Secure Exchange of Medical Data Using a Novel Real-Time Biometric-Based Protection and Recognition Method
Abstract
:1. Introduction
- Imperceptibility preservation: The proposed work not only preserves the imperceptibility of the cover image, but it also maintains the imperceptibility of the recovered watermark. The preservation of both the host image and the watermarked image is achieved through a specialized filter to extract the middle range of frequencies and order of SVD, which are used as a decomposer in the proposed framework. For increasing the payload and maintaining the imperceptibly level for both host and watermark images, SVD is used in the proposed framework.
- Robustness: Extensive experimental verification from different perspectives proved the robustness of the proposed framework against intentional and unintentional attacks in a real-time environment. The incorporation of the proposed framework into the frequency domain and the decomposition of the middle frequencies extracted via specialized filters nourish the proposed algorithm to resist intentional and unintentional attacks.
- Payload: The embedding capacity in the proposed technique increases while maintaining imperceptibility and robustness. The coefficients acquired by decomposing the middle frequencies of the watermarked image and host image guarantee the trade-off between imperceptibility, robustness, and payload. Payload increases due to the embedding in the diagonal matrix in decomposition SVD; the imperceptibility is not affected due to the suitable frequencies using a special filter.
- Cost-Effectiveness: Embedding, recovery, and verification of the watermarked can be performed in real-time. After recovery of the watermark, the proposed framework not only retains reasonable accuracy of watermark recognition but also authenticates the originality of the cover image in real-time.
- The proposed technique can also be used for official correspondence and medical images, and other standard medical documents such as HL7 CDA (clinical document architecture), HL7 CCD (continuity of care documents). The specialized filter and diagonal matrix provide the facility to protect the official or medical documents from unauthorized access. The application has many advantages to secure the ownership with human identification property (fingerprint) such as statements, letters, medical images.
2. Related Work
- Most of them rely on imperceptibility and robustness, but they failed to recover the full watermark after some attacks being applied.
- The algorithms are failed to facilitate in a real-time environment; they deal in the offline environment.
- Most of the existing algorithms do not embed the biometric as a watermark. If someone does so, then it is not recovered, which may able to recognize entirely.
- The payload is a fundamental issue for the existing algorithms, as, concerning the watermark capacity, the algorithms are collapsible.
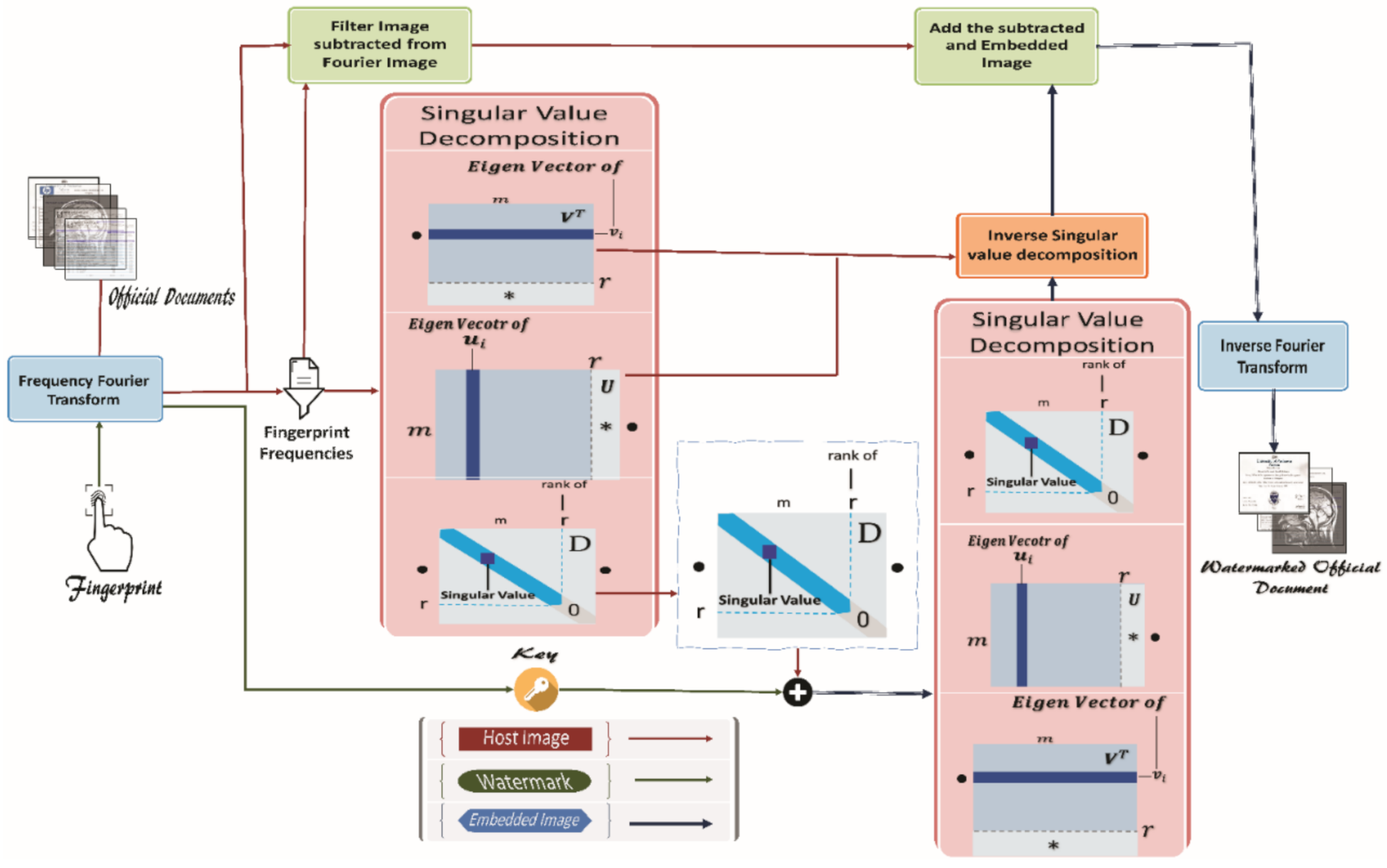
3. Research Methods
| Algorithm 1 Embedding Algorithm |
| Input: Host image , watermark , secret key , filter for host image , filter for the watermark image Output: Watermarked image Steps:
