A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions
Abstract
1. Introduction
1.1. Motivation
1.2. Scope of This Survey
1.3. Main Contribution
- Discussion of IoT architectures and IoT Protocols, covering their technologies, frequency bands, and data rates.
- Explanation of vulnerabilities, threat dimensions and attack surfaces of IoT systems, including attack types related to IoT protocols, which are discussed in detail.
- Review of ML- and DL-based IDSs, involving their design choices, pros, cons and detection methods, which are covered in detail.
- Discussion of the datasets available for network and IoT security-related research, covering the advantages and limitations of each enumerated with details.
- Explanation of the applications of ML and DL techniques for developing IDSs in IoT networks and their systems.
- Presentation of the current research challenges and their future directions for research in this field.
2. Current Reviews
3. IoT System Environment
3.1. IoT Architecture
- A 3-layer architecture. The most common and basic model is a 3-layer architecture comprising of the perception, network and application layers [3,4,43], as depicted in Figure 2, the perception layer is also called ‘the device layer’ that includes physical devices and sensors. The network layer is also named ‘the transmission layer’, which should securely transmit the telemetry data of sensors to processing and data analytical systems. The application layer offers global management of applications using the systems at the network layer.
- International Telecommunication Union (ITU) recommended Reference Model for IoT. ITU recommends a reference model for IoT that comprises four layers, along with security and management capabilities linked to the layers [45]. The layers are as follows: device layer, network layer, application support layer, service support and application layer, as shown in Figure 3.
- IoT-A Architectural Reference Model proposed by the European Commission (FP7). The European Commission within the Seventh Framework Program (FP7) supported the project IoT-A proposed by Martin Bauer et al. [6]. The IoT-A model attempts to design an architecture that could meet the requirements of the industry and researchers. It offers high-level architectural perspectives and views for building IoT systems. The architecture comprehensively describes the structuring and modeling of IoT business process management, IoT services, cross-service organization and virtual entities, information and functional viewpoints, in an abstract way [46]. Amongst these various views, a functional view of IoT architecture is depicted in Figure 4.
- An IoT Reference Architecture developed by Web Service Oxygen (WSO2). WSO2, an open-source technology provider, has proposed an Architectural Reference Model based on its skills in the IoT solutions development. Figure 5 depicts the WSO2 recommended architecture. It consists of five layers: (1) Client/external communications—Web/Portal, Dashboard, Application Programming Interface (APIs), (2) Event processing and analytics (including data storage), (3) Aggregation/bus layer—Enterprise Service Bus (ESB) and message broker, (4) Relevant transports—XMPP/CoAP/AMQP/HTTP/MQTT, etc. and (5) Devices [47]. The model includes the cross-cutting layers that have (1) a device manager, and (2) an identity and access management system.
- An IoT Reference Architecture suggested by Cisco: Cisco introduced a seven-layered IoT reference model [48]. The model and its levels are illustrated in Figure 6. The authors described that control information flows from level 7 to level 1 in a control pattern. The flow of information is the reverse in a monitoring pattern and it is bidirectional in most systems.
3.2. IoT Protocols
4. IoT-Based Threats and Attacks
4.1. User Interface
4.2. Cloud Services
- Authorization Attacks. Through the exploitation of vulnerabilities in data security mechanisms, an attacker may be able to gain unauthorized access to information on both cloud and IoT systems.
- Integrity Attacks. Such attacks enable an attacker to compromise the integrity of data through spoofing and bypass the authorization controls to gain direct access to databases.
- Compromise of Visualization platform. A vulnerability in the virtualization platform can be exploited by an attacker to bypass security and isolation controls between the host and the guest operating system (OS), resulting in privilege escalation and pivoting attacks [65].
- Confidentiality Attacks. IoT systems, like wearable devices, are used to monitor health-related data of highly confidential nature. Similarly, smart home devices capture sensitive private data of the users. Privacy and confidentiality concerns overshadow the advantages of cloud services. Moreover, multi-tenancy and geographical location of cloud services pose a serious threat to the confidentiality of data through privilege escalation and hacking [66].
4.3. Connections of Multiple IoT Systems
4.4. Protocols Level Attacks
4.5. Radio-Frequency Identification (RFID)
- Tag Disable. An attacker may remove the tag, delete the tag memory by sending a kill command, remove the antenna, give a high energy wave to a tag, and use a Faraday cage to block electromagnetic waves.
- Tag Modification. An attacker modifies or deletes valuable data from the memory of the tag.
- Cloning Tags. An attacker imitates or clones the tags after skimming the tag’s information.
- Reverse Engineering. Using reverse engineering, an attacker can make a copy of a tag, and using tag examination, the attacker may get confidential data stored within a tag.
- Eavesdropping. RFID systems working in ultra high frequency (UHF) are more vulnerable to this threat. An attacker gathers the information shared between a valid tag and valid reader.
- Snooping. An attacker introduces an unauthorized reader to interact with the tag.
- Skimming. An attacker snoops data shared between a legitimate reader and legitimate tag.
- Replay Attack. An attacker spies to collect information about the IoT device or node replays eavesdropped information to achieve deception.
- Relay Attacks. An attacker places an illegitimate device between the tag and the reader to intercept, modify and forward information directly to other systems.
- Electromagnetic (EM) Interference. An attacker creates a signal in the same range as the reader to preclude tags from communicating with readers.
- Fake RFID Tag Query. An attacker sends queries and gets the same response from a tag at various locations to determine the location of a specific tag.
- Cryptograph Decipher Attack. An attacker decodes encryption algorithms by launching violent attacks and gets the plain text by deciphering the intercepted cryptography.
- Blocker tag Attack. Using a blocker tag, an attacker attempts to restrict the reader from reading tags.
4.6. Zigbee Protocol
- Sniffing. Zigbee networks are exposed to sniffing attacks since they do not implement encryption techniques. The attacker can capture some packets to execute malicious activities using some software tools like KillerBess’s zbdump tool [76].
- Replay Attack. If an attacker is able to intercept the packets, the attacker can sniff raw packets of a network and could re-send the captured data as normal traffic [76].
- Attaining the Link or Network key. Since keys need to be reinstalled on the air when its objects require reflashing, an attacker can obtain the ZigBee network or link keys. Also, physical attacks can be used to obtain the key, where the keys can be extracted from ZigBee devices’ flash memory when the device is physically accessed [77,78].
- Eavesdropping. An attacker can eavesdrop a ZigBee network and redirect its packets using an MiTM attack.
- ZED Sabotage Attack. Authors in [79] proposed an attack against the ZigBee protocol called the ZigBee End-Device (ZED). The purpose of the attack is to make the ZED unavailable by transmitting a particular signal periodically to wake up the device to drain its battery.
4.7. Wireless Fidelity (WiFi)
- Attacks Related to Retrieving Key. An attacker would monitor specific packets and then crack the key process offline. The common attacks in this category are Pyshkin, Tews, and Weinmann (PTW) attacks, Fluhrer, Mantin, and Shamir (FMS) attack, KoreK Family Attacks, Dictionary Attack and address resolution protocol (ARP) Injection [80].
- Attacks Related to Retrieving Keystream. An attacker only required to monitor for specific packets and then go on to perform the key cracking process offline. The common attacks in this category are PTW attacks, FMS attack, KoreK Family Attacks, Dictionary Attack and ARP Injection [80].
- DoS or Availability Attacks. This category of attacks includes those attacks that result in the unavailability of some service or network that is commonly called a DoS attack. These attacks usually target either a specific user or device, or try to exhaust network resources (e.g., the network router or Access Point), resulting in corrupting services for all users in that network. These attacks mostly depend on the broadcast of forged 802.11 management messages, which are easy to launch in versions of the WiFi standards up to 802.11n, as the management messages are transmitted unguarded [81]. Attacks in this category include: Disassociation Attack, Block ACK flood, Authentication Request Flooding Attack, Deauthentication Broadcast Attack, Fake Power Saving Attack, Beacon Flooding Attack, Probe Request and Response Flooding Attacks. A survey of DoS attacks in 802.11 is covered in [82].
4.8. Bluetooth
- PIN Cracking Attack. This type of attack is performed during the pairing of the device and the process of authentication. An attacker collects the random number (RAND) and the Bluetooth Device Address (BD_ADDR) of the targeted device using some frequency sniffer tool. Then, a brute-force algorithm (for example, E22 algorithm) is applied to check all possible combinations of the PIN with the data collected earlier until the correct PIN is determined [84].
- MAC Spoofing Attack. An attack is launched during the process of link keys generation and before encryption is established. Devices manage to authenticate each other using generated link-keys. In this, attackers can imitate another user. Attackers can also dismiss connections or even alter data [84].
- Man-in-the-Middle (MIM) Attack. MIM attacks are launched when devices are trying to pair [86]. After the attack is launched, devices share messages unknowingly [58]. During this time authentication is performed without the shared secret keys [58]. When the attack is successful, the two devices are paired to the attacker [57,58], while they believe the pairing was successful.
- Bluebugging. An attacker exploits vulnerabilities of old devices firmware to spy on phone calls, send and receive messages, and connect to the Internet without legal users’ knowledge.
- Bluesnarfing. An attacker gets unauthorized access to devices to retrieve information and redirect the incoming calls.
- BluePrinting Attack. This attack is launched to capture the device model, manufacturer, and firmware version of the device. This attack will work only if the target device’s BD_ADDR is known.
- Fuzzing Attack. In a fuzzing attack, a device is forced to behave abnormally by an attacker through sending malformed data packets to Bluetooth radio of the device.
- Brute-Force BD_ADDR Attack. Since the first three bytes of BD_ADDR are fixed and known publicly, the brute-force attack is launched to scan on the last three bytes [84].
- Worm Attacks. In this attack, an attacker sends a malicious software or Trojan file to available vulnerable Bluetooth devices. Examples of these attacks are Sculls’ worm, Cabir worm and Lasco worm.
- DoS attacks. These attacks target the physical layer or above layers in the protocol stack. Some typical DoS attacks are battery exhaustion, BlueChop, BD_ADDR duplication, BlueSmack, Big NAK (Negative Acknowledgement) and L2CAP guaranteed service.
4.9. Near Field Communication (NFC)
- Eavesdropping. By using powerful and bigger antennas than those of mobile devices, NFC communications can be received or intercepted by an attacker in the vicinity of the devices. This allows an attacker to eavesdrop an NFC communication across larger distances.
- Data Corruption. An attacker can modify data transmitted over an NFC interface. If the attacker alters the data into an unrecognized format, this may result in DoS attacks.
- Data Modification. An attacker alters the actual data using amplitude modulations of data transmissions.
- Data Insertion. Malicious and undesirable data can be inserted in the form of messages into the data during the data exchange between two devices.
- NFC Data Exchange Format (NDEF) attacks. An attacker would exploit partial signatures, record composition attacks and establish trust [88].
4.10. IEEE 802.15.4
- Radio interference Attack. An attacker transmits high transmission powered radio interference signals over all channels of the related frequency band.
- Symbol Flipping/ Signal Overshadowing Attack. An attacker injects wrong data into a network by converting a legitimate data frame into an altered frame comprising information of the attacker’s choice.
