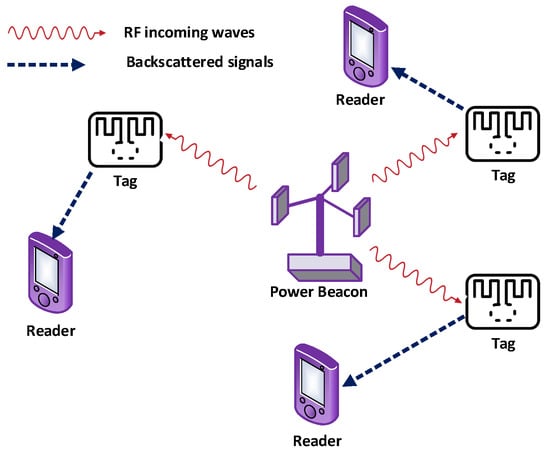
Figure 29.
Wirelessly powered Backcom.
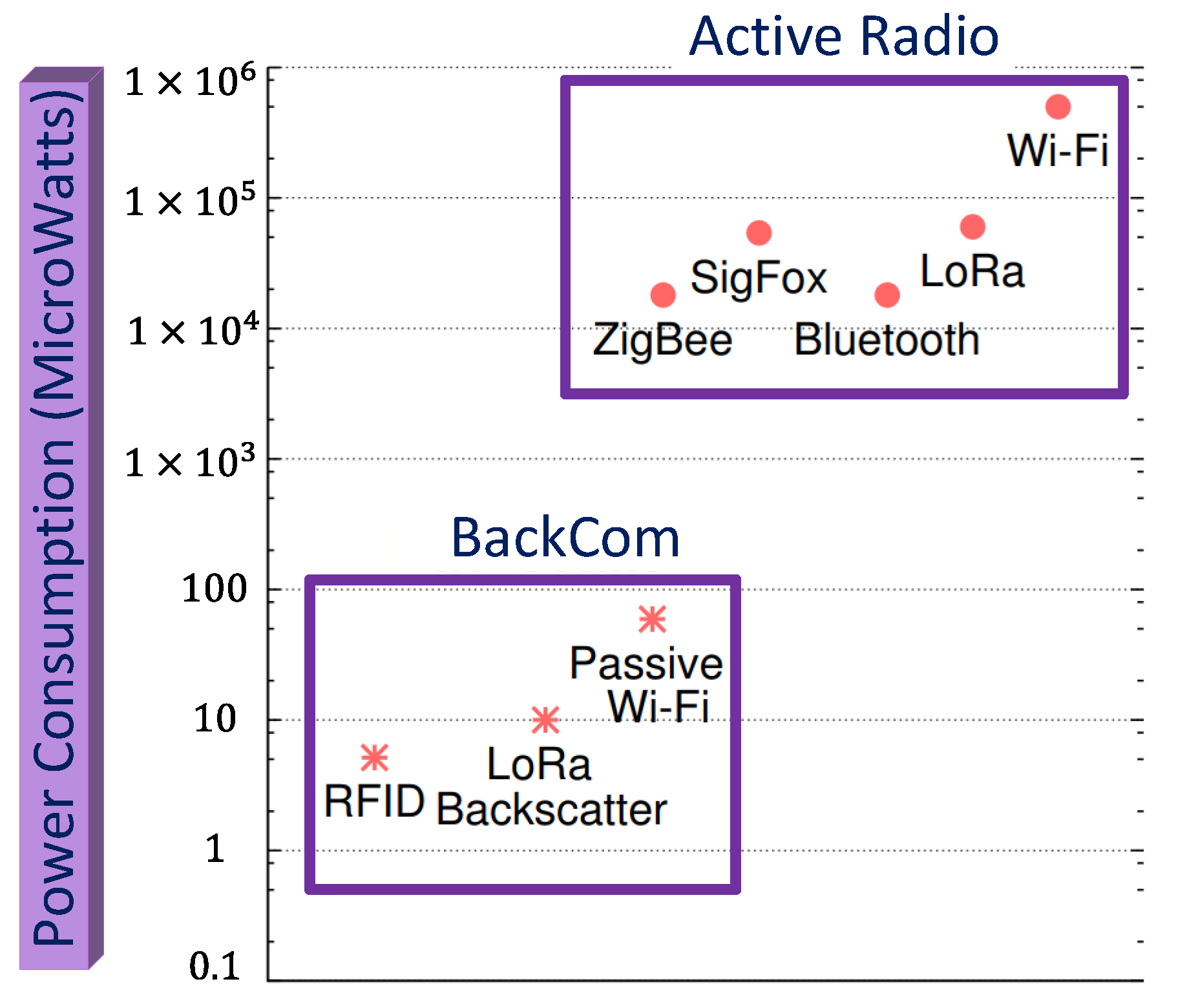
An overview of RF-based wireless energy transfer technologies and their utilization in wireless communications have been discussed to highlight key design challenges and solutions, with opportunities in BackCom [79,121]. Usually, in traditional wireless transceivers, the power consumed by Bluetooth ranges from 20 to 60 mW, while the power consumption of WiFi is more than 200 mW [122,123]. Interestingly, the power consumption of devices in BackCom is in micro-watts [8,32]. Figure 30 exhibits the power consumption of various devices operating with active radio and BackCom technologies. Ambient signals can fulfill this tiny power requirement. Moreover, the ambient RF sources with additional peripheral components (e.g., boost converter) could overcome the need of a battery in passive devices [124]. Liu et al. introduced Amb-BackCom to power passive tags. This technique harvests power from surrounding RF waves and modulates the information on backscattered signals [12]. Subsequently, as there is no requirement of dedicated power sources, Amb-BackCom leverages the complete power from the surrounding radio signals.
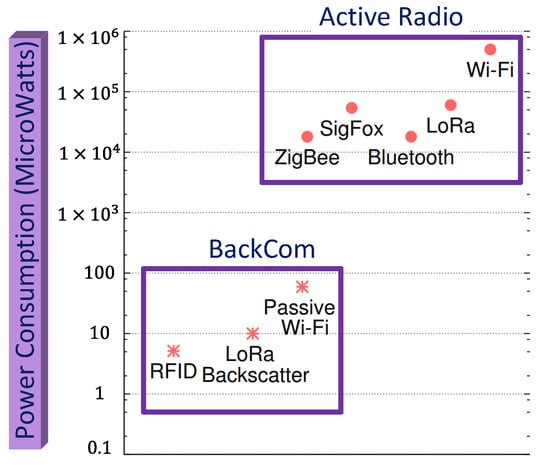
Figure 30.
Power consumption of active and BackCom devices.
Mobile base transceiver station (BTS) and TV broadcasting towers as power sources in Amb-BackCom were studied in [125]. These power sources are preferred in urban environments, due to their easy availability and high transmitting power. Furthermore, this work considers energy harvesting topology, with dual ambient RF sources, for entirely practical sensor nodes in real-world scenarios. This topology achieves the lowest available input RF power levels and improves operational capabilities of the harvester in urban and semi-urban environments. Pinuela et al. showed the efficiency of harvesters up to in urban or semi-urban areas, while operating on a single frequency band [126]. This circuit requires low power levels of about dBm for its operation. A hardware prototype was built for BackCom devices, and it could draw complete power for its circuitry through energy harvesting from TV signals and solar energy [32]. This design enabled tags to communicate through walls at a distance of tens of meters.
Backscatter fading channel principles and characteristics, such as beam-forming, were considered for BackCom energy transfer [127]. Subsequently, the latest trends in small cells, 5G, mm-waves, and massive MIMO encourage implementation of wireless power transfer, along with information exchange [128]. Likewise, a simple model for energy harvesting, by a tag, was proposed to show the trade-off between link reliability and the duty cycle of the tag for only downlink tags [74]. A model consisting of the WiFi source to power-up RF-powered devices was suggested [37]. The proposed WiFi BackCom model connects RF-powered tags to the Internet. Moreover, a hardware-based model demonstrated a communication link between WiFi devices and RF-powered tags [37]. The passive WiFi chipset that works on BackCom consumes 3–4 times less power in magnitude, compared to the available, common WiFi generating transmissions [35,129]. PoWiFi was proposed to utilize existing WiFi chipsets to power up passive tags [130]. The multi-channel harvester in PoWiFi can harvest energy from various GHz WiFi channels. Furthermore, the design of WiFi chipset-powered camera sensors and temperature sensors were suggested. Authors also demonstrated the recharging utility of batteries made up of , , and coin-cell materials that can be charged by WiFi signals.
Bradio was proposed to consume little power and ranges from 16 to 129 micro-watts [131]. Moreover, compared to Bluetooth, it improves the total number of transmitted bits. Likewise, HitchHike was presented for a low power BackCom system and can harvest power from ambient WiFi signals [34]. HitchHike enables the little-powered tag to reflect the signals from commodity WiFi transmitters on existing IEEE standards. Thus, the commodity receiver can decode backscattered signals as a standard WiFi packet. Later, a low power operating system for ultra-low power devices was proposed to scale down the buffer size in dynamic and ultra-low harvesting conditions [27]. Xu et al. suggested a two-user cooperation procedure in a WPCN assisted by BackCom [132]. This procedure saves energy by reusing wireless power transfer for simultaneous data exchange during harvesting time. Furthermore, the authors present a battery-free BER modulated data transmission technology that works on ambient WiFi signals [133].
The harvest-then-transmit (HTT) protocol is used for wireless energy transfer by H-AP [134]. H-AP transmits energy to tags in the downlink and users can send their information utilizing harvested energy. The optimal harvesting ratio was obtained using the HTT protocol with non-dedicated sources [54]. This harvesting ratio can enhance the expected throughput for decode-and-forward (DF) relay transmissions, as well as direct transmissions (DTs). A mixture of backscatter modulation and wireless power transfer with a diode-based design was proposed for the continuous flow of energy [135].
6.2. Power Transfer Management and Technology Interchange
6.2.1. Energy Management and Efficient Power Transfer
Energy management in passive device communications is crucial to supply continuous energy to inactive tags. A balance may be needed between harvesting rate and information transfer. Some optimal policies have been suggested for balancing the energy harvesting rate, which cannot be controlled by tags [136]. The proposed optimal stationary policy can maximize the long-term average read probability of tags. Moreover, the energy scheduler and the power amplifier were used; they are able to control the probability of successful transmissions by varying the drawn energy from the storage device.
Efficient power transfer is always needed to enhance the lifetime of passive tags. Liu et al. considered ambient power sources, rather than dedicated sources, for efficient power transfer in BackCom [12]. Similarly, RF-based efficient power transfer was suggested with energy beam-forming. This technique considers a power transmitter (reader) with multiple antennas for sending data and energy to various power receivers [127]. Figure 31 demonstrates a multi-antenna RFID reader with an M number of transmitting antennas and an R number of receiving antennas. A K number of RFID tags is equipped with a single antenna each. The reader in this scenario can perform channel estimation, energy beam-forming, and other signal processing operations, and each tag has an RF-energy harvesting module for its operation. The notation represents the forward channel between the m-th transmit antenna. The shows the backward channel between it and the k-th tag [127]. Likewise, a rectifier design was suggested for the efficient harvesting of electrical energy to energize a WSN [137]. This technique works in dual load conditions by utilizing two distinct frequencies.
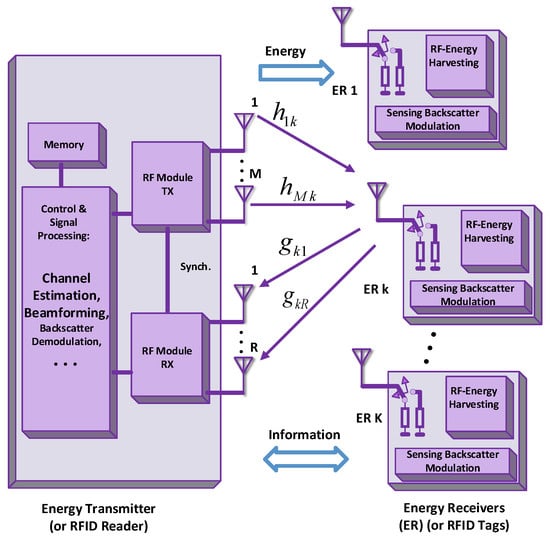
Figure 31.
Efficient power transfer in BackCom.
6.2.2. Technology Conversion and Frequency Shifting Technique
The technology conversion technique enables BackCom to use the frequency spectrum of two technologies, by transforming the frequency band of one wireless technology to another [36]. Figure 32 delineates the concept of technology conversion, which converts the Bluetooth frequency to a WiFi spectrum. Similarly, WiFi devices can be used for the creation of Bluetooth- and ZigBee-compatible wireless signals for BackCom [36]. Moreover, this work suggests a single side-band backscatter design, which can cause a frequency shift on one side of the carrier. The suggested technique leads to the communications between contact lens and smartphones and smart-watches. Ensworth et al. proposed smartphone Bluetooth 4.0 Low Energy (BLE) [51]. They utilized low cost, commonly available smartphones, and other handy devices, to work as a ready-made infrastructure for IoT nodes. These devices are supported by the ultra-low power modulated BackCom scheme (MBS), which is commonly used in ultra high frequency (UHF) RFID systems. Moreover, MBS is now compatible with BLE software and hardware. Similarly, a BLE-compatible full-duplex BackCom system model for mobile devices was proposed to demonstrate monostatic full-duplex communications [97]. This model further considers the carrier source co-located with the Bluetooth chipset. This enables specially designed BLE-based backscatter tags to transmit information via a Bluetooth chipset, without any software modifications.
Figure 32.
Technology conversion in BackCom.
The frequency shifting technique allows backscatter tags to shift the carrier frequency to a nearby spectrum [138]. This type of scenario shifts carrier signals to a nearby non-overlapping band of frequency (using Bluetooth and a WiFi band) [97]. This scheme also separates the frequency range of backscattered signals from the primary (signals) band to strengthen decoding.
Discussion:Table 9 highlights different power sources for BackCom in addition to energy management and efficient power transfer techniques. Moreover, technology conversion techniques and frequency shifting techniques are also given:

Table 9.
Summary of BackCom efficient power and data transfer.
- The energy consumption of BackCom devices is in micro-watts [8,32]. This small amount of power can be extracted from surrounding (ambient) radio waves [12], such as WiFi signals [37], cellphone signals [125] and TV signals [93].
- The optimal harvesting ratio and different harvesting modes for BackCom are discussed. Energy management policies for energy harvesting using BackCom were discussed [136].
- Efficient power transfer schemes use energy beam-forming and multiple antennas for BackCom [127].
- Technology conversion in BackCom utilizes the frequency spectrum of Bluetooth and converts those signals to WiFi and Zigbee signals [36].
- The frequency shifting technique in BackCom allows the carrier signals to shift in nearby frequency bands [138].
6.3. Scheduling and Resource Allocation
This subsection considers energy scheduling and data scheduling for the efficient management of power with information transfer. Moreover, the allocation of resources and time is considered, in addition to cognitive radio and optimization techniques, to bring about the best use of resources.
6.3.1. Energy and Data Scheduling
Energy scheduling is essential for better power harvesting and efficient data transfer. A scheme for backscatter-assisted wireless power communication networks (BAWPCNs) was proposed by Lyu et al. [95]. Similarly, a BAWPCN-based model considers energy scheduling using TDMA. This energy scheduling scheme has the trade-off between successful transmission probability and the energy harvesting rate [51].
