Building Standardized and Secure Mobile Health Services Based on Social Media
Abstract
:1. Introduction
2. Materials and Methods
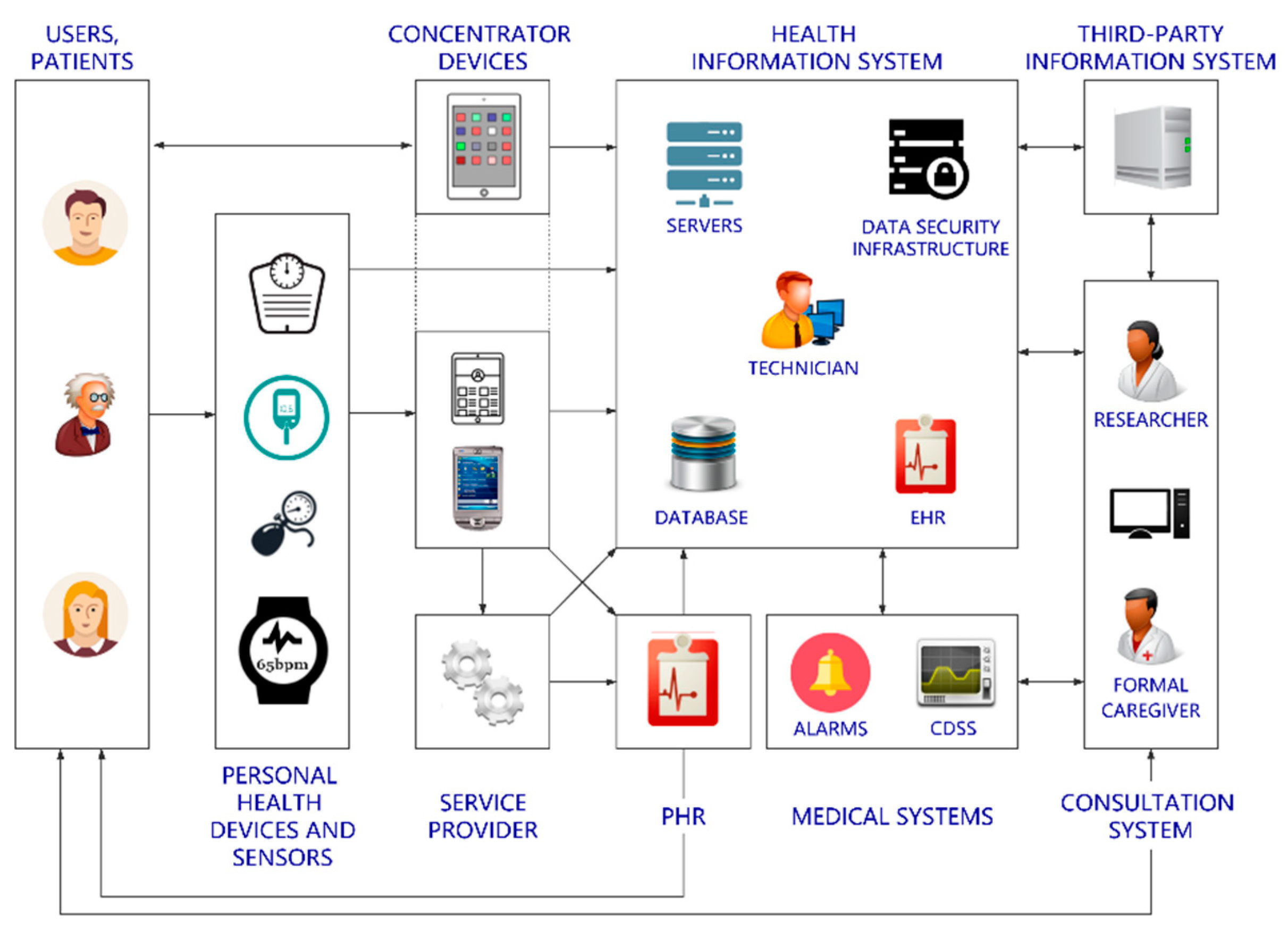
2.1. Analysis of Traditional Telemonitoring mHealth Architectures
- The patients or users: They record the biomedical measurements remotely.
- The formal caregivers: Nurses and physicians who review the information and follow up patients/users.
- Researchers: Eventually, a researcher would analyze the data gathered from a patient/user or a group of them to investigate into a specific scenario or pathology.
- The technicians: They are in charge of ensuring that the hospital devices and the back-end services work properly.
2.2. Limitations of the Traditional Approach, Current Evolution and Potential Features
3. Results
3.1. Proposal of a Generic mH3S Architecture
3.1.1. Actors of the Proposed Architecture
- User/Patient: They will gather the biomedical information and use a mobile phone or tablet to post them. They could also receive feedback from formal or informal caregivers.
- PHDs: The medical devices used to monitor the user’s status.
- Informal caregiver: A friend, a neighbor or a relative that helps the user/patient to monitor and control their biomedical data within the healthy range of values. Informal caregivers are typically in charge of a reduced number of user/patients.
- Formal caregiver: A healthcare provider associated to a professional formal system, e.g., physicians, nurses or social workers. They are able to take care of a relatively large number of patients.
- EHR/HIS: This represents the traditional EHR/HIS. A proxy would be required to receive the biomedical data (by means of the social media API), decrypt, decode and send such information—with an appropriate format– to the actual EHR/HIS, which would store the information. This may need further policies in order to ensure the correct identification of the sender.
- Cloud providers: Such systems may be used for further computing (e.g., signal processing), redistribution or massive storage.
- Researcher: They would perform medical research over a potentially high volume of anonymized biomedical information thorough appropriate data mining. The open lock in Figure 2 means that the content has been decrypted—and anonymized—for research purposes.
- Social media: The core of the proposed system, which is used as a backbone for communication and, to a certain extent, storage purposes.
3.1.2. Configuration, Usage and Communication Flow
3.1.3. Eligible Social Media
- The social media must offer a public API, so that the medical information can be exchanged programmatically. Most social media today offer this option.
- The social media must allow the sharing of information among users. Naturally, this is something that most social media enable, since it is part of the foundation of social media themselves.
- The social media must allow the sharing of multimedia contents, where the biomedical information would be embedded. Again, this is a common feature in current social media.
- The social media API rate limits and delays (if present) must be good enough to support mHealth services exchanging biomedical information in a sufficiently fluent fashion.
- The social media must fulfill the security and privacy regulatory requirements where applicable (GDPR, HIPAA, etc.)
- If the social media has a comprehensive, non-expiring search engine that allows searches against past posts using the API, the social media could be used as a reliable cloud storage system. Otherwise, the architecture shall rely on distributed local storage or re-posts for handling persistence.Given that the data uploaded will be encrypted, the search would rely on additional plaintext keywords. For example, the user could add a comment (e.g., “#vitalsigns” or “#myPHR”) alongside the picture with biomedical data embedded, so that the social media search engine can find the post later. A wise selection of plaintext keywords is naturally required to preserve the actual content.
- If the social media has no API rate limits, the architecture can be scaled more easily. Some social media may offer paying plans for higher API rate limits. In any case, the limits established by most social media are high enough to support small-scale project, such as those involving informal caregiving.
