Fast Logic Function Extraction of LUT from Bitstream in Xilinx FPGA
Abstract
:1. Introduction
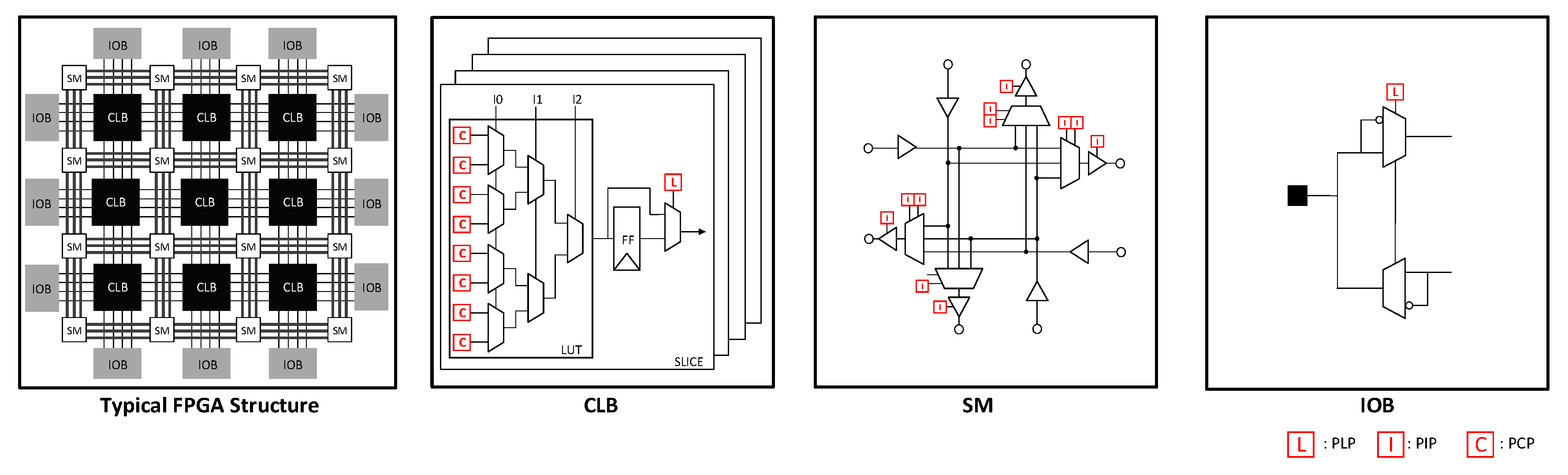
2. Background
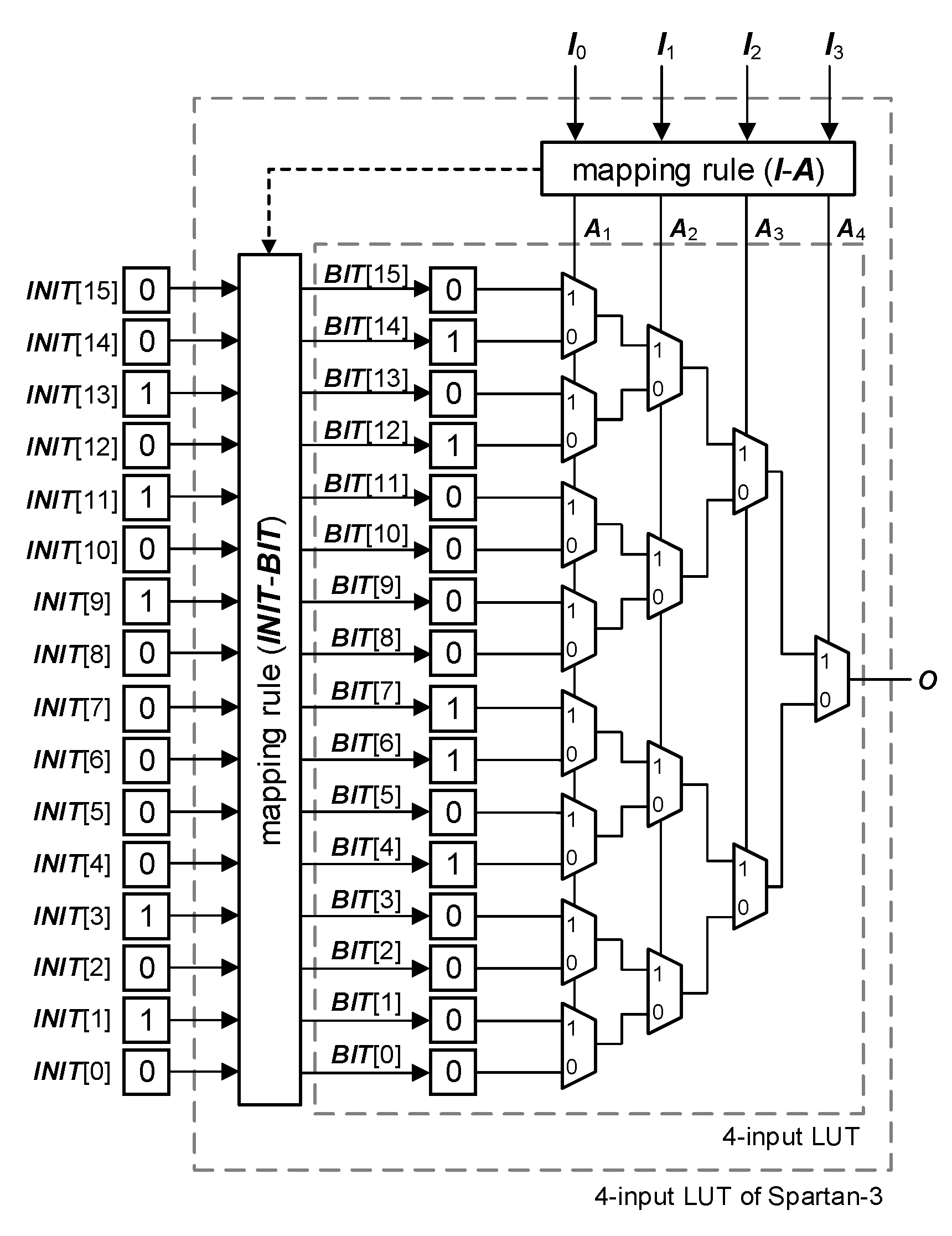
2.1. LUT Structure
2.2. The Previous LUT Extract Method
2.2.1. Bit Position Search
2.2.2. Mapping Table Construction
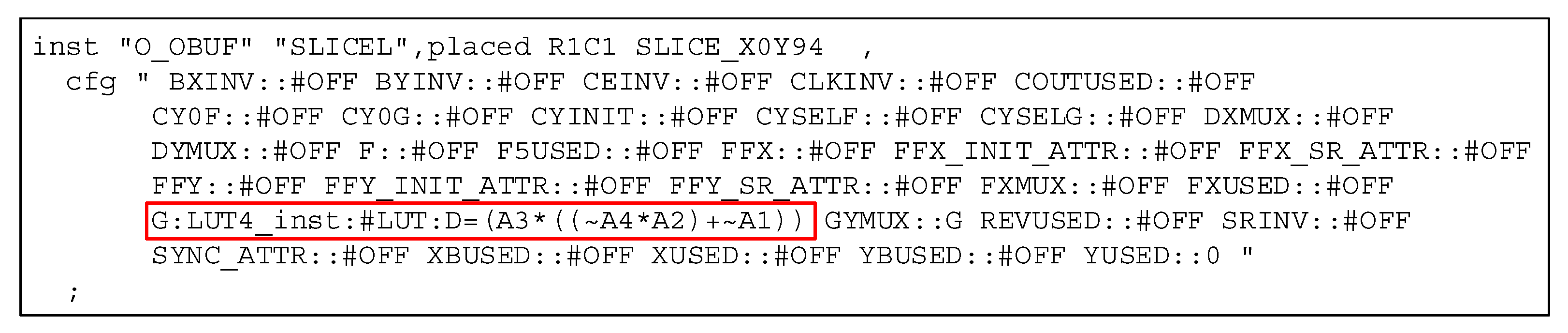
2.2.3. Logic Restoration
3. Proposed Method
3.1. I-A Mapping Construction
3.2. INIT-BIT Mapping Construction
4. Experimental Results
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Yu, H.; Lee, H.; Lee, S.; Kim, Y.; Lee, H.-M. Recent Advances in FPGA Reverse Engineering. Electronics 2018, 7, 246. [Google Scholar] [CrossRef] [Green Version]
- Lysaght, P.; Blodget, B.; Mason, J.; Young, J.; Bridgford, B. Invited Paper: Enhanced Architectures, Design Methodologies and CAD Tools for Dynamic Reconfiguration of Xilinx FPGAs. In Proceedings of the 2006 International Conference on Field Programmable Logic and Applications, Madrid, Spain, 28–30 August 2006. [Google Scholar]
- Yokoyama, H.; Toda, K. FPGA-based content protection system for embedded consumer electronics. In Proceedings of the 11th IEEE International Conference on Embedded and Real-Time Computing Systems and Applications (RTCSA’05), Hong Kong, China, 17–19 August 2005. [Google Scholar]
- Chamola, V.; Patra, S.; Kumar, N.; Guizani, M. FPGA for 5G: Re-configurable Hardware for Next Generation Communication. IEEE Wirel. Commun. 2020, 27, 140–147. [Google Scholar] [CrossRef]
- Cao, T.P.; Deng, G.; Mulligan, D. Implementation of real-time pedestrian detection on FPGA. In Proceedings of the 23rd International Conference Image and Vision Computing New Zealand, Christchurch, New Zealand, 26–28 November 2008. [Google Scholar]