BackCom enables each tag to communicate simultaneously through the reflection of incident signals. This simultaneous reflection by each tag causes data collisions [59,82]. In order to avoid data collisions by tags, priorities and procedures for data transmissions are needed. Hoang et al. considered data scheduling for backscatter sensor network to prevent collisions [139]. Moreover, the authors highlighted the data sending technique through a gateway. This technique changes the impedance of antenna while backscattering received RF signals. This work reduced the complexity and power consumption and addressed the data collection problem in addition to data scheduling. They also suggested a data scheduling algorithm for BackCom sensors, shown in Figure 33. Similarly, the principles for RFID data management were highlighted with comparative analysis to understand the essential features of BackCom [140].
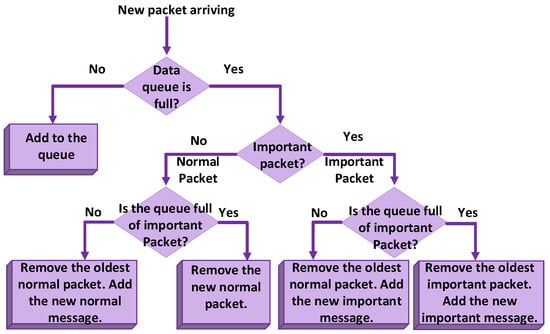
Figure 33.
Data scheduling for backscatter WSN.
6.3.2. Resource and Time Allocation
Proper allocation of resources in BackCom enhanced the life of the network. An algorithm for the allocation of resources was proposed to maximize the energy efficiency, while considering data transmission [101,141,142]. Kalamkar et al. suggested three schemes for resource allocations, which consider equal time allocation, minimum throughput maximization, and proportional time allocation, to enhance the fairness in a wirelessly powered cooperative cognitive radio network [143]. Efficient energy resource allocation for WPCN can address the energy efficiency maximization problem for WPCNs [144]. Lyu et al. optimized three resources together: (i) the transmission power of the reader, (ii) the reflection ratio, and (iii) the time allocation for semi-passive and passive tags [145]. Optimal allocation of time and energy was considered to maximize the total throughput. This allocation scheme also saved energy in the tags of the upcoming data blocks [146].
Optimal time allocation was achieved for a full-duplex and half-duplex BAWPCN, to maximize the system throughput while considering H-AP [95]. Similarly, optimal time and energy allocation techniques were found to enhance the sum throughput in BackCom [100]. The model based on the time block bifurcated the time block into two pieces. One was for data backscattering in BackCom and the other was for data transmission in HTT [101]. Moreover, optimal time allocation policies were shown to improve the system throughput. That work considered optimization to maximize performance. The authors also suggested time allocation policies for energy harvesting and data backscattering while transmitting data.
6.3.3. Cognitive Radio
Cognitive radio efficiently utilizes the wireless channel, for the best allocation of resources. Mohjazi et al. presented an overview of a cognitive radio network powered by RF energy [147]. This work addressedthe problem of relay selection and resource allocation, in cognitive radio sensor networks, to harvest power wirelessly [148]. The advantages of combined WPCN and cooperative cognitive radio have been explored [143]. The authors further presented a sum throughput optimal resource allocation (STORA) scheme. STORA provides a trade-off between fairness and overall throughput while considering this combined scheme [143,149]. Similarly, a technique for the improvement of data rate was proposed in the secondary system of an RF-powered backscatter cognitive radio network [150,151]. The maximum data rate of the secondary system was obtained by optimization of the allocated time for energy harvesting, transmission, and backscattering, respectively.
As shown in Figure 34, the concept of integration of an RF-powered cognitive radio network with Amb-BackCom was proposed to improve the performance of secondary systems [152]. Figure 34a delineates the case where a primary transmitter sends signals (i.e., a primary channel is busy), and the secondary transmitter transmits data to a secondary receiver using BackCom. In other cases, the secondary receiver can harvest energy as demonstrated in Figure 34b. The symbol represents the normalized channel idle time period, and denotes the normalized channel busy time period. In the case of the busy channel, stands for the time ratio for energy harvesting, and denotes the time ratio for BackCom. Notation shows that the data transmission period [152]. Moreover, the trade-off between HTT and the BackCom network protocols was analyzed. The results show that the proposed scheme outperforms the individual backscattering mode and HTT protocols [152]. A hybrid HTT and BackCom mode was suggested for a secondary communication system in cognitive wirelessly powered radio networks [153]. Subsequently, Lee et al. proposed a network architecture based on cognitive radio. This architecture enables secondary users to harvest energy while primary users operate on the same frequency spectrum [154]. Guo et al. investigated the cognitive BackCom with multiple RF sources and showed high throughput with multiple antennas at a single tag [155].
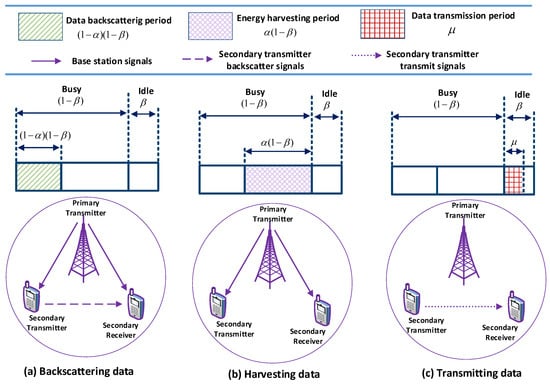
Figure 34.
RF-powered cognitive radio network with Amb-BackCom.
6.3.4. Optimization
The efficient use of resources in BackCom improves the efficiency of a system. This type of scenario was considered in backscatter sensor networks. Authors focused on data optimization using a Markov decision process framework, and a state action reward state action (SARSA) algorithm, to achieve optimal policy [139]. Similarly, Yang et al. focused on the optimization of channel-training energy and energy allocation weights for multiple energy beams [127]. The performance optimization problem for cognitive radio networks with an RF energy harvesting ability was studied for secondary users [156]. This work also showed a system model of secondary users that can increase the throughput of the complete network by identifying a group of ordinary channels.
Clerckx et al. considered link optimization for wireless power transfer [157]. This work further suggested a method for designing and optimizing multi-sine waveforms for wireless power transfer. Moreover, Wu et al. proposed energy efficiency maximization for WPCNs [158]. In this case, users can harvest energy from a dedicated energy source even before communicating with the station. Ma et al. proposed the design for two optimal transmission strategies for a buffer-aided Amb-BackCom system [159]. This system can minimize energy consumption while sending data. The throughput can be maximized with a certain amount of energy. Zheng et al. proposed an efficient method of obtaining an optimal solution to the maximum common throughput optimization problem [160].
Discussion:Table 10 demonstrates the summary of scheduling and resource allocation, and the critical points of scheduling and resource allocation are enumerated below.

Table 10.
Summary of BackCom scheduling and resource allocation.
- There are two types of scheduling in BackCom. The energy scheduling [95] and data scheduling [139].
- The allocation of resources is carried out depending on different parameters, such as time [100], throughput [143], and energy [101].
- Optimal allocation policies for time are shown for BackCom [143].
- The cognitive radio-based allocation of resources is considered for Amb-BackCom, and this depends on the availability of channels [152].
- The SARSA algorithm performs well for the optimization of resources [139].
7. BackCom: Range Extension and Reliability
The network coverage problem for BackCom and its solution is highlighted in addition to security and reliability of data. Various techniques are used to extend the communication range of BackCom. These include multi-antennas and MIMO technology, followed by relaying and D2D communications. Moreover, techniques for reliable communications and security for BackCom are also explained.
7.1. Coverage and Range Improvement
7.1.1. Coverage Problem
BackCom deals with the reflected signals having very low signal parameters (such as amplitude and frequency). Moreover, the round trip path loss and interference also attenuate the BackCom signals [61]. Consequently, the communication range of backscattered signals is very limited. In order to address the challenge of short range and to maximize communication range, various techniques are suggested. The coverage problem was analyzed in the wireless passive sensor network, and the analysis results can be used to determine the design procedures for battery-free wireless passive sensor networks and RFID networks [161].
7.1.2. Increasing Range
Various techniques have been used to increase the communication range in BackCom. Fasarakis et al. maximized the range of the BiS radio channel by proposing the coherent receiver [66]. Similarly, long-range (LoRa)-dependent BackCom, to extend communication ranges and to include a wide area network, was achieved by chip spread spectrum (CSS) design [129]. The CSS design can successfully backscatter at a distance of 475 m. Figure 35 delineates the operating distance of the LoRa BackCom compared to the traditional RFID and WiFi backscatter systems. Peng et al. proposed PLoRA, an extended range data network for Amb-BackCom LoRa transmissions [162], PLoRA uses LoRa transmissions as excitation signals to convey the data. In order to improve the range, RFID technology combined with the bar-code technique on the same label was proposed [163]. A range extension of m was achieved for a 12 cm sized tag. Quantum tunneling-based BackCom considers a highly sensitive GHz tag that can backscatter in free space up to km and consumes only 20.4 W [164,165,166]. The quantum tunneling tag (QTT) consists of a battery-assisted quantum tunneling reflection (QTR) connected to a tag antenna, and a waveform generator [167]. The tag antenna and waveform generator are responsible for the modulation, amplification, and backscattering of input carrier waves.
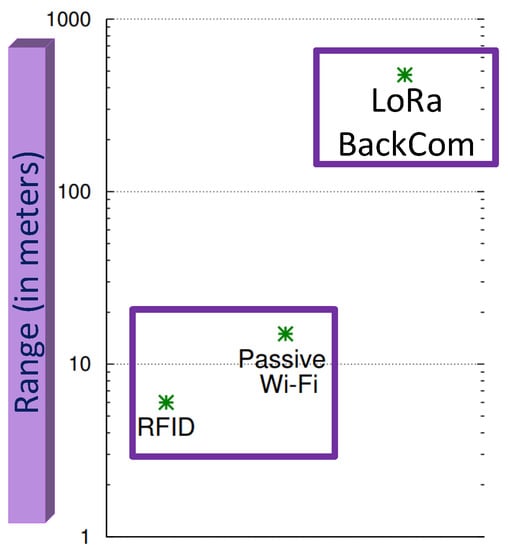
Figure 35.
Increased range in the LoRa BackCom.
A power amplifier with an energy storage device for passive RFID tags was proposed to extend the communication range of backscattered devices by amplification [136]. Choi et al. demonstrated a backscatter-based WPCN that could attain a high range compared to its active counterpart [168]. Ultra-wide-band technology was also considered to increase the range and bandwidth of a BackCom system [169]. Bacha et al. suggested a stochastic geometry approach in passive IoT networks to enhance the field of powered communications [170]. Their study showed that the communication range of BackCom can be equal to a traditional wireless communication range if power beacons are densely deployed.
7.1.3. Multi-Antenna and MIMO Systems
The construction of antennas with any shape of radiation pattern is possible [13]. Multiple antennas can be placed in the reader or tag to enhance the communication range and throughput of backscatter devices. MIMO technology embeds various antennas at the source tag or the destination tag. MIMO systems in wireless communications can also improve the throughput and coverage area. Parks et al. suggested a Micro-Mo design that is considered the first design of multi-antenna BackCom tags [32]. Micro-Mo utilize ambient signals to communicate between tags.
Duan et al. proposed a system that can convert bistatic modulated backscatter to an ambient bistatic modulated re-scatter model in [171]. This system also enables the transmission of data from many antenna transmitters to multiple antenna receivers. Darsena et al. studied the physical layer of a BackCom system and designed a protocol that focuses on the use of various antennas at the tag and the receiver [172]. BackFi also utilizes multiple antennas to improve the range and throughput of WiFi backscattered signals [173]. Figure 36 illustrates the multi-antenna reader design to collect backscattered signals of a single antenna tag, coming from different paths [91]. The letters represent different channels, and M shows the number of antennas in the reader. Boyer et al. presented a dyadic backscatter channel (DBC) that is especially designed for BackCom [74].
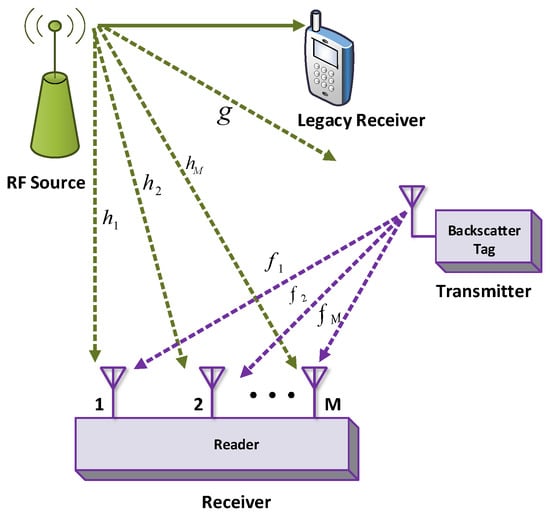
Figure 36.
Multi-antenna in BackCom.
A signal detection algorithm was proposed for a multi-antenna Amb-BackCom model based on information of the channel state [91]. This algorithm shows that the increased number of receiving antennas reduces the bit error rate. However, if the number of receiving antenna rises above a certain level, an error floor can be observed. The work in [74] investigated RFID MIMO systems for BackCom to improve throughput. Likewise, a unitary query scheme for MIMO backscatter RFID channels was proposed for the data rate [174]. This scheme consists of three components: (i) a query component, (ii) a tag component, and (iii) a receiver component. The query component includes M number of antennas in the reader for the transmission of data, the tag component has L antennas, and the receiver component is embedded with N receiving antennas for the reader. The unitary query scheme enables time diversity in coherent time of channel, while displaying performance improvements of 5–10 dB in mid-range SNR regimes.
Zhang et al. considered a MIMO wireless broadcast system for three nodes [175]. This system demonstrates all transmitters and receivers with multiple antennas. One receiver can harvest energy, while other receivers decode information received from the same transmitter. This work is based on two practical designs, namely (a) time stitching and (b) power splitting for the co-located receiver. Afterwards, a cooperative receiver was suggested that could recover signals from two directions, i.e., from Amb-BackCom devices and from RF sources [89].
7.1.4. Relaying for BackCom
Relaying is a procedure to extend the communication range of BackCom devices. This technique enables some nodes to assist other nodes while carrying information in the network. Figure 37 delineates a simple concept of relaying for Amb-BackCom devices [93]. They consider backscatter tags to relay information from the source tag to the destination tag. Due to the full-duplex mode of relaying tags, the data can be sent simultaneously during the reception of signals. Two cases are considered in this relaying scheme [93]. In the first case, the selected relay tag has its own data to transmit; in the other case, it does not. The time period is divided into two blocks, and information is carried from source to relay, and from relay to destination, in each half time block, respectively.
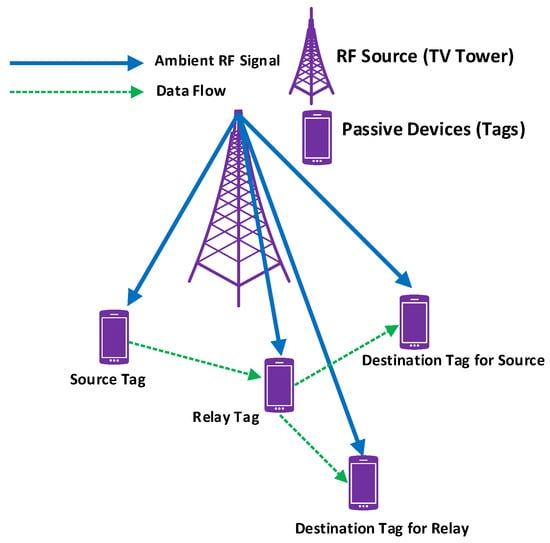
Figure 37.