|
| Algorithm 2 Extraction Algorithm |
| Input: Watermarked image secret key . Output: Host image , watermark
|
3.1. Middle-Frequency Selection in FFT
3.2. Singular Value Decomposition (SVD)
4. Experimental Results
4.1. Dataset
4.2. Experimental Setup
4.3. Robustness Against Attacks
4.4. Non-Parametric Statistical Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| Host image | |
| Watermark image | |
| Secrete key | |
| Fourier Transform Image | |
| Orthogonal Matrix | |
| Orthogonal Matrix | |
| Diagonal Matrix | |
| Low Pass Filter | |
| High Pass Filter | |
| Last row of the image | |
| Last column of the image | |
| Last row of the image | |
| Rows of the image | |
| A column of the Image | |
| Filtered Frequencies of the Host Image | |
| Distance computed for the low pass filter | |
| Distance computed for the high pass filter | |
| Watermarked required frequencies | |
| Watermarked Diagonal matrix | |
| Unembedded frequencies of a host image |
References
- Loganathan, A.; Kaliyaperumal, G. An adaptive HVS based video watermarking scheme for multiple watermarks using BAM neural networks and fuzzy inference system. Expert Syst. Appl. 2016, 63, 412–434. [Google Scholar] [CrossRef]
- Dadkhah, S.; Abd Manaf, A.; Hori, Y.; Ella Hassanien, A.; Sadeghi, S. An effective SVD-based image tampering detection and self-recovery using active watermarking. Signal Process. Image Commun. 2014, 29, 1197–1210. [Google Scholar] [CrossRef]
- Hossain, M.; Islam, S.M.R.; Ali, F.; Kwak, K.S.; Hasan, R. An Internet of Things-based health prescription assistant and its security system design. Future Gener. Comput. Syst. 2018, 82, 422–439. [Google Scholar] [CrossRef]
- Ali, M.; Ahn, C.W.; Pant, M.; Siarry, P. An image watermarking scheme in wavelet domain with optimized compensation of singular value decomposition via artificial bee colony. Inf. Sci. 2014. [Google Scholar] [CrossRef]
- Amiri, S.H.; Jamzad, M. Robust watermarking against print and scan attack through efficient modeling algorithm. Signal Process. Image Commun. 2014, 29, 1181–1196. [Google Scholar] [CrossRef]
- Lang, J.; Zhang, Z. Blind digital watermarking method in the fractional Fourier transform domain. Opt. Lasers Eng. 2014, 53, 112–121. [Google Scholar] [CrossRef]
- Ali, M.; Ahn, C.W. An optimized watermarking technique based on self-adaptive de in DWT-SVD transform domain. Signal Process. 2014, 94, 545–556. [Google Scholar] [CrossRef]
- Bhatnagar, G.; Wu, Q.J. A new logo watermarking based on redundant fractional wavelet transform. Math. Comput. Model. 2013, 58, 204–218. [Google Scholar] [CrossRef]
- Al-nabhani, Y.; Jalab, H.A.; Wahid, A.; Noor, R. Robust watermarking algorithm for digital images using discrete wavelet and probabilistic neural network. J. King Saud Univ. Comput. Inf. Sci. 2015. [Google Scholar] [CrossRef] [Green Version]
- Elshazly, E.H.; Faragallah, O.S.; Abbas, A.M.; Ashour, M.A.; EI-Rabaie, E.-S.M.; Kazemian, H.; Alshebeili, S.A.; EI-Samie, F.E.A.; El-sayed, H.S. Robust and secure fractional wavelet image watermarking. Signal Image Video Process. 2014, 9, 89–98. [Google Scholar] [CrossRef] [Green Version]
