Fast Packet Inspection for End-To-End Encryption
Abstract
1. Introduction
2. Related Works
2.1. End-To-End Encryption (E2EE)
2.2. Deep Packet Inspection (DPI)
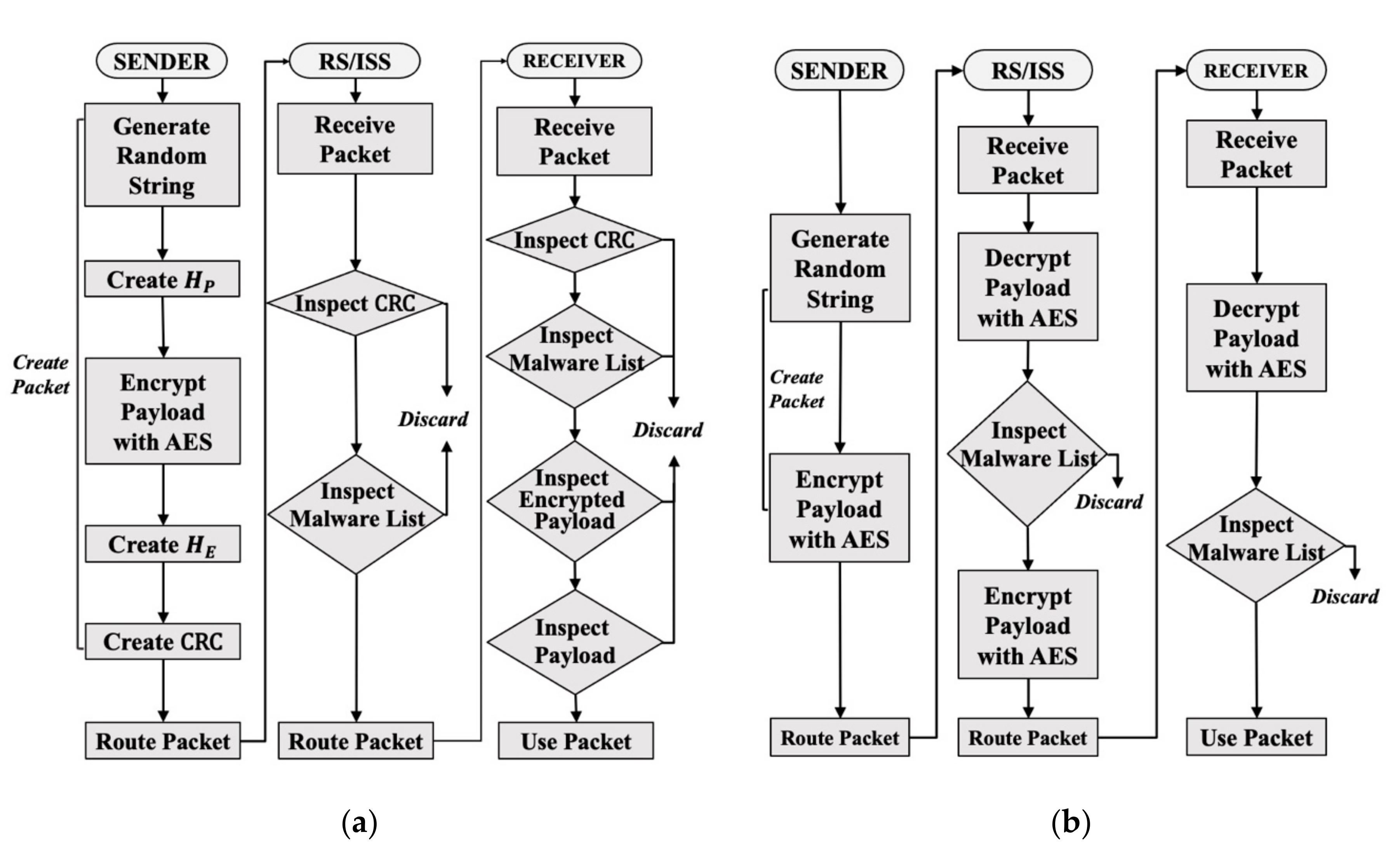
3. Proposed Mechanism
3.1. FPI Structure and Operation Mechanism
3.2. FPI Packet Frame Structure
3.3. FPI Packet Transport Mechanism
4. Evaluation
4.1. Experimental Conditions and Environment
4.2. Experiment Procedures
4.3. Experimental Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| E2EE | End-to-End Encryption |
| FPI | Fast Packet Inspection |
| DPI | Deep Packet Inspection |
| CRC | Cyclic Redundancy Check |
| RS/ISS | Relay Server including an Information Security System |
References
- Wang, D.; Cheng, H.; He, D.; Wang, P. On the Challenges in Designing Identity-Based Privacy-Preserving Authentication Schemes for Mobile Devices. IEEE Syst. J. 2018, 12, 916–925. [Google Scholar] [CrossRef]
- DMC MEDIA. 2019 Mobile Messenager App Usage Behavior by DMC REPORT. Available online: https://www.dmcreport.co.kr/ (accessed on 7 May 2019).