- Swierczynski, P.; Fyrbiak, M.; Koppe, P.; Paar, C. FPGA Trojans Through Detecting and Weakening of Cryptographic Primitives. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2015, 34, 1236–1249. [Google Scholar] [CrossRef]
- Greene, J.; Hamdy, E.; Beal, S. Antifuse field programmable gate arrays. Proc. IEEE 1993, 81, 1042–1056. [Google Scholar] [CrossRef]
- McCollum, J. ASIC versus antifuse FPGA reliability. In Proceedings of the 2009 IEEE Aerospace conference, Big Sky, MT, USA, 7–14 March 2009. [Google Scholar]
- M. Kamoun, N.; Bossuet, L.; Ghazel, A. Experimental implementation of 2ODPA attacks on AES design with flash-based FPGA technology. In Proceedings of the 2010 International Conference on Microelectronics, Cairo, Egypt, 19–22 December 2010. [Google Scholar]
- Greene, J.; Kaptanoglu, S.; Feng, W.; Hecht, V.; Landry, J.; Li, F.; Krouglyanskiy, A.; Morosan, M.; Pevzner, V. A 65nm flash-based FPGA fabric optimized for low cost and power. In Proceedings of the 19th ACM/SIGDA international symposium on Field programmable gate arrays (FPGA ’11), Monterey, CA, USA, 27 February–1 March 2011. [Google Scholar]
- Heron, O.; Arnaout, T.; Wunderlich, H. On the reliability evaluation of SRAM-based FPGA designs. In Proceedings of the International Conference on Field Programmable Logic and Applications, Tampere, Finland, 24–26 August 2005. [Google Scholar]
- Wirthlin, M. High-reliability FPGA-based systems: Space, high-energy physics, and beyond. Proc. IEEE 2015, 103, 379–389. [Google Scholar] [CrossRef]
- Gören, S.; Ozkurt, O.; Yildiz, A.; Ugurdag, H.F. FPGA bitstream protection with PUFs, obfuscation, and multi-boot. In Proceedings of the 6th International Workshop on Reconfigurable Communication-Centric Systems-on-Chip (ReCoSoC), Montpellier, France, 20–22 June 2011. [Google Scholar]
- Note, J.-B.; Rannaud, É. From the bitstream to the netlist. In Proceedings of the 16th international ACM/SIGDA symposium on Field programmable gate arrays, New York, NY, USA, 24–26 February 2008. [Google Scholar]