- If the social media enables closed, easy-to-administrate groups, the architecture could be used for helping communities of users, such as users/patients with the same condition.
- If the social media enables private messages, the architecture can provide an extra layer of privacy.
- If the social media allows the verification of accounts, hospitals and formal caregivers could make use of them, increasing thereby users’ trust.
3.1.4. Formatting of the Biomedical Objects
- Standards and Interoperability: First, the medical information shall be standardized with a medical standard, e.g., HL7, SCP-ECG, DICOM, etc. This enables that the information involved be transmitted and stored in an open, known format, which ensures a common structure, fostering thereby further exchange with hospitals or service providers. The selected standards may also use a medical terminology as a reference, such as SNOMED-CT.
- Security and privacy: To ensure the security and privacy of the users, the exchanged biomedical data, which were previously standardized into the medical standard chosen, e.g., HL7, shall be subsequently encrypted and signed. To do so, we propose that the architecture shall rely in any of the existing, standardized envelopes, such as the Cryptographic Message Syntax (CMS) [41] or openPGP (open Pretty Good Privacy) [42], which are able to encrypt and sign arbitrary data. These envelopes support a set of cryptographic algorithms. Thus, when implementing a specific envelope, a number of algorithms should be selected among the aforementioned set. In general, security envelopes are hybrid cryptographic systems, meaning that they combine symmetric and asymmetric cryptography. First, a session key is generated and used to encrypt the plain data. Then, the session key is encrypted with the public key of the receiver. The first process is performed fast (in bytes/second) while the latter is slower. However, given that the session key is small compared to the data to be encrypted, the whole process is carried out swiftly. All keys shall be created using high entropy key generators and have appropriate lengths in order to guarantee resilience against cryptanalysis.All cryptographic-related activities (cryptographic functions and cryptographic material management) are encouraged to be performed and stored inside a Trusted Platform Module (TPM).
- Presentation: The architecture proposed is based on social media, and as such, it is desirable that the information exchanged be presented in a user-friendly way. Therefore, we propose that the biomedical information—after being standardized into a medical standard and secured in an envelope—be embedded into a multimedia content. Such content could be a simple static image, an animated image, an audio file, a video file, etc., as long as the chosen social media supports the selected format(s).
- Embedding: Social media usually limit the amount of characters that can be sent in a single post. Thus, embedding the biomedical information—standardized and encrypted—into a multimedia content—such as image, audio or video—not only favors user friendliness, but it also provides a much higher data-per-post ratio. There exist a wide variety of embedding algorithms in the literature. As an example, an algorithm aimed at embedding biomedical information into images can be found here [43]. Any embedding algorithm could be potentially used within the architecture proposed. Nonetheless, in the architecture proposed, some features related to the embedding process have to be taken into account. First, the multimedia content has no clinical meaning per se. Second, the fact that there are data embedded has not necessarily to be a secret. Third, there is a need for some manipulation resilience—since social media may process images or videos for compression purposes. Finally, all embedded data must be flawlessly recovered. In general, when selecting an embedding algorithm, it is worth mentioning that there is usually a trade-off between speed, distortion and robustness, as discussed below in Section 4.
3.2. Technical Proof-of-Concept Implementation of the Architecture Proposed
3.2.1. Actors of the Implemented Architecture
3.2.2. Configuration, Usage and Communication Flow
3.2.3. Social Media Selected
3.2.4. Implemented Formatting of the Biomedical Objects
- Standards and Interoperability: HL7 version 2 has been selected to provide interoperability. Such standard aims at supporting hospital workflows by means of short, human-readable messages. More specifically, the message implemented is the “unsolicited transmission of an observation message” (referred to as “ORU” type). This message gathers the clinical findings of the user/patient. For enhanced interoperability, the findings are referred to with the appropriate LOINC [46] code, which is a common terminology for laboratory and clinical observations. In addition, the units of measure are expressed through Unified Code for Units of Measure (UCUM) [47], which is a code system intended to include all units of measures being contemporarily used in international science, engineering, and business.
- Security and Privacy: Regarding the social media selected, posting on behalf of an account in Twitter relies on version 1.0A of OAuth [40]. OAuth is a protocol aimed at allowing users to grant access to third-party applications to their account without sharing their password.As regards to the security envelope, we implemented openPGP, which allows the encryption and digital signature of messages. The encryption algorithms behind openPGP are Advanced Encryption Standard (AES) and Rivest, Shamir and Adleman (RSA). The length of the keys is 128 bit for the session keys and 2048 bit for the asymmetric keys. The digital signature algorithm is SHA-256. openPGP is based on the Web of Trust concept, a decentralized Public Key Infrastructure (PKI) where every user can potentially be a Certification Authority (CA), so a user’s certificate can be signed by other users, which in turn creates an open way of distributing public keys. In practice, we exchange the public keys by scanning a QR code and store them in a PGP keyring. In order to accomplish the implementation, we used the Spongy Castle Android library, which is a collection of cryptography APIs repackaged from the Bouncy Castle Java library.In addition, the Twitter API post and get requests rely on HTTPS with in turn uses the Transport Layer Security (TLS) protocol, which enhances communications security and privacy.
- Presentation: Among all the possibilities of multimedia content available, we propose that the biomedical blob—i.e., the clinical findings formatted in HL7 and subsequently encrypted and signed with openPGP—be inserted into a pre-existing picture in compliance with a “Red Green Blue + Alpha” (RGBA/ARGB) color model (see below).
- Embedding: A simple embedding algorithm has been implemented, and it is explained as follows. As is well known, a raw image contains a number of pixels, each of them comprised by four bytes: three for color information—red, green and blue—and one byte related to transparency—also referred to as alpha channel. In this implementation, two versions have been tested:
- ○
- In the first one, the data blob is embedded into the picture by replacing the transparency bytes of the pre-existing image with the bytes of the data blob. This modification will add some “noise” to the image.
- ○
- In the second one, the bytes to be embedded are preprocessed, adding 0x85 to each byte beforehand (see Figure 6). The rationale behind this approach is as follows. We are embedding openPGP data. openPGP uses Radix-64 encoding, which is similar to Base64 [48], but with an additional 3-byte cyclic redundancy check. Base64 was designed to convey data across channels that only reliably support (printable) text content. Thus, the most common Base64 implementation uses these 64 characters: A–Z, a–z, 0–9, plus symbols + and/. Those will be the most frequent characters. It also needs a character for padding (=), and openPGP will use line feed and carriage return to introduce BEGIN and END lines. Among those, the highest ASCII character is “z” (hexadecimal 0x7A). Adding 0x85 to 0x7A results in 0xFF, meaning that such pixel would be fully transparent after the embedding. This mechanism allows a less noisy image (the embedding uses bytes closer to transparent) at a cost of longer compression (the more transparent the bytes, the more complex the image in terms of color variation). See Section 4.2 for a numerical discussion.
4. Discussion
4.1. Discussion about the Overall Architecture
- Architecture: Architecturally speaking, this paper is innovative and different to every other approach published in the literature. We propose and end-to-end, encrypted and interoperable service running over online social networks. By creating and managing a pair of keys, the users become complete owners of their data. In addition, this is achieved without the users having to spend any money or deploying complicated frameworks. The social networks have usually powerful data centers with high uptime availability. Thus, the users are able to leverage such servers without actually sharing any personal/medical information travelling through them. Moreover, the process of information exchange is user-friendly.
