Neighbor Aware Protocols for IoT Devices in Smart Cities—Overview, Challenges and Solutions
Abstract
:1. Introduction
2. Challenges Faced in Smart Cities
2.1. Information Sensing in a City and from Its Inhabitants
2.2. Information Management
2.3. Privacy and Security
2.4. Human Interaction
3. Neighbor Aware/Assistance Challenges in Smart Cities
- (1)
- Neighbor Recognition: Neighbor Recognition is one of the most important challenges. A node needs to correctly recognize the presence of the neighbor nodes that lie within communication range. Moreover, the knowledge that the neighbor nodes and no longer within communication range, is also required to conserve resources. The discovery time for neighbor nodes needs also to be bounded, to enable the node to fully utilize the connection time for the communication tasks.
- (2)
- Mobility Models: The recognition of the mobility pattern of a node is a broad area of research. The current mobility models aim to capture the temporal and spatial movement characteristics. Additional metrics may be useful to predict the accuracy of the mobility models such as, popularity (the number of visits to a certain location), ranking locations, neighbor memberships, friendships, and location tagging of places (e.g., bus stops, schools, hotels, railway stations). By utilizing the geographical locations, these metrics can be used as features defining the mobility patterns.
- (3)
- Knowledge Acquisition: The final challenge is the knowledge of the neighboring nodes future mobility (i.e., when will the neighbor node return in the future?). This has the capacity of reducing energy consumption. The information acquisition allows the node to understand, and learn about the neighbor nodes’ recurrence. This creates the possibility of predicting a future nodes arrival, and helps in scheduling, both the discovery and communication, based on the mobility patterns (i.e., future location, arrival time, and link duration). The IoT devices and usually battery operated, with limited storage. These fundamental limitations of the IoT devices, creates difficulties for planning a network with an extended lifetime. Thus, the need to optimally utilize the resources of IoT devices in an energy-efficient manner is extremely important. NA techniques and better in employing these resources, maintaining the requirements of the application of a particular node, while reducing the energy consumption.
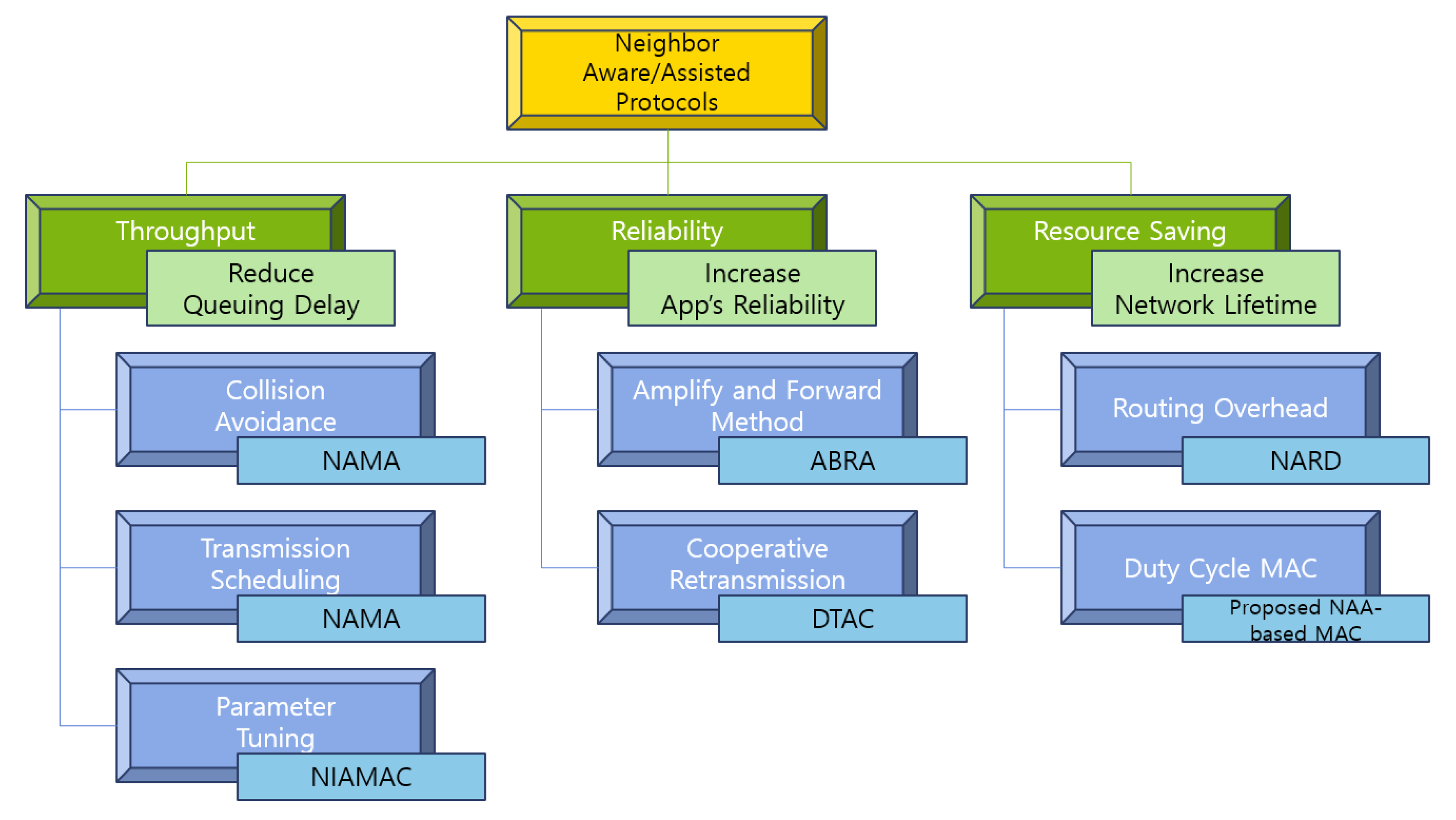
4. Neighbor Aware/Assistance Solutions
4.1. Throughput
- (1)