- Steganography Attack. Adversaries would use a hidden channel to exchange information about the launching of new attacks in the network.
- Node-Specific Flooding. In this, the emission of packets is used to cause degradation throughput IoT networks by flooding massive fake data.
- Back-Off Manipulation. An attacker transmits unnecessary packets to the victim and due to excessive packet reception, the targeted nodes’ power sources are ultimately exhausted.
- Battery Life Extension (BLE) Pretense. An attacker transmits unnecessary packets to the victim and due to excessive packet reception, the targeted nodes’ power sources are ultimately exhausted.
- Random Number Generator (RNG) Tampering. An attacker uses RNG in a way that guarantees that the back-off periods chosen by the adversary are much smaller than those selected by legitimate nodes.
- Back-Off Countdown Omission. This type of attack implicates the complete exclusion of the random back-off countdown by a malicious attacker.
- Clear Channel Assessment (CCA) Manipulation/ Reduction/Omission. An attacker gains channel access more frequently and quickly than it is done by legitimate network nodes.
- Same-Nonce Attack. An attacker obtains ciphertext keys to gather valuable information about transmitted data.
- Replay-Protection Attack. In this type of attack, frames with large sequence numbers are sent by attackers to targeted legitimate nodes. This results in dropping data frames with smaller sequence numbers from other legitimate nodes.
- Acknowledgment (ACK) Attack. An attacker sends back a false ACK on behalf of the receiver with the correct expected sequence number to the sender. This prohibits data retransmission by misleading the sender into believing that the frame has been delivered to the receiver successfully [89].
- Guaranteed Time Slot (GTS) Attack. GTS attacks are initiated against the network by exploiting the GTS management scheme.
- Personal Area Networks Identifier (PANId) Conflict Attack. An attacker can abuse the conflict resolution procedure by sending fake PANId conflict notifications to the targeted PAN coordinator to start conflict resolution, thus temporarily preventing or delaying communications between the PAN coordinator and member nodes.
- Ping-Pong Effect Attack. This attack causes packet loss and service interruption, dropping node performance, and increasing consumption of energy and network load.
- Bootstrapping Attack. An attacker forces a targeted network node to become unrelated with its PAN at a time of the attacker’s choosing by initiating any of the MAC or PHY layer attacks with the ultimate aim of causing DoS.
- Steganography Attack. An attacker hides information within the MAC and PHY frame fields of the IEEE 802.15.4 protocol [89]. Data can be hidden in IEEE 802.15.4 networks by using the PHY header field of PHY frames. Similarly, Steganography attacks would also be launched by hiding information within the MAC fields. Steganography attacks form a hidden channel between cooperating attackers in the network, which opens up a large number of prospects for adversaries.
4.11. Routing Protocol for Low Power and Lossy Network (RPL) Attack
- Sinkhole Attack. An attacker may announce a favorable route or falsified path to entice many nodes to redirect their packets through it.
- Sybil Attack. An attacker may use different identities in the same network to overcome the redundancy techniques in scattered data storage. Also, this can be used to attack routing algorithms.
- Wormhole Attack. An attacker disturbs both traffic and network topology. This attack can be launched by generating a private channel between two attackers in the network and transmitting the selected packets through it.
- Blackhole Attack. An attacker maliciously advertises itself as the shortest path to the destination during the path-discovering mechanism and drops the data packets silently.
- Selective Forward Attack. It is a variant of the Blackhole attack, where an attacker only rejects a specific subpart of the network traffic and forwards all RPL control packets. This attack is mainly targeted to disturb routing paths; however, it can also be used to filter any protocol [74].
- Hello flooding attack. An attacker can announce itself as a neighbor to many nodes, even the complete network by broadcasting a “HELLO” message with a strong powered antenna and a favorable routing metric. This is done by an attacker in order to deceive other objects to send their packet through it [94].
4.12. Internet Protocol (IPv6) and Low-Power Wireless Personal Area Networks (6LoWPAN) Based Attacks
- Fragmentation Attack. IoT object communicating in IEEE 802.15.4 has a Maximum Transmission Unit (MTU) of 127 bytes, as opposed to in IPv6, which has a minimum MTU of 1280 bytes. This is done using a fragmentation mechanism. Since fragmentation is performed without using any type of authentication, an attacker can inject fragments among a fragmentation chain [95].
- Authentication Attack. In the absence of an authentication mechanism in 6LowPAN, any malicious object can join the network and get legitimate access [92].
- Confidentiality Attack. In the absence of an encryption technique in 6loWPAN, attacks affecting confidentiality, like eavesdropping, spoofing and Man in the Middle can be launched.
5. Intrusion Detection System (IDS)
5.1. Design Choices of ML/DL Based IDS
- Detection methods. It could be signature-based, anomaly-based or hybrid-based detection.
- Architecture. It can be classified as centralized and distributed architecture.
- Data source. It would be host-based, network-based, or hybrid-based data inputs.
- Time of detection. It can be online or offline detection.
- Environment. It would be wired, wireless, ad-hoc networks.
5.2. Detection Methods of IDSs
5.2.1. Signature-Based Detection Techniques
5.2.2. Anomaly-Based Detection Techniques
5.2.3. Specification-Based Detection Techniques
5.2.4. Hybrid-Based Detection Techniques
6. Machine Learning (ML) Techniques for IDS
6.1. Naive Bayes (NB) Classifier
6.2. K-Nearest Neighbor (KNN)
6.3. Decision Trees (DTs)
6.4. Support Vector Machines (SVMs)
6.5. Ensemble Learning (EL)
6.6. Random Forest (RF)
6.7. k-Means Clustering
6.8. Principle Component Analysis (PCA)
7. Deep Learning (DL) Techniques for IDSs
7.1. Recurrent Neural Networks (RNNs)
7.2. Convolutional Neural Network (CNN)
7.3. Deep Autoencoders (AEs)
7.4. Restricted Boltzmann Machine (RBM)
7.5. Deep Belief Network (DBN)
7.6. Generative Adversarial Network (GAN)
7.7. Ensemble of DL Networks (EDLNs)
8. Datasets Available for IoT Security
- KDD99. This is a modification of the DARPA funded DARPA98 dataset that initiated from an IDS program conducted at MIT’s (Massachusetts Institute of Technology) Lincoln Laboratory for evaluating IDSs that differentiate between inbound normal and attack connections. Later on, this dataset was used in the International Knowledge Discovery and Data Mining Tools Competition [202] after some filtering, resulting in what is known as the KDD CUP 99 dataset [199]. This dataset has been used by most of the researchers for the last two decades now. The absence of alternatives has resulted in several works directed on the KDD CUP 99 dataset [199] as a widespread benchmark for the accuracy of the classifier. However, KDD-99 possesses numerous weaknesses, which discourage its use in the current context, including its age, highly skewed targets, non-stationarity between training and test datasets, pattern redundancy, and irrelevant features.
- NSL-KDD. NSL-KDD is an effort by the researchers who published their work in [199] to overcome the weaknesses of KDD-99. It is a more balanced resampling of KDD-99 where the emphasis is laid on examples that are expected to be missed by classifiers trained on the basic KDD-99. However, as their authors acknowledge themselves, there are still weaknesses in the dataset, like its non-representation of low footprint attacks [200].
- The DEFCON dataset. DEFCON-8 dataset, generated in 2000, comprises of port scanning and buffer overflow attacks. Another version, the DEFCON-10 dataset, generated in 2002 uses bad packets, FTP by telnet protocol, administrative privilege, port scan and sweeps attacks [203]. The traffic produced during the Capture the Flag (CTF) competition is dissimilar from network traffic of the real world because it primarily consists of attack traffic as opposed to usual background traffic, therefore its applicability for evaluating IDS is limited. The dataset is mostly used to assess alert correlation techniques [204,205].
- The Center of Applied Internet Data Analysis (CAIDA)—2002–2016 datasets [203,206]. This organization has three different datasets: (1) the CAIDA OC48, covering various types of data observed on an OC48 link, (2) the CAIDA DDOS, which comprises of one-hour DDoS attack traffic that happened in August 2007, and (3) the CAIDA Internet traces 2016, which is passive traffic traces from CAIDA’s Equinix-Chicago monitor on the high-speed Internet backbone [207]. These datasets are specific to certain events or attacks and are anonymized with their protocol information, payload, and destination. These are not effective benchmarking datasets because of several shortcomings, as discussed in [207], like the unavailability of ground truth about the attack instances.
- The LBNL dataset contains anonymized traffic, which is comprised of only header data. The dataset was generated at the Lawrence Berkley National Laboratory, by gathering real outbound, inbound and routing traffic from two edge routers [206]. It lacked the labeling process and also no extra features were created [206].
- The UNSW-NB15 is a dataset developed at UNSW Canberra by the researchers of [208] for the evaluation of IDS. The researchers used the IXIA PerfectStorm tool to generate a mixture of attack and benign traffic, at the Australian Center of Cyber Security (ACCS) over two days, in sessions of 16 and 15 h. They generated a dataset of size 100 GB in the form of pcap files with a substantial number of novel features. NB15 was planned as a step-up from the KDD99 dataset discussed above. It covers 10 targets: one benign, and nine anomalous, namely: DoS, Exploits, Analysis, Fuzzers, Worms, Reconnaissance, Generic, Shell Code and Backdoors [208]. However, the dataset was designed based on a synthetic environment for producing attack activities.
- The ISCX datasets [207]. The Canadian Institute for Cybersecurity has been working on the generation of numerous datasets that are used by independent researchers, universities and private industry around the world. A few datasets relevant to our work are IPS/IDS dataset on AWS (CSE-CIC-IDS2018), IPS/IDS dataset (CICIDS2017), CIC DoS dataset (application-layer), ISCX Botnet dataset, ISCX IDS 2012 dataset, ISCX Android Botnet dataset, and ISCX NSL-KDD dataset. Their latest dataset related to our work is CICIDS2017. This dataset covers benign and the most up-to-date common attacks, which is comparable to the real-world data [209]. The CICIDS2017 consists of multiple attack scenarios, with realistic user-related background traffic produced by using the B-Profile system. For this dataset they built the abstract behavior of 25 users based on the FTP, SSH, HTTP, HTTPS and email protocols. However, the ground truth of the datasets, which would improve the reliability of the labeling process, was not shared. Moreover, applying the idea of profiling, which was used to produce these datasets, in real networks could be problematic due to their intrinsic complexity [209].
- The Tezpur University IDS (TUIDS) dataset [206]. This dataset was generated by the professors from Tezpur University, India. This dataset features DoS, Probing, Scan, U2R and DDoS attack scenarios, performed in a testbed. However, the flow level data does not contain any new features other than those produced by the flow-capturing process [209].
- BoT-IoT [209] The BoT-IoT dataset was created by designing a realistic network environment in the Cyber Range Lab of The center of UNSW Canberra Cyber. The environment incorporates a combination of normal and botnet traffic. Researchers also present a testbed setting for handling the existing dataset shortcomings of capturing complete network information, correct labeling, and the latest and complex attack diversity. In their work, the authors also evaluate the reliability of the BoT-IoT dataset using different ML and statistical techniques for forensics purposes in comparison to the other datasets discussed above. The dataset’s source files are provided in different formats, including the original pcap files, the generated argus files and CSV files. The files were separated, based on attack category and subcategory, to better assist in the labeling process. The dataset contains OS and Service Scan, DoS, DDoS, Data exfiltration and Keylogging attacks. Based on the protocol used, the DDoS and DoS attacks are further organized [209].