- Social media: The importance and necessity of the introduction of social media for mHealth architectures is due to a number of reasons. They are user-friendly, social, empowering, self-manageable, decentralized, flexible, easy to deploy, global, (usually) free of charge, with high availability data centers, low latency and a vast mass of users.There are some other drawbacks or debatable characteristics as well. For example, the social media the architecture relies on may be a private company. This implies that the social media may unilaterally decide to modify the publicly exposed API. This could lead to temporary unavailability of the mHealth service until the applications are reprogrammed and redistributed. However, although the modification could be decided unilaterally, they are always announced in advance. Social media offer temporal windows to adapt the applications relaying on their API to the new situation. If the API is discontinued or the criteria for being an eligible social media are no longer met, the mHealth service as it is would be forced to definitive closure. Such reliance on corporations could be grappled with by using—or implementing—an open, decentralized social media, such as the Twitter-like microblogging systems GNU social [49] or Mastodon [50], or the Facebook-like, non-profit, user-owned, distributed, social media Diaspora [51]. However, users and caregivers would be forced to migrate to—or at least create a new account for—this service, while the number of active users in the main social media—Twitter, Facebook, etc.—is rather big, which clearly eases adoption. Users may join existing servers of open social media, which could be a simple option, or alternatively, servers could be installed and controlled by user themselves or by formal or informal caregivers. However, installing and maintaining a server is not a simple process for most users. With the proposal depicted in this paper, however, the only required set-up is the installation of the applications in mobile phones, which is easy and straightforward, even for users with reduced technological literacy.Another point of debate is the proposal of using social media as a backbone. As opposed to traditional clouds, social media offer limited capabilities for storage and searching, and they do not provide computing power whatsoever. Nonetheless, social media are user oriented, and they certainly enable data communication, which may suffice for most telemonitoring use cases (see Section 4.2. for a specific analysis on speed and data capacity).The decentralized nature of the architecture presented here is also debatable. The authors propose an architecture based on social media opposed to cloud services, while social media are themselves cloud based. However, social media are used in the system as a backbone. In traditional architecture proposals, the biomedical data were conveyed through a typical client/server architecture to a computing cloud or sent to a single HIS located at the hospital, where they would be persisted. By using the proposed architecture, the biomedical data are scattered throughout the mobile devices of the users/patients and formal/informal caregivers. Thus, the architecture is, by nature, decentralized. Biomedical data do go through and are stored in the servers of the social media selected, but encryption prevents data from being accessed by them.The actual worth of introducing social media is something that requires further research and falls beyond the scope of the paper. The perceived worthiness should be validated in real scenarios. In any case, the success of the platform may depend on the final users and their technological literacy, as well as on the specific architecture selected, among other factors.
- Standards and Interoperability: In principle, any standard is eligible for the proposed architecture. It is noteworthy however, that some standards may be more suitable for a specific use case or may be more practical depending on whether such standard is used in some other place within the overall architecture. In any case, the inclusion of relevant biomedical standards in the architecture allows the straightforward integration of the gathered biomedical health information in healthcare systems, whenever required.
- Security and privacy: The claimed security and privacy is provided by the end-to-end envelope encryption. This provides confidentiality, via a combination of symmetric and public-key encryption. Additionally, the digital signatures provide authentication and integrity validation. The integrity validator could be crucial in an embedding application like this, since it can be used to verify that the content of the message has not be tampered with.The proposed architecture only adds one mandatory layer of encryption, that enforced by openPGP. The rest of the security measures are built-in features provided by the social network or the internet protocols. Generally, the users cannot opt-out of such measures, but they are applied in a transparent way.Once configured, the use of the application is straightforward. However, a trade-off between security/privacy and usability is always present when designing technological architectures. In general, including additional security measures reduces usability. In the proposed approach, the security and privacy procedure added implies the management of a pair of public/private keys (generation, exchange and storage). Users must create a pair of public/private keys. This has to be done only once and it is as easy as pushing a button. The exchange of the public key is only required when contacting to a new user. The procedure could also be simple, for example, transmitting the key through a messaging app or using a QR code. Finally, users would only have to manage a way to access the keys stored in the keyring (e.g., password, pin, drawn pattern or even biometric authentication, such as fingerprint or facial recognition). Thus, the additional complexity of the platform could be considered low. Although the added complexity is naturally a subjective matter, the authors consider that the improved security and privacy outweighs the decreased usability.The security and privacy measures presented herein are structured under an end-to-end paradigm, from the user/patient device to the formal/informal caregiver device. This means that the security protocols used are stacked as different layers that partially overlap each other, providing security along the whole communication and storage process. For example, the requests to the social media API may be carried out using HTTPS/TLS, but this covers only the segment from the devices to the social media server. The additional security envelope provides further encryption so that the information is not in accessible even within the social media servers.For increased security, the algorithms selected shall be—whenever possible—different from and complementary to the algorithms already defined by the physical network, the social media and the biomedical standard—if they implement any. This way, if one cryptographic algorithm is compromised, the other may still be valid. In any case, if any of the chosen algorithms for a specific implementation were compromised, it would have to be replaced with another existing algorithm considered secure and suitable for the application at such time.Users/patients may configure multiple receivers of biomedical information within the application. The architecture proposed implies the need of creating one encryption per follower. This may cause scalability issues, although this is not a problem in small-scale projects with few formal or informal caregivers. This end-to-end encryption is required in order to prevent potential eavesdropping—including the social media service provider itself—and is widely implemented in digital services today—such as Telegram, Signal or WhatsApp.Security and privacy could still be compromised due to, for example, the user/patient exposing his/her private key. In that case, the biomedical information should be removed from the social media network. In general, online social networks are exposed to a variety of privacy and security threats, such as phishing, fake profile creation, or identity clone attacks [52]. The proposal presented herein is vulnerable to these attacks inasmuch as it relies on both the internet and on online social networks. Internet users in general and online social network users in particular must be aware of them and follow general recommendations. For example, they should customize adequate privacy settings of the social network or build trust with those applications and persons receiving or managing the users’ personal information [52]. In addition, online social networks today offer recommendation to minimize these potential threats. For example, Twitter has published a webpage to offer guidance and help with general safety and security concerns [53], such as potentially compromised/hacked accounts, report impersonation accounts, and fake accounts, among others.In any case, for the architecture to function, the concept and scope of trust needs to be addressed. In a scenario with a formal caregiver, both the caregiver and the final user must trust the application. However, this could be achieved if the application is developed and distributed via official channels by the hospital itself. In addition, users must naturally trust the doctor suggesting the use of the application. Effective health care is based on substantial trust between patients and professionals, including the clinical tools they choose to use [54]. In any case, patients should be properly informed and should sign an informed consent beforehand. For the informal caregiver scenario, the user and the caregiver must trust each other. This could be easily achieved, since they know each other personally and would even be relatives. They must also trust the application. Such application could be the same one as in the formal caregiver scenario, that is, developed and published by a hospital they trust. Finally, regardless of the scenario, the application code could be open source in order to enhance trust through transparency.Having this concept of trust among users developed, there is no reason to mistrust the other end. Therefore, the exchange of the public keys is always performed in a way that can always be considered trustworthy. The exchange of public keys could be easily performed in person. For the formal caregiver scenario, the exchange is performed at the moment of enrolling in the program, for example, by showing a printed QR code for the other user to scan. Nevertheless, if the public keys are sent through the internet, there are mechanisms to confirm that the keys have not been tampered with. For example, users could generate a token of the public keys (e.g., a hash) and exchange them through an alternative channel (e.g., they would be short enough to be read over the phone).All said, despite of the measures proposed, no security scheme is 100% secure or private. There is always room for security or privacy breaches. However, the proposed architecture provides users with a framework that is secure and private enough to create a feasible mobile health scenario. In general, a project like this does require constant maintenance and supervision. Specifically, those parts related to cryptography (libraries, algorithms, keys, etc.) might be compromised and need special attention.