- Collision Avoidance and Transmission Scheduling: In a Smart City network, due to the high density of IoT devices, contention frequently occurs when too many IoT devices attempt to simultaneously transmit packets. During the contention period, packets cannot be transmitted, and this needs to be resolved quickly. The use of random backoff based collision avoidance mechanisms is not appropriate, because many nodes could select the same random backoff value. Therefore, each IoT devices should be aware of the transmission schedule of neighboring nodes, and be able to determine its own transmission schedule.The Neighbor Aware Multiple Access (NAMA) is an example of an NA based Collision avoidance solution [12]. In NAMA, all IoT devices initially transmit packets through a random backoff mechanism. During the contention period, devices that have not yet won the contention, count the number of ACK(acknowledgement) messages transmitted from different neighbors. When this node wins contention and transmits its data packet successfully, the number of ACKs is determined and used as its transmission slot sequence. In other words, the nodes will be aware of the neighbors’ transmission schedule sequence, using overheard ACK messages, and are then able to determine their own transmission schedule [12].
- (2)
- Network Parameter Tuning: Although the network parameters may have a significant impact on performance, the optimal values of the network parameters differ, according to the network environments. Hence, if the NA based parameter tuning methods and defined, an IoT device can determine the network parameter value that maximizes the network performance, for example, the throughput. In particular, IEEE 802.11, which is a key technology of Smart Cities, defines the distributed coordination function (DCF) that performs the collision avoidance through random backoff [13]. In order to minimize any unnecessary transmission retries, each device selects a different random backoff value. Since the random off-value is selected between CWinit (initial CW) and CWmax (maximum CW), where CW is the contention window, it is important to define the optimal CW-related parameters.Therefore, NA solution based network parameter tuning protocols, such as the Neighbor and Interference Aware MAC (NIAMAC), which determines the optimal CW-related parameters are needed. In these protocols, IoT devices determine the CWinit value, according to the number of active neighbors. Moreover, the network parameters that can increase the variation of CWmax, and determined, since the distance between a sender device and its neighbor is closer. These protocols can improve throughput by reducing packet collisions and unnecessary transmission retries [14].