- IoTPoT Dataset [210]. This dataset was generated through honeypots, so there was no process for manual labeling and anonymization; however, it has restricted view of the network traffic since only attacks launched at the honeypots could be observed. Authors claim that IoTPoT examines Telnet-based attacks against different IoT devices running on different CPU architectures such as MIPS, ARM and PPC. During 39 days of operation, authors recorded 76,605 download attempts of malware binaries from 16,934 visiting IP. Authors further claim that none of these binaries could have been detected by existing honeypots that handle the Telnet protocol, such as telnet password honeypot and honeyd, because these honeypots are not capable of handling different incoming commands initiated by the attackers [210].
- N-BaIoT Dataset. The most recent dataset, specifically related to the evaluation of IDS for IoT networks is generated by the authors [41] as part of their research work on online network IDS. They generated and collected traffic from two networks: one, an IP camera video surveillance network where they launched eight different types of attacks that affect the availability and integrity of the video uplinks; two, an IoT network comprising of three PCs and nine IoT devices, out of which one was infected with the Mirai botnet malware. A detailed explanation of the attacks and network topologies is available in their published papers [41]. The authors compiled a dataset of extracted feature vectors for each of these nine attacks. The attack types include: OS Scan, Fuzzing, Video injection, ARP MiTM, Active Wiretap, SSDP flood, SYN DoS, SSL Renegotiation and Mirai.
9. Challenges and Future Research Directions
- To test and validate proposed NIDS, a good quality dataset related to IoT IDS is very essential. Such a dataset should possess a reasonable size of network flow data covering both attack and normal behavior with the corresponding label. Furthermore, in order to capture normal behavior, normal traffic data from each type of IoT device is required, other than the attack data for testing the NIDS. However, as discussed in the previous section, most of the publicly available datasets lack in providing the required features, like missing labels, incomplete network features, missing raw pcap files and are difficult to comprehend and/or have incomplete CSV files. Moreover, datasets available only capture normal behavior of a specific type of IoT devices, which restricts training of IDS on those devices only. Creating a dataset that can address these issues in a real environment will be a challenge and a potential area of research.
- Developing an online and real-time, anomaly-based IDS for IoT networks is very challenging. This is because such an IDS would require to learn a normal behavior first to detect abnormal or malicious behavior. The learning phase assumes that there is no noise or attack traffic during this period which cannot be guaranteed. Such an IDS may generate false alarms if these issues are not addressed.
- As also described in this paper, most of the anomaly-based NIDS tries to construct a model that captures the profile of all possible behavior or patterns of normal traffic. This, however, is extremely challenging because it has been proven that such models tend to bias towards the dominated class, that is, normal class, resulting in high false-positive rates. Furthermore, it is also not possible to capture all possible normal observations that may be generated in a network, particularly in a heterogeneous environment of IoT networks, which increases false-negative rates. Completely avoiding or minimizing false-positive rates and false-negative rates in NIDS is another research challenge.
- It would be interesting to develop models trained on specific types of devices. These models can be applied to IDSs in other organizations using a similar type of device. This will assist other organizations, which can deploy these models and thus save time that would have been required to collect the data and train the IDSs. It will also help in detecting malicious IoT devices, which are already compromised because their behavior would be different from normal behavior captured by trained models. Developing such models is a challenging task and a potential area for future research.
- Different stages involved in the design and implementation of NIDS, like data-preprocessing and feature reduction, model training and deployment, in particular, ML and DL based NIDS, increase computational complexity. Thus designing an efficient NIDS that is light on computational requirements is another challenge and area for future research.
- Feature selection and dimensionality reduction methods used for proposed IDSs are suitable to work on a specific type of normal traffic and to detect a particular type of attacks which may not work once the environment of normal or attack sequences change a bit, especially under a fast-changing environment of IoT devices and networks. Thus, dynamic and computationally efficient mechanism for feature selection which can work under all types of normal and attack traffic is a potential research challenge.
- DL and ML-based techniques and algorithms are being widely used for training a model on a large dataset. This has facilitated in effective handling of cyber-attacks. However, with regards to the use of DL and ML algorithms for attack detection in IoT networks, some challenges need the attention of researchers; for example, resource constraints issue with IoT devices limits the use of DL/ML algorithms [163] for protection of IoT networks. Another challenge with the use of ML/DL techniques in large and distributed networks, like that of IoT networks, is that they face scalability issues, for example in terms of various scenarios and choices of IDS deployment. One possible solution to limitations of individual DL or ML algorithms suggested by some of the authors [211] is the use of an ensemble of ML/DL algorithms that performed better in comparison to an individual ML algorithm; however, such algorithms were computationally expensive and thus resulted in network latency issues, which cannot be afforded in critical systems involving risks to human lives, like health and autonomous or internet of vehicles (IoVs) systems.
- The techniques of semi-supervised learning, transfer learning and reinforcement learning (RL) are still not well explored and experimented for designing an IDS for IoT security in order to achieve important objectives like real-time, fast training and unified models for anomaly detection in IoT and thus are potential areas of future research. Moreover, it would be an interesting research area to use RL in combination with DL because their combined use can be beneficial in IoT network scenarios involving large data dimensionality and non-stationary environments.
10. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ray, S.; Jin, Y.; Raychowdhury, A. The changing computing paradigm with internet of things: A tutorial introduction. IEEE Des. Test 2016, 33, 76–96. [Google Scholar] [CrossRef]
- Diechmann, J.; Heineke, K.; Reinbacher, T.; Wee, D. The Internet of Things: How to Capture the Value of IoT. Technical Report, Technical Report May. 2018, pp. 1–124. Available online: https://www.mckinsey.com/featured-insights/internet-of-things/our-insights/the-internet-of-things-how-to-capture-the-value-of-iot# (accessed on 13 July 2020).
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future internet: The internet of things architecture, possible applications and key challenges. In Proceedings of the 2012 10th International Conference on Frontiers of Information Technology, Islamabad, India, 17–19 December 2012; pp. 257–260. [Google Scholar]
- Yang, Z.; Yue, Y.; Yang, Y.; Peng, Y.; Wang, X.; Liu, W. Study and application on the architecture and key technologies for IoT. In Proceedings of the 2011 International Conference on Multimedia Technology, Hangzhou, China, 26–28 July 2011; pp. 747–751. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Torkaman, A.; Seyyedi, M. Analyzing IoT reference architecture models. Int. J. Comput. Sci. Softw. Eng. 2016, 5, 154. [Google Scholar]
- Chaqfeh, M.A.; Mohamed, N. Challenges in middleware solutions for the internet of things. In Proceedings of the 2012 International Conference on Collaboration Technologies And Systems (CTS), Denver, CO, USA, 21–25 May 2012; pp. 21–26. [Google Scholar]
- Moustafa, N.; Creech, G.; Sitnikova, E.; Keshk, M. Collaborative anomaly detection framework for handling big data of cloud computing. In Proceedings of the 2017 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 14–16 November 2017; pp. 1–6. [Google Scholar]
- Moustafa, N.; Choo, K.K.R.; Radwan, I.; Camtepe, S. Outlier Dirichlet mixture mechanism: Adversarial statistical learning for anomaly detection in the fog. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1975–1987. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.; Du, X.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. arXiv 2018, arXiv:1807.11023. [Google Scholar] [CrossRef]
- Kolias, C.; Stavrou, A.; Voas, J.; Bojanova, I.; Kuhn, R. Learning internet-of-things security “hands-on”. IEEE Secur. Priv. 2016, 14, 37–46. [Google Scholar] [CrossRef]
- Marsden, T.; Moustafa, N.; Sitnikova, E.; Creech, G. Probability risk identification based intrusion detection system for SCADA systems. In International Conference on Mobile Networks and Management; Springer: Berlin, Germany, 2017; pp. 353–363. [Google Scholar]
- Moustafa, N.; Misra, G.; Slay, J. Generalized outlier gaussian mixture technique based on automated association features for simulating and detecting web application attacks. IEEE Trans. Sustain. Comput. 2018. [Google Scholar] [CrossRef]
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, H.; Patel, A.; Rajarajan, M. A survey of intrusion detection techniques in cloud. J. Netw. Comput. Appl. 2013, 36, 42–57. [Google Scholar] [CrossRef]
- Rizwan, R.; Khan, F.A.; Abbas, H.; Chauhdary, S.H. Anomaly detection in wireless sensor networks using immune-based bioinspired mechanism. Int. J. Distrib. Sens. Netw. 2015, 11, 684952. [Google Scholar] [CrossRef]
- Moustafa, N.; Creech, G.; Slay, J. Anomaly detection system using beta mixture models and outlier detection. In Progress in Computing, Analytics and Networking; Springer: Berlin, Germany, 2018; pp. 125–135. [Google Scholar]
- Butun, I.; Morgera, S.D.; Sankar, R. A survey of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2013, 16, 266–282. [Google Scholar] [CrossRef]
- Mitchell, R.; Chen, I.R. A survey of intrusion detection techniques for cyber-physical systems. ACM Comput. Surv. (CSUR) 2014, 46, 55. [Google Scholar] [CrossRef]
- Mishra, A.; Nadkarni, K.; Patcha, A. Intrusion detection in wireless ad hoc networks. IEEE Wirel. Commun. 2004, 11, 48–60. [Google Scholar] [CrossRef]
- Anantvalee, T.; Wu, J. A survey on intrusion detection in mobile ad hoc networks. In Wireless Network Security; Springer: Berlin, Germany, 2007; pp. 159–180. [Google Scholar]
- Kumar, S.; Dutta, K. Intrusion detection in mobile ad hoc networks: Techniques, systems, and future challenges. Secur. Commun. Netw. 2016, 9, 2484–2556. [Google Scholar] [CrossRef]
- Sfar, A.R.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Keshk, M.; Moustafa, N.; Sitnikova, E.; Creech, G. Privacy preservation intrusion detection technique for SCADA systems. In Proceedings of the 2017 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 14–16 November 2017; pp. 1–6. [Google Scholar]
- Zhao, K.; Ge, L. A survey on the internet of things security. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Leshan, China, 14–15 December 2013; pp. 663–667. [Google Scholar]
- Kumar, J.S.; Patel, D.R. A survey on internet of things: Security and privacy issues. Int. J. Comput. Appl. 2014, 90. [Google Scholar] [CrossRef]
- Suo, H.; Wan, J.; Zou, C.; Liu, J. Security in the internet of things: A review. In Proceedings of the 2012 International Conference on Computer Science and Electronics Engineering, Hangzhou, China, 23–25 March 2012; Volume 3, pp. 648–651. [Google Scholar]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Benkhelifa, E.; Welsh, T.; Hamouda, W. A critical review of practices and challenges in intrusion detection systems for IoT: Toward universal and resilient systems. IEEE Commun. Surv. Tutor. 2018, 20, 3496–3509. [Google Scholar] [CrossRef]
- Abduvaliyev, A.; Pathan, A.S.K.; Zhou, J.; Roman, R.; Wong, W.C. On the vital areas of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2013, 15, 1223–1237. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Zarpelao, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT security techniques based on machine learning. arXiv 2018, arXiv:1801.06275. [Google Scholar]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Mishra, P.; Varadharajan, V.; Tupakula, U.; Pilli, E.S. A detailed investigation and analysis of using machine learning techniques for intrusion detection. IEEE Commun. Surv. Tutor. 2018, 21, 686–728. [Google Scholar] [CrossRef]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network Intrusion Detection for IoT Security based on Learning Techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. Security analysis of network anomalies mitigation schemes in IoT networks. IEEE Access 2020, 8, 43355–43374. [Google Scholar] [CrossRef]
- Garg, S.; Kaur, K.; Batra, S.; Kaddoum, G.; Kumar, N.; Boukerche, A. A multi-stage anomaly detection scheme for augmenting the security in IoT-enabled applications. Future Gener. Comput. Syst. 2020, 104, 105–118. [Google Scholar] [CrossRef]
- Garg, S.; Kaur, K.; Kumar, N.; Kaddoum, G.; Zomaya, A.Y.; Ranjan, R. A hybrid deep learning-based model for anomaly detection in cloud datacenter networks. IEEE Trans. Netw. Serv. Manag. 2019, 16, 924–935. [Google Scholar] [CrossRef]
- Mirsky, Y.; Doitshman, T.; Elovici, Y.; Shabtai, A. Kitsune: An ensemble of autoencoders for online network intrusion detection. arXiv 2018, arXiv:1802.09089. [Google Scholar]
- Sethi, P.; Sarangi, S.R. Internet of things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017. [Google Scholar] [CrossRef]
- Wu, M.; Lu, T.J.; Ling, F.Y.; Sun, J.; Du, H.Y. Research on the architecture of Internet of Things. In Proceedings of the 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), Chengdu, China, 20–22 August 2010; Volume 5. [Google Scholar]
- Tan, L.; Wang, N. Future internet: The internet of things. In Proceedings of the 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), Chengdu, China, 20–22 August 2010; Volume 5. [Google Scholar]
- ITU, T. Telecommunication Standardization Sector of ITU. Annex C RTP Payload Format H 1993, 261, 108–113. [Google Scholar]
- Weyrich, M.; Ebert, C. Reference architectures for the internet of things. IEEE Softw. 2015, 33, 112–116. [Google Scholar] [CrossRef]
- Fremantle, P. A Reference Architecture for the Internet of Things. WSO2 White Paper. 2015. Available online: https://docs.huihoo.com/wso2/wso2-whitepaper-a-reference-architecture-for-the-internet-of-things.pdf (accessed on 13 July 2020).