- Presentation: We proposed embedding the biomedical data blob into a multimedia content. The rationale behind this decision is twofold. First, because of the social benefit: it is clearly friendlier to share a beautiful image than an array of apparently nonsense bytes. Additionally, there is also an economy factor, measured in number of posts per biomedical data. Social media usually restrict the maximum amount of characters (e.g., 140—recently 280—Unicode codepoints in a tweet) or the maximum size of an image or video (a few megabytes usually) shared in a single post. Thus, the multimedia approach was selected since it is possible to embed far more data in a single social media post if a multimedia content is used, compared to plain text. In exchange, the approach selected increases the overhead and the processing load, which implies higher delays. Nevertheless, this is not an issue, since the architecture is not intended to work in real time, and the encryption algorithms are fast enough, given the amount of biomedical data that fit in a single multimedia content.
- Embedding: Designers have to take into account that social media may tamper with the uploaded multimedia content in a way that may not be public, and, if the embedding algorithm selected is not robust enough, the information could be corrupted partially or completely. In the proposed architecture, a robust enough embedding algorithm could prevent in practice any potential data corruption. However, if the data are corrupted, the recipient will detect that the information has not been received properly. The envelope provides a mechanism to check this. Thus, the receiver could ask for a retransmission. Then, the embedding could be carried out using a more robust algorithm to prevent the same problem from occurring again. The sender’s application could be provided with a pool of embedding algorithms, ordered in terms of robustness, so that the simplest/fastest one would selected, as long as the data could be retrieved at the other end. In any case, there is a trade-off between speed and robustness.
4.2. Discussion about the Proof of Concept
- Social Media: Private messages have been used to address a particular receiver. However, users may exchange other images aside from the healthcare service. If that is the case, checking the alpha channel and looking for the openPGP data structure is an effective mechanism to detect if there is actual biomedical information embedded into the picture.Twitter offers a kind of groups (referred to as “lists”), which can be public or private. However, users are not allowed to post directly to a list, so that every member of the list receive the tweet. Alternatively, in the system proposed, users can send a private message to all receivers (see the paragraph below).We propose sharing the pictures through private messages, although this could be carried out via the public timeline. While the former would enable the possibility of multiple receivers in one single post/image, the latter enhances privacy.As regards to the Twitter API maximum rates, it can be noted that they are generous enough for store-and-forward, small-scale projects, but they may not be enough in scenarios requiring higher data rate transmission or when dealing with a vast amount of users/patients and/or caregivers.Twitter offers a free search API, but it is restricted to the past seven days and it is focused on relevance—and not in completeness. This limits the use of Twitter as a reliable persistence handler. However, they offer some enterprise, high-level search APIs that could be implemented with a monetary cost.Finally, since users only publish images that are aligned with their taste and the topic of their usual social posts, the system is minimally invasive with regard to information noise. In any case, users may also create a different account for this purpose.
- Standards and Interoperability: Version 2 of HL7 is sufficient for the use case portrayed in the proof of concept—a user connecting with an informal caregiver. The amount of data transmitted in an HL7 version 2 message does not give rise to any issues –regarding the embedding, for example. In the proof of concept, there is no integration with personal health records or higher HIS, so one can envision that the use of a standard may not be necessary. However, the implementation of HL7 leaves open the possibility of further integration.
- Security and Privacy: We chose to implement openPGP over CMS. Technical differences among them are not decisive. Indeed, both can be used as a base for Secure/Multipurpose Internet Mail Extensions (S/MIME), which is an Internet Engineering Task Force (IETF) standard for public key encryption and digital signing of MIME data. CMS is widely used by companies by building a PKI through X.509 certificates, which had to be approved and signed by a CA beforehand, which usually requires some kind of payment. openPGP, on the other hand, provides an open, decentralized, free system for certificate management, which are the main reasons why we chose to implement this envelope.The security library chosen, Spongy Castle, based on Bouncy Caste, currently supports all versions of Android. However, Android has announced the deprecation of Bouncy Castle. Therefore, the implemented applications will require changing to (most likely) the default Android implementation in the forthcoming future.Regarding OAuth, we have implemented version 1.0a. Twitter supports both versions 1.0a and 2.0. However, only version 1.0a can be used for posting on behalf of another account.
- Presentation: The image shared in the proof of concept is pre-stored in the application. However, in order to enhance the user satisfaction and personal binding, the application could be improved by letting users upload their own images.We have selected an image with a RGBA/ARGB color model in order to modify the alpha channel while embedding the information. One could envision that tagged formats could be selected to embed the information in tags, thereby eliminating distortion. However, this could not be implemented in this specific proof of concept, since, at the moment of writing, Twitter strips and discards the metadata from uploaded images.
- Embedding: The algorithm implemented works flawlessly under the conditions documented. As the transparency information is being modified, the process naturally distorts the image. Less distorting and more robust algorithms could be implemented. However, as discussed above, there is a trade-off between speed and robustness/distortion. In our implementation, version 2 of the embedding algorithm results in less noisy images, but it takes longer to compress them (see Table 2).The fact that the image becomes distorted does not have any effect on the “clinical” functioning of the platform, since the picture itself has no clinical meaning. However, a distorted image may diminish the “social” component of the platform. Under the conditions tested, with only a few bytes of information being transmitted, little distortion can be perceived by the human eye (see and zoom the dog picture in Figure 4b).Additionally, since the social media processing algorithm may not be public and, moreover, the owners of the social media can change the internal algorithms over time without notification, there is a need to review and update the proposed embedding algorithms periodically. It is worth noting as well that, since social media select their processing algorithms, an embedding algorithm that works for a social media may not work for another.