- Benz, F.; Seffrin, A.; Huss, S.A. Bil: A tool-chain for bitstream reverse-engineering. In Proceedings of the 22nd International Conference on Field Programmable Logic and Applications (FPL), Oslo, Norway, 29–31 August 2012. [Google Scholar]
- Ding, Z.; Wu, Q.; Zhang, Y.; Zhu, L. Deriving an NCD file from an FPGA bitstream: Methodology, architecture and evaluation. Microprocess. Microsyst. 2013, 37, 299–312. [Google Scholar] [CrossRef]
- Yoon, J.; Seo, Y.; Jang, J.; Cho, M.; Kim, J.; Kim, H.; Kwon, T. A Bitstream Reverse Engineering Tool for FPGA Hardware Trojan Detection. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018. [Google Scholar]
- Seo, Y.; Yoon, J.; Jang, J.; Cho, M.; Kim, H.; Kwon, T. Poster: Towards reverse engineering FPGA bitstreams for hardware trojan detection. In Proceedings of the Network Distribution System Security Symposium (NDSS), San Diego, CA, USA, 18–21 February 2018. [Google Scholar]
- Zhang, T.; Wang, J.; Guo, S.; Chen, Z. A Comprehensive FPGA Reverse Engineering Tool-Chain: From Bitstream to RTL Code. IEEE Access 2019, 7, 38379–38389. [Google Scholar] [CrossRef]
- Ender, M.; Swierczynski, P.; Wallat, S.; Wilhelm, M.; Knopp, P.M.; Paar, C. Insights into the mind of a trojan designer. In Proceedings of the 24th Asia and South Pacific Design Automation Conference, Tokyo, Japan, 21–24 January 2019. [Google Scholar]
- Choi, S.; Park, J.; Yoo, H. Reverse Engineering for Xilinx FPGA Chips using ISE Design Tools. J. Integr. Circuits Syst. 2020, 6, 1. [Google Scholar]
- Project X-Ray. Available online: https://symbiflow.readthedocs.io/projects/prjxray/en/latest/ (accessed on 12 June 2020).
- Yu, H.; Lee, H.; Shin, Y.; Kim, Y. FPGA reverse engineering in Vivado design suite based on X-ray project. In Proceedings of the 2019 International SoC Design Conference (ISOCC), Jeju, Korea, 6–9 October 2019. [Google Scholar]