- Green, J. The Internet of Things Reference Model; Internet of Things World Forum: Geneva, Switzerland, 2014; pp. 1–12. [Google Scholar]
- Notra, S.; Siddiqi, M.; Gharakheili, H.H.; Sivaraman, V.; Boreli, R. An experimental study of security and privacy risks with emerging household appliances. In Proceedings of the 2014 IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; pp. 79–84. [Google Scholar]
- Banerjee, A.; Venkatasubramanian, K.K.; Mukherjee, T.; Gupta, S.K.S. Ensuring safety, security, and sustainability of mission-critical cyber–physical systems. Proc. IEEE 2011, 100, 283–299. [Google Scholar] [CrossRef]
- AlTawy, R.; Youssef, A.M. Security tradeoffs in cyber physical systems: A case study survey on implantable medical devices. IEEE Access 2016, 4, 959–979. [Google Scholar] [CrossRef]
- Wamba, S.F.; Anand, A.; Carter, L. A literature review of RFID-enabled healthcare applications and issues. Int. J. Inf. Manag. 2013, 33, 875–891. [Google Scholar] [CrossRef]
- Malasri, K.; Wang, L. Securing wireless implantable devices for healthcare: Ideas and challenges. IEEE Commun. Mag. 2009, 47, 74–80. [Google Scholar] [CrossRef]
- Keshk, M.; Sitnikova, E.; Moustafa, N.; Hu, J.; Khalil, I. An Integrated Framework for Privacy-Preserving based Anomaly Detection for Cyber-Physical Systems. IEEE Trans. Sustain. Comput. 2019. [Google Scholar] [CrossRef]
- Bertino, E.; Islam, N. Botnets and internet of things security. Computer 2017, 50, 76–79. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on internet-scale IoT exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Faruki, P.; Bharmal, A.; Laxmi, V.; Ganmoor, V.; Gaur, M.S.; Conti, M.; Rajarajan, M. Android security: A survey of issues, malware penetration, and defenses. IEEE Commun. Surv. Tutor. 2014, 17, 998–1022. [Google Scholar] [CrossRef]
- Huang, J.; Zhang, X.; Tan, L.; Wang, P.; Liang, B. Asdroid: Detecting stealthy behaviors in android applications by user interface and program behavior contradiction. In Proceedings of the 36th International Conference on Software Engineering, Hyderabad, India, 31 May–7 June 2014; pp. 1036–1046. [Google Scholar]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Bekara, C. Security issues and challenges for the IoT-based smart grid. Procedia Comput. Sci. 2014, 34, 532–537. [Google Scholar] [CrossRef]
- Steinhubl, S.R.; Muse, E.D.; Topol, E.J. The emerging field of mobile health. Sci. Transl. Med. 2015, 7, 283rv3. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.E.; Kim, B.G.; Gupta, B. Secure integration of IoT and cloud computing. Future Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Lee, K.; Murray, D.; Hughes, D.; Joosen, W. Extending sensor networks into the cloud using amazon web services. In Proceedings of the 2010 IEEE International Conference on Networked Embedded Systems for Enterprise Applications, Suzhou, China, 25–26 November 2010; pp. 1–7. [Google Scholar]
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. Integration of cloud computing and internet of things: A survey. Future Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Bhattasali, T.; Chaki, R.; Chaki, N. Secure and trusted cloud of things. In Proceedings of the 2013 Annual IEEE India Conference (INDICON), Mumbai, India, 13–15 December 2013; pp. 1–6. [Google Scholar]
- Subashini, S.; Kavitha, V. A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 2011, 34, 1–11. [Google Scholar] [CrossRef]
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The effect of IoT new features on security and privacy: New threats, existing solutions, and challenges yet to be solved. IEEE Internet Things J. 2018, 6, 1606–1616. [Google Scholar] [CrossRef]
- Ronen, E.; Shamir, A.; Weingarten, A.O.; O’Flynn, C. IoT goes nuclear: Creating a ZigBee chain reaction. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2017; pp. 195–212. [Google Scholar]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A link layer security architecture for wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 162–175. [Google Scholar]
- Garg, S.; Kaur, K.; Kaddoum, G.; Ahmed, S.H.; Jayakody, D.N.K. SDN-based secure and privacy-preserving scheme for vehicular networks: A 5G perspective. IEEE Trans. Veh. Technol. 2019, 68, 8421–8434. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context aware computing for the internet of things: A survey. IEEE Commun. Surv. Tutor. 2013, 16, 414–454. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A survey on sensor networks. IEEE Commun. Mag. 2002, 40, 102–114. [Google Scholar] [CrossRef]
- Abdul-Ghani, H.A.; Konstantas, D.; Mahyoub, M. A comprehensive IoT attacks survey based on a building-blocked reference model. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 355–373. [Google Scholar]
- Khattab, A.; Jeddi, Z.; Amini, E.; Bayoumi, M. RFID Security: A Lightweight Paradigm; Springer: Berlin, Germany, 2016. [Google Scholar]
- Fan, X.; Susan, F.; Long, W.; Li, S. Security Analysis of Zigbee. 2017. Available online: https://courses.csail.mit.edu/6.857/2017/project/17.pdf (accessed on 13 July 2020).
- Lee, K.; Lee, J.; Zhang, B.; Kim, J.; Shin, Y. An enhanced Trust Center based authentication in ZigBee networks. In International Conference on Information Security and Assurance; Springer: Berlin, Germany, 2009; pp. 471–484. [Google Scholar]
- Dini, G.; Tiloca, M. Considerations on security in zigbee networks. In Proceedings of the 2010 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Newport Beach, CA, USA, 7–9 June 2010; pp. 58–65. [Google Scholar]
- Vidgren, N.; Haataja, K.; Patino-Andres, J.L.; Ramirez-Sanchis, J.J.; Toivanen, P. Security threats in ZigBee-enabled systems: Vulnerability evaluation, practical experiments, countermeasures, and lessons learned. In Proceedings of the 2013 46th Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2013; pp. 5132–5138. [Google Scholar]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Gritzalis, S. Intrusion detection in 802.11 networks: Empirical evaluation of threats and a public dataset. IEEE Commun. Surv. Tutor. 2015, 18, 184–208. [Google Scholar] [CrossRef]
- IEEE Computer Society LAN/MAN Standards Committee. IEEE Standard for Information Technology- Telecommunication and Information Exchange between Systems-Local and Metropolitan Area Networks-Specific Requirements Part11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment1: Radio Resource Measurement of Wireless LANs. 2009. Available online: http://standards.ieee.org/getieee802/download/802.11n-2009.pdf (accessed on 13 July 2020).