4.2. Reliability
- (1)
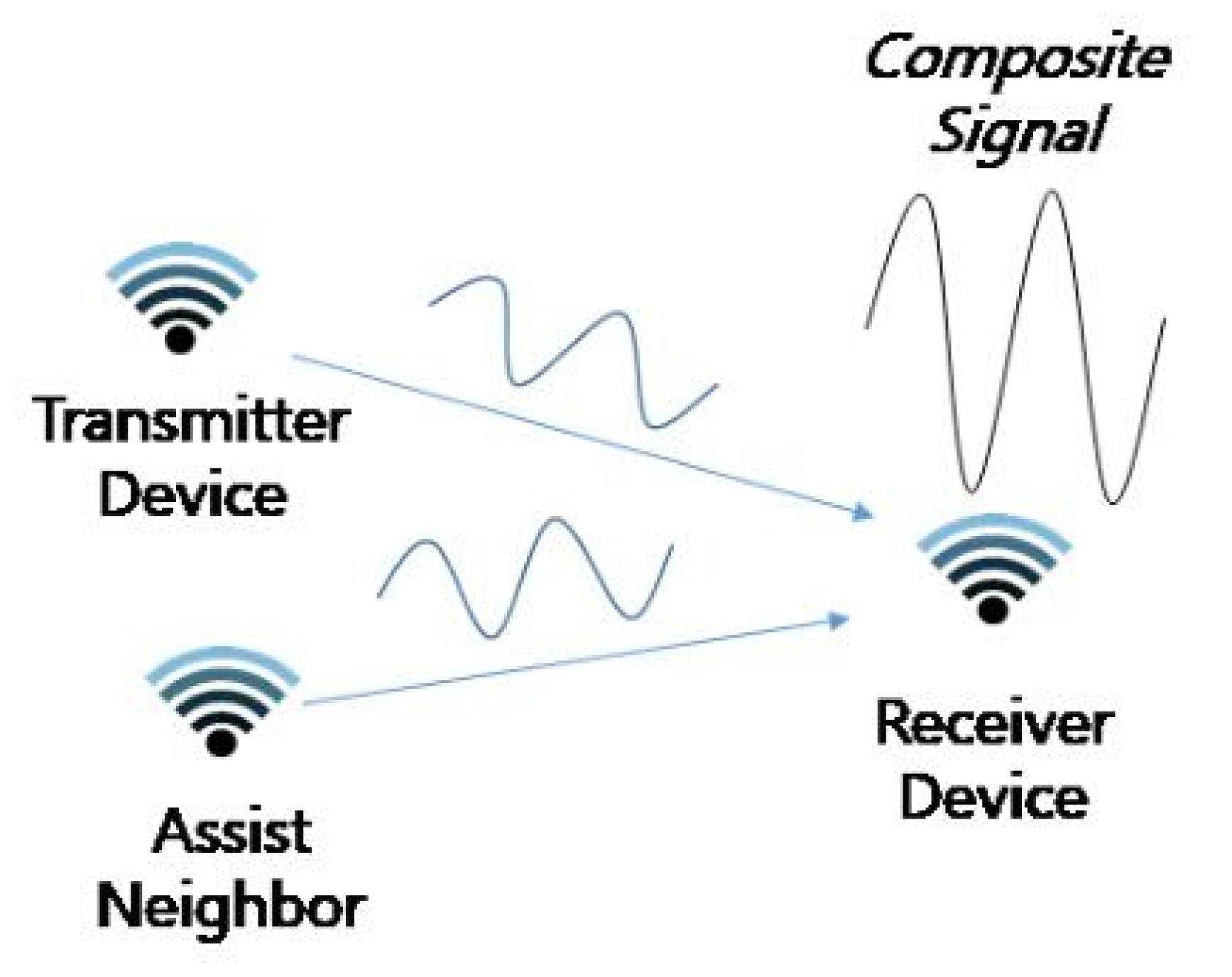
- Amplify and Forward Method: In common networks, both the link quality and transmission range and proportional to the transmit power of the transmitter [5]. Therefore, as the transmission power is increased, the receiver can receive the transmitted signal from the transmitter without error, resulting in improved reliability. However, IoT devices in Smart cities have limited transmission power, due to characteristics of their communication interfaces.The Amplify and Forward Method is a NA-based transmission method that utilizes the neighbors to increase the signal strength. In this method, the sender selects a neighbor and sends its packet to the selected neighbor. Then, the sender and the selected neighbor transmit the same signal with a time difference, which results in amplification of the signal at the receiver. This signal amplification phenomenon not only improves the transmission range, but also improves the transmission reliability [15]. As shown in Figure 2, a receiver device receives the attenuated signal from the transmitter device. Because of the signal attenuation, the receiver may not be able to decode the original signal. However, if the assist neighbor transmits the same signal, the signal could be decoded at the receiver device by the signal amplify phenomenon.
- (2)
- Cooperative Retransmission: Cooperative retransmission is an NA based transmission protocol. It improves reliability by transmitting a packet, transmitted from a node with low reliability, to a neighbor device, after receiving it. In this protocol, even if the receiver does not receive the packet correctly from the sender, there is the additional chance that it will still receive the packet transmitted from the neighbors [16].