- Data capacity: In order to discuss the performance of the proposed technical proof of concept, we present below an analysis in terms of data capacity and speed (at the transmitter end). Two scenarios were considered: the one proposed for proof-of-concept (a small-scale telemonitoring system transmitting just a few bytes) and a boundary scenario for the proof of concept (when all the space available is used up). In order to assess the speed, two sizes of images were tested for the small-scale scenario. For the boundary scenario, both versions of the embedding algorithm were tested.For calculating the space available in the latter scenario, some calculations have to be performed, according to Twitter’s current image support policies [55]. For this proof of concept, we have decided to use the alpha channel for embedding purposes. Among the image formats supported by Twitter, WebP and Portable Networks Graphics (PNG) provide such channel. However, Twitter states that it will transcode all WebP formats to 85% quality Joint Photographic Experts Group (JPEG) with 4:2:0 chroma subsampling. This may distort the embedded information. A PNG-32 (8 bits per channel ARGB), on the other hand, will be left as-is if the image has more than 256 colors and it is 900 pixels or smaller in the longest dimension (that is, it can fit into 900 × 900). If it has fewer colors, it will be transcoded to PNG-8. If it is greater than 900 × 900, it will be tested to consider if they will remain PNG or if they will be converted to JPEG, being the latter more likely.Thus, if these requirements are met, an image with 900 × 900 pixels and alpha channel could be uploaded and it will not be transcoded by Twitter. Thus, the receiver application will be able to retrieve the embedded information flawlessly. Given that a pixel is composed of 4 bytes (ARGB/RGBA), a maximum of 900 × 900 = 810,000 alpha-channel bytes are available. However, not all of those bytes would be actual biomedical information. First, the begin PGP and end PGP lines, the version line, the digital signature and the aforementioned redundancy check shall be deducted (95 bytes). The remaining data are encoded in Radix-64. In such encoding, 4*(n/3) characters are needed to represent n bytes, and this needs to be rounded up to a multiple of 4. In this case, 1 byte is needed for padding. After decoding, the resulting data include the session key encrypted with the RSA algorithm (in our proof-of-concept, once encrypted, its length is 2048 bits, that is, 256 bytes) and the biomedical data encrypted with the AES session key. AES works in blocks, in our case of 128 bits (16 bytes). Therefore, some padding may be needed. In this situation, 4 padding bytes are required. At the end, a maximum of 607,168 bytes of biomedical data would be available.The amount of biomedical data could fit in approximately 600 kB depends on the data themselves and the medical standard selected, if any. For example, the size of the HL7-compliant message generated in the proof of concept (including weight, heart rate, oxygen saturation and blood pressure) is just 439 bytes in HL7-formatted plaintext, 1035 bytes after encrypting and encoding. In a 900 × 900 image, it will distort only the first row and partly the second row (out of 900 rows). A non-compressed SCP-ECG file (12 ECG leads, 1000 samples/second, 2 bytes/sample, 10 s) is just 240 kB of ECG data, plus a few bytes of SCP-ECG metadata. A number of compression techniques could be applied to enable larger registration times. For the case of digital images, a DICOM file would also have some metadata, but a picture of 600 kB would probably have enough quality for a telemonitoring scenario (e.g., teledermatology). It is worth noting that DICOM itself also supports image compression using JPEG2000 [56], and it could be used internally. Although there is lack of consensus about the tolerable degree of compression, JPEG2000 have been reported to allow compression ratios ranging 30:1–50:1 without affecting the clinical quality. Even that could be enhanced by selecting an optimized, ad-hoc parametrization for the specific medical use case [57]. Thus, with a 40:1 compression ratio, a 600 kB compressed image would mean a 24 MB raw image (8 megapixels RGB), which should be enough for a teledermatology consultation.Furthermore, this is considering just one tweet. Naturally, more than one tweet could be used, enabling the transmission of large amounts of data (even the whole EHR) in a few tweets. The size of an EHR depends on a variety of factors. As a reference, in a 2011 report of the Beth Israel Deaconess Medical Center, a teaching hospital of Harvard Medical School, it was published that they generate 1 terabyte of clinical text data (structured and unstructured) per year and 19 terabyte of image data per year [58]. With 250,000 active patients at that time, that means 80 megabytes per patient per year. That translates to approximately 138 tweets per patient per year, that is, one tweet per patient every 2–3 days.
- Speed: The speed of the whole procedure depends on a variety of factors. For example, the processor, the programming language, the programming coding efficiency, the amount of data to be embedded, the size of the image, the embedding algorithms and the size of the keys, among others.Regarding the cryptography algorithms, the test data published in [59] have been used as a reference. Such tests were run with an Intel Core 2 at 1.83 GHz (similar to current mobile devices). The algorithms selected are those comparable to our proof of concept: AES (128-bit key) and RSA (2048-bit key). The results are shown in Table 2 for the two aforementioned scenarios. Such table also shows the time required for encoding in Radix-64, considering the same 1.83 GHz processor. The speed used for the calculations is 2 cycles/byte, which is a typical speed for base64 encoding/decoding, although it could be up to ten times faster using vector instructions [60]. The data show that encrypting and encoding is a matter of milliseconds (subtotal 1, row number 05 in Table 2), even for ~600 kB of data. The most time-consuming task would be the RSA encryption (row 02 in Table 2) for both scenarios.As regards the time required for embedding, there are not publicly available data, because this is not a standard algorithm. The authors have performed a pool of tests under the following conditions. The process measured includes opening a bitmap image, setting up the necessary variables, modify the required alpha-channel bytes and generate a compressed file in PNG format in ARGB/RBGA.First, the system was tested for the small-scale telemonitoring scenario. More specifically, 1035 bytes (corresponding to the size of the encrypted HL7-compliant message) were embedded into the alpha channel of the dog picture in Figure 4b, testing two sizes: 900 × 900 pixels and a rescaled version of 225 × 225 pixels (exactly 16 times less pixels). Secondly, we performed two tests (one per each version of the embedding algorithm) using all space available (900 × 900 alpha bytes). The rationale of testing two different versions of the embedding algorithm is that the PNG compression uses DEFLATE [61], a lossless compressed data format involving a combination of Lempel–Ziv-77 compression algorithm and Huffman coding. This implies that faster compression could be achieved for images with small variations of color. In other words, the higher the transparency, the faster the compression. Conversely, the image would be noisier and therefore less friendly.The tests were run in a current (as of 2019), mid-range mobile phone with an octa-core MediaTek Helio G90T, including 2 ARM Cortex-A76 at 2.05 GHz and 6 ARM Cortex-A55 at 2.0 GHz, 6 GB of RAM and running Android 9.0 (PPR1.180610.011). We performed 10 executions per test and calculated the average time and the standard deviation. This provides the reader with a notion of the central value of the results (arithmetic mean) and the amount of dispersion of the set of results (standard deviation). Throughout the paper, the results are expressed as “mean ± standard_deviation”.The results are shown in Table 2. In general, the standard deviation is low compared to the average. This suggests that the data are clustered around the mean. The embedding is fast (row 12 in Table 2) for both small-scale and boundary scenarios, taking up less than 30 ms in any case. It is particularly fast for the smaller image, where it needs only 3.7 ± 0.5 ms. When comparing the two embedding algorithms for the boundary scenario, we can observe that the shifting process itself (that is, adding 0x85 to each byte) only adds 0.3 ms (5.6 ± 0.5 ms vs. 5.3 ± 0.5 ms, row 11 in Table 2). For the small-scale scenario, the two embedding algorithms were not tested, as they would behave similarly, since only a few bytes are being modified, and thus the image remains largely unaffected (see zoomed images in row 07 in Table 2).As regards the PNG compression, it can be seen that it depends largely on the size of the image (38.1 ± 0.6 ms at 225x255 vs. the rest, several times slower, at 900 × 900, row 13 in Table 2). The other factor affecting the PNG compression time is the version of the embedding algorithm. The compression of the shifted version is slower compared to the non-shifted one (703.5 ± 4.2 ms vs. 548.5 ± 3.8 ms, row 13 in Table 2). On the other hand, the image is clearer, which could improve users’ engagement (row 07 in Table 2).The data show that the bottleneck of the whole procedure is the PNG compression (row 13 in Table 2). Approximately 80-95% of the total time (row 14 in Table 2) is spent on the PNG compression. In these tests, we use the built-in compressor provided by Android, which is single-threaded. It is arguably feasible to parallelize the compression process, achieving a reduction of time that would scale linearly with the number of cores of the machine. Besides the cores of the central processing unit, mobile phones nowadays also incorporate multi-core graphic processing units, which could also be used for parallelized compression. To the best of our knowledge, there is no Android library available able to perform a parallel compression of PNG files (at the moment of writing). There exist, however, Java-based parallel compressors for GZIP [62], a file format similar to PNG, since it is also based on DEFLATE. Nevertheless, programming such a compressor falls out of the scope of this paper.As a conclusion, for both the small-scale telemonitoring scenario and the boundary scenario, the whole process could be performed rather fast (less than 1 s in any case). It can be carried out considerably faster with smaller images: 48.2 ± 0.9 ms (225 × 225) vs. 719.6 ± 9.6 ms (900 × 900). In addition, using the non-shifted algorithm, the process can be performed faster in the boundary scenario to the detriment of noisier images. In any case, the results show that the speed would not be a critical issue for most mHealth scenarios.