- Bicakci, K.; Tavli, B. Denial-of-Service attacks and countermeasures in IEEE 802.11 wireless networks. Comput. Stand. Interfaces 2009, 31, 931–941. [Google Scholar] [CrossRef]
- Cope, P.; Campbell, J.; Hayajneh, T. An investigation of Bluetooth security vulnerabilities. In Proceedings of the 2017 IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 9–11 January 2017; pp. 1–7. [Google Scholar]
- Lonzetta, A.M.; Cope, P.; Campbell, J.; Mohd, B.J.; Hayajneh, T. Security vulnerabilities in Bluetooth technology as used in IoT. J. Sens. Actuator Netw. 2018, 7, 28. [Google Scholar] [CrossRef]
- Hassan, S.S.; Bibon, S.D.; Hossain, M.S.; Atiquzzaman, M. Security threats in Bluetooth technology. Comput. Secur. 2018, 74, 308–322. [Google Scholar] [CrossRef]
- Liu, Y.; Cheng, C.; Gu, T.; Jiang, T.; Li, X. A lightweight authenticated communication scheme for smart grid. IEEE Sens. J. 2015, 16, 836–842. [Google Scholar] [CrossRef]
- Singh, M.M.; Adzman, K.A.A.K.; Hassan, R. Near Field Communication (NFC) Technology Security Vulnerabilities and Countermeasures. Int. J. Eng. Technol. 2018, 7, 298–305. [Google Scholar]
- Roland, M.; Langer, J.; Scharinger, J. Security vulnerabilities of the NDEF signature record type. In Proceedings of the 2011 Third International Workshop on Near Field Communication, Hagenberg, Austria, 22 February 2011; pp. 65–70. [Google Scholar]
- Amin, Y.M.; Abdel-Hamid, A.T. A comprehensive taxonomy and analysis of IEEE 802.15. 4 attacks. J. Electr. Comput. Eng. 2016, 2016, 4. [Google Scholar]
- Amin, Y.M.; Abdel-Hamid, A.T. Classification and analysis of IEEE 802.15. 4 PHY layer attacks. In Proceedings of the 2016 International Conference on Selected Topics in Mobile & Wireless Networking (MoWNeT), Cairo, Egypt, 11–13 April 2016; pp. 1–8. [Google Scholar]
- Amin, Y.M.; Abdel-Hamid, A.T. Classification and analysis of IEEE 80215. 4 MAC layer attacks. In Proceedings of the 2015 11th International Conference on Innovations in Information Technology (IIT), Dubai, UAE, 1–3 November 2015; pp. 74–79. [Google Scholar]
- Mayzaud, A.; Badonnel, R.; Chrisment, I. A Taxonomy of Attacks in RPL-based Internet of Things. Int. J. Netw. Secur. 2016, 18, 459–473. [Google Scholar]
- Cao, Z.; Hu, J.; Chen, Z.; Xu, M.; Zhou, X. Feedback: Towards dynamic behavior and secure routing forwireless sensor networks. In Proceedings of the 20th International Conference on Advanced Information Networking and Applications (AINA’06), Vienna, Austria, 18–20 April 2006; Volume 2, pp. 160–164. [Google Scholar]
- Sen, J. Security in wireless sensor networks. Wirel. Sens. Netw. Curr. Status Future Trends 2012, 407, 53–57. [Google Scholar]
- Hummen, R.; Hiller, J.; Wirtz, H.; Henze, M.; Shafagh, H.; Wehrle, K. 6LoWPAN fragmentation attacks and mitigation mechanisms. In Proceedings of the Sixth ACM Conference on Security and Privacy in Wireless and Mobile Networks, Budapest, Hungary, 17–19 April 2013; pp. 55–66. [Google Scholar]
- Vacca, J.R. Computer and Information Security Handbook; Steve Elliot: Sydney, Australia, 2012. [Google Scholar]
- Keshk, M.; Turnbull, B.; Moustafa, N.; Vatsalan, D.; Choo, K.K.R. A Privacy-Preserving Framework based Blockchain and Deep Learning for Protecting Smart Power Networks. IEEE Trans. Ind. Inf. 2020, 16, 5110–5118. [Google Scholar] [CrossRef]
- Liu, C.; Yang, J.; Chen, R.; Zhang, Y.; Zeng, J. Research on immunity-based intrusion detection technology for the internet of things. In Proceedings of the 2011 Seventh International Conference on Natural Computation, Shanghai, China, 26–28 July 2011; Volume 1, pp. 212–216. [Google Scholar]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar]
- Kasinathan, P.; Costamagna, G.; Khaleel, H.; Pastrone, C.; Spirito, M.A. An IDS framework for internet of things empowered by 6LoWPAN. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 1337–1340. [Google Scholar]
- Oh, D.; Kim, D.; Ro, W. A malicious pattern detection engine for embedded security systems in the Internet of Things. Sensors 2014, 14, 24188–24211. [Google Scholar] [CrossRef]
- Keshk, M.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Privacy-preserving big data analytics for cyber-physical systems. Wireless Netw. 2018, 2018, 1–9. [Google Scholar] [CrossRef]
- Debar, H. An introduction to intrusion-detection systems. Proc. Connect 2000, 2000. [Google Scholar]
- Scarfone, K.; Mell, P. Guide to Intrusion Detection and Prevention Systems (Idps); Technical Report; National Institute of Standards and Technology: Gaithersburg, MA, USA, 2012. [Google Scholar]
- Amaral, J.P.; Oliveira, L.M.; Rodrigues, J.J.; Han, G.; Shu, L. Policy and network-based intrusion detection system for IPv6-enabled wireless sensor networks. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 1796–1801. [Google Scholar]
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time intrusion detection in the Internet of Things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- D’Agostini, G. A multidimensional unfolding method based on Bayes’ theorem. Nucl. Instrum. Methods Phys. Res. Sect. A Accel. Spectrometers Detect. Assoc. Equip. 1995, 362, 487–498. [Google Scholar] [CrossRef]
- Panda, M.; Patra, M.R. Network intrusion detection using naive bayes. Int. J. Comput. Sci. Netw. Secur. 2007, 7, 258–263. [Google Scholar]
- Mukherjee, S.; Sharma, N. Intrusion detection using naive Bayes classifier with feature reduction. Procedia Technol. 2012, 4, 119–128. [Google Scholar] [CrossRef]
- Agrawal, S.; Agrawal, J. Survey on anomaly detection using data mining techniques. Procedia Comput. Sci. 2015, 60, 708–713. [Google Scholar] [CrossRef]
- Swarnkar, M.; Hubballi, N. OCPAD: One class Naive Bayes classifier for payload based anomaly detection. Expert Syst. Appl. 2016, 64, 330–339. [Google Scholar] [CrossRef]
- Box, G.E.; Tiao, G.C. Bayesian Inference in Statistical Analysis; John Wiley & Sons: Hoboken, NJ, USA, 2011; Volume 40. [Google Scholar]
- Ng, A.Y.; Jordan, M.I. On discriminative vs. generative classifiers: A comparison of logistic regression and naive bayes. In Advances in Neural Information Processing Systems; 2002; pp. 841–848. Available online: https://ai.stanford.edu/~ang/papers/nips01-discriminativegenerative.pdf (accessed on 13 July 2020).
- Soucy, P.; Mineau, G.W. A simple KNN algorithm for text categorization. In Proceedings of the 2001 IEEE International Conference on Data Mining, San Jose, CA, USA, 29 November–2 December 2001; pp. 647–648. [Google Scholar]
- Deng, Z.; Zhu, X.; Cheng, D.; Zong, M.; Zhang, S. Efficient kNN classification algorithm for big data. Neurocomputing 2016, 195, 143–148. [Google Scholar] [CrossRef]
- Adetunmbi, A.O.; Falaki, S.O.; Adewale, O.S.; Alese, B.K. Network intrusion detection based on rough set and k-nearest neighbour. Int. J. Comput. ICT Res. 2008, 2, 60–66. [Google Scholar]
- Li, L.; Zhang, H.; Peng, H.; Yang, Y. Nearest neighbors based density peaks approach to intrusion detection. Chaos Solitons Fractals 2018, 110, 33–40. [Google Scholar] [CrossRef]
- Su, M.Y. Real-time anomaly detection systems for Denial-of-Service attacks by weighted k-nearest-neighbor classifiers. Expert Syst. Appl. 2011, 38, 3492–3498. [Google Scholar] [CrossRef]
- Pajouh, H.H.; Javidan, R.; Khayami, R.; Ali, D.; Choo, K.K.R. A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Trans. Emerg. Top. Comput. 2016. [Google Scholar] [CrossRef]
- Li, W.; Yi, P.; Wu, Y.; Pan, L.; Li, J. A new intrusion detection system based on KNN classification algorithm in wireless sensor network. J. Electr. Comput. Eng. 2014, 2014. [Google Scholar] [CrossRef]
- Kotsiantis, S.B.; Zaharakis, I.; Pintelas, P. Supervised machine learning: A review of classification techniques. Emerg. Artif. Intell. Appl. Comput. Eng. 2007, 160, 3–24. [Google Scholar]
- Du, W.; Zhan, Z. Building decision tree classifier on private data. In Proceedings of the IEEE International Conference on Privacy, Security and Data Mining; Australian Computer Society, Inc.: Sydney, Australia, 2002; Volume 14, pp. 1–8. [Google Scholar]
- Quinlan, J.R. Induction of decision trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef]
- Kotsiantis, S.B. Decision trees: A recent overview. Artif. Intell. Rev. 2013, 39, 261–283. [Google Scholar] [CrossRef]
- Goeschel, K. Reducing false positives in intrusion detection systems using data-mining techniques utilizing support vector machines, decision trees, and naive Bayes for off-line analysis. In Proceedings of the SoutheastCon 2016, Norfolk, VA, USA, 30 March–3 April 2016; pp. 1–6. [Google Scholar]
- Kim, G.; Lee, S.; Kim, S. A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst. Appl. 2014, 41, 1690–1700. [Google Scholar] [CrossRef]
- Alharbi, S.; Rodriguez, P.; Maharaja, R.; Iyer, P.; Subaschandrabose, N.; Ye, Z. Secure the internet of things with challenge response authentication in fog computing. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–2. [Google Scholar]
- Tong, S.; Koller, D. Support vector machine active learning with applications to text classification. J. Mach. Learn. Res. 2001, 2, 45–66. [Google Scholar]
- Vapnik, V. The Nature of Statistical Learning Theory; Springer Science & Business Media: Berlin, Germany, 2013. [Google Scholar]
- Miranda, C.; Kaddoum, G.; Bou-Harb, E.; Garg, S.; Kaur, K. A collaborative security framework for software-defined wireless sensor networks. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2602–2615. [Google Scholar] [CrossRef]
- Liu, Y.; Pi, D. A novel kernel svm algorithm with game theory for network intrusion detection. KSII Trans. Internet Inf. Syst. 2017, 11. [Google Scholar] [CrossRef]
- Hu, W.; Liao, Y.; Vemuri, V.R. Robust Support Vector Machines for Anomaly Detection in Computer Security. ICMLA. 2003, pp. 168–174. Available online: https://web.cs.ucdavis.edu/~vemuri/papers/rvsm.pdf (accessed on 13 July 2020).