- Triyason, T.; Tassanaviboon, A.; Kanthamanon, P. Hybrid Classroom: Designing for the New Normal after COVID-19 Pandemic. In Proceedings of the 11th International Conference on Advances in Information Technology (IAIT2020), Bangkok, Thailand, 1–3 July 2020; ACM: New York, NY, USA, 2020; Volume 30, pp. 1–8. [Google Scholar]
- Endeley, R.E. End-to-End Encryption in Messaging Services and National Security—Case of WhatsApp Messenger. J. Inf. Secur. 2018, 9, 95–99. [Google Scholar] [CrossRef]
- Rösler, P.; Mainka, C.; Schwenk, J. More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 415–429. [Google Scholar]
- Cohn-Gordon, K.; Cremers, C.; Dowling, B.; Garratt, L.; Stebila, D. A Formal Security Analysis of the Signal Messaging Protocol. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 451–466. [Google Scholar]
- Karbasi, A.H.; Shahpasand, S. A post-quantum end-to-end encryption over smart contract-based blockchain for defeating man-in-the-middle and interception attacks. Peer-to-Peer Netw. Appl. 2020, 13, 1–19. [Google Scholar] [CrossRef]
- Wang, W.; Zhu, M.; Wang, J.; Zeng, X.; Yang, Z. End-to-end encrypted traffic classification with onedimensional convolution neural networks. In Proceedings of the IEEE International Conference on Intelligence and Security Informatics (ISI), Beijing, China, 22–24 July 2017; pp. 43–48. [Google Scholar]
- Amaral, P.; Dinis, J.; Pinto, P.; Bernardo, L.; Tavares, J.; Mamede, H.S. Machine learning in software defined networks: Data collection and traffic classification. In Proceedings of the IEEE 24th International Conference on Network Protocols (ICNP), Singapore, 8–11 November 2016; pp. 1–5. [Google Scholar]
- Ren, H.; Li, H.; Liu, D.; Xu, G.; Cheng, N.; Shen, X.S. Privacy-preserving Efficient Verifiable Deep Packet Inspection for Cloud-assisted Middlebox. IEEE Trans. Cloud Comput. 2020. [Google Scholar] [CrossRef]
- Garcia, J.; Korhonen, T.; Andersson, R.; Västlund, F. Towards Video Flow Classification at a Million Encrypted Flows Per Second. In Proceedings of the IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 358–365. [Google Scholar]
- Sherry, J.; Lan, C.; Popa, R.A.; Ratnasamy, S. Blindbox: Deep packet inspection over encrypted traffic. In Proceedings of the 2015 ACM Conference on Special Interest Group on Data Communication, London, UK, 17–21 August 2015; pp. 213–226. [Google Scholar]
- Nabeel, M. The Many Faces of End-to-End Encryption and Their Security Analysis. In Proceedings of the IEEE International Conference on Edge Computing (EDGE), Honolulu, HI, USA, 25–30 June 2017; pp. 252–259. [Google Scholar]
- Shirvanian, M.; Saxena, N.; George, J.J. On the pitfalls of end-to-end encrypted communications: A study of remote key-fingerprint verification. In Proceedings of the 33rd Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; pp. 499–511. [Google Scholar]
- Espinoza, A.M.; Tolley, W.J.; Crandall, J.R.; Crete-Nishihata, M.; Hilts, A. Alice and bob, who the FOCI are they?: Analysis of end-to-end encryption in the LINE messaging application. In Proceedings of the 7th USENIX Workshop on Free and Open Communications on the Internet (FOCI 17), Vancouver, BC, Canada, 14 August 2017. [Google Scholar]
- Zoom. E2E Encryption for Zoom Meetings. Available online: https://blog.zoom.us/end-to-end-encryption-update/ (accessed on 17 June 2020).