- Lai, C.C. An improved SVD-based watermarking scheme using human visual characteristics. Opt. Commun. 2011, 284, 938–944. [Google Scholar] [CrossRef]
- Gao, L.; Qi, L.; Wang, Y.; Chen, E.; Yang, S.; Guan, L. Rotation Invariance in 2D-FRFT with Application to Digital Image Watermarking. J. Signal Process. Syst. 2013, 72, 133–148. [Google Scholar] [CrossRef]
- Hu, H.; Hsu, L. Exploring DWT—SVD—DCT feature parameters for robust multiple watermarking against JPEG and JPEG2000. Comput. Electr. Eng. 2014. [Google Scholar] [CrossRef]
- Zheng, P.; Feng, J.; Li, Z.; Zhou, M. A novel SVD and LS-SVM combination algorithm for blind watermarking. Neurocomputing 2014, 142, 520–528. [Google Scholar] [CrossRef]
- Cox, I.J.; Kilian, J.; Leighton, F.T.; Shamoon, T. Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 1997, 6, 1673–1687. [Google Scholar] [CrossRef]
- Chen, P.; Zhao, Y.; Pan, J. Image Watermarking Robust to Print and Generation Copy. In Proceedings of the First International Conference on Innovative Computing, Information and Control—Volume I (ICICIC’06), Beijing, China, 30 August–1 September 2006. [Google Scholar]
- Chang, J.; Chen, B.; Tsai, C. LBP-based Fragile Watermarking Scheme for Image Tamper Detection and Recovery. In Proceedings of the 2013 International Symposium on Next-Generation Electronics, Kaohsiung, Taiwan, 25–26 February 2013; pp. 173–176. [Google Scholar]
- Li, Y.; Tu, Y.; Lu, J. Multi-point collaborative authentication method based on user image intelligent collection in the internet of things. Electronics 2019, 8, 978. [Google Scholar] [CrossRef] [Green Version]
- Solanki, K.; Madhow, U.; Manjunath, B.S.; Chandrasekaran, S.; El-khalil, I.; Member, S. ‘Print and Scan’ Resilient Data Hiding in Images. IEEE Trans. Inf. Forensics Secur. 2006, 1, 464–478. [Google Scholar] [CrossRef]
- Pramila, A.; Keskinarkaus, A.; Sepp, T. Multiple Domain Watermarking for Print-Scan and JPEG Resilient Data Hiding. In Proceedings of the 6th International Workshop on Digital Watermarking, Guangzhou, China, 3–5 December 2007; pp. 279–293. [Google Scholar] [CrossRef]
- Wang, C.-p; Wang, X.-y.; Xia, Z.-q. Signal Processing: Image Communication Geometrically invariant image watermarking based on fast Radial Harmonic Fourier Moments. Signal Process. Image Commun. 2016, 45, 10–23. [Google Scholar] [CrossRef]
- Chen, B.; Coatrieux, G.; Chen, G.; Sun, X.; Coatrieux, J.L.; Shu, H. Full 4-D quaternion discrete Fourier transform based watermarking for color images. Digit. Signal Process. A Rev. J. 2014, 28, 106–119. [Google Scholar] [CrossRef] [Green Version]
- Su, Q.; Niu, Y.; Wang, G.; Jia, S.; Yue, J. Color image blind watermarking scheme based on QR decomposition. Signal Process. 2014, 94, 219–235. [Google Scholar] [CrossRef]
- Lin, S.D.; Shie, S.; Guo, J.Y. Computer Standards & Interfaces Improving the robustness of DCT-based image watermarking against JPEG compression. Comput. Stand. Interfaces 2010, 32, 54–60. [Google Scholar] [CrossRef]
- Shih, F.Y.; Zhong, X. High-capacity multiple regions of interest watermarking for medical images. Inf. Sci. 2016, 367–368, 648–659. [Google Scholar] [CrossRef]