Resource Saving
- (1)
- Reducing Routing Overhead: Neighbor-Assisted Route Discovery (NARD) is a route discovery protocol. It reduces routing overhead for a mobile Ad-hoc network (MANET) architecture, which is defined by IETF(Internet Engineering Task Force). In the common routing protocols proposed for MANET, the source node floods its routing message using a blind-flooding technique, which enables it to find a route toward the corresponding destination node [13].To reduce routing overhead using the NARD flooding technique, all nodes collect their neighbor’s information by the overhearing of packets (in the form of a data packet or hello message) during the neighbor discovery phase. After this phase, the source node, which requires a route toward the corresponding destination, floods a RREQ (Route REQuest) message, limited by the hop count n, and hops away from the source node. The limited hop count n, is increased when the route discovery fails. If the RREQ message is received at, not only the destination node, but also the nodes which have a route towards the destination nodes (e.g., neighbors of the destination node), these nodes reply with RREP (Route Reply) messages towards the source node. After receiving the RREP message, the source node can transmit its data packet [12].Furthermore, whenever a new RREQ message towards the same destination node is received at the source node, the source node can reply with a RREP message, since it has a route towards the destination. Therefore, routing overhead can be reduced, as many routes and found due to the neighbor assistance in the route discovery.
- (2)
- Duty-cycle MAC protocol: Among the various energy efficient protocols, a duty-cycle MAC protocol is one of the most promising solutions in increasing the network lifetime. We introduce an NA solution based on the duty-cycle MAC protocol in Section 4.
4.3. Proposed NA Based Duty-Cycle MAC Protocol
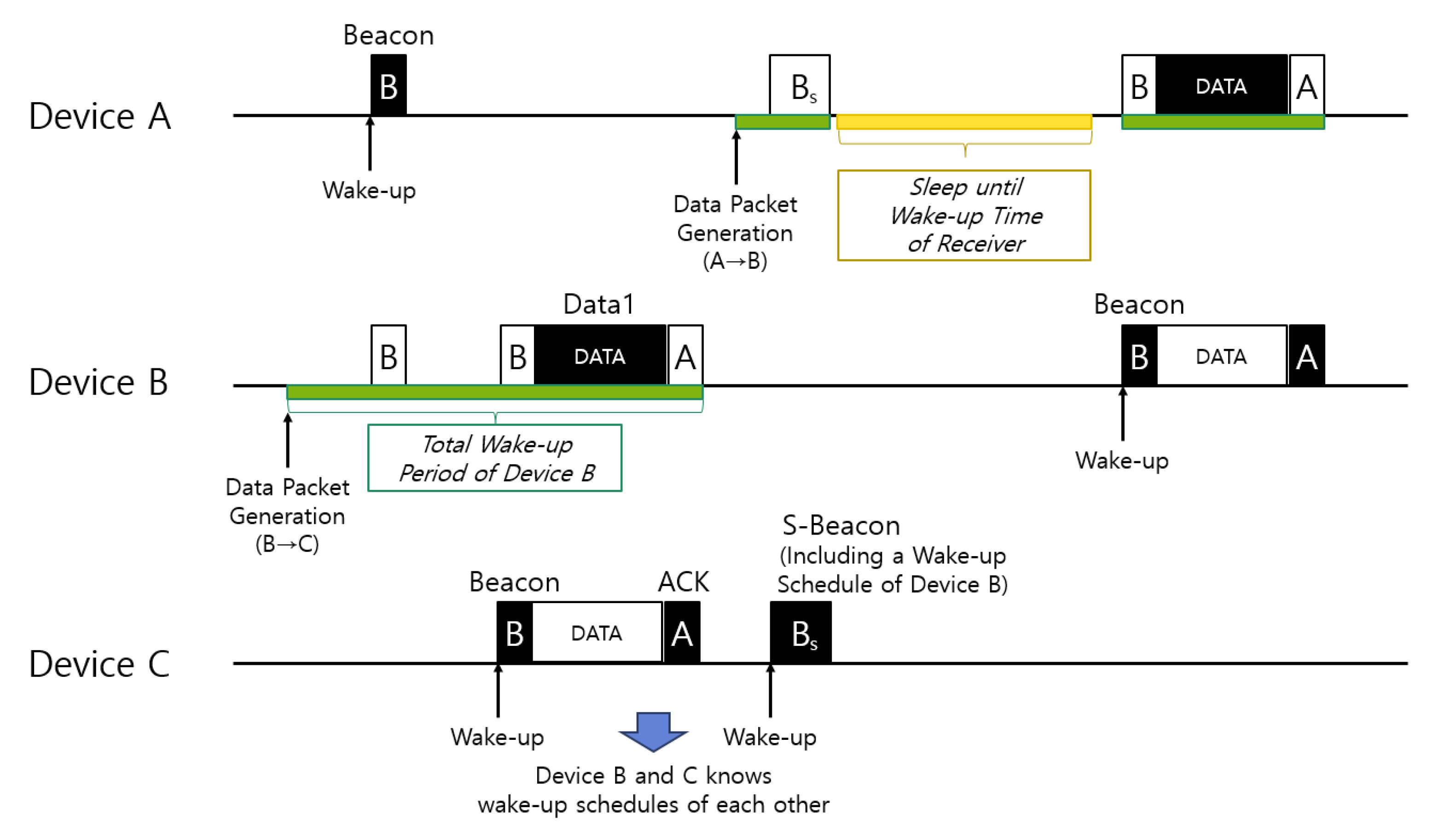
4.3.1. Duty-Cycle MAC Protocol and Power Saving
4.3.2. Neighbor Assisted Power Saving Method
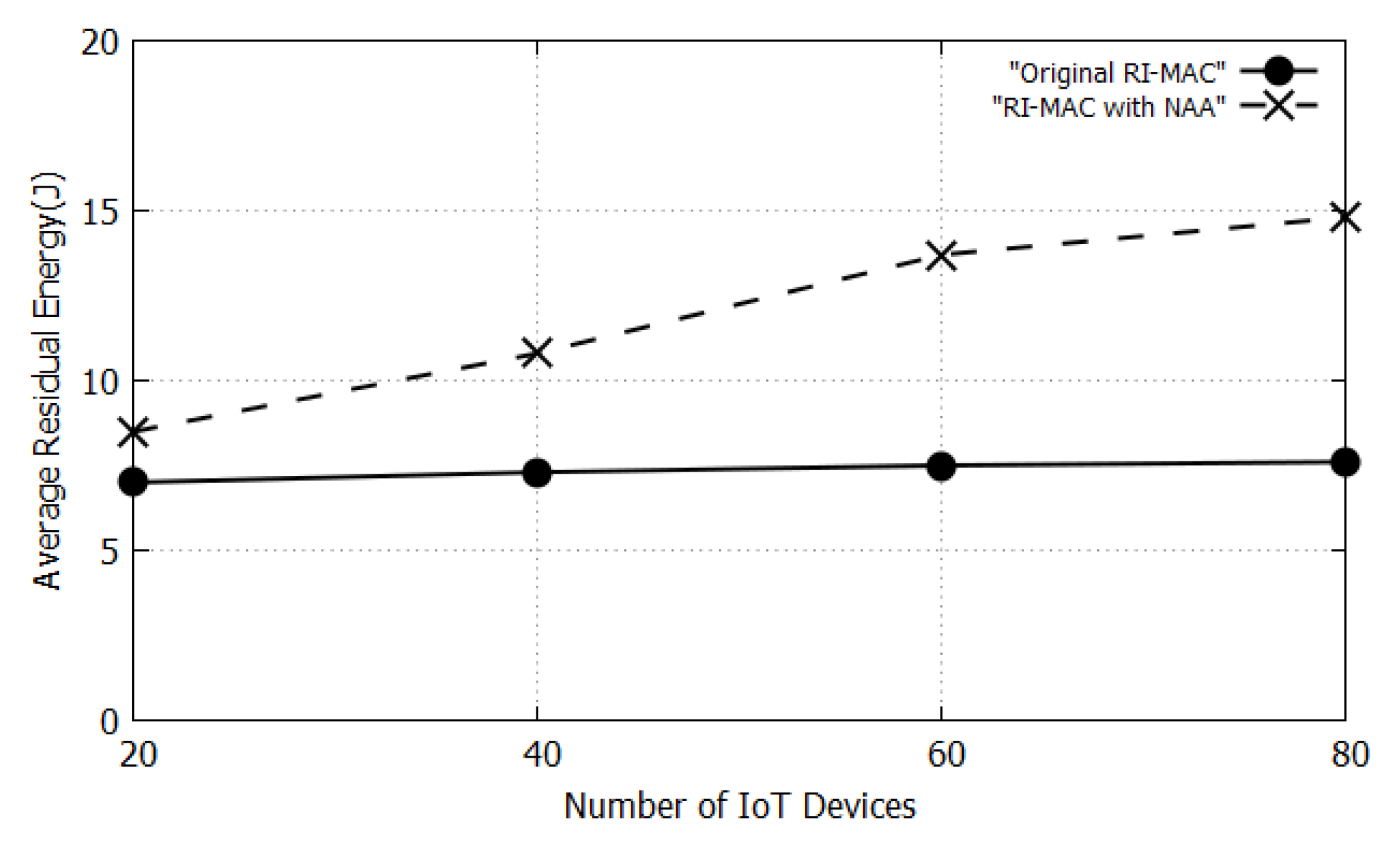
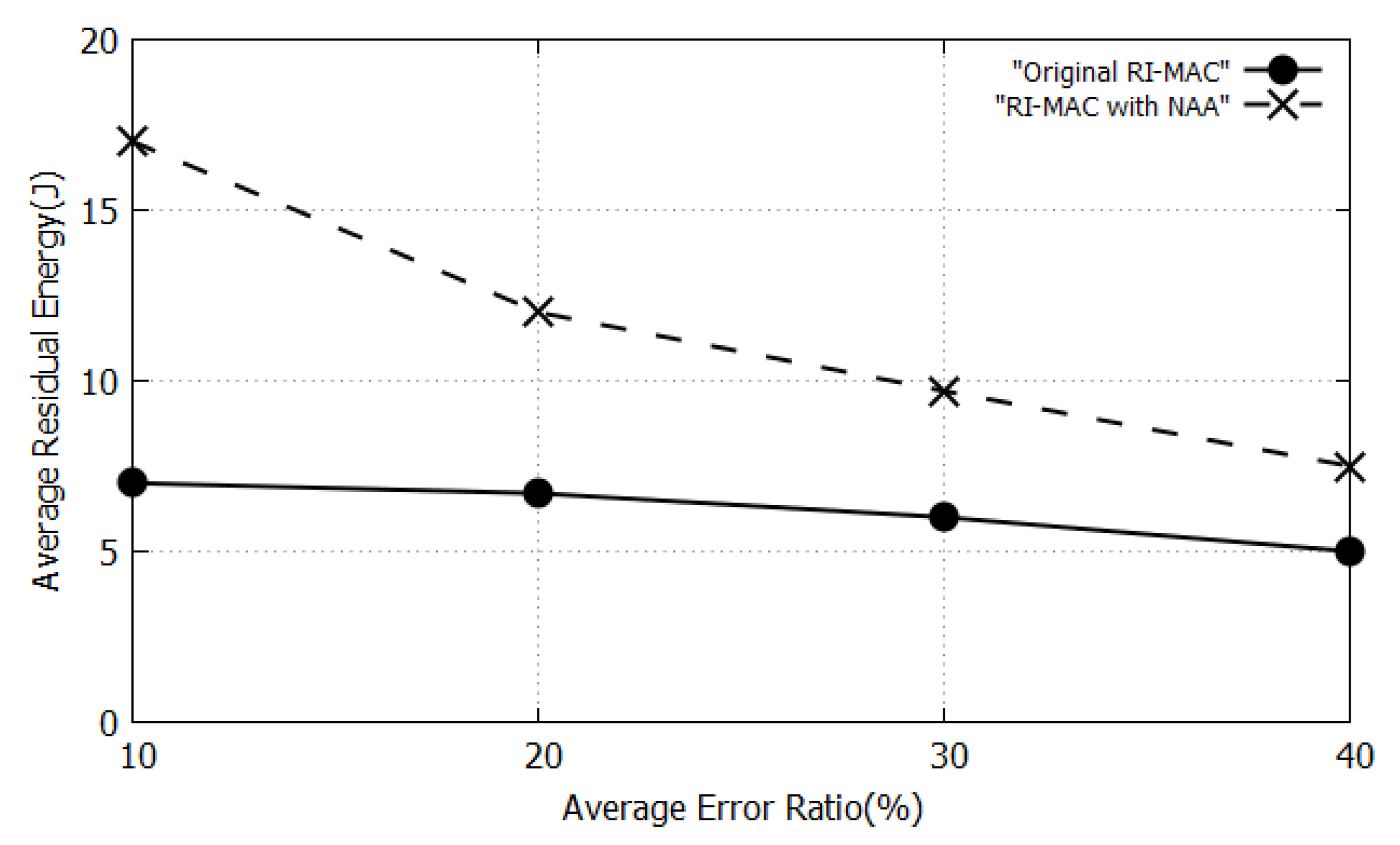
5. Performance Evaluation
5.1. Simulation Environment
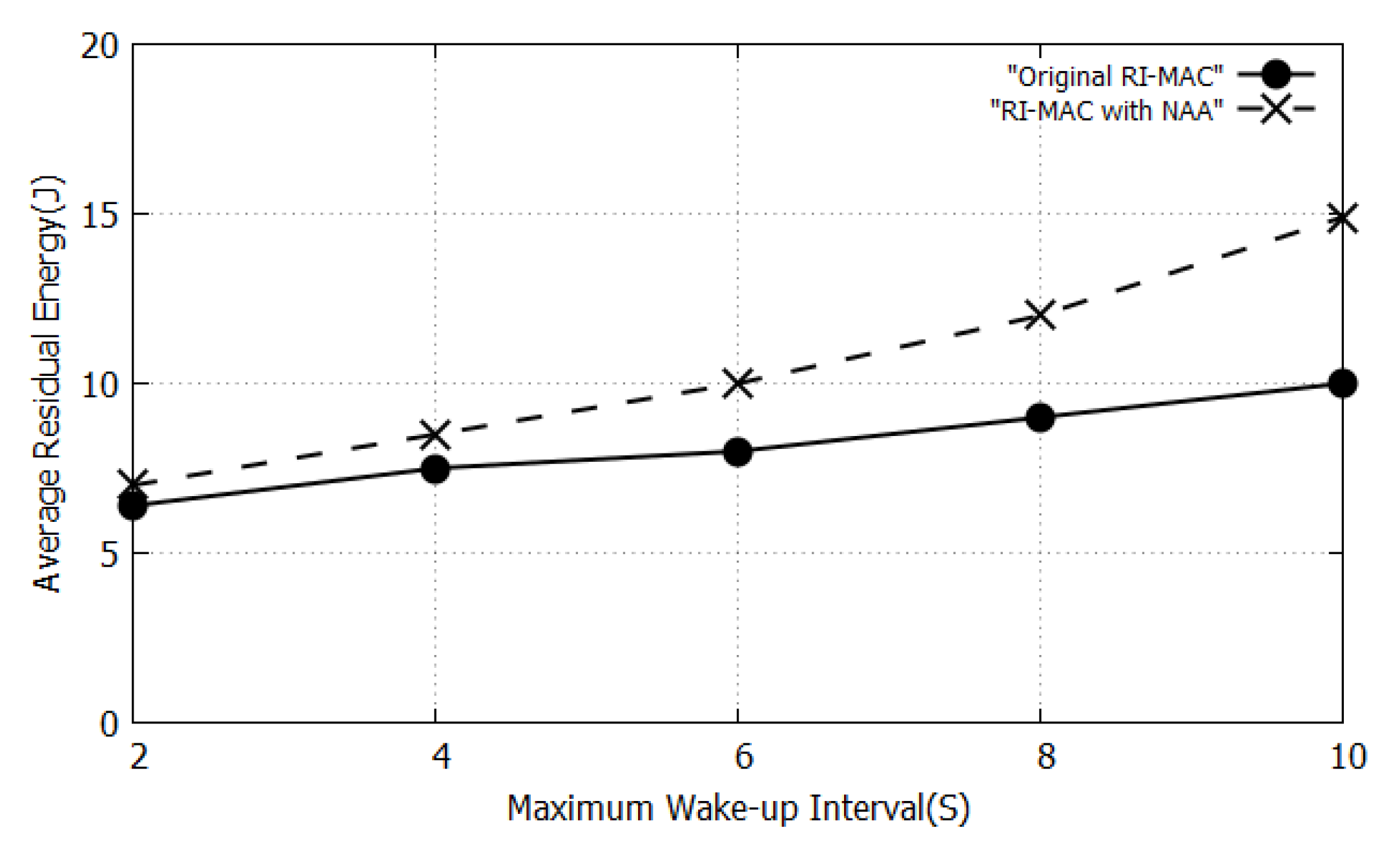
5.2. Results and Discussions
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- El-Mougy, A.; Ibnkahla, M.; Hattab, G.; Waleed, E. Reconfigurable Wireless Networks. Proc. IEEE 2015, 103, 1125–1158. [Google Scholar] [CrossRef] [Green Version]
- Saint, A. Where next for the internet of things? Information Technology Internet of Things. Eng. Technol. 2015, 10, 72–75. [Google Scholar] [CrossRef]
- Davoli, L.; Belli, L.; Cilfone, A.; Ferrari, G. From Micro to Macro IoT: Challenges and Solutions in the Integration of IEEE 802.15.4/802.11 and Sub-GHz Technologies. IEEE Internet Things J. 2018, 5, 784–793. [Google Scholar] [CrossRef]