- Wagner, C.; François, J.; Engel, T. Machine learning approach for ip-flow record anomaly detection. In International Conference on Research in Networking; Springer: Berlin, Germany, 2011; pp. 28–39. [Google Scholar]
- Garg, S.; Kaur, K.; Kaddoum, G.; Gagnon, F.; Kumar, N.; Han, Z. Sec-IoV: A multi-stage anomaly detection scheme for internet of vehicles. In Proceedings of the ACM MobiHoc Workshop on Pervasive Systems in the IoT Era, Catania, Italy, 2 July 2019; pp. 37–42. [Google Scholar]
- Torres, J.M.; Comesaña, C.I.; García-Nieto, P.J. Machine learning techniques applied to cybersecurity. Int. J. Mach. Learn. Cybern. 2019, 10, 2823–2836. [Google Scholar] [CrossRef]
- Ioannou, C.; Vassiliou, V. Classifying Security Attacks in IoT Networks Using Supervised Learning. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini, Greece, 29–31 May 2019; pp. 652–658. [Google Scholar]
- Lin, K.C.; Chen, S.Y.; Hung, J.C. Botnet detection using support vector machines with artificial fish swarm algorithm. J. Appl. Math. 2014, 2014. [Google Scholar] [CrossRef]
- Woźniak, M.; Graña, M.; Corchado, E. A survey of multiple classifier systems as hybrid systems. Inf. Fusion 2014, 16, 3–17. [Google Scholar] [CrossRef]
- Illy, P.; Kaddoum, G.; Moreira, C.M.; Kaur, K.; Garg, S. Securing fog-to-things environment using intrusion detection system based on ensemble learning. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–7. [Google Scholar]
- Domingos, P.M. A few useful things to know about machine learning. Commun. ACM 2012, 55, 78–87. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, D.; Luo, Y.; Wang, D. Adaptive Dynamic Programming for Control: Algorithms And Stability; Springer Science & Business Media: Berlin, Germany, 2012. [Google Scholar]
- Baba, N.M.; Makhtar, M.; Fadzli, S.A.; Awang, M.K. Current Issues in Ensemble Methods and Its Applications. J. Theor. Appl. Inf. Technol. 2015, 81, 266. [Google Scholar]
- Santana, L.E.; Silva, L.; Canuto, A.M.; Pintro, F.; Vale, K.O. A comparative analysis of genetic algorithm and ant colony optimization to select attributes for an heterogeneous ensemble of classifiers. In Proceedings of the IEEE Congress on Evolutionary Computation, Barcelona, Spain, 18–23 July 2010; pp. 1–8. [Google Scholar]
- Aburomman, A.A.; Reaz, M.B.I. A novel SVM-kNN-PSO ensemble method for intrusion detection system. Appl. Soft Comput. 2016, 38, 360–372. [Google Scholar] [CrossRef]
- Gaikwad, D.; Thool, R.C. Intrusion detection system using bagging ensemble method of machine learning. In Proceedings of the 2015 International Conference on Computing Communication Control and Automation, Pune, India, 26–27 February 2015; pp. 291–295. [Google Scholar]
- Reddy, R.R.; Ramadevi, Y.; Sunitha, K. Enhanced anomaly detection using ensemble support vector machine. In Proceedings of the 2017 International Conference on Big Data Analytics and Computational Intelligence (ICBDAC), Chirala, India, 23–25 March 2017; pp. 107–111. [Google Scholar]
- Bosman, H.H.; Iacca, G.; Tejada, A.; Wörtche, H.J.; Liotta, A. Ensembles of incremental learners to detect anomalies in ad hoc sensor networks. Ad Hoc Netw. 2015, 35, 14–36. [Google Scholar] [CrossRef]
- Breiman, L. Random forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Cutler, D.R.; Edwards, T.C., Jr.; Beard, K.H.; Cutler, A.; Hess, K.T.; Gibson, J.; Lawler, J.J. Random forests for classification in ecology. Ecology 2007, 88, 2783–2792. [Google Scholar] [CrossRef] [PubMed]
- Chang, Y.; Li, W.; Yang, Z. Network intrusion detection based on random forest and support vector machine. In Proceedings of the 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), Guangzhou, China, 21–24 July 2017; Volume 1, pp. 635–638. [Google Scholar]
- Zhang, J.; Zulkernine, M. A hybrid network intrusion detection technique using random forests. In Proceedings of the First International Conference on Availability, Reliability and Security (ARES’06), Vienna, Austria, 20–22 April 2006; p. 8. [Google Scholar]
- Doshi, R.; Apthorpe, N.; Feamster, N. Machine learning ddos detection for consumer internet of things devices. In Proceedings of the 2018 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 24 May 2018; pp. 29–35. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Shabtai, A.; Ochoa, M.; Tippenhauer, N.O.; Guarnizo, J.D.; Elovici, Y. Detection of unauthorized IoT devices using machine learning techniques. arXiv 2017, arXiv:1709.04647. [Google Scholar]
- Jain, A.K. Data clustering: 50 years beyond K-means. Pattern Recognit. Lett. 2010, 31, 651–666. [Google Scholar] [CrossRef]
- Hartigan, J.A.; Wong, M.A. Algorithm AS 136: A k-means clustering algorithm. J. R. Stat. Society. Ser. C Appl. Stat. 1979, 28, 100–108. [Google Scholar] [CrossRef]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Network anomaly detection: Methods, systems and tools. IEEE Commun. Surv. Tutor. 2013, 16, 303–336. [Google Scholar] [CrossRef]
- Kanjanawattana, S. A Novel Outlier Detection Applied to an Adaptive K-Means. Int. J. Mach. Learn. Comput. 2019, 9. [Google Scholar] [CrossRef]
- Muniyandi, A.P.; Rajeswari, R.; Rajaram, R. Network anomaly detection by cascading k-Means clustering and C4. 5 decision tree algorithm. Procedia Eng. 2012, 30, 174–182. [Google Scholar] [CrossRef]
- Zhao, S.; Li, W.; Zia, T.; Zomaya, A.Y. A dimension reduction model and classifier for anomaly-based intrusion detection in internet of things. In Proceedings of the 2017 IEEE 15th International Conference on Dependable, Autonomic and Secure Computing, 15th International Conference on Pervasive Intelligence and Computing, 3rd International Conference on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; pp. 836–843. [Google Scholar]
- Hoang, D.H.; Nguyen, H.D. Detecting Anomalous Network Traffic in IoT Networks. In Proceedings of the 2019 21st International Conference on Advanced Communication Technology (ICACT), Pyeong Chang, Korea, 17–20 February 2019; pp. 1143–1152. [Google Scholar]
- Hoang, D.H.; Nguyen, H.D. A PCA-based method for IoT network traffic anomaly detection. In Proceedings of the 2018 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon-si, Korea, 11–14 February 2018; pp. 381–386. [Google Scholar]
- Zhang, B.; Liu, Z.; Jia, Y.; Ren, J.; Zhao, X. Network intrusion detection method based on PCA and Bayes algorithm. Secur. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef]
- Moustafa, N.; Turnbull, B.; Choo, K.K.R. An ensemble intrusion detection technique based on proposed statistical flow features for protecting network traffic of internet of things. IEEE Internet Things J. 2018, 6, 4815–4830. [Google Scholar] [CrossRef]
- Ahmad, A.; Dey, L. A k-mean clustering algorithm for mixed numeric and categorical data. Data Knowl. Eng. 2007, 63, 503–527. [Google Scholar] [CrossRef]
- Nweke, H.F.; Teh, Y.W.; Al-Garadi, M.A.; Alo, U.R. Deep learning algorithms for human activity recognition using mobile and wearable sensor networks: State of the art and research challenges. Expert Syst. Appl. 2018, 105, 233–261. [Google Scholar] [CrossRef]
- De Coninck, E.; Verbelen, T.; Vankeirsbilck, B.; Bohez, S.; Simoens, P.; Demeester, P.; Dhoedt, B. Distributed neural networks for Internet of Things: The Big-Little approach. In International Internet of Things Summit; Springer: Berlin, Germany, 2015; pp. 484–492. [Google Scholar]
- Yousefi-Azar, M.; Varadharajan, V.; Hamey, L.; Tupakula, U. Autoencoder-based feature learning for cyber security applications. In Proceedings of the 2017 International Joint Conference on Neural Networks (IJCNN), Anchorage, AK, USA, 14–19 May 2017; pp. 3854–3861. [Google Scholar]
- Hinton, G.E. A practical guide to training restricted Boltzmann machines. In Neural Networks: Tricks of the Trade; Springer: Berlin, Germany, 2012; pp. 599–619. [Google Scholar]
- Hiromoto, R.E.; Haney, M.; Vakanski, A. A secure architecture for IoT with supply chain risk management. In Proceedings of the 2017 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Bucharest, Romania, 21–23 September 2017; Volume 1, pp. 431–435. [Google Scholar]