Relaying in BackCom.
A passive two-hop relaying scheme via BackCom in cooperative wireless networks was proposed by Gong et al. [176]. Their scheme maximizes the throughput by jointly optimizing the WPT and relay strategies. Yan et al. proposed the three-time-slot decode-and-forward relay system for Amb-BackCom [177]. Amb-BackCom-assisted wirelessly powered relaying was suggested in [178]. This technique utilizes hybrid relay in a dual-hop relaying system with widely distributed energy sources. Similarly, a relay selection scheme for cooperative BackCom enables communication with out-of-coverage devices using Hybrid-AP [179]. A team of MIT researchers introduced the “RFLY” relay to extend the range of backscatter tags with the help of drones [180]. They also addressed the problem of self-interference and localization, by preserving the phase information of the reflected signals.
7.1.5. D2D Communications for BackCom
D2D communications can be used for extension of the network coverage in BackCom. As D2D is an essential part of IoT technology that helps in the design, deployment, and maintenance of a sustainable IoT ecosystem. Researchers from both industry and academia are focussing on implementing energy-efficient IoT networks, which can work on BackCom. Intelligent D2D communication using passive IoT devices is among the challenges faced. A wirelessly powered BackCom architecture was proposed to allow D2D communications between passive nodes by integrating BackCom and wireless power transfer together [181]. Furthermore, Bello et al. analyzed routing algorithms for D2D communications in IoT and suggested four different approaches to attain D2D communications with a routing algorithm [182].
The authors in [183] proposed hybrid D2D communication. The communication technique integrates Amb-BackCom with WPCN. Figure 38 shows the concept of hybrid D2D communication for two groups of coexisting ambient transmitters X and Y, which can work on separating frequency bands in WPCN. This approach considers two modes of operation: (i) the ambient backscatter mode and (ii) the HTT mode. The RF energy harvester of the hybrid transmitter operates on the frequency band of X. If the mode of the hybrid transmitter is ambient-backscattered, load modulation is performed on incident signals from the frequency band of X transmitters. If hybrid transmitter is in HTT mode, the energy can be harvested using the frequency band of ambient transmitters X, and information can be transmitted using the frequency band of Y transmitters. D2D communication is performed during HTT mode. Received signals at the hybrid receiver are impaired by the interference of Y. Lu et al. addressed this interference issue with the -Ginibre point process [183].
Figure 38.
Hybrid D2D Amb-BackCom.
7.2. Reliability and Security
Achieving reliability and security in a network is an important task in BackCom. Passive tags do not have a signal generator component, and always seek signals from nearby sources. These external sources may risk the security and reliability of tag data. The reliability issue in BackCom was addressed by modeling uplink transmissions in backscatter networks [59]. Moreover, this approach considers transmissions by only a single virtual transmitter and deals with collisions as a sparse rateless code among nodes.
Griffin et al. addressed the reliability of backscattered radio systems using multiple antennas [62]. Similarly, security attacks using D2D communications include interference attack. This type of attack is on privacy and can be executed by statistically or logically determining data transmission patterns between devices [182]. Another type of security attack is the distributed denial of service attack, which can jam autonomous D2D communications and stop the exchange of data between devices. These above-mentioned types of attacks can also exist in IoT with backscatter devices and need to be addressed carefully. Furthermore, the carrier signals used to energize passive devices for retrieving data may be exploited by hackers. The overhearing of data without permission is called an eavesdropper attack. This attack is more common in BackCom. Several security measures have been taken to solve this problem [109,184].
Figure 39 shows a secure BackCom assisted by nearby relays. This scenario considers no direct link between reader and tag, and BackCom is only possible with the help of relays [184]. All relays communicate in half duplex mode, having a single antenna and perform amplify-and-forward task. The relay node (forward) is selected from all relays, to power up the tag by transmitted carrier waves. The relay node (backward) is selected nearer to the reader, to receive the backscattered signals from tags. The nearer selection of relay node improves the secrecy rate and avoids attack from eavesdroppers.
Figure 39.
Secure BackCom assisted by helping relays.
Discussion:Table 11 summarizes the range extension of BackCom devices in addition to the reliability and security of data. Key points are discussed below.

Table 11.
Extension and reliability in BackCom.
- To enhance the communication range of BackCom in a BiS scenario, a coherent receiver is suggested [66], the BackCom LoRa scheme performs well for long distance communications [129]. Quantum tunneling-based backscattering [167] and power amplifiers [136] are also suggested for an extension of range.
- BackCom tags can use multiple antennas and MIMO system designs for the enhancement of communication range. These designs are suitable for large size tags that are used in MicroMo [32], multi-antenna BiS [171] and unitary query schemes [174].
- RFID MIMO systems for a dyadic backscatter channel also improve the communication range of the dyadic channel [74].
- A full-duplex relaying scheme for BackCom based on the division of time slots increases the communication range by simultaneous energy reception and data transmission [93].
- A D2D-based communication scenario improves the coverage in passive devices [182].
It is observed from the above literature that, besides BackCom range extension, researchers are also trying to address interference attack, denial of service attack, and eavesdropping attacks for the sake of BackCom security. However, there is much room for improvement in range extension in addition to the reliability and security of data.
8. BackCom Applications
Various energy harvesting techniques to energize the passive devices are becoming popular [185]. BackCom is one of the exciting techniques among them. Figure 40 depicts a wide range of applications for BackCom with next-generation 5G networks. BackCom can be used in smart homes and cities, in unmanned aerial vehicles (UAVs), in the bio-medical field, and in textile and environmental monitoring systems. Similarly, the advantages of BackCom in body area sensor networks, vehicle monitoring, and backscatter sensor network cannot be ignored. BackCom makes the future vision of massive IoT more realistic by connecting and monitoring every object remotely. The details of these applications are discussed below.
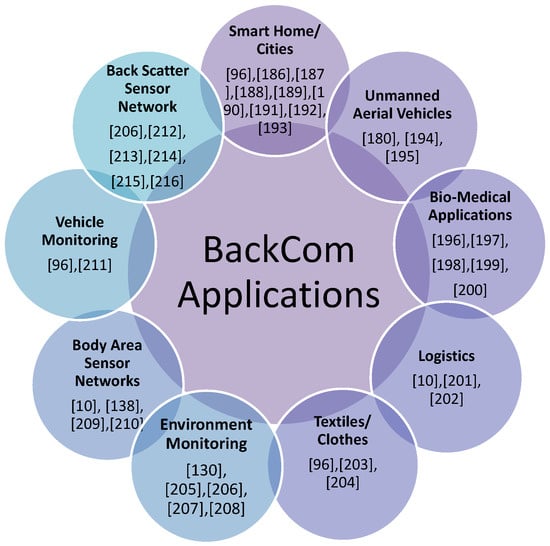
Figure 40.
Applications of BackCom.
8.1. Smart Homes/Cities using BackCom
Figure 41 shows the concept of smart home that enables each object in the smart home having a backscatter tag to communicate through WiFi signals. Smart home consists of a considerable number of BackCom passive tags deployed at multiple locations (e.g., roof, walls, furniture, etc.). These tags can seek power from ambient sources such as WiFi access points, TV towers, or cellular eNBs/gNBs. The applications of passive tags are smoke detection, gas leakage check, movement monitoring, surveillance, and indoor positioning [186,187]. Smart cities utilize ubiquitous BackCom passive tags in buildings, streets, bridges, and parking spaces. The tags could help to improve the quality of life by monitoring air pollution, traffic monitoring, and parking availability. Furthermore, due to the availability of ambient signals in each home, it is now possible to remotely access household items utilizing BackCom. It is expected that BackCom enable smart cities and homes, making life more easy and comfortable.
Figure 41.
The concept of a smart home using BackCom.
The concept of BackCom in a smart home helps to monitor human breathing and heart rate without mounting any devices on one’s body [188]. Researchers have also investigated object detection [189,190] and activity recognition [191], using backscattered signals. Passive tags have fine-scale motion capture and localization accuracy up to 5–400 cm at a range of a few hundred meters [192]. Likewise, robots for in-house navigation can work by reflecting BackCom signals from tags, fixed on furniture and doors [193]. Smart cities enable communication between each outdoor or indoor object. This application of BackCom helps to energize passive devices (such as signposts at bus stops) at outdoor spots to communicate without possession of any dedicated power connection. Smart posters are capable of broadcasting music to nearby users using FM BackCom. Moreover, FM receivers in nearby cars can receive that information [96].
8.2. Unmanned Aerial Vehicles and BackCom
UAVs have revolutionized many areas of life. BackCom can be used with UAVs to extend the lifetime of communication. UAVs can be considered in relaying utilizing D2D communications in BackCom. Figure 42 shows the connectivity of BackCom tags using UAVs. The “RFLY” drone was proposed to relay information from tag to reader [180]. RFLY extends the communication range of the tag using UAV. Moreover, RFLY can read data of various tags at a time while flying in the air. Similarly, Zeng et al. highlighted opportunities and challenges for BackCom-enabled UAVs [194]. UAVs in rural areas are utilized to supply ambient power to passive sensors for efficient communication [195].
Figure 42.
UAV-based relay with antenna array in RFLY.
8.3. BackCom for Bio-Medical Applications
Tiny passive BackCom tags, with ultra-low power consumption, are widely used in the field of medical science. BackCom tags enable medical devices to communicate without power constraint, with the help of available ambient WiFi signals. Moreover, Amb-BackCom tags allow medical practitioners to diagnose patients remotely. Figure 43 demonstrates an example of WiFi-enabled tags, which can sense a patient’s conditions remotely and transmit data using WiFi signals using BackCom. A WiFi-based gesture recognition for humans uses BackCom to recognize emotions with the reflected WiFi signals [196,197].
Figure 43.
BackCom in the bio-medical field.
The reflection of WiFi signals, along with machine learning techniques, is used to identify human emotions and heartbeats [198]. This design helps smart devices to recognize a person’s emotions for the purpose of treatment. Wang et al. suggested an RF-ECG design using passive tags [199]. The RF-ECG design utilizes a BackCom tag array to extract inter-beat interval in cardiac pulses. Brain machine interface (BMI) technology also uses BackCom neural tags to monitor the neural activities of patients [200]. Similarly, RFID-based backscattering is expected to be a promising solution to empower small neural sensors used in BMI. This work also presents the measurement and design of a 1 mm backscattering device, based on a cubic loop attached to an RFID chip. The results of this design show that small loops obtain sufficient energy to energize the hardware IC when such hardware is implanted in the head of a pig. This experiment shows the possibility of tiny implant antennas in BackCom-enabled bio-medical systems.
8.4. BackCom for Logistics
BackCom, due to its popularity and cost-effectiveness, has been widely utilized in logistics [201]. BackCom assists in reading information of heavy logistics items even without picking them up. Figure 44 shows BackCom tags used in logistics. These passive tags are used for the online tracking and effective management of different items. The emerging BackCom technique in logistics is based on three-dimensional orientation tracking [202]. This technique considers an array of tags, mounted on the surface of an object, to determine three-dimensional information available online [10]. Consequently, BackCom is boosting the logistics industry.

Figure 44.
BackCom in logistics.
8.5. BackCom in Textile/Clothes
Wang et al. made the connectivity of regular clothes by transforming them into frequency modulation radio wave stations [96]. This prototype is fabricated on the chest of the cotton T-shirt by making an antenna of a conductive thread. This T-shirt can transmit information to nearby smart devices using BackCom. Project Jacquard proposes BackCom for interactive digital textiles. Figure 45 shows the movement detection on smart devices by interactive clothes. Project Jacquard suggests that interactive clothing materials be made more economical, while utilizing existing textile weaving equipment and technology [203]. Similarly, a battery-free platform is suggested for wearable devices [204]. This platform works on harvested energy generated from feet movement, in addition to Amb-BackCom.

Figure 45.
BackCom-based interactive clothing.
8.6. Environmental Monitoring Using BackCom
To address the problem of global warming and to improve the environment, backscatter tags can be used for the constant monitoring of environmental parameters (e.g., temperature, humidity, etc.) so that the effects of environmental conditions on human life can be reduced. Ambient FM BackCom can measure the moisture level in plants, with the help of wireless leaf temperature sensors [205]. BackCom-based leaf sensing system for water stress management can measure leaf canopy temperature [206]. A WiFi-powered camera and temperature sensor have been deployed in six homes of a metropolitan area to sense and communicate a real-life scenario. These devices have a communication range varying from 17 and 20 feet [130]. Battery-free connected cameras consume only W and can be used for environment monitoring [207]. Kampianakis et al. demonstrated the analog (BiS) radio enabled sensors for environmental monitoring. These sensors have a power consumption of less than 1 mW and range over 100 m. Moreover, this design allows receiver-less sensing and communication without collisions between sensors [208].
8.7. Body Area Sensor Networks Using BackCom
A body area sensor network enables the connectivity of on-body sensing devices for the measurement of different body parameters. Enabling BackCom for on-body sensors allow communication on the principle of backscattering, between body-mounted sensing tags and commercial WiFi and Bluetooth radios [138]. Figure 46 shows a Google lens as an example of a body area sensor, which uses BackCom to transmit data. This was invented by Google in 2014. This lens can measure glucose level from tears [10]. These type of devices are useful for monitoring diabetic patients for the timely injection of insulin. Other applications include the monitoring of cardiac patients in case of cardiac arrest. Furthermore, secure on-body BackCom based on signature was proposed for on-body propagation without any change in hardware [209]. Vasisht et al. suggested ReMIX, which shows deep tissue BackCom and localization [210]. ReMIX utilizes circuit non-linearities to avoid interference by shifting the frequency of reflected signals.
Figure 46.
BackCom-based lens.
8.8. Vehicle Monitoring by BackCom
National Aeronautics and Space Administration (NASA) aims to use passive WSN for a vehicle health monitoring system (VHMS) that can ensure the safety of crew and vehicles. Figure 47 illustrates the concept of the VHMS. BackCom has many applications in aerospace vehicles to obtain benefits from ubiquitous passive sensor nodes. Wilson et al. highlighted the need for a passive sensor node communication network in aerospace vehicles [211]. In local traffic management, smart signboards use backscatter tags to communicate with FM radio receivers in cars [96]. Figure 48 shows the concept of vehicle safety using BackCom. This type of communication can be used to reduce the number of accidents.
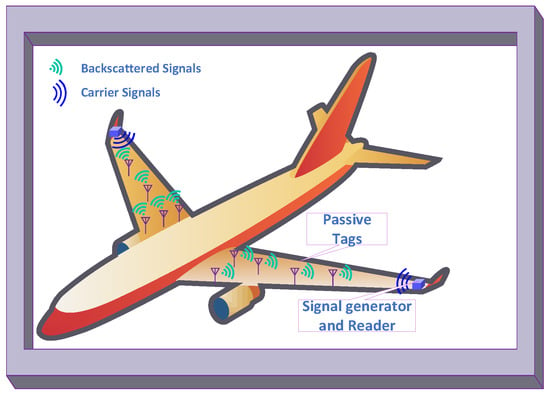
Figure 47.