- Wu, X.; Sun, W. Robust copyright protection scheme for digital images using overlapping DCT and SVD. Appl. Soft Comput. J. 2013, 13, 1170–1182. [Google Scholar] [CrossRef]
- Ali, M.; Ahn, C.W.; Pant, M. A robust image watermarking technique using SVD and differential evolution in DCT domain. Optik 2014, 125, 428–434. [Google Scholar] [CrossRef]
- Lu, C.; Liao, H.M. Multipurpose Watermarking for Image Authentication and Protection. IEEE Trans. Image Process. 2001, 10, 1579–1592. [Google Scholar]
- Yin, C.; Li, L.; Lv, A.; Qu, L. Color Image Watermarking Algorithm Based on DWT-SVD. In Proceedings of the 2007 IEEE International Conference on Automation and Logistics, Jinan, China, 18–21 August 2007; pp. 2607–2611. [Google Scholar]
- Makbol, N.M.; Khoo, B.E. A new robust and secure digital image watermarking scheme based on the integer wavelet transform and singular value decomposition. Digit. Signal Process. 2014, 33, 134–147. [Google Scholar] [CrossRef]
- Chetan, K.R.; Nirmala, S. An efficient and secure robust watermarking scheme for document images using Integer wavelets and block coding of binary watermarks. J. Inf. Secur. Appl. 2015. [Google Scholar] [CrossRef]
- Liu, Q.; Yang, S.; Liu, J.; Xiong, P.; Zhou, M. A discrete wavelet transform and singular value decomposition-based digital video watermark method. Appl. Math. Model. 2020, 85, 273–293. [Google Scholar] [CrossRef]
- Santhi, V.; Arulmozhivarman, P. Hadamard transform based adaptive visible / invisible watermarking scheme for digital images. Inf. Secur. Tech. Rep. 2013, 1–13. [Google Scholar] [CrossRef]
- Wang, X.; Liu, Y.; Li, S.; Yang, H.; Niu, P.; Zhang, Y. A new robust digital watermarking using local polar harmonic transform. Comput. Electr. Eng. 2015, 1–16. [Google Scholar] [CrossRef]
- Bouslimi, D.; Coatrieux, G. A Crypto-Watermarking System for Ensuring Reliability Control and Traceability of Medical Images. Signal Process. Image Commun. 2016. [Google Scholar] [CrossRef]
- Wójtowicz, W.; Ogiela, M.R. Digital images authentication scheme based on bimodal biometric watermarking in an independent domain. J. Vis. Commun. Image Represent. 2016. [Google Scholar] [CrossRef]
- Sang, J.; Liu, Q.; Song, C.-L. Robust video watermarking using a hybrid DCT-DWT approach. J. Electron. Sci. Technol. 2020, 100052. [Google Scholar] [CrossRef]
- Fan, M.Q.; Wang, H.X.; Li, S.K. Restudy on SVD-based watermarking scheme. Appl. Math. Comput. 2008, 203, 926–930. [Google Scholar] [CrossRef]
- Ghofrani, M.J.S.S. A robust blind watermarking method using quantization of distance between wavelet coefficients. Signal Image Video Process. 2013, 7, 799–807. [Google Scholar] [CrossRef]
- Anuja, D.; Rahul, D. A Review on Digital Image Watermarking Techniques. Int. J. Image Graph. Signal Process. 2017, 4, 56–66. [Google Scholar]
- Hsu, C.-S.; Hou, Y.-C. Copyright protection scheme for digital images using visual cryptography and sampling methods. Opt. Eng. 2005, 44, 1–10. [Google Scholar] [CrossRef] [Green Version]
- Khan, A.; Siddiqa, A.; Munib, S.; Malik, S.A. A recent survey of reversible watermarking techniques. Inf. Sci. 2014, 279, 251–272. [Google Scholar] [CrossRef]