- Bonino, D.; Delgado, M.T.; Alapetite, A.; Gilbert, T.; Axling, M.; Udsen, H.; Soto, J.A.C.; Spirito, T.G. ALMANAC: Internet of Things for Smart Cities. In Proceedings of the International Conference of Future Internet of Things and Cloud, Rome, Italy, 10–12 August 2015; pp. 309–316. [Google Scholar]
- Camps-Mur, D.; Garcia-Villegas, E.; Lopez-Aguilera, E.; Loureiro, P.; Lambert, P.; Raissinia, A. Enabling always on service discovery: Wifi neighbor awareness networking. IEEE Wirel. Commun. 2015, 22, 118–125. [Google Scholar] [CrossRef]
- Ejaz, W.; Naeem, M.; Shahid, A.; Anpalagan, A.; Minho, J. Efficient Energy Management for the Internet of Things in Smart Cities. IEEE Commun. Mag. 2017, 55, 84–91. [Google Scholar] [CrossRef] [Green Version]
- Xiao, Z.; Hock, B.L.; Ponnambalam, L. Participatory Sensing for Smart Cities: A Case Study on Transport Trip Quality Measurement. IEEE Trans. Ind. Inf. 2017, 13, 759–770. [Google Scholar] [CrossRef]
- Petrolo, R.; Loscri, V.; Mitton, N. Towards a smart city based on cloud of things, a survey on the smart city vision and paradigms. Trans. Emerg. Telecommun. Technol. 2017, 28, 2161–3915. [Google Scholar] [CrossRef] [Green Version]
- Ding, D.; Conti, M.; Solanas, A. A smart health application and its related privacy issues. In Proceedings of the Smart City Security and Privacy Workshop (SCSP-W), Vienna, Austria, 11–14 April 2016; pp. 1–5. [Google Scholar]