Vehicle health monitoring using BackCom.
Figure 48.
Vehicle safety using BackCom.
8.9. Backscatter Sensor Network
One of the important applications of BackCom is the backscatter sensor network. The passive sensors in this type of network can sense data, and BackCom can be used for data transmission [206]. This network can be efficiently used in many battery-constrained IoT applications to extend the lifetime of the network. A practical system implementation of such a network is shown to receive continuous backscattered signals reflected from wireless sensing nodes [212]. Moreover, Liu et al. discussed the integration of RFID and wireless sensors that can be used in a wide range of applications [213]. Furthermore, three forms of network designs for integrated RFID-based WSN were proposed by Zhang et al. [214]. Researchers also presented a WSN based on RFID to eliminate the limitations of battery life [215]. Likewise, the feasibility of ambient-powered embedded sensors was proposed for soft nervous materials [216].
Discussion:Table 12 highlights the summary of BackCom applications. Various applications of BackCom are enumerated below.

Table 12.
Summary of BackCom applications.
- Smart cities allow smart posters to communicate by reflecting nearby FM receivers using BackCom [96].
- Smart homes enable robots in a room to use BackCom for sensing passages with the help of backscattered signals, received from different room items [193].
- Smart homes can use BackCom to monitor the breathing rates and heartbeats of individuals without any physical contact [188].
- UAVs along with BackCom can be used to extend the communication range [180] to supply power and to enhance the efficiency of the reader [195].
- BackCom in bio-medical applications can check the emotions and heartbeats of patients using WiFi signals [198].
- Backscatter-based neural tags were developed for the brain–machine interface and can be used to monitor neural signals [200].
- Logistics is the most popular application of BackCom. Recent developments include the three-dimensional online tracking of items using backscattered signals [10].
- BackCom enables new conductive threads in textiles to produce interactive clothes in Project Jacquard [203].
- Environmental monitoring can be done using backscatter-powered cameras and sensors [130].
- BackCom enables the body area sensor to use an eye lens for the measurement of glucose in tears [10].
- BackCom can be used in traffic monitoring to reduce the number of accidents, and BackCom allows for the communication of signboards to nearby vehicles using FM signals [96].
- A backscatter sensor network can be made by integration of WSN and RFID to eliminate limited battery life constraints [213].
9. Challenges and Future Directions
BackCom for next-generation 5G wireless has the potential to extend the boundary lines of ubiquitous computing, WSN, IoT, machine-to-machine communication, D2D communications, etc. BackCom-based computing is a new and emerging field of wireless communications [217]. There are many advantages of BackCom in various applications, but there are limitations, too. This section covers open problems and future research directions for BackCom.
9.1. Open Problems
9.1.1. Interference Management
BackCom tags communicate with weak information signals in the presence of strong carrier signals and noise in the wireless networks. Moreover, the simultaneous transmission by tags also creates interference among them. The interference management schemes such as interference cancellation and interference alignment can be used to address interference problems for certain channels [182]. To address deep fading in BackCom channels [218], transmit diversity was proposed for BackCom with single-tag antennas [219]. Zhang et al. proposed a multi-tag selection combining scheme to combat the double fading channel [220]. Moreover, they also correlated a BackCom wireless channel with Nakagami-fading channels. A parallel approach to resolving single-source fading issues is wideband Amb-BackCom, which enables a transmitter to backscatter energy across an extremely wide bandwidth, allowing any signal in the complete band to be a host for BackCom [202]. More work needs to be done to resolve interference problems in 5G with different networking scenarios, as well as in various fading channels.
9.1.2. Eavesdropping Security
BackCom considers RF carrier signals to reflect information, and these signals may be used for eavesdropping by nearby unwanted tags. Many security measures are taken to address eavesdropper attacks. These measures include the selection of the best relay scheme to avoid the eavesdropper’s attack for reliable communication [109]. Saad et al. also addressed the data theft problem by injecting noise-like signals into the carrier waves. These noise-like signals interfere with the eavesdropper’s reception to secure BackCom communication [184].
Liu et al. highlighted the black hole attack, which is a security risk in the collection of data [221]. They also suggested that an ActiveTrust scheme for WSNs to secure data. The techniques highlighted by Yang et al. can leak information from the neighboring laptop or smart device, and it has a range between 2 m (without walls) and 70 m (with walls), and a data rate of bps [222,223]. Therefore, BackCom eavesdropping security needs more attention to establish secure and reliable passive device communications for next-generation 5G networks.
9.1.3. Limited Range
Various steps have already been taken to improve the communication range of BackCom, which includes using different coherent receivers for bistatic scatter [66], long-range (LoRa) BackCom [129], BackCom quantum tunneling [164,167], power amplifiers [136], multi-antenna and MIMO systems [32,74,89,91,171,174,175], relaying [93], and D2D communication [181,182]. Researchers are also focusing on the limited range problem of BackCom, to render it suitable for long-range communication, by deploying dense power beacons [170]. BackCom aims to replace battery-powered wireless communications with passive device communication, targeting a similar communication range. Hence, there is immense need for improvement in the communication range to enhance the coverage of backscattered signals.
9.1.4. Networking
To address the networking issues in BackCom tags, Wang et al. considered all BackCom nodes as a virtual sender, while dealing transmissions by tags as rateless codes [59]. This networking scheme deals with a large number of backscatter tags (100 or 1000). Similarly, efficient communication with BackCom-enabled passive devices is one of the challenging tasks. There are number of research opportunities to use backscattered signal-based network connectivity in a ubiquitous 5G network that enable efficient networking protocols.
9.1.5. Achieving High Data Rates
Amb-BackCom enables tags to utilize available RF signals to modulate their information. The data rates of the backscattered signals are very low. Yang et al. considered a data rate for BackCom of up to bps [222], whereas a throughput of 1 kbps was achieved by Liu et al. [12]. However, the increasing need of massive IoT in 5G networks require high data rate services, which seems very difficult for BackCom considering the limitations of telecommunication laws [224] in different regions of the world to enable mm-wave-based battery-free IoT communications.
Discussion: BackCom is popular technology and has the potential to address the future needs of 5G and massive IoT connectivity with battery-less communications. Figure 49 demonstrates some challenges faced by BackCom. These are enumerated as follows:
Figure 49.
Open problems in BackCom.
- Interference management for a small powered BackCom network is hard to attain. The transmitting nodes are not able to communicate with the surrounding nodes, which causes all tags to transmit data simultaneously. Moreover, simultaneous data transmissions cause interference between backscattered signals of various nodes [77].
- The eavesdropping attack in the BackCom system is a serious security threat to data carried by backscattered signals [109].
- The communication range of backscattered signals is very less, which causes tags to communicate within a very narrow range. [129].
- Networking among tiny powered nodes needs much attention. The networking schemes should support low energy and battery-less scenarios.
- Achieving high data rates in BackCom can address the demands of future BackCom IoT devices [173].
9.2. Areas to Explore
9.2.1. New Protocols for BackCom
Recently, a battery-free cellphone was shown to operate on the principle of BackCom to achieve voice calls [8]. This battery-free cellphone design did not consider analog to digital conversion in the handset, and no digital processing module was incorporated. The analog voice signals were directly sent to (few meters distant) a base station for signal processing. This work motivates us to think about future network models for 5G that can support BackCom at the cellphone while considering all signal processing at base stations or cloud radio access networks (CRAN). This seems possible in the near future by utilizing massive MIMO and coordinated multi-point with joint transmission (CoMP-JT) to establish cell-free communications between BackCom devices [225]. The nearest AP in cell-free structures can support passive user equipment to harvest power and then transmit data using BackCom. Moreover, battery-free cellular network protocols for BackCom-enabled 5G devices can be suggested to establish effective communication in mission-critical communication without the need of the battery.
9.2.2. D2D Communications in IoT Devices
The communication between passive IoT devices using D2D communications needs continuous power supply for its operation. Various solutions are proposed to address energy efficiency in BackCom IoT devices [5,26,27,138]. It is estimated that, by 2020, there will be 26 billion IoT devices, apart from PCs, smartphones, and tablets [5]. All these devices need to be operated by battery. The limited battery life problem would be among the challenges faced by IoT technology. To combat the limited battery life challenge in IoT devices, BackCom could be one of the viable solutions, as it does not require a battery. Furthermore, cluster-based D2D communications between BackCom IoT devices can also assist each other in establishing an energy-efficient network.
The University of Washington created a backscatter-based IoT ecosystem in a suite, where web-supported tools and applications were designed to empower its users. This suite also helped individuals to understand and manage the RFID data [226]. Tozlu et al. showed the feasibility of WiFi-powered sensors in IoT [227]. This work further highlights that detecting objects in homes (such as smoke detectors, air conditioners sensors, motion detectors, etc.) is more feasible with BackCom than with traditional battery-powered counterparts.
9.2.3. Machine-to-Machine Communications (M2M)
BackCom is the key enabler for M2M in IoT [228]. M2M communications are widely used in emerging autonomous applications. M2M communications consider small chunks of sensed data from different sensors, and these chunks can be transmitted rapidly to establish low latency communications. The Amb-BackCom tags can transmit the small amount of data by backscattering cellular signals [229]. BackCom can be employed in M2M. This technique allows driverless cars and other autonomous vehicles to communicate with each other using BackCom. Eventually, M2M communications can be used to save power and to maintain reliable communications. Amb-BackCom is also used in M2M communication [230], to maximize energy harvesting and data transmission.
9.2.4. Artificial Intelligence and BackCom
Artificial intelligence, machine learning, and deep neural networks are revolutionizing technology in almost every discipline of engineering. Wireless communications is not an exception. An introduction to a machine-learning-based communication system highlights different applications of machine learning to a wireless communication system architecture [231,232,233,234]. This work includes an auto-encoder, which can jointly learn the transmission and reception functions in the absence of previous knowledge. Similarly, machine learning tools equivalent to digital signal processing components of wireless communications are discussed in [235]. This work shows that a convolutional layer in deep learning is similar to a finite impulse response (FIR) filter, and a recurrent cell in a neural network resembles an infinite impulse response (IIR). Machine learning can be used with BackCom [236] to enhance the performance of a BackCom network.
Word-Fi is an accurate handwriting system using BackCom and machine learning to recognize tiny gestures [237]. In order to maximize the network performance in an RF-powered cognitive radio network, an online reinforcement learning approach was proposed by Van et al. [238]. Furthermore, a deep learning model usually includes an input layer, deep hidden layers, and an output layer. This model learns by training. The training set includes the input and desired output for training. A deep-learning-based communication model for wireless communications can extract the relationship between the input and output, referred to as the trained model. The obtained relation can be used at the receiver for the detection of unknown transmitted information.
A deep-learning-based algorithm was proposed for a communication system. It did not require any mathematical model for channels between transmitters and receivers [239]. This technique can extract features of channels with the help of supervised training at the receiver and reinforcement training at the transmitter. Moreover, this technique could be used for detecting features of BackCom channels in battery-free communication. Likewise, various deep-learning-based channel coding algorithms [240,241] have been suggested for wireless communications, and these could be utilized for the extraction of tag information.
Other authors proposed a WiFi-based gesture recognition system through the reflection of WiFi signals and machine learning techniques [196,197]. These works improved the performance in gesture recognition. Similarly, optimization in the wireless network based on deep learning shows a decrease in computation cost without any effect on optimality. Optimization using deep learning in BackCom may be an exciting area for researchers [242]. Researchers from the Massachusetts Institute of Technology (MIT) explained the utilization of Amb-BackCom (using WiFi signals) and machine learning techniques to detect heart rate and breathing conditions without physical contact. This work is just the beginning of the revolutionary wireless communications with Amb-BackCom radio signals [188]. More research can still be done by using deep learning techniques for BackCom.
9.2.5. BackCom Channel Coding
The traditional wireless communications consider channel coding and modern error correcting codes for high throughput and error correction. These modern error correcting codes include low density parity check (LDPC) codes and the most recent polar codes. The LDPC and polar codes have been adopted in 5G standards to enable reliable data transmission with high data rates. The traditional coding schemes need an encoder to encode the information into a message by adding redundancy. These encoded messages are then transmitted to a wireless channel, and the decoder then decodes the data from the received signals at the receiver end. Usually, these encoders and decoders are designed for battery-powered digital communication systems, nor for BackCom. Coding schemes for BackCom should be considered.
Durgin et al. tried to improve the coding rate by proposing improved channel codes for BackCom, but there is still much room for improvement in data rates [71]. Similarly, the work in [243] shows the signal capacity could be achieved when RF signal distribution is not equiprobably backscattered by tag. Moreover, it has also been realized that the capacity of complex Gaussian signals was not exactly twice that of real Gaussian channels. Varner et al. presented the effects of partitioning scattering arrays with retro-directive structures on channel capacity [244]. These structures improved the range and channel capacity, and allowed passive tags to operate in mm-wave frequencies. The latest polar codes, discovered by Arikan, work on the phenomenon of channel polarization [245]. Polar codes are famous for their low complexity and have achieved the capacity of a binary symmetric channel. Polar codes may be used with BackCom for the improvement of data rates. Moreover, modern error correcting codes, the encoder and decoder for backscatter tags, can be an exciting research direction to enable BackCom for high data rates. Similarly, the deep-learning-based joint source-channel coding technique [240] can be used for structured data scenarios of BackCom.
Discussion: The future directions for BackCom is shown in Figure 50. The recent advanced tools such as deep neural networks, machine learning, and artificial intelligence have helped us to process big data in different fields of science and technology. In the same way, the high bandwidth of mm-waves in 5G, D2D communications in IoT and modern error correcting codes can be used for sending information at higher data rates over a communication channel near the Shannon capacity. These progressive tools lead us to expect similar deep learning system models for BackCom in addition to the modern error correcting codes.
Figure 50.
Future directions.
- It may be possible for BackCom in the near future to replace the battery-powered communication systems in IoTs and cellular communications.
- The deep learning algorithms at the cloud radio access of 5G network architecture may execute the signal processing task for low energy systems [242]. Moreover, the signal processing work may be done by training real BackCom systems and by generating similar patterns with the help of deep neural networks or a Generative Adaptive Neural Network (GANN).
- The modern short block length error correcting codes, such as, polar codes are adopted in the 5G control channel, and can be explored for improving data rates in BackCom [245]. This higher data rate communication at the tag side and speedy processing at the cloud radio access network can use artificial intelligence to change the future of BackCom.
10. Conclusions
In this survey, we presented BackCom as a solution to address energy problems in emerging wireless heterogeneous networks. First, we explored the limited battery life problem from a cellular perspective, in a disaster management scenario, and in the IoT context, since limited battery life is the primary cause of power interruption in wireless communications. Next, we suggested BackCom as a solution to the energy problem and elaborated the basics of signal backscattering, the evolution of BackCom, and BackCom tag’s architecture in addition to various types of BackCom. We explained various signal processing aspects in BackCom such as channel coding, interference, decoding, and signal detection schemes including coherent and non-coherent detection techniques. Moreover, we discussed BackCom communication modes involving half-duplex and full-duplex modes followed by modulation techniques and multiple access schemes. Subsequently, we highlighted different power sources for BackCom in addition to efficient energy and data transfer approaches, while considering scheduling and resource allocations schemes for uninterrupted communications. The BackCom coverage problem was then explored with different solutions for range extension. Afterward, we illustrated security measures and reliability techniques for BackCom followed by BackCom applications. Finally, we concluded with current challenges and future directions for BackCom to address the high-technology needs of battery-free communication in next-generation 5G wireless communications.