- Qasim, A.F.; Meziane, F.; Aspin, R. Digital watermarking: Applicability for developing trust in medical imaging workflows state of the art review. Comput. Sci. Rev. 2018, 27, 45–60. [Google Scholar] [CrossRef]
- Fabian, B.; Ermakova, T.; Junghanns, P. Collaborative and secure sharing of healthcare data in multi-clouds. Inf. Syst. 2015, 48, 132–150. [Google Scholar] [CrossRef]
- Al-Otum, H.M. Secure and robust host-adapted color image watermarking using inter-layered wavelet-packets. J. Vis. Commun. Image Represent. 2020, 66, 102726. [Google Scholar] [CrossRef]
- Ma, B.; Chang, L.; Wang, C.; Li, J.; Wang, X.; Shi, Y.Q. Robust image watermarking using invariant accurate polar harmonic Fourier moments and chaotic mapping. Signal Process. 2020, 172, 107544. [Google Scholar] [CrossRef]
- Sharma, S.; Sharma, H.; Sharma, J.B. An adaptive color image watermarking using RDWT-SVD and artificial bee colony based quality metric strength factor optimization. Appl. Soft Comput. J. 2019, 84, 105696. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. An improved DWT-SVD domain watermarking for medical information security. Comput. Commun. 2020, 152, 72–80. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, S.; Yang, J. Color image watermark decoder by modeling quaternion polar harmonic transform with BKF distribution. Signal Process. Image Commun. 2020, 88, 115946. [Google Scholar] [CrossRef]
- Das, S.; Kundu, M.K. Effective management of medical information through ROI-lossless fragile image watermarking technique. Comput. Methods Programs Biomed. 2013, 111, 662–675. [Google Scholar] [CrossRef] [PubMed]




| Particulars | SVD | HVS-SVD | FWT | DWTQ | FrFT | DWT-SVD-ABC | Proposed |
|---|---|---|---|---|---|---|---|
| Host Image | 512 × 512 | 512 × 512 | 512 × 512 | 512 × 512 | 512 × 512 | 512 × 512 | 512 × 512 |
| Watermark | 32 × 32 | 32 × 32 | 20 × 50 | 32 × 16 | 64 × 64 | 32 × 32 | 32 × 32/ 64 × 64 |
| Finger Print | Biometric | Biometric | Biometric | Biometric | Biometric | Biometric | Biometric |
| Domain | Spatial | Transform | Transform | Transform | Transform | Transform | Transform |
| S | Manually | Manually | Manually | Automatic | Manually | Automatic | Manually |
| Capacity (b/p) | 0.0625 | 0.0156 | N/A | 0.0104 | N/A | 0.0156 | - |
| Image Name | SVD [38] | HVS+SVD [11] | FWT [10] | DWTQ [41] | FrFT [6] | RDWT [4] | Proposed |
|---|---|---|---|---|---|---|---|
| Lena | 48.3212 | 43.2054 | 22.7807 | 42.6139 | 41.2173 | 44.0207 | 57.6982 |
| Cameraman | 49.3212 | 44.2054 | 23.7807 | 43.6139 | 41.2173 | 43.0207 | 56.6982 |
| House | 46.2274 | 41.3311 | 22.8192 | 43.1897 | 41.2221 | 45.0148 | 55.1524 |
| Airplane | 45.0615 | 42.0315 | 22.6162 | 43.7749 | 41.2274 | 43.0222 | 53.6556 |
| Sailboat | 45.3672 | 33.9873 | 22.6162 | 41.2493 | 41.2165 | 40.0038 | 54.5675 |
| Couple | 46.2274 | 41.3311 | 22.8192 | 43.1897 | 41.2221 | 42.0148 | 52.1524 |
| Baboon | 42.2943 | 37.7291 | 22.8836 | 44.6238 | 41.2227 | 40.0256 | 54.1256 |
| Pirate | 45.4251 | 43.1866 | 22.6162 | 41.2494 | 41.328 | 45.0227 | 51.6896 |
| Bridge | 41.8111 | 35.3789 | 22.4779 | 38.9901 | 41.2623 | 40.1107 | 52.5699 |
| Blond | 42.9307 | 40.5057 | 22.8338 | 43.0604 | 41.2284 | 42.0381 | 54.5689 |
