Efficient Opportunistic Routing Protocol for Sensor Network in Emergency Applications
Abstract
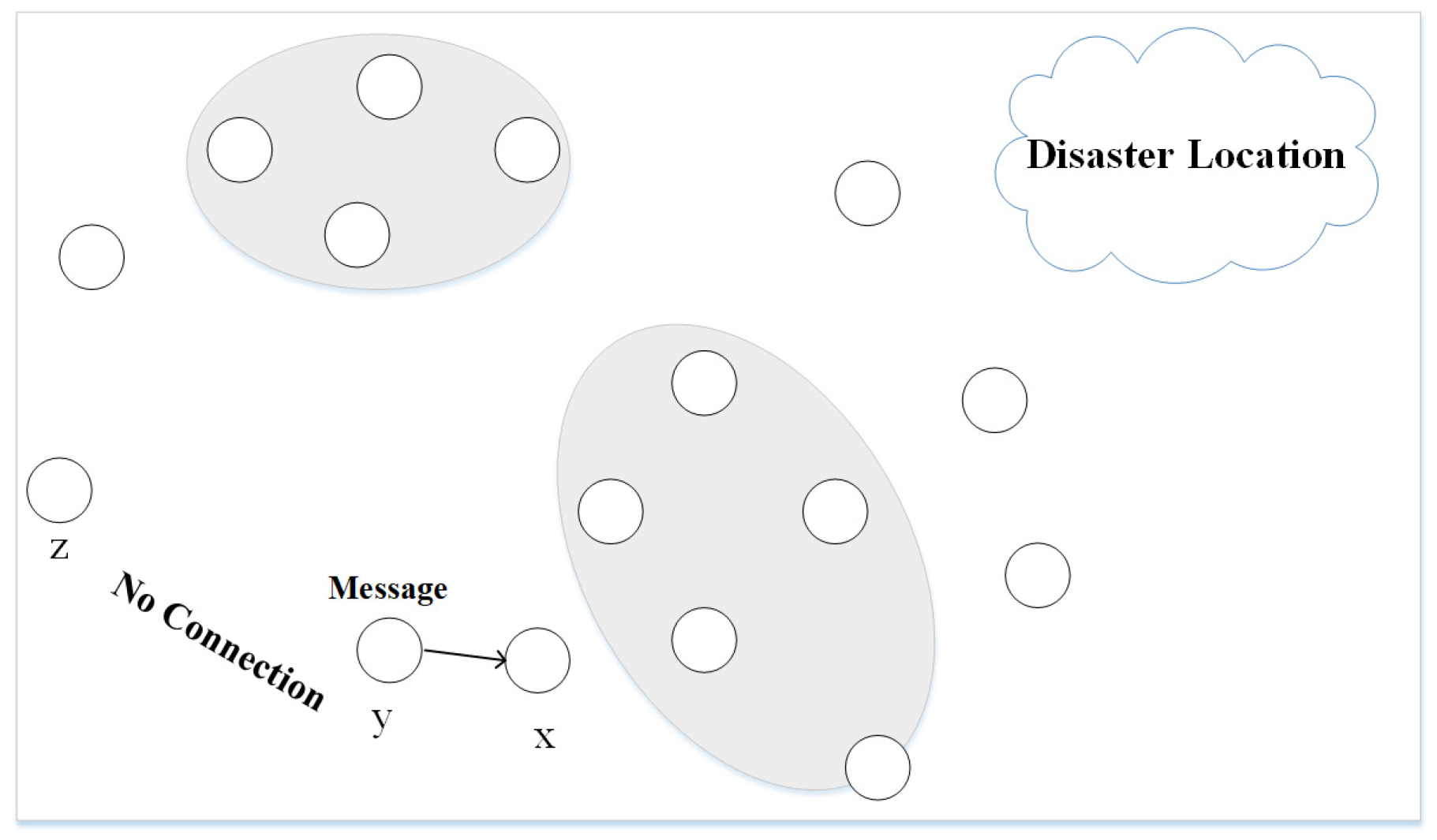
:1. Introduction
- This paper integrates edge computing with opportunistic networking for disaster recovery;
- The sensors in the network process and aggregate data locally to reduce the amount of data transmitted;
- The sensors create density-based clusters where sensors with the most neighboring nodes become cluster heads. This approach reduces the number of data collectors and transmitters and distributes energy consumption equally over sensor nodes;
- The nodes, which are not part of any cluster (e.g., isolated nodes) opportunistically forward data to the forwarder nodes. These nodes, while moving, join to the cluster closest to them;
- If any node moves out of a cluster due to mobility, the cluster restoration process starts based on the node’s property, called the minimum period of connectivity (MPC). This property ensures an energy efficient cluster restoration process compared to the cluster restoration process of existing protocols, which involve all nodes in cluster restoration at the end of each round.