Author Contributions
Conceptualization, M.L.M. and N.S.; methodology, A.R.; investigation, M.L.M.; resources, M.L.M.; data curation, M.L.M.; writing—original draft preparation, M.L.M.; writing—review and editing, N.S. and A.R.; supervision, N.S., A.R. and D.R.S.; project administration, N.S. and D.R.S.; funding acquisition, N.S. and D.R.S.
Acknowledgments
This research was supported by the Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2016R1D1A1B03935633).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Networking Index, C.V. Cisco Visual Networking Index: Forecast and Methodology, 2016–2021; White Paper; Cisco Systems, Inc.: San Jose, CA, USA, 2017. [Google Scholar]
- Heuveldop, N. Ericsson Mobility Report; Ericsson AB, Technol. Emerg. Business, Stockholm, Sweden, Tech. Rep. EAB-18 4510; Ericsson: Stockholm, Sweden, 2015. [Google Scholar]
- Kutty, S.; Sen, D. Beamforming for millimeter wave communications: An inclusive survey. IEEE Commun. Surv. Tutor. 2016, 18, 949–973. [Google Scholar] [CrossRef]
- Ahmad, H.; Agiwal, M.; Saxena, N.; Roy, A. D2D-based Survival on Sharing for critical communications. Wirel. Netw. 2018, 24, 1–13. [Google Scholar] [CrossRef]
- Jammes, F. Internet of Things in Energy Efficiency: The Internet of Things (Ubiquity symposium). Ubiquity 2016, 2016, 1–8. [Google Scholar] [CrossRef]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless charging technologies: Fundamentals, standards, and network applications. IEEE Commun. Surv. Tutor. 2016, 18, 1413–1452. [Google Scholar] [CrossRef]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless networks with RF energy harvesting: A contemporary survey. IEEE Commun. Surv. Tutor. 2015, 17, 757–789. [Google Scholar] [CrossRef]
- Talla, V.; Kellogg, B.; Gollakota, S.; Smith, J.R. Battery-free cellphone. In Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies; ACM: New York, NY, USA, 2017; Volume 1, p. 25. [Google Scholar]
- Chawla, V.; Ha, D.S. An overview of passive RFID. IEEE Commun. Mag. 2007, 45, 11–17. [Google Scholar] [CrossRef]
- Liu, W.; Huang, K.; Zhou, X.; Durrani, S. Backscatter communications for internet-of-things: Theory and applications. arXiv, 2017; arXiv:1701.07588v1. [Google Scholar]
- Jankowski-Mihułowicz, P.; Węglarski, M.; Pitera, G.; Kawalec, D.; Lichoń, W. Development board of the autonomous semi-passive RFID transponder. Bull. Pol. Acad. Sci. Tech. Sci. 2016, 64, 647–654. [Google Scholar] [CrossRef]
- Liu, V.; Parks, A.; Talla, V.; Gollakota, S.; Wetherall, D.; Smith, J.R. Ambient backscatter: Wireless communication out of thin air. In Proceedings of the ACM SIGCOMM 2013 conference on SIGCOMM, Hong Kong, China, 12–16 August 2013; Volume 43, pp. 39–50. [Google Scholar]
- Van Huynh, N.; Hoang, D.T.; Lu, X.; Niyato, D.; Wang, P.; Kim, D.I. Ambient backscatter communications: A contemporary survey. IEEE Commun. Surv. Tutor. 2018, 20, 2889–2922. [Google Scholar] [CrossRef]
- Agiwal, M.; Roy, A.; Saxena, N. Next generation 5G wireless networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2016, 18, 1617–1655. [Google Scholar] [CrossRef]
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.; Zhang, J.C. What will 5G be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Ghosh, A.; Thomas, T.A.; Cudak, M.C.; Ratasuk, R.; Moorut, P.; Vook, F.W.; Rappaport, T.S.; MacCartney, G.R.; Sun, S.; Nie, S. Millimeter-wave enhanced local area systems: A high-data-rate approach for future wireless networks. IEEE J. Sel. Areas Commun. 2014, 32, 1152–1163. [Google Scholar] [CrossRef]
- Liu, X.; Zhang, X.; Jia, M.; Fan, L.; Lu, W.; Zhai, X. 5G-based green broadband communication system design with simultaneous wireless information and power transfer. Phys. Commun. 2018, 28, 130–137. [Google Scholar] [CrossRef]
- Hoang, D.T.; Niyato, D. RF-Based Energy Harvesting Cognitive Cellular Networks. In Handbook of Cognitive Radio; Springer: Singapore, 2017; pp. 1–43. [Google Scholar]
- Tu, L.T.; Di Renzo, M. Analysis of millimeter wave cellular networks with simultaneous wireless information and power transfer. In Proceedings of the IEEE International Conference on Recent Advances in Signal Processing, Telecommunications & Computing (SigTelCom), Da Nang, Vietnam, 9–11 January 2017; pp. 39–43. [Google Scholar]
- Freidl, P.F.; Gadringer, M.E.; Amschl, D.; Bcõsch, W. mm-Wave RFID for IoT applications. In Proceedings of the IEEE Integrated Nonlinear Microwave and Millimetre-wave Circuits Workshop, (INMMiC), Graz, Austria, 20–21 April 2017; pp. 1–3. [Google Scholar]
- Denicke, E.; Hartmann, H.; Peitzmeier, N.; Geck, B. Backscatter Beamforming: A Transponder for Novel MIMO RFID Transmission Schemes. IEEE J. Radio Freq. Identif. 2018, 2, 80–85. [Google Scholar] [CrossRef]
- Wang, L.; Elkashlan, M.; Heath, R.W.; Di Renzo, M.; Wong, K.K. Millimeter wave power transfer and information transmission. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Khan, T.A.; Alkhateeb, A.; Heath, R.W. Millimeter wave energy harvesting. IEEE Trans. Wirel. Commun. 2016, 15, 6048–6062. [Google Scholar] [CrossRef]
- Prasad, A.; Kunz, A.; Velev, G.; Samdanis, K.; Song, J. Energy-efficient D2D discovery for proximity services in 3GPP LTE-advanced networks: ProSe discovery mechanisms. IEEE Veh. Technol. Mag. 2014, 9, 40–50. [Google Scholar] [CrossRef]
- Hunukumbure, M.; Moulsley, T.; Oyawoye, A.; Vadgama, S.; Wilson, M. D2D for energy efficient communications in disaster and emergency situations. In Proceedings of the IEEE 21st International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Primosten, Croatia, 18–20 September 2013; pp. 1–5. [Google Scholar]
- Sarwesh, P.; Shet, N.S.V.; Chandrasekaran, K. Energy-Efficient Network Architecture for IoT Applications. In Beyond the Internet of Things; Springer: Berlin, Germany, 2017; pp. 119–144. [Google Scholar]
- Zhang, P.; Ganesan, D.; Lu, B. Quarkos: Pushing the operating limits of micro-powered sensors. In Proceedings of the 14th USENIX conference on Hot Topics in Operating Systems, Santa Ana Pueblo, NM, USA, 13–15 May 2013; p. 7. [Google Scholar]
- Magno, M.; Aoudia, F.A.; Gautier, M.; Berder, O.; Benini, L. WULoRa: An energy efficient IoT end-node for energy harvesting and heterogeneous communication. In Proceedings of the Conference on Design, Automation & Test in Europe, Lausanne, Switzerland, 27–31 March 2017; pp. 1532–1537. [Google Scholar]
- Wang, G.; Bytyn, A.; Khajavi, D.; Wang, Y.; Negra, R.; Ascheid, G. Power Efficiency of Millimeter Wave Transmission Systems with Large Number of Antennas. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–6. [Google Scholar]
- Bogale, T.E.; Le, L.B. Massive MIMO and mmWave for 5G wireless HetNet: Potential benefits and challenges. IEEE Veh. Technol. Mag. 2016, 11, 64–75. [Google Scholar] [CrossRef]
- Zhang, P.; Hu, P.; Pasikanti, V.; Ganesan, D. Ekhonet: High speed ultra low-power backscatter for next generation sensors. In Proceedings of the 20th Annual International Conference on Mobile Computing and Networking, Maui, HI, USA, 7–11 September 2014; pp. 557–568. [Google Scholar]
- Parks, A.N.; Liu, A.; Gollakota, S.; Smith, J.R. Turbocharging ambient backscatter communication. ACM SIGCOMM Comput. Commun. Rev. 2015, 44, 619–630. [Google Scholar] [CrossRef]
- Hu, P.; Zhang, P.; Ganesan, D. Laissez-faire: Fully asymmetric backscatter communication. ACM SIGCOMM Comput. Commun. Rev. 2015, 45, 255–267. [Google Scholar] [CrossRef]
- Zhang, P.; Bharadia, D.; Joshi, K.; Katti, S. Hitchhike: Practical backscatter using commodity wifi. In Proceedings of the 14th ACM Conference on Embedded Network Sensor Systems CD-ROM, Stanford, CA, USA, 14–16 November 2016; pp. 259–271. [Google Scholar]
- Kellogg, B.; Talla, V.; Gollakota, S.; Smith, J.R. Passive Wi-Fi: Bringing Low Power to Wi-Fi Transmissions; USENIX Association: Berkeley, CA, USA, 2016; Volume 16, pp. 151–164. [Google Scholar]
- Iyer, V.; Talla, V.; Kellogg, B.; Gollakota, S.; Smith, J. Inter-technology backscatter: Towards internet connectivity for implanted devices. In Proceedings of the 2016 ACM SIGCOMM Conference, Florianopolis, Brazil, 22–26 August 2016; pp. 356–369. [Google Scholar]
- Kellogg, B.; Parks, A.; Gollakota, S.; Smith, J.R.; Wetherall, D. Wi-Fi backscatter: Internet connectivity for RF-powered devices. In Proceedings of the 2014 ACM Conference on SIGCOMM, Chicago, IL, USA, 17–22 August 2014; Volume 44, pp. 607–618. [Google Scholar]
- Brooker, G.; Gomez, J. Lev Termen’s Great Seal bug analyzed. IEEE Aerosp. Electron. Syst. Mag. 2013, 28, 4–11. [Google Scholar] [CrossRef]
- Dobkin, D.M. The rf in RFID: uhf RFID in Practice; Newnes: St Albans, UK, 2012. [Google Scholar]
- Stockman, H. Communication by means of reflected power. Proc. IRE 1948, 36, 1196–1204. [Google Scholar] [CrossRef]
- Abramson, N. THE ALOHA SYSTEM: Another alternative for computer communications. In Proceedings of the November 17–19, 1970, Fall Joint Computer Conference, Houston, TX, USA, 17–19 November 1970; pp. 281–285. [Google Scholar]
- Riley, P.F. The tolls of privacy: An underestimated roadblock for electronic toll collection usage. Comput. Law Secur. Rev. 2008, 24, 521–528. [Google Scholar] [CrossRef]
- Landt, J. The history of RFID. IEEE Potentials 2005, 24, 8–11. [Google Scholar] [CrossRef]
- Want, R.; Fishkin, K.P.; Gujar, A.; Harrison, B.L. Bridging physical and virtual worlds with electronic tags. In Proceedings of the SIGCHI conference on Human Factors in Computing Systems, Pittsburgh, PA, USA, 15–20 May 1999; pp. 370–377. [Google Scholar]
- Fuschini, F.; Piersanti, C.; Paolazzi, F.; Falciasecca, G. Analytical approach to the backscattering from UHF RFID transponder. IEEE Antennas Wirel. Propag. Lett. 2008, 7, 33–35. [Google Scholar] [CrossRef]
- Finkenzeller, K. RFID Handbook: Fundamentals and Applications in Contactless Smart Cards, Radio Frequency Identification and Near-Field Communication; John Wiley & Sons: New York, NY, USA, 2010. [Google Scholar]
- Nath, B.; Reynolds, F.; Want, R. RFID technology and applications. IEEE Pervasive Comput. 2006, 22–24. [Google Scholar] [CrossRef]
- Hatch, B. Hacking Linux Exposed: Linux Security & Solutions, Osborne; McGraw-Hill Education: New York, NY, USA, 2001. [Google Scholar]
- Global, E. EPC Radio-Frequency Identity Protocols Class-1 Generation-2 UHF RFID Protocol for Communications at 860 MHz–960 MHz; GS1: Brussels, Belgium, 2008; Volume 1, p. 23. [Google Scholar]
- Kimionis, J.; Bletsas, A.; Sahalos, J.N. Increased range bistatic scatter radio. IEEE Trans. Commun. 2014, 62, 1091–1104. [Google Scholar] [CrossRef]
- Ensworth, J.F.; Reynolds, M.S. Every smart phone is a backscatter reader: Modulated backscatter compatibility with bluetooth 4.0 low energy (ble) devices. In Proceedings of the 2015 IEEE International Conference on RFID (RFID), San Diego, CA, USA, 15–17 April 2015; pp. 78–85. [Google Scholar]
- Kim, S.H.; Kim, D.I. Hybrid backscatter communication for wireless-powered heterogeneous networks. IEEE Trans. Wirel. Commun. 2017, 16, 6557–6570. [Google Scholar] [CrossRef]
- Pérez-Penichet, C.; Noda, C.; Varshney, A.; Voigt, T. Battery-free 802.15. 4 receiver. In Proceedings of the 17th ACM/IEEE International Conference on Information Processing in Sensor Networks, Porto, Portugal, 11–13 April 2018; pp. 164–175. [Google Scholar]
- Xia, H.; Li, Y.; Zhang, H. Throughput Maximization for Wireless Powered Communications Harvesting from Non-dedicated Sources. arXiv, 2017; arXiv:1701.07153. [Google Scholar]
- Ju, H.; Zhang, R. Throughput maximization in wireless powered communication networks. IEEE Trans. Wirel. Commun. 2014, 13, 418–428. [Google Scholar] [CrossRef]
- Gummeson, J.; Zhang, P.; Ganesan, D. Flit: A bulk transmission protocol for RFID-scale sensors. In Proceedings of the 10th International Conference on Mobile Systems, Applications, and Services, Low Wood Bay, Lake District, UK, 25–29 June 2012; pp. 71–84. [Google Scholar]
- Zhang, P.; Ganesan, D. Enabling Bit-by-Bit Backscatter Communication in Severe Energy Harvesting Environments; USENIX Association: Berkeley, CA, USA, 2014; pp. 345–357. [Google Scholar]
- Hessar, M.; Najafi, A.; Gollakota, S. NetScatter: Enabling Large-Scale Backscatter Networks. arXiv, 2018; arXiv:1808.05195. [Google Scholar]
- Wang, J.; Hassanieh, H.; Katabi, D.; Indyk, P. Efficient and reliable low-power backscatter networks. In Proceedings of the ACM SIGCOMM 2012 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Helsinki, Finland, 13–17 August 2012; pp. 61–72. [Google Scholar]
- Griffin, J.D.; Durgin, G.D. Complete link budgets for backscatter-radio and RFID systems. IEEE Antennas Propag. Mag. 2009, 51, 11–25. [Google Scholar] [CrossRef]
- Su, Z.; Cheung, S.C.; Chu, K.T. Investigation of radio link budget for UHF RFID systems. In Proceedings of the 2010 IEEE International Conference on RFID-Technology and Applications (RFID-TA), Guangzhou, China, 17–19 June 2010; pp. 164–169. [Google Scholar]
- Griffin, J.D.; Durgin, G.D. Gains for RF tags using multiple antennas. IEEE Trans. Antennas Propag. 2008, 56, 563–570. [Google Scholar] [CrossRef]
- Griffin, J.D.; Durgin, G.D. Multipath fading measurements at 5.8 GHz for backscatter tags with multiple antennas. IEEE Trans. Antennas Propag. 2010, 58, 3693–3700. [Google Scholar] [CrossRef]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Wang, G.; Gao, F.; Fan, R.; Tellambura, C. Ambient backscatter communication systems: Detection and performance analysis. IEEE Trans. Commun. 2016, 64, 4836–4846. [Google Scholar] [CrossRef]
- Fasarakis-Hilliard, N.; Alevizos, P.N.; Bletsas, A. Coherent detection and channel coding for bistatic scatter radio sensor networking. IEEE Trans. Commun. 2015, 63, 1798–1810. [Google Scholar] [CrossRef]
- Lu, K.; Wang, G.; Qu, F.; Zhong, Z. Signal detection and BER analysis for RF-powered devices utilizing ambient backscatter. In Proceedings of the International Conference on Wireless Communications & Signal Processing (WCSP), Nanjing, China, 15–17 October 2015; pp. 1–5. [Google Scholar]
- Hu, P.; Zhang, P.; Ganesan, D. Leveraging interleaved signal edges for concurrent backscatter. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2015, 18, 26–31. [Google Scholar] [CrossRef]
- Zhao, J.; Gong, W.; Liu, J. Spatial Stream Backscatter Using Commodity WiFi. In Proceedings of the 16th Annual International Conference on Mobile Systems, Applications, and Services, Munich, Germany, 10–15 June 2018. [Google Scholar]
- US EGU. Class 1 Generation 2 UHF RFID Protocol for Operation at 860 MHz-960 MHz; Version 2.0.1. Available online: https://www.gs1.org/sites/default/files/docs/epc/Gen2_Protocol_Standard.pdf (accessed on 11 September 2018).