- Zhang, Q.; Yang, L.T.; Chen, Z.; Li, P. A survey on deep learning for big data. Inf. Fusion 2018, 42, 146–157. [Google Scholar] [CrossRef]
- Li, H.; Ota, K.; Dong, M. Learning IoT in edge: Deep learning for the Internet of Things with edge computing. IEEE Netw. 2018, 32, 96–101. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Tang, F.; Mao, B.; Kato, N.; Akashi, O.; Inoue, T.; Mizutani, K. State-of-the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent network traffic control systems. IEEE Commun. Surv. Tutor. 2017, 19, 2432–2455. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef]
- Hermans, M.; Schrauwen, B. Training and analysing deep recurrent neural networks. Adv. Neural Inf. Process. Syst. 2013, 26, 190–198. [Google Scholar]
- Pascanu, R.; Gulcehre, C.; Cho, K.; Bengio, Y. How to construct deep recurrent neural networks. arXiv 2013, arXiv:1312.6026. [Google Scholar]
- Torres, P.; Catania, C.; Garcia, S.; Garino, C.G. An analysis of recurrent neural networks for botnet detection behavior. In Proceedings of the 2016 IEEE biennial congress of Argentina (ARGENCON), Buenos Aires, Argentina, 15–17 June 2016; pp. 1–6. [Google Scholar]
- Almiani, M.; AbuGhazleh, A.; Al-Rahayfeh, A.; Atiewi, S.; Razaque, A. Deep recurrent neural network for IoT intrusion detection system. Simul. Model. Pract. Theory 2019, 101, 102031. [Google Scholar] [CrossRef]
- Guo, T.; Xu, Z.; Yao, X.; Chen, H.; Aberer, K.; Funaya, K. Robust Online Time Series Prediction with Recurrent Neural Networks. In Proceedings of the 3Rd IEEE/Acm International Conference on Data Science and Advanced Analytics, (Dsaa 2016), Montreal, QC, Canada, 17–19 October 2016; pp. 816–825. [Google Scholar]
- Qin, Y.; Song, D.; Chen, H.; Cheng, W.; Jiang, G.; Cottrell, G. A dual-stage attention-based recurrent neural network for time series prediction. arXiv 2017, arXiv:1704.02971. [Google Scholar]
- Malhotra, P.; Vig, L.; Shroff, G.; Agarwal, P. Long Short Term Memory Networks for Anomaly Detection in Time Series; Presses Universitaires de Louvain: Louvain-la-Neuve, Belgium, 2015; Volume 89, pp. 89–94. [Google Scholar]
- Shipmon, D.T.; Gurevitch, J.M.; Piselli, P.M.; Edwards, S.T. Time series anomaly detection; detection of anomalous drops with limited features and sparse examples in noisy highly periodic data. arXiv 2017, arXiv:1708.03665. [Google Scholar]
- Bontemps, L.; McDermott, J.; Le-Khac, N.A. Collective anomaly detection based on long short-term memory recurrent neural networks. In International Conference on Future Data and Security Engineering; Springer: Berlin, Germany, 2016; pp. 141–152. [Google Scholar]
- Zhu, L.; Laptev, N. Deep and confident prediction for time series at uber. In Proceedings of the 2017 IEEE International Conference on Data Mining Workshops (ICDMW), New Orleans, LA, USA, 18–21 November 2017; pp. 103–110. [Google Scholar]
- Goodfellow, I.; Bengio, Y.; Courville, A. Deep Learning; The MIT Press: Cambridge, MA, USA, 2016. [Google Scholar]
- Chen, X.W.; Lin, X. Big data deep learning: Challenges and perspectives. IEEE Access 2014, 2, 514–525. [Google Scholar] [CrossRef]
- Ciresan, D.C.; Meier, U.; Masci, J.; Gambardella, L.M.; Schmidhuber, J. Flexible, high performance convolutional neural networks for image classification. In Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence, Barcelona, Spain, 16–22 July 2011. [Google Scholar]
- Scherer, D.; Müller, A.; Behnke, S. Evaluation of pooling operations in convolutional architectures for object recognition. In International Conference on Artificial Neural Networks; Springer: Berlin, Germany, 2010; pp. 92–101. [Google Scholar]
- Chen, Y.; Zhang, Y.; Maharjan, S. Deep learning for secure mobile edge computing. arXiv 2017, arXiv:1709.08025. [Google Scholar]
- McLaughlin, N.; Martinez del Rincon, J.; Kang, B.; Yerima, S.; Miller, P.; Sezer, S.; Safaei, Y.; Trickel, E.; Zhao, Z.; Doupé, A.; et al. Deep android malware detection. In Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, Scottsdale, AZ, USA, 22–24 March 2017; pp. 301–308. [Google Scholar]
- Wang, W.; Zhu, M.; Zeng, X.; Ye, X.; Sheng, Y. Malware traffic classification using convolutional neural network for representation learning. In Proceedings of the 2017 International Conference on Information Networking (ICOIN), Da Nang, Vietnam, 11–13 January 2017; pp. 712–717. [Google Scholar]
- Mohammadi, M.; Al-Fuqaha, A.; Sorour, S.; Guizani, M. Deep learning for IoT big data and streaming analytics: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 2923–2960. [Google Scholar] [CrossRef]
- Mayuranathan, M.; Murugan, M.; Dhanakoti, V. Best features based intrusion detection system by RBM model for detecting DDoS in cloud environment. J. Ambient Intell. Hum. Comput. 2019, 1–11. [Google Scholar] [CrossRef]
- Fiore, U.; Palmieri, F.; Castiglione, A.; De Santis, A. Network anomaly detection with the restricted Boltzmann machine. Neurocomputing 2013, 122, 13–23. [Google Scholar] [CrossRef]
- Hinton, G.E.; Osindero, S.; Teh, Y.W. A fast learning algorithm for deep belief nets. Neural Comput. 2006, 18, 1527–1554. [Google Scholar] [CrossRef]
- Li, Y.; Ma, R.; Jiao, R. A hybrid malicious code detection method based on deep learning. Int. J. Secur. Its Appl. 2015, 9, 205–216. [Google Scholar] [CrossRef]
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative adversarial nets. Adv. Neural Inf. Process. Syst. 2014, 2, 2672–2680. [Google Scholar]
- Salimans, T.; Goodfellow, I.; Zaremba, W.; Cheung, V.; Radford, A.; Chen, X. Improved techniques for training gans. Adv. Neural Inf. Process. Syst. 2016, 2234–2242. [Google Scholar]
- Kuncheva, L.I. Combining Pattern Classifiers: Methods and Algorithms; John Wiley & Sons: Hoboken, NJ, USA, 2014. [Google Scholar]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- McHugh, J. Testing intrusion detection systems: A critique of the 1998 and 1999 darpa intrusion detection system evaluations as performed by lincoln laboratory. ACM Trans. Inf. Syst. Secur. (TISSEC) 2000, 3, 262–294. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J. The evaluation of Network Anomaly Detection Systems: Statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set. Inf. Secur. J. A Glob. Perspect. 2016, 25, 18–31. [Google Scholar] [CrossRef]
- Stolfo, S.J.; Fan, W.; Lee, W.; Prodromidis, A.; Chan, P.K. Cost-based modeling for fraud and intrusion detection: Results from the JAM project. In Proceedings of the DARPA Information Survivability Conference and Exposition, DISCEX’00, Hilton Head, SC, USA, 25–27 January 2000; Volume 2, pp. 130–144. [Google Scholar]
- Sharafaldin, I.; Gharib, A.; Lashkari, A.H.; Ghorbani, A.A. Towards a reliable intrusion detection benchmark dataset. Softw. Netw. 2018, 2018, 177–200. [Google Scholar] [CrossRef]
- Shiravi, A.; Shiravi, H.; Tavallaee, M.; Ghorbani, A.A. Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput. Secur. 2012, 31, 357–374. [Google Scholar] [CrossRef]
- Nehinbe, J.O. A simple method for improving intrusion detections in corporate networks. In International Conference on Information Security and Digital Forensics; Springer: Berlin, Germany, 2009; pp. 111–122. [Google Scholar]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Towards Generating Real-life Datasets for Network Intrusion Detection. IJ Netw. Secur. 2015, 17, 683–701. [Google Scholar]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization. In Proceedings of the 4th International Conference on Information Systems Security and Privacy, ICISSP, Funchal, Portugal, 22–24 January 2018; pp. 108–116. Available online: https://www.scitepress.org/Papers/2018/66398/66398.pdf (accessed on 13 July 2020).
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Pa, Y.M.P.; Suzuki, S.; Yoshioka, K.; Matsumoto, T.; Kasama, T.; Rossow, C. IoTPOT: Analysing the rise of IoT compromises. In Proceedings of the 9th USENIX Workshop on Offensive Technologies (WOOT 15), Washington, DC, USA, 10–11 August 2015. [Google Scholar]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT security techniques based on machine learning: How do IoT devices use AI to enhance security? IEEE Signal Process. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]