- Chakraborty, R.S.; Narasimhan, S.; Bhunia, S. Hardware Trojan: Threats and emerging solutions. In Proceedings of the 2009 IEEE International High Level Design Validation and Test Workshop, San Francisco, CA, USA, 4–6 November 2009. [Google Scholar]
- Wallat, S.; Fyrbiak, M.; Schlögel, M.; Paar, C. A Look at the Dark Side of Hardware Reverse Engineering—A Case Study. In Proceedings of the 2017 IEEE 2nd International Verification and Security Workshop (IVSW), Thessaloniki, Greece, 3–5 July 2017. [Google Scholar]
- Chakraborty, R.S.; Saha, I.; Palchaudhuri, A.; Naik, G.K. Hardware Trojan Insertion by Direct Modification of FPGA Configuration Bitstream. IEEE Des. Test 2013, 30, 45–54. [Google Scholar] [CrossRef]
- Khaleghi, B.; Ahari, A.; Asadi, H.; Bayat-Sarmadi, S. FPGA-Based Protection Scheme against Hardware Trojan Horse Insertion Using Dummy Logic. IEEE Embedded Sys. Lett. 2015, 7, 46–50. [Google Scholar] [CrossRef]
- Swierczynski, P.; Fyrbiak, M.; Paar, C.; Huriaux, C.; Tessier, R. Protecting against Cryptographic Trojans in FPGAs. In Proceedings of the 2015 IEEE 23rd Annual International Symposium on Field-Programmable Custom Computing Machines, Vancouver, BC, Canada, 2–6 May 2015. [Google Scholar]
- Jeong, M.; Lee, J.; Jung, E.; Kim, Y.H.; Cho, K. Extract LUT Logics from a Downloaded Bitstream Data in FPGA. In Proceedings of the 2018 IEEE International Symposium on Circuits and Systems (ISCAS), Florence, Italy, 27–30 May 2018. [Google Scholar]
- Xilinx. Spartan-3 Libraries Guide for HDL Designs; Xilinx: San Jose, CA, USA, 2013. [Google Scholar]
- Xilinx. Virtex-5 Ligraries Guide for HDL Designs; Xilinx: San Jose, CA, USA, 2013. [Google Scholar]
- Xilinx. Available online: http://www.xilinx.com (accessed on 12 June 2020).