- Kumar, S.; Hu, Y.; Andersen, M.P.; Popa, R.A.; Culler, D.E. JEDI: Many-to-Many End-to-End Encryption and Key Delegation for IoT. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 1519–1536. [Google Scholar]
- Park, S.-Y.; Park, S.-M.; Park, U.-S.; Kim, H.-G. Messenger Program with End-to-end Encryption and Digital Signature. JKICS 2016, 305–306. [Google Scholar]
- Aceto, G.; Ciuonzo, D.; Montieri, A.; Pescapè, A. MIMETIC: Mobile encrypted traffic classification using multimodal deep learning. Comput. Netw. 2019, 165, 106944. [Google Scholar] [CrossRef]
- Xu, C.; Chen, S.; Su, J.; Yiu, S.M.; Hui, L.C.K. A Survey on Regular Expression Matching for Deep Packet Inspection: Applications, Algorithms, and Hardware Platforms. IEEE Commun. Surv. Tutor. 2016, 18, 2991–3029. [Google Scholar] [CrossRef]
- Elagin, V.S.; Goldshtein, B.S.; Onufrienko, A.V.; Zarubin, A.A.; Savelieva, A.A. The efficiency of the DPI system for identifying traffic and providing the quality of OTT services. Systems of Signals Generating and Processing in the Field of on Board Communications. In Proceedings of the 2018 Systems of Signals Generating and Processing in the Field of on Board Communications, Moscow, Russia, 14–15 March 2018; pp. 1–5. [Google Scholar]
- Yu, F.; Katz, R.H.; Lakshman, T.V. Gigabit rate packet pattern-matching using TCAM. In Proceedings of the 12th IEEE International Conference on Network Protocols, Berlin, Germany, 8 October 2004; pp. 174–183. [Google Scholar]
- Jung, J.-W. Communication Equipment Related Information Leakage Risk Analysis and Preparation. Available online: https://intelligence.na.go.kr:444/intelligence/reference/reference01.do?mode=view&articleNo=663003&article.offset=0&articleLimit=10 (accessed on 9 April 2019).
- Al-hisnawi, M.; Ahmadi, M. Deep Packet Inspection Using Quotient Filter. IEEE Commun. Lett. 2016, 20, 2217–2220. [Google Scholar] [CrossRef]
- Al-hisnawi, P.M.; Ahmadi, M. QCF for deep packet inspection. IET Netw. 2018, 7, 346–352. [Google Scholar] [CrossRef]
- Li, Y.; Li, J. MultiClassifier: A combination of DPI and ML for application-layer classification in SDN. In Proceedings of the 2014 2nd International Conference on Systems and Informatics (ICSAI 2014), Shanghai, China, 15–17 November 2014; pp. 682–686. [Google Scholar]
- Doroud, H.; Aceto, G.; Donato, W.-D.; Jarchlo, E.A.; Lopez, A.M.; Guerrero, C.D. Speeding-Up DPI Traffic Classification with Chaining. In Proceedings of the 2018 IEEE Global Communications Conference, Abu Dhabi, UAE, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Kim, J.-W.; Choi, J.-I. Software-Defined Networking (SDN) Based Integrated Security Switch Design. IEIE 2019, 103, 552–553. [Google Scholar]
- John, W.; Olovsson, T. Detection of malicious traffic on back-bone links via packet header analysis. Campus-Wide Inf. Syst. 2008, 25, 342–358. [Google Scholar] [CrossRef]
- Mansoori, M.; Hirose, Y.; Welch, I.; Choo, K.R. Empirical Analysis of Impact of HTTP Referer on Malicious Website Behaviour and Delivery. In Proceedings of the IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 23–25 March 2016; pp. 941–948. [Google Scholar]
- Gong, C.; Sarac, K. IP traceback based on packet marking and logging. In Proceedings of the IEEE International Conference on Communications, Seoul, Korea, 16–20 May 2005; Volume 2, pp. 1043–1047. [Google Scholar]
- Lin, P.-C.; Lin, Y.-D.; Lee, T.-H.; Lai, Y.-C. Using String Matching for Deep Packet Inspection. IEEE Comput. 2008, 41, 23–28. [Google Scholar] [CrossRef]





| Category | DPI | FPI | ||
|---|---|---|---|---|
| Inspection coverage | 100% | 10% | 20% | 100% |
| Transmission speed average (ms) | 15.74 | 1.06 | 1.09 | 2.88 |
| E2EE retention | X | O | ||
| Complexity of establishing environment | Complex [31] | Simple | ||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, S.-Y.; Yun, S.-W.; Lee, E.-Y.; Bae, S.-H.; Lee, I.-G. Fast Packet Inspection for End-To-End Encryption. Electronics 2020, 9, 1937. https://doi.org/10.3390/electronics9111937
Kim S-Y, Yun S-W, Lee E-Y, Bae S-H, Lee I-G. Fast Packet Inspection for End-To-End Encryption. Electronics. 2020; 9(11):1937. https://doi.org/10.3390/electronics9111937
Chicago/Turabian StyleKim, So-Yeon, Sun-Woo Yun, Eun-Young Lee, So-Hyeon Bae, and Il-Gu Lee. 2020. "Fast Packet Inspection for End-To-End Encryption" Electronics 9, no. 11: 1937. https://doi.org/10.3390/electronics9111937
APA StyleKim, S.-Y., Yun, S.-W., Lee, E.-Y., Bae, S.-H., & Lee, I.-G. (2020). Fast Packet Inspection for End-To-End Encryption. Electronics, 9(11), 1937. https://doi.org/10.3390/electronics9111937