2. Related Work
3. Proposed Opportunistic Routing Protocol
3.1. Terminologies
3.2. Form Density-Based Clusters
| Algorithm 1 (cluster formation) |
| Input: node x, MPCg, minimum number of nodes in a cluster (minNode). Output: a cluster with a cluster head CH. |
| begin 1: N← GetNeighbors(x) //find number of neighbors of node x 2: weight ←GetWeight(x) //find weight of node x and all other nodes using Equations (2)–(4) 3: If |N| minNode 4: Select x as a core point //i.e., a good candidate to be a CH 5: if weight(x) ≤ weight (y), 6: select x as CH of cluster C 7: minNode = |N| // minNode is set to the number of neighbors of node x 8: end if 9: else 10: select x as border point // if weight of x is greater than all its neighboring nodes 11: end if 12: for each y∈N do 13: if y is not CH nor member of any cluster 14: if (MPCx,y ≥ MPCg) 15: C←{y}; include y in the cluster C // y is in cluster C if its MPC greater than global MPC 16: else 17: select node y as a noise to C 18: end if 19: end if 20: return CH 21: Repeat steps 1–20 until all clusters are formed 22: end |
3.3. Routing
3.4. Cluster Restoration
| Algorithm 2 (Cluster Restoration) |
| Input: y is a border point from a neighbor cluster to C, C is a cluster to be connected to y, MPCg is the minimal period of connectivity. |
| Begin 1: Find x such as MPC y, x = Max, where x is a noise 2: Relay x = FindBestCandidate(y, x), where x noise & MPCy,x is a max 3: if x is Member(C) then //Scenario 1 4: y.increaseRc(getMPC(x, y), MPCg) // increase Rc of y to maintain MPC x,y, same as MPCg 5: else //Scenario 2 6: temp = min(getMPC(x,y), getMPC(x,C)) 7: y.increaseRc(temp, MPCg) 8: end if 9: end |
4. Performance Evaluation
4.1. Computation Efficiency
4.2. Energy Efficiency
5. Simulation Model, Setup and Results
5.1. Energy Model
5.2. Network and Mobility Model
5.3. Performance Metrics
- Energy consumption is the total energy consumed by the sensor nodes in the network over a number of rounds.
- Throughput is the amount of data transmitted by a node per second. We calculate throughput in Gigabytes/second in this paper.
- Packet delivery ratio is the ratio of the total number of packets delivered to the total number of packets transmitted.
- Packet loss ratio is the ratio of the total number of packets lost to the total number of packets transmitted.