- Intel FPGA. Available online: https://www.intel.com/content/www/us/en/products/programmable/fpga.html?elq_cid=4776342&erpm_id=7614038 (accessed on 12 June 2020).
- Beckhoff, C.; Koch, D.; Torresen, J. The Xilinx Design Language (XDL): Tutorial and use cases. In Proceedings of the 6th International Workshop on Reconfigurable Communication-Centric Systems-on-Chip (ReCoSoC), Montpellier, France, 20–22 June 2011. [Google Scholar]
- Lavin, C.; Padilla, M.; Lamprecht, J.; Lundrigan, P.; Nelson, B.; Hutchings, B. RapidSmith: Do-It-Yourself CAD Tools for Xilinx FPGAs. In Proceedings of the 2011 21st International Conference on Field Programmable Logic and Applications, Chania, Greece, 5–7 September 2011. [Google Scholar]



| FPGA type (LUT type) | Spartan-3 (4-input LUT) | Virtex-5 (6-input LUT) | ||
|---|---|---|---|---|
| Algorithm | Exhaustive [6] | Proposed | Exhaustive [6] | Proposed |
| Bit position search | 1.1 min | 1.1 min (0%) | 1.6 min | 1.6 min (0%) |
| Mapping table construction | 8.5 min | 3.1 min (64%) | 52 min | 6.3 min (88%) |
| Logic restoration | 0.01 ms | 0.01 ms (0%) | 5 ms | 5 ms (0%) |
| Total time | 9.6 min | 4.1 min (57%) | 53.6 min | 7.9 min (86%) |
| FPGA (LUT Type) | Spartan-3 (4-input LUT) | Virtex-5 (6-input LUT) | |||||
|---|---|---|---|---|---|---|---|
| Algorithm | # of LUT | Time | # of LUT | Time | |||
| Exhaustive [6] | Proposed | Exhaustive [6] | Proposed | ||||
| ISCAS’85 Benchmark | C17 | 2 | 19.2 min | 8.3 min | 2 | 1.8 h | 15.9 min |
| C499 | 78 | 13.1 h | 5.7 h | 66 | 2.5 days | 8.7 h | |
| C880 | 115 | 18.6 h | 8.0 h | 77 | 2.9 days | 10.2 h | |
| C1908 | 103 | 16.2 h | 6.9 h | 81 | 3.0 days | 10.7 h | |
| C3540 | 326 | 2.2 days | 0.9 days | 222 | 8.3 days | 1.2 days | |
| C6288 | 703 | 4.7 days | 2.0 days | 468 | 2.5 weeks | 2.6 days | |
| Practical applications | DES | 1397 | 9.3 days | 4.0 days | 983 | 5.2 weeks | 5.4 days |
| AES | 7644 | 7.3 weeks | 3.1 weeks | 2742 | 14.7 weeks | 2.2 weeks | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Choi, S.; Yoo, H. Fast Logic Function Extraction of LUT from Bitstream in Xilinx FPGA. Electronics 2020, 9, 1132. https://doi.org/10.3390/electronics9071132
Choi S, Yoo H. Fast Logic Function Extraction of LUT from Bitstream in Xilinx FPGA. Electronics. 2020; 9(7):1132. https://doi.org/10.3390/electronics9071132
Chicago/Turabian StyleChoi, Soyeon, and Hoyoung Yoo. 2020. "Fast Logic Function Extraction of LUT from Bitstream in Xilinx FPGA" Electronics 9, no. 7: 1132. https://doi.org/10.3390/electronics9071132
APA StyleChoi, S., & Yoo, H. (2020). Fast Logic Function Extraction of LUT from Bitstream in Xilinx FPGA. Electronics, 9(7), 1132. https://doi.org/10.3390/electronics9071132