| Dark hair | 47.9664 | 46.8601 | 23.8102 | 42.1843 | 42.2973 | 50.0194 | 54.1256 |
| Einstein | 50.2175 | 44.4398 | 22.6162 | 49.2493 | 41.2186 | 45.0182 | 58.6894 |
| Rose | 44.8065 | 41.7695 | 22.6162 | 42.8834 | 41.2171 | 42.9883 | 55.4586 |
| Barbara | 45.4251 | 43.1866 | 22.6162 | 41.2494 | 41.3289 | 45.0227 | 51.6896 |
| Women | 45.0615 | 42.0315 | 22.6162 | 43.7749 | 41.2274 | 43.0222 | 53.6556 |
| Average | 45.7643 | 41.4120 | 22.8345 | 42.9931 | 41.3100 | 43.3576 | 54.4334 |
| Image | SVD | HVS+SVD | FWT | DWTQ | FrFT | RDWT | Proposed |
|---|---|---|---|---|---|---|---|
| Lena | 1 | 1 | 0.9082 | 0.8936 | 1 | 1 | 1 |
| Cameraman | 0.9268 | 0.8066 | 0.9268 | 0.7734 | 1 | 0.9945 | 1 |
| House | 0.9568 | 1 | 0.9219 | 0.8262 | 1 | 1 | 1 |
| Airplane | 0.9568 | 0.9971 | 0.9248 | 0.8965 | 0.9999 | 1 | 1 |
| Sailboat | 1 | 1 | 0.9111 | 0.8047 | 1 | 1 | 0.9999 |
| Couple | 1 | 1 | 0.9326 | 0.7921 | 1 | 1 | 1 |
| Baboon | 1 | 1 | 0.9209 | 0.8594 | 0.9688 | 1 | 1 |
| Pirate | 0.9564 | 0.9521 | 0.9355 | 0.8848 | 1 | 0.9941 | 1 |
| Bridge | 0.9951 | 0.9789 | 0.9336 | 0.8184 | 0.9866 | 1 | 1 |
| Blond | 1 | 1 | 0.9258 | 0.8382 | 0.9696 | 1 | 1 |
| Darkhair | 0.9951 | 0.9981 | 0.9375 | 0.8523 | 0.9988 | 0.9722 | 1 |
| Eienstine | 0.9551 | 0.9766 | 0.9474 | 0.8184 | 0.9588 | 0.9889 | 0.9999 |
| Rose | 0.9599 | 0.9867 | 0.9245 | 0.8545 | 0.9878 | 0.9678 | 1 |
| Barbara | 0.9854 | 0.9568 | 0.9356 | 0.8105 | 1 | 0.9699 | 1 |
| Women | 1 | 0.9878 | 0.9436 | 0.8208 | 0.9689 | 0.9632 | 1 |
| Average | 0.9792 | 0.9760 | 0.9286 | 0.8362 | 0.9893 | 0.9900 | 0.9999 |
| Image | SVD | HVS+SVD | FWT | DWTQ | FrFT | RDWT | Proposed |
|---|---|---|---|---|---|---|---|
| lena | 0.9915 | 0.9776 | 0.9253 | 0.8376 | 0.9972 | 0.9988 | 0.9999 |
| Cameraman | 0.7435 | 0.9423 | 0.8167 | 0.5832 | 0.6236 | 0.9076 | 0.9998 |
| House | 0.7312 | 0.9518 | 0.6963 | 0.6978 | 0.5531 | 0.9134 | 1 |
| Airplane | 0.9835 | 0.9727 | 0.8494 | 0.6808 | 0.5247 | 0.9973 | 1 |
| Sailboat | 0.4983 | 0.4987 | 0.4975 | 0.4656 | 0.4775 | 0.9988 | 0.9999 |
| Couple | 0.8690 | 0.8311 | 0.8916 | 0.7893 | 0.7781 | 0.8490 | 0.9999 |
| Baboon | 0.9782 | 0.9731 | 0.9510 | 0.7108 | 0.9456 | 0.9982 | 1 |
| Pirate | 0.9031 | 0.9384 | 0.9279 | 0.6832 | 0.9912 | 0.9830 | 1 |
| Bridge | 0.8389 | 0.9576 | 0.9039 | 0.8065 | 0.7476 | 0.9574 | 1 |
| Blond | 0.8398 | 0.8017 | 0.8881 | 0.5365 | 0.8249 | 0.8104 | 0.9998 |
| Darkhair | 0.9250 | 0.8714 | 0.8936 | 0.6408 | 0.8579 | 0.9347 | 1 |
| Eienstine | 0.9466 | 0.9705 | 0.9197 | 0.7699 | 0.9581 | 0.9964 | 0.9999 |
| Rose | 0.4807 | 0.9579 | 0.9761 | 0.6813 | 0.9966 | 0.9972 | 1 |
| Barbara | 0.8754 | 0.7303 | 0.9305 | 0.7006 | 0.8631 | 0.9443 | 0.9999 |
| Women | 0.4807 | 0.4822 | 0.5028 | 0.5286 | 0.4719 | 0.9988 | 1 |
| lena | 0.5150 | 0.5566 | 0.4982 | 0.4758 | 0.4755 | 0.9988 | 0.9999 |
| Average | 0.8175 | 0.8384 | 0.8168 | 0.6618 | 0.7548 | 0.9552 | 0.9998 |
| Attacks Category | SVD | HVS+SVD | FWT | DWTQ | FrFT | RDWT | Proposed |
|---|---|---|---|---|---|---|---|
| Attacks/No Attack |  Recognized |  Recognized |  Not Recognized |  Not Recognized |  Recognized |  Recognized |  Recognized |