- Ramirez, A.R.G.; Carrasco, I.G.; Jasper, G.H.; Lopez, A.L.; Cuadrado, J.L.L.; Crespo, A.|G. Towards Human Smart Cities: Internet of Things for sensory impaired individuals. Computing 2017, 99, 107–126. [Google Scholar] [CrossRef]
- Naphade, M.; Banavar, G.; Harrison, C.; Paraszczak, J.; Morris, R. Smarter Cities and Their Innovation Challenges. Computer 2011, 44, 32–39. [Google Scholar] [CrossRef]
- Yang, Y.; Song, G.; Zhang, W.; Ge, X.; Wang, C. Neighbor-aware multiple access protocol for 5G mMTC applications. China Commun. 2016, 13, 80–88. [Google Scholar] [CrossRef]
- Gomez, J.; Cervantes, J.M.; Rangel, V.; Atahualpa, R.; Lopez-Guerrero, M. NARD: Neighbor-Assisted Route Discovery in Wireless Ad Hoc Networks. In Proceedings of the IEEE International Conference on Mobile Adhoc and Sensor Systems, Pisa, Italy, 8–11 October 2007. [Google Scholar]
- Romaszko, S.; Blondia, C. (NIAMac) Neighbor and Interference-Aware MAC Protocol for Wireless Ad Hoc Networks. In Proceedings of the IST Mobile and Wireless Communications Summit, Budapest, Hungary, 1–5 July 2007. [Google Scholar]
- Celik, Y.; Odabasioglu, N.; Uysal, M. Adaptive relay selection method for asynchronous amplify and forward cooperative communications. In Proceedings of the International Conference on Telecommunications, Thessaloniki, Greece, 16–18 May 2016. [Google Scholar]
- Yao, Y.; Huang, S.; Beaulieu, N.C.; Yin, C. Cooperative Transmission in Cognitive and Energy Harvesting-based D2D Networks. In Proceedings of the IEEE Wireless Communications and Networking Conference, San Francisco, CA, USA, 19–22 March 2017. [Google Scholar]