- Durgin, G.D.; Degnan, B.P. Improved Channel Coding for Next-Generation RFID. IEEE J. Radio Freq. Identif. 2017, 1, 68–74. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, G.; Dou, Z.; Zhong, Z. Coding and detection schemes for ambient backscatter communication systems. IEEE Access 2017, 5, 4947–4953. [Google Scholar] [CrossRef]
- Alevizos, P.N.; Bletsas, A. Noncoherent composite hypothesis testing receivers for extended range bistatic scatter radio WSNs. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8 June 2015; pp. 4448–4453. [Google Scholar]
- Boyer, C.; Roy, S. —Invited Paper—Backscatter Communication and RFID: Coding, Energy, and MIMO Analysis. IEEE Trans. Commun. 2014, 62, 770–785. [Google Scholar] [CrossRef]
- Cnaan-On, I.; Harms, A.; Krolik, J.L.; Calderbank, A.R. Run-length limited codes for backscatter communication. In Proceedings of the 2017 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), New Orleans, LA, USA, 5–9 March 2017; pp. 6110–6114. [Google Scholar]
- Kim, Y.G.; Vinck, H. Anti-Collision Algorithms for FM0 Code and Miller Subcarrier Sequence in RFID Applications. IEEE Trans. Veh. Technol. 2018, 67, 5168–5173. [Google Scholar] [CrossRef]
- Liu, W.; Huang, K.; Zhou, X.; Durrani, S. Full-duplex backscatter interference networks based on time-hopping spread spectrum. IEEE Trans. Wirel. Commun. 2017, 16, 4361–4377. [Google Scholar] [CrossRef]
- Sabharwal, A.; Schniter, P.; Guo, D.; Bliss, D.W.; Rangarajan, S.; Wichman, R. In-band full-duplex wireless: Challenges and opportunities. IEEE J. Sel. Areas Commun. 2014, 32, 1637–1652. [Google Scholar] [CrossRef]
- Bi, S.; Ho, C.K.; Zhang, R. Wireless powered communication: Opportunities and challenges. IEEE Commun. Mag. 2015, 53, 117–125. [Google Scholar] [CrossRef]
- Niyato, D.; Hossain, E.; Kim, D.I.; Shafai, L.; Bhargava, V. Wireless-Powered Communication Networks; Cambridge University Press: Cambridge, UK, 2016. [Google Scholar]
- Alhassoun, M.; Varner, M.A.; Durgin, G.D. Design and evaluation of a multi-modulation retrodirective RFID tag. In Proceedings of the 2018 IEEE International Conference on Design and Evaluation of a Multi-Modulation Retrodirective RFID Tag, RFID (RFID), Orlando, FL, USA, 10–12 April 2018; pp. 1–8. [Google Scholar]
- Bletsas, A.; Siachalou, S.; Sahalos, J.N. Anti-collision backscatter sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 5018–5029. [Google Scholar] [CrossRef]
- Ou, J.; Li, M.; Zheng, Y. Come and be served: Parallel decoding for cots rfid tags. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking, Paris, France, 7–11 September 2015; pp. 500–511. [Google Scholar]
- Qian, J.; Gao, F.; Wang, G.; Jin, S.; Zhu, H. Noncoherent detections for ambient backscatter system. IEEE Trans. Wirel. Commun. 2017, 16, 1412–1422. [Google Scholar] [CrossRef]
- Guo, H.; Zhang, Q.; Xiao, S.; Liang, Y.C. Exploiting multiple antennas for cognitive ambient backscatter communication. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Wang, G.; Gao, F.; Dou, Z.; Tellambura, C. Uplink detection and BER analysis for ambient backscatter communication systems. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Kim, T.; Lee, W. Exploiting Residual Channel for Implicit Wi-Fi Backscatter Networks. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 1268–1276. [Google Scholar]
- Tao, Q.; Zhong, C.; Lin, H.; Zhang, Z. Symbol Detection of Ambient Backscatter Systems with Manchester Coding. IEEE Trans. Wirel. Commun. 2018, 17, 4028–4038. [Google Scholar] [CrossRef]
- Yang, G.; Liang, Y.C.; Zhang, Q. Cooperative receiver for ambient backscatter communications with multiple antennas. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Qian, J.; Gao, F.; Wang, G. Signal detection of ambient backscatter system with differential modulation. In Proceedings of the 2016 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Shanghai, China, 20–25 March 2016; pp. 3831–3835. [Google Scholar]
- Mat, Z.; Zeng, T.; Wang, G.; Gao, F. Signal detection for ambient backscatter system with multiple receiving antennas. In Proceedings of the 2015 IEEE 14th Canadian Workshop on Information Theory (CWIT), St. John’s, NL, Canada, 6–9 July 2015; pp. 50–53. [Google Scholar]
- Kang, X.; Ho, C.K.; Sun, S. Full-duplex wireless-powered communication network with energy causality. IEEE Trans. Wirel. Commun. 2015, 14, 5539–5551. [Google Scholar] [CrossRef]
- Munir, D.; Shah, S.T.; Lee, W.J.; Chung, M.Y. Low-power backscatter relay network. In Proceedings of the 11th International Conference on Ubiquitous Information Management and Communication, Beppu, Japan, 5–7 January 2017; p. 52. [Google Scholar]
- Liu, V.; Talla, V.; Gollakota, S. Enabling instantaneous feedback with full-duplex backscatter. In Proceedings of the 20th Annual International Conference on Mobile Computing and Networking, Maui, HI, USA, 7–11 September 2014; pp. 67–78. [Google Scholar]
- Lyu, B.; Yang, Z.; Gui, G.; Feng, Y. Throughput maximization in backscatter assisted wireless powered communication networks. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2017, 100, 1353–1357. [Google Scholar] [CrossRef]
- Wang, A.; Iyer, V.; Talla, V.; Smith, J.R.; Gollakota, S. FM Backscatter: Enabling Connected Cities and Smart Fabrics; USENIX Association: Berkeley, CA, USA, 2017; pp. 243–258. [Google Scholar]
- Ensworth, J.F.; Hoang, A.T.; Phu, T.Q.; Reynolds, M.S. Full-duplex Bluetooth low energy (BLE) compatible backscatter communication system for mobile devices. In Proceedings of the 2017 IEEE Topical Conference on Wireless Sensors and Sensor Networks (WiSNet), Phoenix, AZ, USA, 15–18 January 2017; pp. 45–48. [Google Scholar]
- Thomas, S.; Reynolds, M.S. QAM backscatter for passive UHF RFID tags. In Proceedings of the 2010 IEEE International Conference On RFID, Orlando, FL, USA, 14–16 April 2010; pp. 210–214. [Google Scholar]
- Ju, H.; Zhang, R. User cooperation in wireless powered communication networks. In Proceedings of the 2014 IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 1430–1435. [Google Scholar]
- Wang, R.; Brown, D.R. Throughput maximization in wireless powered communication networks with energy saving. In Proceedings of the 2014 48th Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 2–5 November 2014; pp. 516–520. [Google Scholar]
- Lyu, B.; Yang, Z.; Gui, G.; Sari, H. Optimal time allocation in backscatter assisted wireless powered communication networks. Sensors 2017, 17, 1258. [Google Scholar] [CrossRef]
- Xu, W.; Piechocki, R.J.; Hilton, G. Probabilistic data association for wireless passive body sensor networks. In Proceedings of the 2013 IEEE 15th International Conference on e-Health Networking, Applications & Services (Healthcom), Lisbon, Portugal, 9–12 October 2013; pp. 140–144. [Google Scholar]
- Mutti, C.; Floerkemeier, C. CDMA-based RFID systems in dense scenarios: Concepts and challenges. In Proceedings of the 2008 IEEE International Conference on RFID, Las Vegas, NV, USA, 16–17 April 2008; pp. 215–222. [Google Scholar]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Wireless information and power transfer: Energy efficiency optimization in OFDMA systems. IEEE Trans. Wirel. Commun. 2013, 12, 6352–6370. [Google Scholar] [CrossRef]
- Saito, Y.; Benjebbour, A.; Kishiyama, Y.; Nakamura, T. System-level performance evaluation of downlink non-orthogonal multiple access (NOMA). In Proceedings of the 2013 IEEE 24th International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC), London, UK, 8–11 September 2013; pp. 611–615. [Google Scholar]
- Ali, M.S.; Tabassum, H.; Hossain, E. Dynamic user clustering and power allocation for uplink and downlink non-orthogonal multiple access (NOMA) systems. IEEE Access 2016, 4, 6325–6343. [Google Scholar] [CrossRef]
- Jain, M.; Choi, J.I.; Kim, T.; Bharadia, D.; Seth, S.; Srinivasan, K.; Levis, P.; Katti, S.; Sinha, P. Practical, real-time, full duplex wireless. In Proceedings of the 17th Annual International Conference on Mobile Computing and Networking, Las Vegas, NV, USA, 19–23 September 2011; pp. 301–312. [Google Scholar]
- Smida, B.; Khaledian, S. ReflectFX: In-Band Full-Duplex Wireless Communication by Means of Reflected Power. IEEE Trans. Commun. 2017, 65, 2207–2219. [Google Scholar] [CrossRef]
- Wang, X.; Su, Z.; Wang, G. Relay selection for secure backscatter wireless communications. Electron. Lett. 2015, 51, 951–952. [Google Scholar] [CrossRef]
- Arnitz, D.; Muehlmann, U.; Witrisal, K. Tag-based sensing and positioning in passive UHF RFID: Tag reflection. In Proceedings of the 3rd Int EURASIP Workshop on RFID Technology, Cartagena, Spain, 6–7 September 2010; Available online: https://www.spsc.tugraz.at/system/files/arnitzeurasip10.pdf (accessed on 9 September 2018).
- Qian, J.; Parks, A.N.; Smith, J.R.; Gao, F.; Jin, S. IoT communications with M-PSK modulated ambient backscatter: Algorithm, analysis, and implementation. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Daskalakis, S.N.; Correia, R.; Goussetis, G.; Tentzeris, M.M.; Carvalho, N.B.; Georgiadis, A. Spectrally Efficient 4-PAM Ambient FM Backscattering for Wireless Sensing and RFID Applications. In Proceedings of the 2018 IEEE/MTT-S International Microwave Symposium-IMS, Philadelphia, PA, USA, 10–15 June 2018; pp. 266–269. [Google Scholar]
- Kapetanovic, Z.; Talla, V.; Parks, A.; Qian, J.; Smith, J.R. Wireless quantization index modulation: Enabling communication through existing signals. In Proceedings of the 2018 IEEE International Conference on RFID (RFID), Orlando, FL, USA, 10–12 April 2018; pp. 1–8. [Google Scholar]
- Yang, G.; Liang, Y.C.; Zhang, R.; Pei, Y. Modulation in the air: Backscatter communication over ambient OFDM carrier. IEEE Trans. Commun. 2018, 66, 1219–1233. [Google Scholar] [CrossRef]
- Darsena, D.; Gelli, G.; Verde, F. Modeling and performance analysis of wireless networks with ambient backscatter devices. IEEE Trans. Commun. 2017, 65, 1797–1814. [Google Scholar] [CrossRef]
- Correia, R.; Carvalho, N.B. Dual-Band High Order Modulation Ambient Backscatter. In Proceedings of the 2018 IEEE/MTT-S International Microwave Symposium-IMS, Philadelphia, PA, USA, 10–15 June 2018; pp. 270–273. [Google Scholar]
- Liu, W.; Liang, Y.C.; Li, Y.; Vucetic, B. On Ambient Backscatter Multiple-Access Systems. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–7. [Google Scholar]
- Wei, W.; Su, J.; Song, H.; Wang, H.; Fan, X. CDMA-based anti-collision algorithm for EPC global C1 Gen2 systems. Telecommun. Syst. 2018, 67, 63–71. [Google Scholar] [CrossRef]
- Kim, T.Y.; Kim, D.I. Novel Sparse-Coded Ambient Backscatter Communication for Massive IoT Connectivity. arXiv, 2018; arXiv:1806.02975. [Google Scholar]
- Guo, J.; Zhou, X.; Durrani, S.; Yanikomeroglu, H. Backscatter communications with NOMA. In Proceedings of the 2018 15th International Symposium on Wireless Communication Systems (ISWCS), Lisbon, Portugal, 28–31 August 2018; pp. 1–5. [Google Scholar]
- Bi, S.; Zeng, Y.; Zhang, R. Wireless powered communication networks: An overview. IEEE Wirel. Commun. 2016, 23, 10–18. [Google Scholar] [CrossRef]
- Texas Instruments: CC2564MODA Bluetooth HCI Module. 2018. Available online: http://www.digikey.com/product-detail/en/CC2564BRVMR/CC2564BRVMR-ND/4915497 (accessed on 7 September 2018).
- Texas Instruments CC3200 WiFi SOC. 2018. Available online: http://www.ti.com/lit/ds/symlink/cc3200.pdf (accessed on 9 September 2018).