5. Conclusions
- Novel architecture: Instead of a client-server architecture or a cloud-based architecture, we propose an end-to-end system that leverages online social networks as a backbone.
- Empowered users and patients: Users do not rely on anyone to create a secure, private communication channel. They decide what to share and with whom.
- User-friendly way: Attractive and relatable media objects (images, videos) with biomedical data embedded are shared through a social media network.
- Straightforward deployment: Users only need to install a mobile application and perform some minor configuration.
- Affordable: The users are not asked to spend any money to use the system. Only a mobile phone with internet connection is required.
- High uptime availability: The system leverages online social networks as a backbone. Thus, the servers are almost always up.
- Improved security and privacy: This is due to the security envelope, based on a hybrid cryptosystem, therefore combining the convenience of public-key approaches with the efficiency of symmetric-key schemes. Social networks convey the information, but not even they are able to read the biomedical data travelling through their servers.
- Reduced added complexity: Users are required to manage some key-related aspects, but this is common practice for current users of smartphones and applications and it could be carried out easily and swiftly.
- Augmented integrability: This is provided by the internal support of medical interoperability standards.
Author Contributions
Funding
Conflicts of Interest
References
- Pew Research Center Mobile Fact Sheet. Available online: http://www.pewinternet.org/fact-sheet/mobile/ (accessed on 7 September 2020).
- World Health Organization (WHO) mHealth. New Horizons for Health through Mobile Technologies. Available online: http://www.who.int/goe/publications/goe_mhealth_web.pdf (accessed on 7 September 2020).
- Adibi, S. Mobile Health: A Technology Road Map; Springer Publishing Company, Inc.: New York, NY, USA, 2015; ISBN 978-3-319-12816-0. [Google Scholar]
- Silva, B.M.C.; Rodrigues, J.J.P.C.; de la Torre Díez, I.; López-Coronado, M.; Saleem, K. Mobile-health: A review of current state in 2015. J. Biomed. Inform. 2015, 56, 265–272. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hamdi, O.; Chalouf, M.A.; Ouattara, D.; Krief, F. eHealth: Survey on research projects, comparative study of telemonitoring architectures and main issues. J. Netw. Comput. Appl. 2014, 46, 100–112. [Google Scholar] [CrossRef]
- Awori, J.; Lee, J.M. A Maker Movement for Health: A New Paradigm for Health Innovation. JAMA Pediatr. 2017, 171, 107–108. [Google Scholar] [CrossRef] [PubMed]
- Lee, J.M.; Hirschfeld, E.; Wedding, J. A Patient-Designed Do-It-Yourself Mobile Technology System for Diabetes: Promise and Challenges for a New Era in Medicine. JAMA 2016, 315, 1447–1448. [Google Scholar] [CrossRef]
- Chen, C.; Haddad, D.; Selsky, J.; Hoffman, J.E.; Kravitz, R.L.; Estrin, D.E.; Sim, I. Making Sense of Mobile Health Data: An Open Architecture to Improve Individual- and Population-Level Health. J. Med. Internet. Res. 2012, 14. [Google Scholar] [CrossRef]
- Househ, M.; Borycki, E.; Kushniruk, A. Empowering patients through social media: The benefits and challenges. Health Inform. J. 2014, 20, 50–58. [Google Scholar] [CrossRef]
- Facebook Statistics. Available online: https://about.fb.com/company-info/ (accessed on 7 September 2020).
- Kaplan, A.M.; Haenlein, M. Users of the world, unite! The challenges and opportunities of Social Media. Bus. Horiz. 2010, 53, 59–68. [Google Scholar] [CrossRef]
- Househ, M. The use of social media in healthcare: Organizational, clinical, and patient perspectives. Stud. Health Technol. Inf. 2013, 183, 244–248. [Google Scholar]
- Rozenblum, R.; Bates, D.W. Patient-centred healthcare, social media and the internet: The perfect storm? BMJ Qual. Saf. 2013, 22, 183–186. [Google Scholar] [CrossRef] [Green Version]
- Grajales, F.J., III; Sheps, S.; Ho, K.; Novak-Lauscher, H.; Eysenbach, G. Social Media: A Review and Tutorial of Applications in Medicine and Health Care. J. Med. Internet Res. 2014, 16, e13. [Google Scholar] [CrossRef]
- Hors-Fraile, S.; Atique, S.; Mayer, M.A.; Denecke, K.; Merolli, M.; Househ, M. The Unintended Consequences of Social Media in Healthcare: New Problems and New Solutions. Yearb. Med. Inf. 2016, 47–52. [Google Scholar] [CrossRef] [Green Version]
- Grover, S.; Aujla, G.S. Twitter data based prediction model for influenza epidemic. In Proceedings of the 2015 2nd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 11–13 March 2015; pp. 873–879. [Google Scholar]
- Al-Bahrani, R.; Danilovich, M.K.; Agrawal, A.; Choudhary, A. Towards Informal Caregiver Identification in Social Media. In Proceedings of the 2016 IEEE International Conference on Healthcare Informatics (ICHI), Chicago, IL, USA, 4–7 October 2016; p. 414. [Google Scholar]
- Nair, L.R.; Shetty, S.D.; Shetty, S.D. Applying spark based machine learning model on streaming big data for health status prediction. Comput. Electr. Eng. 2017. [Google Scholar] [CrossRef]
- Triantafyllidis, A.K.; Koutkias, V.G.; Chouvarda, I.; Maglaveras, N. A Pervasive Health System Integrating Patient Monitoring, Status Logging, and Social Sharing. IEEE J. Biomed. Health Inform. 2013, 17, 30–37. [Google Scholar] [CrossRef] [PubMed]
- Trigo, J.D.; Eguzkiza, A.; Martínez-Espronceda, M.; Serrano, L. A cardiovascular patient follow-up system using Twitter and HL7. In Proceedings of the Computing in Cardiology (CinC), Zaragoza, Spain, 22–25 October 2013; pp. 33–36. [Google Scholar]
- Luxton, D.D.; Kayl, R.A.; Mishkind, M.C. mHealth Data Security: The Need for HIPAA-Compliant Standardization. Telemed. E Health 2012, 18, 284–288. [Google Scholar] [CrossRef]