- Sun, Y.; Gurewitz, O.; Johnson, D.B. RI-MAC: A Receiver Initiated Asynchronous Duty Cycle MAC Protocol for Dynamic Traffic Load. In Proceedings of the ACM Conference on Embedded Networked Sensor Systems, Berkeley, CA, USA, 4–6 November 2008. [Google Scholar]
| Parameters | Value |
|---|---|
| Path loss model | Two-ray ground model |
| Transmission range | 250 m |
| MAC layer | IEEE 802.15.4 |
| Transmission rate | 200 Kbps |
| Traffic type | CBR |
| Packet size | 64 bytes |
| Queue size | 500 bytes |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, S.; Azfar Yaqub, M.; Kim, D. Neighbor Aware Protocols for IoT Devices in Smart Cities—Overview, Challenges and Solutions. Electronics 2020, 9, 902. https://doi.org/10.3390/electronics9060902
Lee S, Azfar Yaqub M, Kim D. Neighbor Aware Protocols for IoT Devices in Smart Cities—Overview, Challenges and Solutions. Electronics. 2020; 9(6):902. https://doi.org/10.3390/electronics9060902
Chicago/Turabian StyleLee, Sungwon, Muhammad Azfar Yaqub, and Dongkyun Kim. 2020. "Neighbor Aware Protocols for IoT Devices in Smart Cities—Overview, Challenges and Solutions" Electronics 9, no. 6: 902. https://doi.org/10.3390/electronics9060902
APA StyleLee, S., Azfar Yaqub, M., & Kim, D. (2020). Neighbor Aware Protocols for IoT Devices in Smart Cities—Overview, Challenges and Solutions. Electronics, 9(6), 902. https://doi.org/10.3390/electronics9060902