- Vougioukas, G.; Dimitriou, A.; Bletsas, A.; Sahalos, J. Practical Energy Harvesting for Batteryless Ambient Backscatter Sensors. Electronics 2018, 7, 95. [Google Scholar] [CrossRef]
- Parks, A.N.; Sample, A.P.; Zhao, Y.; Smith, J.R. A wireless sensing platform utilizing ambient RF energy. In Proceedings of the IEEE Topical Conference on Power Amplifiers for Wireless and Radio Applications (PAWR), Santa Clara, CA, USA, 20–20 January 2013; pp. 160–162. [Google Scholar]
- Piñuela, M.; Mitcheson, P.D.; Lucyszyn, S. Ambient RF energy harvesting in urban and semi-urban environments. IEEE Trans. Microw. Theory Tech. 2013, 61, 2715–2726. [Google Scholar] [CrossRef]
- Yang, G.; Ho, C.K.; Guan, Y.L. Multi-antenna wireless energy transfer for backscatter communication systems. IEEE J. Sel. Areas Commun. 2015, 33, 2974–2987. [Google Scholar] [CrossRef]
- Huang, K.; Zhou, X. Cutting the last wires for mobile communications by microwave power transfer. IEEE Commun. Mag. 2015, 53, 86–93. [Google Scholar] [CrossRef]
- Talla, V.; Hessar, M.; Kellogg, B.; Najafi, A.; Smith, J.R.; Gollakota, S. Lora backscatter: Enabling the vision of ubiquitous connectivity. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2017, 1, 105. [Google Scholar] [CrossRef]
- Talla, V.; Kellogg, B.; Ransford, B.; Naderiparizi, S.; Gollakota, S.; Smith, J.R. Powering the next billion devices with Wi-Fi. In Proceedings of the 11th ACM Conference on Emerging Networking Experiments and Technologies, Heidelberg, Germany, 1–4 December 2015; p. 4. [Google Scholar]
- Hu, P.; Zhang, P.; Rostami, M.; Ganesan, D. Braidio: An integrated active-passive radio for mobile devices with asymmetric energy budgets. In Proceedings of the 2016 ACM SIGCOMM Conference, Florianopolis, Brazil, 22–26 August 2016; pp. 384–397. [Google Scholar]
- Xu, W.; Bi, S.; Lin, X.; Wang, J. Reusing Wireless Power Transfer for Backscatter-Assisted Cooperation in WPCN. In International Conference on Machine Learning and Intelligent Communications; Springer: Berlin, Germany, 2018; pp. 229–239. [Google Scholar]
- Ishizaki, H.; Ikeda, H.; Yoshida, Y.; Maeda, T.; Kuroda, T.; Mizuno, M. A battery-less wifi-ber modulated data transmitter with ambient radio-wave energy harvesting. In Proceedings of the 2011 Symposium on VLSI Circuits (VLSIC), Honolulu, HI, USA, 15–17 June 2011; pp. 162–163. [Google Scholar]
- Ju, H.; Zhang, R. Throughput maximization in wireless powered communication networks. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013. [Google Scholar] [CrossRef]
- Correia, R.; Carvalho, N.B.; Kawasaki, S. Continuously power delivering for passive backscatter wireless sensor networks. IEEE Trans. Microw. Theory Tech. 2016, 64, 3723–3731. [Google Scholar] [CrossRef]
- Iannello, F.; Simeone, O.; Spagnolini, U. Energy management policies for passive RFID sensors with RF-energy harvesting. In Proceedings of the 2010 IEEE International Conference on Communications (ICC), Cape Town, South Africa, 23–27 May 2010; pp. 1–6. [Google Scholar]
- Correia, R.; de Carvalho, N.B.; Fukuday, G.; Miyaji, A.; Kawasaki, S. Backscatter wireless sensor network with WPT capabilities. In Proceedings of the 2015 IEEE MTT-S International Microwave Symposium (IMS), Phoenix, AZ, USA, 17–22 May 2015; pp. 1–4. [Google Scholar]
- Zhang, P.; Rostami, M.; Hu, P.; Ganesan, D. Enabling practical backscatter communication for on-body sensors. In Proceedings of the 2016 ACM SIGCOMM Conference, Florianopolis, Brazil, 22–26 August 2016; pp. 370–383. [Google Scholar]
- Hoang, D.T.; Niyato, D.; Wang, P.; Kim, D.I.; Le, L.B. Optimal data scheduling and admission control for backscatter sensor networks. IEEE Trans. Commun. 2017, 65, 2062–2077. [Google Scholar] [CrossRef]
- Xie, L.; Yin, Y.; Vasilakos, A.V.; Lu, S. Managing RFID data: Challenges, opportunities and solutions. IEEE Commun. Surv. Tutor. 2014, 16, 1294–1311. [Google Scholar] [CrossRef]
- Yang, G.; Yuan, D.; Liang, Y.C. Optimal Resource Allocation in Full-Duplex Ambient Backscatter Communication Networks for Green IoT. arXiv, 2018; arXiv:1805.01365. [Google Scholar]
- Yang, G.; Yuan, D.; Liang, Y.C.; Zhang, R.; Leung, V. Optimal Resource Allocation in Full-Duplex Ambient Backscatter Communication Networks for Wireless-Powered IoT. arXiv, 2018; arXiv:1806.06598. [Google Scholar] [CrossRef]
- Kalamkar, S.S.; Jeyaraj, J.P.; Banerjee, A.; Rajawat, K. Resource allocation and fairness in wireless powered cooperative cognitive radio networks. IEEE Trans. Commun. 2016, 64, 3246–3261. [Google Scholar] [CrossRef]
- Wu, Q.; Tao, M.; Ng, D.W.K.; Chen, W.; Schober, R. Energy-efficient resource allocation for wireless powered communication networks. IEEE Trans. Wirel. Commun. 2016, 15, 2312–2327. [Google Scholar] [CrossRef]
- Lyu, B.; Yang, Z.; Gui, G.; Feng, Y. Optimal resource allocation policies for multi-user backscatter communication systems. Sensors 2016, 16, 2016. [Google Scholar] [CrossRef] [PubMed]
- Xia, H.; Li, Y.; Zhang, H. Throughput maximization for wireless powered relay communications. In Proceedings of the 2017 IEEE/CIC International Conference on Communications in China (ICCC), Qingdao, China, 22–24 October 2017. [Google Scholar] [CrossRef]
- Mohjazi, L.; Dianati, M.; Karagiannidis, G.K.; Muhaidat, S.; Al-Qutayri, M. RF-powered cognitive radio networks: Technical challenges and limitations. IEEE Commun. Mag. 2015, 53, 94–100. [Google Scholar] [CrossRef]
- Wang, Y.; Lin, W.; Sun, R.; Huo, Y. Optimization of relay selection and ergodic capacity in cognitive radio sensor networks with wireless energy harvesting. Pervasive Mob. Comput. 2015, 22, 33–45. [Google Scholar] [CrossRef]
- Xu, L.; Zhu, K.; Wang, R.; Gong, S. Performance analysis of ambient backscatter communications in RF-powered cognitive radio networks. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Park, K.H.; Munir, D.; Kim, J.S.; Chung, M.Y. Integrating RF-powered backscatter with underlay cognitive radio networks. In Proceedings of the 2017 International Conference on Information Networking (ICOIN), Da Nang, Vietnam, 11–13 January 2017; pp. 288–292. [Google Scholar]
- Wang, W.; Hoang, D.T.; Niyato, D.; Wang, P.; Kim, D.I. Stackelberg Game for Distributed Time Scheduling in RF-Powered Backscatter Cognitive Radio Networks. arXiv, 2018; arXiv:1804.02630. [Google Scholar] [CrossRef]
- Thai, H.D.; Niyato, D.; Wang, P.; Kim, D.I.; Han, Z. The tradeoff analysis in RF-powered backscatter cognitive radio networks. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Lyu, B.; Guo, H.; Yang, Z.; Gui, G. Throughput Maximization for Hybrid Backscatter Assisted Cognitive Wireless Powered Radio Networks. IEEE Internet Things J. 2018, 5, 2015–2024. [Google Scholar] [CrossRef]
- Lee, S.; Zhang, R.; Huang, K. Opportunistic wireless energy harvesting in cognitive radio networks. IEEE Trans. Wirel. Commun. 2013, 12, 4788–4799. [Google Scholar] [CrossRef]
- Guo, H.; Zhang, Q.; Li, D.; Liang, Y.C. Noncoherent Multiantenna Receivers for Cognitive Backscatter System with Multiple RF Sources. arXiv, 2018; arXiv:1808.04316 2018. [Google Scholar]
- Hoang, D.T.; Niyato, D.; Wang, P.; Kim, D.I. Performance Optimization for Cooperative Multiuser Cognitive Radio Networks with RF Energy Harvesting Capability. IEEE Trans. Wirel. Commun. 2015, 14, 3614–3629. [Google Scholar] [CrossRef]
- Huang, Y.; Clerckx, B. Waveform design for wireless power transfer with limited feedback. IEEE Trans. Wirel. Commun. 2018, 17, 415–429. [Google Scholar] [CrossRef]
- Wu, Q.; Chen, W.; Ng, D.W.K.; Li, J.; Schober, R. User-centric energy efficiency maximization for wireless powered communications. IEEE Trans. Wirel. Commun. 2016, 15, 6898–6912. [Google Scholar] [CrossRef]
- Ma, Z.; Qian, J.; Gao, F.; Wang, G.; Li, Y. Transmission strategies of buffer-aided ambient backscatter system. In Proceedings of the 2017 IEEE/CIC International Conference on Communications in China (ICCC), Qingdao, China, 22–24 October 2017; pp. 1–5. [Google Scholar]
- Zheng, Y.; Bi, S.; Lin, X. Backscatter-Assisted Relaying in Wireless Powered Communications Network. In International Conference on Machine Learning and Intelligent Communications; Springer: Berlin, Germany, 2018; pp. 273–283. [Google Scholar]
- Bereketli, A.; Akan, O.B. Communication coverage in wireless passive sensor networks. IEEE Commun. Lett. 2009, 13, 133–135. [Google Scholar] [CrossRef]
- Peng, Y.; Shangguan, L.; Hu, Y.; Qian, Y.; Lin, X.; Chen, X.; Fang, D.; Jamieson, K. PLoRa: A passive long-range data network from ambient LoRa transmissions. In Proceedings of the 2018 Conference of the ACM Special Interest Group on Data Communication, Budapest, Hungary, 20–25 August 2018; pp. 147–160. [Google Scholar]
- Abdelnour, A.; Kaddour, D.; Tedjini, S. Transformation of Barcode Into RFID Tag, Design, and Validation. IEEE Microw. Wirel. Compon. Lett. 2018, 28, 398–400. [Google Scholar] [CrossRef]
- Amato, F.; Torun, H.M.; Durgin, G.D. Beyond the limits of classic backscattering communications: A quantum tunneling RFID tag. In Proceedings of the 2017 IEEE International Conference on RFID (RFID), Phoenix, AZ, USA, 9–11 May 2017; pp. 20–25. [Google Scholar]
- Amato, F.; Durgin, G.D. Tunnel Diodes for Backscattering Communications. In Proceedings of the 2018 IEEE 2nd URSI Atlantic Radio Science Meeting (AT-RASC), Meloneras, Spain, 28 May–1 June 2018; pp. 1–3. [Google Scholar]
- Amato, F.; Peterson, C.W.; Degnan, B.P.; Durgin, G.D. Tunneling RFID Tags for Long-Range and Low-Power Microwave Applications. IEEE J. Radio Freq. Identif. 2018, 2, 93–103. [Google Scholar] [CrossRef]
- Amato, F.; Peterson, C.W.; Degnan, B.P.; Durgin, G.D. A 45 μW bias power, 34 dB gain reflection amplifier exploiting the tunneling effect for RFID applications. In Proceedings of the 2015 IEEE International Conference on RFID (RFID), San Diego, CA, USA, 15–17 April 2015; pp. 137–144. [Google Scholar]
- Choi, S.H.; Kim, D.I. Multi-cell structure backscatter based wireless-powered communication network (WPCN). IEICE Trans. Commun. 2016, 99, 1687–1696. [Google Scholar] [CrossRef]
- Dardari, D.; D’Errico, R.; Roblin, C.; Sibille, A.; Win, M.Z. Ultrawide bandwidth RFID: The next generation? Proc. IEEE 2010, 98, 1570–1582. [Google Scholar] [CrossRef]
- Bacha, M.; Clerckx, B.; Huang, K. Backscatter communications for the internet of things: A stochastic geometry approach. arXiv, 2017; arXiv:1711.07277. [Google Scholar]
- Duan, R.; Jäntti, R.; Yiğitler, H.; Ruttik, K. On the achievable rate of bistatic modulated rescatter systems. IEEE Trans. Veh. Technol. 2017, 66, 9609–9613. [Google Scholar] [CrossRef]
- Darsena, D.; Gelli, G.; Verde, F. Exploiting noncircularity in backscattering communications. In Proceedings of the 2015 International Symposium on Wireless Communication Systems (ISWCS), Brussels, Belgium, 25–28 August 2015; pp. 546–550. [Google Scholar]
- Bharadia, D.; Joshi, K.R.; Kotaru, M.; Katti, S. Backfi: High throughput wifi backscatter. ACM SIGCOMM Comput. Commun. Rev. 2015, 45, 283–296. [Google Scholar] [CrossRef]
- He, C.; Wang, Z.J.; Leung, V.C. Unitary Query for the M × L × N MIMO Backscatter RFID Channel. IEEE Trans. Wirel. Commun. 2015, 14, 2613–2625. [Google Scholar] [CrossRef]
- Zhang, R.; Ho, C.K. MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef]
- Gong, S.; Xu, J.; Gao, L.; Huang, X.; Liu, W. Passive relaying scheme via backscatter communications in cooperative wireless networks. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Yan, W.; Li, L.; He, G.; Li, X.; Gao, A.; Zhang, H.; Han, Z. Performance analysis of two-way relay system based on ambient backscatter. In Proceedings of the 2018 13th IEEE Conference on Industrial Electronics and Applications, (ICIEA), Wuhan, China, 31 May–2 June 2018; pp. 1853–1858. [Google Scholar]
- Lu, X.; Li, G.; Jiang, H.; Niyato, D.; Wang, P. Performance analysis of wireless-powered relaying with ambient backscattering. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Munir, D.; Mughal, D.M.; Mahboob, T.; Chung, M.Y. Relay Selection Scheme for Cooperative Backscatter Communications Networks. In International Conference on Computational Science and Its Applications; Springer: Berlin, Germany, 2018; pp. 558–569. [Google Scholar]
- Ma, Y.; Selby, N.; Adib, F. Drone relays for battery-free networks. In Proceedings of the Conference of the ACM Special Interest Group on Data Communication, Los Angeles, CA, USA, 21–25 August 2017; pp. 335–347. [Google Scholar]
- Han, K.; Huang, K. Wirelessly powered backscatter communication networks: Modeling, coverage, and capacity. IEEE Trans. Wirel. Commun. 2017, 16, 2548–2561. [Google Scholar] [CrossRef]
- Bello, O.; Zeadally, S. Intelligent device-to-device communication in the internet of things. IEEE Syst. J. 2016, 10, 1172–1182. [Google Scholar] [CrossRef]
- Lu, X.; Jiang, H.; Niyato, D.; Kim, D.I.; Han, Z. Wireless-powered device-to-device communications with ambient backscattering: Performance modeling and analysis. IEEE Trans. Wirel. Commun. 2018, 17, 1528–1544. [Google Scholar] [CrossRef]