- Cherdantseva, Y.; Hilton, J. A Reference Model of Information Assurance & Security. In Proceedings of the 2013 International Conference on Availability, Reliability and Security, Regensburg, Germany, 2–6 September 2013; pp. 546–555. [Google Scholar]
- Velsen, L.V.; Hermens, H.; d’Hollosy, W.O.N. A maturity model for interoperability in eHealth. In Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–17 September 2016; pp. 1–6. [Google Scholar]
- Turnitsa, C.D. Extending the Levels of Conceptual Interoperability Model. In Proceedings of the IEEE Summer Computer Simulation Conference (SCSC), New Jersey, NY, USA, 24–28 July 2005. [Google Scholar]
- Islam, S.M.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K. The Internet of Things for Health Care: A Comprehensive Survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Voskarides, S.; Pattichis, C.S.; Istepanian, R.S.H.; Kyriacou, E.; Pattichis, M.S.; Schizas, C.N. Mobile Health Systems: A Brief Overview. In Proceedings of the SPIE 4740, Digital Wireless Communications IV, Orlando, FL, USA, 1–5 April 2002; Volume 4740, pp. 124–132. [Google Scholar]
- Price, S.; Summers, R. Clinical knowledge management and m-health. In Proceedings of the Second Joint EMBS-BMES Conference: 24th Annual Engineering in Medicine and Biology Society Conference and the Annual Fall Meeting of the Biomedical Engineering Society, Houston, TX, USA, 23–26 October 2002; Volume 3, pp. 1865–1866. [Google Scholar]
- Martínez, I.; Escayola, J.; Martínez-Espronceda, M.; Muñoz, P.; Trigo, J.D.; Muñoz, A.; Led, S.; Serrano, L.; García, J. Seamless Integration of ISO/IEEE11073 Personal Health Devices and ISO/EN13606 Electronic Health Records into an End-to-End Interoperable Solution. Telemed. E Health 2010, 16, 993–1004. [Google Scholar] [CrossRef] [Green Version]
- Clarke, M.; de Folter, J.; Verma, V.; Gokalp, H. Interoperable End-to-End Remote Patient Monitoring Platform based on IEEE 11073 PHD and ZigBee Health Care Profile. IEEE Trans. Biomed. Eng. 2017. [Google Scholar] [CrossRef] [Green Version]
- Harvey, M.J.; Harvey, M.G. Privacy and security issues for mobile health platforms. J. Assn. Inf. Sci. Technol. 2014, 65, 1305–1318. [Google Scholar] [CrossRef]
- Arora, S.; Yttri, J.; Nilsen, W. Privacy and Security in Mobile Health (mHealth) Research. Alcohol Res. 2014, 36, 143–151. [Google Scholar]
- Atienza, A.A.; Zarcadoolas, C.; Vaughon, W.; Hughes, P.; Patel, V.; Chou, W.-Y.S.; Pritts, J. Consumer Attitudes and Perceptions on mHealth Privacy and Security: Findings from a Mixed-Methods Study. J. Health Commun. 2015, 20, 673–679. [Google Scholar] [CrossRef]
- Rubio, Ó.J.; Trigo, J.D.; Alesanco, Á.; Serrano, L.; García, J. Analysis of ISO/IEEE 11073 built-in security and its potential IHE-based extensibility. J. Biomed. Inf. 2016, 60, 270–285. [Google Scholar] [CrossRef] [PubMed]
- Rahimi, M.R.; Ren, J.; Liu, C.H.; Vasilakos, A.V.; Venkatasubramanian, N. Mobile Cloud Computing: A Survey, State of Art and Future Directions. Mob. Netw. Appl. 2014, 19, 133–143. [Google Scholar] [CrossRef]
- Hsieh, J.C.; Hsu, M.W. A cloud computing based 12-lead ECG telemedicine service. BMC Med. Inf. Decis. Mak. 2012, 12, 77. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ribeiro, L.S.; Viana-Ferreira, C.; Oliveira, J.L.; Costa, C. XDS-I outsourcing proxy: Ensuring confidentiality while preserving interoperability. IEEE J. Biomed. Health Inf. 2014, 18, 1404–1412. [Google Scholar] [CrossRef]
- Hanen, J.; Kechaou, Z.; Ayed, M.B. An enhanced healthcare system in mobile cloud computing environment. Vietnam. J. Comput. Sci. 2016, 3, 267–277. [Google Scholar] [CrossRef] [Green Version]
- Systematized Nomenclature of Medicine—Clinical Terms (SNOMED-CT). Available online: https://www.snomed.org/snomed-ct/ (accessed on 7 September 2020).
- Unified Medical Language System (UMLS). Available online: https://www.nlm.nih.gov/research/umls/ (accessed on 7 September 2020).
- Open Authorization (oAuth). Available online: https://oauth.net/ (accessed on 7 September 2020).
- Housley, R. Vigil Security CMS. Available online: https://tools.ietf.org/html/rfc5652 (accessed on 7 September 2020).
- Callas, J.; Donnerhacke, L.; Finney, H.; Shaw, D.; Thayer, R. openPGP. Available online: https://tools.ietf.org/html/rfc4880 (accessed on 7 September 2020).
- Parah, S.A.; Ahad, F.; Sheikh, J.A.; Bhat, G.M. Hiding clinical information in medical images: A new high capacity and reversible data hiding technique. J. Biomed. Inform. 2017, 66, 214–230. [Google Scholar] [CrossRef]
- Twitter’s GDPR Hub. Available online: https://gdpr.twitter.com/en.html (accessed on 7 September 2020).
- Twitter’s GDPR: FAQ. Available online: https://gdpr.twitter.com/en/faq.html (accessed on 7 September 2020).
- Logical Observation Identifiers Names and Codes (LOINC). Available online: https://loinc.org/ (accessed on 7 September 2020).
- Unified Code for Units of Measure (UCUM). Available online: http://unitsofmeasure.org/trac (accessed on 7 September 2020).
- Josefsson, S. Base64. Available online: https://tools.ietf.org/html/rfc4648 (accessed on 7 September 2020).
- GNU Social. Available online: https://www.gnu.org/software/social/ (accessed on 7 September 2020).
- Mastodon.social—Mastodon. Available online: https://mastodon.social/about (accessed on 7 September 2020).
- Diaspora*. Available online: https://diasporafoundation.org/ (accessed on 7 September 2020).
- Ali, S.; Islam, N.; Rauf, A.; Din, I.U.; Guizani, M.; Rodrigues, J.J.P.C. Privacy and Security Issues in Online Social Networks. Future Internet 2018, 10, 114. [Google Scholar] [CrossRef] [Green Version]
- Twitter Help Center Safety and Security. Available online: https://help.twitter.com/en/safety-and-security (accessed on 17 November 2020).