5.4. Simulation Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Jang, H.-C.; Lien, Y.-N.; Tsai, T.-C. Rescue information system for earthquake disasters based on MANET emergency communication platform. In Proceedings of the IWCMC’09: Proceedings of the 2009 International Conference on Wireless Communications and Mobile, Leipzig, Germany, 21–24 June 2009. [Google Scholar]
- Ramesh, M.V.; Jacob, A.; Devidas, A.R. Enhanced Emergency Communication using Mobile sensing and MANET. In Proceedings of the ICACCI’12 Proceedings of the International Conference on Advances in Computing, Communications and Informatics, Chennai, India, 3–5 August 2012. [Google Scholar]
- Zheng, C.; Chen, L.; Sicker, D. Hybrid cellular-MANETs: An energy-aware routing design. In Proceedings of the 2014 11th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Obergurgl, Austria, 2–4 April 2014; pp. 9–16. [Google Scholar]
- Verma, H.; Chauhan, N. MANET based emergency communication system for natural disasters. In Proceedings of the 2015 International Conference on Computing, Communication & Automation (ICCCA), Noida, India, 15–16 May 2015; pp. 480–485. [Google Scholar]
- Lu, Z.; Sun, X.; Porta, T.L. Cooperative data offloading in opportunistic mobile networks. In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; p. 19. [Google Scholar]
- Lu, Z.; Cao, G.; Porta, T.L. Networking smartphones for disaster recovery. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communications (PerCom), Sydney, Australia, 14–19 March 2016; pp. 1–9. [Google Scholar]
- Ester, M.; Kriegel, H.; Sander, J.; Xu, X. A density-based algorithm for discovering clusters in large spatial databases with noise. In Proceedings of the 2nd International Conference on Knowledge Discovery and Data Mining, Shanghai, China, 26–28 April 2019; Volume 1996, pp. 226–231. [Google Scholar]
- Sanchez-Iborra, R.; Cano, M.-D. JOKER: A novel opportunistic routing protocol. IEEE J. Sel. Areas Commun. 2016, 34, 1690–1703. [Google Scholar] [CrossRef]
- Higashino, T.; Yamaguchi, H.; Hiromori, A.; Uchiyama, A.; Yasumoto, K. Edge computing and IoT based research for building safe smart cities resistant to disasters. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 1729–1737. [Google Scholar]
- Casadei, R.; Fortino, G.; Pianini, D.; Russo, W.; Savaglio, C.; Viroli, M. A development approach for collective opportunistic Edge-of-Things services. Inf. Sci. 2019, 498, 154–169. [Google Scholar] [CrossRef]
- Said, J.E.; Karim, L.; Almhana, J.; Anpalagan, A. Heterogeneous mobility and connectivity-based clustering protocol for wireless sensor networks. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 257–262. [Google Scholar]
- Jadhav, P.; Satao, R. A Survey on Opportunistic Routing Protocols for Wireless Sensor Networks. Procedia Comput. Sci. 2016, 79, 603–609. [Google Scholar] [CrossRef] [Green Version]
- Kang, M.W.; Chung, Y.W. An energy-efficient opportunistic routing protocol in delay tolerant networks. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016; pp. 655–659. [Google Scholar]
- Santos, R.M.; Orozco, J.; Ochoa, S.F.; Meseguer, R.; Mosse, D. Providing Real-Time Message Delivery on Opportunistic Networks. IEEE Access. 2018, 6, 40696–40712. [Google Scholar] [CrossRef]
- Kang, M.W.; Kim, Y.; Chung, Y.W. An opportunistic forwarding scheme for ICN in disaster situations. In Proceedings of the 2017 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 18–20 October 2017; pp. 948–950. [Google Scholar] [CrossRef]
- Manjeshwar, A.; Agrawal, D.P. TEEN: A Routing Protocol for Enhanced Efficiency in Wireless Sensor Networks. In Proceedings of the 15th International Parallel and Distributed Processing Symposium, IPDPS 2001, San Francisco, CA, USA, 23–27 April 2001; Volume 22, p. 189. [Google Scholar] [CrossRef]
- Yassein, M.B.; Khamayseh, Y.; Mardini, W. Improvement on LEACH protocol of wireless sensor network (VLEACH). Int. J. Digit. Content Technol. Appl. 2009, 132–136. [Google Scholar] [CrossRef] [Green Version]