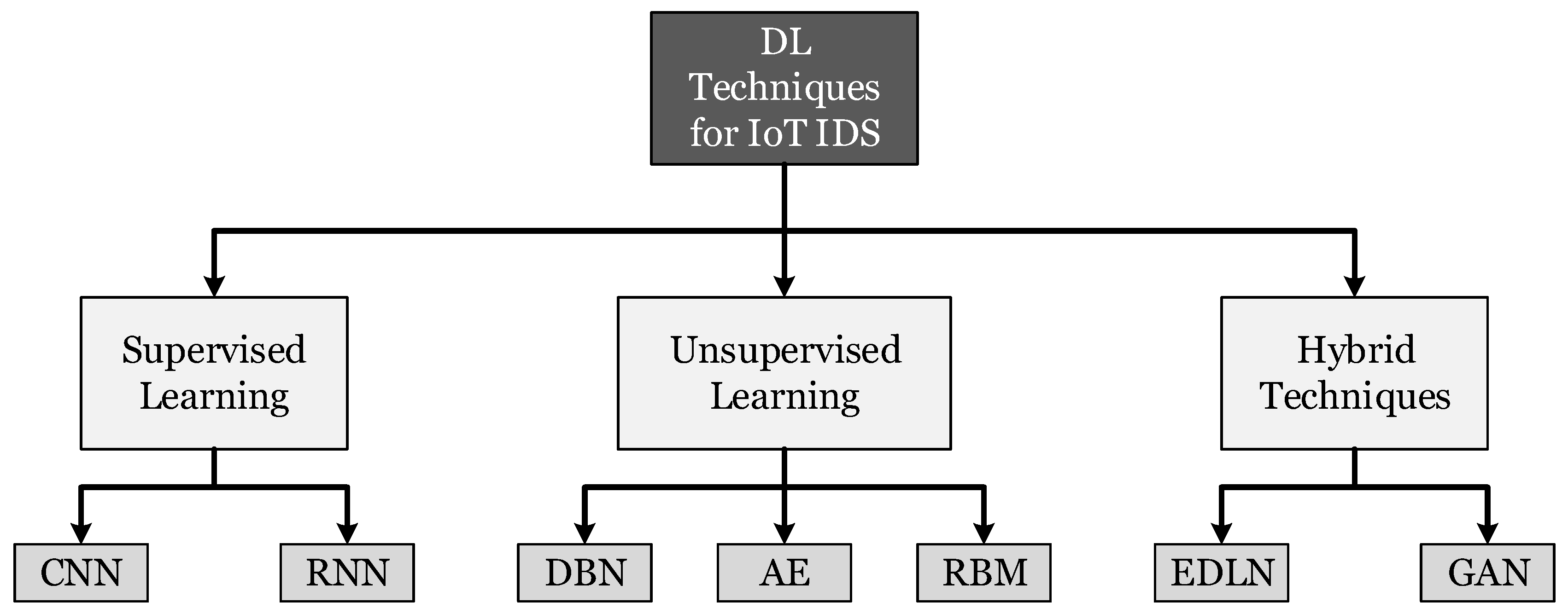


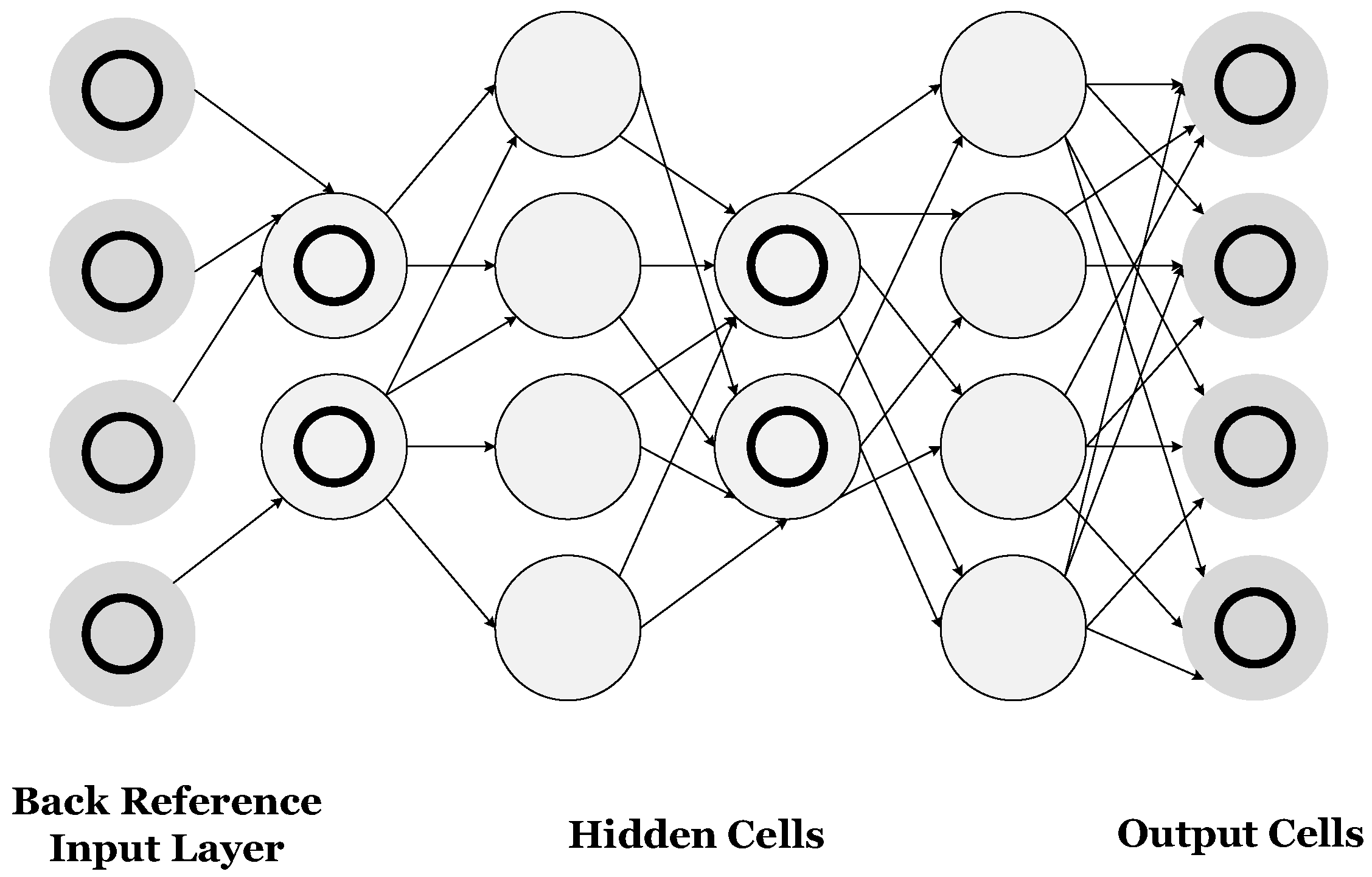

| IoT IDS Aspects | |||||||
|---|---|---|---|---|---|---|---|
| Survey Ref | IoT Architecture | IoT Protocols | IoT Threats | IoT IDS Design Choices | IoT IDS-ML Techniques | IoT IDS-DL Techniques | IoT Datasets |
| [30] | ✓ | ✓ | ✓ | ✓ | × | × | × |
| [16] | × | × | ✓ | ✓ | ✓ | × | × |
| [31] | × | × | ✓ | × | × | × | × |
| [19] | × | × | × | ✓ | × | × | × |
| [21] | × | × | ✓ | ✓ | × | × | × |
| [22] | × | × | ✓ | ✓ | × | × | × |
| [23] | × | × | ✓ | ✓ | ✓ | ✓ | × |
| [32] | × | ✓ | ✓ | × | × | × | × |
| [33] | × | ✓ | ✓ | ✓ | × | × | × |
| [34] | × | × | ✓ | × | ✓ | × | × |
| [35] | × | × | × | × | ✓ | ✓ | ✓ |
| [36] | × | × | ✓ | × | ✓ | ✓ | ✓ |
| [37] | ✓ | × | × | ✓ | ✓ | ✓ | ✓ |
| [38] | × | × | ✓ | ✓ | × | × | × |
| This Survey | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Technology | Frequency Bands | Data Rate | Physical Coverage |
|---|---|---|---|
| WiFi 802.11 | 2.5 GHz, 5 GHz | <1 Gbps | up to 50 m |
| WiFi HaLow | 900 MHz | 0.3–234 Mbps | up to 1 km |
| White-Fi | 54–790 MHz | 26.7–568.9 Mbps | up to 100 m |
| Bluetooth | 2.4 GHz | 100 Kbps | up to 100 m |
| Bluetooth LE | 2.4 GHz | <1 Gbps | up to 50 m |
| Z-Wave | 686 MHz, 908 MHz, 2.4 GHz | 40 K | up to 100 m |
| ZigBee | 868 MHz, 915 MHz, 2.4 GHz | 20 kbps to 250 kbps | 10–75 m |
| ISA100.11a | 868 MHz, 915 MHz, 2.4 GHz | 20 kbps to 250 kbps | up to 600 m |
| MiWi | 868 MHz, 915 MHz, 2.4 GHz | 20 kbps to 250 kbps | 20–50 m |
| Thread | 868 MHz, 915 MHz, 2.4 GHz | 20 kbps to 250 kbps | up to 100 m |
| WirelessHART | 868 MHz, 915 MHz, 2.4 GHz | 20 kbps to 250 kbps | 30–100 m |
| LTE-A | Cellular bands | 1 G (up), 500 M (down) | up to 50 km |
| GSM | Cellular bands | 150 Mbps | up to 50 km |
| LTE-Cat M | Cellular bands | up to 1 Mbps | 15 km |
| NB-IoT | Cellular bands | <180 kbps | 15 km |
| LoRaWAN | 169/433/868/780/915 MHz ISM | 300 bit to 100 kbit/s | 2.5–15 km |
| NFC | 13.56 MHz | up to 424 kbps | <20 cm |
| DASH7 | 433/868/915 MHz ISM/SRD | 9.6–166.667 kbit/s | up to 5 km |
| nWave | Sub-1 GHz ISM | 100 bit/s | 10–30 km |
| SigFox | 868/902 MHz ISM | 100 bit/s | 12–30 km |
| Technology/Protocol | Attack | Threat | Threat Category |
|---|---|---|---|
| RFID | Tag Disable | Jamming | A |
| Tag Modification | Unauthorized Access and modification of critical information | C, I | |
| Cloning Tags | Counterfeiting and spoofing | C, A | |
| Reverse Engineering | Counterfeiting and spoofing | C, A | |
| Eavesdropping | Unauthorized Access of critical information | C | |
| Snooping | Unauthorized Access of identity and data | C | |
| Skimming | Imitates the original RFID tag | C, A | |
| Replay Attack | Deceiving readers | C, A | |
| Relay Attacks | man-in-the-middle | I, A | |
| EM Interference | Jamming | A | |
| Fake RFID tag queries | illicit Tracing and Tracking | C, A | |
| Cryptograph Decipher attack | Password Decoding | C, I | |
| blocker tag Attack | DoS Attack | A | |
| ZigBee | Sniffing | sniffing the keys | C |
| Replay attack | MiTM | C, I | |
| Killerbee Packer | Manipulation Attack Device Spoofing | C | |
| Killerbee - zbassocflood | Crash the device | A | |
| Eavesdropping | MiTM | C, I | |
| ZED Sabotage Attack | DoS | A | |
| WiFi | FMS/KoreK/PTW/ARP Injection/Dictionary Attack | Key Retrieving Attacks | C |
| ChopChop/ Fragmentation/Caffe Latte/Hirte | Keystream Retrieving Attacks | C, I | |
| Authentication related Attacks | DoS | A | |
| Association related Attack | DoS | A | |
| Flooding related attacks | DoS | A | |
| Honeypot | MiTM | C, I | |
| Evil Twin/Rogue AP | MiTM | C, I | |
| Bluetooth | Bluebugging | Espionage | C, I |
| Bluesnarfing | Espionage and DoS | C, A | |
| Sniffing Attacks | Interception | C | |
| Hijacking | DoS and spoofing | A, C, Identity | |
| Fuzzing | DoS | A | |
| Spoofing | Spoofing | Identity | |
| NFC | Interception | Eavesdropping | C |
| Data corruption through Interception | DoS | I, A | |
| Data Modification through interception | MiTM | I | |
| Data Insertion | MiTM | I | |
| NFC Data Exchange Format (NDEF) attacks | Identity Theft and Non repudiation | C, Identity |
| ML Method | Attack Types Handled | Pros | Cons |
|---|---|---|---|
| KB [108,109,111,113] | HTTP attacks (Buffer overflow, Shell attacks) [111], DoS, Probe, R2L [109] |
| It fails to take into account interdependencies between features for classification purposes, which affect its accuracy [113]. |
| KNN [116,117,118,119,120] | U2R, R2L, Flooding attacks, DoS, DDoS |
| Determining optimal value of K and identifying missing nodes are challenging. |
| DT [125,126,127] | DDoS [127], U2R, R2L [125] |
|
|
| SVM [131,132,133] | Scan, DDoS (TCP, UDP flood), smurf, portsweep |
|
|
| EL [144,145,146,163] | DoS, Probe, R2L, U2R attacks |
|
|
| RF [150,151] | DoS, Probe, R2L, U2R |
|
|
| K-Means [157,158,164] | DoS, Probe, R2L, U2R |
|
|
| PCA [159,160,161,162] | Used in combination with other ML methods |
|
|
| Study | Machine Learning | Deep Learning | Dataset | Threat Detected | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| NBC | KNN | DT | SVM | EL | RF | K-Means | RNN | CNN | AE | RBM | DBN | EDLN | GAN | |||
| [110,111] | ✓ | - | - | ✓ | - | - | ✓ | ✓ | - | - | - | - | - | - | KDD99 | Anomaly Detection |
| [116] | - | ✓ | - | - | - | - | - | - | - | - | - | - | - | - | KDD99 | apache2 udpstorm processtable mailbomb |
| [125] | - | - | - | - | - | - | - | ✓ | ✓ | - | - | - | - | - | ADFA-LD and ADFA-WD | Adduser Meterpreter Webshell |
| [129] | - | - | - | ✓ | - | - | - | - | - | - | - | - | - | - | DARPA dataset | Probe attack, U2R attack |
| [143] | - | - | - | - | ✓ | - | - | - | - | - | - | - | - | - | KDD99 | Network Traffic anomaly detection |
| [150] | - | - | - | - | - | ✓ | - | - | - | - | - | - | - | - | Boot-strapped | Worms, Buffer overflows |
| [157] | - | - | - | - | - | - | ✓ | - | - | - | - | - | - | - | KDD99 | - |
| [165] | - | - | - | - | - | - | - | ✓ | - | - | - | - | - | - | ISCX2012 | PROBE attacks or non-PROBE attacks |
| [166] | - | - | - | - | - | - | - | ✓ | ✓ | - | - | - | - | - | Android Malware Genome project | Malware |
| [167] | - | - | - | - | - | - | - | - | - | ✓ | - | - | - | - | Outlier Detection DataSets | Anomaly detection |
| [168] | - | - | - | - | - | - | - | - | - | - | ✓ | - | - | - | KDD | - |
| [169] | - | - | - | - | - | - | - | - | - | - | - | - | - | ✓ | NSL-KDD | - |
| [170] | - | - | - | - | - | - | - | - | - | - | - | ✓ | - | - | 500 samples for dataset | Anomaly detection |
| DL Technique | Attack Types Handled | Pros | Cons |
|---|---|---|---|
| RNNs [176,177,178,179,180,181,182,183] |
| The major challenge in the use of RNNs is handling the issue of vanishing or exploding gradients, which hinders learning of long data sequences. | |
| CNNs [189,190] | Malware attacks |
|
|
| Deep Autoencoders [41,167] |
|
|
|
| RBM [192,193] | -R2L, DoS, U2R and Probe |
|
|
| DBNs [188,195] |
|
|
|
| GAN [191] |
|
|
|
| EDLNs [41,198] |
|
|
|
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Asharf, J.; Moustafa, N.; Khurshid, H.; Debie, E.; Haider, W.; Wahab, A. A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions. Electronics 2020, 9, 1177. https://doi.org/10.3390/electronics9071177
Asharf J, Moustafa N, Khurshid H, Debie E, Haider W, Wahab A. A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions. Electronics. 2020; 9(7):1177. https://doi.org/10.3390/electronics9071177
Chicago/Turabian StyleAsharf, Javed, Nour Moustafa, Hasnat Khurshid, Essam Debie, Waqas Haider, and Abdul Wahab. 2020. "A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions" Electronics 9, no. 7: 1177. https://doi.org/10.3390/electronics9071177
APA StyleAsharf, J., Moustafa, N., Khurshid, H., Debie, E., Haider, W., & Wahab, A. (2020). A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions. Electronics, 9(7), 1177. https://doi.org/10.3390/electronics9071177