- Saad, W.; Zhou, X.; Han, Z.; Poor, H.V. On the physical layer security of backscatter wireless systems. IEEE Trans. Wirel. Commun. 2014, 13, 3442–3451. [Google Scholar] [CrossRef]
- Xie, L.; Shi, Y.; Hou, Y.T.; Lou, A. Wireless power transfer and applications to sensor networks. IEEE Wirel. Commun. 2013, 20, 140–145. [Google Scholar]
- Liu, W.; Huang, K.; Zhou, X.; Durrani, S. Next generation backscatter communication: Theory and applications. arXiv, 2017; arXiv:1701.07588. [Google Scholar]
- Gao, C.; Li, Y.; Zhang, X. LiveTag: Sensing Human-Object Interaction through Passive Chipless WiFi Tags. In Proceedings of the 15th USENIX Symposium on Networked Systems Design and Implementation (NSDI 18), Renton, WA, USA, 9–11 April 2018. [Google Scholar]
- Adib, F.; Mao, H.; Kabelac, Z.; Katabi, D.; Miller, R.C. Smart homes that monitor breathing and heart rate. In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing Systems, Seoul, Korea, 18–23 April 2015; pp. 837–846. [Google Scholar]
- Ding, H.; Han, J.; Liu, A.X.; Xi, W.; Zhao, J.; Yang, P.; Jiang, Z. Counting Human Objects Using Backscattered Radio Frequency Signals. IEEE Trans. Mob. Comput. 2018. [Google Scholar] [CrossRef]
- Chen, B.; Zhang, Q.; Zhao, R.; Li, D.; Wang, D. SGRS: A sequential gesture recognition system using COTS RFID. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Ryoo, J.; Karimi, Y.; Athalye, A.; Stanaćević, M.; Das, S.R.; Djurić, P. BARNET: Towards Activity Recognition Using Passive Backscattering Tag-to-Tag Network. In Proceedings of the 16th Annual International Conference on Mobile Systems, Munich, Germany, 10–15 June 2018; pp. 414–427. [Google Scholar]
- Yang, Q.; Taylor, D.G.; Durgin, G.D. Kalman filter based localization and tracking estimation for HIMR RFID systems. In Proceedings of the 2018 IEEE International Conference on RFID (RFID), Orlando, FL, USA, 10–12 April 2018; pp. 1–5. [Google Scholar]
- Deyle, T.; Nguyen, H.; Reynolds, M.; Kemp, C. RFID-guided robots for pervasive automation. IEEE Pervasive Comput. 2010, 9, 37–45. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. arXiv, 2016; arXiv:1602.03602. [Google Scholar] [CrossRef]
- Shigeta, R.; Suzuki, K.; Okuya, F.; Kawahara, Y. Trilateration-Inspired Sensor Node Position Estimation for UAV-Assisted Microwave Wireless Power Transfer. SICE J. Control Meas. Syst. Integr. 2017, 10, 350–359. [Google Scholar] [CrossRef]
- Abdelnasser, H.; Youssef, M.; Harras, K.A. Wigest: A ubiquitous wifi-based gesture recognition system. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Kowloon, Hong Kong, 26 April–1 May 2015; pp. 1472–1480. [Google Scholar]
- Virmani, A.; Shahzad, M. Position and orientation agnostic gesture recognition using wifi. In Proceedings of the 15th Annual International Conference on Mobile Systems, Niagara Falls, NY, USA, 19–23 June 2017; pp. 252–264. [Google Scholar]
- Zhao, M.; Adib, F.; Katabi, D. Emotion recognition using wireless signals. In Proceedings of the 22nd Annual International Conference on Mobile Computing and Networking, New York, NY, USA, 3–7 October 2016; pp. 95–108. [Google Scholar]
- Wang, C.; Xie, L.; Wang, W.; Chen, Y.; Bu, Y.; Lu, S. RF-ECG: Heart Rate Variability Assessment Based on COTS RFID Tag Array. In Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies; ACM: New York, NY, USA, 2018; Volume 2, p. 85. [Google Scholar]
- Moradi, E.; Amendola, S.; Björninen, T.; Sydänheimo, L.; Carmena, J.M.; Rabaey, J.M.; Ukkonen, L. Backscattering neural tags for wireless brain-machine interface systems. IEEE Trans. Antennas Propag. 2015, 63, 719–726. [Google Scholar] [CrossRef]
- Roy, S.; Jandhyala, V.; Smith, J.R.; Wetherall, D.J.; Otis, B.P.; Chakraborty, R.; Buettner, M.; Yeager, D.J.; Ko, Y.C.; Sample, A.P. RFID: From supply chains to sensor nets. Proc. IEEE 2010, 98, 1583–1592. [Google Scholar] [CrossRef]
- Jiang, C.; He, Y.; Zheng, X.; Liu, Y. Orientation-aware RFID tracking with centimeter-level accuracy. In Proceedings of the 17th ACM/IEEE International Conference on Information Processing in Sensor Networks, Porto, Portugal, 11–13 April 2018; pp. 290–301. [Google Scholar]
- Poupyrev, I.; Gong, N.W.; Fukuhara, S.; Karagozler, M.E.; Schwesig, C.; Robinson, K.E. Project Jacquard: Interactive digital textiles at scale. In Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems, San Jose, CA, USA, 7–12 May 2016; pp. 4216–4227. [Google Scholar]
- Huang, Q.; Mei, Y.; Wang, W.; Zhang, Q. Toward Battery-Free Wearable Devices: The Synergy between Two Feet. ACM Trans. Cyber-Phys. Syst. 2018, 2, 20. [Google Scholar] [CrossRef]
- Daskalakis, S.N.; Kimionis, J.; Collado, A.; Tentzeris, M.M.; Georgiadis, A. Ambient FM backscattering for smart agricultural monitoring. In Proceedings of the 2017 IEEE MTT-S International Microwave Symposium (IMS), Honololu, HI, USA, 4–9 June 2017; pp. 1339–1341. [Google Scholar]
- Daskalakis, S.N.; Goussetis, G.; Assimonis, S.D.; Tentzeris, M.M.; Georgiadis, A. A uW Backscatter-Morse-Leaf Sensor for Low-Power Agricultural Wireless Sensor Networks. IEEE Sens. J. 2018, 18, 7889–7898. [Google Scholar] [CrossRef]
- Naderiparizi, S. Battery-Free Connected Cameras. Ph.D. Thesis, University of Washington, Seattle, WA, USA, 2018. Available online: https://digital.lib.washington.edu/researchworks/handle/1773/41771 (accessed on 11 November 2018).
- Kampianakis, E.; Kimionis, J.; Tountas, K.; Konstantopoulos, C.; Koutroulis, E.; Bletsas, A. Wireless environmental sensor networking with analog scatter radio and timer principles. IEEE Sens. J. 2014, 14, 3365–3376. [Google Scholar] [CrossRef]
- Luo, Z.; Wang, W.; Xiao, J.; Huang, Q.; Jiang, T.; Zhang, Q. Authenticating On-Body Backscatter by Exploiting Propagation Signatures. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2018, 2, 123. [Google Scholar] [CrossRef]
- Vasisht, D.; Zhang, G.; Abari, O.; Lu, H.M.; Flanz, J.; Katabi, D. In-body backscatter communication and localization. In Proceedings of the 2018 Conference of the ACM Special Interest Group on Data Communication, Budapest, Hungary, 20–25 August 2018; pp. 132–146. [Google Scholar]
- Wilson, W.C.; Juarez, P.D. Emerging needs for pervasive passive wireless sensor networks on aerospace vehicles. Procedia Comput. Sci. 2014, 37, 101–108. [Google Scholar] [CrossRef]
- Vannucci, G.; Bletsas, A.; Leigh, D. Implementing backscatter radio for wireless sensor networks. In Proceedings of the IEEE 18th International Symposium on Personal, Indoor and Mobile Radio Communications, PIMRC 2007, Athens, Greece, 3–7 September 2007; pp. 1–5. [Google Scholar]
- Liu, H.; Bolic, M.; Nayak, A.; Stojmenovic, I. Taxonomy and challenges of the integration of RFID and wireless sensor networks. IEEE Netw. 2008, 22, 26–35. [Google Scholar] [CrossRef]
- Zhang, L.; Wang, Z. Integration of RFID into wireless sensor networks: Architectures, opportunities and challenging problems. In Proceedings of the 2006 Fifth International Conference on Grid and Cooperative Computing Workshops, Hunan, China, 21–23 October 2006; pp. 463–469. [Google Scholar]
- Akan, O.B.; Isik, M.T.; Baykal, B. Wireless passive sensor networks. IEEE Commun. Mag. 2009, 47, 92–99. [Google Scholar] [CrossRef]
- Qureshi, K.K.; Mekid, S.; Saleh, A.; Sharawi, M.S. Ambient RF-powered Soft Nervous Materials: A Case Study. Sens. Mater. 2018, 30, 1349–1356. [Google Scholar] [CrossRef]
- Gollakota, S.; Reynolds, M.S.; Smith, J.R.; Wetherall, D.J. The emergence of RF-powered computing. Computer 2014, 47, 32–39. [Google Scholar] [CrossRef]
- Devineni, J.K.; Dhillon, H.S. Ambient Backscatter Systems: Exact Average Bit Error Rate under Fading Channels. arXiv, 2018; arXiv:1804.09307. [Google Scholar] [CrossRef]
- Hasanvand, A.; Khaleghi, A.; Balasingham, I. Coherent query scheme for wireless backscatter communication systems with single tag. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 184. [Google Scholar] [CrossRef]
- Zhang, Y.; Gao, F.; Fan, L.; Jin, S.; Zhu, H. Performance Analysis for Tag Selection in Backscatter Communication Systems over Nakagami-m Fading Channels. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–5. [Google Scholar]
- Liu, Y.; Dong, M.; Ota, K.; Liu, A. ActiveTrust: Secure and trustable routing in wireless sensor networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2013–2027. [Google Scholar] [CrossRef]
- Yang, Z.; Huang, Q.; Zhang, Q. NICScatter: Backscatter as a Covert Channel in Mobile Devices. In Proceedings of the 23rd Annual International Conference on Mobile Computing and Networking, Snowbird, UT, USA, 16–20 October2 017; pp. 356–367.
- Yang, Z.; Huang, Q.; Zhang, Q. Backscatter as a Covert Channel in Mobile Devices. GetMobile Mob. Comput. Commun. 2018, 21, 31–34. [Google Scholar] [CrossRef]
- Telecommunication Laws and Regulations. 2018. Available online: https://ppp.worldbank.org/public-private-partnership/sector/telecom/laws-regulations (accessed on 11 September 2018).
- Interdonato, G.; Björnson, E.; Ngo, H.Q.; Frenger, P.; Larsson, E.G. Ubiquitous Cell-Free Massive MIMO Communications. arXiv, 2018; arXiv:1804.03421. [Google Scholar]
- Welbourne, E.; Battle, L.; Cole, G.; Gould, K.; Rector, K.; Raymer, S.; Balazinska, M.; Borriello, G. Building the internet of things using RFID: The RFID ecosystem experience. IEEE Internet Comput. 2009, 13, 48–55. [Google Scholar] [CrossRef]
- Tozlu, S.; Senel, M.; Mao, W.; Keshavarzian, A. Wi-Fi enabled sensors for internet of things: A practical approach. IEEE Commun. Mag. 2012, 50, 134–143. [Google Scholar] [CrossRef]
- Tan, L.; Wang, N. Future internet: The internet of things. In Proceedings of the 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), Chengdu, China, 20–22 August 2010; Volume 5, pp. 376–380. [Google Scholar]
- Shariatmadari, H.; Ratasuk, R.; Iraji, S.; Laya, A.; Taleb, T.; Jäntti, R.; Ghosh, A. Machine-Type Communications: Current Status and Future Perspectives toward 5G systems. IEEE Commun. Mag. 2015, 53, 10–17. [Google Scholar] [CrossRef]
- Kim, S.H.; Kim, D.I. Traffic-Aware Backscatter Communications in Wireless-Powered Heterogeneous Networks. arXiv, 2018; arXiv:1807.08903. [Google Scholar]
- O’Shea, T.J.; Hoydis, J. An introduction to machine learning communications systems. arXiv, 2017; arXiv:1702.00832v1. [Google Scholar]
- Zhang, C.; Patras, P.; Haddadi, H. Deep Learning in Mobile and Wireless Networking: A Survey. arXiv, 2018; arXiv:1803.04311. [Google Scholar]
- O’Shea, T.J.; Karra, K.; Clancy, T.C. Learning to communicate: Channel auto-encoders, domain specific regularizers, and attention. In Proceedings of the 2016 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Limassol, Cyprus, 12–14 December 2016; pp. 223–228. [Google Scholar]
- O’Shea, T.J.; Erpek, T.; Clancy, T.C. Physical layer deep learning of encodings for the MIMO fading channel. In Proceedings of the 2017 55th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 3–6 October 2017; pp. 76–80. [Google Scholar]
- De Vrieze, C.; Barratt, S.; Tsai, D.; Sahai, A. Cooperative Multi-Agent Reinforcement Learning for Low-Level Wireless Communication. arXiv, 2018; arXiv:1801.04541. [Google Scholar]
- Zhu, G.; Ko, S.W.; Huang, K. Backscatter Sensing by Inference from Randomized Transmissions. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Ren, D.; Zhang, Y.; Xiao, N.; Zhou, H.; Li, X.; Qian, J.; Yang, P. Word-Fi: Accurate Handwrite System Empowered by Wireless Backscattering and Machine Learning. IEEE Netw. 2018, 32, 47–53. [Google Scholar] [CrossRef]
- Van Huynh, N.; Hoang, D.T.; Nguyen, D.N.; Dutkiewicz, E.; Niyato, D.; Wang, P. Reinforcement learning approach for RF-powered cognitive radio network with ambient backscatter. arXiv, 2018; arXiv:1808.07601. [Google Scholar]
- Aoudia, F.A.; Hoydis, J. End-to-End Learning of Communications Systems Without a Channel Model. arXiv, 2018; arXiv:1804.02276. [Google Scholar]
- Farsad, N.; Rao, M.; Goldsmith, A. Deep Learning for Joint Source-Channel Coding of Text. arXiv, 2018; arXiv:1802.06832. [Google Scholar]
- Kim, H.; Jiang, Y.; Rana, R.; Kannan, S.; Oh, S.; Viswanath, P. Communication Algorithms via Deep Learning. arXiv, 2018; arXiv:1805.09317. [Google Scholar]
- Liu, L.; Cheng, Y.; Cai, L.; Zhou, S.; Niu, Z. Deep learning based optimization in wireless network. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Zhao, W.; Wang, G.; Fan, R.; Fan, L.S.; Atapattu, S. Ambient Backscatter Communication Systems: Capacity and Outage Performance Analysis. IEEE Access 2018, 6, 22695–22704. [Google Scholar] [CrossRef]
- Varner, M.A.; Alhassoun, M.; Durgin, G.D. Partitioned pseudo-retrodirective arrays for capacity expansion of backscatter communication channels. In Proceedings of the 2018 IEEE International Conference on RFID (RFID), Orlando, FL, USA, 10–12 April 2018; pp. 1–7. [Google Scholar]
- Arikan, E. Channel polarization: A method for constructing capacity-achieving codes for symmetric binary-input memoryless channels. IEEE Trans. Inf. Theory 2009, 55, 3051–3073. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).