- Heinzelman, W.; Chandrakasan, A.; Balakrishnan, H. Energy-Efficient Communication Protocol for Wireless Microsensor Networks. In Proceedings of the 33rd Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2000. [Google Scholar]
- Senturk, I.F.; Akkaya, K. Connectivity restoration in disjoint Wireless Sensor Networks using centrality measures. In Proceedings of the 39th Annual IEEE Conference on Local Computer Networks Workshops, Edmonton, AB, Canada, 8–11 September 2014; pp. 616–622. [Google Scholar]
- Han, Y.; Wu, H.; Yang, Z.; Li, D. A New Data Transmission Strategy in Mobile D2D Networks—Deterministic, Greedy, or Planned Opportunistic Routing? IEEE Trans. Veh. Technol. 2017, 66, 594–609. [Google Scholar] [CrossRef]
- Hawbani, A.; Wang, X.; Sharabi, Y.; Ghannami, A.; Kuhlani, H.; Karmoshi, S. LORA: Load-Balanced Opportunistic Routing for Asynchronous Duty-Cycled WSN. IEEE Trans. Mob. Comput. 2019, 18, 1601–1615. [Google Scholar] [CrossRef]
- Saha, B.K.; Misra, S.; Pal, S. SeeR: Simulated Annealing-Based Routing in Opportunistic Mobile Networks. IEEE Trans. Mob. Comput. 2017, 16, 2876–2888. [Google Scholar] [CrossRef]
- So, J.; Byun, H. Load-Balanced Opportunistic Routing for Duty-Cycled Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2017, 16, 1940–1955. [Google Scholar] [CrossRef]
- Xing, G.; Lu, C.; Pless, R.; Huang, Q. Impact of sensing coverage on greedy geographic routing algorithms. IEEE Trans. Parallel Distrib. Syst. 2006, 17, 348–360. [Google Scholar] [CrossRef] [Green Version]
- Aschenbruck, N.; Ernst, R.; Gerhards-Padilla, E.; Schwamborn, M. BonnMotion: A mobility scenario generation and analysis tool. In Proceedings of the 3rd International ICST Conference on Simulation Tools and Techniques (SIMUTools’10); ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2010; Article 51; pp. 1–10. [Google Scholar] [CrossRef] [Green Version]
- Libelium Waspmote. Available online: http://www.libelium.com/waspmote (accessed on 13 January 2020).
- Ghate, V.V.; Vijayakumar, V. Machine Learning for Data Aggregation in WSN: A Survey. Int. J. Pure Appl. Math. 2018, 118, 1–12. [Google Scholar]
- Savaglio, C.; Pace, P.; Aloi, G.; Liotta, A.; Fortino, G. Lightweight reinforcement learning for energy efficient communications in wireless sensor networks. IEEE Access 2019, 7, 29355–29364. [Google Scholar] [CrossRef]










| Parameter | Value |
|---|---|
| Simulation network area | 2000 × 2000 m2 |
| Number of node | 100 |
| Communication range of a node | 200 m |
| Transport protocol | UDP |
| MAC protocol | IEEE 802.11 |
| Mobility Model | Random |
| Mobility Speed | 5 m/s |
| Pause time | ½ s |
| Duration of a round | 200 s |
| Traffic type | Constant Bit Rate (CBR) |
| Data transmission rate | 250 Kbit/s |
| Data packet size | 128 Bytes = 1 Kbit |
| Features | LEACH | TEEN | LORA | ODCR |
|---|---|---|---|---|
| Cluster formation is done at the end of each round | √ | √ | X | X |
| All nodes in the network involve in cluster restoration or reform | √ | √ | X | X |
| Nodes that connect or communication other nodes for a longer period time are good candidate to be selected as cluster head | X | X | √ | X |
| Consider mobility of nodes | X | X | √ | √ |
| Construct candidate zone at each with a number of forwarder nodes | X | X | √ | X |
| Requires reselecting forwarder nodes very often due to mobility | X | X | √ | X |
| Use opportunistic forwarding as a cluster member or isolated nodes | X | X | X | √ |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-kahtani, M.S.; Karim, L.; Khan, N. Efficient Opportunistic Routing Protocol for Sensor Network in Emergency Applications. Electronics 2020, 9, 455. https://doi.org/10.3390/electronics9030455
Al-kahtani MS, Karim L, Khan N. Efficient Opportunistic Routing Protocol for Sensor Network in Emergency Applications. Electronics. 2020; 9(3):455. https://doi.org/10.3390/electronics9030455
Chicago/Turabian StyleAl-kahtani, Mohammed S., Lutful Karim, and Nargis Khan. 2020. "Efficient Opportunistic Routing Protocol for Sensor Network in Emergency Applications" Electronics 9, no. 3: 455. https://doi.org/10.3390/electronics9030455