- Reddy, S.; Allan, S.; Coghlan, S.; Cooper, P. A governance model for the application of AI in health care. J. Am. Med. Inform. Assoc. 2020, 27, 491–497. [Google Scholar] [CrossRef]
- O’Brien, N. Upcoming Changes to PNG Image Support. Available online: https://twittercommunity.com/t/upcoming-changes-to-png-image-support/118695 (accessed on 7 September 2020).
- NEMA DICOM—JPEG 2000 Image Compression. Available online: http://dicom.nema.org/medical/dicom/2016c/output/chtml/part05/sect_8.2.4.html (accessed on 7 September 2020).
- Helin, H.; Tolonen, T.; Ylinen, O.; Tolonen, P.; Näpänkangas, J.; Isola, J. Optimized JPEG 2000 Compression for Efficient Storage of Histopathological Whole-Slide Images. J. Pathol. Inf. 2018, 9. [Google Scholar] [CrossRef]
- Halamka, J.D. Information Lifecycle Management at Beth Israel Deaconess Medical Center. Available online: http://mycourses.med.harvard.edu/ec_res/nt/DD5E7835-72FA-4CFD-9CF8-B0D31113E652/nlm.pdf (accessed on 7 September 2020).
- Dai, W. Speed Comparison of Popular Crypto Algorithms. Available online: https://www.cryptopp.com/benchmarks.html (accessed on 7 September 2020).
- Muła, W.; Lemire, D. Faster Base64 Encoding and Decoding Using AVX2 Instructions. ACM Trans. Web 2018, 12, 1–26. [Google Scholar] [CrossRef] [Green Version]
- Deutsch, L.P. DEFLATE. Available online: https://tools.ietf.org/html/rfc1951 (accessed on 7 September 2020).
- Shevek Parallel GZIP. Available online: https://github.com/shevek/parallelgzip (accessed on 7 September 2020).





| Acronym | Meaning |
|---|---|
| AES | Advanced Encryption Standard |
| API | Application Programming Interface |
| CA | Certification Authority |
| CIA | Confidentiality, Integrity and Availability |
| CDSS | Clinical Decision Support Systems |
| CMS | Cryptographic Message Syntax |
| DICOM | Digital Imaging and Communication in Medicine |
| ECG | ElectroCardioGram |
| EHR | Electronic Health Record |
| GDPR | General Data Protection Regulation |
| GZIP | GNU ZIP |
| HIPAA | Health Insurance Portability and Accountability Act |
| HIS | Health Information System |
| HL7 | Health Level 7 |
| HS | Host System |
| HTTPS | Hypertext Transfer Protocol Secure |
| IAS | Information Assurance and Security |
| IEEE | Institute of Electrical and Electronics Engineers |
| IETF | Internet Engineering Task Force |
| IHE | Integrating the Healthcare Enterprise |
| ISO | International Organization for Standardization |
| JPEG | Joint Photographic Experts Group |
| LOINC | Logical Observation Identifiers Names and Codes |
| mH3S | Standardized, secure/private, social-media-based mobile health architecture |
| OAuth | Open Authorization |
| openPGP | open Pretty Good Privacy |
| ORU | Observation Result Unsolicited |
| PHD | Personal Health Device |
| PHR | Personal Health Record |
| PKI | Public Key Infrastructure |
| PNG | Portable Network Graphics |
| QR | Quick Response |
| RGBA/ARGB | Red Green Blue + Alpha |
| RSA | Rivest, Shamir and Adleman |
| S/MIME | Secure/Multipurpose Internet Mail Extensions |
| SCP-ECG | Standard Communications Protocol for computer assisted ElectroCardioGraphy |
| SNOMED-CT | Systematized Nomenclature of Medicine—Clinical Terms |
| TLS | Transport Layer Security |
| TPM | Trusted Platform Modules |
| UCUM | Unified Code for Units of Measure |
| UMLS | Unified Medical Language System |
| Row | Scenario | Small-Scale | Boundary | ||
|---|---|---|---|---|---|
| 01 | Plaintext (biomedical) data (bytes) | 439 | 607,168 | ||
| 02 | RSA encryption (ms) | 6.370 | |||
| 03 | AES set-up and encryption (ms) | 0.004 | 5.309 | ||
| 04 | Radix-64 encoding (ms) | 0.001 | 0.664 | ||
| 05 | Subtotal 1: encryption and encoding (ms) | 6.375 | 12.343 | ||
| 06 | Embedding Algorithm Version | Shifted | Shifted | Shifted | Not shifted |
| 07 | Zoomed (upper-right zone) image transparency overview |  |  |  |  |
| 08 | Image dimension (width × height in pixels) | 225 × 225 | 900 × 900 | ||
| 09 | Bytes embedded (bytes) | 1035 | 900 × 900 = 810,000 | ||
| 10 | Embedding set up (ms) | 3.6 ± 0.5 | 20.9 ± 1.2 | 24.3 ± 3.2 | 22.3 ± 1.8 |
| 11 | Embedding (ms) | 0.1 ± 0.3 | 3.9 ± 0.9 | 5.6 ± 0.5 | 5.3 ± 0.5 |
| 12 | Embedding subtotal (ms) | 3.7 ± 0.5 | 24.8 ± 1.9 | 29.9 ± 3.3 | 27.6 ± 1.1 |
| 13 | PNG compression (ms) | 38.1 ± 0.6 | 688.4 ± 9.1 | 703.5 ± 4.2 | 548.5 ± 3.8 |
| 14 | % PNG compression (100 * row 13/row 16) | 79.1 | 95.7 | 94.3 | 93.2 |
| 15 | Subtotal 2: embedding and compression (ms) | 41.8 ± 0.9 | 713.2 ± 9.6 | 733.4 ± 5.2 | 576.1 ± 4.1 |
| 16 | TOTAL TIME: subtotal 1 + subtotal 2 (ms) | 48.2 ± 0.9 | 719.6 ± 9.6 | 745.7 ± 5.2 | 588.4 ± 4.1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Trigo, J.D.; Rubio, Ó.J.; Martínez-Espronceda, M.; Alesanco, Á.; García, J.; Serrano-Arriezu, L. Building Standardized and Secure Mobile Health Services Based on Social Media. Electronics 2020, 9, 2208. https://doi.org/10.3390/electronics9122208
Trigo JD, Rubio ÓJ, Martínez-Espronceda M, Alesanco Á, García J, Serrano-Arriezu L. Building Standardized and Secure Mobile Health Services Based on Social Media. Electronics. 2020; 9(12):2208. https://doi.org/10.3390/electronics9122208
Chicago/Turabian StyleTrigo, Jesús D., Óscar J. Rubio, Miguel Martínez-Espronceda, Álvaro Alesanco, José García, and Luis Serrano-Arriezu. 2020. "Building Standardized and Secure Mobile Health Services Based on Social Media" Electronics 9, no. 12: 2208. https://doi.org/10.3390/electronics9122208
APA StyleTrigo, J. D., Rubio, Ó. J., Martínez-Espronceda, M., Alesanco, Á., García, J., & Serrano-Arriezu, L. (2020). Building Standardized and Secure Mobile Health Services Based on Social Media. Electronics, 9(12), 2208. https://doi.org/10.3390/electronics9122208