| Median filter |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |
| Rescaling |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |
| Gamma Correction with 0.2 |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |  Recognized |  Recognized |
| Rotational attacks |  |  |  |  |  |  Recognized |  Recognized |
| Cropping |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |
| Histogram equalization |  Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |  Recognized |
| Noise (Gaussian) |  Recognized |  Not Recognized |  Recognized |  Not Recognized |  Recognized |  Not Recognized |  Recognized |
| JPEG Compression |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |
| Noise (S&P) |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |
| Deletion of rows and column |  Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |  Recognized |
| Filters |  Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |  Not Recognized |  Recognized |
| Sharping |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |  Recognized |  Recognized |
| Contrast adjustment |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |  Recognized |  Recognized |
| Flipping of Rows |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |
| Flipping of Column |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Not Recognized |  Recognized |
| Index | SVD-P-value | HVS+S-P-value | FWT-P-value | DWTQ-P-value | FrFT-P-value | RDWT-P-value | Sig |
|---|---|---|---|---|---|---|---|
| 0 | 0.100 | 0.100 | 0.003 | 0.003 | 0.028 | 0.028 | ↑ |
| 1 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
| 2 | 0.003 | 0.006 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
| 3 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
| 4 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
| 5 | 10.006 | 0.006 | 0.100 | 0.003 | 0.003 | 0.657 | ↑ |
| 6 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
| 7 | 0.003 | 0.011 | 0.003 | 0.003 | 0.003 | 0.006 | ↑ |
| 8 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
| 9 | 0.003 | 0.003 | 0.100 | 0.003 | 0.028 | 0.028 | ↑ |
| 10 | 10.006 | 0.006 | 0.006 | 0.003 | 0.003 | 0.003 | ↑ |
| 11 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
| 12 | 0.003 | 0.006 | 0.003 | 0.003 | 0.028 | 0.028 | ↑ |
| 13 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | 0.003 | ↑ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ud Din, S.; Jan, Z.; Sajjad, M.; Hussain, M.; Ali, R.; Ali, A.; Lee, S. Secure Exchange of Medical Data Using a Novel Real-Time Biometric-Based Protection and Recognition Method. Electronics 2020, 9, 2013. https://doi.org/10.3390/electronics9122013
Ud Din S, Jan Z, Sajjad M, Hussain M, Ali R, Ali A, Lee S. Secure Exchange of Medical Data Using a Novel Real-Time Biometric-Based Protection and Recognition Method. Electronics. 2020; 9(12):2013. https://doi.org/10.3390/electronics9122013
Chicago/Turabian StyleUd Din, Shams, Zahoor Jan, Muhammad Sajjad, Maqbool Hussain, Rahman Ali, Asmat Ali, and Sungyoung Lee. 2020. "Secure Exchange of Medical Data Using a Novel Real-Time Biometric-Based Protection and Recognition Method" Electronics 9, no. 12: 2013. https://doi.org/10.3390/electronics9122013






